Risky Biz News: Russian bill will hide the PII data of military, police, and intelligence agents
In other news: Bitfinex 2016 hacker finally uncovered; ransomware attack cripples hospitals across five US states; and LetMeSpy shuts down after hack.
This newsletter is brought to you by no-code automation platform Tines. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
The Russian government has submitted a bill to the Duma (the Russian Parliament) that would grant the military, law enforcement, and intelligence agencies the power to edit, anonymize, or delete the personal data of certain groups of people—presumably their own employees.
At first reading, the proposed law appears to allow these agencies to freely edit the personal information of their own employees in order to protect their identities or hide deep cover agents.
As TASS reports, the draft law allows the Russian president to place certain groups of individuals into a special category, for which special rules will be in place when processing their personal data by local data operators.
The law will allow the Ministry of Defense, the Ministry of Internal Affairs, the FSB, the FSO, and the SVR to access the systems of local data operators in order to "clarify, extract, depersonalize, block, delete, or destroy personal data."
In addition, the proposed law also amends Russia's data protection law to prohibit state and municipal databases from storing information about the "departmental affiliation" of military, police, and intelligence agents.
If approved—and there are high chances this will go through the Duma quite quickly—parts of the proposed law will start being enacted as soon as March 1, 2024.
From an intelligence perspective, the law might help with the creation of covert identities, but the lack of data on certain Russian citizens is often also a big red flag that you're looking at a possible fake persona, so we're not really buying its potential use for intelligence operations. Foreign intelligence agencies have far more resources and data points to spot fake personas than Russian government databases.
Instead, cyber threat intelligence researcher Roman Sannikov believes the proposed law will have a major impact on another front—namely, in regard to investigative journalism.
"During the administration of Dmitry Medvedev, Russia actually implemented various new laws and regulations to foster transparency and make it appear as if they were tackling corruption. Subsequently, groups like Belingcat and Navalny's team, as well as other investigative and anti-corruption organizations, used these resources to identify things like cell phone locations and call patterns to figure out who was where and who was communicating with whom or who owned what property," Sannikov says.
"If that information is no longer available for certain intelligence operatives, one would suspect that they are involved in sensitive or corrupt activities, but it will be much harder to show that individual A was in location B at the same time that C happened.
"Honestly, this seems like a law designed to thwart the activities of organizations like Belingcat. Though it may also help prevent the targetting of some Russian military personnel," he adds.
Breaches, hacks, and security incidents
Bitfinex hack: A New York man arrested last year for laundering cryptocurrency from the Bitfinex hack has admitted, in an unexpected turn of events, to being the hacker behind the incident. Ilya Lichtenstein's guilty plea comes seven years after he hacked the company in 2016, and stole almost 120,000 Bitcoin. The stolen funds were worth $71 million at the time of the hack but are now worth more than $4.5 billion. Lichtenstein was detained in February 2022, together with his wife, Heather Morgan. Morgan pleaded guilty to money laundering charges but said she didn't find out about the hack until 2020, at which point she helped her husband cover the crime. The couple's arrest drew intense media coverage in 2022 due to Morgan using some of her acquired wealth to finance a rapper career.
NISC's Barracuda hack: Japan's cybersecurity agency NISC has disclosed a breach of its email systems. The agency says a threat actor had access to sensitive emails between October 2022 and June 2023 after they exploited a vulnerability in its email servers. While the agency did not specifically mention it, the NISC appears to be one of the victims of the Barracuda email server hacks. The attacks were linked to a threat actor tracked as UNC4841, which Google's Mandiant says might be linked to China.
CDHE breach: The Colorado Department of Higher Education (CDHE) has disclosed a massive data breach stemming from a ransomware attack it suffered in June. The Department says hackers gained access to its systems for nine days, during which time they stole years-worth of personal data belonging to current and past students and teachers. Anyone who attended or taught at a Colorado high school between 2004 and 2020 is most likely impacted. The Department says it plans to notify each affected individual by email once its investigation is over.
"While the review is ongoing, those that attended a public institution of higher education in Colorado between 2007-2020, attended a Colorado public high school between 2004-2020, individuals with a Colorado K-12 public school educator license between 2010-2014, participated in the Dependent Tuition Assistance Program from 2009-2013, participated in Colorado Department of Education's Adult Education Initiatives programs between 2013-2017, or obtained a GED between 2007-2011 may be impacted by this incident."
Prospect Medical ransomware attack: Hospitals and clinics in five US states closed their emergency rooms last week in the aftermath of a ransomware attack. The incident hit Prospect Medical Holdings and impacted facilities in California, Connecticut, Rhode Island, Pennsylvania, and Texas. The company's systems have been offline since Tuesday when the intrusion was first detected. [Additional coverage in CBS News]
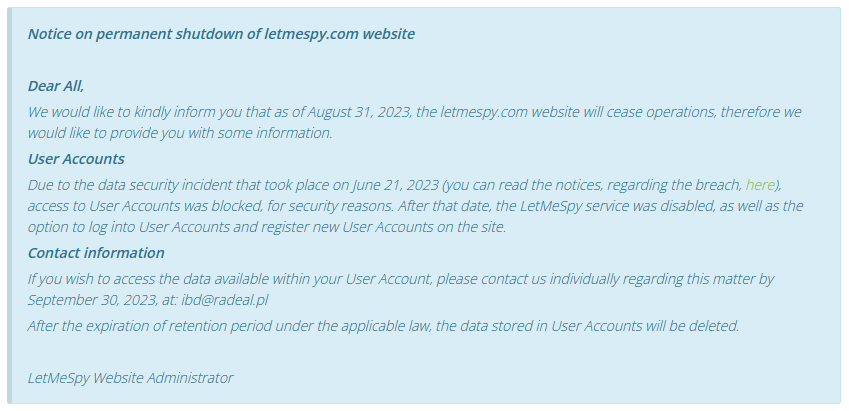
LetMeSpy to shut down: Poland-based spyware company LetMeSpy has announced it will shut down at the end of the month. LetMeSpy's announcement comes after a hacker breached the company's servers and posted its customers' information online. The hack exposed the names and email addresses of all LetMeSpy customers and the data each customer collected from infected devices. Even if the shutdown is scheduled for August 31, LetMeSpy has already disabled customer logins on its site and removed its Android app from its servers. [Additional coverage in TechCrunch]
General tech and privacy
Chrome downloads redesign: Google has redesigned the Chrome downloads popups.
Pixel Binary Transparency: Google has published a technical breakdown of Pixel Binary Transparency, a security system in Google Pixel smartphones that keeps metadata records of official factory image records, allowing devices to cryptographically verify they are using official Pixel factory operating system images that have not been tampered with during transit.
Chrome OS split: Google is getting close to shipping Lacros, a new version of the Chrome OS where the underlying Linux OS is split from the Chrome browser. The new Chrome OS Lacros version has been in the works for years, and it will allow Google to update each component separately. For example, Chrome browser security updates won't need to be packaged as an OS update anymore. [Additional coverage in ArsTechnica]
Twitter Blue update: Twitter now lets Blue users hide their blue verification checkmark. Yet another measure from Twitter to allow propaganda to flourish on its site. Pay for prime placement, and hide your checkmark to avoid getting exposed as a bot in an InfoOp. [Additional coverage in TechCrunch]
Government, politics, and policy
Separate telco for RU state employees: The Russian government is preparing to launch a virtual cellular operator for the exclusive use of state employees. The new virtual operator will run on top of the networks of four "classic" Russian ISPs, allowing government workers to have optimal signal connection and quality at all times. [Additional coverage in Izvestia]
Shin Bet warns of Iranian phishing: The Shin Bet security agency says it uncovered an Iranian spear-phishing campaign that targeted Israeli researchers and state employees. Officials say the campaign had been going on for months and aimed to obtain intelligence on state policy. Initial contact would take place via email or LinkedIn, and targets would be sent malware-laced documents after operatives gained their trust. [Additional coverage in the Times of Israel]
Pakistan loves Cellebrite: An investigation has discovered that Pakistan's main spy agency, the Federal Investigation Agency, is a Cellebrite customer. Interesting news since Pakistan doesn't recognize Israeli passports but apparently likes its cyber tools. [Additional coverage in Haaretz/non-paywall]
"As Haaretz has reported on numerous occasions, Cellebrite's clients have included oppressive regimes that were or still are subject to sanctions, including Belarus, China (including Hong Kong), Uganda, Venezuela, Indonesia, the Philippines, Russia and Ethiopia, as well as Bangladesh's notorious Rapid Action Battalion."
UK's mad: The UK's privacy watchdog, the ICO, is mad because Meta plans to seek consent from EU users for behavioral advertising but not from UK users. Hmm! There's something here that both I and the ICO can't put our finger on. I wonder what!
CISA calls for better UEFI security practices: CISA has asked the UEFI community to improve the standard's cybersecurity by adopting a "secure by design" practice. The agency's request comes after security researchers spotted a piece of UEFI malware named BlackLotus that had taken advantage of weak UEFI security practices. CISA has asked for more UEFI security updates from vendors, better UEFI-related logging, and the ability to audit and manage UEFI components.
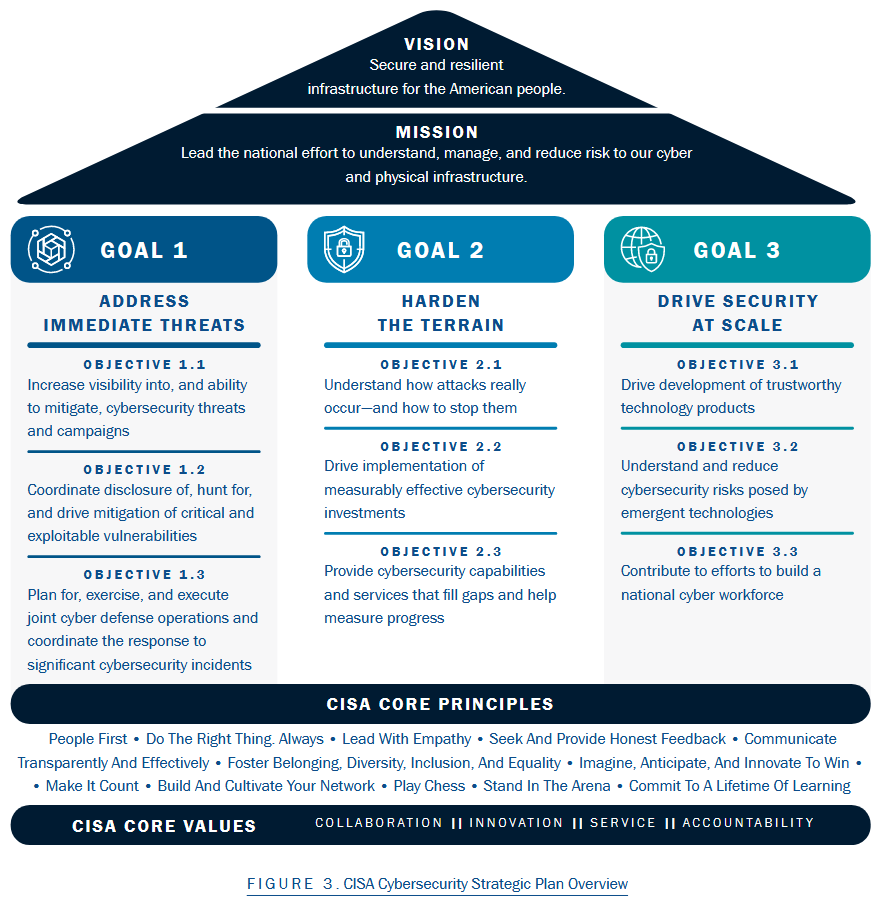
CISA Cybersecurity Strategic Plan: CISA has released its strategic plan on how it plans to improve the cybersecurity posture of the US's government agencies and private sector. The plan is centered around three areas of focus:
—› Address Immediate Threats by making it increasingly difficult for our adversaries to achieve their goals by targeting American and allied networks;
—› Harden the Terrain by adopting strong practices for security and resilience that measurably reduce the likelihood of damaging intrusions; and
—› Drive Security at Scale by prioritizing cybersecurity as a fundamental safety issue and ask more of technology providers to build security into products throughout their lifecycle, ship products with secure defaults, and foster radical transparency into their security practices so that customers clearly understand the risks they are accepting by using each product.
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Tines co-founder and CEO Eoin Hinchy about how organizations can maximize the potential of their security teams during an economic downturn, with a concentration on why human error and burnout caused by excessive workloads on security teams can be a risk.
Cybercrime and threat intel
Nigerian BEC scammer pleads guilty: A Nigerian man has pleaded guilty to stealing $1.25 million from a US company via a BEC attack. The suspect is named Onwuchekwa Nnanna Kalu, 39, from Rivers State, Nigeria, and the victim was identified as an investment firm located in Boston.
Hacktivism financing: KELA looked at the various tactics employed by hacktivist groups to finance their operations, such as renting their DDoS botnet, engaging in hacked data trading, extortion, and classic donations.
FBI's NFT warning: The FBI has published an official security alert warning that threat actors are posing as Non-Fungible Token (NFT) developers in fraud schemes targeting the NFT community. Officials say scammers are hacking official accounts or creating clones that lure NFT owners to malicious sites. These websites ask users to link their cryptocurrency wallet to claim limited NFT assets but secretly steal the victim's cryptocurrency or NFTs. Stolen funds and assets are often sold and laundered through mixers to hide their final destination and make their recovery almost impossible.
Adware on the Play Store: McAfee researchers have identified 43 apps on the official Play Store that contain adware. The apps were downloaded more than 2.5 million times and targeted audiences in South Korea. The apps posed as TV/DMB players, music downloaders, calendars, and news applications.
Healthcare data leaks: Just like HDD/SDD storage devices, USB drives, printers, and almost any other piece of smart gear, old discarded or decommissioned medical devices are also rife with healthcare data, according to a study performed by Rapid7.
New npm malware: Thirty-seven malicious npm packages were discovered last week. Check out GitHub's security advisory portal for more details. DevSecOps company Phylum looks at one of these campaigns that abused the brands of CryptoRocket and Binarium.
New PyPI malware: And since FOSS malware comes in pairs, there's also a report (actually two) on recent malicious Python libraries imitating popular open-source packages.
Cloudflare Tunnel abuse: Guide Point researchers describe how threat actors have abused CloudflareD, a client app for the Cloudflare Tunnel service, to exfiltrate data from compromised environments.
Malware technical reports
Operation PhantomControl: eSentire analyzes Operation PhantomControl, a malspam campaign infecting users with a version of AsyncRAT.
Batloader: Trend Micro looks at Batloader's recent campaigns and techniques employed since June 2023.
MerlinAgent: Ukraine's CERT team has posted IOCs on MerlinAgent, an infostealer used in attacks against Ukrainian government and private sector entities.
DODO and Proton: Fortinet has a write-up on DODO and Proton, two new ransomware strains spotted in attacks. Both target end users rather than enterprise environments.
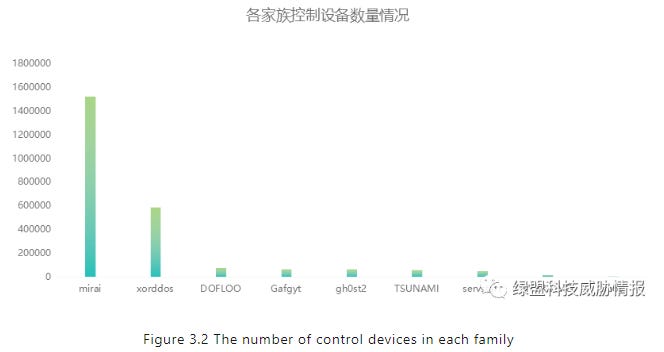
XORDDOS: Chinese security firm NSFOCUS takes a look at the evolution of XORDDOS, today's second-most populous IoT malware strain, right behind Mirai.
Sponsor Demo
In this demo, Tines CEO and co-founder Eoin Hinchy demonstrates the Tines no-code automation platform to RiskyBiz host Patrick Gray.
APTs and cyber-espionage
Bitter=Mysterious Elephant: Chinese security firm KNOW Chuangyu says that the Mysterious Elephant APT group that Kaspersky described in a recent report is the Bitter APT group they spotted earlier this year using a new backdoor named ORPCBackdoor.
HUI Loader: A security researcher named Morimolymoly has published a technical analysis of HUI Loader, a malware strain used by multiple APT groups, such as APT10, A41APT, DEV-0401, and Blue Termite.
Vulnerabilities, security research, and bug bounty
Points.com vulnerabilities: A team of security researchers has identified and helped fix multiple vulnerabilities in the API of Points[.]com, a reward points platform used by some of the world's largest airlines and hotel chains. The vulnerabilities could have allowed attackers to retrieve customer data, manipulate rewards points, or perform various administrative actions. Companies that could have had their platforms impacted included Delta, United, Hilton, Marriott, Etihad, and others.
Incognito Chain vulnerability: Security firm Trail of Bits has identified a vulnerability in the Incognito blockchain that could have been used to mint arbitrary tokens and drain user funds.
New LOLBAS binaries: Security researchers at Pentera have identified 12 new LOLBAS (Living Off the Land Binaries And Scripts) items that can be abused by malware and threat actors for stealthy attacks. New binaries include executables for the Microsoft Outlook email client and the Microsoft Access database, but also the PyCharm Python IDE.
Silent Pthon security patches: An academic study has found that the vast majority of security fixes to Python packages have been resolved using "silent" patches and without vulnerabilities being publicly acknowledged or receiving a CVE identifier. The study analyzed more than 749,000 security issues across 197,000 Python packages. Researchers say they found only 1,232 vulnerabilities that received a CVE and only 556 security flaws with fixes publicly reported.
"The hidden security fixes pose a threat to the security and privacy of users, since attackers may exploit the undisclosed vulnerabilities to comprise the unpatched software systems."
New PaperCut vulnerability: Security firm Horizon3 has published a technical analysis for CVE-2023-39143, another RCE vulnerability in PaperCut print management servers. The vulnerability was patched last month.
"Compared to CVE-2023-27350, CVE-2023-39143 also does not require attackers to have any prior privileges to exploit, and no user interaction is required.
In contrast to CVE-2023-27350, CVE-2023-39143 is more complex to exploit, involving multiple issues that must be chained together to compromise a server. It is not a "one-shot" RCE vulnerability."
Zoho ManageEngine PoC: A technical write-up and PoC are now available for CVE-2023-35719, an authentication bypass in the Zoho ManageEngine ADSelfService Plus component. Not that of a big deal since the bug requires physical access.
Microsoft patches Azure: Microsoft has patched an Azure Power Platform vulnerability discovered by Tenable. The patch was initially scheduled for September but was accelerated after Tenable's CEO chewed Microsoft out for its unprofessionalism.
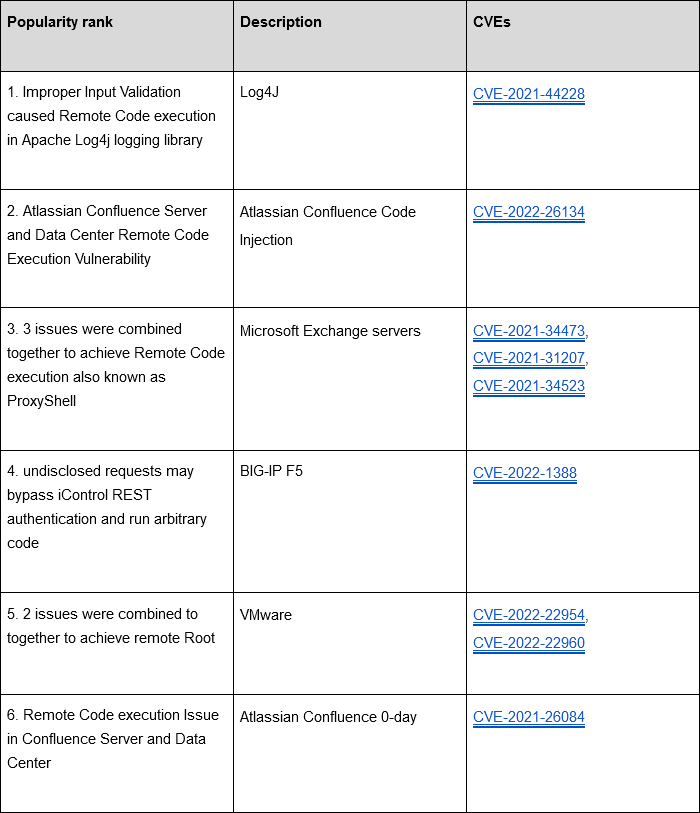
Top exploited vulnerabilities, per Cloudflare: After CISA published its list of most commonly exploited vulnerabilities of 2022, internet infrastructure company Cloudflare published its own list. CISA's top vulnerability (a Fortinet bug, CVE-2018-13379) didn't make Cloudflare's list, which shows the different sets of bugs used to target US government entities, compared to Cloudflare's mostly private sector worldwide customer base.
Infosec industry
SBOM usage: A study carried out by DevSecOps company Sonatype has found that roughly 92% of today's large enterprises now maintain an SBOM strategy or plan to implement one in the next year.
Tool update—Suricata: V7.0 of the Suricata network threat detection system is out. V6.0 came out in 2020, so this is a major release after a long, long time.
New tool—Mido: Security researcher Elliot Killick has released Mido, a tool for downloading the latest Windows ISO images from Microsoft's servers. Killick says the tool was the product of "reverse engineering of Microsoft's hidden downloading API."
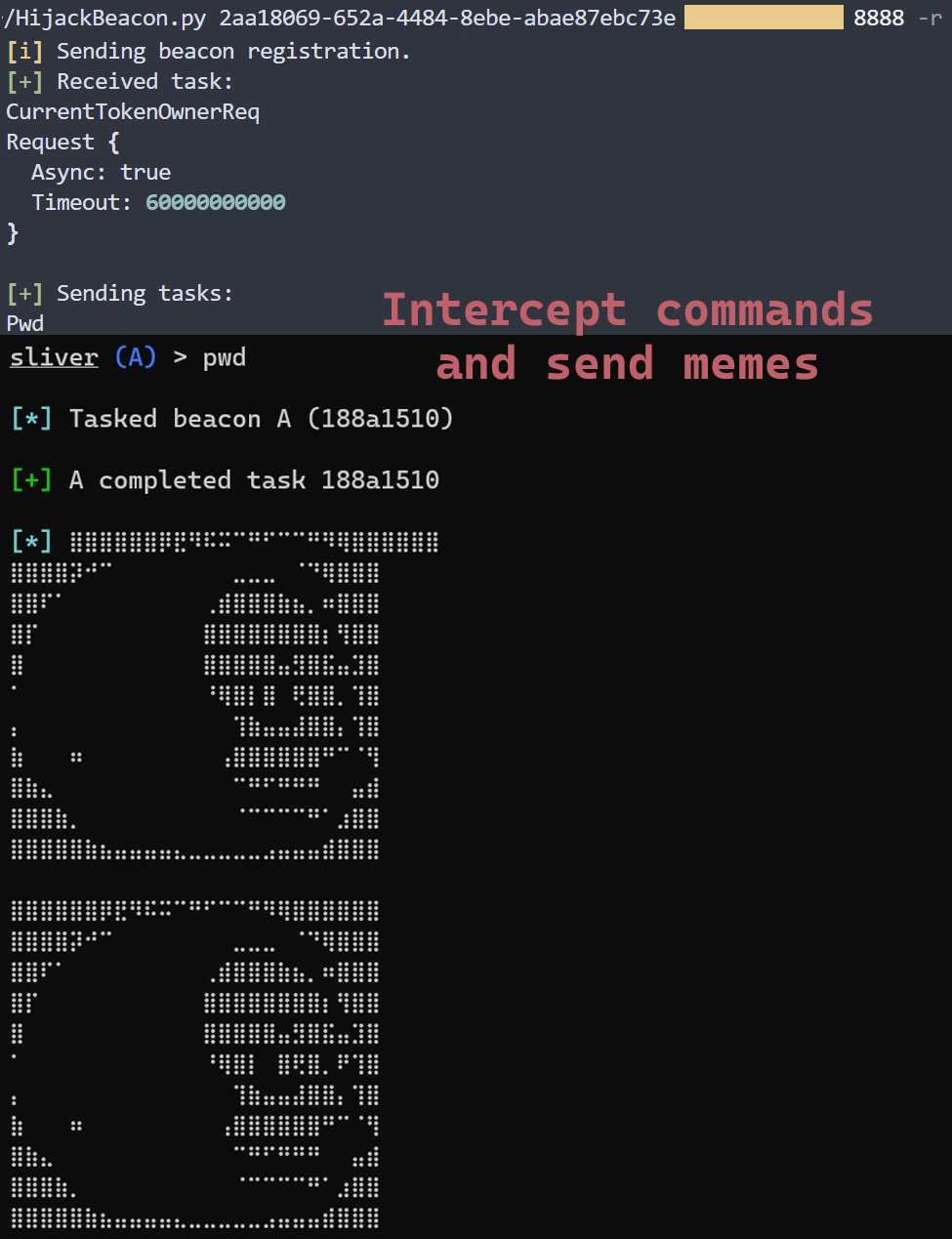
New tool—RogueSliver: ACE Responder has released a tool named RogueSliver that can disrupt malware or red-team operations that use the Sliver C2 framework. It can hijack beacons, send memes to the attacker, or flood and crash C2 servers.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq look at the arguments against intellectual property theft and why there isn't a universal agreement that it should be prohibited.




