Risky Bulletin: US lifts sanctions on three Intellexa execs
In other news: MongoBleed vulnerabilities exploited in the wild; scammers steal a Belgian MP's salary; Coupang hands out $1.2 billion in coupons as hack compensation.

Breaches, hacks, and security incidents
Trust Wallet heist: A threat actor compromised the browser extension of Trust Wallet and stole almost $7 million worth of crypto from nearly 2,600 wallets. [SlowMist // Trust Wallet CEO thread]
Unleash Protocol crypto-heist: Hackers have stolen $3.9 million worth of crypto from the Unleash Protocol token platform after exploiting one of its smart contracts. [CoinDesk]
Flow crypto-heist: The Flow project has scraped a plan to roll back its blockchain after community backlash. The company was trying to recover $3.9 million stolen by hackers last week. [AMB Crypto]
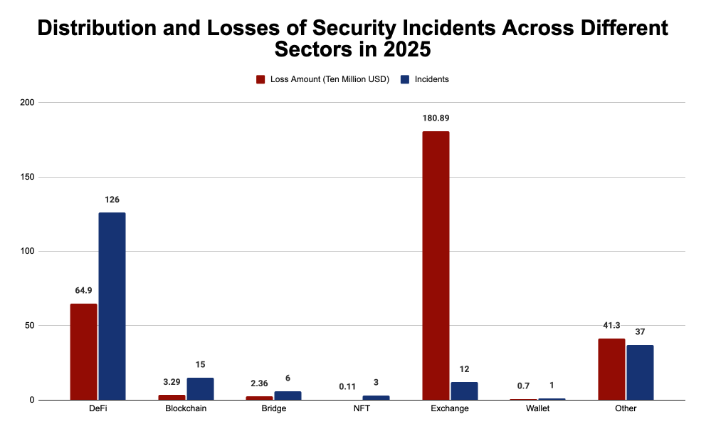
2025 crypto-hacks: Blockchain security firm SlowMist has recorded 200 security breaches last year impacting the crypto community, with losses at around $2.935 billion. [PDF]
R6S hacked: A threat actor hacked the backend servers of Ubisoft's Rainbow Six Siege FPS game and assigned billions in in-game currency to user accounts. Ubisoft confirmed the breach, took down servers, and rolled back the bans for users who received the currency and were automatically flagged and banned by the backend. The hack was linked to a MongoDB vulnerability known as MongoBleed, CVE-2025-14847, disclosed two days before Christmas and which very few companies had a chance to patch. [Dexerto]
Conde Nast gets hacked: A hacker breached news powerhouse Conde Nast and leaked the data of 2.3 million WIRED subscribers. The newest data points are from September 2024, the date of the presumed breach. Conde Nast has yet to confirm due to the winter holiday break. [DataBreaches.net]
ESA breach: Hackers breached the JIRA and Bitbucket servers of the European Space Agency (ESA). [BleepingComputer]
Goldman Sachs breach: Investment bank Goldman Sachs has notified customers that some of their data was stolen following a security breach at one of its law firms. [Bloomberg]
Chipotle breach: Chipotle has notified employees that their personal data was exposed following the October breach of enterprise platform Workday.
Korean Air breach: The data of almost 30,000 Korean Air employees was stolen this year as part of the Oracle EBS zero-day attacks. The data was taken from the company's Korean Air Catering & Duty-Free subsidiary. [Korea JoongAng Daily]
Apple supplier hit by hack: One of Apple's Chinese suppliers was hit by a cyberattack that impacted its factories and production lines. The supplier was not named and it's unclear if Apple-related information was compromised. [DigiTimes]
CET Oltenia ransomware attack: CET Oltenia, one of Romania's largest energy producers, was hit by The Gentlemen ransomware group on the second day of Christmas. [BleepingComputer]
Orange Poland DDoS attack: A massive 1.5 Tbps DDOS attack hit Orange's network in Poland on Christmas Eve.
Scammers steal MP's salary: Scammers have tricked the Belgian Chamber of Representatives and diverted an MP's salary. The victim was identified as Mathieu Michel, a former secretary of state for Digitisation, Administrative Simplification, Privacy Protection and Building Regulation, of all things. [SudInfo]
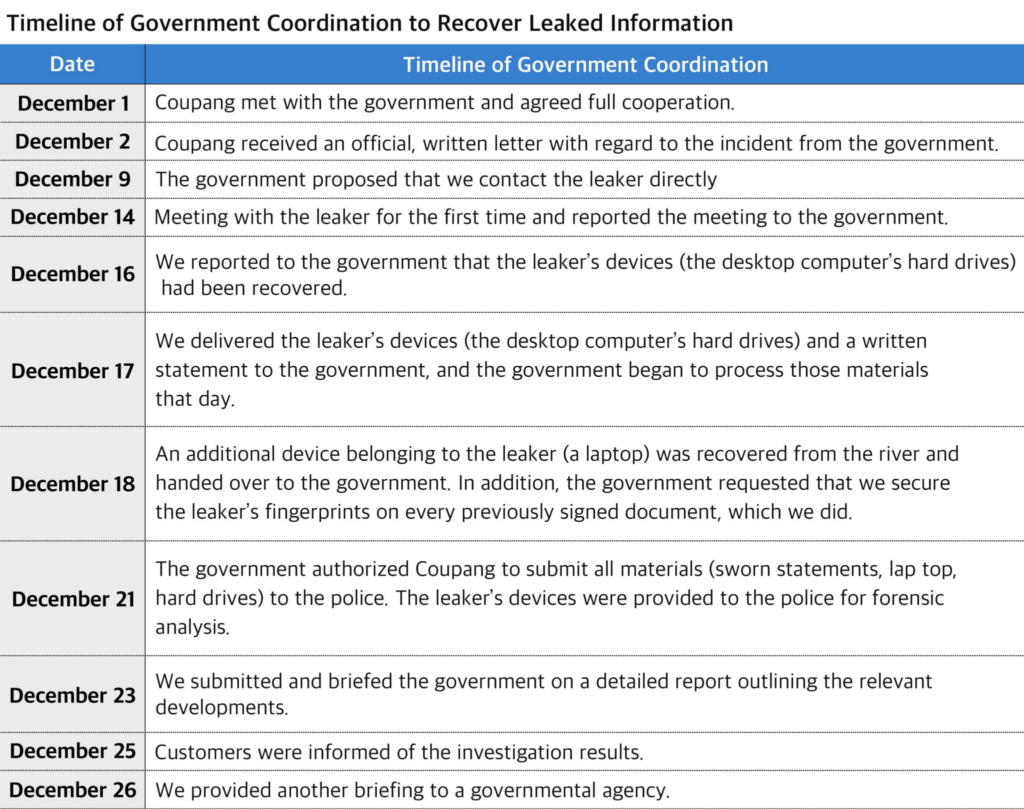
Coupang hands out coupons after hack: South Korean retail giant Coupang is handing out $1.2 billion worth of coupons to users affected by its recent security breach. According to the company's press release, they also managed to retrieve the hacker's laptop, which he allegedly threw into a river. [The Korea Herald]
General tech and privacy
New code-signing cert lifespan: The CA/B Forum has voted to reduce the lifespan of code-signing certificates from 39 months to 460 days starting with March 1.
Notepad++ removes self-signed cert: Text and code editor Notepad++ has removed a self-signed certificate from its code as part of upgrades to prevent future update hijacking incidents like the one it had last year.
ChatGPT to prioritize ads: In its quest for its first positive financial year, OpenAI has announced it will prioritize ads in ChatGPT responses. [Tom's Hardware]
Meta hides scam ads from regulators: New leaks of internal documents have revealed a Meta project that hid scammy-looking ads from regulators and researchers in an attempt to hide its scam problem and continue profiting from it. [Reuters]
https://bsky.app/profile/romanad.bsky.social/post/3mbce7lsxq223
Disney fined for privacy breaches: Disney will pay a $10 million fine to settle a DOJ lawsuit over breaches of the COPPA child privacy law.
PyPI 2FA adoption: The Python Software Foundation says 52% of active PyPI users are now using two-factor authentication to secure their account.
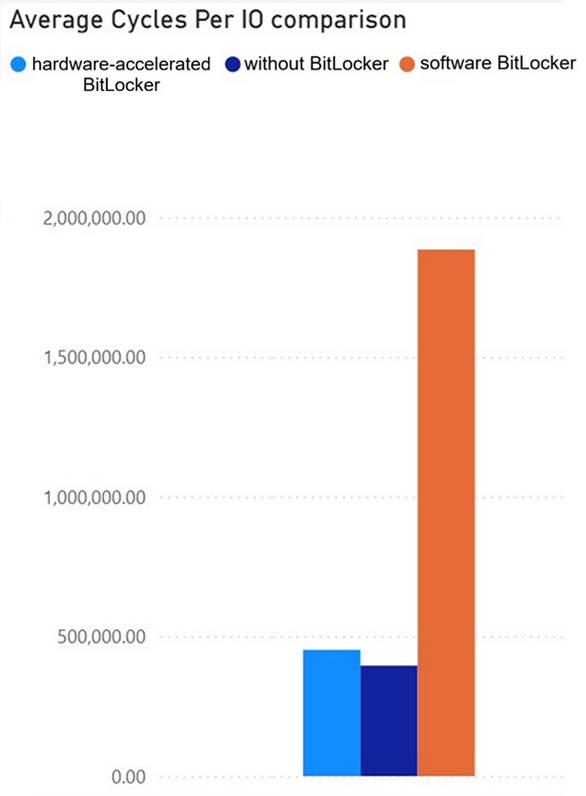
Hardware-accelerated BitLocker: Microsoft is adding a hardware-accelerated BitLocker version to Windows 11.
Government, politics, and policy
Russia updates fraud detection rules: The Russian Central Bank has updated the criteria for detecting banking fraud at the bank level. The number of rules has doubled from six to 12. The new rules have entered into effect this year.
Russia turns against the Probiv, too late: The Russian government is cracking down on illegal underground markets dedicated to the sale of private data, also known as probiv. Officials are turning against it after Ukrainian intelligence agencies have started using the data sold underground for its operations. [The Guardian]
Poland calls for EU TikTok inquiry: The Polish government has called on the EU to investigate TikTok after the company's role in a massive disinformation campaign active in the country. The campaign used AI-generated videos to call for Poland to leave the EU, criticize pro-EU leaders, and support far-right political figures. [Notes from Poland]
Spain Pegasus hacking scandal: French authorities believe the Moroccan intelligence used the Pegasus spyware in attempts to spy on Spanish PM Pedro Sanchez. The campaign targeting Spain allegedly contained similar markers to a campaign targeting France. [Antena3] [h/t Vas Panagiotopoulos]
NYC bans hacking devices for mayoral inauguration: New York City Hall has banned attendants of the Zohran Mamdani mayoral inauguration from carrying Raspberry Pi and Flipper Zero devices. [Adafruit]
US lifts sanctions on three Intellexa execs: The US has lifted sanctions on three executives at spyware maker Intellexa. US officials said the individuals distanced themselves from the company and are not subject to the sanctions, imposed in September 2024. [Reuters]
Today, the U.S. Treasury Department announced that it took three people closely affiliated with Intellexa, the company behind Predator spyware, off of a sanctions list. The public deserves to know what evidence exists to prove that these individuals have ceased their involvement with Intellexa. 1/
— Natalia Krapiva 🕊️👩🏻💻 (@natynettle.bsky.social) 2025-12-30T22:01:38.314Z
US hands visa to Russian propagandist: Lauren Chen, a right-wing influencer behind Tenet Media, has received a US visa after the US State Department blissfully forgot her involvement in a scheme to pay US right-wing influencers to push pro-Kremlin and anti-Ukraine disinformation and propaganda. The US handing her a new visa came days after the US imposed visa bans on disinformation researchers. [The Bulwark]
Stephen Miller found an immigrant he likes.
— emptywheel (@emptywheel.bsky.social) 2025-12-30T10:53:12.162Z
Banning people who study propaganda from the country, while bringing known propagandists back in. Merry Christmas, everybody!
— Greg Greene (he/him/his) (@greene.haus) 2025-12-26T02:03:43.615Z
Risky Business podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq talk to Hamid Kashfi, CEO and founder of DarkCell, about the Iranian cyber espionage scene.
Arrests, cybercrime, and threat intel
South Korea arrests crypto-thief: South Korean police have arrested a man suspected of having stolen 17 billion won ($11.7 million) worth of cryptocurrency assets. The man was identified as a 29-year-old Lithuanian. He was detained in Georgia and extradited to South Korea last week. He allegedly coded and distributed a clipboard hijacker, also known as a clipper, which intercepted and stole crypto. [The JoongAng]
US charges Coinbase account hacker: The US Justice Department has charged a New York man for social engineering Coinbase users by posing as a support representative and tricking them into transferring their funds to his wallets. He allegedly stole $16 million worth of crypto.
Coinbase tech support arrested in India: Coinbase CEO Brian Armstrong said Indian authorities have arrested a customer support representative from India that took a bribe and handed data to hackers, which then extorted the company for $20 million. [Crypto News]
Investment scammers arrested in Pakistan: Pakistani authorities have arrested eight Chinese nationals for running an illegal call center in Karachi that tricked locals into investing funds through their fake platforms. [Dawn]
Video from scene of raid. 3/3
— Cyber Scam Monitor (@cyberscammonitor.bsky.social) 2025-12-22T13:20:16.176Z
Internet-wide scans and attacks: A threat actor has launched a massive internet-wide scan and exploitation campaign that targeted 767 distinct CVEs across 47 technology stacks. [GreyNoise]
Silver Fox targets India now: The Silver Fox e-crime group is now targeting Indian users after spending the past two-three years targeting Chinese speakers exclusively.
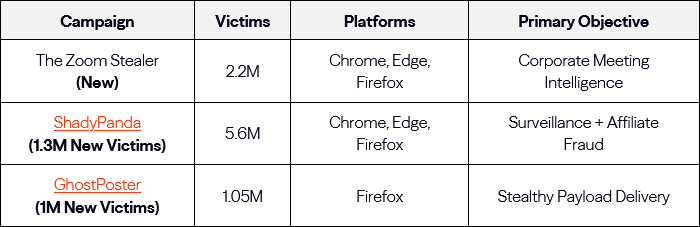
DarkSpectre spreads malicious Chrome extensions: Koi Security has uncovered a China-based threat actor named DarkSpectre. The group has infected over 8.8 million users across three different campaigns that deployed malicious browser extensions.
Malware technical reports
Shai-Hulud 3.0: A new version of the Shai-Hulud worm was seen by Snyk spreading on the npm ecosystem.
GlassWorm returns: Koi Security has spotted a new version of GlassWorm spreading through VSCode extensions, this time targeting macOS environments.
Keenadu pre-installed malware: Kaspersky has found Keenadu, a new backdoor trojan pre-installed on some Android tablets. To technical report out yet, just a tweet.
RondoDox adopts React2Shell: The RondoDox IoT botnet has adopted the React2Shell vulnerability for its offensive operations. [CloudSEK]
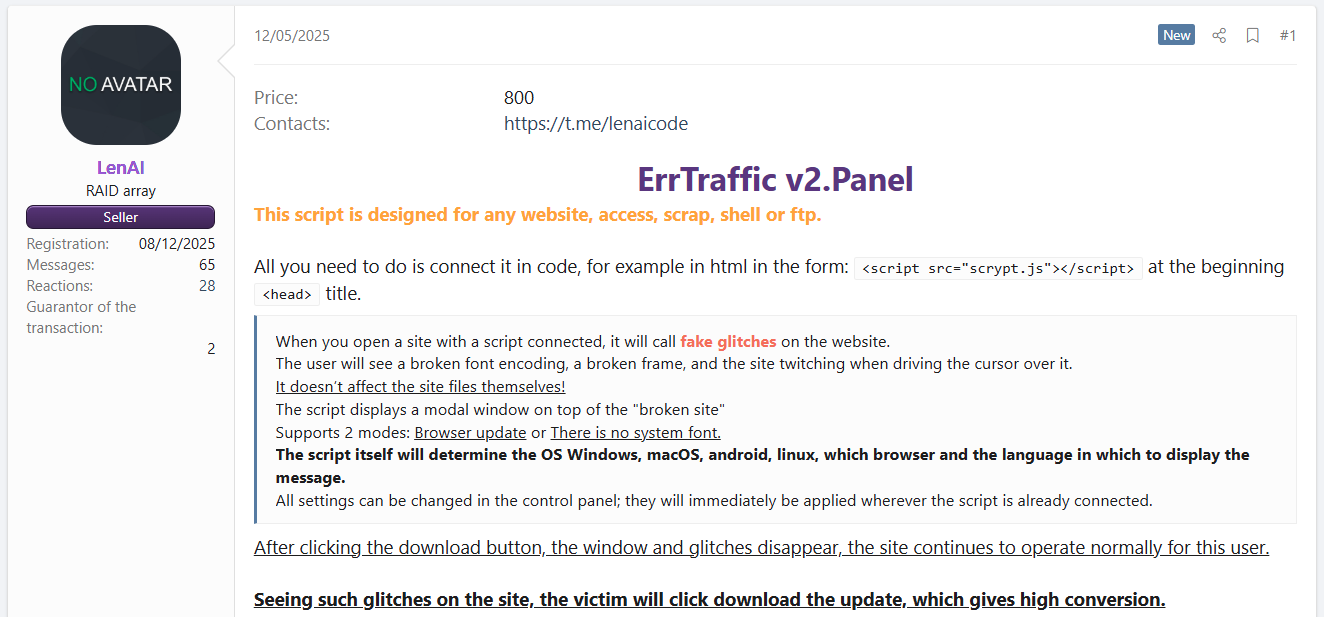
ErrTraffic: Hudson Rock looks at ErrTraffic, a new cybercrime tool to automate the deployment of ClickFix social engineering lures and pages. The tool is currently being advertised on Russian-speaking hacking forums.
Risky Business podcasts
In this edition of Seriously Risky Business, Tom Uren and Patrick Gray talk about America's increasing dependence on Chinese manufacturers for electrical sector equipment. This doesn't seem like a good idea when China is hacking electric utilities for sabotage and PLA researchers are dreaming up ways to attack the grid.
APTs, cyber-espionage, and info-ops
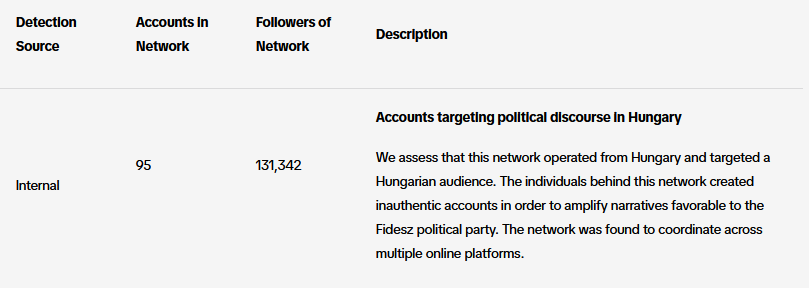
TikTok info-ops summary: TikTok has published its monthly report on covert influence operations the company has spotted on its platform in November this year. The company took down influence networks targeting political discourse in Hungary, Taiwan, Indonesia, Chile, and Palestine. The largest cluster was in Hungary in support of Viktor Orban's party.
APT36 campaigns: CyFirma looks at recent campaigns from suspected Pakistani APT group Transparent Tribe (APT36) that targeted Indian government agencies.
UAC-0184 (Hive0156): Qihoo360 looks at a phishing campaign targeting Ukraine's Parliament, the Rada. The campaign has been linked to a suspected Russian APT known as UAC-0184.
UNG0801: Seqrite has spotted a new cyber-espionage cluster, UNG0801, targeting organizations in Israel. The company says the activity originates from "Western Asia."
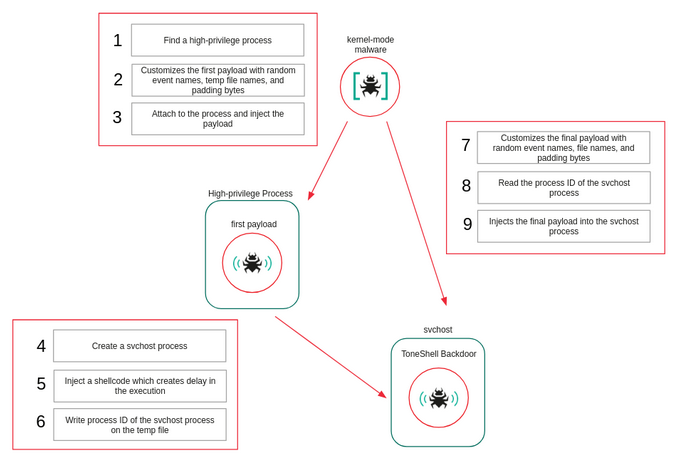
HoneyMyte APT: A suspected Chinese APT group named HoneyMyte (Mustang Panda) has deployed kernel-mode loaders to deploy its payloads in attacks against SE Asian government organizations throughout 2025. This included the ToneShell backdoor, PlugX, and the ToneDisk USB worm.
Vulnerabilities, security research, and bug bounty
Important security updates: Bitrix, IBM, LangChain, Notepad++, SmarterTools.
MongoBleed exploitation: After a patch was released before Christmas, attacks targeting the MongoBleed vulnerability (CVE-2025-14847) began on December 26, after a public PoC was published online. [ACSC // CISA // Wiz]
BLE vulnerability in Airoha chips: ERNW has published a technical write-up on three vulnerabilities impacting Bluetooth headphones using Airoha chips. The bugs impact headphones from Sony, Marshall, JBL, and Beyerdynamic, and were patched back in June.
GPG vulnerabilities: A security researcher has disclosed 14 vulnerabilities in GnuGPG, minisign, and other GPG-based tools. Some of the vulnerabilities can lead to remote code execution or encryption downgrades.
LangGrinch vulnerability: Amla Labs has discovered a serialization vulnerability in the LangChain AI platform that could have allowed the theft of API secrets.
Petlibro vulnerabilities: A security researcher known as BobDaHacker has found six vulnerabilities in Petlibro, a popular smart pet feeder app. One of the bugs include an auth bypass that could let anyone access user accounts. Other bugs could tamper with pet-feeding schedulers and even leak user data and pet recordings.
WebKit zero-day incoming: Security researcher Joseph Goydish claims he found a new zero-day in Apple's WebKit web engine. Goydish reported the finding publicly after previously accusing the company of privately patching his bugs without credit.
TCC bypass write-up: Security researcher Mickey Jin has published a write-up on CVE-2025-43530, a TCC bypass that can be exploited via a private macOS VoiceOver API. This was patched in December.
Xspeeder vulnerability: PwnAI has published details and a PoC for an unauth root RCE in the firmware of Xspeeder, a Chinese company that makes SD-WAN routers. It's unclear if this was patched.
HP Aruba VIA VPN client EoP: Security researcher JC has published a write-up on a privilege escalation in the HP Aruba VIA VPN client for Linux. It's unclear if this was patched.
Infosec industry
Threat/trend reports: ANY.RUN, IDC, Positive Technologies, and SlowMist have recently published reports and summaries covering various threats and infosec industry trends.
New tool—certgrep: Security researchers Juxhin Dyrmishi Brigjaj and Ian Muscat have released certgrep, a free Certificate Transparency search tool.
New tool—ProfileHound: Security researcher M4lwhere has open-sourced ProfileHound, a tool to find and achieve red-teaming objectives by locating domain user profiles on machines.
New tool—DumpChromeSecrets: The MalDev Academy has released DumpChromeSecrets, a tool to extract data from modern Chrome versions, including refresh tokens, cookies, saved credentials, autofill data, browsing history, and bookmarks.
New tool—MalwareTracesGenerator: Security researcher Frack113 has released MalwareTracesGenerator, a tool to generate malware traces for detection tests.
PQC Conference videos: Talks from the PKI Consortium's PQC 2025 security conference, which took place in October in Kuala Lumpur, are available on YouTube.
39C3 videos: Talks from the 39th Chaos Computer Club security conference, which took place last week, are available on the conference's website.
Risky Business Podcasts
The main Risky Business podcast is now on YouTube with video versions of our recent episodes. Below is our latest weekly show with Pat and Adam at the helm!




