Risky Bulletin: Scattered Spider goes after aviation sector
In other news: Russia throttles Cloudflare traffic; Mexican cartel hired hackers to track FBI official; Canada tells Hikvision to cease operations.

This newsletter is brought to you by Sandfly Security. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
Individuals associated with a large cluster of hackers known as Scattered Spider (Muddled Libra, UNC3944) are targeting companies in the aviation and transportation sectors.
The group, which was previously very active in 2023 and had some members arrested in 2024, saw a resurgence in activity this year.
It returned with a bang with attacks that targeted UK retail chains, moved to go after US retailers, and then targeted US insurance businesses before a new change in targets this month.
Google, Palo Alto Networks, and the FBI have put out public statements on Friday warning about the group's new shift towards aviation.
The three warnings come after WestJet and Hawaiian Airlines disclosed breaches this month. Reports from Axios and Bleeping Computer claim the two companies were hit by the group.
Scattered Spider's hacking spree this year also included intrusions at UK retail chains Mark & Spencers and Co-op. While still unconfirmed, three insurance companies—Aflac, Eerie Insurance, and Philadelphia Insurance—also disclosed security breaches shortly after reports that the group shifted to target their industry vertical.
"Scattered Spider has a history of focusing on sectors for a few weeks at a time before expanding their targeting," Charles Carmakal, Google Mandiant CTO, wrote on LinkedIn. Carmakal urged companies to read guidance on the group's normal TTPs and take preemptive measures.
"The actor's core tactics, techniques, and procedures have remained consistent. This means that organizations can take proactive steps like training their help desk staff to enforce robust identity verification processes and deploying phishing-resistant MFA to defend against these intrusions," Carmakal told Risky Business.
"We are still working on attribution and analysis, but given the habit of this actor to focus on a single sector we suggest that the industry take steps immediately to harden systems," he added.
When it comes to these TTPs, the group is widely known for the use of extremely clever social engineering techniques and its ability to move across cloud and SaaS environments with greater ease than many other threat actors.
They typically use public or leaked/hacked data to pose as employees, contact a company's tech support or IT help desk, and then trick support staff into resetting that employee's account passwords to bypass existing MFA protections.
They then use this account to move laterally across corporate accounts and apps, steal data, and even deploy ransomware when they can. In the next stage, the group uses the stolen data and the encrypted files to extort the companies for multi-million dollar ransoms. Their attacks are typically very thorough and devastating. Many of its victims encountered prolonged multi-week outages, which is why they demand so much money from victims they put on their knees.
These are basically the same techniques they've been using in 2023, although these new intrusions are carried out by a new batch of "members."
We used the quotes here because, technically speaking, you can't call the people behind these newer attacks "Scattered Spider members."
The term Scattered Spider is very generously used to describe individuals who learned the same hacking techniques from an underground Discord and Telegram community known as The Com.
There are hundreds of these individuals who are organized in their own smaller cliques, sometimes jump between them, and even merc out their hacking services on specific intrusions to other groups.
It's a stupid name, but it can't be helped since it's difficult tracking such a flowy and mercurial bunch of people.
Risky Business Podcasts
The main Risky Business podcast is now on YouTube with video versions of our recent episodes. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
Hawaiian Airlines cyberattack: A cyberattack has disrupted the internal IT systems of Hawaiian Airlines. The airline says the incident didn't impact flight schedules. Hawaiian didn't provide details about the incident, but the aftermath is typical of ransomware attacks.
Resupply crypto-heist: Hackers exploited a vulnerability in the Resupply DeFi platform to steal $10 million worth of crypto assets. The bug allowed the attackers to place a $200,000 deposit but extract millions in return. The hackers used the Tornado Cash mixer to deposit the funds, and their identity remains unknown.
Société Générale intern linked to SIM swaps: A cybercrime group has stolen more than €1 million from 50 customers of French bank Société Générale. The group used customer data provided by a bank intern to access and empty customer accounts. The group had four members—one man who created forged documents, one individual conducting SIM swaps, and a couple who laundered the stolen funds. All five were arrested earlier this month. [Additional coverage in CommRisk]
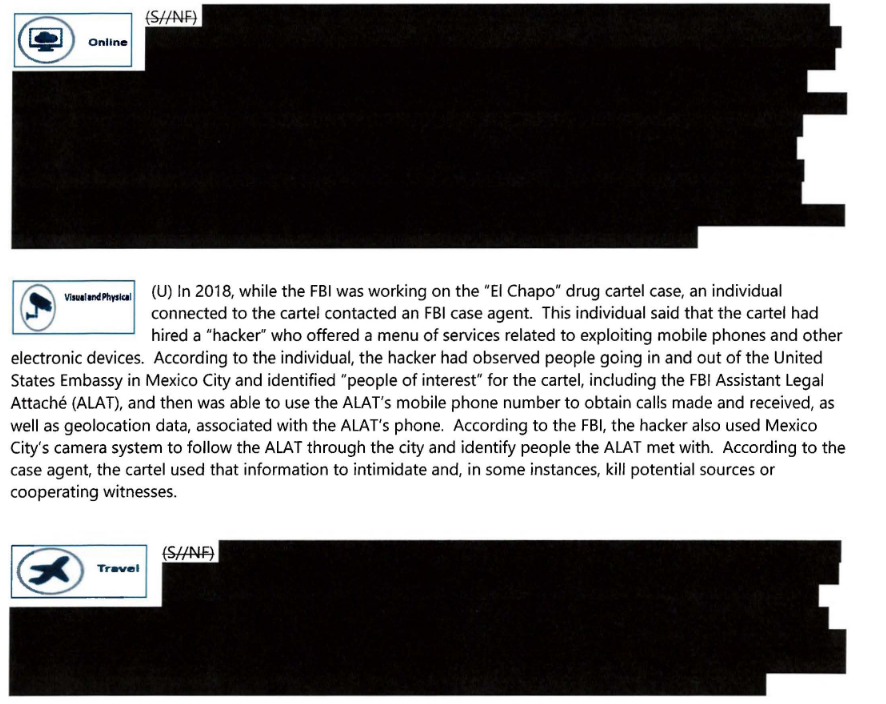
Mexican cartel hired a hacker: The Sinaloa drug cartel hired a hacker in 2018 to track an FBI official's phone. The hacker obtained call records and geolocation data and tracked the agent's movements across Mexico City. The cartel used the data to identify and even kill informants in a case against the cartel's leader, Joaquín "El Chapo" Guzmán. [Additional coverage in CyberScoop/FBI OIG audit/PDF]
It's almost like surveillance capitalism is a problem for *everyone*
— Ian Campbell (@neurovagrant.bsky.social) 2025-06-28T20:43:36.295Z
General tech and privacy
Azure AD Graph retirement: A reminder that Microsoft is retiring the Azure AD Graph API service in September.
Microsoft to launch new endpoint security platform: Microsoft will launch next month a private preview of a new Windows technology that will allow antivirus and security tools to run without kernel access. The new endpoint security platform was developed in response to last year's CrowdStrike incident. A bug in the CrowdStrike kernel driver took down over 8.5 million Windows systems. Several EDR vendors are working with Microsoft to test the new technology.
New Chrome anti-XSS security feature: Google has added a new security feature to the Chrome browser that automatically escapes "<" and ">" characters inside HTML attributes. The new feature is designed to prevent cross-site scripting attacks that rely on sneaking malicious code inside HTML. The feature shipped with Chrome 138 last week.
New Meta intrusive AI training: Meta is asking users for access to their camera roll to use AI and suggest photos to share. As TechCrunch points out, this is the company's clever way of training its AI on private photos.
This is the most insane thing Meta has done… this year… so far… except when they tracked browser activities for users who weren’t even logged in, violating Google Play’s terms of service. techcrunch.com/2025/06/27/f... #Privacy #Meta
— Karl Emil Nikka (@karlemilnikka.nikkasystems.com) 2025-06-28T14:27:43.649Z
Government, politics, and policy
New US Cyber Command Executive Director: The US government has named Patrick Ware as the new Executive Director of US Cyber Command. Ware will occupy the No. 3 spot inside the US military's cyber operations branch, a spot typically assigned to an NSA official. Ware previously served 34 years with the NSA and replaces Morgan Adamski in the role. [Additional coverage in The Record]
No Adversarial AI Act: Two US senators have introduced a bill that would ban the US federal agencies from using AI tools developed by foreign adversaries. This would apply to AI technologies produced in China, Russia, Iran, and other countries the US considers adversaries. The No Adversarial AI Act comes after several agencies and US States banned employees from using Chinese AI tool DeepSeek.
Supreme Court upholds porn ID law: The US Supreme Court on Friday ruled in favor of a Texas law mandating adult sites to verify the age of their visitors. [Additional coverage in Wired]
Proposed CISA cuts: Ongoing negotiations and adjustments to DHS budgets for the next year seem to have softened CISA workforce and budget cuts. Still ongoing. [Additional coverage in Federal News Network]
NASA needs cyber risk management: A GAO report found that NASA is lagging behind in implementing an organization-wide cybersecurity risk assessment framework.
Canada tells Hikvision to get out: The Canadian government has ordered Chinese security camera maker Hikvision to close operations in the country. Officials said the company's business is a threat to Canada's national security and banned government agencies from purchasing new Hikvision products. The US previously sanctioned the company for helping the Chinese government surveil the Uyghur minority in Western China. [Additional coverage in CBC]
KYC for Dutch hosting providers: The Dutch government is exploring implementing a Know-Your-Customer requirement for Dutch web hosting providers.
Germany looks to ban DeepSeek: Berlin's data protection agency is seeking to ban DeepSeek in Germany for illegal user data transfer to China. The agency says it reported both apps to the Apple and Google app stores last week for GDPR violations. According to CNBC, an initial action in Germany may lead to an EU-wide ban.
Brazil supreme court ruling to impact online moderation: Brazil's Supreme Court has ruled that social media networks are liable for their users' posts. Online social networks will have to monitor and remove user posts that contain hate speech, racism, and calls for violence. The Trump administration previously threatened to sanction any foreign officials going after US tech firms using fines, taxes, or content moderation attempts. [Additional coverage in Rest of World]
Russia throttles Cloudflare: Russian internet service providers are throttling traffic to Cloudflare sites. Throttling began on June 9, and Cloudflare says it has not received a formal outreach from the Russian government. The throttling is a de-facto block, as ISPs are only allowing 16 KB of data to load from Cloudflare before freezing the connection. In February, the Kremlin also used traffic throttling to block YouTube inside the country.
Sponsor section
In this Risky Bulletin sponsor interview Craig Rowland, CEO of Sandfly Security, talks to Tom Uren about the disconnect between how important Linux systems are and how much security attention they get. The pair discuss the variety of reasons that security teams underinvest in protecting Linux.
Arrests, cybercrime, and threat intel
CryLock couple gets prison time: Belgian authorities have sentenced a Russian man to seven years in prison for developing the CryLock ransomware. A Russian woman also received a five-year prison sentence for advertising the ransomware and negotiating with victims. Both received two years on their sentence for refusing to cooperate with authorities and hand over passwords for their devices and crypto wallets. The couple is believed to have infected more than 400,000 users and made over €3 million from the attacks. The two were detained in Spain in 2023 and extradited to Belgium to face trial. [Additional coverage in VRT]
IT worker jailed over cyberattack: A UK judge has sentenced a 31-year-old man to more than seven months in prison for hacking and sabotaging his former employer. A day after being suspended from work, Mohammed Umar Taj changed login credentials and multi-factor authentication settings. The sabotage caused IT outages for the company's customers across the UK, Germany, and Bahrain. The incident led to at least £200,000 in lost business and reputational damage.
New npm malware: Seventy-five malicious npm packages were discovered and taken down last week. Check out the GitHub security advisory portal for more details.
FBI warns of healthcare scams: The FBI has warned Americans of cybercriminals cold-calling victims, impersonating healthcare providers, and asking for private details and payments.
ConnectWise's signing boo-boo: River CISO Cem Paya has published a technical deep dive into ConnectWise's technical snafu of storing way too much technical data in an area of its installer that was not signed. This allowed threat actors to abuse this area to load malware via official ConnectWise ScreenConnect installers. Paya is one of the many security researchers who looked at this, mainly because the threat actors impersonated his employer.
New Werewolves Group attacks: Russian security firm F6 is seeing new attacks from the Werewolves Group, a double-extortion group targeting Russian companies with a version of the LockBit leaked ransomware.
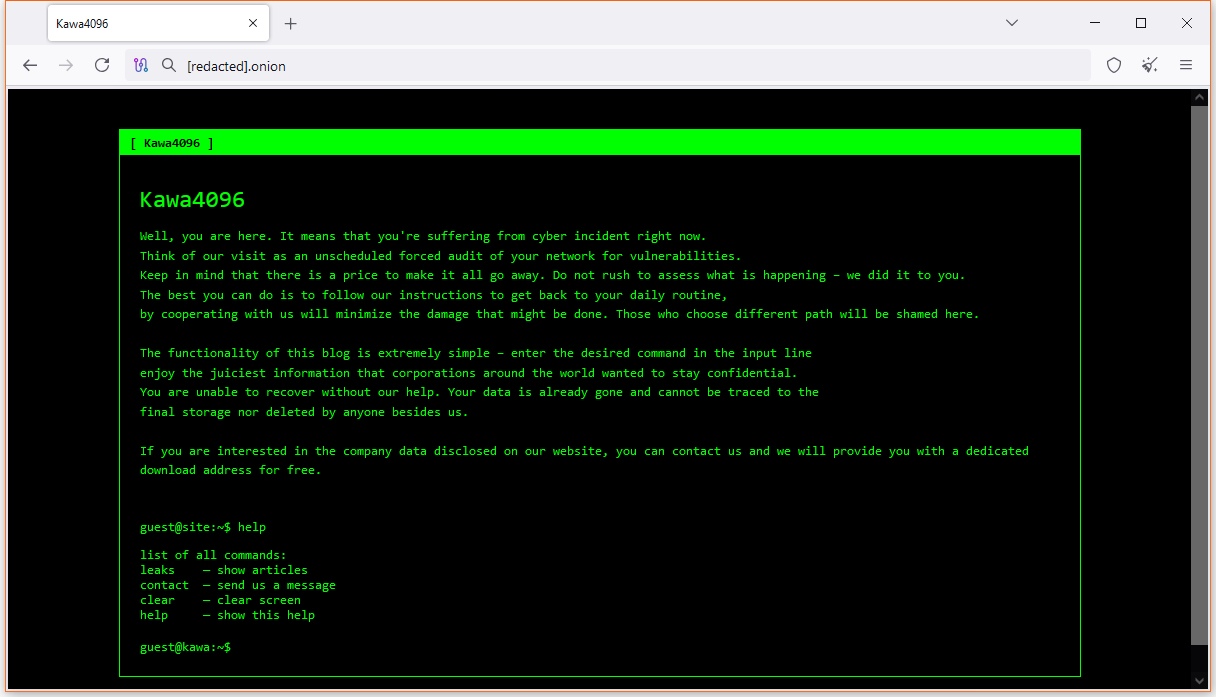
New Kawa ransomware gang: A new ransomware operation named Kawa launched last week. Its dark web leak site currently lists five victims.
Israel-Iran "cyber war": NSFOCUS and Tenable published overviews of recent hacking and hacktivist activity linked to the military conflict between Iran and Israel.
Cybercrime in Africa: Cybercrime reports account for more than 30% of all reported crimes in Western and Eastern Africa, according to an Interpol report. Online scams, ransomware, BEC, and digital sextortion are the most common incidents. Most African countries said their legal systems are not prepared to handle the scale of the new problem.
Cambodia's cyber scam ecosystem: Amnesty International published a report on the cyber scam ecosystem in Cambodia, alluding that the local government is deliberately ignoring the problem. This is most likely because some officials are making a fortune off these compounds, as other previous reports have hinted.
"Under international human rights law, the Cambodian state has a duty to ensure that no one is held in slavery or servitude or required to perform forced labour. It is obligated to protect children from economic exploitation and must prevent, prohibit, investigate and prosecute acts of torture. The Cambodian government must also effectively investigate, prosecute and adjudicate trafficking whether committed by governmental or non-state actors; it must identify trafficking victims and provide remedy; and it must implement measures to ensure that 'rescue' operations of trafficked persons do not further harm their rights and dignity."
Terrorgram named terrorist organization: The Australian government has designated the Terrorgram online community a terrorist organization. The group operates on Telegram, where it recruits and encourages members to carry out murders, physical attacks, and other hate crimes. The US arrested two Terrorgram admins last year after shootings and stabbings in Slovakia and Turkey. Australia previously sanctioned the group's members in February.
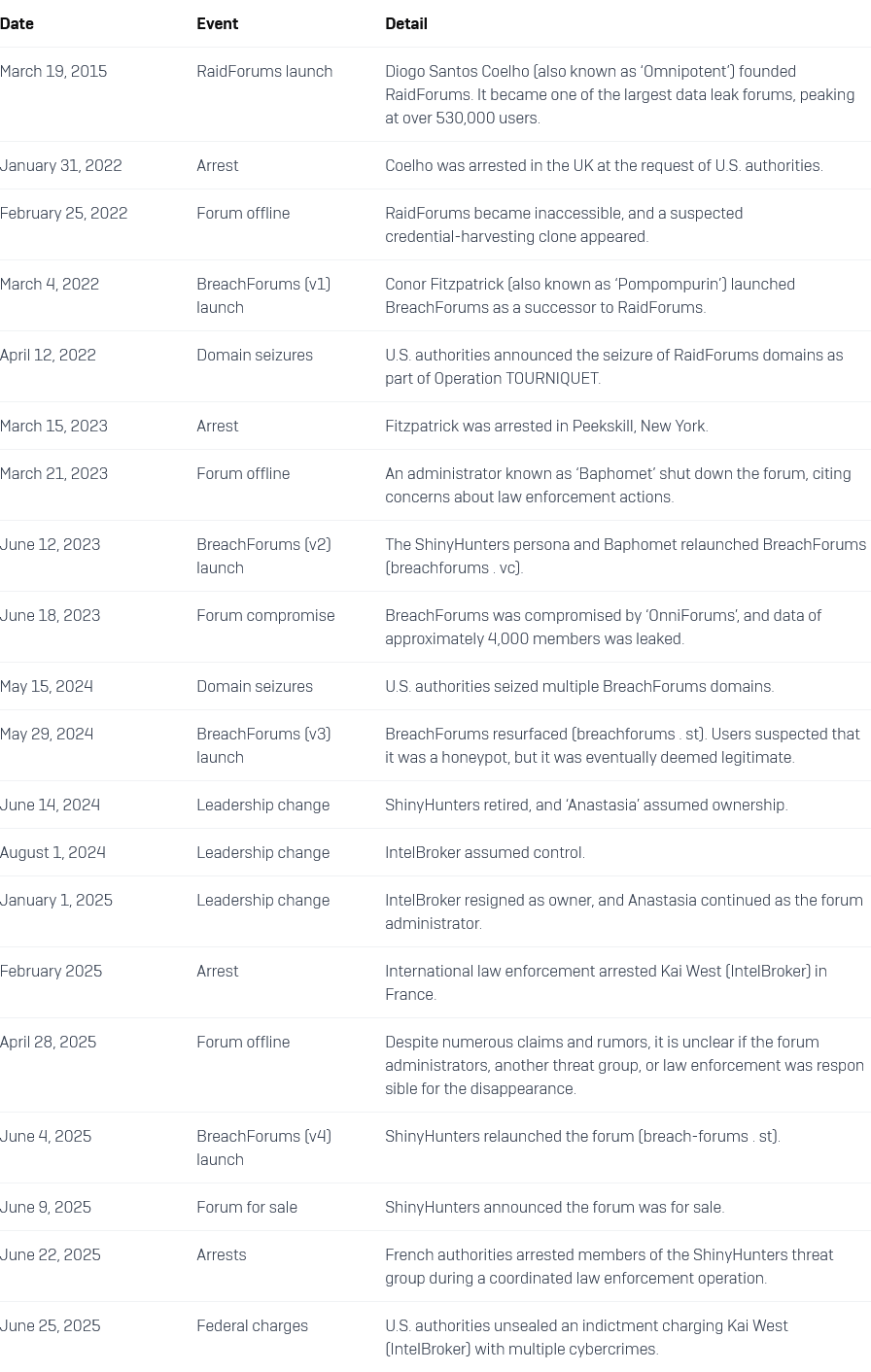
BreachForums profile: Sophos has published a profile and timeline of BreachForums, the rebranded version of the old RaidForums. This doesn't include the millions of clones.
Malware technical reports
Snake Keylogger: Lab52 has spotted the Snake Keylogger being used in an oil industry-centered spear-phishing campaign.
Sponsor section
Sandfly Security can help you find Linux packet-sniffing malware instantly and at scale. You can get a free trial and know immediately if any suspicious processes are sniffing traffic today.

APTs, cyber-espionage, and info-ops
Blind Eagle linked to Proton66: Trustwave has linked campaigns from LATAM APT Blind Eagle to the infrastructure of Russian bulletproof hosting provider Proton66.
DPRK hackers abuse ChatGPT: North Korean hacking groups are abusing ChatGPT to automate OSINT, reconnaissance operations, and cryptocurrency thefts. Hackers linked with the Andariel and Kimsuky groups have used ChatGPT to generate malicious code that automatically empties crypto-wallets. They also used ChatGPT to analyze public data to find targets for attacks. South Korean officials found traces of this activity on 39 servers they seized last year. [Additional coverage in TechM/English coverage in CoinTelegraph]
UAC-0226's GIFTEDCROOK updates: Arctic Wolf has published a report detailing new updates to GIFTEDCROOK, an infostealer used by Russian espionage group UAC-0226 in Ukrainian operations. Arctic Wolf says the malware evolved from a browser stealer to a full-blown data exfiltration platform.
Pravda Catalan: The Open Measures team looks at the Catalan branch of Russian disinformation network Pravda.
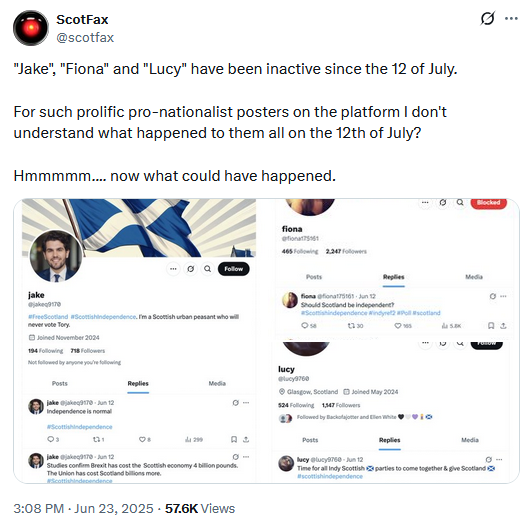
Iranian info-op goes silent during Israeli strikes: An investigation by the UK Defence Journal found that dozens of pro-Scottish independence accounts went silent at the start of Israel's military operation in Iran. The accounts remained silent for over 10 days while Iran imposed an internet blackout, and the country dealt with power outages from Israeli strikes. Iran is known to run influence operations in multiple foreign countries, where it blends local political themes with its own foreign interests, such as pro-Hamas and anti-Israel narratives.
Vulnerabilities, security research, and bug bounty
CitrixBleed 2 exploitation: Security firm ReliaQuest has spotted evidence that hackers are likely exploiting a new Citrix vulnerability known as CitrixBleed 2. Tracked as CVE-2025-5777, the vulnerability is a memory corruption issue that allows remote attackers to dump a Citrix device's memory. The exploit can be used to steal session data and impersonate users. Citrix has not confirmed the attacks and ReliaQuest's findings.
CentOS Web Panel RCE: The CentOS Web Panel project has fixed a vulnerability that could have allowed threat actors to hijack web hosting servers. Tracked as CVE-2025-48703, the vulnerability allows attackers who know at least one username on the panel to take over the underlying servers. The attack bypasses authentication, and proof-of-concept code is available online.
SAP GUI Client vulnerabilities: Security firm Pathlock has published a write-up on two bugs it found in the SAP GUI Client.
Synology app leak: A leaked secret in a Synology Microsoft 365 app could have allowed threat actors to access the Azure cloud data of any of the app's users.
Teammate Leonid discovered a leaked credential that allowed anyone unauthorized access to all Microsoft tenants of orgs that use Synology's "Active Backup for Microsoft 365" (ABM), including sensitive data like Teams channel messages. 🤓 #synology #disclosure #modzero modzero.com/en/blog/when...
— modzero (@modzero.bsky.social) 2025-06-29T08:01:00.166Z
Infosec industry
Threat/trend reports: Bitdefender, ESET, GitHub, GuidePoint, and Interpol have recently published reports and summaries covering various infosec trends and industry threats.
NIS2 guidance: ENISA has published new guidance to support the implementation of the EU NIS2 Directive.
New tool—RIFT: Microsoft has open-sourced RIFT, or the Rust Interactive Function Tool, a toolkit to assist reverse engineers in identifying library code in Rust malware. The code is also on GitHub.
New tool—Orange Me2eets: Cloudflare has open-sourced Orange Me2eets, a new demo app to support end-to-end encrypted video calling. The app's code is also on GitHub.
BSides Seattle 2025 videos: Talks from the BSides Seattle 2025 security conference, which took place in April, are available on YouTube.
BSides Tampa 2025 videos: Talks from the BSides Tampa 2025 security conference, which took place in May, are available on YouTube.
Nullcon Goa 2025 videos: Talks from the Nullcon Goa 2025 security conference, which took place at the start of March, are available on YouTube.
Risky Business podcasts
In this edition of Seriously Risky Business, Tom Uren and Patrick Gray talk about a new report that compares Chinese and American 0-day pipelines. The US is narrowly focused on acquiring exquisitely stealthy and reliable exploits, while China casts a far broader net. That was fine in the past, but as 0-days get harder and harder to find, the report argues that the US needs to change the way it goes about getting them.
In this edition of Between Two Nerds, Tom Uren and The Grugq dive into the motivations and actions of Predatory Sparrow, a purported hacktivist group that has been attacking Iran for the last five years and has leaped into the Iran-Israel work.




