Risky Bulletin: Scam compound operators sentenced to death in China
In other news: UK makes new request for Apple user data; APT35 has another leak; Microsoft launches a Security Store.

This newsletter is brought to you by Authentik. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
China has sentenced 11 individuals to death for their role in running cyber scam compounds in Myanmar.
Five other individuals received suspended death sentences for two years, 11 others received life sentences, and 12 more got prison terms ranging from five to 24 years.
The suspects were members of the infamous Ming crime family. They were arrested in November of 2023, when the Chinese government first started seriously cracking down on scam compounds targeting its citizens.
The Ming family ran some of the largest scam operations at the time, operating primarily out of the Kokang region of Myanmar, near the Chinese border.
They ran prison-like compounds where individuals who were trafficked or tricked into signing contracts had to engage in unlicensed gambling and online scams designed to trick victims into handing over their funds or crypto-assets.
According to court documents, the compounds made the Ming family at least $1.4 billion between 2015 and 2023, when the compounds were raided in a joint Burmese and Chinese operation.
Chinese judges said the group operated like an "armed force" in the region and often used torture and beatings to prevent their workers from leaving.
Authorities said at least ten workers died and two more suffered serious injuries after they were beaten when they tried to leave. According to GlobalTimes, four others died and four more were injured when members of the Ming family opened fire on a group of workers while trying to move them and hide them from Myanmar authorities.
The Ming family syndicate killed or injured individuals involved in fraud who attempted to escape or resisted control, resulting in 10 deaths and 2 injuries. 3/4
— Cyber Scam Monitor (@cyberscammonitor.bsky.social) 2025-09-29T12:38:53.090Z
According to reports in Burmese media, the Ming family worked closely and had protection from the local Kokang Border Guard Force, some of whom were also detained and extradited to China.
Burmese and Chinese officials freed thousands of workers from Ming family compounds. Beijing later also ramped up diplomatic pressure on the Golden Triangle nations to crack down on scam compounds operating within their borders.
A UN report warned that hundreds of thousands were trapped and forced to work in scam compounds across Southeast Asia. A subsequent report also warned that these types of forced-labor scam compounds were spreading across Africa and the Middle East.
Risky Business Podcasts
The main Risky Business podcast is now on YouTube with video versions of our recent episodes. Pat's away on leave, so Amberleigh and Adam did their own show!
Breaches, hacks, and security incidents
Motility breach: Dealer management software (DMS) provider Motility has disclosed a data breach related to a ransomware attack. The incident impacted over 766,000 users, which is likely to trigger a class-action lawsuit.
Qantas gets permanent injunction: Australian airline Qantas has obtained a permanent injunction to prevent the use of data stolen in a recent ransomware attack. The airline obtained a temporary injunction in July, which has now been made permanent by the NSW Supreme Court. The court order prevents third parties from publishing, viewing, or accessing the data if it is released by the attackers. Almost 6 million customer details were stolen from the company in a security breach in June.
Adobe Analytics leak: A bug accidentally exposed the data of Adobe Analytics customers. Adobe says some user data appeared in other customers' backends. The company traced the bug to a recent change designed to improve performance.
SBI Crypto hacked for $21 million: Hackers have stolen $21 million worth of crypto assets from SBI Crypto at the end of September. The stolen funds were almost immediately taken and laundered through the Tornado Cash service. According to blockchain investigators, the hack exhibits the characteristics of a North Korean intrusion. [Additional coverage in CoinMarketCap]
Griffin AI token heist: Hackers breached Griffin AI, minted, and then dumped $2.93 million of the company's crypto token. [Additional coverage in ICO Bench]
Red Hat got extorted: A hacking group named the Crimson Collective has breached and stolen sensitive customer data from software giant Red Hat. The hack took place two weeks ago, and the data was stolen from the company's private Git repositories. The data allegedly includes information on the internal networks of almost 800 customers. The group tried extorting Red Hat, but the company did not respond. [Additional coverage in Bleeping Computer]
Judging by what they are posting on Telegram, Crimson Collective expected a quick and easy payout from Red Hat, while Red Hat floundered and panicked about how to respond and essentially left them hanging in the wind. www.bleepingcomputer.com/news/securit...
— realhackhistory.org (@bsky.realhackhistory.org) 2025-10-02T11:32:34.876Z
They were literally emailing the generic support address, lol. They tried going to InfoSec via that too, unsurprisingly they didn’t know what to do.
— Kevin Beaumont (@doublepulsar.com) 2025-10-02T12:12:10.890Z
General tech and privacy
Brave MAUs: The Brave browser says it now has more than 100 million active users.
Accenture to cut 11,000: Consulting giant Accenture will lay off more than 11,000 employees as the company pushes for broader adoption. Accenture CEO Julie Sweet said the company plans to fire other employees who cannot be trained to use AI tools for their work. [Additional coverage in CX Today]
Signal threatens to leave EU: The Signal secure instant messaging app will leave the EU if the bloc passes its Chat Control legislation. Signal President Meredith Whittaker has made similar threats when authorities in France, Sweden, and the UK considered similar encryption backdoor laws. EU officials are set to vote on the EU Chat Control proposal on October 14. Twelve of the bloc's 27 members are publicly backing the proposal, with eight against, and the rest undecided. [Additional coverage in Taggeschau]
Microsoft Security Store: Microsoft has launched a dedicated store for Azure security products. The new Microsoft Security Store will host SaaS security solutions and AI agents that integrate with Microsoft security products.
Outlook blocks inline SVGs: Microsoft will block the display of inline SVG images in Outlook for Web and Outlook for Windows. The decision comes after SVG files saw a huge adoption this year by cybercrime operations. The change came into effect this month. Microsoft says it will only impact under 0.1% of all images loaded in Outlook.
Windows bi-annual release: The fall update to Windows OS is now live with the release of Windows 11 25H2.
Chrome 141: Google has released version 141 of its Chrome browser. See here for security patches and webdev-related changes. The biggest change in this release is initial support for the Digital Credentials API, a new system to let Chrome mobile request information from wallet apps in a secure manner. There's also a new JavaScript-based Proofreader API that uses AI for text corrections. Chrome also has a new security feature that detects when malicious extensions are intercept and hijacking search queries via the address bar. The previous Site Isolation feature that blocked CPU side-channel attacks has been morphed into Origin Isolation, which now groups a site's resources even more tighter together than before.
Gmail POP change: Starting next year, Gmail will no longer support checking emails from third-party accounts through POP.
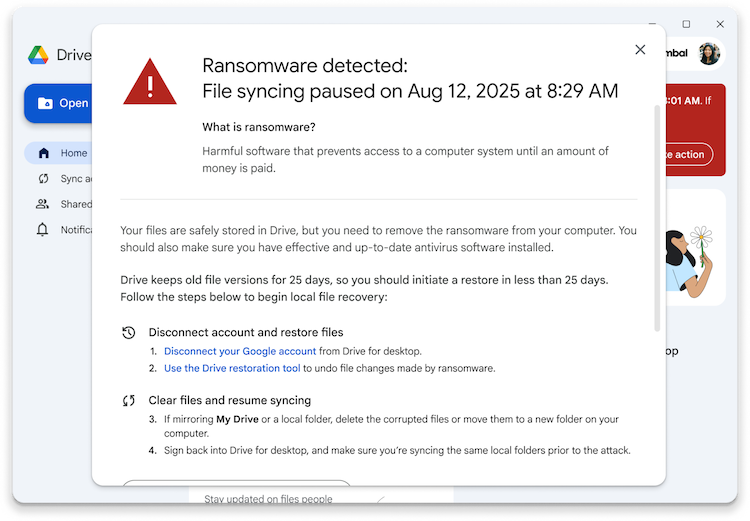
Google Drive gets ransomware protection: Google has added a new feature to its Drive app to detect and counter ransomware attacks. The app will use AI to detect ransomware encryption operations and stop file syncing before files are damaged on the server side. Users will also have the ability to restore affected files.
Government, politics, and policy
Sen. Cruz blocks privacy protection law: Texas Senator Ted Cruz has blocked an effort to pass increased privacy protections for Americans. The Protecting Americans from Doxing and Political Violence Act would have extended privacy protections currently available to US lawmakers to every American. Under the new law, data brokers would have been prohibited from selling certain types of personal data belonging to Americans. According to TechCrunch, Sen. Cruz was the only vote against.
UK tries to access Apple data again: The UK government has made a new attempt to access the encrypted cloud user data of Apple customers. The government sent a new request to Apple in September after a previous failed attempt in January. According to the Financial Times, the new request is narrower in scope and seeks access to the encrypted cloud data of UK citizens only. The previous January request wanted access to all Apple user cloud data.
Geopolitics aside, the technical mess that implementing geographical backdoors that dont weaken the overall system, gives me the shivers www.ft.com/content/d101... To be a fly on the wall when the advisors try and explain how this would work. So there’s Alice and bob and then Peter, in the corner
— Daniel Cuthbert (@dcuthbert.bsky.social) 2025-10-02T09:05:56.573Z
Recovery is hard for UK schools: UK schools and colleges have made progress in cybersecurity training, but they are still struggling to recover from cyberattacks. Almost three-quarters of UK teachers receive cybersecurity training, according to the UK's education watchdog office. Despite this, once a school gets hit, only 55% are able to recover immediately.
EU MPs angry over spyware funding: A group of EU MPs has sent a letter to the European Union raising concerns that some member states have provided financial aid to spyware companies. At least four companies received EU subsidies or other funding. The hidden financing came to light after several news reports last month. [Additional coverage in The Record]
🚨 The 🇪🇺 European Investment Fund (EIF), provided venture capital for Israeli #spyware firm Paragon Solutions, confirmed a spokesperson for the European Investment Bank Group, to which the EIF belongs, @apache.be is reporting. apache.be/2025/10/01/e...
— Vas Panagiotopoulos (@vaspanagiotopoulos.com) 2025-10-01T08:25:07.657Z
Sponsor section
In this Risky Business sponsor interview, Authentik CEO Fletcher Heisler talks to Tom Uren about how identity providers (IdP) are fundamental to everything an organisation does. He explains how organisations are making themselves resilient by managing their redundancy and failover options.
Arrests, cybercrime, and threat intel
Oracle extortion campaign: The Clop extortion group is emailing Oracle customers demanding ransom payments. The group says they have the victim data, which they allegedly stole from their E-Business Suite platform. Hundreds of emails have been sent, according to Google, but no breaches have been confirmed so far. [Additional coverage in CyberScoop]
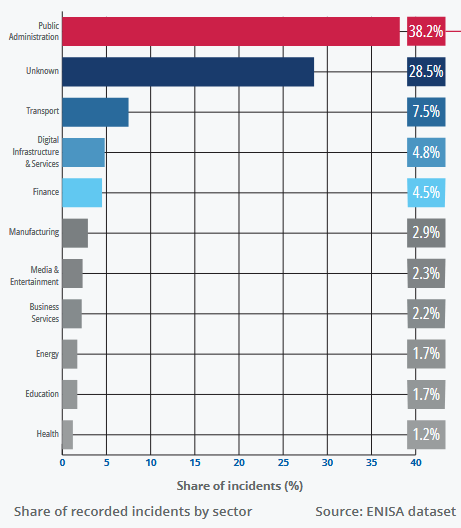
Most EU cyberattacks were DDoS attacks: Almost two-thirds of cyberattacks reported in the EU were DDoS attacks carried out by the Russian hacktivist group NoName057. The EU's cybersecurity agency ENISA says almost 80% of all cyberattacks over the past year have been ideology-driven and related to political events. Russian groups were the most active in both the cyber-espionage and the disinformation categories.
US govt shutdown scams: Michigan's Attorney General warns that threat actors will likely attempt to use the current US government shutdown to scam consumers or trick them into running malware.
NIST portable storage guidance: US NIST has released guidance on how organizations could reduce the risks of portable media to OT networks. Mediums like CDs, DVDs, and USB drives have been known to carry USB worms and other malware inside segregated OT networks.
Duo OTP campaign: Abnormal AI has spotted a campaign trying to steal Duo OTP codes from people working in the educational sector. The company says it identified more than 40 compromised organizations and over 30 universities and colleges targeted in this campaign.
Malicious PyPI package: JFrog's security team has spotted another malicious Python package that offers to help create SOCKS5 proxies, but actually behaves like a backdoor proxy to a developer's system.
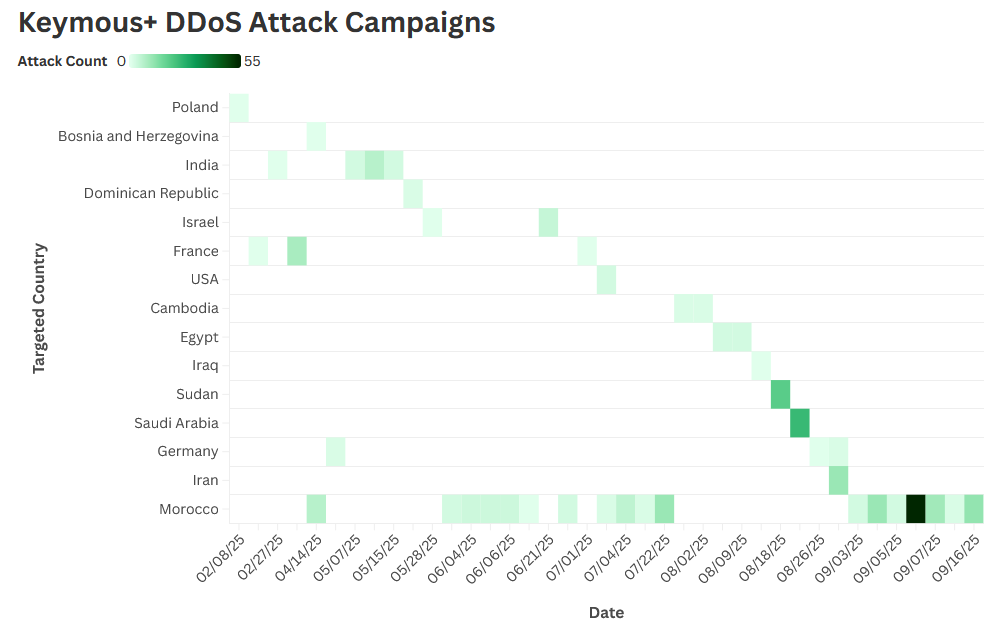
Keymous+ profile: Netscout researchers have published a profile on Keymous+, a threat actor that uses public available DDoS booter services to launch DDoS attacks.
Lunar Spider ops: NVISO looks at Lunar Spider, a cybercrime group believed to have developed both IcedID and Latrodectus, which is now using fake CAPTCHA trickery to infect victims with their malware.
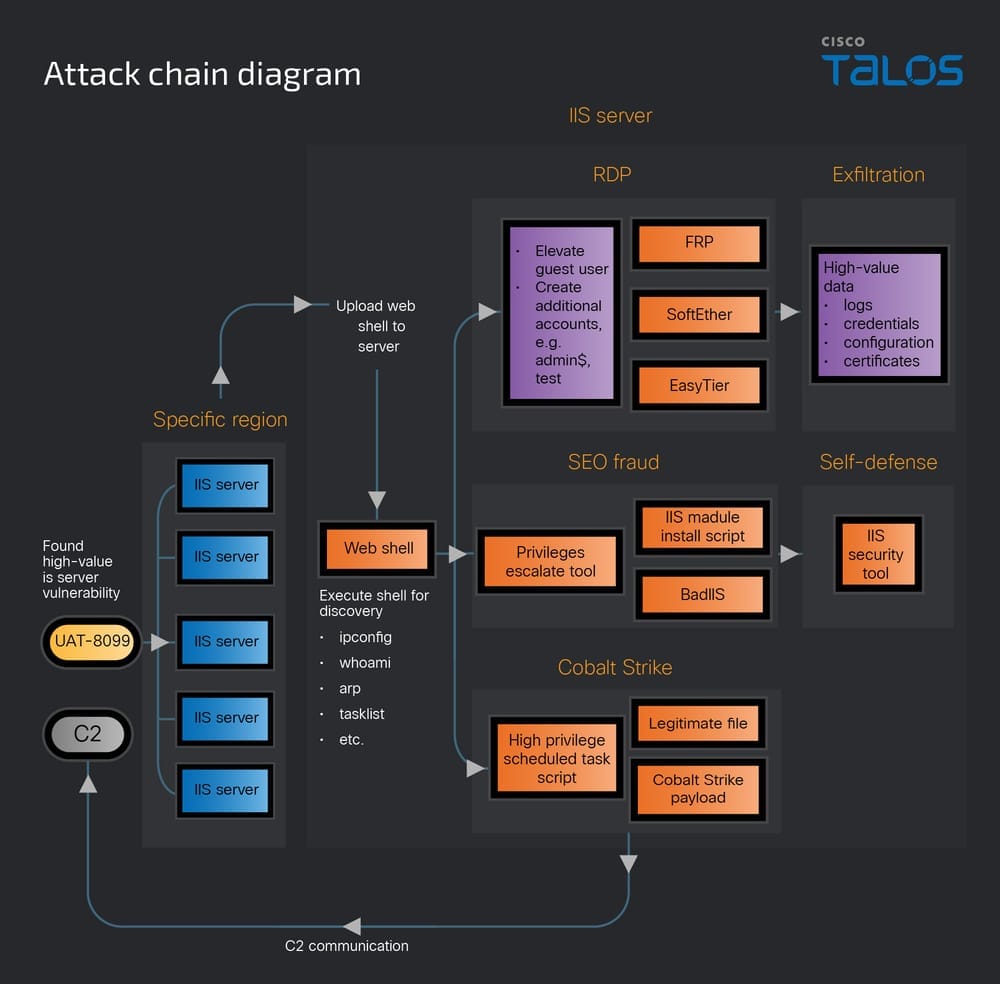
UAT-8099 profile: Cisco Talos looks at UAT-8099, a Chinese hacking group that is manipulating Google search results using hacked IIS servers. This is the same thing that ESET spotted as GhostRedirector and Palo Alto Networks tracks as Operation Rewrite.
Malware technical reports
Rhadamanthys: Check Point's Aleksandra "Hasherezade" Doniec has published an analysis of v0.9 of the Rhadamanthys infostealer.
FunkLocker: ANY.RUN looks at FunkLocker, an attempt by the FunkSec ransomware group to use AI to developer a new ransomware strain.
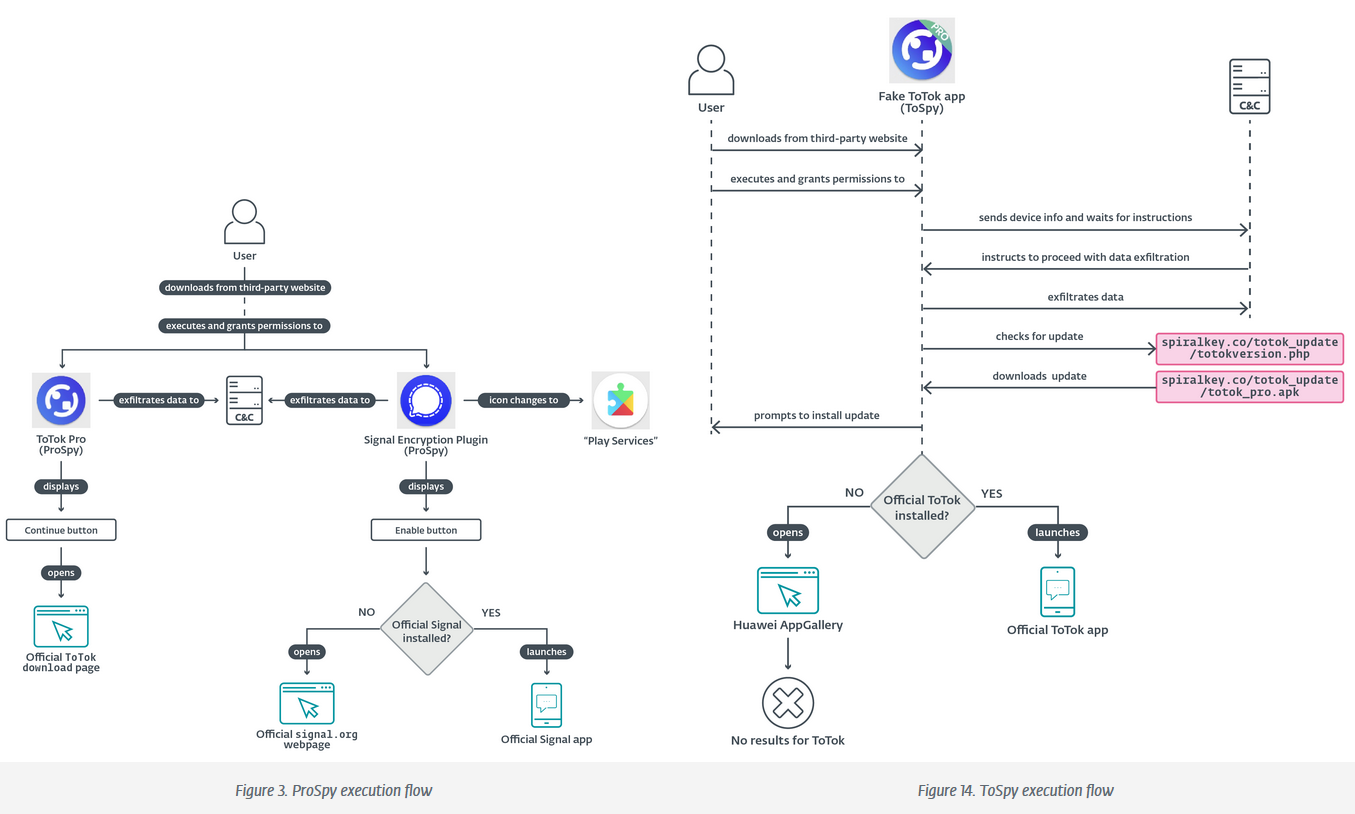
Android spyware in the UAE: Two separate Android spyware campaigns have been spotted targeting users in the UAE this year. The two spyware strains were hidden in trojanized versions of the Signal and ToTok apps distributed through dedicated websites. ESET said the two spyware strains used different infrastructure. The company tracks them as ProSpy and ToSpy.
Sponsor section
Authentik is an open-source identity provider that is also offered with paid enterprise features. In this demo, CEO Fletcher Heisler and CTO Jens Langhammer walk Risky Business host Patrick Gray through an overview and a demo of the technology.
APTs, cyber-espionage, and info-ops
Cavalry Werewolf: A suspected Kazakhstan APT group has launched espionage campaigns targeting Russian state agencies and critical enterprises. The group used spear-phishing for initial access and then deployed custom malware such as the FoalShell reverse shell and StallionRAT. Russian security firm BI.ZONE tracks the group as Cavalry Werewolf, but it is also known as YoroTrooper, SturgeonPhisher, Silent Lynx, Comrade Saiga, Tomiris, and ShadowSilk.
UAC-0245's CABINETRAT: CERT Ukraine has published a technical analysis of CABINETRAT, a remote access trojan used in recent 0245 operations.
Confucius ops: Fortinet's security team has spotted a new Confucius APT campaign targeting Pakistan with spear-phishing operations deploying a Python-based backdoor named AnonDoor.
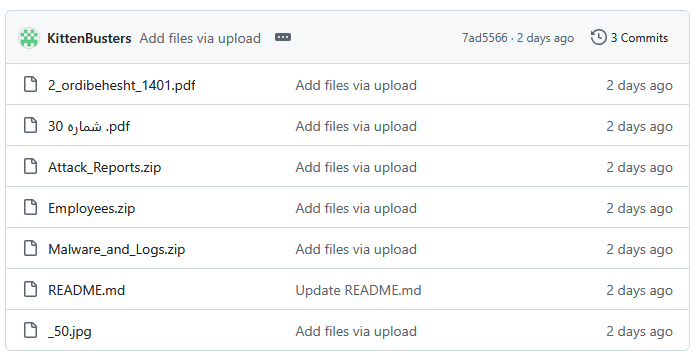
Charming Kittens (APT35) data leaked, again: A major leak has exposed sensitive data from an Iranian cyber-espionage group known as Charming Kittens and APT35. A mysterious group calling itself KittenBusters has published several archives on GitHub detailing the group's malware, past attacks, and alleged members. The leak includes the names of tens of individuals who work for front companies linked to APT35 hacking operations. The leak also identifies the APT35 leader as an individual named Abbas Hossein. The APT35 group was previously linked to Unit 1500 of Iran's Islamic Revolutionary Guard Corps Intelligence Organization, also known as the IRGC-IO. [Additional coverage by Nariman Gharib]
Vulnerabilities, security research, and bug bounty
KEV update: CISA has updated its KEV database with three vulnerabilities that are currently exploited in the wild. This includes a 2014 GNU Bash exploit, a 2015 Juniper vulnerability, a 2017 Jenkins bug, a 2025 Smartbedded Meteobridge command injection, and a recent Samsung zero-day that was used together with a WhatsApp exploit.
TOTOLINK vulnerabilities: PAN's Unit42 has found three new vulnerabilities in TOTOLINK routers. The worst of them is an unauth command injection.
DrayTek security updates: DrayTek has released a security patch for its popular Vigor router models. Tracked as CVE-2025-10547, the vulnerability allows attackers to hijack Vigor routers using specially crafted HTTP or HTTPS requests sent to the device's web management panel. Valid credentials are not required for exploitation.
FlipSwitch technique: Elastic's security team details FlipSwitch, a new syscall hooking technique.
Battering RAM attack: A team of Belgian academics has built a malicious memory module that can be used to break the confidentiality of modern clouds. The module, called Battering RAM, must be deployed by rogue data center employees. It sits between the RAM and motherboard and can allow attackers to break the security features of Intel and AMD processors powering cloud servers. According to the research team, the entire module only costs around $50.
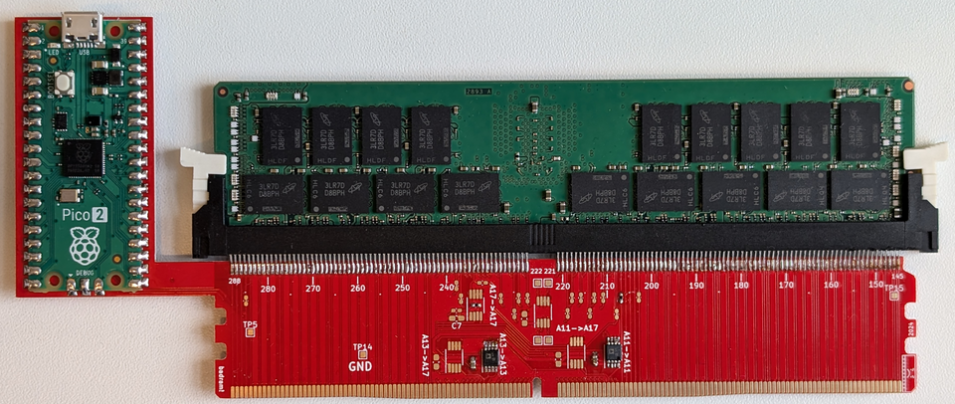
WireTap attack: A similar device named WireTap was also developed by a second research team, and this one can hack Intel SGX. This thing costs over $1,000, though.
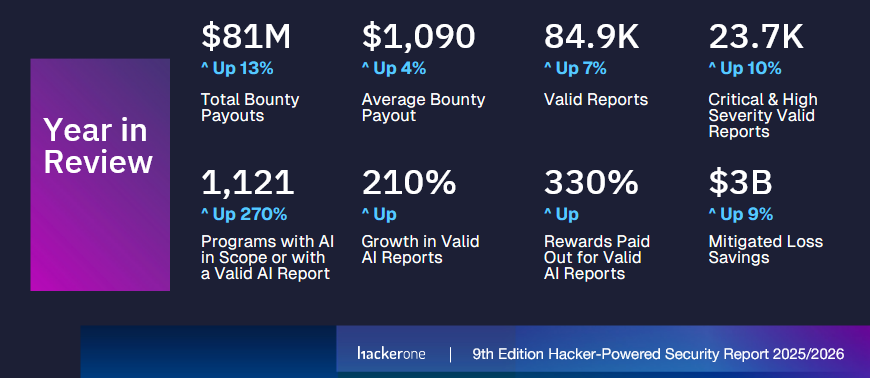
HackerOne year in review: The HackerOne bug bounty platform paid $81 million to security researchers last year. The company received almost 85,000 valid reports and paid out rewards of $1,090 on average. Vulnerabilities in AI products were a rising category this year, with more than $2.1 million paid out to researchers. Most of the reports covered prompt injection attacks.
Infosec industry
New tool—IAMhounddog: Virtue Security has released IAMhounddog, a tool to identify privileged principals and second-order privilege escalation opportunities in AWS environments.
Acquisition news: Vectra AI has acquired Netography, a company specializing cloud-native network observability.
Threat/trend reports: Dr.Web, ENISA, and HackerOne have recently published reports and summaries covering various threats and infosec industry trends.
Risky Business podcasts
In this edition of Seriously Risky Business, Tom Uren and Amberleigh Jack talk about different ways foreign intelligence services are finding to recruit local proxies. These methods could be too risky for Western intelligence agencies, but for some states' services, they just make sense.
In this edition of Between Two Nerds, Tom Uren and The Grugq discuss the power of cyber.




