Risky Bulletin: Russian bill would require researchers to report bugs to the FSB
In other news: WSUS bug under attack; US charges poker hacking group; data breach at Iran's top hacking school.

This newsletter is brought to you by Knocknoc. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
Russian lawmakers are working on a new bill that would require security researchers, security firms, and other white-hat hackers to report all vulnerabilities to the state, in a law that's similar in spirit to a law already in effect in China since 2021.
The bill is currently being discussed among lawmakers, and no official draft is available. It is part of Russia's efforts to regulate its white-hat ecosystem, a process officials began back in 2022.
All previous efforts failed, with the most recent one being knocked down in the Duma in July on the grounds that it did not take into account the special circumstances and needs of reporting bugs in government and critical infrastructure networks.
Now, according to sources who spoke to Russian business magazine RBC, a new draft of the bill is being prepared.
The biggest change in this version is the addition of a requirement to report all vulnerabilities to the vendor or a network's owner, but also to Russian authorities.
Three state agencies will be in control of this new unified system that takes in vulnerability reports and will be making new rules or requirements for researchers going forward.
They include the country's main internal intelligence service, the FSB, the National Coordination Center for Computer Incidents (NKTsKI), a CERT-like organization created and operating under the FSB since 2018, and FSTEC, Russia's cryptography, export control, and dual-use technology agency, under the country's military.
Security researchers who fail to report bugs to this state unified system will face criminal charges for "unlawful transfer of vulnerabilities."
The bill will also introduce registries for companies that run bug bounty programs and for the researchers themselves, where white-hats will have to provide their real names to the state.
This last part has been a contention in previous versions of the bill, with the private sector and security researchers pushing hard against it, for legitimate reasons.
As the RBC piece again points out, researchers are uncomfortable with providing the government with real names. They argue that a leak or hack of this system would pose serious threats to their safety, being at risk of being kidnapped by criminal groups and forced to produce vulnerabilities under the threat of violence. They also fear their data falling into the hands of foreign governments, which may sanction their accounts or arrest them on trips abroad for conferences or vacations.
The bill is intended to cover all facets of the white-hat ecosystem, from commercial bug bounty programs to internal vulnerability rewards programs (VRP) at private corporations, and from individual researchers doing hobby work to pen-testing assignments.
All bugs, no matter where and how they were found, must be reported, and researchers will receive legal liability protection if they follow the rules.
This liability protection was not enough to get the Russian infosec community on the government's side last time, and I doubt it will be enough to convince them this time around that it's in their best interests to reveal their real names and give the government a copy of all their research for free.
In July 2021, the Chinese government passed a similar law that required all Chinese researchers and security firms to report bugs to the government no more than 48 hours after discovery.
While people were skeptical at first that the Chinese government would abuse reports of unpatched bugs for its offensive operations, time has proven that the use of zero-days by Chinese APTs has increased dramatically since the law entered into effect.
A draft for Russia's new white-hat research law is expected to reach the Duma by the end of the year, although it's unclear if it will pass since this whole thing has had three years' worth of controversy attached to it, with the infosec community making a good argument against it—or at least the public registry part of it.
Risky Business Podcasts
The main Risky Business podcast is now on YouTube with video versions of our recent episodes. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
WazirX resumes trading 15 months after hack: India's WazirX cryptocurrency exchange has resumed trading 15 months after a major security breach. The company was hacked for $235 million worth of assets in July of last year. According to CoinDesk, the exchange has relaunched after a Singapore High Court-approved restructuring and with zero trading fees at launch.
Toys 'R' Us Canada breach: Toys 'R' Us Canada is notifying customers of a security breach that exposed their names, addresses, emails, and phone numbers. [Additional coverage in the CBC]
FFTir breach: The French Shooting Federation is notifying members of a security breach. Hackers stole the personal data of almost 274,000 members. This includes license holders across multiple firearm shooting sports. The hack took place last week, on October 18. [Additional coverage in TF1 INFO]
Hack cost TfL £39m: A ransomware attack against Transport for London at the start of September 2024 has cost the organization £39 million. Two teenagers were arraigned in court on Friday for the incident. The two, aged 18 and 19, are members of the Scattered Spider hacking group. A trial date has been set for next June. [Additional coverage in the BBC]
Rosselkhoznadzor hack: A cyberattack on Russia's agricultural and food safety watchdog has caused food delivery delays across the country. The attacks targeted two certification platforms, Mercury and VetIS. This was the second time the platforms went down after a cyberattack this year, after a first attack in June. Food producers and delivery companies need certificates issued by the two platforms to move products across Russia. [Additional coverage in The Record]
KCNSC hack: Foreign hackers used a recent SharePoint zero-day to breach the Kansas City National Security Campus (KCNSC), a key manufacturing site for the US National Nuclear Security Administration (NNSA). [Additional coverage in CSO Online]
General tech and privacy
New UBIOS standard: The Global Computing Consortium, a Chinese tech standards body, has announced UBIOS, a replacement for the BIOS and UEFI standards. [Additional coverage in PBX Science]
Meta, TikTok don't provide research access: The EU says Meta and TikTok are violating the bloc's Digital Services Act by not providing academics and researchers proper access to their data. Meta was also found in violation of the DSA because Facebook and Instagram don't provide users an easy way to appeal suspensions or content removal. Both companies can respond to the EU's preliminary findings. If found guilty, they can be fined up to 6% of their total worldwide annual turnover.
Microsoft Teams to get WiFi tracking feature: A new Microsoft Teams feature will let organizations track employees based on nearby WiFi networks. The feature is designed to let employers know what building an employee is working on based on nearby networks. According to privacy experts, the new feature will allow companies to crack down on workers who dodge return-to-office mandates. The new WiFi tracking is expected to roll out in December for the Teams Mac and Windows desktop clients.
HP breaks Windows devices: HP has pulled a faulty update for the OneAgent app that deleted certificates from customer devices. The faulty update was caused by a cleanup script that removed all certificates containing the string "1E" in its subject, issuer, or friendly-name fields. One of the removed certificates was MS-Organization-Access, used by Windows PCs to authenticate on the Entra service. This disconnected users from enterprise networks and prevented them from logging in. [Additional coverage in Patch My PC]
Wow... 🤯
— Nathan McNulty (@NathanMcNulty) October 23, 2025
This is even bigger than Entra/Intune btw :(
Certificates issued based on serial number, GUID, lots of stuff could be affected
HP's script literally just searches the LocalMachine\My cert store where Subject or FriendlyName contains "1E" and deletes the cert..... https://t.co/R0NNwxSLZT
Government, politics, and policy
Predatorgate scandal: One of the main targets of the Predatorgate spyware scandal in Greece, main opposition PASOK leader Nikos Androulakis, testified last week in court in a sham lawsuit that ignored the ruling government for deploying the spyware and went after four nobodies at four companies that provided the spyware. [Additional coverage in eKathimerini]
Belarus blocks VK: The Belarusian government has blocked access to Russian social network VK. The block order came from the country's intelligence agency and carried no explanation. Belarusian officials previously blocked VK after users shared news articles that the regime didn't like. [Additional coverage in Pozirk]
UN cybercrime treaty signed: Seventy-two countries have signed a new controversial UN cybercrime enforcement treaty over the weekend.
The recording of the signing ceremony is available here webtv.un.org/en/asset/k1m... It features not only routine signings but also artful cybersecurity-themed dance performance
— Oleg Shakirov (@shakirov2036.bsky.social) 2025-10-25T06:23:52.998Z
Sponsor section
In this sponsored podcast Patrick Gray chats with Knocknoc CEO Adam Pointon about why true Zero Trust architectures never really got there. Spinning up ZTNA access to core applications and slapping SSO prompts on everything else is great, but if we’re honest, it’s not really Zero Trust. So, how and why did we get here?
Arrests, cybercrime, and threat intel
US charges poker hacking group: US authorities have arrested and charged 31 suspects for their role in a poker cheating scheme. Suspects include members of the Italian mob, former NBA coach Chauncey Billups, and former NBA player Dee Jones. The group used celebrities to lure victims to high-stakes poker games, where they used hacked deck shuffling machines to rig games. The group also used specially designed sunglasses and contact lenses to read the back of playing cards that were previously marked with invisible ink. Victims allegedly lost at least $7 million to the group. [Additional coverage in WIRED]
Thailand revokes scammer's citizenship: The Thai government has revoked the citizenship of a naturalized Cambodian businessman for running scam compounds. Phat Suphapa had his citizenship revoked last week through an order by Thailand's prime minister. They also seized 70 million baht ($2.1 million) of his funds. Suphapa also goes by the name of Ly Yong Phat and was also sanctioned by the US Treasury in September of last year. [Additional coverage in the Bangkok Post]
KK Park exodus: More than a thousand individuals who were held at the KK Park scam compound have fled or have been moved to new locations over the past week, according to Cyber Scam Monitor. The moves come after new US Treasury sanctions and a Myanmar military junta raid. KK Park is generally considered Myanmar's largest scam compound.
Zagnet: There's a new hacktivist group named ZagNet that made waves with DDoS attacks over the past two weeks.
New CryptoChameleon campaign: LastPass users have been targeted with a clever phishing campaign claiming that one of their family members is trying to access their account using a death certificate. The goal is to get users to cancel the request and authenticate and share their master passwords on a phishing site. LastPass linked the campaign to CryptoChameleon (UNC5356), a group known for targeting the crypto community.
New npm malware: Ninety-three malicious npm packages were discovered and taken down last week. Check out the GitHub security advisory portal for more details.
The backups dilemma: A recent study has found that while 95% of respondents are confident about their ability to recover from a ransomware attack using their backups, only 15% of those who were attacked managed to do so.
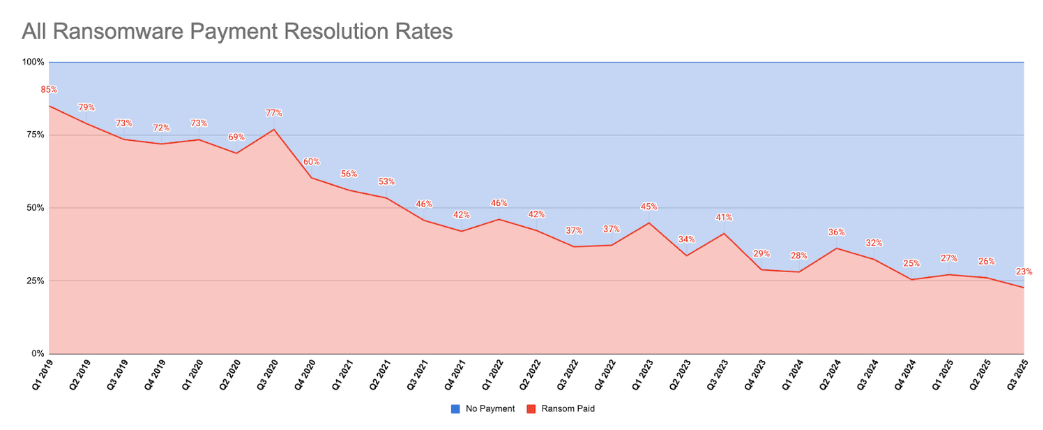
Ransomware pay rates hit an all-time low: Ransomware payment rates have dropped below 25% for the first time in history. Payment rates in the third quarter of the year were only 23% according to data gathered by Coveware, a company specializing in ransomware negotiations. The company says cyber defenders, law enforcement, and legal specialists should take this as a validation of their efforts.
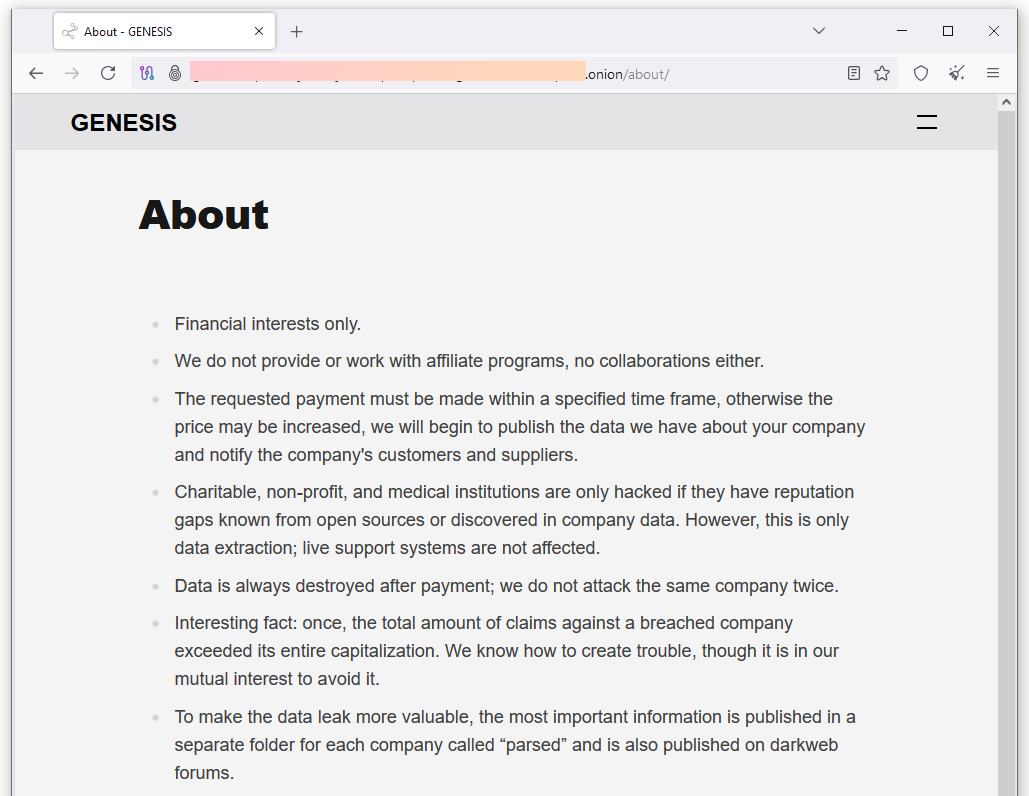
New Genesis ransomware group: A new ransomware group named Genesis launched a data leak site on the dark web last week. The site currently lists ten public victims.
Malware technical reports
Caminho Loader: Arctic Wolf researchers have spotted Caminho Loader, a new malware loader sold on the Brazilian underground malware scene that sure loves steganography.
Sponsor section
In this sponsored product demo, Knocknoc CEO Adam Pointon walks Patrick Gray through the Knocknoc secure access platform. Knocknoc is a platform that restricts network and service availability to authenticated users via existing network security equipment. Users don't need to install an agent. It also has an identity-aware proxy component that supports web applications and RDP.
APTs, cyber-espionage, and info-ops
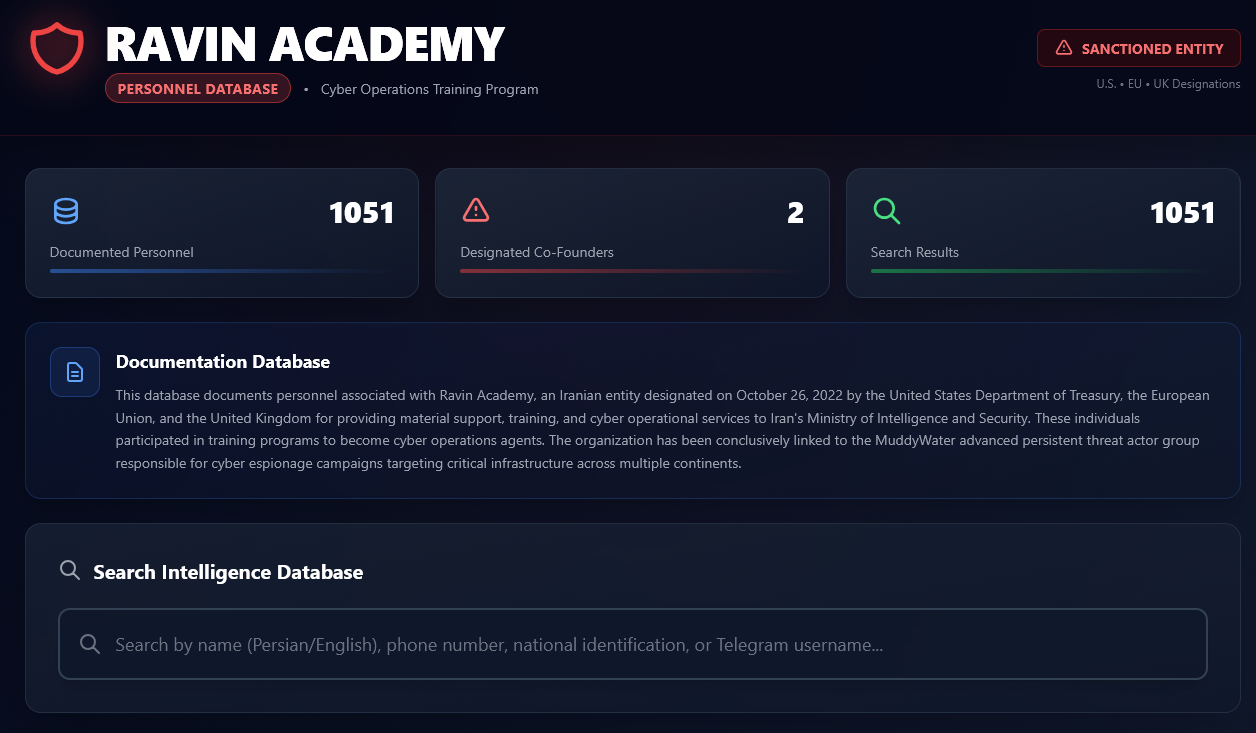
Ravin Academy leak: A private school that trains hackers for Iran's intelligence service has suffered a security breach. A database with information on all students of the Ravin Academy was published online last week. The data contains student names, their phone numbers, and the classes they attended. The leak occurred days before Ravin Academy was set to hold its annual Tech Olympics hacking contest. The US Treasury sanctioned Ravin Academy in 2022 for training hackers for the MOIS. [Additional coverage in Iran International/English coverage by Nariman Gharib/Public searchable database of the Ravin data]
Lazarus DreamLoaders: Lab52 takes a look at two new DLL sideloading mechanisms used by North Korean hackers (the Lazarus Group) in their DreamJob campaign. Lab52 calls these techniques DreamLoaders.
Salt Typhoon: Silent Push says it identified some new Salt Typhoon server infrastructure.
APT-Q-37 (APT-C-08, Bitter): QiAnXin and Qihoo 360 reports look at new backdoors deployed by the APT-Q-37, a suspected Indian APT also known as Bitter and APT-C-08.
SideWinder: Trellix looks at a new campaign from Indian APT SideWinder. The campaign targeted diplomatic entities across South Asia.
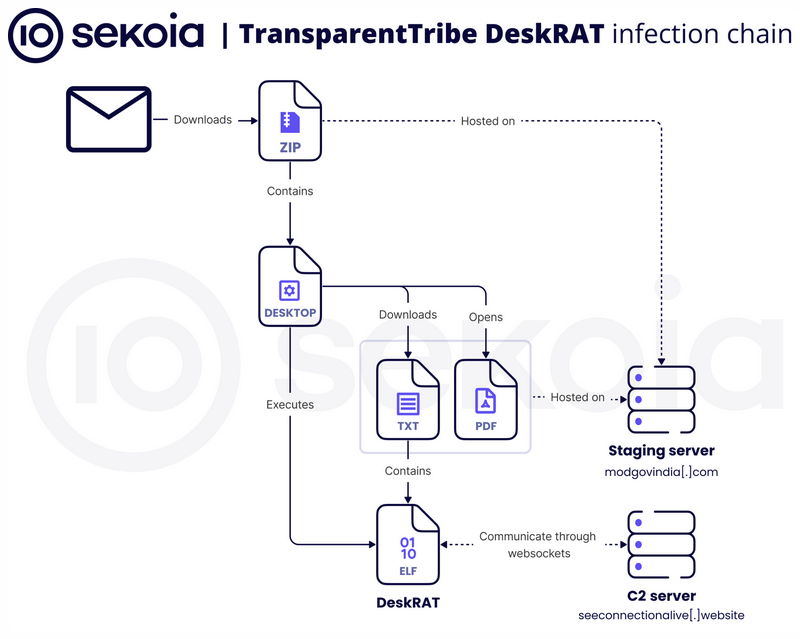
TransparentTribe targets Indian military: Pakistani APT group TransparentTribe has targeted Indian military organizations with DeskRAT, a Go-based remote access trojan, capable of running on the military's Linux BOSS-based environments.
Vulnerabilities, security research, and bug bounty
WSUS bug under attack: Microsoft has released an out-of-band security update to patch a vulnerability in the Windows Server Update Services that is being exploited in the wild. The targeted WSUS component allows administrators to control how they deploy Windows OS updates inside closed networks. Tracked as CVE-2025-59287, the vulnerability allows remote code execution on Windows Servers where the WSUS Server Role is enabled. That role is typically disabled, but even when enabled, there is a very small number of networks with WSUS exposed on the internet. Attacks have been spotted by CISA, Huntress, Horizon3, and Eye Security after proof-of-concept code was published online earlier this month.
KEV update: CISA has updated its KEV database with two vulnerabilities that are currently exploited in the wild. This includes the recent WSUS bug and a Magento vulnerability known as SessionReaper.
Blue Angel exploitation: Threat actors are targeting VOIP and SIP servers using vulnerabilities in the Blue Angel Software Suite. Attacks have been observed by the SANS Internet Storm Center, the Shadowserver Foundation, and VulnCheck. Exploitation started in January and has continued through the year, using at least two vulnerabilities.
New credential dumping technique: Security firm SpecterOps has discovered a new technique to dump NTLMv1 hashes from fully-patched modern versions of Windows. The technique bypasses the Credential Guard protection using Remote Credential Guard, a security feature included with the Remote Desktop Protocol. An open-source tool to demo the attack is also included.
EfficientLab vulnerabilities: EfficientLab has patched three vulnerabilities discovered in the WorkExaminer Professional employee monitoring software. The bugs can allow remote attackers to gain access to the software's servers due to hardcoded FTP credentials or via port 12306 due to missing authentication checks.
GCP suspension bypass: After Security Explorations had its Firebase database suspended by Google Cloud for "hosting malware" (actually some PoC code), the team found a way to bypass the suspension, which they argue could be abused and automated by attackers as well.
Infosec industry
Threat/trend reports: Cisco Talos, Coveware, Cybereason, Mimecast, NCC Group, OpenText, Pew Research, and Red Canary have recently published reports and summaries covering various threats and infosec industry trends.
r2con videos: Talks from the r2con 2025 security conference, which took place over the weekend, are available on the conference's website and YouTube.
ACM KDD videos: Talks from the ACM 2025 Knowledge Discovery and Data Mining conference, which took place in August, are available on YouTube, in two playlists.
IMC 2025 papers: Papers from the 2025 ACM Internet Measurement Conference are available for download. The conference is set to take place this week.
New CRI guidance: The Counter Ransomware Initiative has released new guidance to help organizations secure their supply chains against possible ransomware attacks coming in that way.
New tool—PDF Object Hashing: Proofpoint has open-sourced PDF Object Hashing, a tool to identify similarities between PDF files without relying on the content of the document.
New tool—DetonatorAgent: Dobin Rutishauser has released DetonatorAgent, a cross-platform Web API for malware execution and EDR log collection.
New tool—PingOneHound: SpecterOps' Andy Robbins has released PingOneHound, a BloodHound extension to analyze and identify issues in the PingOne (IDP) service.
New tool—DumpGuard: SpecterOps' Valdemar Carøe has released DumpGuard, a tool to dump NTLMv1 hashes from sessions on modern Windows systems by using the Remote Credential Guard security feature to bypass Credential Guard protections.
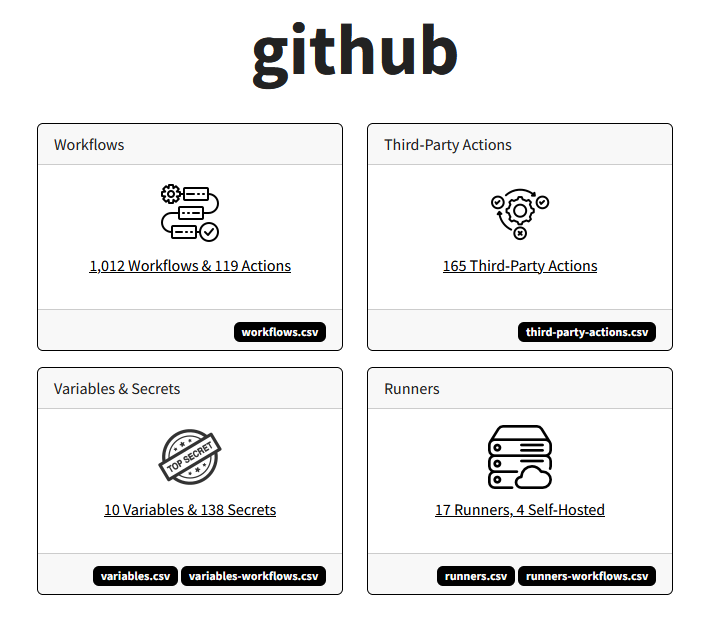
New tool—Butler: Security researcher Pavel Tsakalidis has open-sourced Butler, a tool that scans GitHub repos for workflows, actions, and other common dangers and misconfigurations, and then produces nice reports on all issues found.
Risky Business podcasts
In this edition of Seriously Risky Business, Tom Uren and Amberleigh Jack talk about how America can better use its private sector to scale up offensive cyber activities, including espionage and disruption operations. Involving it to tackle ransomware and cryptocurrency scammers makes a lot of sense.
In this edition of Between Two Nerds, Tom Uren and The Grugq talk to Joe Devanny, senior lecturer from King's College London, all about India's missing cyber power. It has the ingredients to become a cyber superpower, but so far, it hasn't shown the motivation.




