Risky Bulletin: Supply chain attack at AdsPower browser platform
In other news: Paragon cuts off Italy's access to its spyware; Trimble zero-day under attack; UN and NATO hacker detained in Spain.

This newsletter is brought to you by Thinkst, the makers of the much-loved Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
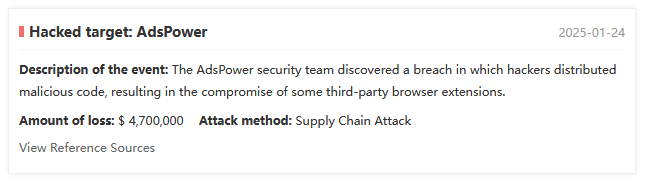
A threat actor has compromised the AdsPower browser platform and injected malicious code that modified third-party crypto wallet extensions and stole user funds.
The breach took place on January 21 and went undetected for three days before the company removed the code and forcibly uninstalled all the targeted extensions from users' browsers.
According to SlowMist founder Yu Xian, the code worked as a backdoor that extracted mnemonic recovery phrases and private keys from the wallet extension and sent them to an attacker's server.
AdsPower, which develops a multi-profile privacy-centric browser, says that users who downloaded and installed cryptocurrency wallet extensions between January 21, 10:00 AM, and January 24, 10:00 AM (UTC+0) were likely affected.
The company says it notified all users it believes were affected by the hack and told them to move funds before the hackers would get to empty their wallets.
According to John Tuckner, the founder of Secure Annex, a company specializing in browser extension security, the attack appears to have targeted browser extensions for MetaMask and OKX.
While the incident is still under investigation, SlowMist estimates that hackers have stolen around $4.7 million worth of crypto-assets with keys linked to the AdsPower incident.
[h/t to our anonymous reader]
Risky Business Podcasts
Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
Delloite pays for Rhode Island breach: Deloitte has agreed to pay $5 million to the state of Rhode Island to cover the costs of a recent ransomware attack. The incident took place in December and targeted the state's health and social services portal—a system managed by the company. Rhode Island says the Deloitte payment will be used to cover a breach call center, credit monitoring, and identity protection for impacted residents. [Additional coverage in StateScoop]
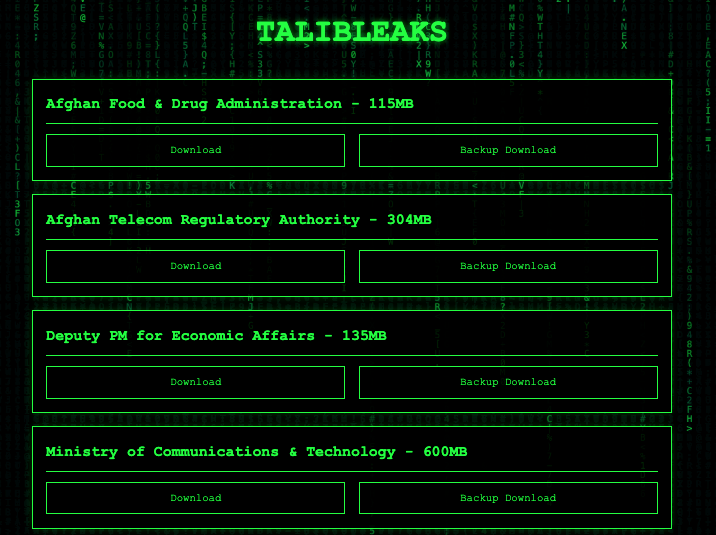
Taliban leak: Hackers have breached and leaked documents from 21 Taliban ministries and government agencies. The hackers have leaked over 50GB of data on a website named TalibLeaks. The documents allegedly include the names of political prisoners and the details of travel bans for certain government employees. The Taliban government has confirmed the authenticity of the files but denied suffering a security breach. [Additional coverage in Amu] [h/t DataBreaches.net]
IMI cyberattack: UK engineering firm IMI has disclosed a cyberattack that hit its internal network last week. [Additional coverage in Computing UK]
Bohemia Interactive DDoS attacks: Bohemia Interactive says it's making progress in mitigating a wave of DDoS attacks that have targeted the servers of its Arma Reforger and DayZ games for the past two weeks. A Russian hacking group named Style Squad Reborn has taken credit for the attacks in a series of online posts. The group claims it's launching the attacks after the gaming studio has failed to invest in its server infrastructure for over a decade, leading to increased lag for current players. [Additional coverage in The Gamer]

General tech and privacy
Google removes ban on using AI for harm: Google has removed text from its 2018 AI principles page that promised not to use its tools to cause harm to humans, such as surveillance and weapons. [Additional coverage in WIRED]
Chrome 133: Google has released version 133 of its Chrome browser. See here for security patches and webdev-related changes. The biggest changes in this release include the rollout of the option to disable JIT for security reasons to Android devices and the integration of AI in the DevTools feature.
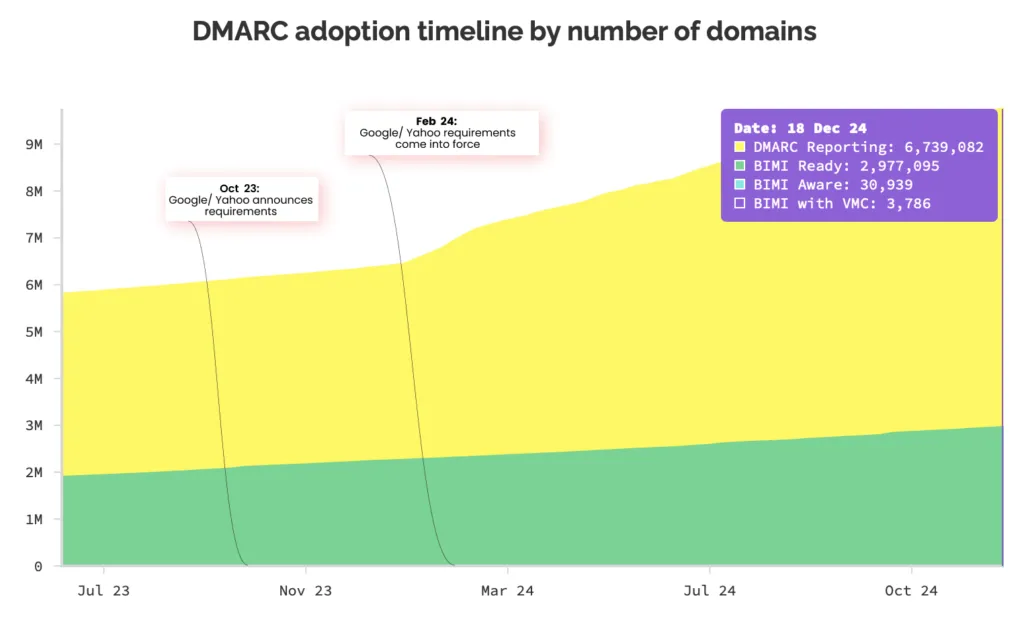
DMARC adoption grows: Email security firm Red Sift says DMARC adoption has almost doubled since Google and Yahoo announced stricter requirements for bulk email senders last year.
Government, politics, and policy
Trump admin extends resignation program to CISA, CIA, NSA: The Trump administration has extended its workforce buyout program to CISA, CIA, and NSA employees. The program allows government workers to retain their pay and benefits until the end of September if they resign this week. The White House has extended the buyout to over two million civilian federal workers. CISA employees were told last week they were exempt from the offer because their work is linked to national security. According to NPR, the Wall Street Journal, and The Record, the White House has changed its mind and is now also purging national security agencies.
DOJ disbands Foreign Influence Task Force: On her first day in office, new US Attorney General Pam Bondi disbanded a Justice Department task force that was tasked with investigating foreign influence operations. The unit was set up in 2017 to counter foreign influence operations targeting US elections. The unit's work contributed to charges and sanctions against many Russian government and private organizations involved in info-ops and bot farms targeting elections in the US around the globe. [Source: Justice Department/PDF]

Unions sue Treasury over DOGE takeover: Multiple worker unions have sued the US Treasury Department over DOGE's unfettered access to the personal data of government workers, their SSNs, tax returns, and other sensitive details. [Additional coverage in The Record]
Australia bans DeepSeek on government devices: The Australian government has banned the use of Chinese AI app DeepSeek on government devices. Officials described the app as an "unacceptable level of security risk to the Australian Government." Australia becomes the second country to ban the use of DeepSeek on government devices after Taiwan.
Paragon cuts off Italy's access to its spyware: Israeli spyware company Paragon has allegedly cut off Italy's access to its platform after reports that the government had targeted journalists and activists. Italian officials have denied the reports, which allegedly targeted vocal critics of the Meloni government. The government says it contacted Meta about the hacking campaign that targeted the WhatsApp accounts of almost 90 people. Meta told the Italian cybersecurity agency that seven of the victims are from Italy, while the the hacks were part of a larger attack that hit 13 other EU countries.
"Belgium, Greece, Latvia, Lithuania, Austria, Cyprus, Czech Republic, Denmark, Germany, the Netherlands, Portugal, Spain and Sweden."
France moves closer to encrypted apps backdoor: According to a paywalled Intelligence Online report, a group of French senators are moving forward with an amendment that would push for backdoors into encrypted messaging apps.
EU investigates French security firm Atos: EU prosecutors have launched an investigation into French IT and cybersecurity group Atos for using its Russian staff to build the EU's new electronic border system. According to the Financial Times, the new system will house the EU's biggest biometrics and personal information database. The European Public Prosecutor's Office is looking at a possible FSB involvement or backdoor into the work of Atos' Russian office.
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Thinkst CTO Marco Slaviero about a concept called Defending off the Land, a way to detect attacks and even deceive and frustrate attackers.
Arrests, cybercrime, and threat intel
Spain arrests hacker: Spain's national police has detained a suspect for allegedly hacking over 40 organizations across the world. Authorities arrested the suspect last week in the city of Calpe, on Spain's Mediterranean coast. Officials say the suspect breached multiple high-level Spanish government agencies, NATO and US Army networks, many private companies, and even several dark web forums. He is also believed to be the prime suspect behind the hack of the UN civil aviation body, ICAO, earlier this year.

Eagle Flush mega trials begin: Nigerian authorities have arraigned two groups of suspects in front of judges for their involvement in a massive online cyber scam operation. A first group was arraigned on Monday, and a second on Tuesday. The suspects were detained in December during Operation Eagle Flush, which saw Nigerian police arrest a whopping 792 suspects who were running online scams from a Lagos seven-story office building.
LEA takedowns in 2024: Intel471 looks at all the cybercrime services taken down by law enforcement agencies in 2024.
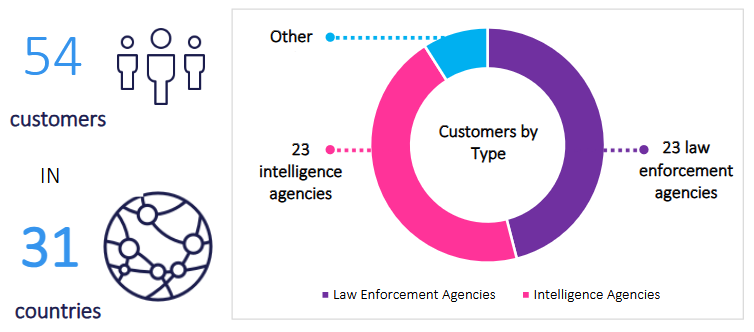
NSO transparency report: Israeli spyware maker NSO Group claims it rejected contracts last year worth over $20 million due to human rights abuse concerns. In its year transparency report [PDF], the company says it currently serves 51 customers in 31 countries. Forty-six of its customers are intelligence or law enforcement agencies. NSO says it received 36 whistleblower complaints about the possible abuse of its tools last year.
UAC-0006 targets PrivatBank: CloudSEK has discovered a new UAC-0006 campaign using SmokeLoader payloads to target Ukraine's largest bank—PrivatBank. The group is known to be a financially motivated threat actor with possible ties to FIN7.
Facebook copyright infringement campaign: Check Point is seeing a massive campaign using Facebook copyright infringement lures to draw users to Facebook credentials phishing sites.
StarkRDP relaunches: StarRDP, an RDP shop seized by law enforcement last week, has relaunched as LaveVPS.
State of cryptominers: Akamai looks at the current state of cryptominer operations and attack volumes. Spoiler alert: They're still going strong!
ScreenConnect abuse continues: SilentPush looks at how threat actors are abusing the ScreenConnect remote management tool for recent operations, such as exploiting bugs in the software and using it for secret backdoor access and data exfiltration.
Babuk loses ransom funds: Threat intel analyst Rakesh Krishnan looks at the funny case of a ransomware gang (Babuk) losing over $20,000 worth of crypto-assets from past ransom payments via an account on Indodax, an Indonesian crypto-exchange that got hacked last September.
FCC fines Telnyx: The US FCC has fined Telnyx $4.5 million for allowing robocallers to place calls posing as the FCC Fraud Prevention Team.
Surge in PTZOptics attacks: Fortinet has seen a surge in attacks targeting PTZOptics cameras.
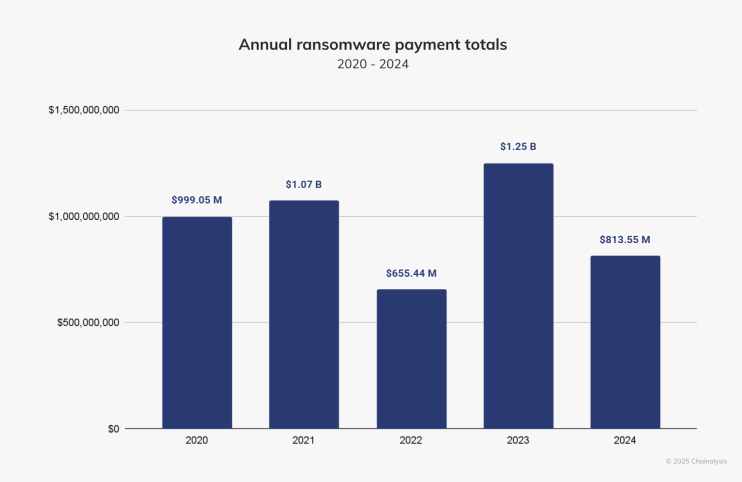
"Bad year" for ransomware gangs: Ransomware gangs pocketed over $814 million worth of cryptocurrency last year, well below the $1.25 billion they made in 2023. Ransomware groups were on pace to break 2023's record year by June, but ransom payments plummeted in the second half of the year. According to Chainalysis, the drop could be attributed to the collapse of big groups such as LockBit and REvil. The smaller numbers may also be linked to the launch of new ransomware operations in the second half of the year, where payment visibility is still limited. Another interesting observation from last year is that ransomware operations have also become faster, with negotiations often starting hours after data exfiltration.
Malware technical reports
BADBOX botnet: Censys has some tips on how to discover BADBOX botnet infrastructure.
LegionLoader: Tehtris researchers look at a recent campaign using the LegionLoader malware, also known as Satacom, CurlyGate, and RobotDropper.
FatBoyPanel: Zimperium has a report out on FatBoyPanel, a new banking trojan targeting Indian banks and audiences.
Abyss Locker ransomware: Sygnia researchers have published a report looking at the anatomy of an Abyss Locker ransomware attack.
Sponsor section
In this Soap Box edition of the podcast, Patrick Gray chats with Thinkst Canary founder Haroon Meer about his "decade of deception."
APTs, cyber-espionage, and info-ops
Sichuan Silence didn't pay employees, for a while: A Natto Thoughts investigation has discovered that the Chinese cyber contractor that hacked over 80,000 Sophos firewalls in 2020 entered a period of financial difficulties shortly after the hacking campaign. Sichuan Silence filed for bankruptcy on December 25 last year, two weeks after the US sanctioned the company and one of its employees. Chinese court documents reveal that the sanctioned employee filed a labor dispute against the company in July 2020. The lawsuit was filed in the same month that other Sichuan Silence employees reported the company to the local provincial government that they had gone three months without pay.
Chinese info-op targeting Japan: Japanese security researcher SttyK has spotted a Chinese info-op targeting Myanmar with anti-Japanese sentiments.
Kimsuky: AhnLab has published a report on a Kimsuky campaign leveraging the PebbleDash backdoor and a custom-made RDP wrapper.
APT37: Genians researchers look at an APT37 (Reaper) campaign distributing malicious LNK files via online chat and IM apps.
Lazarus campaign: Bitdefender looks at an active social engineering and phishing campaign from the North Korea-linked Lazarus Group targeting organizations through fake LinkedIn job offers.
Vulnerabilities, security research, and bug bounty
Nextcloud 2FA bypasses: Germany's cybersecurity agency has discovered multiple vulnerabilities in the Nextcloud cloud file syncing and sharing platform that can be used to bypass 2FA security systems. The vulnerabilities are just one of the many issues the agency has discovered following a recent security audit. The BSI has recently conducted security audits of multiple open-source projects, such as KeePass, Bitwarden, and Vaultwarden. All Nextcloud issues have been patched.
OpenAI jailbreak: CyberArk claims it used an internal AI fuzzing tool to jailbreak OpenAI's O3 model.
Cisco security updates: Cisco has released or updated eight security advisories for various products.
F5 security updates: Cisco has released or updated 13 security advisories for various products.
KEV update: CISA has updated its KEV database (twice) with six vulnerabilities that are currently exploited in the wild. This includes a Linux kernel bug from 2024, a recent 7-Zip zero-day exploited by Russian hackers, the MonikerLink Outlook exploit, a 2022 vulnerability in Dante Discovery, and two 2020 bugs in CyberoamOS and the Sophos XG firewall.
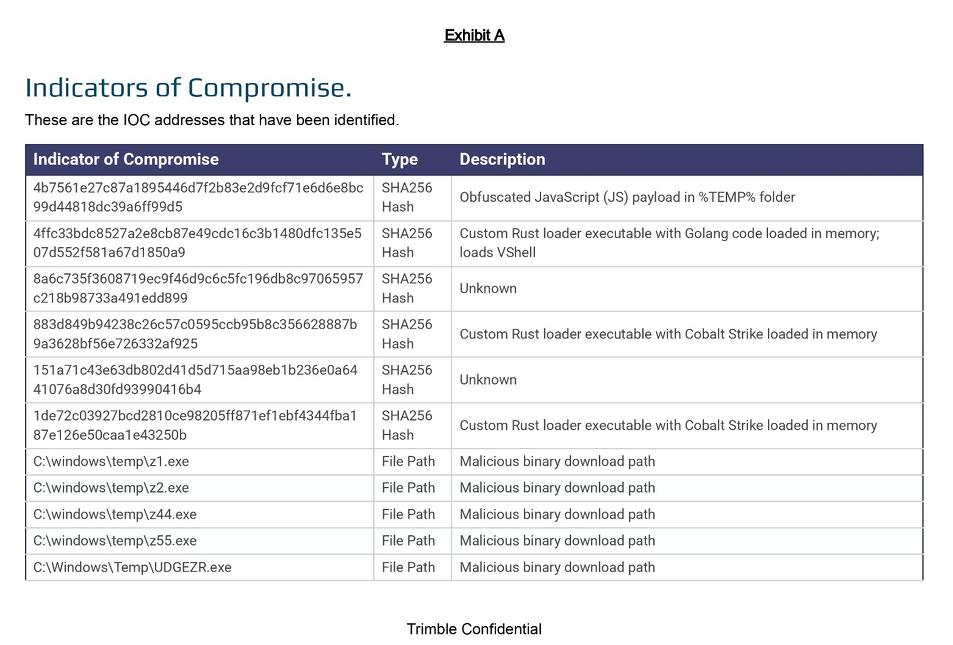
Trimble zero-day: Hackers are exploiting a zero-day vulnerability in Trimble CityWorks, a platform for managing remote assets. According to CISA, the platform is used in the US for managing water and wasterwater systems. The zero-day (CVE-2025-0994) is an untrusted deserialization vulnerability that can lead to remote code execution and allow hackers to take over the platforms. Trimble says the vulnerability has been used to deploy Cobalt Strike implants and a custom Rust malware on CityWorks servers.
Infosec industry
Threat/trend reports: Chainalysis, CyFirma, Gen Digital, LatticeFlow, Malwarebytes, PortSwigger, ReturnOnSecurity, and Sygnia have published reports and summaries covering various infosec trends and industry threats.
Infosec salaries: The global infosec salary index for 2025 is out.
New tool—RansomWhen: Cloud security firm Permiso has open-sourced RansomWhen, a tool to enumerate cloud identities that can lock S3 buckets, resulting in possible ransomware attacks.
New tool—soxy: The Airbus security team has released soxy, a modular debug tool to interact with several VDIs that operate over RDP, such as VMware Horizon, Citrix, and native Windows RDP.
New tool—RDBye: NexusFuzzy has released RDBye, a tool to shut down servers exposing their RDP interface on the internet.
Black Hat USA 2024 videos: Videos from the Black Hat USA 2024 security conference, which took place in August, are available on YouTube (finally).
Risky Business Podcasts
In this podcast, Tom Uren and Patrick Gray talk about the cyber espionage implications of Chinese AI firm DeepSeek's recently released models. They will certainly be picked up by various APT crews to try and accelerate their campaigns.
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about the evolution of Russian cyber operations during its invasion of Ukraine.




