Risky Bulletin: US charges major ransomware figure
In other news: White House to keep CyberCom and NSA dual role; Apple ships "always-on" memory safety protection feature; another massive supply chain attack hits the npm world.

This newsletter is brought to you by Trail of Bits. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
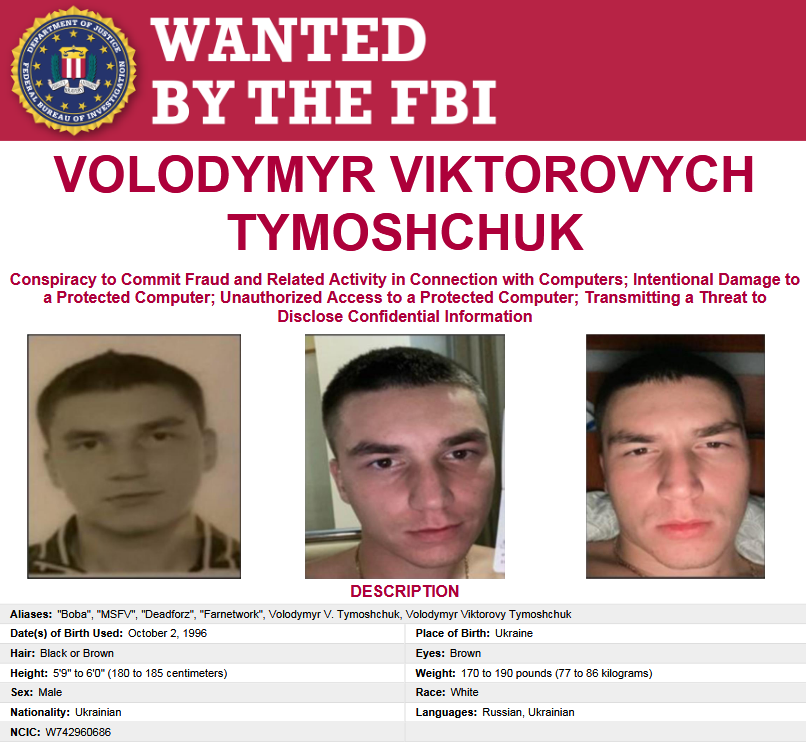
The US Department of Justice unsealed charges on Tuesday against a major figure in the ransomware underground, a Ukrainian national who was involved in or managed at least seven ransomware platforms.
The charging documents identify Volodymyr Viktorovich Tymoshchuk as the administrator of the LockerGoga, MegaCortex, and Nefilim ransomware operations.
From his role, he coordinated or was involved in the hacks and extortions of more than 250 US organizations, and hundreds more around the world.
Tymoshchuk went online under multiple hacker names, such as deadforz, Boba, msfv, and farnetwork.
A Group-IB report published in November 2023 linked the farnetwork persona to four other ransomware groups and multiple other malware strains.
Although not in the DOJ charges, Tymoshchuk appears to have also been involved with the JSWORM, Karma, Nemty, and Nokoyawa Ransomware-as-a-Service (RaaS) platforms.
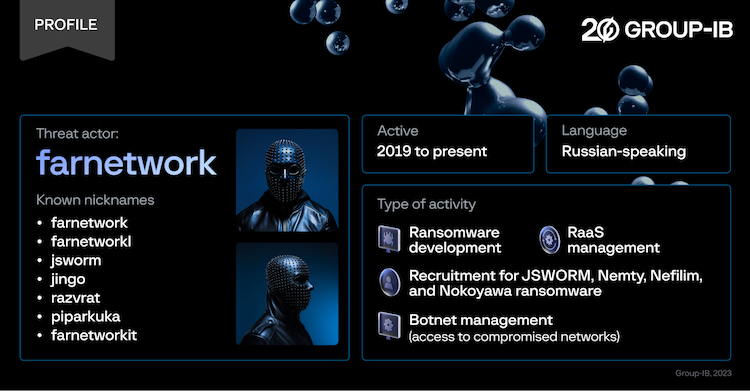
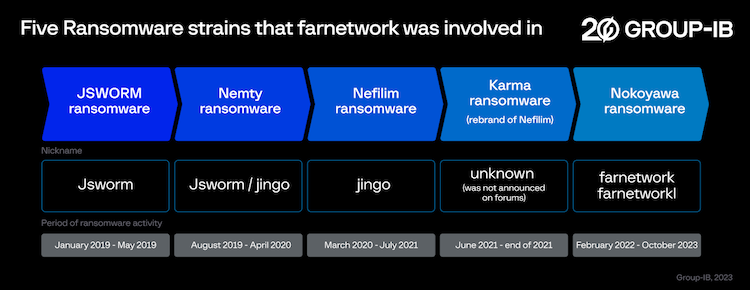
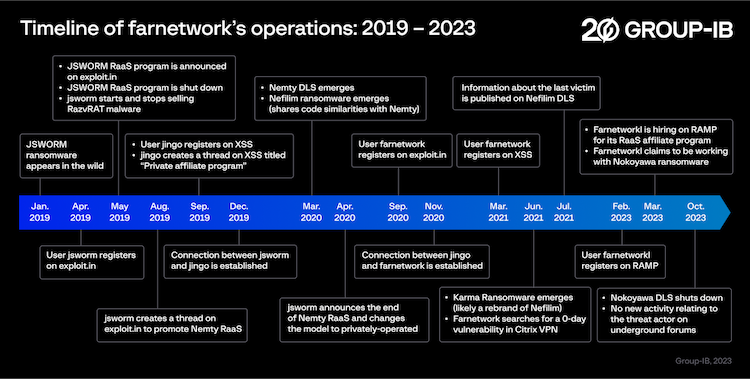
The Group-IB report described "farnetwork" as being a developer and a manager of these platforms, but also an active marketer and recruiter.
He was active on multiple hacking forums promoting his malware and asking others to join his RaaS, help deploy the ransomware, and be given a cut of the profits, with cuts ranging from 65% to 85% of the ransoms.
Tymoshchuk's platforms barely survived a year in most cases. According to a recent Australian Institute of Criminology study, the median age of a RaaS platform is 1.36 years, after which they shut down or rebrand.
All of Tymoshchuk's ransomware efforts seemed to have focused on and used manpower from Ukraine.
In November 2022, Ukraine's Cyber Police detained five suspects involved in LockerGoga, MegaCortex, Hive, and Dharma ransomware attacks.
Earlier this year, in May, the US DOJ secured the extradition from Spain of a Ukrainian national who was involved in attacks with Tymoshchuk's Nefilim ransomware.
Tymoshchuk itself is still at large, and his whereabouts are unknown. The FBI is offering a $10 million reward for information that may lead to Tymoshchuk's arrest, and up to $1 million in separate rewards for information on any of his other accomplices.
Risky Business Podcasts
The main Risky Business podcast is now on YouTube with video versions of our recent episodes. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
Another npm supply chain attack: A threat actor compromised 27 npm libraries and added malicious code designed to intercept and hijack cryptocurrency transactions. The attacker allegedly compromised developers using a phishing email that mimicked a 2FA reset request. The compromised packages had collectively more than two billion weekly downloads. The updates containing the malicious code were taken down in less than an hour due to a swift community response, and the malicious versions had zero downloads.

Jeremy Clarkson's farm hacked: Hackers have stolen £27,000 ($36,000) from the pub of former Top Gear presenter Jeremy Clarkson. Clarkson said the hackers broke into the pub's accounting system. It's unknown who was behind the intrusion. [Additional coverage in Oxford Mail]
Ransomware hits K Club before Irish Open: A ransomware group has leaked the data of a golf club days before it was set to host the Irish Open. The SafePay ransomware took credit for the attack on K Club, a five-star golfing resort in Kildare, Ireland. The tournament took place as scheduled over the weekend. K Club didn't say if it paid the ransom. [Additional coverage in KFM Radio]
Vietnam mega-breach: A hacking group claims to have stolen the personal data of almost all Vietnamese citizens. The data was allegedly taken from the country's Credit Information Center, a national agency that keeps track of citizens' credit status. The full data is more than 160 million records containing highly sensitive personal information. The Vietnamese government has yet to confirm the incident. [Additional coverage in DataBreaches.net]
St. Joseph ransomware: The city of St. Joseph, Missouri, has spent more than $1 million to recover from a June ransomware attack. The funds were spent to improve outdated platforms. The city has also notified more than 11,000 people who had their data stolen in the incident. St. Joseph had an estimated population of more than 70,000 residents. [Additional coverage in News Press Now]
New Salesloft victims: New companies have added their names to the list of organizations impacted by the Salesloft Drift supply chain attack. They include Qualys, Dynatrace, and Fastly.
Nemo Protocol crypto-heist: Hackers have stolen $2.4 million worth of crypto assets from the Nemo Protocol. The platform suspended all smart contracts to investigate the breach. [Additional coverage in The Block]
SwissBorg crypto-heist: Hackers have stolen $41 million worth of Solana crypto tokens from the SwissBorg platform. The attackers exploited a vulnerability in a partner's API integration. SwissBorg said it would reimburse all customers from its own funds. The stolen assets represent 2% of all its funds. [Additional coverage in CoinTelegraph]
Plex resets passwords: Media streaming platform Plex is resetting all user passwords after a security breach. A hacker accessed a Plex database and allegedly stole emails, usernames, hashed passwords, and other authentication data. The company said it already patched the method used by the attacker to get in.
plex got pwned, reset your passwords
— tierney cyren (@bnb.im) 2025-09-08T21:59:28.163Z
General tech and privacy
Tor VPN available: The Tor Project has released an official VPN app that allows Android users to route all their traffic through the Tor network.
Signal Secure Backups: Secure messaging app Signal has introduced a new feature that lets users create secure backups of their text conversations. The feature will keep backups for up to 45 days. Users who want to keep text conversations and media for longer periods will have to pay $1.99/month. This is Signal's first paid feature. All backups will be encrypted end-to-end, with a 64-character recovery key generated on a user's device.
Chat Control open letter: More than 500 researchers from 34 countries published an open letter against the EU's proposed Chat Control regulation.
Former head of security sues Meta: Meta's former head of security is suing the company for wrongful termination. Attaullah Baig claims the company ignored repeated warnings about WhatsApp vulnerabilities and privacy violations. He claims that more than 1,500 WhatsApp engineers had unrestricted access to user data, but only 10 worked on the app's security team. Baig says WhatsApp leadership retaliated with negative work reviews as soon as he started reporting on its security issues. He was eventually fired in April for alleged poor performance. [Additional coverage in CyberScoop]
Chinese company exports GFW tech: A Chinese company linked to China's Academy of Sciences is exporting the technology to build national censorship firewalls. The governments of Kazakhstan, Ethiopia, Pakistan, and Myanmar have purchased and installed equipment from Geedge Networks. Geedge's secret exports came to light after more than 100,000 files leaked from its network. [Additional coverage in InterSecLabs, Amnesty International, Justice for Myanmar]
BlueSky adds bookmarks: BlueSky has rolled out an update this week to add support for post bookmarking.
v1.108 is rolling out today 🚚 Now live, at long last: Bookmarks, aka Saved Posts. For all those posts you'll definitely plan to come back to! Update the app and give it a try. The button is right down there 👇
— Bluesky (@bsky.app) 2025-09-08T18:24:18.334Z
Government, politics, and policy
US ends fight to combat fake news: The US has terminated agreements with European countries to fight disinformation from hostile countries like Russia, China, and Iran. The agreements were signed last year under the previous Biden administration. They were managed by the Global Engagement Center (GEC), a division that the State Department shut down earlier this year. [Additional coverage in the Financial Times]
CISA to delay CIRCIA rules: CISA is expected to delay the implementation of the Cyber Incident Reporting for Critical Infrastructure Act. CIRCIA was set to go into effect next month once CISA published the final implementation rules. The implementation rules are now expected around May next year. [Additional coverage in InsidePrivacy]
FCC bans bad labs: The FCC has revoked authorization for seven test labs based in China. The labs reviewed and approved electronics for sale in the US. They also approved which devices would bear the US Cyber Trust Mark, a special label that signifies a secure product. The FCC began an investigation into US Cyber Trust Mark test labs in March over national security concerns.
White House shelves dual-hat split plans: The Trump administration has abandoned any intention of breaking up the joint leadership of US Cyber Command and the National Security Agency. According to The Record, officials quietly accepted that splitting the dual-hat arrangement would prove too lengthy and complex. The White House is expected to nominate Army Lt. Gen. William Hartman to take up the leadership of both agencies.
ICE contracts Clearview AI: The US Immigration and Customs Enforcement will pay up to $10 million to use Clearview AI's facial recognition software. The agency says it will use the software to identify individuals who assault its agents. ICE also recently reactivated a contract with Israeli spyware and surveillance maker Paragon Solutions. It also uses hacking tools from Cellebrite, Magnet, and Pen-Link. [Additional coverage in Forbes]
Hackers leak Boris Johnson emails: Hackers have leaked more than 2,000 emails allegedly taken from former UK Prime Minister Boris Johnson. The emails date from his time in office between 2019 and 2022. They allegedly contain information on the COVID-19 response and the war in Ukraine. The email leak has not been ruled out as a possible foreign influence operation. [Additional coverage in SAN]
Nepal lifts social media ban after violent protests: Nepal lifted a ban on 26 social media networks after the block sparked days of violent anti-government protests. At least 22 people have lost their lives since the protests began last week. The country's prime minister resigned on Tuesday after the protests turned extremely violent. Most of the country's capital has shut down after protesters set fire to the Parliament, the Supreme Court, police stations, and the houses of major politicians. [Additional coverage in CNN and the BBC]
BREAKING: Nepal is going through a violent revolution right now as the Parliament, Supreme Court, police stations, and houses of politicians have been set on fire by Gen-Z. The Prime Minister and Home Minister have resigned in succession in the last 24-ish hours. www.nytimes.com/live/2025/09...
— Alex Ip 葉清霖 (@alexip718.com) 2025-09-09T15:06:36.041Z
Young people are using the social media platforms that were just recently unbanned by the Nepalese government to circulate videos of them burning a former Prime Minister's wife alive and stripping the Finance Minister naked, then throwing him into a river. Oh my God. Oh my God.
— Alex Ip 葉清霖 (@alexip718.com) 2025-09-09T15:17:16.708Z
Sponsor section
In this Risky Business sponsor interview, Casey Ellis chats with Keith Hoodlet from Trail of Bits. Keith is Trail of Bits' director of engineering for AI, machine learning, and application security, and he joined Casey to talk about why prompt injection attack techniques that target AI are an unsolvable problem.
Arrests, cybercrime, and threat intel
Treasury sanctions more scam compound operators: The US Treasury Department has imposed sanctions on scam compound operators in Cambodia and Myanmar. Sanctions were levied on three individuals and their six companies operating a crypto scam compound in the border town of Shwe Kokko, Myanmar. The three are the leaders of the Karen National Army, a breakaway military force that now runs the Karen state of Myanmar. Sanctions were also levied on four Chinese nationals for running scam compounds in the Cambodian cities of Bavet and Sihanoukville. The compounds are run out of casino and hotel complexes managed by the group.
Money mule sentenced: A California man was sentenced to 51 months in prison for laundering $36.9 million in crypto assets linked to scam compounds operating out of Cambodia.
BlackDB admin pleads guilty: A Kosovo man pleaded guilty to running BlackDB. The site was an online marketplace for selling hacked accounts, hacked servers, and stolen payment card details. Liridon Masurica was arrested at the end of last year and extradited to the US in May.
Myanmar scam compounds report: ASPI has published a report on the rise of scam compounds in Myanmar and how the ruling military junta allows them to operate as a way to enrich and keep loyal its military allies.
DDoS booters attempt comebacks in hours: DDoS-for-hire services that were seized by authorities typically try a comeback within hours. The new sites look nearly identical to the old ones. Despite this, traffic to the revived clones usually collapses within weeks. According to new academic research, users move to new DDoS booter services. Researchers conclude that takedowns work in the short term, reduce attack traffic, but the DDoS-for-hire market is resilient.
Ransomware gangs live around one year: According to the Australian Institute of Criminology, ransomware gangs typically remain active for 1.36 years on median. Larger groups can remain active for 1.76 years. Groups that rebrand can remain active for longer.
Calcio streaming service shuts down: An illegal pirated sports streaming service named Calcio has shut down following legal pressure from the Alliance for Creativity and Entertainment (ACE).
Madgicx Plus campaign: Cybereason has spotted a fake and malicious Chrome extension for Madgicx, an AI-based platform for managing Meta ads. Researchers found "potentially malicious functionalities capable of hijacking business sessions, stealing credentials, and compromising Meta Business accounts."
Docker cryptomining: Akamai looks at a campaign exploiting exposed Docker APIs to deploy cryptominers. This is the same campaign spotted by Trend Micro in June.
Axios abuse: ReliaQuest reports a 241% surge in email spam coming from the Axios lightweight HTTP client.
Alviva Holding profile: Threat intel analyst Rakesh Krishnan has published a profile on Alviva Holding, a bulletproof hosting provider for ransomware operations.
New Desolator ransomware group: A new ransomware operation named Desolator has been spotted leaking victims on the dark web.
Malware technical reports
GPUGate malware: ArcticWolf has spotted a clever new malware strain named GPUGate that is being delivered via trojanized GitHub Desktop installers promoted via malvertising campaigns.
"The delivered malware is unique: the bloated 128 MB Microsoft Software Installer (MSI) evades most existing security sandboxes, while a Graphics Processing Unit (GPU)-gated decryption routine keeps the payload encrypted on systems without a real GPU. We have called this new attack technique 'GPUGate'."
Salat Stealer: CyFirma has a report on Salat Stealer, also known as WEB_RAT. The malware is offered as a MaaS by a Russian-speaking team of developers known as the NyashTeam.
RatOn: Mobile security firm ThreatFabric has discovered a new Android banking trojan named RatOn. The trojan targets cryptocurrency wallets and has an automated money transfers (ATS) feature that uses the Android Accessibility API to empty accounts. It currently targets users in Czechia and Slovakia.
MostereRAT: Fortinet researchers have spotted a phishing campaign spreading the new MostereRAT. Some of this campaign also uses scripts written in the Easy Programming Language (EPL), a Simplified-Chinese-based programming language.
ZynorRAT: Sydig has discovered a new Go-based RAT named ZynorRAT. The malware appears to be the work of a Turkish-speaking developer and can run on both Linux and Windows.
The Gentlemen ransomware: Trend Micro has published a technical report on The Gentlemen, a new ransomware group that popped up online last month.
Sponsor section
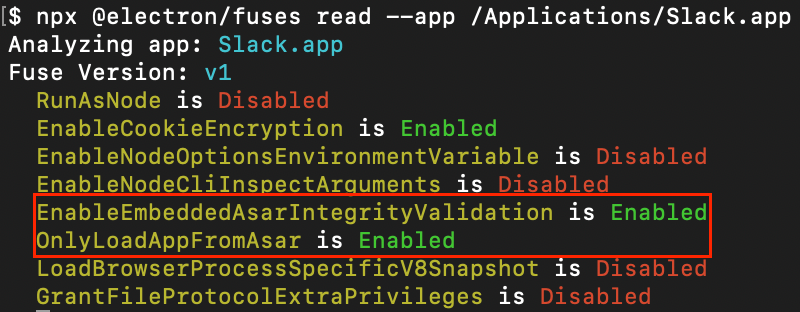
A vulnerability discovered by Trail of Bits in Electron applications allows attackers to bypass code integrity checks by tampering with V8 heap snapshot files, enabling local backdoors in applications like Signal, 1Password, and Slack.
APTs, cyber-espionage, and info-ops
New Salt Typhoon infrastructure: Security firm SilentPush has found new domains that appear to be operated by the Salt Typhoon Chinese cyber-espionage group. The team also found another group tracked as UNC4841 that overlaps with Salt Typhoon infrastructure, which is currently launching attacks against Barracuda email security gateways.
APT28's GONEPOSTAL: Kroll's cybersecurity team has published a report on GONEPOSTAL, an Outlook backdoor also known as NotDoor.
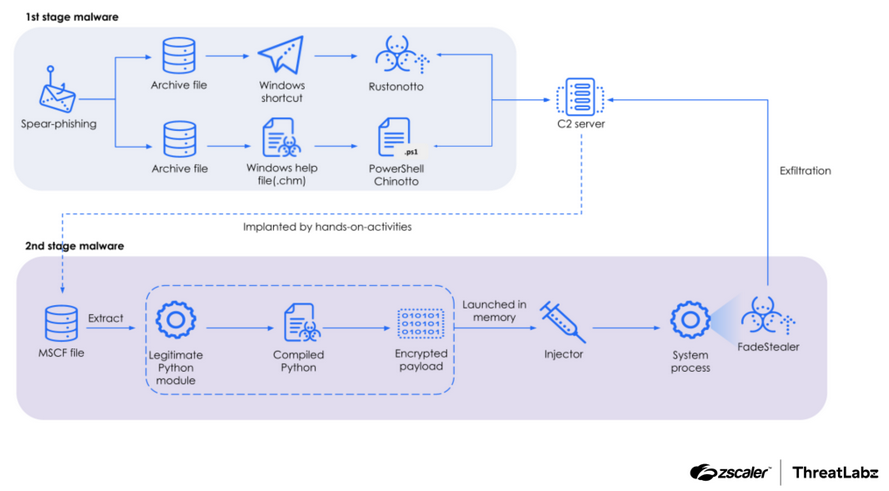
New APT37 tooling: Zscaler has published a report looking at new APT37 tooling, a Rust-based backdoor (Rustonotto), and a Python loader that deploys FadeStealer.
Vulnerabilities, security research, and bug bounty
Patch Tuesday: Yesterday was the September 2025 Patch Tuesday. We had security updates from Microsoft, Adobe, SAP, Ivanti, Dell, IBM, NVIDIA, AMD, Arm, Qualcomm, Palo Alto Networks, D-Link, Axis, Zoom, Rockwell Automation, Schneider Electric, and Siemens. The Android Project, Chrome, Cisco, Drupal, Sitecore, Jenkins, Synology, ABB, and Gigabyte released security updates last week as well.
Microsoft Patch Tuesday: This month, Microsoft patched 81 vulnerabilities, but no actively exploited zero-days.
New Apple Memory Integrity Enforcement system: Apple has shipped a new security feature named Memory Integrity Enforcement (MIE). The new feature combines hardware and software-based defenses to run "always-on" memory safety protections for Apple products. Apple's security team says it worked on the industry-first design for half a decade. MIE shipped with iPhone 17, released on Tuesday. [Allison Husain Mastodon thread]
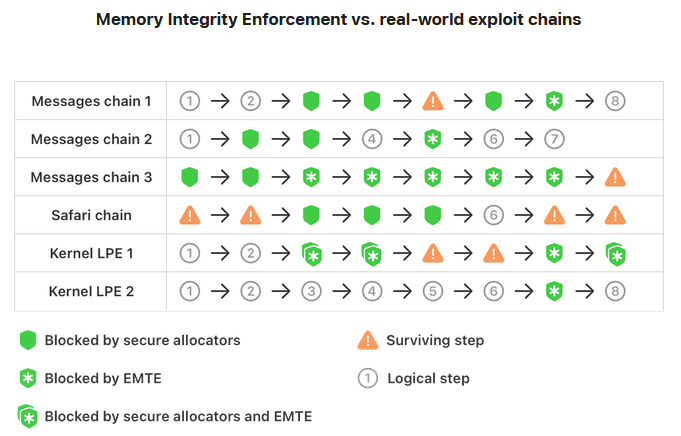
🔺iPhone models announced today include Memory Integrity Enforcement, the culmination of an unprecedented design and engineering effort that we believe represents the most significant upgrade to memory safety in the history of consumer operating systems. https://t.co/ule9gaXzc1
— Ivan Krstić (@radian) September 9, 2025
Apache Jackrabbit unsecure deserialization: The Apache project has patched an untrusted data serialization bug (CVE-2025-58782) in the Apache Jackrabbit API and content repository platform.
New Defender disable technique: Red teamer Two Seven One Three has found a new folder redirection technique that can be used to disable Windows Defender.
Apple zero-day write-up: pwn.LLC has published an analysis of CVE-2025-43300, the macOS/iOS zero-day that Apple patched last month, the one that was used together with a WhatsApp zero-day in a sophisticated targeted spyware attack. Also, see this Quarkslab analysis too.
LookCam app is a complete disaster: The Android app of the LookCam security cameras is fraught with security flaws. According to security researcher Wladimir Palant, the app uses a bogus protocol encryption scheme, fake access controls, and its firmware is riddled with security flaws. Palant says the app abides by Murphy's Law and that "everything that could be done wrong, has been done wrong." The LookCam app has more than 1 million downloads on the Google Play Store and also comes with iPhone and Windows versions, although they were not reviewed.
SessionReaper vulnerability: Adobe has released a security update to patch a critical vulnerability in the Magento and Adobe Commerce platforms. Named SessionReaper (CVE-2025-54236), the vulnerability allows unauthenticated remote attackers to run malicious code and take over online stores. According to Sansec, automated abuse is expected, and merchants should patch immediately.
Bluetooth AP oopsie: Researchers have found that the Amp'ed RF BT-AP 111 Bluetooth Access Point exposes an HTTP-based administrative interface without authentication controls. Yey!!!! I love dumb bugs!
Hiawatha vulnerabilities: Keysight researchers have found three major vulnerabilities in the Hiawatha barebones open-source web server. This includes request smuggling, a double-free bug, and an authentication timing attack.
XSS at Microsoft: Microsoft's Security Response Center has posted an explainer on how it triages XSS reports, and which of them it considers bad versus boring.
Sapphos temporarily shuts down after security bug report: Sapphos, a dating app for lesbian women in Brazil, temporarily shut down operations this week after reports of a security flaw that could expose the sensitive data of its users. [Additional coverage in The Record]
DNS4EU audit: BadCyber has published a review/audit of the EU's new DNS4EU private DNS service.
Infosec industry
Acquisition news: The Mitsubishi Electric Corporation has announced plans to acquire OT/IoT cybersecurity company Nozomi Networks.
Threat/trend reports: Cisco Talos, Guardsquare, Kaspersky, Sophos, and WalletHub have recently published reports and summaries covering various threats and infosec industry trends.
Risky Business podcasts
In this edition of Between Two Nerds, Two Nerds Tom Uren and The Grugq talk about the trend toward outrageously complicated exploits and what it means for hacking and cyber espionage.
In this edition of Seriously Risky Business, Tom Uren and Amberleigh Jack talk about Google starting a cyber disruption unit. It's a sign of the times, but could also point the way forward for policymakers looking to involve the private sector in government-endorsed efforts to strike back in cyberspace.




