Risky Bulletin: US indicts two rogue cybersecurity employees for ransomware attacks
In other news: Hackers extort massage parlor visitors; Balancer hacked for $128 million; cargo thieves use hackers to go after trucking and freight companies.

This newsletter is brought to you by Sublime Security, whose agentic platform stops more email attacks with less work. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
The US Department of Justice has charged employees at two cybersecurity firms with hacking US companies and deploying ransomware.
According to court documents, charges have been levied against Kevin Tyler Martin, a former ransomware negotiator at DigitalMint, and Ryan Clifford Goldberg, a former incident response manager at cybersecurity company Sygnia.
The two worked with a third suspect to hack into US companies, steal their data, encrypt computers, and then ask for huge ransoms in the realm of millions of US dollars.
Victims mentioned in the indictment include a medical device company in Tampa, a pharmaceutical company in Maryland, a drone manufacturer based in Virginia, and an engineering company and a doctor's office from California.
At least in one incident—the medical device company—the group requested a $10 million reward and made off with a final payment of $1.27 million.
To encrypt victim networks, the trio leveraged the AlphV (BlackCat) ransomware, which, at the time, was the top ransomware an individual could rent from underground cybercrime communities.
The group's double life appears to have come to an abrupt end after the US and European partners seized AlphV servers in December 2023. While not specifically mentioned in court documents, it is very likely that data seized by authorities helped identify the three.
US authorities claim the scheme continued until April 2025, but the indictment doesn't mention any new victims after 2023.
News of this scheme first broke in July, when Bloomberg reported that the FBI was investigating the role of a DigitalMint employee in ransomware attacks. The initial report claimed that the employee had secret deals with ransomware groups to take a cut of the ransom if they convinced victims to pay faster. This turned out to be much worse than it initially reported.
According to the Chicago Sun Times, which first broke the story on Monday, the two rogue employees were recruited by the third, unnamed co-conspirator, an individual from Land O'Lakes, north of Tampa, Florida.
All three have been interviewed by authorities between April and June and were released after initial questioning.
Only Martin and Goldberg were charged. Both were detained. Goldberg is still in custody, while Martin was released on $400,000 bond.
The third suspect was not charged. There are two scenarios here. He may be charged in a separate, more sprawling indictment, or he may have entered a plea deal after, possibly, cooperating with authorities.
DigitalMint president Marc Grens told TechCrunch on Monday that the third suspect may also be another former DigitalMint employee.
Risky Business Podcasts
The main Risky Business podcast is now on YouTube with video versions of our recent episodes. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
UPenn hack gets feisty: The University of Pennsylvania has been hacked and is being extorted by hackers. The intruders hacked a Penn employee account and pivoted to internal systems. The group stole and is now threatening to release more than 1.2 million donor records. To pressure the university to pay, hackers also mass-mailed students and staff about the hack last week. [Additional coverage in BleepingComputer]
SuperGrosz breach: Hackers have stolen extremely sensitive information from Polish online loan platform SuperGrosz. Government officials have called the incident "very serious." They have urged affected citizens to freeze their national PESEL ID number in the government's official app. The stolen data includes extremely sensitive personal and financial information that could be used for fraud. [Additional coverage in the OCCRP]
SK Telecom damages: A South Korean government mediation panel has advised the country's largest telco to pay 300,000 won ($208) in damages to each customer over a recent security breach. Almost 4,000 customers have filed complaints over SK Telecom's breach. More than 23 million customers have had their personal and USIM data stolen in a hack disclosed in April. The company told investors this week that the incident led to a 90% drop in operating profit for the third quarter. [Additional coverage in the Korea Times]
Balancer hacked for $128m: Hackers have stolen $128 million worth of crypto assets from the Balancer DeFi platform. The attackers gained control over Balancer's access control system and were able to modify balances on the platform. Funds were later laundered through Tornado Cash. [Additional coverage in PYMNTS]
Hack exposes Kansas City dirty cops: A hack of the Kansas City Police Department has exposed the department's list of cops with disciplinary investigations. The files were leaked online last year by the BlackSuit ransomware after the PD refused to pay a ransom. The leaked documents show that officers with known records of misconduct, accused of crime, were not only kept on the force, but also promoted. [Additional coverage in KCUR and WIRED]
These are among 62 current and former officers the department itself decided couldn’t be trusted…cops so compromised that the department believes their involvement in cases could jeopardize prosecutions. Some stayed on the job for years. Some were promoted
— Dhruv Mehrotra (@dmehro.bsky.social) 2025-11-03T12:34:10.623Z
General tech and privacy
Data brokers threaten EU privacy: A joint investigation between five news outlets looks at how easy it is to purchase data on any EU citizen from data brokers and track their movements, including EU government officials. [Additional coverage in Netzpolitik]
WhatsApp for Apple Watch: Meta has launched a WhatsApp app for the Apple Watch.
Twitter to show more user info: Twitter plans to show additional information about user profiles. Information like account creation date, country of origin, and the number of name changes will soon be visible on all profiles. A similar feature already exists for Facebook and Instagram. Twitter head of product Nikita Bier says the change is designed to reduce inauthentic engagements.
Government, politics, and policy
US to face-scan all foreign travelers: The US Department of Homeland Security will photograph all foreign nationals entering the US. The new rule will take effect on December 26 and will apply to all foreign nationals, including green card holders. The DHS plans to use the data to track foreigners who overstay their visas. [Additional coverage in Fox News]
CyberCorps deferment: The Office of Personnel Management will defer the enforcement of the CyberCorps scholarship and give students additional time to find government jobs. The CyberCorps program provides free cybersecurity training for students, as long as they get jobs in the US government. Several participants warned last week that due to layoffs and freezes in government hiring, they now risk being saddled with six-figure loans. [Additional coverage in CyberScoop]
Australia expands kids social media ban to Reddit and Kick: Australia's eSafety Commission has expanded the country's kids social media ban to Reddit and video streaming service Kick. The companies must block Australian users under the age of 16 from their platform starting on December 10. Australia's kids social media ban will be enforced on nine platforms. The other seven are Facebook, Instagram, Snapchat, Threads, TikTok, X, and YouTube.
Sponsor section
In this Risky Business sponsor interview, Casey Ellis chats with Sublime Security CEO and founder, Josh Kamdjou, about how Sublime is seeing a massive surge in ICS or calendar invite phishing and how the email security platform can help.
Arrests, cybercrime, and threat intel
MrICQ arrested: A developer of the old Jabber Zeus banking trojan has finally been caught. Yuriy Igorevich Rybtsov was arrested in Italy and handed over to US authorities. The 41-year-old Ukrainian national was known online as MrICQ. He is the second Jabber Zeus member to be detained after the group's leader, who is already serving an 18-year prison sentence in the US. [Additional coverage in KrebsOnSecurity]
US sanctions DPRK money launderers: The US Treasury has sanctioned eight individuals and two entities for laundering money for various North Korea schemes, including crypto-heists and ransomware attacks.
Scammers arrested in Europe: EU authorities have arrested nine suspects who stole more than €600 million via online scams. Suspects were detained in Cyprus, Spain, and Germany. The group used social media ads, cold calling, and fake celebrity testimonials to lure victims to fake investment portals and steal their money.
SMS blaster detained in Cambodia: Cambodian authorities have arrested two suspects for driving with SMS blasters around the city of Sihanoukville. The two were arrested at a police roadblock over the weekend. According to CommsRisk, other individuals driving with SMS blasters in their cars were also arrested last week in Switzerland and the Philippines.
Massage parlor hackers arrested: South Korean authorities have arrested a criminal group that hacked massage parlors and extorted male customers. The group collected customer records by tricking massage parlor owners into installing malicious apps on their phones. Group members collected data from each device and then contacted customers to ask for money, threatening to release videos of their massage sessions. According to authorities, the group made almost $1.2 million from 62 customers over the past three years. [Additional coverage in the Chosun Daily]
India arrests CCTV hackers: Indian authorities have arrested multiple individuals for hacking CCTV networks and selling recorded footage on online fetish communities. The group allegedly hacked security cameras at hospitals, schools, malls, and private homes. The hacks exploited cameras that used factory or weak passwords. Recorded footage was sold for $8 to $45 per clip on dedicated Telegram channels. The footage was later uploaded to online fetish porn sites. [Additional coverage in the Economic Times]
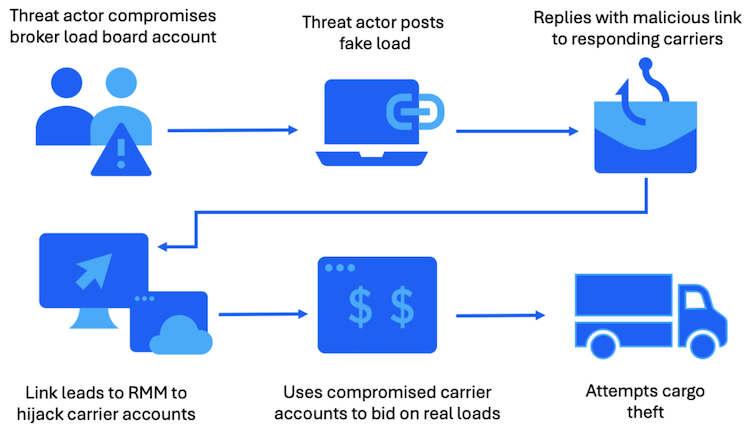
Thieves use hackers to go after trucking companies: Organized crime groups are working with hackers to infiltrate trucking and land freight companies. The scheme involves hacking truck companies, deploying remote access tools, and then placing bids on freight haul contracts. The goal is to win the contract, intercept the shipment, and then resell the goods online. According to Proofpoint, the campaign has been taking place for over a year.
LabHost user sentenced to jail: A 37-year-old Dutch national, who was a user of the LabHost phishing platform, was sentenced to 300 days in jail and three years of probation.
EditaPaper spam: Open Measures looks at a VK spam campaign promoting EditaPapers, an essay-writing service that likely uses generative AI. The campaign has posted a whopping 200,000 times since June by abusing the VK API.
Aura interview: Threat intelligence analyst g0njxa has published an interview with the developer of the Aura infostealer.
"Our software does not work in CIS countries. Many people have asked us to remove this restriction and offered us large sums of money, but we have refused every request. AURA does not work and will never work in CIS countries. Our builds include checks for CIS systems (which have already been attempted to be bypassed, but unsuccessfully) as well as IP address checks on our servers for additional protection."
Scattered LAPSUS$ Hunters: Trustwave has published a profile on cybercrime group Scattered LAPSUS$ Hunters, its members, and its new Extortion-as-a-Service (EaaS) platform.
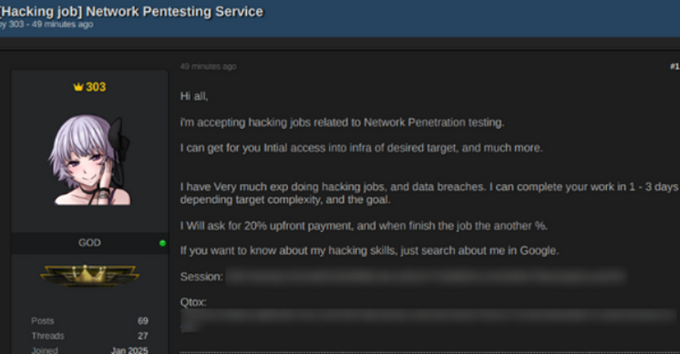
303 profile: KELA has published a profile on a hacker who goes online under multiple names, but is referenced in this report as 303, their username on the old BreachForums. KELA believes the suspect, a prolific leaker, is a Spanish-speaking user based in Uruguay.
Malware technical reports
SesameOp: A recently discovered backdoor uses the OpenAI Assistants API for its command and control channel. The SesameOp malware was discovered in July by Microsoft's security teams in a cyber-espionage-related intrusion. SesameOp is deployed in compromised environments and then fetches commands from the OpenAI API to run. IT also uses the API to store and relay data back to its operators. Microsoft has not yet attributed the malware to any group.
"The stealthy nature of SesameOp is consistent with the objective of the attack, which was determined to be long term-persistence for espionage-type purposes."
XLoader: Check Point has reverse-engineered the latest version of the XLoader malware, v8.0.
NGate NFC relay malware: Poland's CERT has published a report on Android malware used in recent NFC relay attacks. This is the malware that infects smartphones and then relays a user's credit card NFC fingerprint to an attacker. Poland's CERT called the malware NGate, after a similar strain spotted in Czechia and Russia last year.
Tycoon 2FA: Cybereason looks at the operations of Tycoon 2FA, a phishing-as-a-service that primarily targets Microsoft 365 and Gmail accounts.
Clop ransomware: Threat intel analyst Rakesh Krishnan has published a report on the ASNs used by the Clop gang in their recent operations.
DragonForce ransomware: The Acronis security team has published a comprehensive report on the evolution of the DragonForce ransomware group—from a Conti-derived RaaS to alliances with The Com members.
Sponsor section
In this sponsored product demo, Sublime Security co-founder and CEO Josh Kamdjou joins Risky Business podcast host Patrick Gray to show off the company's email security platform, including its latest agentic AI bells and whistles.
APTs, cyber-espionage, and info-ops
Dutch bakery front: It appears that Iranian APT group Charming Kittens repeatedly used the address of a real Dutch bakery in buying and registering servers and domains.
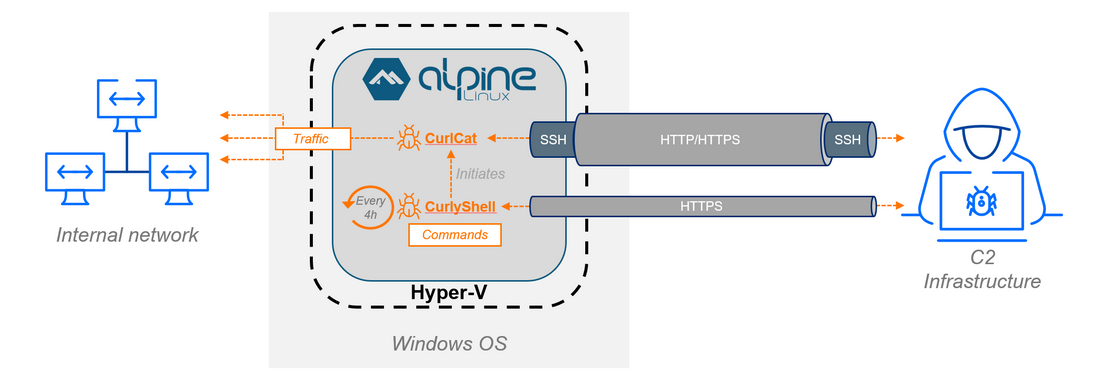
Curly COMrades: Bitdefender has spotted the Curly COMrades APT using Microsoft Hyper-V virtual machines to run malicious code on infected hosts inside a stripped-down version of Alpine Linux, and essentially avoid EDRs and other security software on the underlying OS.
Vulnerabilities, security research, and bug bounty
Windows EoP write-up: Security firm Out of Bounds has published a write-up on CVE-2025-50168, a Windows EoP bug they used at Pwn2Own Berlin this year.
KEV update: CISA has updated its KEV database with five vulnerabilities that are currently exploited in the wild. This includes a CWP web panel command injection and a recent Gladinet zero-day.
AMD patches RDSEED failures: Chipmaker AMD has confirmed a major security bug in the RDSEED entropy generator impacting Zen 5 processors. The RDSEED process has been failing to produce random numbers on Linux systems. AMD is planning to release patches through November for all affected CPU models. The Linux kernel team disabled support for RDSEED on Zen5 chips last month, after initial reports.
Post SMTP vulnerability: More than 400,000 WordPress sites are vulnerable to a security flaw in the Post SMTP plugin. The vulnerability allows remote, unauthenticated attackers to read a WordPress site's email logs. Attackers can reset passwords for admin accounts and extract the password reset link from the plugin logs to take over sites. Tracked as CVE-2025-11833, the bug has a severity rating of 9.8/10.
React Native CLI RCE: JFrog researchers have discovered a remote unauth command injection bug (CVE-2025-11953) that can lead to RCE attacks on React Native apps that have a CLI component.
Microsoft patches Teams bugs: Microsoft has patched four vulnerabilities in its Teams messaging platform that could have allowed malicious users to impersonate other users, alter messages and notifications, and forge identities in audio and video calls. Security firm Check Point says the bugs could have been abused in cybercrime and fraud operations to impersonate executives or tech support personnel. The bugs were reported to Microsoft in March and received final patches at the end of last month.
Android Security Bulletin: Google has released the Android security updates for November 2025. The update fixes two security flaws.
Apple security updates: Apple has released a bunch of security updates this month. No zero-days.
KASLR not working on Android: According to new research from Project Zero, the Kernel Address Space Layout Randomization (KASLR) security feature on Android has been broken for quite some time now.
We really should be talking about this more....KASLR is just not working properly on Android right now, and it hasn't for a long time.https://t.co/AE0vBXEcob
— Seth Jenkins (@__sethJenkins) November 3, 2025
Infosec industry
Threat/trend reports: Abnormal AI, CrowdStrike, IANS, Proofpoint, ReliaQuest, and RH-ISAC have recently published reports and summaries covering various threats and infosec industry trends.
CrowdStrike 2025 European Threat Landscape Report is out. You'll notice all of the initial access methods don't involve AI, and generative AI or GenAI isn't mentioned once. Which is interesting... considering it contradicts their own narrative a few weeks ago.
— Kevin Beaumont (@doublepulsar.com) 2025-11-03T10:34:33.057Z
Acquisition news #1: Bug bounty platform Bugcrowd has acquired Mayhem Security, a specialist in offensive AI security.
Acquisition news #2: Cybersecurity giant Zscaler has acquired SPLX, a provider of AI security solutions.
Acquisition news #3: Managed cybersecurity provider RKON has acquired ScaleSec, a provider of cloud security services.
New tool—SlopGuard: Cybersecurity engineer Aditya Tiwari has released SlopGuard, a tool to detect AI-hallucinated package dependencies and supply chain attacks.
New tool—Linux/Wasm: Software engineer Joel Severin has open-sourced Linux/Wasm, a WebAssembly port of the Linux kernel that can run inside a web browser.
New tool—SilentButDeadly: A red teamer named LooseHose has released SilentButDeadly, a tool to block network connections for EDR/AV software by preventing their cloud connectivity using the Windows Filtering Platform (WFP).
USENIX Security videos: Talks from the USENIX Security 2025 security conference, which took place in August, are now available on YouTube.
Risky Business podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq discuss the futility of using aggressive cyber operations to send messages between states.
In this edition of Seriously Risky Business, Tom Uren and Amberleigh Jack talk about Peter Williams, the general manager of vulnerability research firm Trenchant, who has pleaded guilty to selling exploits to the Russian zero-day broker Operation Zero. It's a terrible look, but it doesn't mean the private sector can't be trusted to develop exploits.




