Risky Bulletin: US sanctions another Russian bulletproof hosting provider
In other news: The ICC discloses security breach; US dismantles 29 DPRK laptop farms; Chinese student gets jailed in the UK for SMS blasting in London.

This newsletter is brought to you by Sandfly Security. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
The US Treasury Department has sanctioned the Aeza Group, a well-known provider of bulletproof web hosting services for malware, disinformation campaigns, and dark web marketplaces.
Sanctions were levied on the main company, three subsidiaries, its three owners, and a fourth high-ranking executive. They cover:
- The main Aeza Group, headquartered in St. Petersburg, Russia;
- Aeza International Ltd., the UK branch;
- Aeza Logistic LLC and Cloud Solutions LLC, Russian subsidiaries;
- Arsenii Aleksandrovich Penzev, CEO and owner;
- Yurii Meruzhanovich Bozoyan, general director and owner;
- Igor Anatolyevich Knyazev, owner and currently managing the company after the arrest of Penzev and Bozoyan;
- and Vladimir Vyacheslavovich Gast, technical director.
Officials have linked Aeza Group's server infrastructure to the Lumma, Meduza, and RedLine infostealers, the BianLian ransomware, and the BlackSprut dark web drugs marketplace.
The sanctions don't mention anything about Aeza hosting disinformation campaigns, but Correctiv and Qurium investigations linked the company to a Russian disinformation group known as Doppelganger.
According to the two reports, Aeza allowed Doppelganger to host its mountain of fake news sites on European data centers and avoid direct and easy-to-spot connections back to Russia.
The sanctions are the last thing Aeza is probably thinking about right now, as the company also got in big trouble in their own backyard, back home in Russia.
Russian police detained both Penzev and Bozoyan at the start of April. Authorities charged them with drug trafficking for their role in hosting BlackSprut, a dark web marketplace that primarily catered to Russian-speaking users.
Aeza is now the third Russia-based bulletproof hosting provider sanctioned this year.
In February, Australia, the US, and the UK sanctioned Zservers, and in May, the EU sanctioned Stark Industries.
Risky Business Podcasts
The main Risky Business podcast is now on YouTube with video versions of our recent episodes. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
ICC contains breach: The International Criminal Court says it detected and contained a "sophisticated" security breach. The intrusion was detected late last week, but no other details are available. The ICC was also hacked in September 2023.
Radix hack impacts Swiss government: A ransomware gang has stolen sensitive data belonging to multiple Swiss federal offices. The files were stolen on June 16 from Radix, a nonprofit organization working with the Swiss government. A ransomware operation named Sarcome took credit for the attack. The group leaked over 1TB of files on the dark web last week after Radix refused to pay a ransom demand.

Hackers threaten to sell stolen Trump emails: Iranian hackers are threatening to sell emails stolen from the Trump campaign last year. The hackers claim to have more than 100GB of emails from the accounts of White House Chief of Staff Susie Wiles, Trump lawyer Lindsey Halligan, Trump adviser Roger Stone, and others. They obtained the files after hacking the Trump campaign in May of last year. The hackers told Reuters they might also release the files online if they don't find a vendor. The US charged three Iranian intelligence agents with the hack.
New: “Robert” is back, and the Iran-linked hacking group is threatening to disclose the balance of what they say are 100GB worth of emails from a trio of Trump allies: www.reuters.com/legal/govern...
— Raphael Satter (@raphae.li) 2025-06-30T22:31:08.838Z
Now disinformation is a forbidden word the regime has to twist themselves into knots to avoid using it.
— Eliot Higgins (@eliothiggins.bsky.social) 2025-07-01T18:32:29.184Z
General tech and privacy
Apple adds PQC support: Apple is adding post-quantum cryptography support to its operating systems. Upcoming versions of iOS 26 and macOS 26 will support the ML-KEM cryptography algorithm. ML-KEM will protect TLS connections against powerful quantum computing attacks, expected to break encrypted comms in the near future. Microsoft also announced PQC support for Windows in May. [Additional details in Apple's WWDC video]
Proton sues Apple too: VPN provider Proton has joined a class-action lawsuit against Apple for abusing its market position to impose huge fees on app developers through its iOS store.
Ubuntu disables GPU Spectre protections: Ubuntu has disabled a security feature that protected Intel GPUs against Spectre side-channel attacks. The OS said it now uses kernel-level protections, and the protections were no longer needed. Ubuntu devs expect the OS to see a 20% in graphics performance following the update. [Additional coverage in ArsTechnica]
Cloudflare blocks AI crawlers: Cloudflare says it is now blocking AI crawlers by default and has offered websites a "pay per crawl" option to let AI companies crawl their content in exchange for a fee.
Tinder makes facial scans mandatory in California: Tinder is running a test in California and will require all new users to scan their faces during the account creation process. The new feature is meant to reduce user impersonation on the platform. All accounts that pass the face scan will automatically receive a verified badge. The feature is already live in Canada and Colombia, and this is the first time being tested in the US. [Additional coverage in Axios]
AT&T Wireless Account Lock: US mobile carrier AT&T has launched a new feature to lock accounts and prevent SIM swapping attacks. The new Wireless Account Lock can be enabled exclusively via the AT&T app. Once enabled, it blocks any changes to a customer's billing details or wireless number transfers until it's disabled again. Similar features already exist on T-Mobile, Verizon, and Google Fi. [Additional coverage in CyberScoop]
MSFT spam-bomb protection: Microsoft has added spam-bomb protection to Defender for Office.
Delayed Windows security updates: Microsoft has confirmed that some devices didn't receive the Windows security updates for June due to an incorrect timestamp. [Additional coverage in BleepingComputer]
Windows loses 400 million users: According to a recent ZDNet report, Microsoft has lost 400 million Windows PC users since 2022.
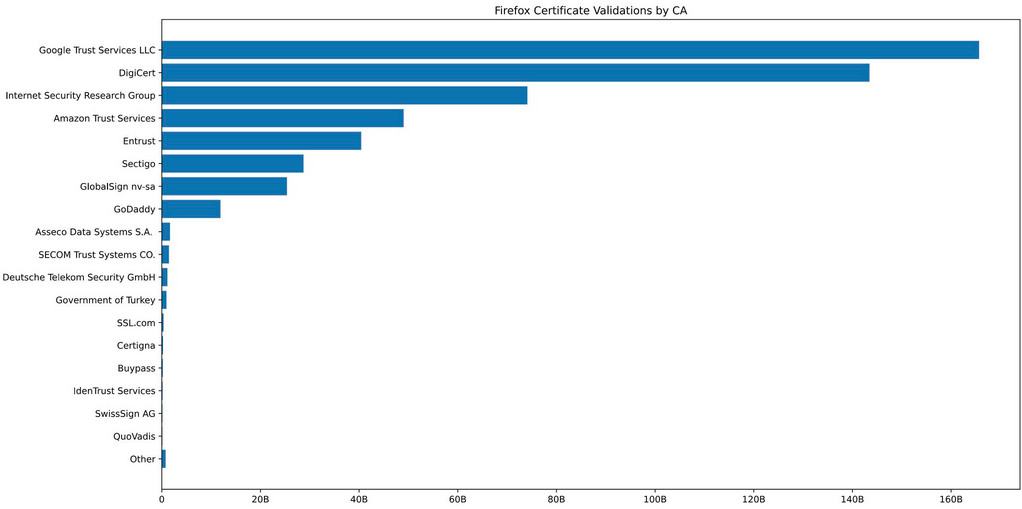
Let's Encrypt is the third-largest CA on the internet: According to Mozilla data, Let's Encrypt (Internet Security Research Group) is the third-largest CA on the internet. [h/t Matthew McPherrin]
Government, politics, and policy
White House builds national citizens database: The Trump administration has built a central database of all US citizens. According to NPR, the White House plans to use the new platform during upcoming elections to verify the identity and citizenship status of US voters. The database was built by the Department of Homeland Security and the Department of Governmental Efficiency and is being rolled out in phases to US states.
US officials need better mobile security guidance: US Senator Ron Wyden has asked the FBI to update the guidance it sends to US officials on how to secure their mobile devices. Sen. Wyden says the guidance is obsolete in the current threat landscape. The guidance should include recommendations that officials enable ad-blocking features and disable ad-tracking IDs. US officials should also be told to enable anti-spyware lockdown modes available in both Android and iOS devices. [Additional coverage from KrebsOnSecurity/Sen. Wyden letter/PDF]
NY breach reporting law: The US state of New York has passed a new cybersecurity law mandating local authorities to report cybersecurity incidents to the state government within 72 hours.
California bill rolls back privacy protections: The EFF warns that a California bill (S.B. 690) will roll back most of the state's privacy protections and grant online companies and data brokers the right to record anything users do online without consent.
CyberCommand requests more funds: US Cyber Command has request an increased budget to support cyber defense in the Pacific region. The new request is for $117.2 million, up from the initial anticipated spending of $20.8 million. [Additional coverage in DefenseScoop]
China's Cyberspace Force: Grey Dynamics has published a profile of China's recently established Cyberspace Force, its structure, doctrine, and composing units.
"The creation of the People's Liberation Army Cyberspace Force marks a pivotal step in China's effort to integrate cyber operations into its core military doctrine. By consolidating offensive, defensive, and electronic warfare capabilities under central command, the PLA has positioned cyberspace as a primary battlefield, not just a supporting tool. This force will almost certainly play a central role in any future conflict involving China."
Sponsor section
In this Risky Bulletin sponsor interview, Craig Rowland, CEO of Sandfly Security, talks to Tom Uren about the disconnect between how important Linux systems are and how much security attention they get. The pair discuss the variety of reasons that security teams underinvest in protecting Linux.
Arrests, cybercrime, and threat intel
Europol dismantles crypto investment ring: Europol has arrested five members of a crypto investment scam ring. The group was detained in Spain. They allegedly laundered over €460 million stolen from over 5,000 victims. The five ran a network of money mules across the world that withdrew cash from ATMs and moved funds through bank and crypto accounts.
US disrupts 29 DPRK laptop farms: The FBI has raided and dismantled 29 laptop farms across the US that were used in North Korean remote IT worker schemes. The farms hosted over 200 laptops that allowed the North Korean workers to appear as if based in the US. The workers used stolen identities to obtain jobs at more than 100 US companies. The Justice Department charged eight individuals who ran the laptop farms, as well as four of the North Korean workers who abused their jobs to steal crypto-assets from their employers.
Chinese student jailed in UK for SMS blasting: A UK judge has sentenced a Chinese student to more than a year in prison for using an SMS Blaster to send SMS phishing texts. Ruichen Xion installed the SMS blaster in a Honda car and drove around London. He allegedly sent tens of thousands of messages before he was caught after a joint investigation between police and UK mobile operators. UK authorities arrested seven other people and seized seven SMS blasters in separate cases.

New Iran cyber warning: US cyber agencies have issued a new warning about possible Iranian cyber operations targeting critical infrastructure. They released the alert after the US struck Iranian nuclear program targets. Now that things have calmed down and that power and internet access have returned to Iran, the US fears a cyber response.
TA829 and UNK_GreenSec link: Proofpoint has spotted some overlaps between the TA829 (RomCom) and UNK_GreenSec (TransferLoader) threat actors.
"In the current threat landscape, the points at which cybercrime and espionage activity overlap continue to increase, removing the distinctive barriers that separate criminal and state actors. [...] While there is not sufficient evidence to substantiate the exact nature of the relationship between TA829 and UNK_GreenSec, there is very likely a link between the groups."
Biterika linked to DDoS attacks: Qurium has linked a Russian web hosting and proxy provider named Biterika to DDoS attacks against two Russian independent media outlets. The attacks came after the two published a joint investigation on a sprawling network that sold sex with minors to Russian oligarchs. Some of the company's founders are linked to Russia's military and electronics research base.
Pakistani freelancers behind cracking websites: A group of Pakistani freelance web developers is behind a network of websites advertising cracked software. The cracks are laced with malware that infects users with infostealers. Security firm Intrinsec says the group has built hundreds of websites over the past four years, most likely for a third-party.
"Nameservers of the domain filescrack[.]com, registered by the same Pakistani individuals, were used since 2021 for more than 300 cracking websites. Additionally, the hosting provider 24xservice, may be used by this network of freelancers to register domains of cracking websites. In fact, the range 216.143[.]0/24 hosted by AS57717 (24xhosting) is almost full of cracking websites."

Malware technical reports
Supper backdoor: Security researcher Cedric Brisson has published an analysis of the Supper backdoor, also known as the Interlock RAT, a malware strain linked to the Vice Society data extortion group.
StealC v2: Per a new S2W report, v2 of the StealC infostealer was released back in March and is prolly out in the wild already.
Devman ransomware: ANY.RUN has published an analysis of Devman, a new RaaS that launched in May.
Sponsor section
Sandfly Security can help you find Linux packet-sniffing malware instantly and at scale. You can get a free trial and know immediately if any suspicious processes are sniffing traffic today.

APTs, cyber-espionage, and info-ops
Houken (UNC5174): A suspected Chinese hacking group is behind three Ivanti zero-days exploited in the wild last September. France's cybersecurity agency believes the Houken group works as an initial broker for a larger APT group. The agency linked the group with UNC5174, which Google also described as a cyber contractor for China's Ministry of State Security.
Jasper Sleet TTPs: Microsoft has published a report with new tactics used by North Korean remote IT workers to obtain jobs at Western companies. Microsoft tracks North Korean IT remote worker activity as Jasper Sleet (formerly known as Storm-0287).
Kimsuky adopts ClickFix: Genians researchers look at how the Kimsuky APT group is using ClickFix tactics in recent operations to deliver the BabyShark malware. Unlike most cybercrime activity, which uses ClickFix inside web pages, Kimsuky integrates the "repair instructions" inside office-related documents.
Vulnerabilities, security research, and bug bounty
C4 Attack: CyberArk published details on an attack that can decrypt cookies encrypted with Chromium's new AppBound Encryption algorithm, which the browser uses to secure cookies from theft.
Akamai CloudTest XXE: XBOW has published a technical analysis of an XXE vulnerability it found in the Akamai CloudTest load-testing tool.
AEM persistent XSS: Searchlight Cyber has found a persistent XSS vulnerability in the Adobe Experience Manager CMS.
Wing FTP server RCE: RCE Security has found major vulnerabilities in the Wing FTP server. Attackers can bypass authentication on the server's web interface just by appending a NULL byte to the username, followed by any random string. This initial issue can be used to gain root access on the FTP server and run malicious code. Wing only patched two of the three reported issues.
IDEs have verification issues: An Ox Security investigation has found vulnerabilities in IDEs that can allow malicious extensions to appear as trusted/verified. The issues affect Visual Studio Code, Visual Studio, and IntelliJ IDEA.
Chrome zero-day: Google has released a security update to patch an actively exploited Chrome zero-day. Tracked as CVE-2025-6554, the vulnerability is a type confusion issue in the browser's V8 JavaScript engine. It was discovered by Google's own security team and is the fourth Chrome zero-day patched this year.
Infosec industry
Acquisition news: MSS provider LevelBlue has acquired MDR provider Trustwave from The Chertoff Group. LevelBlue was previously known as AT&T Cybersecurity.
Threat/trend reports: CertiK, Dr.Web, Jamf, and SquareX have recently published reports and summaries covering various infosec trends and industry threats.
New tool—GitPhish: Security firm Praetorian has open-sourced GitPhish, a tool to automate device code phishing attacks against GitHub users.
New tool—Octelium: Octelium Labs has open-sourced Octelium, a self-hosted, unified platform for zero-trust resource access that is primarily meant to be a modern alternative to remote access VPNs and similar tools.
fwd:cloudsec 2025 streams: Live streams from the fwd:cloudsec 2025 security conference, which took place this week, are available on YouTube.
leHACK 2024 videos: Talks from the leHACK 2024 security conference, which took place last July, are available on YouTube.
Risky Business podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about how Microsoft has embraced digital sovereignty and is bending over backward to satisfy European tech supply chain concerns.
In this edition of Seriously Risky Business, Tom Uren and Patrick Gray talk about a new report that compares Chinese and American 0-day pipelines. The US is narrowly focused on acquiring exquisitely stealthy and reliable exploits, while China casts a far broader net. That was fine in the past, but as 0-days get harder and harder to find, the report argues that the US needs to change the way it goes about getting them.




