Risky Bulletin: Russian military personnel targeted with Android spyware reminiscent of Russia's own tactics
In other news: Hegseth involved in second Signalgate scandal; two CISA Secure by Designs execs leave; Asian cyber scam call centers are spreading worldwide.

This newsletter is brought to you by Devicie. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
An unidentified threat actor is targeting Russian military personnel with spyware hidden in Android geo-mapping apps in what seems to be a campaign designed to spy on Russian military movements and positions.
The spyware is hidden inside legitimate versions of Alpine Quest, a mobile app used by Russian troops to coordinate operations in Ukraine.
According to Russian security firm Dr.Web, which spotted the campaign, the poisoned apps are spread via Telegram channels advertising a pirated PRO version of the app and even through some Russian Android app portals.
Once the spyware infects a target, it collects data from the device and sends it to a remote server. Collected data includes the usual data points, such as the victim's phone number, contacts list, geolocation details, and data about local files.
Dr.Web says the attackers are "particularly interested" in searching and retrieving "confidential documents" that military personnel might have sent via Telegram and WhatsApp.
They also steal locLog, an AlpineQuest file that logs location data and could be used to reproduce a victim's movements across time—just the file you wanna steal on a target you keep under surveillance.
Dr.Web didn't attribute the attack, and it won't be a stretch of the imagination to believe this is a Ukrainian intelligence op.
If it was, then the Ukrainians most likely learned all these tricks from the Russians themselves, who deployed similar tactics against Ukrainian soldiers in the past.
The attacks are a mirror of UAC-0185 (UNC4221) operations in Ukraine. The Russian hacking group has relentlessly targeted Ukraine's military and defense contractors, seeking to access data from military apps (DELTA, Teneta, and Kropyva) and encrypted messaging apps (Signal, Telegram, and WhatsApp).
Other Russian groups like Gamaredon, UAC-0142, UAC-0200, and UAC-0195 (UNC5792) have also carried out similar operations, seeking to track military movements by targeting soldiers' military or encrypted IM apps.
This marks the first time Russia reported seeing a similar attack against its own troops.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq discuss whether cyber operations can be 'strategic' and affect the fate of nations.
Breaches, hacks, and security incidents
XRP supply chain attack: A threat actor has hacked the npm account of the Ripple Foundation and added malicious code to the organization's official JavaScript library. According to Aikido Security, the code was designed to steal private keys and gain access to customer wallets. The malicious versions were live on GitHub and npm for only a few hours. The Ripple Ledger JavaScript library has more than 140,000 weekly downloads and is used by hundreds of thousands of apps and websites.
Marks & Spencer cyberattack: British retailer Marks & Spencer says it's dealing with a cyberattack that hit the company a few days back. No other details are available.
SK Telecom incident: South Korea's largest telecom says hackers accessed sensitive customer SIM data following a malware infection over the weekend. SK Telecom says it deleted the malware and is investigating the breadth of the breach. The company is investigating if the data was used for unauthorized SIM transfers or registrations.
Ayden DDoS attack: Payments platform Ayden was down for several hours due to a DDoS attack.
General tech and privacy
Microsoft inventoried 99% of network assets: Microsoft says it has honored its CISA Secure by Design pledge and rolled out dozens of security upgrades to its internal infrastructure. The company boasts it has now inventoried 99% of its network assets and rolled out proof-of-presence MFA to protect 80% of its production code. All new Azure tenants are now also automatically enrolled in Microsoft's security emergency response system. Microsoft says it also started rotating access token signing keys—the same ones compromised by Chinese hackers in 2023.
Durov threatens to leave France: Telegram founder and CEO Pavel Durov has taken a page out of Signal's book and says he'll pull the app out of France if officials demand an encryption backdoor.
Verified accounts on BlueSky: Rising social media darling BlueSky is adding support for classic Twitter-like "blue check" verified accounts. In the initial rollout phase, BlueSky staff will verify notable accounts and display a blue check next to their name. It will then open the application process for everyone as the feature "stabilizes."

FTC sues Uber: The FTC has sued Uber for allegedly charging customers for the Uber One subscription service without their consent. The FTC says users who signed up willingly also didn't receive the discounts they were promised, and Uber also made it extremely difficult to cancel the service. The agency says Uber is in violation of multiple consumer protection laws. Uber says it has now rolled out an easier way to cancel the service.
Opera adds a new privacy feature: The Opera browser will soon support a "Clear History on Exit" feature for enhanced privacy.
Google to keep third-party cookies in Chrome: The Google Chrome browser will continue to support third-party cookies for the foreseeable future. Google previously announced plans to deprecate third-party cookies, a widely used mechanism to track users across the web. The company announced the decision this week after its Privacy Sandbox technology failed to gain traction with some of the ad tech industry. Google is currently under investigation in the US for monopoly practices in both the browser and advertising markets. Experts believe that a forced push towards the Privacy Sandbox would have granted the company more control over both markets.
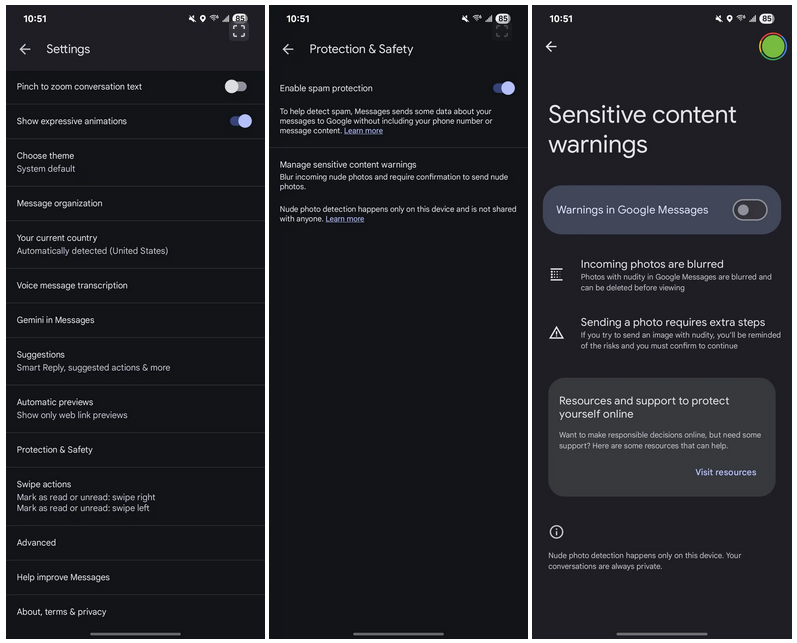
Nudity warning rolls out for Google Messages: Google is rolling out a new safety system that warns users when they're about to send or view an image that may contain nudity. The feature is disabled by default for adult users but will be automatically enabled for all underage accounts. Users can enable or disable it from their Google Account settings. [Additional coverage in 9to5Google]
Government, politics, and policy
UK bans the lease of Global Titles: The UK's communications watchdog has banned telecom operators from leasing Global Titles on UK phone networks. Ofcom officials launched an investigation into the abuse of Global Titles last year. Threat actors have abused Global Titles for years to track the physical locations of targets or intercept SMS MFA and other security codes.
Russia to boost domain registration security: Russian lawmakers are working on a bill that will require anyone registering a new .ru domain to verify their identity through their Gosuslugi e-government portal account.
Russian cyber sabotage against the Netherlands: Dutch military intelligence agency MIVD says Russian hackers attempted a cyber sabotage attack against a critical infrastructure entity. The attack took place last year and was unsuccessful, the agency said in its yearly report. Other cyber attacks targeted the websites of political parties and public transport companies during its elections. Dutch officials say Russia also started prepositioning for physical attacks, such as possible attacks on internet cables and energy supply.
Two CISA Secure by Design execs leave: Two top CISA officials involved in the Secure by Design program have left the agency. Bob Lord and Lauren Zabierek announced their departures on LinkedIn on Monday. CISA says the Secure by Design program will continue despite the departures. According to reports, the agency is set to fire up to 1,300 employees—a number that would include about half of its full-time staff and 40% of its contractors. [Additional coverage in The Record]
Hegseth involved in second Signalgate scandal: US Defense Secretary Pete Hegseth shared information about Yemen strikes in a second Signal group containing members of his family and inner circle. According to the New York Times, the messages included the same war planning information Hegseth shared in another Signal group where a journalist from The Atlantic was also included. The Signal group was allegedly named "Defense | Team Huddle" and was created by Hegseth himself.
US builds centralized databases: The US government has recently begun assembling two huge databases with the personal data of its citizens. The first will be run by USCIS and DOGE and will allow immigration officials to identify and track down immigrants. The second is a giant biometrics and medical database with the data of all Americans for a so-called "autism study." I have really warm feelings about these two DBs. /s
As a person who has studied history, an autism registry is a five alarm fire.
— Ian Coldwater 📦💥 (@lookitup.baby) 2025-04-22T00:26:39.633Z
Sponsor section
In this Risky Bulletin sponsor interview, Shane Harding, CEO of Devicie, talks to Tom Uren about trends in the enterprise software and security market that he thinks will have huge impacts. Software is becoming smarter and aims to solve problems rather than simply provide capabilities, and Microsoft has embarked on a big push into the SME security market.
Arrests, cybercrime, and threat intel
WhatsApp-v-NSO case update: A judge has placed a restriction on NSO and has forbidden the company from sharing data on its customers. Experts believe NSO was trying to portray its customers as law enforcement agencies and their operations as legitimate investigations in an attempt to justify its hacking of over 1,400 WhatsApp users. Many of these victims have proven to be government critics and journalists and certainly not the targets of legitimate investigations. [Additional coverage in CyberScoop]
Cyber scam centers are spreading globally: Cyber scam compounds are slowly spreading out of Southeast Asia to new regions of the globe. According to a new UN report, cyber scam centers have been found operating in Africa, South Asia, the Middle East, and some Pacific islands. The centers have ties to the same cybercrime groups operating in Southeast Asia and operate at the same industrial scale. They also use the same recruiting, human trafficking, and money laundering tactics first seen across the Mekong region.
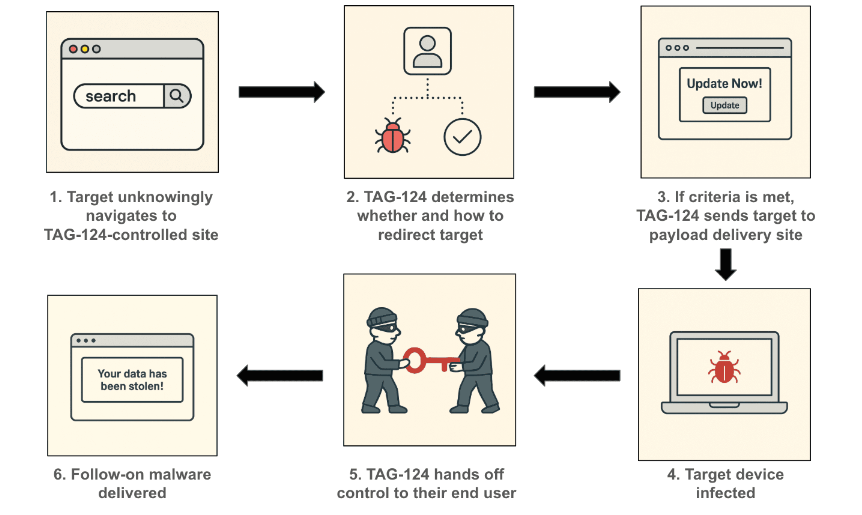
TAG-124 TDS: Recorded Future has published a profile of TAG-124, a traffic distribution system (TDS) used by multiple cybercrime crews, including big-game hunting ransomware gangs.
Discord phishing campaign: BinaryDefense researchers look at a recent Discord phishing campaign spreading the MalenuStealer.
New Docker cryptomining campaign: Darktrace has spotted a new campaign hacking Docker instances for crytpomining operations.
Scallywag campaign: Human Security has discovered a set of four WordPress plugins designed to help piracy websites bypass ad industry protections and show ads on their portals. The plugins work by redirecting users to clean domains where ads are shown and then redirected back to the piracy portals to view or download their content. The operation is allegedly showing up to 1.4 billion fraudulent ads per day.

Malware technical reports
AgeoStealer: Flashpoint has published a report on the AgeoStealer, an infostealer first spotted last year.
Lumma Stealer: Kaspersky looks at the various ways used to distribute the Lumma Stealer, an infostealer offered through a MaaS model.
PE32 ransomware: ANY.RUN has published a technical analysis of the new PE32 ransomware.
DOGE-themed ransomware: An unidentified threat actor has deployed DOGE-themed ransomware on the systems of more than 100 victims since January this year. The ransom notes contain the names of prominent DOGE employees and ask victims to pay $1,000 in Monero to recover their files. It's unclear if paying helped victims recover their data or if this was an elaborate troll.

Sponsor section
No race. No pressure. Just a better way forward to Windows 11, built for wherever you’re at and wherever you’re going. Visit devicie.com/windows11.

APTs, cyber-espionage, and info-ops
Kimsuky deploys BlueKeep: In a new report, AhnLab looks at a new Kimsuky operation using the BlueKeep vulnerability to target South Korean and Japanese orgs.
Konni campaign: RixedLabs researcher Navneet takes a look at a recent Konni APT campaign that took place earlier this month.
TraderTraitor: S2W has published a report on Willo Campaign, a recent TraderTraitor campaign that used GitHub social engineering to target the crypto world with the GopherGrabber malware.
Shedding Zmiy's Bulldog backdoor: Rostelecom's security team has published a report on Bulldog, a backdoor used by Ukrainian APT Shedding Zmiy.

Russian APTs target Microsoft 365 OAuth: Two Russian APT groups are using a novel phishing technique to hack Microsoft 365 accounts. The new technique involves making targets access official Microsoft links and then sending part of the URL response back to the attacker. The part shared by victims contains their OAuth authorization code, which attackers can then use to access their accounts. Volexity says the new attack was used to target individuals and organizations with ties to Ukraine and human rights.

Canadian Facebook flooded with disinfo: After Meta blocked news articles on its platform in Canada last year, Facebook has been flooded with political content from right-wing groups spreading disinformation ahead of the country's upcoming election. Chuck this on the growing pile of elections Meta is having an active role in, either intentionally or by its sheer lack of disinterest in addressing info-ops on its platform. [Additional coverage in the New York Times]
The Liberals have ensured that there's no real Canadian news on Facebook while simultaneously not punishing the company, at all, for all the fake news they're injecting into our country. If the Liberals had spines, they'd tell Meta either they get rid of the disinformation or they'll be banned.
— Mary Gillis (@marygillis.bsky.social) 2025-04-21T13:40:23.026Z
Facebook suspends Romanian anti-disinformation group: Meta has suspended a Facebook group dedicated to fighting disinformation in Romania. The group had over 10,000 members. It was set up in late December after Romania canceled its presidential election due to a massive disinformation campaign that boosted one candidate. The group's admins claim they were the victim of a coordinated mass-reporting attack from disinformation farms. Facebook has yet to respond days after the suspension.

Vulnerabilities, security research, and bug bounty
Android zero-day PoC released: Security researcher Zhuowei Zhang has released proof-of-concept code for CVE-2024-53104, a zero-day used by Cellebrite to unlock Android devices. Google patched the zero-day in February. Amnesty International says the zero-day was used by Serbian law enforcement to unlock the phones of anti-government protesters and journalists.
Zero Day Quest 2025: Microsoft has awarded more than $1.6 million in prizes during its first-ever Zero Day Quest hacking contest. Security researchers submitted more than 600 vulnerabilities in Microsoft cloud and AI services. The company says the Zero Day Quest event was a success and plans to hold it on an annual basis.
Cookie-Bite attack: Varonis has developed a PoC tool named Cookie-Bite that uses a rogue browser extension to steal cookies for Azure Entra and access cloud resources using a session hijack attack.
WinZIP MotW bypass: There's a fix for a new Mark-of-the-Web bypass (CVE-2025-33028) in WinZIP. This is apparently a patch for an incomplete fix for an older MotW bypass from last year (CVE-2024-8811).
ConfusedComposer vulnerability: Tenable discovered a privilege-escalation vulnerability in the Google Cloud Platform (GCP). The issue, which Tenable named ConfusedComposer, is now fixed.
Secrets in deleted files: Security researcher Sharon Brizinov explains how he made over $64,000 from bug bounties by hunting for secrets and tokens in previously deleted GitHub files.
Infosec industry
Threat/trend reports: Broadridge, Check Point, Check Point, Cloudflare, Imperva, Rubrik, and Valence Security have recently published reports and summaries covering various infosec trends and industry threats.

ATT&CK v17: MITRE has released v17 of the ATT&CK framework.
New tool—bincrypter: The Hacker's Choice has released bincrypter, a Linux binary runtime crypter.
Take Command videos: Talks from Take Command, a cybersecurity summit from AWS and Rapid7 that took place in May, are now available on the conference's Brighttalk website.
FIRST CTI 2025 streams: Live streams from the last FIRST CTI 2025 security conference, which are taking place this week, are available on YouTube.
KernelCon 2023 videos: Talks from the KernelCon 2023 security conference are available on YouTube. Better late than never, I guess!
Risky Business podcasts
Tom Uren and Patrick Gray discuss Trump's order singling out Chris Krebs, former head of CISA, which requires investigations into Krebs and also punishes his employer. It is a move deliberately designed to chill dissent, and they look at what the cybersecurity industry will likely do in response, which is probably not much.
Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and Adam at the helm!




