Risky Bulletin: The growing influencer problem to national security
In other news: Russia sanctions Recorded Future; US prepares to ban TP-Link; Raccoon Stealer dev sentenced to five years in prison.

You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
China and Russia appear to have understood before everyone else the role social media influencers play in modern societies, and are using them as weapons against unprepared Western democracies.
Both autocratic regimes have passed strict laws regulating the online presence of social media personalities while at the same paying foreign influencers in covert operations designed to subvert and influence foreign societies and elections.
China passed a law at the end of last year mandating that social media influencers and bloggers with over 500,000 followers must list their legal names on their profiles.
Similarly, in Russia, the Kremlin passed a law this year requiring any online personality with over 100,000 followers to register with the country's internet watchdog by the start of next year.
The two countries now have firm control over their social media landscape through the new laws, as well as their national firewall and internet censorship systems.
The crackdown is both the normal response from two paranoid autocratic regimes fearing they might lose control of their societies, but also a means of self-defense.
On the flipside, both countries have used opaque networks of companies to pay and weaponize influencers in other countries to promote their political agendas.
A Recorded Future report published last week concluded China has established over 100 so-called international communication centers (ICCs) across the country since 2023. The centers are tasked with running news websites that push Chinese-friendly propaganda and criticize democratic countries in various areas of the globe. The ICCs have also assembled "networks of thousands of foreign influencers" that get paid to push the same narratives inside the borders of other countries in posts that are designed to look as genuine as possible. Australian think tank ASPI also published a report on this.
Meanwhile in Russia, earlier this year the US disrupted and charged Russian nationals and organizations for a large-scale disinformation operation that meddled in the US election and tried to sabotage US support for Ukraine. Two RT employees allegedly paid an American company and its right-wing influencers, such as Tim Pool, to push the Kremlin's anti-Ukraine talking points, sometimes for as much as $100,000 per video.
Russia also allegedly paid Romanian-speaking social media influencers to push pro-Kremlin candidates in this year's presidential elections in Moldova and Romania.
Some of the influencers who accepted the payments are believed to have ties to Romania's criminal underground. So mobsters with huge TikTok followings are meddling in internal politics, candidly admitting to receiving payments to promote Sputnik and TASS talking points? This is not fine.
In Romania, influencers who are believed to have taken money to promote Calin Georgescu, the pro-Kremlin presidential candidate, are currently being investigated by financial authorities. Some have already fled the country, knowing the role they played and from whom they took the money.
In a first for a country in the EU bloc, Romania also annulled its recent presidential elections. The move sent shockwaves through the EU and has sent European governments and intelligence agencies into a frenzy to address the new "influencer problem".
The EU launched a formal investigation into TikTok for its failure to detect a large network of bots that meddled in Romania's election, but also on how these bots and influencer accounts managed to skirt the company's rules on political advertising.
In another report this week, French Foreign Minister Jean-Noel Barrot said the French government has evidence that Russia approached thousands of influencers across Europe to push their propaganda. Barrot says they have identified 20 influencers who have accepted deals, including nine in France, as part of an ongoing investigation.
In Spain, the government said it plans to submit a bill that would require social media personalities to issue corrections to posts that peddle disinformation. The bill comes after the prime minister's wife was the subject to a corruption investigation that was discovered to have been entirely based on unverified media reports.
While there's no Russian involvement in this instance, it's still similar to the influencer problem that Russia and China have addressed—namely, that governments are starting to get tired of random nobodies yapping bulls**t on social media and causing problems. The UK government went through something similar over the summer when race riots were fuelled by misinformation that was amplified and amplified over and over again on social media for days, including via big accounts, and with the government unable to stop it.
In an op-ed for the Nieman Lab earlier this month, Alice Marwick, director of research at Data & Society, predicted that "mainstream media will lose its last grip on relevancy" next year, and social media influencers will become the main avenue of how people get their news.
A Pew Research study published last month found that one in five adult Americans were getting their news from social media influencers instead of news organizations. For adults under 30, that figure was 37%. For anyone with a social media account, it is not a surprising stat.
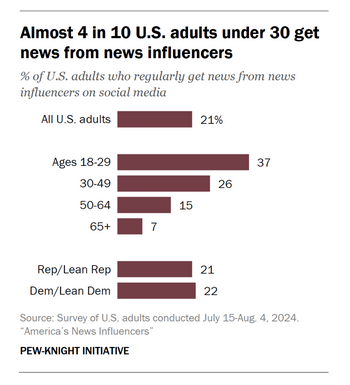
As it stands right now, Western societies are becoming—and at a very accelerated rate—extremely vulnerable to malicious parties active on their social media feeds.
There are no good solutions here. Free democracies cannot introduce blanket regulations like China and Russia have. It's fraught in Europe and the incoming administration in the United States has shown hostility toward any government efforts to tackle disinformation and misinformation. But it's time to start thinking about what can be done about this before we're drowning in a sea of influencer-peddled Kremlin and CCP propaganda.
Risky Business Podcasts
Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
China says US state hackers breached local firms: China's CERT team claims that hackers linked to a US intelligence agency have breached two local tech companies. US hackers allegedly breached a Chinese company in the smart energy and digital information sector in May of last year and a company involved in advanced materials research and design in August this year. China's CERT says the attackers exploited Microsoft Exchange vulnerabilities for the first intrusion and stole trade secrets during the second.
SS7 hacks: The US Department of Homeland Security says threat actors from China, Russia, Iran, and Israel have exploited vulnerabilities in the SS7 protocol to spy on US citizens. The hacks were part of a campaign that targeted individuals across the world. The US Defense Department says all US telcos are vulnerable to SS7 hacks and have not taken any steps to mitigate future attacks. [Additional coverage in 404 Media/Wyden letter PDF]
Rspack supply chain attack: A threat actor has gained access to the Rspack npm bundling utility and released a malicious version of the library and its CLI package. According to Socket Security, the two malicious versions contained a crypto-miner. The two packages were live for only a few hours but are believed to have been downloaded by thousands of developers already—mainly because of Rspack's popularity.
Cisco breach: IntelBroker has started leaking data they stole from Cisco back in October. [Additional coverage in SecurityWeek]
Hapn leak: GPS tracker firm Hapn is leaking the names of thousands of customers via its website, per TechCrunch.
Correctiv DDoS attacks: German news website Correctiv says it was the target of a large-scale DDoS attack after it published a report exposing Russia's disinformation campaigns across Europe. The attack lasted for days and attempted to prevent the site's visitors from reading the report. Correctiv says it traced the attack back to a company linked to Russia's Ministry of Defense.
BeyondTrust security breach: Identity and PAM provider BeyondTrust says a threat actor has gained access to some Remote Support SaaS instances. The breach took place on December 2. The attackers used a compromised API key to reset passwords for some customer applications. BeyondTrust also patched two vulnerabilities that appear to have been used during the intrusions. The two allowed attackers to run code on behalf of a legitimate user on Remote Support platforms.
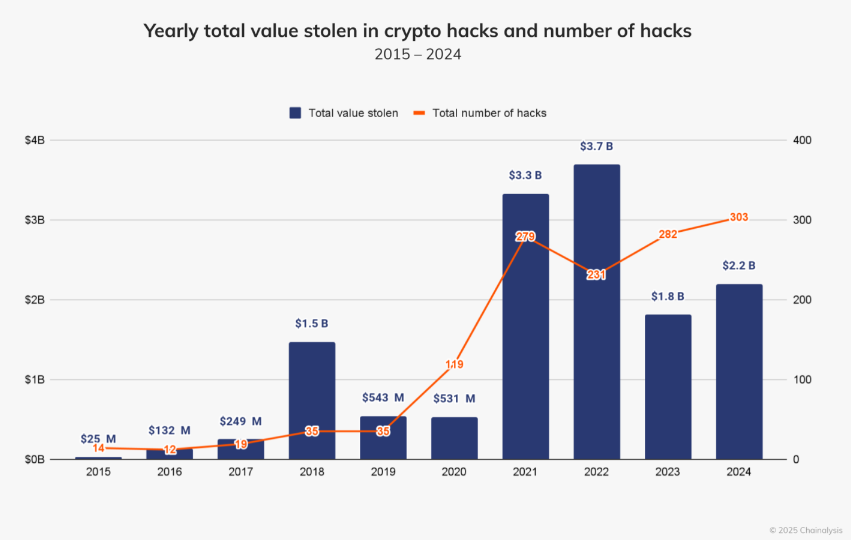
Crypto-heist numbers: Blockchain analysis firm Chainalysis says threat actors stole over $2.2 billion worth of crypto assets last year. Most of the hacks took place in the first part of the year, with activity slowing down after July. Most of the funds were stolen from DeFi platforms. This year's biggest hack was the DMM Bitcoin crypto-heist in May, when the company lost $305 million. DMM shut down earlier this month.
General tech and privacy
Netflix fined in the Netherlands: Dutch authorities have fined US streaming service Netflix €4.75 million for GDPR violations. The Dutch data protection agency says Netflix failed to inform consumers what it was doing with their personal data between 2018 and 2020. The company has since fixed this situation by updating its privacy policy.
Google will allow device fingerprinting next year: Google will allow advertisers to use device-based fingerprinting techniques to track users starting next year. The new policy will enter into effect on February 16. Google says the new policy is needed to replace cookie-based tracking and because on-device privacy-preserving technologies have matured. The UK's privacy watchdog was not convinced and plans to hold a consultation on Friday, December 20. The ICO says the new policy might be illegal because it's harder to track, block, and consent—something that Google itself said five years ago.
"Unlike cookies, users cannot clear their fingerprint, and therefore cannot control how their information is collected. We think this subverts user choice and is wrong."
Apple discontinues some services in Russia: Apple will discontinue its Fitness and Apple TV inside Russia starting this month, per iPhones.ru.
Government, politics, and policy
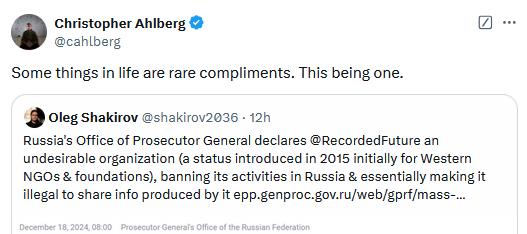
Russia sanctions Recorded Future: The Russian government has added security firm Recorded Future to its list of "undesireable" organizations. The Kremlin cited the company's work with Ukraine and foreign intelligence agencies to support so-called "propaganda" against Russia. Russian officials say the company also collects and analyzes data on its armed forces. Recorded Future was one of the first security firms to provide aid to Ukraine after Russia's invasion, together with Microsoft and Cisco Talos. Over the past two years, Recorded Future has published numerous reports exposing Russia's hacking and influence operations. It has also helped its prosecutors investigate war crimes.
CISA tells agencies to secure their clouds: CISA has ordered federal government agencies to review and secure their Microsoft cloud environments. Federal agencies will be required to inventory and report all their cloud infrastructure to CISA by February 21, next year. Agencies will also have to run CISA's SCuBA tool to audit their Microsoft 365 tenants for common misconfigurations. Agencies will have to integrate the tool's result feeds with CISA's monitoring solutions by April 25.
CISA tells HVTs to secure mobile devices: CISA has asked high-ranking government officials to secure their mobile devices in the face of rising cybersecurity risks from foreign adversaries. The agency published a guide on Wednesday with a series of steps and recommendations officials can take to safeguard their devices. The guide urges officials to use and prioritize end-to-end encrypted communications, use FIDO-based authentication, and keep their devices and software up to date. It also advises officials to use a password manager, avoid using VPNs, and set up a PIN for their telco voice mail.
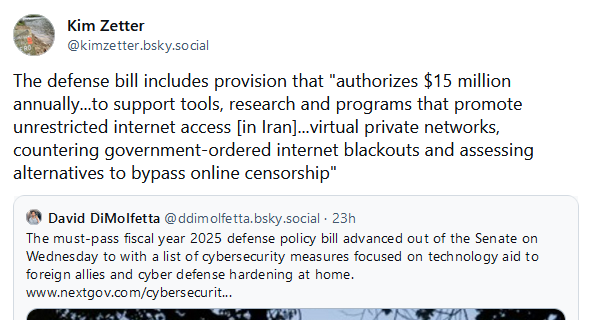
Congress passes NDAA with cyber provisions: The US Congress has passed the 2025 National Defense Authorization Act. This year, the NDAA included several cyber provisions, such as cyber and technology aid for foreign allies and US cyber defense hardening projects. [Additional coverage in NextGov]
US considering TP-Link ban: The US government is considering a ban of TP-Link products in the US on the grounds of national security. Officials say the company's routers have been linked to cyberattacks against US critical infrastructure. According to reports, the Commerce, Defense, and Justice departments have opened separate investigations into the Chinese company. An official ban is expected early next year. [Additional coverage in the Wall Street Journal]
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about the evolution of Russian cyber operations during its invasion of Ukraine.
Arrests, cybercrime, and threat intel
Raccoon Stealer dev sentenced: A US judge has sentenced a Ukrainian man to five years in prison for creating and selling the Racoon Stealer malware. Mark Sokolovsky was arrested in the Netherlands in March 2022 after authorities seized and shut down the Raccoon Stealer operation. Until US authorities announced his arrest in October of that year, fellow malware developers thought Sokolovsky had died in the war in Ukraine. Other threat actors have now taken over the Racoon Stealer malware and have released new versions. Sokolovsky was known online as "Photix."
US seeks extradition of LockBit developer: The US government is seeking the extradition of an Israeli citizen for their role in developing the LockBit ransomware. Rostislav Panev allegedly developed components for the LockBit gang, including a module that printed ransom notes via a victim's printers. Israeli police detained Panev in the city of Haifa in August. Investigators allegedly found evidence at his home linking him to LockBit ransom notes and payments. [Additional coverage in Ynet]
Web scanner linked to Turkish IT firm: Brian Krebs says a Turkish IT firm called Bilitro Yazilim is behind a web-based vulnerability scanner known as Araneida.
Rockstar 2FA goes down, FlowerStorm emerges: Sophos security researchers say that a new Phishing-as-a-Service platform named FlowerStorm has recently risen in popularity. The service gained traction after a rival platform named Rockstar 2FA went down two weeks ago due to a technical failure on its backend. Sophos says FlowerStorm has made several mistakes during its recent sudden expansion, mistakes that may be exploited during future law enforcement disruptions.
Bluesky typosquatting: Tedium reports on an extortion scheme currently targeting Bluesky users where threat actors register domains typosquatting the names of famous people, create and then verify Bluesky accounts with that domain, and then extort the target for access to the domain and verified Bluesky account.
Telegram still reigns supreme: According to a new KELA report, cybercriminals are still active on Telegram despite claiming they would leave after Pavel Durov's arrest earlier this year.
"The ransomware group known as Bl00dy Ransomware Gang has declared on September 24, 2024, that following the Telegram policy change, the group is leaving Telegram. Despite the claims and the sudden abruption of the activity on the channel after the quitting, message, one month later, on October 24, 2024, they resumed their activity in a new Telegram channel, sharing on the channel their ransomware victims, as well as advertising the new Telegram channel on their X account."
AI-generated malvertising: Malwarebytes looks at a malvertising campaign that uses AI tools to generate content for their fake websites.
Azure phishing campaign: A threat actor has targeted over 20,000 employees working at European companies in an attempt to gain access to their employer's Microsoft Azure cloud infrastructure. The campaign took place between June and September this year and broadly abused HubSpot infrastructure.
Google Calendar phishing campaign: Check Point says there's a massive phishing campaign going on that's mimicking Google Calendar and Google Drawings notifications to lure victims to phishing sites.
Cyber Anarchy Squad: Kaspersky has published a profile on Cyber Anarchy Squad, a pro-Ukrainian hacktivist group attacking Russian and Belarussian organizations. The group's tools include RATs and ransomware.
NoName057: Radware has published a report on the activity of the NoName057 GRU-controlled hacktivist group and its evolution this year.
Holy League: Suspected Russian, Iranian, Hamas, and Hezbollah "hacktivists" have announced the creation of the Holy League, a super-group dedicated to launching DDoS attacks against the mean NATO, Western nations, India, and Israel. Per Radware, the Holy League members include:
"High Society, Seven October Union, UserSec, NoName057(16), CyberArmy Of Russia, HorusTeam, CyberHood, Keymous, 313 Team, SilentCyberForce, InsanePakistan, AstroNetworks, GhostXNet, Anonymous Arabs, Team YSG, DXQRTXX, Khilafah Hackers, CyberVolk, CyberStine, Cryptaris, VoltActivist, NetSycho, AlixSec, AzzaSec, Hunt3rKill3rs, HexaLocker, Lapasus, NetForceZ, Al Jihadi, ShadowedWhisper, VendettaNetworks, Anonymous DZ, UCC Team, Nasa1788, KotoBot, YourAnon, B&D Services, Nemesis, CryptoCorp, ZBlackHat, ColtisHere, Al Ahad, SumatraSelatan, LulzSec, WebSec, UnderWorld (Anonymous Revengers), PicoCorp, RedHatElite, UFC Leagues, ShadowSeekers, Spectrum Botnet, TarzanBotnet, Pro-Palestinian Hacker Movement (PPHM), Anon Collective, MarioC2, Fatimion, Ahadun Ahad, CyberDragon, Phantom Group, Islamic Cyber, Team HTR, Morrocan Black Cyber Army, LulzSec Pakistan"
Malicious VSCode extensions: ReversingLabs researchers have identified 18 malicious VSCode extensions available through the official VSCode Marketplace. The extensions were live in October and tried to deploy backdoors on the systems of crypto-related projects. ReversingLabs says that as soon as the extensions were removed from the VSCode Marketplace, the attacker uploaded similar malicious projects on the npm portal.
Malicious npm libraries: On the same software supply chain theme, Sonatype looks at two npm libraries (ESLint and Node Types clones) that managed to get thousands of downloads before being taken down. On top of that, SourceCodeRED has also found seven npm pacakges that dropped macOS malware.
Juniper SSR attacks: Networking equipment vendor Juniper says that threat actors have breached and deployed malware on Session Smart Router (SSR) in a series of attacks last week. Attackers targeted routers that were still using their default passwords and installed a version of the Mirai malware. Juniper says the devices were later used to launch DDoS attacks.
Spyware on the Amazon App Store: McAfee researchers have found Android spyware hidden in apps uploaded to the Amazon App Store.
Valencia Leaks: A new ransomware gang named Valencia popped up in September. Since then, it got its website and Twitter account taken down. Unclear if they're still active.

Malware technical reports
Chaya_003: Forescout has discovered a new OT/ICS malware that can terminate Siemens engineering processes. Named Chaya_003, the malware uses Discord for C2 communications and appears to have been developed by a Dutch-speaking developer. So far, Forescout has spotted at least three samples of the new malware.
NodeStealer evolution: Trend Micro has spotted a Python-based version of the NodeStealer malware, whose original versions were based on Node.js, hence its name.
Diicot: Wiz has published a report on Diicot, a crypto-mining group also known as Mexals that targets Linux environments.
cShell: AhnLab has published a technical analysis on cShell, a new DDoS botnet malware strain targeting Linux servers with exposed SSH services.
NotLockBit ransomware: Qualys has published a report on NotLockBit, described as "one of the first fully functional ransomware strains to target macOS and Windows systems." Similar reports are also available from SentinelOne and Trend Micro.
Risky Business Podcasts
In this podcast Tom Uren and Patrick Gray talk about the likelihood that the incoming Trump administration will end the ‘dual-hat’ arrangement where a single officer leads both US Cyber Command and the National Security Agency. This would result in Cyber Command outranking NSA and could prioritise cyber disruption operations over intelligence collection. That would be a bad outcome.
They also talk about how changes to SEC disclosure rules have led to an outpouring of corporate drivel and how WhatsApp became an everything app.
APTs, cyber-espionage, and info-ops
Q4 info-op takedowns: Google TAG has published its review of all takedowns of info-ops in Q4 2024. Lots of China and Russia activity. Busy bees!
New Doppelganger infra: Security firm ClearSky has discovered new infrastructure linked to the Russian disinfo group Doppelganger and posing as Western media outlets.
ASA reward: The US State Department is now offering a $10 million reward for information on a company named Aria Sepehr Ayandehsazan. According to a recent FBI report [PDF], this is the new company from which the old Emennet Pasargad threat actor is now operating.

UAC-0125: CERT-UA has detected activity from a Sandworm-related cluster (UAC-0125) that is using a clone of the Army+ official app website to go after Ukrainian military-related targets.
Lazarus DeathNote campaign: Kaspersky analyzes recent changes in Lazarus DeathNote (DreamJob) campaigns.
"In this blog, we provide an overview of the significant changes in their infection chain and show how they combined the use of new and old malware samples to tailor their attacks."
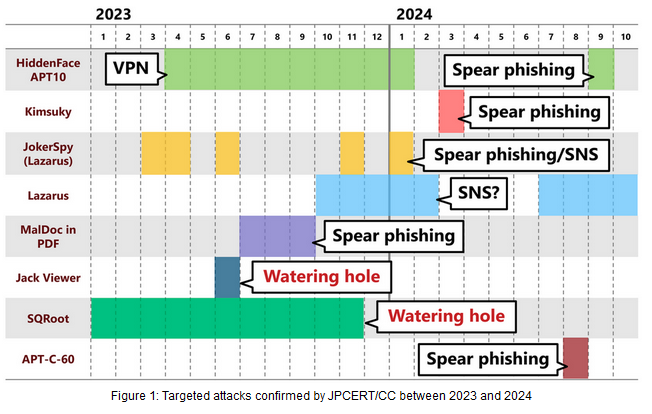
Recent APT watering hole attacks: Japan CERT/CC looks at recent APT watering hole attacks that targeted Japanese organizations.
Vulnerabilities, security research, and bug bounty
DigiEver exploitation: A threat actor is exploiting a vulnerability in DigiEver DVRs to install the Mirai DDoS malware on unpatched devices. Akamai has linked the attacks to a new botnet named Hail Cock that appeared in September this year. The attacks are targeting a DigiEver DVR that has been end-of-life since 2014 and for which no patch will likely be available.
Cleo exposure: According to Censys, over 70% of all internet-exposed Cleo file-transfer servers may be vulnerable to an actively exploited unauth RCE tracked as CVE-2024-55956.
Craft CMS RCE: Assetnote security researchers have found an RCE vulnerability in Craft CMS, one of today's most popular CMS solutions. Tracked as CVE-2024-56145, the vulnerability occurs when the CMS runs on PHP servers with a certain configuration enabled (register_argc_argv). The configuration allows threat actors to run malicious code via URL arguments. The Craft team has fixed the bug this week but researchers warn that other PHP apps may also be vulnerable.
Major FortiWLM vulnerability: Fortinet has released a security update for its Wireless Manager software to fix a critical vulnerability. Tracked as CVE-2023-34990, the vulnerability can be used to execute unauthorized code or commands via specially crafted web requests. The issue has a severity rating of 9.6/10.
Tomcat security update: The Apache Foundation has released a security update to fix a new RCE tracked as CVE-2024-50379.
KEV update: CISA has updated its KEV database (twice) with five vulnerabilities that are currently exploited in the wild. This includes a second bug exploited in the Cleo hacks and two vulnerabilities in NUUO NVRs and Reolink security cameras, respectively.
McDonald's India pwnage: Security researcher Eaton Zveare has discovered vulnerabilities in the McDonald's India McDelivery API system that could have allowed threat actors to order any menu item for just ₹1. The vulnerabilities also allowed attackers to collect customer and order details, track deliveries in real-time, and even retrieve data on drivers and their vehicles. All issues were fixed in September.
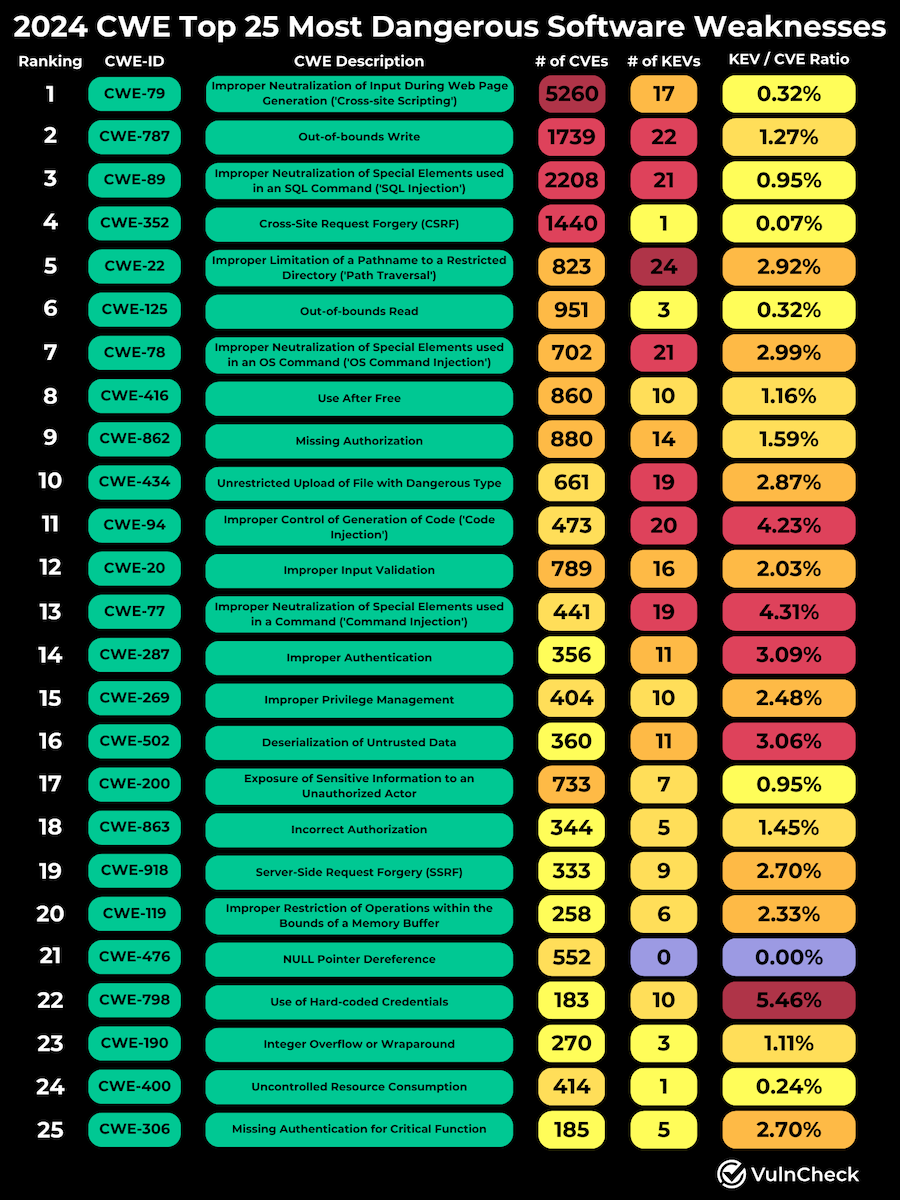
CWE stats: VulnCheck takes the MITRE Top 25 CWEs and compares it to the CISA KEV CWEs to see what are this year's true top security weaknesses.
Infosec industry
Infosec whistleblower lawsuits: ArsTechnica looks at infosec and IT whistleblowers using the False Claims Act to expose big corps skirting cybersecurity and other government contract requirements—and get paid along the way.
CrowdStrike asks judge to dismiss Delta lawsuit: CrowdStrike has asked the court to dismiss Delta Air Lines' lawsuit over the company's July cybersecurity outage. [Additional coverage in CNBC]
Threat/trend reports: Dragos, Flashpoint, Google TAG, Promon, SlashNext, and VulnCheck have recently published reports and summaries covering various infosec trends and industry threats.
DefCamp 2024 videos: Talks from the DefCamp 2024 security conference, which took place in Bucharest at the end of November, are now available on YouTube.
Risky Business Podcasts
Brian A. Coleman, Senior Director for Insider Risk, Information Security, and Digital Forensics at Pfizer, talks to us about how his security team is experimenting with AI to improve their insider risk detection systems. The system Brian and his team put together can detect sensitive information or documents handled by unauthorized accounts, but can also spot documents moving around and ending up where they shouldn’t be - either by accident, malice, or as a result of a security breach.




