Risky Bulletin: Russia returns the favor one year later, hacks Ukraine's state registers
In other news: Netwalker affiliate sentenced to 20 years; ColdFusion gets pre-Xmas security update; UN passes controversial cybercrime treaty.

You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
Risky Business Podcasts
Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
Cyberattack hits Ukrainian state registers: Ukrainian officials claim that Russian GRU hackers have breached the government's electronic state registers, a collection of databases that stores information on the Ukrainian population and private sector. The hack took place a year after Ukraine intelligence hacked and wiped data from Russia's tax agency last year.
Japan Airlines cyberattack: Japan Airlines was hit by a cyberattack on December 19 that led to the cancelation of over 20 domestic flights. Most systems were recovered within days. Per a Japan Airlines statement, this looks to have been a DDoS attack. [Additional coverage in the Associated Press]
DMM hack linked to North Korea: The FBI and Japan's National Police have linked the DMM Bitcoin $308 million crypto-heist to North Korean hackers—and specifically to a group tracked as TraderTraitor.
ESA hack: The European Space Agency's web store was hacked with a skimmer, per Sansec.
Rapido data leak: Indian ride-hailing service Rapido has fixed a security issue that exposed personal information associated with its users and drivers. Per TechCrunch, the leak came from an improperly secured API.
Play claims Krispy Kreme attack: The Play ransomware gang has taken credit for the incident at donut restaurant chain Krispy Kreme.
Apple redirects spyware victims to AccessNow: A TechCrunch report reveals that Apple's security team typically tells users suspected of being hacked with spyware to reach out to AccessNow.
General tech and privacy
Judge rules in favor of WhatsApp: A US judge has sided with Meta in its lawsuit against NSO Group and has found the Israeli spyware maker liable for damages caused to over 1,400 WhatsApp users who had their devices hacked in May 2019. A jury trial in March next year will determine the damages owed by NSO. [Additional coverage in The Guardian]
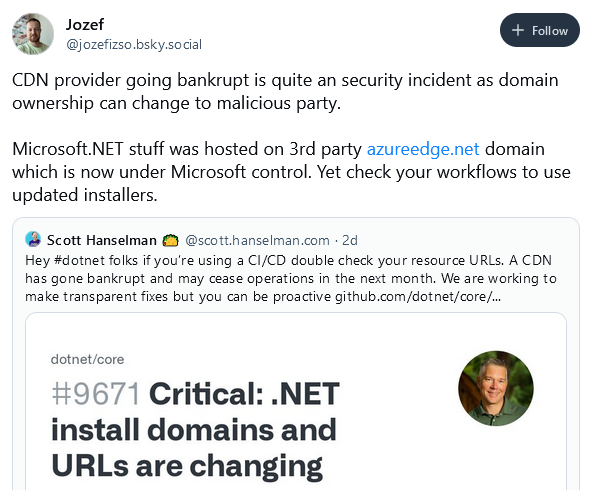
CDN shuts down, causes chaos: Microsoft was forced to move some domains around after the Edg.io CDN suddenly announced it was ceasing operations due to bankruptcy, leaving the domains without hosting.
Mozilla boosts revenue: Mozilla reported $653 million in revenue in 2023, $59 million over the previous year. A breakdown is available via gHacks.
Bluesky Trending beta: Bluesky is testing a beta version of an upcoming Trending section.
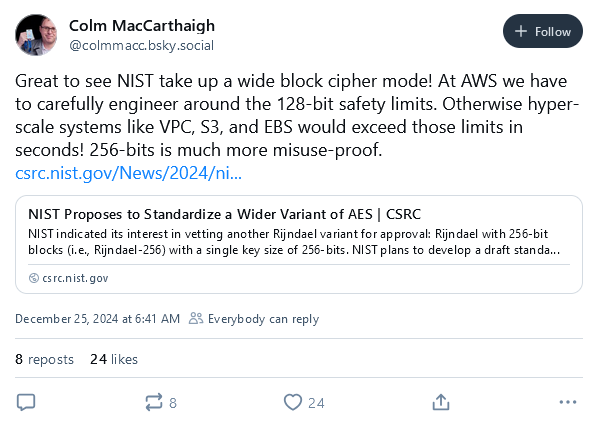
NIST prepares to standardize new block cipher: US NIST is preparing to standardize a new AES Rijndael-256 block cipher mode next year.
Tesla update bricks Cybertrucks: A Tesla firmware update this week has bricked several Cybertrucks.
Windows 11 security update bug: There's currently a bug in the Windows 11 installation media where the OS can't install security updates. The bug was discovered over Christmas and might take a while to fix.
Tor integrations: The Tor Project has promised that next year, it will make its Tor technology easier to integrate inside other third-party apps.
Apple security documentation: Apple has updated its platform security guide [PDF] to add information on the company's latest M4 chip.
Government, politics, and policy
Iran lifts WhatsApp, Google Play bans: The Tehran regime has lifted its bans on the Google Play Store and instant messaging service WhatsApp, per Iran International.
Russia looks to ban IM voice calls: Russia's internet watchdog agency has confirmed it is looking at ways to ban voice calls made via instant messaging clients. [Additional coverage in Interfax]
Russia prepares more messenger app bans: The Roskomnadzor is also taking the first steps towards banning Skype and WhatsApp next year. Other messengers on the agency's hit list also include Wire, Element, KakaoTalk, Dust, Keybase, Trillian, Pinngle Safe Messenger, Status, and Crypviser. [Additional coverage in Novaya Gazeta]
GEC shuts down: The State Department's Global Engagement Center, an office that hunts down and exposes foreign disinformation campaigns, has shut down after Congress did not allocate new funding in the NDAA for next year. [Additional coverage in CyberScoop]
Ohio defers cyber liability to state employees: The US state of Ohio has warned state employees that they might be held personally liable if they fall to online email scams. [h/t DataBreaches.net]
Serbia spyware scandal: Several Serbian NGOs filed complaints this week against Serbian police and security services after an Amnesty International report revealed that authorities used a piece of spyware called NoviSpy to spy on journalists and activists. [Additional coverage in Barron's]
Countries ask Thailand for help: At least 14 countries have asked Thailand to help free citizens who have been taken prisoner and are being forced to work in cyber scam compounds in Myanmar, near the Thai border. [Additional coverage in the Bangkok Post]
UN adopts new cybercrime treaty: The UN General Assembly has adopted this week a new controversial cybercrime treaty. The treaty was adopted without a vote and will be signed in Hanoi, Vietnam, next year. It will enter into effect 90 days after the 40th country signs it.
Risky Business Podcasts
Brian A. Coleman, Senior Director for Insider Risk, Information Security, and Digital Forensics at Pfizer, talks to us about how his security team is experimenting with AI to improve their insider risk detection systems. The system Brian and his team put together can detect sensitive information or documents handled by unauthorized accounts, but can also spot documents moving around and ending up where they shouldn't be - either by accident, malice, or as a result of a security breach.
Arrests, cybercrime, and threat intel
Netwalker affiliate sentenced to prison: A US court has sentenced a Romanian named Daniel Christian Hulea to 20 years in prison for his role as an affiliate for the Netwalker RaaS. He was also ordered to forfeit $21.5 million of his interests in an Indonesian company and associated luxury resort property under construction in Bali, Indonesia—a business he financed with proceeds from the attacks. He was also ordered to pay $15 million in restitution to victims.
Zhdanova arrest: A LeMonde report has revealed that French authorities secretly arrested a Russian woman named Ekaterina Zhdanova in October 2023. Zhdanova was sanctioned by the US last year for helping launder cryptocurrency related to Ryuk ransom payments. The UK NCA linked her to a huge Russian money laundering network earlier this month.
NFT rug-puller charged: The US has charged two California men with defrauding investors of more than $22 million through a series of NFT project rug pulls. This includes projects such as Vault of Gems, Faceless, Sinful Souls, Clout Coin, Dirty Dogs, Uncovered, MoonPortal, Squiggles, and Roost Coin.
Data extortionist charged in NJ: US officials have charged a Brazilian man for trying to extort a US company with leaking data from its Brazilian subsidiary unless paid a $3 million ransom back in 2020.
LockBit coder charged: The US has formally charged a Russian-Israeli national named Rostislav Panev for working as a coder for the LockBit gang. Panev is currently in custody in Israel pending extradition.
LockBit 4.0 announced: The LockBit RaaS has announced version 4.0 of its platform. v4.0 will launch in February, almost a year after v3.0 of its RaaS was thoroughly dismantled by authorities.
Dragon RaaS interview: Threat intelligence analyst Marco A. De Felice has published an interview with the operators of the Dragon Ransomware-as-a-Service platform, which launched earlier this year in July.
Nam3L3ss interview: DataBreaches.net has published a multi-part interview with Nam3L3ss, a threat actor who leaked data from over 100 companies and organizations on underground hacking forums.
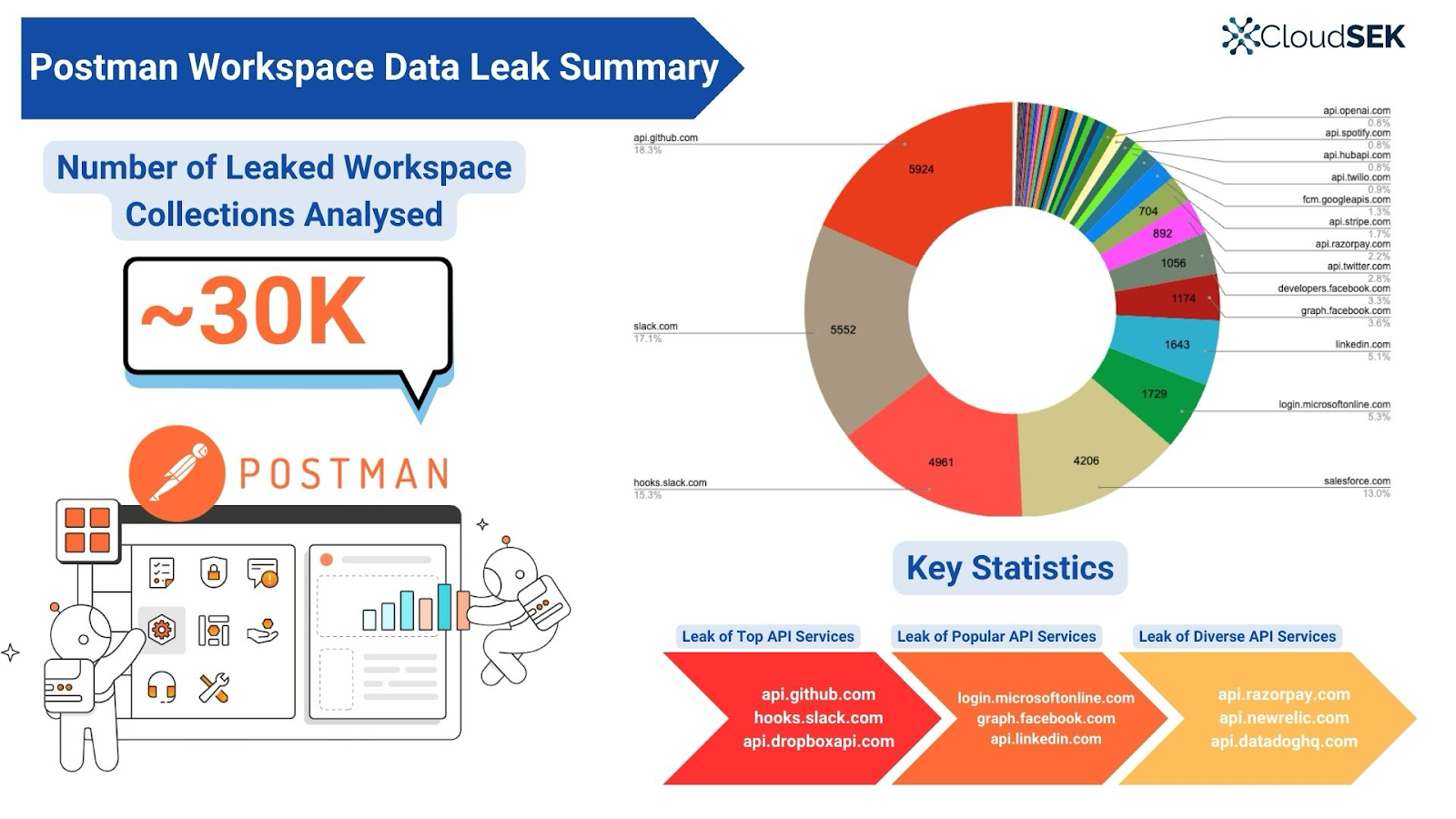
Leaky Postman servers: CloudSEK researchers have found more than 30,000 Postman workspaces that were leaking some sort of sensitive information.
NoName extortion campaign: A threat actor is using the name of a Russian hacktivist group (NoName057) to send DDoS threats and conduct a mass extortion campaign. A second campaign targets actual NoName057 just with the extortion part and lets the real NoName057 do the DDoSing.
New infostealer announced: ThreatMon has spotted a Telegram ad for a new infostealer named NunuStealer.
New Masque group targets Russia: FACCT has published a profile on Masque, a new financially motivated group that targets Russian organizations with ransomware. The ransomware is based on leaked strains such as Babuk, Conti, and LockBit. The group has been active since January 2024. Although other ransomware gangs attacking Russia have been previously linked to pro-Ukraine causes, FACCT has not made a formal attribution in the report.
PlugX disinfections: Sekoia has published some stats on its PlugX disinfection operation this year.
"At the end of the campaign, 34 countries requested simple sinkhole logs to identify which networks were compromised, 22 countries expressed interest in the disinfection process, and we were able to establish a legal framework and conduct disinfection operations for 10 countries. In total, 59,475 disinfection payloads were sent during the campaign, targeting 5,539 IP addresses, sometimes hundreds of times to a single IP address (probably related to VPN exit nodes or SAT links)."
Astrill VPN IP list: Security firm Spur has released a list of 2,400 IP addresses linked to Astrill, a VPN service often used by North Korean IT workers to hide their location.
Virtual office abuse: Team Cymru has published an interesting report on how threat actors are abusing tax havens and virtual office providers to hide their operations and real identities.
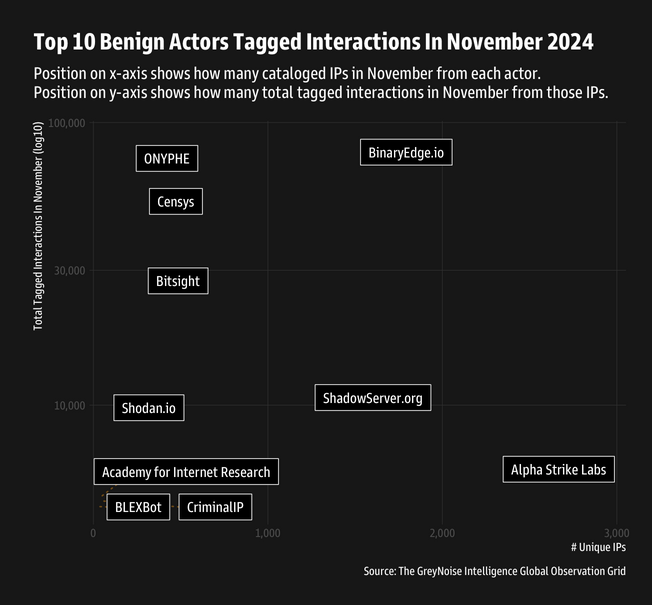
Internet scanners landscape: GreyNoise looks at internet benign mass scanners the platform has documented over the past year.
Malware technical reports
Akira ransomware: ThreatMon has published a technical analysis of the Akira ransomware.
PlayfulGhost: Google Cloud's security team looks at PlayfulGhost, a variant of the Gh0st RAT malware.
Cometlogger and Zebo: Fortinet has discovered more malware uploaded on the PyPI repository. This batch contained two keyloggers named Cometlogger and Zebo.
Rhadamanthys Stealer: Forcepoint researchers look at a phishing campaign targeting hotels, restaurants, and other businesses in Switzerland and the United Kingdom with the Rhadamanthys Stealer.
WikiKit: TRAC Labs has published a breakdown of WikiKit, a phishing kit with a weird quirk of redirecting victims to Wikipedia pages if JavaScript is disabled in their browser or if the phishing link is invalid.
LITTLELAMB.WOOLTEA: Northwave researchers have published a report [PDF] on a new backdoor named LITTLELAMB.WOOLTEA they have found on PAN firewalls compromised using the CVE-2024-9474 vulnerability.
BADBOX: Bitsight says the BADBOX adware botnet is still on roughly 192,000 devices across the globe. The report comes days after Germany's BSI sinkholed the botnet's traffic on the country's ISPs.
Risky Business Podcasts
In this podcast, Tom Uren and Adam Boileau talk about the continued importance of hack and leak operations. They didn't really affect the recent US presidential election, but they are still a powerful tool for vested interests to influence public policy.
APTs, cyber-espionage, and info-ops
Charming Kitten's BellaCPP: Kaspersky has published a report on BellaCPP, a C++ variant of BellaCiao, a .NET backdoor previously used in operations by Iranian APT group Charming Kitten.
Cloud Atlas: The Cloud Atlas APT is back with a new tool named VBCloud.
"This time, instead of an executable library to load malware modules, the group relied on the VBShower backdoor as the loader. Besides, they are now using a new module in their attacks: VBCloud. This collects and uploads system information and other data. These actions employ a variety of PowerShell scripts that enable the attackers to perform a range of tasks on the victim's system. VBCloud uses public cloud storage as a C2 server."
Paper Werewolf: Russian security firm BI.ZONE has published a profile on a new APT group it tracks as Paper Werewolf, also known as Goffee.
Rybar profile: OpenMeasures has published a profile on Rybar, a Russian media entity involved in the Kremlin's foreign disinformation campaigns. The company is particularly known for its involvement in supporting the Texas secession movement on right-wing social media sites.
TikTok info-ops: TikTok has published overviews of the influence operations it disrupted on its network during October and November. This includes info-ops that targeted the Romanian elections and political discourse in Armenia, Bangladesh, Indonesia, Moldova, the US, and Brazil.
Vulnerabilities, security research, and bug bounty
Windows EoP write-up: SSD Disclosure has published a write-up and PoC for CVE-2024-30085, an EoP vulnerability in the Windows Cloud Files Mini Filter Driver that Microsoft patched back in June.
Palo Alto neuters POC tool: Palo Alto Networks has silently patched an issue used by security researchers to dump cleartext PAN GlobalProtect VPN appliance passwords.
KEV update: CISA has updated its KEV database (twice) with two vulnerabilities that are currently exploited in the wild. This includes vulnerabilities exploited in BeyondTrust authentication solutions and the Acclaim Systems USAHERDS animal livestock management platform.
JWT algorithm confusion bug: PentesterLab researchers have found a new algorithm confusion vulnerability in the C implementation of the JSON Web Tokens internet standard.
"Algorithm confusion occurs when a system improperly verifies the type of signature used, allowing attackers to exploit the lack of distinction between signing methods. If the system doesn't differentiate between an HMAC signed token and an RS/EC/PS signed token during verification, it becomes vulnerable to this kind of attack."
ColdFusion pre-Xmas security patch: Adobe has released an emergency out-of-band security update to fix a ColdFusion vulnerability tracked as CVE-2024-53961 after proof-of-concept code was published online.
Apache SQLi: The Apache Foundation has released a security update for an SQL injection (CVE-2024-45387) in the Apache Traffic Control CDN platform codebase. It's a bad one, with a 9.9 CVSS score.
Sophos fixes SQLi: Security vendor Sophos has fixed three vulnerabilities in its firewalls, including a pre-auth SQL injection bug (CVE-2024-12727) that looks to be quite juicy.

Infosec industry
Spyware business moves to Barcelona: Haaretz reports that at least three teams of Israeli spyware developers have relocated offices to Barcelona, Spain, over the past few months.
AE-Paragon acquisition: Israeli officials say they have not yet approved the sale of spyware maker Paragon Solutions to US investment firm AE. The approval process, on both the US and Israeli sides, might take months.
Acquisition news: Swedish security firm Truesec has acquired threat intel provider Foresights.
OPA standard: The Open Policy Agent organization has released v1.0 of OPA, a new standard for Policy-as-Code development.
Threat/trend reports: Cloudflare, Dr.Web, IBM, Kaspersky, Northwave, Paul Hastings, and Red Canary have recently published reports and summaries covering various infosec trends and industry threats.
New tool—Krueger: IBM X-Force's Logan Goins has released Krueger, a .NET tool for remotely killing EDR using the Windows Defender Application Control (WDAC) utility.
New tool—SCCMHound: CrowdStrike has open-sourced SCCMHound, a tool to collect BloodHound session information from Microsoft Configuration Manager users.
New tool—BlackPill: The DualHorizon security research group has released BlackPill, a stealthy Linux rootkit made in Rust.
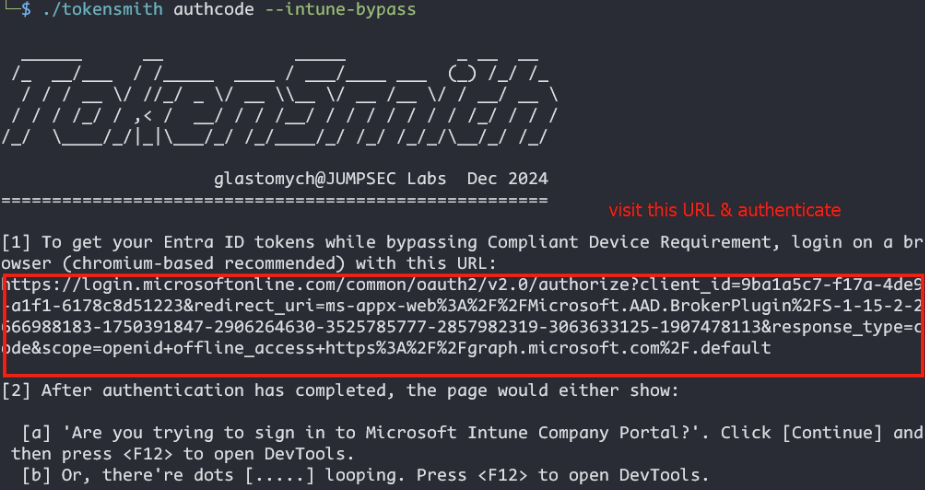
New tool—TokenSmith: Security firm JumpsecLabs has open-sourced TokenSmith, a tool to generate Entra ID access & refresh tokens on offensive engagements.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about the evolution of Russian cyber operations during its invasion of Ukraine.




