Risky Bulletin: Thai army and police behind dissident doxing campaign
In other news: CISA extends MITRE's CVE contract; Chris Krebs resigns from SentinelOne following White House attack; Apple patches two iOS zero-days.

This newsletter is brought to you by application allow-listing software maker Airlock Digital. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
The Royal Thai Armed Forces and the Royal Thai Police ran an online harassment and doxing campaign against anti-government dissidents.
The campaign doxed victims and asked followers to report them to the police, which then happily launched investigations.
The secretive attacks came to light after Thai MP Chayaphon Satondee leaked confidential police documents online at the end of March.
The documents revealed the existence of a joint Thai army and police "cyber team" that allegedly ran the harassment campaign.
According to a CitizenLab report, most of the attacks took place with the help of Facebook and Twitter accounts, but other online services were also involved.
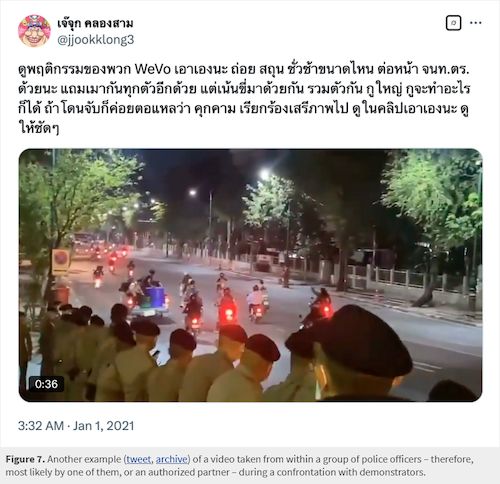
CitizenLab researchers claim that the nature and the amount of private data used for doxing dissidents is not the type of data you usually find in private online databases—which is a lawyered-up way of saying they might have come from government systems.
The campaign appears to have been taking place since at least 2020, when the country experienced a huge wave of pro-democracy protests demanding major reforms to the country's monarchical structure and military junta-led regime.
It is unclear if the campaign helped Thai officials secure any convictions, but around 270 anti-regime dissidents have been charged in Thailand with lèse-majesté crimes that carry long prison sentences.
Regardless, CitizenLab described the campaign—which they named JUICYJAM—as one of the most successful in recent memory. This is because social networks failed to act on it, even if doxing was and is against each network's terms of service, and because the campaign was quickly followed through by real-world judicial actions in some sort of weird uroboros government process.
"With a high rate of following and engagement across platforms, JUICYJAM is an uncommon instance of a successful state-sponsored influence operation. JUICYJAM's tactics support a larger network of judicial harassment and democratic suppression that is infrequently enforced by social media platforms, but poses a significant threat to civil society."
Risky Business Podcasts
Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
BreachForums defacement: A hacking group named Darkstorm has taken credit for defacing BreachForums with a fake FBI seizure banner. [Additional coverage in Cybernews]
CISA warns of Oracle Cloud breach (instead of Oracle): CISA has published an alert on the Oracle Cloud data breach before Oracle did—mainly because the company is still busy wordsmithing its way around the issue.
Tempo DDoS attack: Indonesian news site Tempo has faced a days-long DDoS attack after publishing a report on online gambling networks in Cambodia.
Russian cyberattacks increase in Poland: Polish authorities say Russian cyberattacks are intensifying as they get close to the country's presidential election in May. [Additional coverage in the Defense Post]
Fontys University data leak: The Fonys University in the Netherlands has leaked the personal and medical data of some of its staff and students. The university blamed the incident on a misconfigured Microsoft Teams instance that mistakenly left some of its channels open to the public.
Law firm fined for brute-force attack: The UK ICO has fined a local law firm £60,000 for leaking sensitive customer information following a brute-force attack on some of its legacy systems in 2022.
General tech and privacy
Bunq phishing losses top €10mil: Mobile banking app Bunq says it had to refund more than €10 million last year to customers who fell for phishing scams. [More in Bunq's yearly report/PDF]
NIST Privacy Framework: NIST has released a new draft of its Privacy Framework.
Mozilla kinda sides with Google: Mozilla CEO hinted in a blog post this week that the Firefox browser might be dead without the payments from the Google search deal, which may be in danger if the DOJ breaks up Google following its monopoly case.
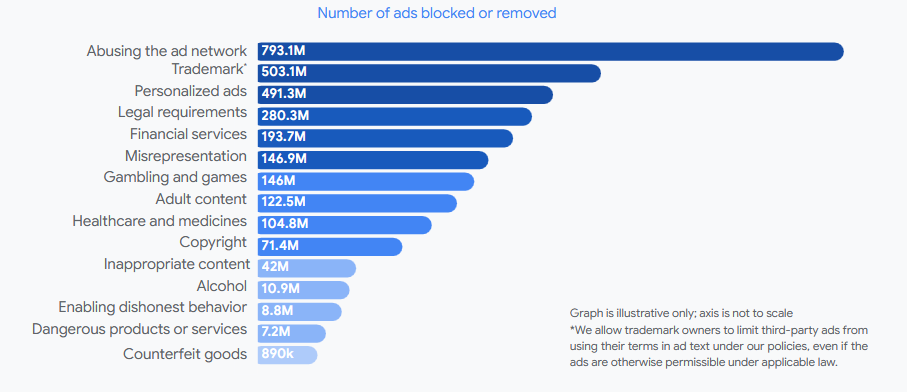
Google blocked 5.1 billion ads: Google blocked over 5.1 billion ads last year, restricted another 9.1 billion, and banned over 39 million advertiser accounts.
Government, politics, and policy
CISA extends MITRE's CVE contract: CISA extended MITRE's contract to manage the CVE database hours before it was set to expire on Wednesday. The agency has extended MITRE's contract for 11 months until March 16, next year. The contract is worth $57.8 million. CISA acted after the cybersecurity industry had a mass panic episode on Tuesday when they realized the CVE program was at risk. [Additional coverage in NextGov]

State Dept shuts down GEC: The US State Department has shut down an office that countered foreign disinformation efforts. The office was named the Office of Counter Foreign Information Manipulation and Interference (R/FIMI) but was previously known as the Global Engagement Center (GEC). Secretary of State Marco Rubio claimed the office silenced and censored the voices of Americans. The office previously exposed Russian and Chinese disinformation operations, and there is no evidence it censored Americans. This is the latest in a recent string of outright lies from the Trump administration. The office was already dead after Congress didn't extend its mandate last December.
Cybersecurity Information Sharing Act renewal: A pair of US senators are trying to renew the Cybersecurity Information Sharing Act, a 2015 law for cyber threat information sharing between the government and the private sector. [Additional coverage in CyberScoop]
DOD DDS mass-resignation: Nearly all the staff at the Pentagon's Defense Digital Service has mass-resigned after pressure from the DOGE boyz. [Additional coverage in Politico]
Texas Cyber Command: Texas lawmakers are debating a bill that would create its own cybersecurity agency, named Texas Cyber Command. [Additional coverage in the Dallas Morning News]
Russia to fine companies that use foreign software: The Russian Duma is working on a law to fine local companies that still use foreign software. The law would only apply to large corporations. SMBs and government agencies will be exempt. [Additional coverage in TASS]
Ukraine has a new cyber defense law: Ukrainian President Volodymyr Zelenskyy signed a new law to boost the country's cyber defenses. The law establishes new reporting obligations, crisis response procedures, and a national cyber incident response system.
South Africa introduces mandatory breach reporting: South African companies must report any security breaches to authorities via the government's official eServices portal. This replaces the previous requirement to report breaches to the country's data regulator via email. The new requirement [PDF] entered into effect this month and applies to any local or foreign company that processes the data of South African citizens. [Additional coverage in Inside Privacy] [h/t DataBreaches.net]
Cyber training for Tibet's police: A Turquoise Roof report has found that a Chinese IT company named Meiya Pico is providing cyber and digital forensics training for police stations in Tibet. The company has a long history of aiding China's oppression of the Uyghur minority.
Sponsor section
In this Risky Bulletin sponsor interview, David Cottingham and Peter Baussman, Airlock Digital’' CEO and CTO, talk to Tom Uren about a new Australian Cyber Security Centre guidance about building defensible networks. The pair cover what they like about the document and where it could be improved.
Arrests, cybercrime, and threat intel
Security researcher arrested in Oklahoma: Oklahoma police have arrested the CEO of a cybersecurity company for allegedly installing malware on the network of a local hospital. Video recordings show Jeffrey Bowie entering the St. Anthony Hospital last August and wandering for 10 minutes until he found an unattended computer. Officials claim Bowie installed malware designed "to take a screenshot every 20 minutes and forward the image out to an external IP address." Current reports don't clarify if Bowie was contracted with the hospital for a pen test. [Additional coverage in KOCO]
Bot students plague US colleges: Fraudsters are signing up for online classes at US community colleges using bot accounts in order to steal federal financial aid money meant for struggling students. The fraudsters submit AI-generated work and stay under the radar long enough for the aid disbursements to go out. Officials in California estimated that roughly one in four community college applicants are bots. Last year, the bot students collected more than $11 million in state and federal funds. [Additional coverage in the Voice of San Diego]
Community college professors have been left to play detective has their online courses fill up with fake students as part of a financial aid scheme. voiceofsandiego.org/2025/04/14/a...
— Voice of San Diego (@voiceofsandiego.org) 2025-04-15T17:02:27.119Z
Lawyer says hackers tainted lawsuit: A New York lawyer wants a previous judgment annulled after hackers stole documents from his case. [Additional coverage in Reuters]
LabHost profile: Intel471 has published a profile on LabHost, a now-defunct Phishing-as-a-Service platform that was seized by authorities last year.
Proton66 profile: Trustwave researchers have published a two-part series on Proton66, a Russian bulletproof hosting provider enabling cybercrime and disinfo operations.
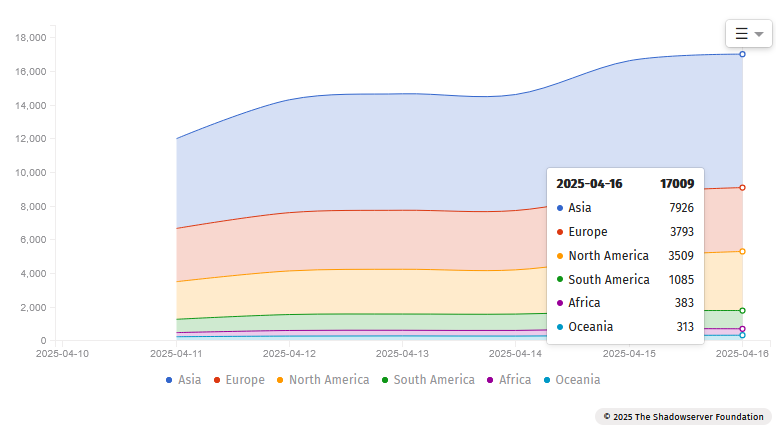
Over 17k backdoored Fortinet devices: The Shadowserver Foundation says that over 17,000 Fortinet devices have been hacked and infected with a new type of read-only access backdoor. Fortinet warned about the technique in a security advisory last week. Attackers are creating symlinks that connect a publicly available folder from the device's web dashboard to the root directory. They then use this connection to retrieve normally-private configuration files and reinfect the device. Most of the backdoored devices are located in the US and Japan.
Malicious PyPI package: JFrog has found a malicious Python library designed to intercept and steal API keys and secrets for the MEXC crypto-trading platform.
New AWS bucket encryption attacks: A threat actor is using leaked AWS credentials to access servers, encrypt data, and demand ransoms of $25,000. The attacker is not using ransomware to encrypt the data but a native AWS feature named Server Side Encryption with Customer Provided Keys (SSE-C). A threat actor named Codefinger first used this technique in a campaign last December. [Additional coverage in Cybernews]
AdSense injection campaign: Sucuri has discovered a threat actor hacking sites to inject Google ads to rack up views on their AdSense accounts.
Rapid Proxy Rotation: The Cyber Vandals team has published a blog post on Rapid Proxy Rotation, a technique used by threat actors to bypass DDoS mitigation systems that rely on detection thresholds and rate limiting. The technique involves constantly switching the source IP address for every individual request.
DKIM replay attack on Google: EasyDMARC looks at a recent phishing attack that managed to pull off a DKIM replay attack against Google.
New cluster of DPRK rogue IT workers: The Ketman Project has published a list of names and GitHub profiles they believe may be North Korean rogue IT workers posing as open-source developers and freelancers and seeking employment at Western software companies.
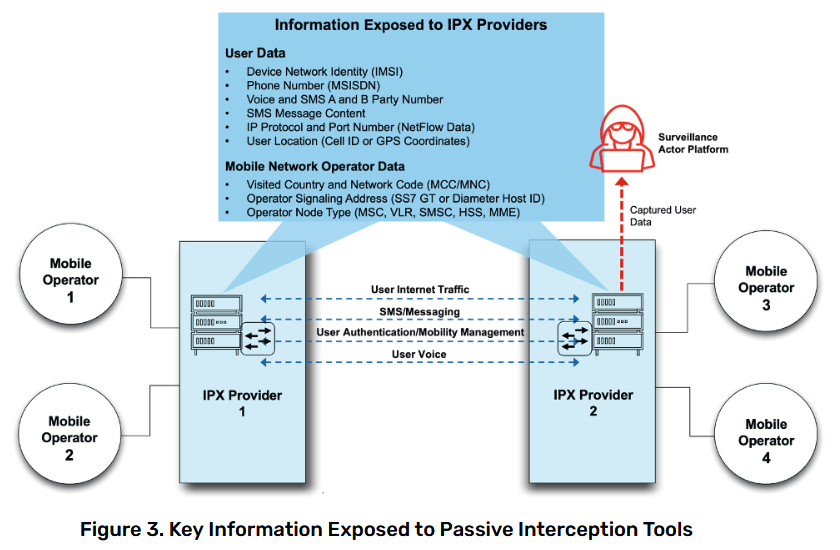
Threats of Chinese mobile telco interceptions: At least 60 mobile operators in 35 countries are routing mobile traffic through Chinese-owned networks. Security firm iVerify claims the access can allow the Chinese government to intercept and spy on mobile traffic. Most of the affected mobile operators are located in Russia and across Southeast Asia.
Malware technical reports
Interlock ransomware: Sekoia has published a report on Interlock, a closed-access ransomware group that was first spotted last September and continues to regularly list new victims on its dark web leak site. The group has also evolved, now using its own custom backdoor/RAT.
CrazyHunter ransomware: Trend Micro looks at CrazyHunter, the ransomware strain allegedly used by a Chinese security researcher against Taiwanese organizations this year.
"Approximately 80% of CrazyHunter's toolkit consists of open-source tool. It is important to monitor and secure these resources to prevent the adaptation for malicious use."
DOGE BIG BALLS ransomware: There's a new ransomware in town—named DOGE BIG BALLS.
Sometimes I can’t wrap my brain around the fact that it is literally my job to hunt and write in executive reports on the status and impact of -checks notes- DOGE “BIG BALLS” ransomware. www.broadcom.com/support/secu...
— (@huntfortheprecious.bsky.social) 2025-04-17T14:10:05.895Z
LummaStealer: A Cybereason report looks at the evolution of the LummaStealer infostealer.
XorDDoS updates: Cisco Talos has uncovered new server infrastructure used by the XorDDoS botnet.
"The language settings of the muti-layer controller, XorDDoS builder and controller binding tool strongly suggest that the operators are Chinese-speaking individuals."
Sponsor section
In this product demo of the Airlock Digital application control and allowlisting solution, Patrick Gray speaks with Airlock Digital co-founders David Cottingham and Daniel Schell.
APTs, cyber-espionage, and info-ops
Massive TikTok disinfo campaign targets Ukraine: A network of thousands of TikTok accounts are exploiting a loophole in TikTok's algorithm to influence public opinion in Ukraine and elsewhere. Because TikTok allows even new accounts to go viral, Russian bot farms are continuously registering new accounts to push propaganda after their old ones get suspended. Ukrainian reporters say they found thousands of accounts pushing Russian propaganda, with some accounts going viral with hundreds of thousands of views even if they didn't have one single follower. Russia used the same TikTok manipulation tactic to boost an unknown candidate to victory in the first round of Romania's canceled presidential election last year. [English coverage in Meduza]
Multiple APTs adopted ClickFix: Proofpoint says that a selected few APT groups have now adopted the ClickFix technique as a way to deliver initial payloads to their targets. The technique is now being used by groups from Russia, Iran, and North Korea. The company says the technique is not revolutionizing operations but merely replacing existing installation techniques due to its current high success rate. Groups spotted using ClickFix include TA427, TA450, UNK_RemoteRogue, and TA422.
Cloud Atlas targets Russia: The Cloud Atlas APT is back with new operations targeting companies in Russia's military-industrial complex. The most interesting thing is how the group used Office documents from previously hacked victims to infect new targets but stripped any metadata to prevent anyone from seeing the document's origin and previous victims.
IronHusky targets Russia too: An APT tracked as IronHusky has updated its old MysterySnail RAT payload for new attacks against government organizations in Russia and Mongolia.
CCCS advisory on Chinese APTs: Canada's cybersecurity agency has put out an alert on Chinese cyber-espionage groups targeting networking edge devices.
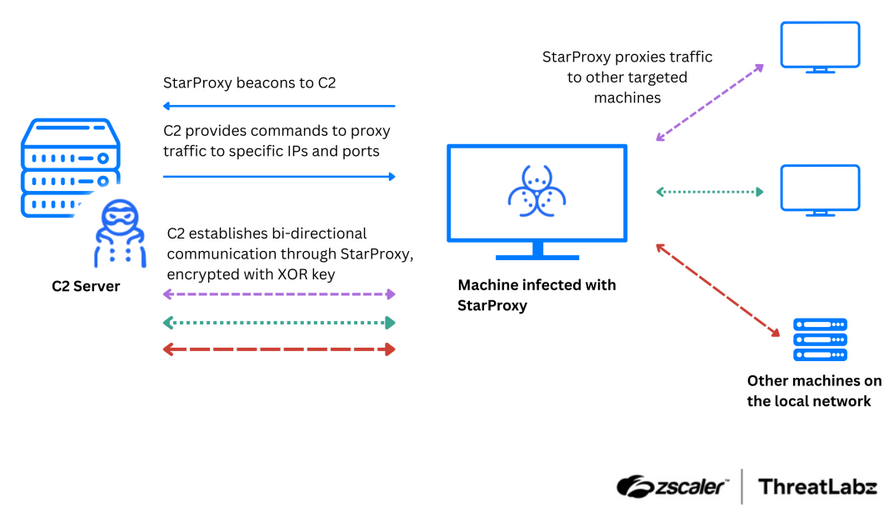
Latest Mustang Panda arsenal: Zscaler published a two-part series on the latest addition to the Mustang Panda APT—malware strains such as ToneShell, StarProxy, PAKLOG, CorKLOG, and SplatCloak.
Vulnerabilities, security research, and bug bounty
Apple fixes two zero-days: Apple has rolled out iOS security updates to fix two zero-days exploited "in an extremely sophisticated attack against specific targeted individuals." The zero-days appear to have been used together and were delivered as malicious audio files. The attacks were spotted by both Apple and Google's security teams.
NTLM bug exploited in the wild: A suspected APT group is exploiting a recently patched Windows vulnerability (CVE-2025-24054) in attacks targeting government and private institutions in Poland and Romania. The attacks use malicious Windows Library files (.library-ms) to leak a victim's NTLM hash. According to Check Point, the attack triggers when users navigate to the folder where the malicious file is stored, with no other interaction required.
New SonicWall bug exploited: CISA says threat actors are exploiting a 2021 command injection vulnerability (CVE-2021-20035) in the wild.
SAP SDK vuln write-up: Two years later, RCE Security published a write-up of a data leak in SAP's Emarsys Android SDK—CVE-2023-6542.
PHP vulnerability: The PHP project has fixed a memory-related vulnerability in the extract() function that can lead to arbitrary code execution on the past three versions.
Unauth RCE in Erlang/OTP SSH servers: A team of academics from Germany has discovered a critical vulnerability in the Erlang implementation of SSH. The vulnerability allows remote attackers to run malicious code on the SSH server without authentication. Any SSH server using the Erlang/OTP SSH library is likely affected. The vulnerability (CVE-2025-32433) received the maximum CVSS severity rating of 10/10.
Cisco security updates: Cisco has released three security advisories for its products.
Infosec industry
Chris Krebs resigns from SentinelOne: Former CISA director Chris Krebs has resigned from SentinelOne to mount a legal battle against the White House. US President Donald Trump revoked Krebs' security clearance and ordered a DOJ investigation of his work on securing the 2020 US elections as CISA director. He also ordered a review of security clearances for all SentinelOne staff. Krebs joined SentinelOne in 2023 and was chief intelligence and public policy officer. [Additional coverage in the Wall Street Journal]
Good for @thekrebscycle.bsky.social I suspect Trump is going to find out just what Krebs, who knows what did and didn’t happen in 2020, is made of. Krebs knows far more than he’s ever let on. Discovery will be interesting…
— Erin (@erinpsyd.bsky.social) 2025-04-16T22:20:32.359Z
Rebrand: Email security company Abnormal Security has rebranded to Abnormal AI.
New tool—dAWShund: Falcon Force has released dAWShund, a tool to enumerate, evaluate, and visualize the access conditions between different AWS resources.
New tool—MCP-Scan: Invariant Labs has released MCP-Scan, a security scanning tool designed to go over your installed MCP servers and check them for common security vulnerabilities like prompt injections, tool poisoning, and cross-origin escalations.
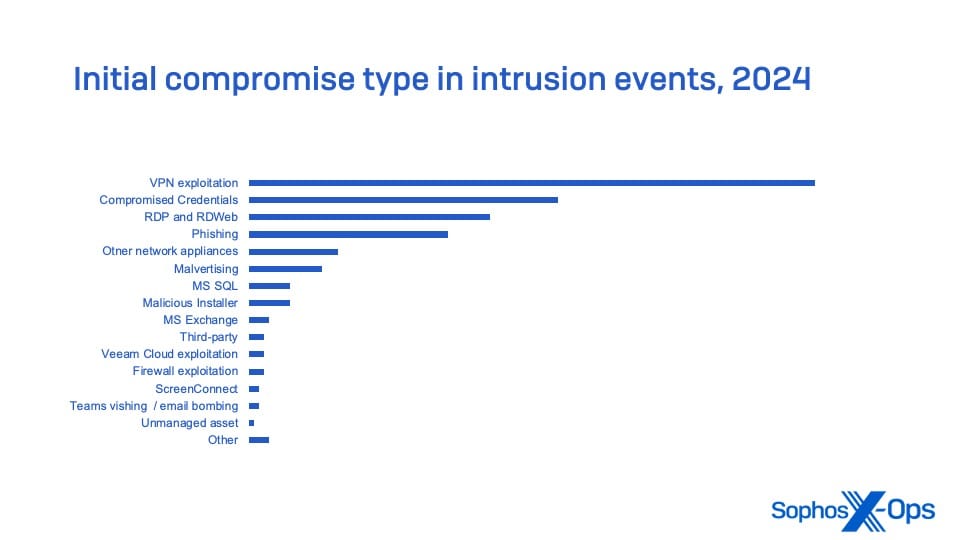
Threat/trend reports: BakerHostetler, Check Point, DataDog, Emsisoft, Google, and Sophos have recently published reports and summaries covering various infosec trends and industry threats.
Risky Business podcasts
Tom Uren and Patrick Gray discuss Trump's order singling out Chris Krebs, former head of CISA, which requires investigations into Krebs and also punishes his employer. It is a move deliberately designed to chill dissent, and they look at what the cybersecurity industry will likely do in response, which is probably not much.
In this edition of Between Two Nerds, Tom Uren and The Grugq look at the idea of global critical infrastructure. One common example is submarine cables, which are globally important but are vulnerable because they are hard to defend. But what about services from tech giants? Are they global critical infrastructure?




