Risky Bulletin: Windows 10 reaches End-of-Life
In other news: CISA layoffs didn't touch cyber personnel; US seizes $15 billion from cyber scam compound operator; Secure Boot bypass impacts 200k Framework systems.

This newsletter is brought to you by Nebulock. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
The Windows 10 operating system reached End-of-Life (EOL) on Tuesday, October 14, after more than 10 years since its official release back in July 2015.
The OS won't receive any new security updates unless users or companies enroll in the Extended Security Updates (ESU) program.
Because Windows 10 is still installed on around 40% of all Windows systems, Microsoft has made this ESU the first one available to home consumers—ESUs were initially introduced to provide extended paid support for larger enterprises.
Initially, home users could pay $30 for Windows 10 ESUs, but Microsoft made them free over the summer. All EU users will get the ESUs for free if they log into Windows 10 with a Microsoft account, while users in other regions will have to sync their PC settings to a Microsoft account to get enrolled (still for free).
Users who don't wanna go through this process still have the option to upgrade to Windows 11 for free, but they should also be aware that they cannot use Windows 11 with an anonymous local account anymore and that Windows 11 will require a Microsoft account and an internet connection to install.
The new OS is also notorious for its intrusive telemetry and bloat/crapware, so it might not be for most users. Many Linux desktops are usable these days—yes, unbelievable, I know—and may be a good alternative for users who may at least want to give it a try.
Companies still have to pay for ESUs, except for organizations in the educational sector. Paid enterprise ESUs will last for three more years, while the home user ESUs will be available just for one.
Micro-patch providers, such as 0patch, have already announced support for Windows 10 for companies that can't afford ESU pricing down the line, since it goes up for every year of support.
Microsoft Exchange 2016 and 2019 email servers also reached End-of-Life on the same day.
Risky Business Podcasts
The main Risky Business podcast is now on YouTube with video versions of our recent episodes. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
South Korea to investigate KT for obstruction: The South Korean government has asked law enforcement to investigate Korea Telecom for obstructing an official probe. The telecom allegedly failed to cooperate with government investigators in a probe of KT's micropayments platform. KT customers reported losing almost $170,000 to suspicious transactions that were later linked to a data breach. KT is the country's second-largest telecom. [Additional coverage in the Korea Times]
Harvard breach: Harvard University is investigating a data breach related to the recent attack wave that targeted Oracle EBS platforms.
Ansell breach: Australian protective equipment maker Ansell has disclosed a security breach. The company linked the hack to vulnerabilities in a third-party software. It also said most of the data is non-sensitive business information. [Additional coverage in iTnews/ASX filing PDF]
Unity shop skimmer incident: Almost 430 users who shopped on the Unity SpeedTree store have had their personal and financial data stolen. Malicious code was active on the site between March 13 and August 26. The website is part of the Unity game engine brand and is used to sell procedural modeling tools.
5CA denies role in Discord hack: Customer support service provider 5CA has denied being the source of a recent Discord security breach. The company is contesting news reports that identified it as the source. 5CA says it never handled ID records for Discord users. It also said the breach took place "outside" of its systems and might have involved "human error." [h/t CucuriguSurprise]
General tech and privacy
4chan fined in the UK: The UK's communications watchdog has fined 4chan £20,000 ($26,000) for non-compliance with the UK Online Safety Act. The law required 4chan to verify the age of its users before showing adult content. The fine will increase by £100 ($133) per day until paid.
Calls to investigate TikTok: British trade unions and online safety experts have urged the UK government to investigate TikTok over its plan to lay off 439 workers from its UK moderation team. The groups say the layoffs will have a massive impact on online safety. The signatories also accused TikTok of union-busting as the company announced the firings a week before the workers scheduled a vote to unionize. [Additional coverage in The Guardian]
Firmware update bricks Jeeps: A firmware update has bricked Jeep 4xE plug-in hybrid models over the weekend. The update was for the car's telematics module. Users who installed it reported losing power to their electric engines and getting stuck on public roads. Jeep canceled the update once reports started coming back from its US customers. [Additional coverage in The Stack]
Firefox 144: Mozilla has released Firefox 144. New features and security fixes are included. The biggest feature in this release is a dedicated profile manager and several UI updates to the tab groups feature. The built-in Firefox Password Manager now also uses a modern encryption scheme (AES-256-CBC) instead of the old 3DES-CBC.
Free Firefox VPN: Mozilla has started the development of a free VPN feature for Firefox users. This will be a separate product from Mozilla VPN, the company's commercial OS-level VPN.
Government, politics, and policy
California regulates AI: California Governor Gavin Newsom signed several bills into law on Monday that regulate the AI industry, AI chatbot companions, introduce social media warning labels, and require mandatory age checks for OS and app store providers.
CISA layoffs avoided cyber division: Last Friday's CISA layoffs did not impact the agency's cybersecurity personnel. The layoffs targeted employees in CISA's Stakeholder Engagement Division, a team that manages relations with local and international partners. They also impacted the Integrated Operations Division, which runs CISA's around-the-clock watch center, and CISA's Chemical Security unit. [Additional coverage in CybersecurityDive]
UK Crypt-Key goes live: The UK has rolled out a new system to distribute encryption keys over the network. The new Crypt-Key system will be used to replace practices where cryptographic keys are distributed via punched tape and CDs. Crypt-Key cost the government £2.6 billion. [Additional coverage in The Stack]
Taiwan warns of "abnormal" social media accounts: Taiwan's intelligence agency has identified more than 10,000 "abnormal" social media accounts that distributed more than 1.5 million disinformation messages. Most of the accounts were active on Facebook. Officials also say that Chinese state media is now coordinating with its troll armies to attack Taiwan's independence and push pro-CCP views. [Additional coverage in Reuters]
Annual threat reports: Cybersecurity agencies in Australia and the UK have published their annual cyber threat reports on Tuesday. The most significant finding was from the UK NCSC report, which saw "nationally significant cyber attacks" go from 89 last year to 204 this year, with the agency warning that the UK now sees four of these every week.
Sponsor section
In this Risky Business sponsor interview, Tom Uren talks to Damien Lewke, CEO and founder of Nebulock, about countering adversary use of AI… with AI. They talk about how threat actors are rapidly adopting AI and what defenders should be doing in response.
Arrests, cybercrime, and threat intel
Operation Heracles: German and Bulgarian authorities have seized more than 1,400 websites that were used for financial scams. The sites lured users to invest in cryptocurrency, collected funds, and then disappeared overnight. Officials recorded more than 866,000 attempts to access the sites over the ten days after they were seized, which highlighted the attackers' success and large footprint. [Additional coverage in Heise]
US cracks down on Prince Group scam operator: The US government has seized $15 billion worth of crypto from one of the world's largest operators of cyber scam compounds. The US has sanctioned and filed charges against the Prince Group and its CEO, Chen Zhi. The Group operated multiple prison-like scam compounds across Cambodia. Individuals trafficked into the country were forced to carry out online scams under the threat of violence. The compounds operated out of casinos and luxury hotels owned by the Group.
About those funds, though: Blockchain analysis company Elliptic has an interesting post about those seized $15 billion funds, which the company says they trace back to the mysterious hack of Chinese mining pool LuBian in December 2020.
"It remains unclear how the bitcoins came to be in US custody. It's also unclear who 'stole' the bitcoins from Chen/LuBian or whether a theft really took place. An orchestrated theft may have provided an extra level of complexity to a scheme designed to obfuscate and launder billions of dollars from online scams. Perhaps more likely, an opportunistic hacker saw the opportunity to take LuBian's bitcoins, before coming to the attention of the US government."
SonicWall SSLVPN mass-compromise: More than a hundred SonicWall SSLVPN devices have been hacked over the past week. Security firm Huntress says attackers used valid credentials to authenticate and take over the devices. All the successful authentications came from the same IP address. On some devices, the attackers moved laterally across the victim network and escalated their access. Huntress believes the attacks are related to a recent breach at SonicWall, where hackers stole device configuration backups from the company's cloud service.
Another surveillance provider exposed: A phone-tracking and surveillance platform named Altamides has been used to secretly track the movements of more than 14,000 phone numbers. According to leaked records, the platform was used to track political figures, famous executives, journalists, and activists. It exploited vulnerabilities in the SS7 telecommunications protocol to pinpoint an individual's location using only their phone number. The platform has been around for two decades and is managed by Indonesian company First WAP, and run by Europe-based executives. [Additional coverage in Lighthouse Reports, Mother Jones, Der Standard, Der Spiegel, Le Monde, IRPImedia]
"In Italy, investigative journalist Gianluigi Nuzzi was tracked days after publishing a dramatic exposé of corruption in the Vatican, as police closed in on his source. In California, Anne Wojcicki, founder of DNA startup 23andMe and then married to Google's Sergey Brin, was tracked more than a thousand times as she moved across Silicon Valley. And in South Africa, associates of Rwandan opposition leader Patrick Karegeya were tracked before his assassination in a Johannesburg hotel room."
TA585 profile: Proofpoint has published a profile on TA585, a cybercrime group that operates its own infrastructure to deploy a newly developed RAT/loader known as MonsterV2 (sold by another threat actor).
Oct 7 DDoS attacks: Radware looks at the wave of DDoS attacks that hit Israel around the anniversary of the October 7 attack.
ClickFix infrastructure: Three-quarters of all malicious ClickFix infrastructure was already known to security researchers for hosting AitM phishing pages. The overlap suggests that existing threat actors are incorporating the ClickFix technique in their operations, rather than new specialized groups emerging around it. Lab539 says it's now tracking over 13,000 domains carrying ClickFix lures.
Telegram phishing emoji packs: Security firm DarkTower has discovered four different Telegram emoji packs that contain bank logos and are likely used in cybercrime channels as a way to order phishing pages.

Malware technical reports
PolarEdge backdoor: Sekoia has published a report on the backdoor that is deployed on hacked servers and IoT devices and controls the PolarEdge proxy botnet.
Qilin ransomware: AhnLab has published a technical report on the Qilin ransomware, an operation that launched in 2022 and has now become one of the top 3 most active ransomware groups.
LinkPro Linux rootkit: Synacktiv looks at LinkPro, a new Linux eBPF-based rootkit it found deployed on a customer's hacked AWS infrastructure.
Sponsor section
Agentic AI platform Nebulock pitches its product in one of our recent Snakeoilers episodes.
APTs, cyber-espionage, and info-ops
TikTok info-ops summary: TikTok has published its monthly report on covert influence operations the company has spotted on its platform in August this year. The company took down influence networks targeting political discourse in Bolivia, Chile, Ecuador, and Moldova. The largest of these networks targeted Moldova, but the one targeting Ecuador was run from abroad, from Venezuela.
UAC-0239: Ukraine's CERT has spotted UAC-0239 impersonating the SSU intelligence service in a phishing campaign targeting local governments and its military.
UNC-RUS-ZIC: Security researcher Mohammad Abdullah Al Mamun has spotted a Russian threat actor attacking APAC countries (Indonesia, Japan, Thailand, Bangladesh, India) in a campaign that began last month.
Flax Typhoon: Chinese APT group Flax Typhoon modified an ArcGIS Java server object extension (SOE) into a webshell to maintain access to a network undetected, per a new ReliaQuest report.
"The attackers repurposed a legitimate Java server object extension (SOE) into a web shell, gated access with a hardcoded key, and embedded it in backups to evade detection and maintain persistence."
China offers reward for Taiwan's psychological warfare unit: Chinese authorities have issued rewards for information on 18 Taiwanese military members. Police in China's Fujian province claim the 18 are part of Taiwan's "psychological warfare unit." The unit is allegedly involved in spreading disinformation, Taiwan independence propaganda, and intelligence gathering. Bounties of $1,400 have been offered for each. [Additional coverage in The Guardian]

Vulnerabilities, security research, and bug bounty
Patch Tuesday: Yesterday was the October 2025 Patch Tuesday. We had security updates from Adobe, Microsoft, Fortinet, Dell, IBM, SAP, Ivanti, D-Link, Axis, ASUS, Firefox, Supermicro, NVIDIA, AMD, Schneider Electric, Siemens, Rockwell Automation, ABB, Samsung, Qualcomm, Moodle, Elastic, and Zoom. Chrome, Oracle, Cisco, Palo Alto Networks, CrowdStrike, Grafana, QNAP, DrayTek, OpenSSH, Unity, Splunk, and Moxa released security updates last week as well.
Microsoft Patch Tuesday: This month, Microsoft patched 172 vulnerabilities, including fixes for three actively exploited zero-days.
- CVE-2025-24990 — Windows Agere Modem Driver Elevation of Privilege Vulnerability
- CVE-2025-59230 — Windows Remote Access Connection Manager Elevation of Privilege Vulnerability
- CVE-2025-47827 — Secure Boot bypass in IGEL OS before 11
KEV update: CISA has updated its KEV database with five vulnerabilities that are currently exploited in the wild. This includes a 2016 SKYSEA bug, the three Microsoft bugs listed above, and a recent Velociraptor bug abused in the wild by ransomware groups.
ICTBroadcast exploitation: Threat actors are exploiting a vulnerability in the ICTBroadcast call center auto-dialer software. Tracked as CVE-2025-2611, the vulnerability allows remote attackers to inject and run commands on ICTBroadcast servers. Exploitation is simple, doesn't require authentication, and involves modifying the cookie field in HTTP headers. According to VulnCheck, there are almost 200 ICTBroadcast servers currently exposed on the internet.
Framework Secure Boot bypass: More than 200,000 Framework laptops and desktops are vulnerable to a Secure Boot bypass. The devices shipped with a signed UEFI shell environment that can be abused to bypass the Secure Boot process and load malicious code at startup. Framework has released security updates after being notified by Eclypsium researchers this year.
NVIDIA GPU driver vulns: Quarkslab has published a write-up on two bugs it found and reported to NVIDIA that impacted its GPU drivers. Both were patched this month.
Kiwire vulnerabilities: LRQA researchers have discovered three vulnerabilities (SQLi, XSS, and open redirection) in the Kiwire Captive Portal software. They were patched in September.
Slider Revolution vulnerability: More than four million WordPress sites are impacted by a vulnerability in the Slider Revolution plugin.
RMPocalypse attack: A team of academics has developed a new attack that breaks the confidentiality of AMD secure enclaves. The RMPocalypse attack targets a security feature of the AMD SEV-SNP enclave named the Reverse Map Table. The attack exploits a short window of time during the boot where the attacker can overwrite the RMP with malicious code. Impacted AMD CPU models include Zen 3 through 5.
Pixnapping attack: A team of academics has developed a new attack that can recover sensitive information from Android smartphones. The Pixnapping attack uses a malicious app installed on a target device. The malicious app opens other apps and steals their sensitive data using native Android APIs. A side-channel attack then allows the attacker to recover individual pixels from the app and later reassemble sensitive information. The attack was successfully used to recover sensitive texts from Signal chats and 2FA codes from Google Authenticator. [h/t Alan Wang]
'Any running Android app can mount this attack, even if it does not have any Android permissions (i.e., no permissions are specified in its manifest file).' 👀 @gate15.bsky.social
— andy jabbour (@andyjabbour.bsky.social) 2025-10-14T12:31:06.148Z
LatentBreak attack: Academics have developed a new type of LLM jailbreak that they named LatentBreak.
>>>>>> "LatentBreak substitutes words in the input prompt with semantically-equivalent ones, preserving the initial intent of the prompt, instead of adding high-perplexity adversarial suffixes or long templates. These words are chosen by minimizing the distance in the latent space between the representation of the adversarial prompt and that of harmless requests."
Half of satellite traffic is unencrypted: A team of academics was able to intercept and spy on satellite communications traffic using a simple $800 device installed on the roof of their building. The project lasted three years, and almost half of the picked-up traffic was unencrypted. Researchers intercepted mobile carrier calls, texts, and even military and government secrets. T-Mobile moved to encrypt its satellite communications following the research team's report. [Additional coverage in WIRED]
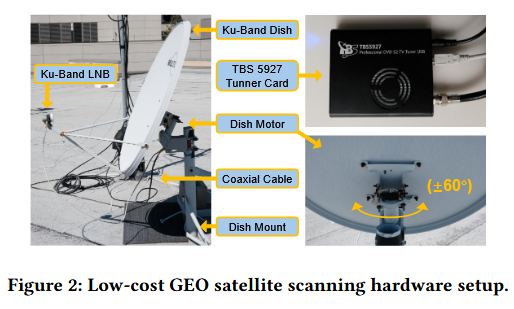
A lot of this data, such as the T-Mobile leak, is now encrypted thanks to the researchers' work. But all of it was obtained from a single dish on the roof of a building in San Diego. These findings are based on just 15% of geostationary satellite signals over the US and Mexico.
— Andy Greenberg (@agreenberg.bsky.social) 2025-10-14T01:06:15.384Z
Infosec industry
JPMorgan Security and Resiliency Initiative: American bank JPMorgan has announced the Security and Resiliency Initiative, a project that plans to invest $1.5 trillion over the next 10 years in national security projects. This will also cover cybersecurity. [Additional coverage in CNBC]
Infosec drama: FuzzingLabs has accused Gecko Security of stealing two CVEs and backdating blogs.
Acquisition news #1: Former AT&T security division, LevelBlue, has acquired struggling XDR provider Cybereason for an unknown sum.
Acquisition news #2: Digital identity and access management company Imprivata has acquired ITDR provider Verosint.
New tool—Rulezet: NGSOTI has launched Rulezet, an open-source web platform for sharing, evaluating, improving, and managing cybersecurity detection rules (YARA, Sigma, Suricata, etc).
Threat/trend reports: ACSC, Kaspersky, Health-ISAC, Microsoft, NewsGuard, and the UK NCSC have recently published reports and summaries covering various threats and infosec industry trends.
Risky Business podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about how different cybercriminal groups are looking for insiders to provide network access.
In this edition of Seriously Risky Business, Tom Uren and Amberleigh Jack talk about the Clop ransomware gang. It is interesting because the Group has arrived at a strategy that rinses a whole lot of enterprises at once and comes with a decent payday. But it's actually the least damaging kind of ransomware. Tom wonders why more gangs can't be like Clop?




