Risky Bulletin: US indicts i-Soon and APT27 hackers
In other news: BADBOX botnet disrupted after return; authorities seize Garantex crypto exchange; Taylor Swift concert ticket hackers arrested.

This newsletter is brought to you by cloud security firm Prowler. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
The US Department of Justice has unsealed charges against twelve Chinese nationals linked to two cyber-espionage groups.
The DOJ DC office indicted Yin Kecheng and Zhou Shuai, two members of the APT27 group, also known as Emissary Panda, Lucky Mouse, and Silk Typhoon.
Officials say the two worked as contractors and conducted hacking operations on behalf of China's Ministry of Public Security (MPS) and Ministry of State Security (MSS) since at least 2011.
Zhou allegedly contracted his work via a front company named Shanghai Heiying Information Technology.
US officials appear to have been aware of Yin since at least 2017. He was initially charged that year in a sealed indictment [PDF] and charged again in a superseding indictment [PDF] in 2023.
The DOJ says the two conducted intelligence collection for their government, which is not technically a crime, but they also hacked dissidents overseas and hacked for their personal profit by stealing and selling data on underground markets.
"For example, on one occasion in September 2013, YIN told an associate he wanted to 'mess with the American military' and 'break into a big target' so that he could earn enough money to buy a car."
Yin's biggest hack was the breach at the US Treasury Department last year when he gained access to the agency's network by compromising one of its identity management providers, BeyondTrust.
The US Treasury sanctioned Yin in January and imposed additional sanctions on Wednesday on Zhou and his front company. The State Department is also offering a $2 million reward for information on each of the two.

At the same time, the DOJ New York office also unsealed charges against ten suspects linked to Chinese security company i-Soon—real name Anxun Information Technology. Eight are employees, including the company's CEO Wu Haibo, while the other two are MPS officers who were directing the group's hacks.
i-Soon became a widely known name in the cybersecurity field after an unknown individual leaked a massive trove of internal documents on GitHub in February of last year.
The leak exposed how Chinese authorities began contracting out its hacking operations to smaller companies like i-Soon as a way to hide official operations and plausibly deny intrusions at diplomatic levels.
The DOJ says i-Soon generated tens of millions of dollars in revenue from contracting work between 2016 through 2023.
The company created hacking tools for itself and other contractors and conducted offensive operations, both internally and externally.
i-Soon performed internal surveillance of minorities and dissidents, was involved in influence operations, and conducted cyber-espionage intelligence collection. Just like APT27, its employees also used the company's infrastructure to conduct personal for-profit hacks.
As the massive revenue suggests, the company was quite prolific, but the US DOJ says it was also quite efficient and involved in some massive hacks. Known victims include a list of who's who:
- The Foreign Ministry of Taiwan.
- The Foreign Ministry of India.
- The Foreign Ministry of South Korea.
- The Foreign Ministry of Indonesia.
- The US Defense Intelligence Agency, an agency within the Department of Defense that specializes in defense and military intelligence.
- The US Department of Commerce and the International Trade Administration, an agency within the Department of Commerce that promotes US exports and defends against unfair trade practices.
- The New York State Assembly, a part of the legislature of the state of New York.
- A newspaper based in New York that publishes news related to China and is opposed to the Chinese Communist Party.
- An additional newspaper based in New York, New York.
- A religious organization based in the US that has thousands of churches and congregations and millions of members.
- A Texas-based organization founded by a prominent critic of the PRC government focused on promoting human rights and religious freedom in China.
- A news service funded by the US government that delivers uncensored domestic news to audiences in Asian countries, including China, and is headquartered in Washington, D.C.
- A state research university in the US
- A religious leader who lived outside of China and the US.
- A newspaper based in Hong Kong that has actively covered the politics of Hong Kong and continues to do so today.
Some of these hacks are tracked as campaigns from APTs named Aquatic Panda, RedHotel, or Charcoal Typhoon.
The US State Department is also offering a reward of up to $10 million for additional information on i-Soon and its government handlers.
According to a new report from Natto Thoughts, i-Soon is technically dead and buried as a cyber contractor following last year's leak.
"When i-SOON suffered a seemingly unexpected leak that exposed details of China's cyber operations, this seems to have hurt the company's business significantly. Furthermore, i-SOON as a company has disappeared from the Chinese media after the leak. We believe this is an intentional move by the Chinese government to limit the attention to i-SOON and the state's cyber operations. Although still in operation, i-SOON companies likely have had even more trouble securing contracts and making profits than before. This is likely because, amidst fierce competition among Chinese information security companies, the leak has damaged i-SOON's reputation."

Risky Business Podcasts
In this Risky Business Talks interview, we invited Will Thomas to talk about the recent leak of internal chats from the Black Basta ransomware group. Will is the co-founder of CTI community research project Curated Intelligence and author and instructor at the SANS Institute. Will walks us through the Black Basta leak and uses the group's attack on US healthcare provider Ascension to break down how the gang operated.
Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
NTT breach: Hackers breached the internal network of Japanese telecommunications company NTT in February this year. The company says hackers stole data on almost 18,000 of its corporate customers. NTT is one of the world's largest companies and is ranked 120th on the Fortune 500 list. This is the company's second major breach after a 2020 incident.
Csyndication supply chain attack: Threat actors have installed backdoors on over 1,000 websites using malicious code delivered via a third-party JavaScript CDN. The code was delivered via a platform named Csyndication[.]com. Security firm C/side says the attackers deployed four different backdoors on each website to ensure they maintained access. Most of the compromised websites are running on WordPress.
FSB says it stopped GUR attacks on youth military: Russia's FSB intelligence agency says it stopped a cyberattack conducted by Ukraine's military intelligence agency GUR designed to steal the personal data of youth military personnel. The alleged attack targeted two Moscow-based organizations that trained young children to promote patriotic and military lifestyles. The FSB says the Ukrainians wanted to collect personal data and recruit some of the young men. [Additional coverage in The Moscow Times]
General tech and privacy
Apple appeals UK data request: Apple's legal team has appealed the UK government's request to access encrypted user data. [Additional coverage in the BBC]
Discord IPO coming: There are reports that Discord is preparing to go public later this year. Fun, fun, fun! [Additional coverage in Kotaku]
Chrome 134: Google has released version 134 of its Chrome browser. See here for security patches and webdev-related changes. The biggest changes in this release include new LLMs to detect and stop scams and notification spam, a new system that automatically blocks unpacked Chrome extensions from running if Developer Mode is not enabled first, and the first dev tests of the new Device Bound Session Credentials system.
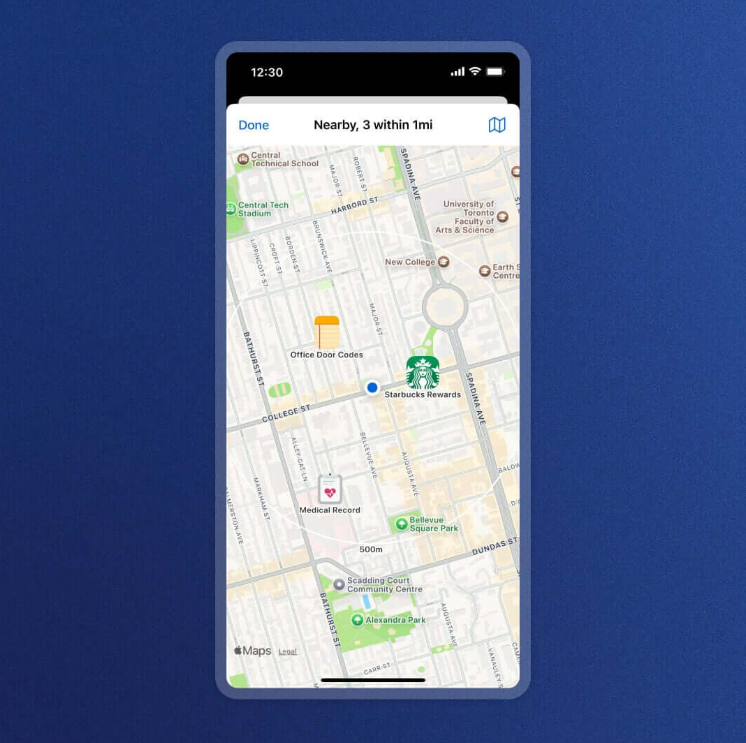
1Password adds support for geo-passwords: Password manager application 1Password has added support for location-based passcodes. The feature will prompt users with passwords and passcodes based on the user's current geolocation. For example, the feature will let users know a door's entry code when they get close to their workplace or WiFi passwords for nearby networks.
Government, politics, and policy
Ukraine honors civilian hackers: Ukraine's military intelligence has honored a group of civilian hackers and security professionals who helped defend the country's national security.
Former NSA officials warn of cyber staff cuts: Speaking at a hearing of the US House Committee on China, former NSA official Rob Joyce has warned lawmakers that the ongoing government layoffs of government cyber staff will have a devastating effect on national security. Kind of a "no s**t, Sherlock" statement, but I'm glad there's still someone speaking some sense to this new US government that seems to have turned belly up to both Trump and Musk's billionaire friends gang. [Additional coverage in TechCrunch]
US to vet prospective citizens' social media activity: The US government will soon demand to see the social media accounts and activity of anyone applying for a green card and citizenship, according to a new USCIS policy submitted to the Federal Register. [Additional coverage in The Verge]
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Toni de la Fuente, founder and CEO of cloud security firm Prowler. Toni talks about his company's latest effort, the Open Cloud Security Movement, an initiative to get more cloud security vendors to open-source their core projects.
Arrests, cybercrime, and threat intel
Taylor Swift ticket hackers arrested: US authorities have arrested two members of a cybercrime group that stole over 900 tickets to Taylor Swift concerts. Tyrone Rose and Shamara P. Simmons allegedly made over $600,000 by reselling the tickets on the black market. The two received the tickets from two accomplices working for a StubHub contractor in Jamaica.
ATM jackpotters detained: The US has arrested and charged two Venezuelan nationals for ATM jackpotting attacks.
IRS hacker extradited: The US has extradited a Nigerian man living in Mexico to face cybercrime charges. Officials claim Matthew A. Akande hacked a Massachusetts tax preparation firm and filed fraudulent tax returns through its systems. The scheme lasted between June 2016 and June 2021 and netted Akande over $1.3 million in fraudulent tax refunds.
Authorities seize Garantex: US and European law enforcement agencies have seized the website of Russian cryptocurrency exchange Garantex. A seizure banner appeared on the portal's front page for a few hours before the platform's administrators took it down. Garantex says it lost $27 million worth of Tether coins that appear to have been seized by law enforcement. The US sanctioned Garantex in April 2022 for laundering funds linked to dark web marketplaces and ransomware activity. The EU imposed its own sanctions last month for helping Russian companies bypass international sanctions related to Russia's invasion of Ukraine. [Additional coverage in CoinTelegraph]

Apple threat notifications go out: Apple has sent out a new wave of threat notifications to users it believes were targeted with spyware, per Amnesty International's head of security, Donncha Ó Cearbhaill.
YouTube private video sharing abused by scammers: YouTube says online fraudsters are using its private video sharing feature to target its customers. The company learned of the campaign after users reported receiving AI-generated videos of YouTube's CEO announcing changes to the company's monetization scheme.
YouTube content creator extortion: YouTube IT and tech content creators are being extorted by a crypto-mining gang. The attackers pose as the developers of software tools and threaten to send copyright strikes to the content creator unless they link to a malicious version of the tool that contains the SilentCryptoMiner. According to Kaspersky, the campaign has been taking place since last year and has targeted Russian-speaking creators.
EFF scammers: Hunt.io has uncovered a group of online scammers posing as the Electronic Frontier Foundation and which targeted the online gaming community.
The Scam Empire: A consortium of 32 media outlets published tens of coordinated stories on Wednesday, unmasking a giant cybercrime cartel named The Scam Empire. The group is comprised of different companies that run call centers and server infrastructure linked to online investment and crypto scams. Investigators estimate the group has stolen at least $275 million from over 32,000 victims across the world. The scams were traced back to call centers in Eastern Europe, Israel, and Georgia. Reporters learned of the illegal activity after they received 1.9 terabytes of leaked data from an anonymous source detailing the activity of two of the Scam Empire companies.
Online survey scams: Infoblox researchers break down one of those annoying online survey emails/popups that are everywhere and show how they lead to online scams (in case you still had any doubts about what they really are).
Malvertising campaign leads to GitHub: Microsoft looks at a malvertising campaign redirecting users to GitHub repositories hosting infostealer-laced software tools.
EncryptHub: Outpost24 says the EncryptHub cybercrime group has had an OpSec leak, exposing some internal infrastructure and tooling.
"Their lapses include directory listing enabled on key infrastructure components, hosting stealer logs alongside malware executables and PowerShell scripts, and revealing Telegram bot configurations used for data exfiltration and campaign tracking."
Black Basta leaks: The Eclypsium team takes its own look over the contents of the Black Basta internal chat leaks.
Hotkey-based malware: Elastic's security team has published recommendations on how defenders can detect hotkey-based malware on their systems, such as keyloggers and infostealers.
PHP-CGI campaign in Japan: Cisco Talos has published a pretty detailed report on a campaign that exploited a PHP-CGI vulnerability (CVE-2024-4577) to breach companies in Japan and deploy loads of backdoors and exploitation frameworks. The vulnerability has been widely exploited by DDoS botnets, cryptomining gangs, and ransomware operators.
Naming schemes are stupid, part 2918: A CyberScoop report cites a US prosecutor who says different threat actor naming schemes are confusing investigators and indirectly helping attackers.
SECP0 RaaS: A new RaaS platform launched this week named SECP0.
Malicious PyPI package: Socket Security has discovered a malicious PyPI package that steals local Ethereum private keys to empty victims' accounts.
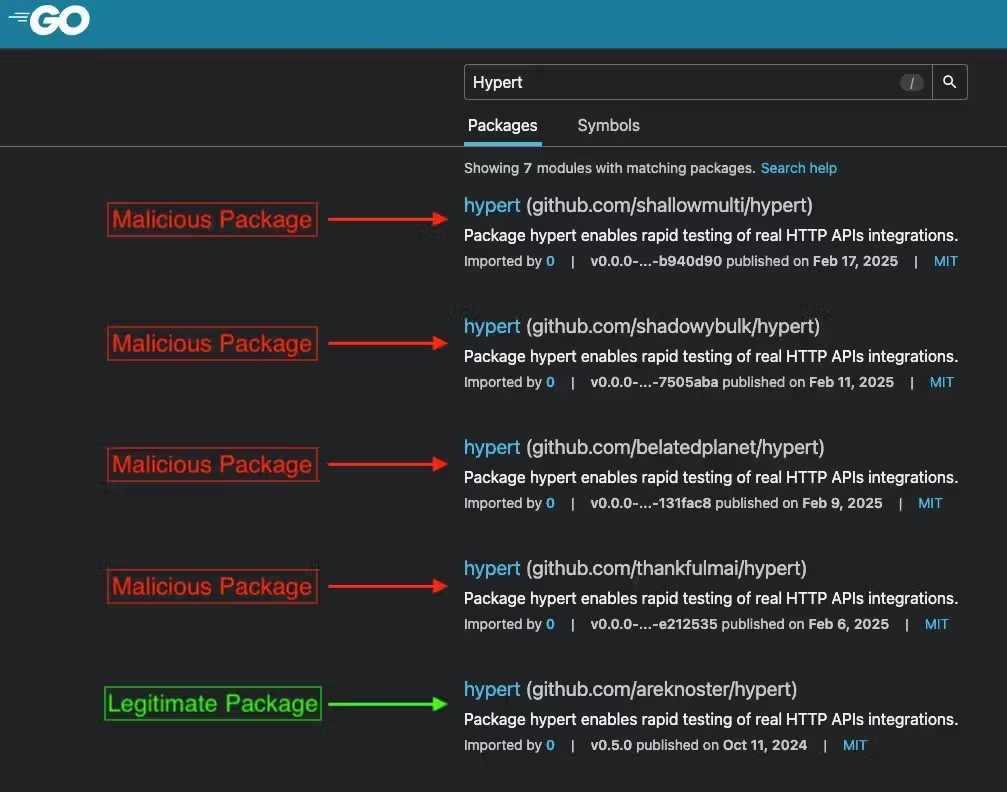
Malicious Go package: The same Socket Security also discovered a malicious Go library that deploys malware on macOS and Linux systems.
Malware technical reports
Boramae ransomware: CyFirma researchers spotted a new ransomware named Boramae advertised in underground forums.
EByte ransomware: The same CyFirma team published a report on the new Go-based EByte ransomware that popped up a few months ago.
Medusa ransomware goes wild: Broadcom's Symantec says it has seen Medusa ransomware attacks jump by 42% between 2023 and 2024.
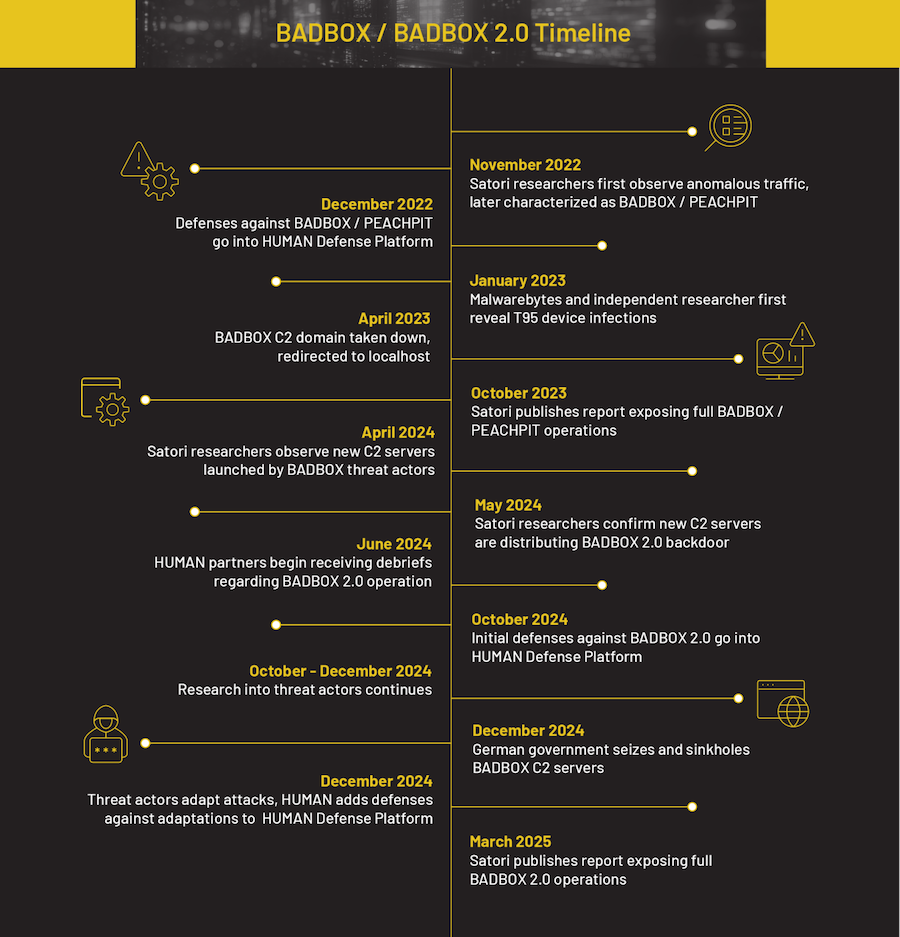
BADBOX disrupted after return: A coalition of security firms has disrupted a new version of the BADBOX botnet. Companies sinkholed botnet traffic and took down 24 Android apps used to infect user devices. The botnet used preinstalled backdoors and malicious apps to infect devices. The devices were used to relay malicious traffic and ad fraud. HUMAN Security says it identified four different threat actors operating different parts of the botnet and cooperating with each other (SalesTracker, Lemon, MoYu, and LongTV). The new BADBOX v2 botnet infected over one million devices and launched this year after German authorities sinkholed the first version at the end of last year.
Sponsor section
In this sponsored product demo, Prowler founder and CEO Toni de la Fuente walks Risky Business host Patrick Gray through the company's open-source cloud security platform. Toni demonstrates how Prowler can identify and remediate security issues across AWS, Azure, GCP, and Kubernetes. There's a pointy-clicky GUI interface and a CLI, and both come in handy in different ways. The Prowler platform is completely free and open source, but there is a hosted version you can pay for if you don't want to run it yourself.
APTs, cyber-espionage, and info-ops
Silk Typhoon: On the day that the US charged Silk Typhoon (APT27) members, Microsoft published a report on the group's recent attacks on IT supply chains, such as companies behind remote management tools and cloud applications, which the group uses to pivot into upstream networks. That's how the group hacked the US Treasury by first breaching IAM provider BeyondTrust. The report also links Silk Typhoon to an Ivanti zero-day from January, tracked as CVE-2025-0282.
DPRK supply chain attack alert: South Korea's intelligence agency has sent out an alert warning local companies that DPRK hackers are conducting software supply chain attacks. Some of the attacks have taken place as recently as last month. Attacks targeted a groupware platform and a mobile identity verification system.
Vulnerabilities, security research, and bug bounty
Sitecore vulnerability: Assetnote researchers have found an unsafe deserialization vulnerability in the Sitecore CMS that can lead to remote code execution attacks—CVE-2025-27218.
Cisco security updates: Cisco released this week three security advisories for its products.
Jenkins update: The Jenkins project has released a security update to fix four vulnerabilities in the platform's core.
Kibana security updates: Elastic has released a security update for its Kibana app. The update fixes a prototype pollution vulnerability that leads to arbitrary code execution via a crafted file upload and specifically crafted HTTP requests.
Sleeping Beauty: SEC Consult researchers have published details on Sleeping Beauty, a technique to suspend the CrowdStrike Falcon sensor.
"SEC Consult reported this issue to the vendor following our coordinated vulnerability process end of 2023, but the vendor told us it is only a "detection gap" and closed the issue without a fix. It seems to be patched now in 2025 and this blog post provides a short write-up of the issue."
EvilLoader: A security researcher known as 0x6rss published details on EvilLoader, a vulnerability in the Telegram Android app that can be used to run malicious code on a user's device.
"This exploit remains unpatched and continues to work on the latest version of Telegram for Android 11.7.4. Even more concerning, the payload has been available for sale on underground forums since January 15, 2025, making it accessible to cybercriminals worldwide." [via Mobile Hacker]
EntrySign exploit: Google has published technical details on EntrySign, an AMD Zen microcode signature validation vulnerability (CVE-2024-56161) that can allow threat actors to install malicious firmware. It also released Zentool, a tool to jailbreak AMD processors.
Polymorphic Chrome extension: SquareX researchers have developed a polymorphic Chrome extension that can mimic any other locally installed extension.
"The polymorphic extensions create a pixel perfect replica of the target's icon, HTML popup, workflows and even temporarily disables the legitimate extension, making it extremely convincing for victims to believe that they are providing credentials to the real extension. These credentials can then be used by attackers to access all the sensitive information, credentials and financial assets stored in the victim's account."
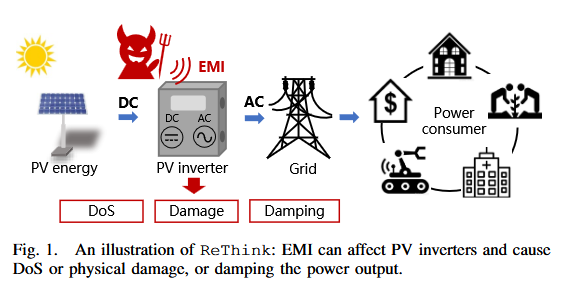
ReThink attack on PV stations: A team of academics has published details on a new type of electronic attack against power inverters installed on photo-voltaic stations. Named ReThink, the attack can physically damage inverters and destroy PV capability.
Infosec industry
Cybereason CEO steps down: Cybereason CEO Eric Gan has stepped down after clashing with investors. Gan sued investment firm SoftBank and former US Treasury Secretary Steven Mnuchin for blocking re-financing efforts claiming their sabotage had brought the company on the edge of bankruptcy. Cybereason has also scrapped its planned merger with US security firm Trustwave. [Additional coverage in Yahoo Finance]
Acquisition news: US cybersecurity firm Armis has acquired Otorio, a provider of OT (Operational Technology) and CPS (Cyber Physical Systems) security.
New tool—Rayhunter: The Electronic Frontier Foundation has open-sourced Rayhunter, a tool to detect cell site simulators via Orbic-made mobile hotspots.
New tool—CVSS-TE: Security researcher Kris Stone has released CVSS-TE, a new vulnerability scoring metric and lookup tool. The source is also on GitHub.
New tool—InvokeADCheck: Orange's SensePost team has released InvokeADCheck, a PowerShell module designed to evaluate the security of Active Directory environments.
Insomi'Hack 2024 videos: Talks from the Insomni'Hack 2024 security conference, which took place year in Switzerland, are available on YouTube.
Threat/trend reports: Corvus, Incogni, and Red Sift have recently published reports and summaries covering various infosec trends and industry threats.

Risky Business Podcasts
In this podcast, Tom Uren and Patrick Gray discuss how Starlink is providing an internet lifeline for scam compounds that have had their internet access cut by Thai authorities. Starlink has a very poor track record dealing with unauthorized use, but it is time for the company to develop the processes to keep on top of these problems.
In this edition of Between Two Nerds, Tom Uren and The Grugq take a deep dive into incident response reports from Chinese cybersecurity firms that attribute the hack of one of the country's top seven defense universities to the US National Security Agency.




