Risky Biz News: Russia hacked 22 Danish critical infrastructure companies
In other news: Personal medical alarm button provider goes down in the Netherlands; Juniper bugs exploited in the wild; and two new bugs let threat actors steal crypto assets.
This newsletter is brought to you by Gigamon. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Spotify:
Russian state-sponsored hackers have breached at least 22 Danish companies operating in the country's energy sector.
Denmark's CERT team for the critical infrastructure sector (SektorCERT) described the intrusions as the largest cyber-attack in the country's history.
In a report [Danish PDF, machine-translated English file] published over the weekend, SektorCERT tentatively attributed the attacks to Sandworm, a cyber unit inside Russia's military intelligence service GRU.
The intrusions happened throughout May and took place across multiple waves.
SektorCERT says the initial point of entry was Zyxel firewalls. The first wave of attacks exploited a vulnerability tracked as CVE-2023-28771, while the other waves used a combination of CVE-2023-33009 and CVE-2023-33010.
Zyxell released patches for the three bugs in June.
The hacked companies had to disconnect from the internet to investigate the hacks, but SektorCERT says there was no impact on their operations, and the attacks were most likely intended for reconnaissance and establishing persistence.
DR, the Danish Broadcasting Corporation, says the 22 hacked companies provide electricity and heat to around 100,000 Danes.
Ironically, the intrusions took place three days after Denmark's cybersecurity agency raised the country's cyberespionage threat level to VERY HIGH.
SektorCERT says it detected the intrusions through a network of sensors it has installed at electricity, heating, and water plants across Denmark.
Breaches, hacks, and security incidents
Tunstall cyber-attack: Dutch company Tunstall has advised customers to keep their phones at hand after a cyber-attack has disrupted its personal medical alarm system. The attack took place on Saturday and is still ongoing. Tunstall says the incident is blocking alarms from reaching its control room. Primarily used by the elderly, these are buttons that trigger alerts in the company's control room whenever a customer is facing a healthcare emergency.
ICBC ransomware incident: The LockBit ransomware group claims the US branch of the Industrial and Commercial Bank of China has paid its ransom after LockBit encrypted its systems at the end of last week, shutting down the Chinese bank's ability to honor transactions on the US market. [Additional coverage in BusinessTimes]
TSTT ransomware incident: The Telecommunications Services of Trinidad and Tobago, the largest telco in the country, has confirmed it got hacked by the RansomExx ransomware gang at the start of October.
Avito data leak: More than 2.7 million user records from Moroccan e-commerce service Avito have been dumped into the public domain. The data was stolen in a November 2022 security breach.
McLaren breach: US healthcare provider McLaren Health says hackers gained access to the private and health data of almost 2.2 million customers after the company suffered a ransomware attack in July. The alleged culprits are the AlphV (BlackCat) gang.
General tech and privacy
Chrome to remote third-party cookies: Google engineers have announced plans to deprecate and remove support for third-party cookies from the Chrome web browser. Third-party cookies will be removed for 1% of the Chrome userbase in Q1 2024, and a gradual phaseout will follow for all users in Q3. Google is removing third-party cookies after it shipped a stable version of its Privacy Sandbox technology this year.
WhatsApp usernames are coming: Meta is working on adding support for usernames on WhatsApp to replace its current system, where phone numbers serve as user identities. Rival instant messaging app Signal is also working on a similar system. Support for WhatsApp usernames is currently available in WhatsApp's Android beta.
.NET 8: Microsoft has released v8 of the .NET runtime.
TikTok denies promoting pro-Hamas content: Chinese social media company TikTok has put out a statement denying accusations that it is promoting Palestinian and pro-Hamas content.
Government, politics, and policy
FCC cybersecurity pilot: The Federal Communications Committee has proposed the creation of a pilot program for K-12 schools and libraries to learn the best ways to protect these organizations against cyber threats. The proposed pilot program will run for three years with a budget of up to $200 million.
CISA AI roadmap: CISA has released a roadmap for the secure development and implementation of artificial intelligence capabilities.
ENISA-UA agreement: The EU's cybersecurity agency ENISA has signed a cooperation agreement with Ukraine's SSSCIP focusing on information exchange and capacity building.
UK NCSC Annual Review: The UK NCSC has published its Annual Review, a report that looks forward to future risks and issues the UK may face next year. At the top are AI, the "epoch-defining challenge posed by China," and an increase in aggressivity from state-aligned cyber groups.
Separate internet for BRICS+ countries: Russian officials are working on a plan to create their own separate internet for all the BRICS+ countries. [Additional coverage in RIA Novosti]
Nepal bans TikTok: The Nepalese government has banned Chinese social media app TikTok. Officials say the app disrupts social harmony. The ban entered into effect this week, shortly after it was announced. Officials didn't provide details on what led to their decision. [Additional coverage in the AP]
Sponsor section
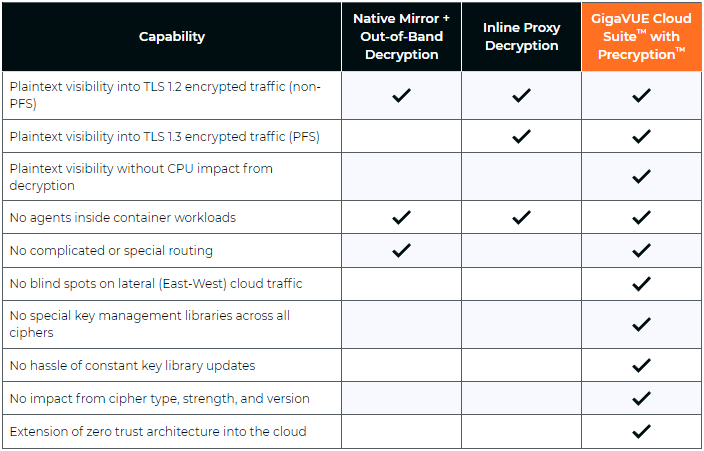
In this Risky Business News sponsor interview, Tom Uren talks to Ryan Mahoney, Product Director at Gigamon. The TLS 1.3 encryption standard makes passive network monitoring inside your network difficult without break-and-inspect contortions. But Gigamon has what they call a "precryption" solution!
Cybercrime and threat intel
FBI dismantles IPStorm botnet: US law enforcement dismantled the IPStorm botnet and detained the malware's creator. Identified as a Russian and Moldovan national named Sergei Makinin, the suspect has already pleaded guilty in the US to three hacking-related charges. He created the malware in 2019 and infected more than 23,000 Windows, Linux, macOS, and Android devices. Officials say Makinin made more than $550,000 by proxying web traffic through the infected devices. He sold access to his proxy botnet on the proxx.io and proxx.net portals.
Scattered Spider investigation: A Reuters investigation has found that the FBI is allegedly aware of the real-world identities of at least a dozen members of the Scattered Spider group. Cybersecurity executives told Reuters the FBI has been aware of this information for at least six months but has not made any arrests, even if some members are based in the US. The Scattered Spider group is responsible for recent breaches at the MGM and Caesars casino operators but has been active for more than two years. Security experts say most of the group's members are based in Western countries. [Additional coverage in Reuters/non-paywall]
Google sues malware devs: Google has sued a group of John Does for distributing malware disguised as its Bard AI tool.
Mirai story: Wired has published a 22,000-word story of how three teens started the Mirai botnet back in 2016. [Additional coverage in Wired/non-paywall]
Campaign targeting French gamers: Sekoia has discovered a malware campaign targeting French gaming influencers.
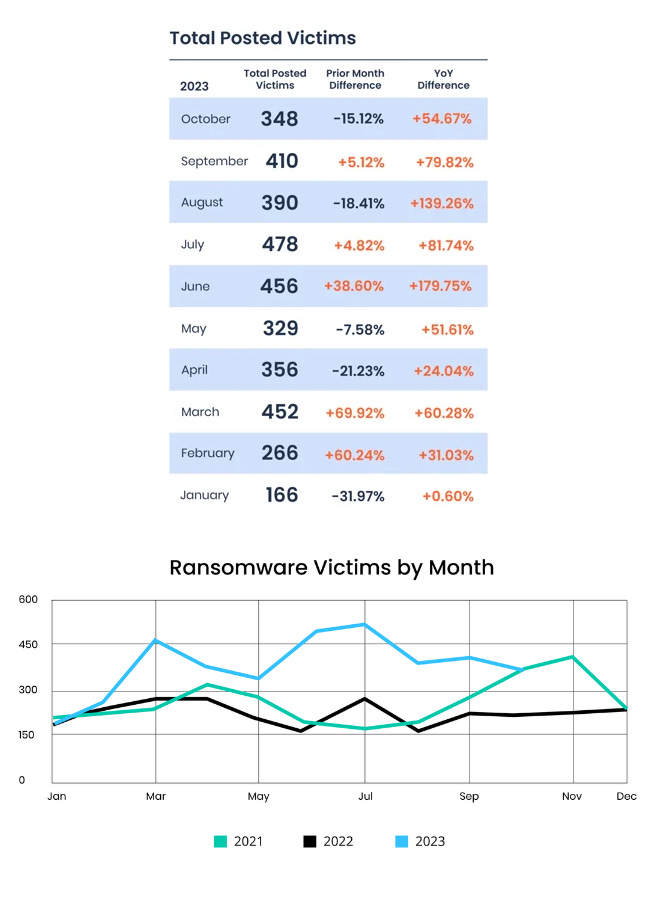
Oct 2023 ransomware stats: Ransomware gangs have listed 348 victims on dark web leak sites in the month of October, but 2023 is still on track to be the most prolific year for ransomware operators, according to cyber insurance provider Corvus.
Malware technical reports
OracleIV: A threat actor is targeting publicly exposed instances of the Docker Engine API to infect cloud infrastructure with a new malware strain named OracleIV. Cado Security says the malware is written in Python and contains functions for cryptomining and DDoS attacks.
Ddostf: South Korean security firm AhnLab has discovered Ddostf, a new DDoS malware strain being installed on MySQL database servers.
PikaBot: OALABS covers the recent resurgence of PikaBot activity.
C3RB3R ransomware: SentinelOne has published a report on the C3rb3r ransomware strain that has been recently deployed on hacked Atlassian Confluence servers via the CVE-2023-22518 vulnerability.
Medusa ransomware: NCC Group takes a deep dive into Medusa, a RaaS platform that's been around since June 2021.
Royal ransomware: CISA and the FBI have published a joint advisory on the Royal ransomware. Officials say the gang targeted more than 350 victims across the world, with ransom demands totaling more than $275 million. Officials did not say how many victims paid and how much.
Sponsor Demo
Brought to you by Gigamon Precryption, a visibility solution for encrypted traffic across virtual machine (VM) or container workloads. Perform advanced threat detection, investigation, and response across the hybrid cloud infrastructure. To learn more, please visit gigamon.com/precryption
APTs, cyber-espionage, and info-ops
APT29 attacks on embassies: Hackers linked to Russia's Foreign Intelligence Service (SVR) have been observed abusing a recently patched WinRAR zero-day (CVE-2023-38831) in attacks targeting embassies across Europe. The attacks took place between April and October of 2023 and targeted embassies in Italy, Greece, Romania, and Azerbaijan. APT29 joins fellow Russian group APT28, which also exploited the same vulnerability in a campaign targeting Ukrainian organizations. APT28 is linked to Russia's military intelligence service, which would explain why they targeted Ukrainian entities only while APT29 targeted other countries.
Storm-0978 (RomCom): Palo Alto Networks has published a write-up detailing how the Storm-0978 (RomCom) group has been exploiting CVE-2023-36884, a zero-day in the Windows Search feature, in attacks against Ukrainian organizations. PAN says the zero-day was used in conjunction with CVE-2023-36584, a MotW bypass, via weaponized Office documents.
UAC-0050: Ukraine's CERT team is warning about a series of attacks against government agencies trying to install the Remcos RAT. The agency attributed the attacks to UAC-0050, a threat actor it's been tracking since 2020. Similar attacks were spotted in a February campaign as well.
TA402: Proofpoint researchers have published a breakdown of a phishing campaign carried out by TA402, a cyber-espionage group also known as Molerats or the Gaza Cybergang. The campaign lasted between July and October, targeted organizations in the MENA region, and used a malware strain named IronWind.
"Based on Proofpoint's tracking of this threat actor since 2020, TA402 remains a persistent and innovative threat actor that routinely retools its attack methods and malware in support of its cyber espionage mandate. Its ongoing use of geofencing and decoy documents continues to serve its detection evasion efforts. While TA402 is an intelligence collection focused threat actor with a specific interest in Middle Eastern and North African government entities, the group could find itself under direction to adjust its targeting or social engineering lures in reaction to the ongoing Israel-Hamas conflict."
Fire Demon Snake: Qihoo 360 has published a report on a new APT group it tracks as Fire Demon Snake (or APT-C-52). The company says the APT is most likely based in South Asia, began operations in 2021, and primarily targets Pakistani military personnel.
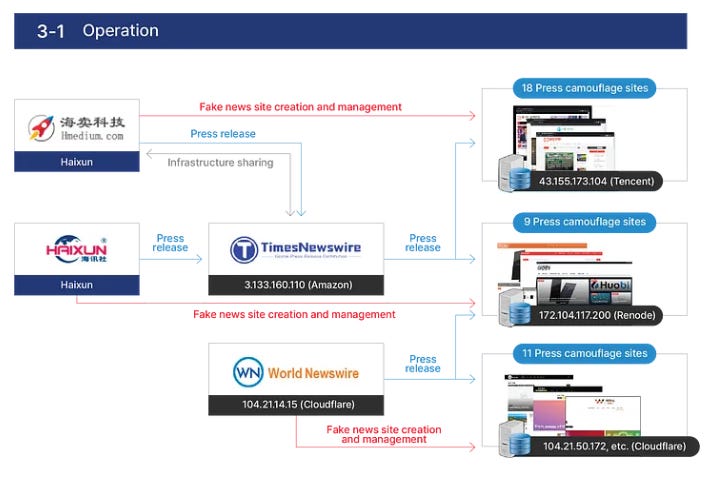
Chinese fake news sites in KR: South Korean spy agency NIS has identified a network of 38 websites posing as fake Korean news agencies. The sites published pro-Chinese and anti-US articles targeting Korean-speaking audiences. NIS says the sites were created and managed by two Chinese PR firms named Haimai and Haixun. The agency says a third unidentified company also tried to distribute fake news articles through a South Korean newswire service. NIS credited South Korean cybersecurity companies EST Security and SK Shieldus for discovering the network. [Additional coverage in S2W]
Vulnerabilities, security research, and bug bounty
Patch Tuesday: Yesterday was the November 2023 Patch Tuesday. We had security updates from Adobe, Microsoft, Chrome, SAP, Citrix, Fortinet, Kubernetes, AMD, Intel, Schneider Electric, and Siemens. The Android Project, Apple, Cisco, Atlassian, VMWare, Zyxel, Juniper, Zoom, OpenVPN, QNAP, Veeam, GitLab, and Drupal released security updates last week as well.
Microsoft zero-days: This month, Microsoft's Patch Tuesday included 83 fixes, including three zero-days tracked as:
- CVE-2023-36025 - Bypass of Windows SmartScreen
- CVE-2023-36033 - EoP in the Windows DWM Core Library
- CVE-2023-36036 - EoP in the Windows Cloud Files Mini Filter Driver
Juniper exploitation: CISA says that five Juniper bugs that were patched in August are now actively exploited in the wild to take over unpatched devices. Proof-of-concept code for the vulnerabilities has been available online since the end of August, shortly after the patches. Juniper says it detected attacks as early as the start of November.
Siemens disables Twitter feed: ICS equipment vendor Siemens has disabled its CERT feed on Twitter, citing the API price hikes.
PyPI security audit: The Python Package Index, also known as PyPI, has completed its first security audit. It was performed by security firm Trail of Bits. The audit found 29 vulnerabilities, including three major issues that could have allowed threat actors to pivot into internal infrastructure and hijack the service.
CacheWarp attack: A team of academics has discovered a vulnerability that can allow threat actors to run malicious code inside virtual machines hosted using the AMD Secure Encrypted Virtualization (SEV) platform. Named CacheWarp (CVE-2023-20592), the attack can be used to grant access and retrieve data from inside SEV-secured virtual machines. AMD has released patches for current CPUs that support the SEV platform. Older models remain vulnerable.
Create2 vulnerability: A threat actor has drained an estimated $60 million worth of crypto assets by exploiting a vulnerability in the Ethereum blockchain. The attacker exploited a bug in the Create2 function to bypass transaction security protections and add itself as the recipient. Discovered by ScamSniffer, the attacks impacted almost 100,000 wallets. ScamSniffer says the vulnerability has now also been integrated into wallet phishing operations.
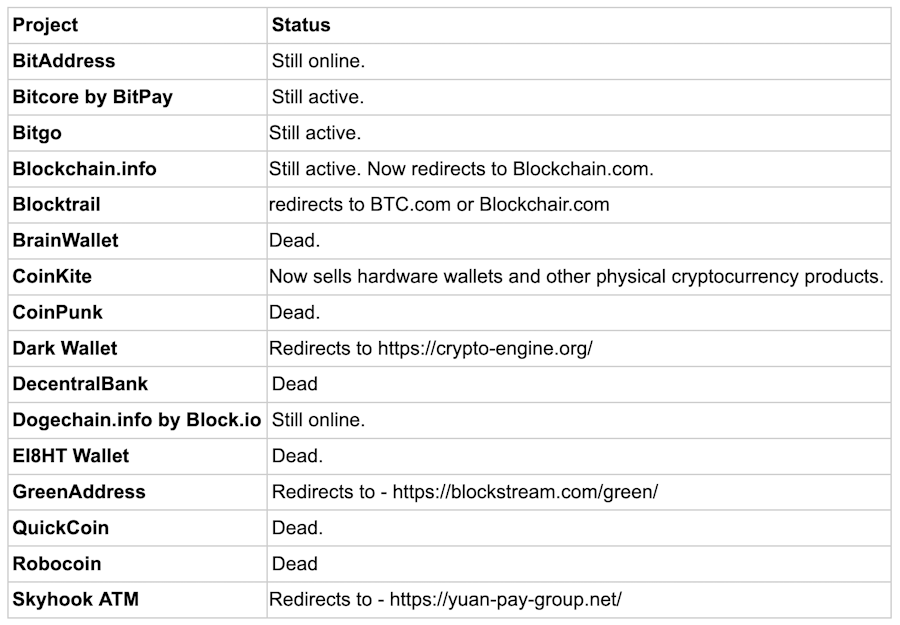
Randstorm vulnerability: Blockchain security firm Unciphered has discovered a vulnerability in BitcoinJS, a popular JavaScript library used in many browser-based crypto-wallets. Named Randstorm, the vulnerability uses an insecure RNG algorithm to generate cryptographic keys needed to access web crypto wallets. Unciphered says the Randstorm bug can be abused to determine private keys generated by BitcoinJS. Unciphered told the Washington Post that up to $1 billion worth of crypto assets are currently stored in vulnerable wallets. Most use private keys generated between 2011 and 2015 when the bug was present in the library. A list of web wallets that use or used BitcoinJS is embedded below.
Infosec industry
New tool—Open Source Fortress: Canonical security engineer George-Andrei Iosif has released Open Source Fortress, a workshop containing theoretical and practical information about detecting vulnerabilities in codebases.
New tool—CVE Half-Day Watcher: AquaSec has open-sourced a tool named CVE Half-Day Watcher, designed to show risks around vulnerability disclosures on how some reports may lead to leaks and early exploitation.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about International Humanitarian Law, aka the Rules of War in cyberspace. These rules don't really make sense in cyberspace, but despite that, Tom and The Grugq think talking about them (and other norms of behavior) is still worthwhile.




