Risky Bulletin: Router APIs abused to send SMS spam waves
In other news: CISA reveals new collaboration model for state governments; South Korea raises cyber threat level after data center fire; Tile tracking devices leak their location.

This newsletter is brought to you by Authentik. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
A mysterious threat actor is abusing Milesight industrial cellular routers to send SMS spam, also known as smishing, to users in several European countries.
According to French security firm Sekoia, the campaign has been silently going on without detection since at least February 2022.
The attackers are targeting a feature of Milesight routers that lets admins configure to receive SMS alerts. Such a feature is common in industrial routers that connect remote equipment to a larger network via a cellular modem, with admins receiving alerts when the equipment connection goes offline and may not be in a state where it can be managed.
Sekoia believes the attackers are exploiting a 2023 vulnerability discovered by Bipin Jitiya, a security researcher and the founder of Cuberk Solutions.
Tracked as CVE-2023-43261, the vulnerability can leak the system logs of Milesight routers. Attackers can comb through the logs, find, and then crack encrypted admin passwords, which they can then use to connect to devices and abuse the SMS router API to send phishing messages to a desired phone number.
"There is no evidence of any attempt to install backdoors or exploit other vulnerabilities on the device. This suggests a targeted approach, aligned specifically with the attacker's smishing operations."
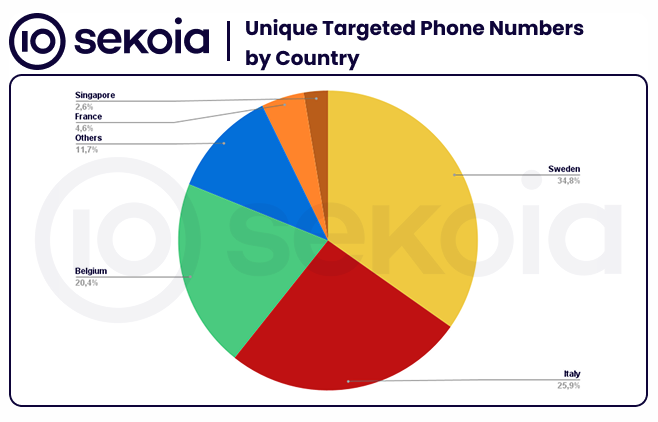
Most of the spam was sent to three countries—Sweden, Italy, and Belgium. Most of the SMS messages contained phishing links for government portals, financial, email, and postal services.
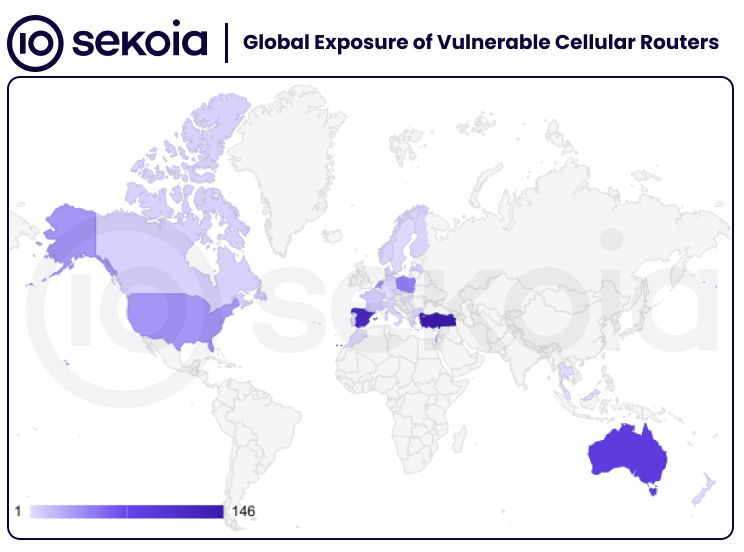
Sekoia says a scan of the internet has found more than 19,000 Milesight routers that have an SMS sending API. At least 572 of them have this API exposed on the internet without authentication, meaning the attackers wouldn't even need to exploit the 2023 bug to access it.
Risky Business Podcasts
The main Risky Business podcast is now on YouTube with video versions of our recent episodes. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
Asahi cyberattack: A cyberattack has disrupted several services at Japan's largest brewery. Call centers, orders, and shipment operations are down at the Asahi Group. The incident impacted only its Japanese business unit, and international operations are up and running. No ransomware group has taken credit for the attack so far.
Mockito malware incident: The Windows download link for the Mockito Java testing framework has redirected users to a malicious file. The link was allegedly modified on the project's wiki page more than three years ago. The Mockito project is the Java ecosystem's most popular unit testing framework, with over 15,000 stars on GitHub. [h/t c/side]
WestJet breach impacted passenger data: Canadian airline WestJet has finally confirmed that the hackers who breached its network in June got their hands on passenger data after all. [Additional coverage in GlobalNews]
FEMA breach: Hackers gained access to FEMA's Citrix environment in a security breach this June. The attackers allegedly abused a vulnerability known as CitrixBleed 2. They stole employee data for both FEMA and CBP staff. DHS head Kristi Noem fired 24 employees from the FEMA IT department over the breach last month. [Additional coverage in NextGov]
General tech and privacy
FTC sues Sendit app: The FTC has filed legal proceedings against the Sendit anonymous messaging app. The agency claims the app used fake accounts to message users and trick them into paying a subscription to see the sender's message. Sendit also allegedly failed to obtain parental consent before collecting the data of children under the age of 13.
France fines Samaritaine for hidden cameras: France's privacy watchdog CNIL has fined French department store chain Samaritaine €100,000 for installing hidden cameras inside smoke alarms in two of its warehouses without proper warning that employees were under surveillance.
Tech firms should be shielded from spyware liability: A US think tank argues that tech platforms that follow certain rules should be shielded from legal liability related to spyware attacks. The Atlantic Council says a safe harbor legal framework would encourage tech firms to aggressively expose spyware operations if they couldn't be sued back by surveillance vendors. The same framework would also protect the companies from lawsuits filed by spyware victims. The legal protections would apply to any tech firm that notifies victims, shares attack data, and patches exploited bugs.
Twitter is the most antisemitic network: A new CounterHate study found that Twitter is the go-to place for posting anti-semitic content and is failing to moderate even the most glaring hate speech.
Imgur blocks UK users over ICO investigation: Image-sharing website Imgur has blocked access for UK users. The site was expected to be fined for failing to implement age checks for UK users. The UK's privacy watchdog started investigating Imgur in March. [Additional coverage in the BBC]
Google deletes political ads history in the EU: Google has deleted its political ads archive for the EU region. The archive covered political spending, messaging, and targeting for 27 countries. According to The Briefing, the archive appears to have been deleted as Google has enforced a full ban on political ads in the EU.
F-Droid project could end: The F-Droid third-party app store says it may soon have to close down because of changes Google is forcing on the Android ecosystem. Starting next year, all Android apps installed on a device will have to come from a verified developer account. The new requirement will apply to all apps, regardless of how they are installed. Apps listed on the F-Droid store won't install unless their developers also register with Google, which is something most devs won't want to follow through, since that was the purpose of the F-Droid store to begin with.
Government, politics, and policy
CISA's new collaboration model with state governments: CISA will replace the role of MS-ISAC in the protection of state and local governments with a new collaboration model. The new agreement includes access to grant funding, no-cost tools, and CISA cybersecurity experts in regional centers. The agency also plans to hold bi-monthly calls with state and local officials to discuss cybersecurity defenses. CISA funding for MS-ISAC expired in September. [Additional coverage in StateScoop]
CISA says it won't be renewing its cooperative agreement with the MS-ISAC, which ends Sept. 30, and will hold bi-monthly cals to share "timely cyber defense updates" with state, local and tribal governments. www.cisa.gov/news-events/...
— Sam Sabin (@samsabin.bsky.social) 2025-09-29T20:20:13.538Z
Also: CISA lists its regional advisers as a source of federal support for state and local governments, but many of those advisers are gone, casualties of Trump's workforce purge. I've heard some regions have no advisers at all. www.cisa.gov/about/regions
— Eric Geller (@ericjgeller.com) 2025-09-29T20:12:42.324Z
Two-thirds of CISA workers could be furloughed: CISA will send two-thirds of its staff home if the US government shuts down on Wednesday. Around 890 employees out of CISA's estimated 2,500 workforce will remain on the job. According to CybersecurityDive, the rest would be furloughed until Congress passed new spending legislation. [Additional coverage in CybersecurityDive]
California has an AI safety law: California Gov. Gavin Newsom has signed an AI safety law, the first such law in the US.
South Korea raises cyber alert level: South Korea has raised its national cyber alert level following a fire at a state data center. The Caution level is the second in a four-tier system. Officials fear threat actors may take advantage of the outage of hundreds of government systems to launch cyberattacks. The government is in the process of moving to a new data center. [Additional coverage in the Korea Herald]
Afghanistan shuts down its internet: The Taliban government in Afghanistan has completely shut off the country's internet connectivity. More than 43 million people are unable to access the internet while the government tries to crack down on what it calls "immoral activities." The sudden shutdown is impacting both businesses and citizens, who are unable to communicate with family members. [Additional coverage in CNN]
⚠️ Update: #Afghanistan is now in the midst of a total internet blackout as Taliban authorities move to implement morality measures, with multiple networks disconnected through the morning in a stepwise manner; telephone services are currently also impacted
— NetBlocks (@netblocks.org) 2025-09-29T15:12:51.969Z
CISA and others release OT guidance: CISA, the UK NCSC, and cybersecurity agencies from five other countries have released joint guidance on securing ICS/OT systems.
Passkey server guide: The German government has posted a guide on implementing passkey support server-side, so more companies move to supporting it as the preferred 2FA method.
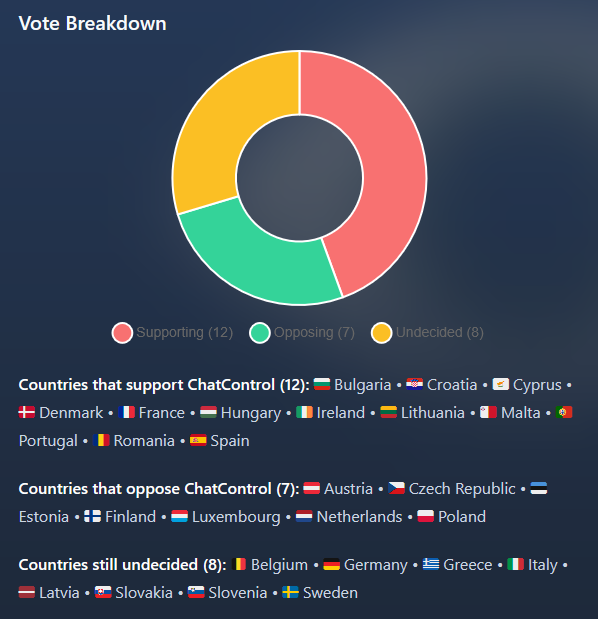
The Netherlands won't support Chat Control proposal: The Dutch government says it won't support Denmark's proposal for an EU Chat Control legislation to force tech companies to introduce encryption backdoors. The proposal is up for a vote on October 14. After initially opposing it, Germany now looks to lean towards a Yes vote.
Sponsor section
In this Risky Business sponsor interview, Authentik CEO Fletcher Heisler talks to Tom Uren about how identity providers (IdP) are fundamental to everything an organisation does. He explains how organisations are making themselves resilient by managing their redundancy and failover options.
Arrests, cybercrime, and threat intel
Silly phishing campaign: Censys has spotted a phishing campaign targeting crypto-wallet owners that misunderstood how the robots.txt file works and thought that by adding the phishing pages to the file, security scanners would not be able to see and detect them.
Lunar Spider ops: The DFIR Report team has published a report on Lunar Spider, a cybercrime group believed to have developed both IcedID and Latrodectus.
Detour Dog group: Security firm Infoblox filed a complaint against domain registrar WebNIC earlier this year for refusing to take down malicious domains. The domains were being used by a threat actor named Detour Dog to redirect hijacked web traffic to malware and online scams. The complaint resulted in an official ICANN investigation of WebNIC operations in July. When security firms sinkholed the malicious domain, Detour Dog registered new domains with WebNIC that the company again refused to take down.
UNC6040 profile: Google's Mandiant team has published more details on the social engineering tactics used by UNC6040, a group that calls employees at large companies, poses as their IT support, and tries to compromise accounts for initial access. The group is behind a recent hacking streak that hit Salesforce enterprise accounts.
PQC adoption: Forescout says that a quarter of all OpenSSH and 8.5% of all SSH servers now support post-quantum cryptography.
Malware technical reports
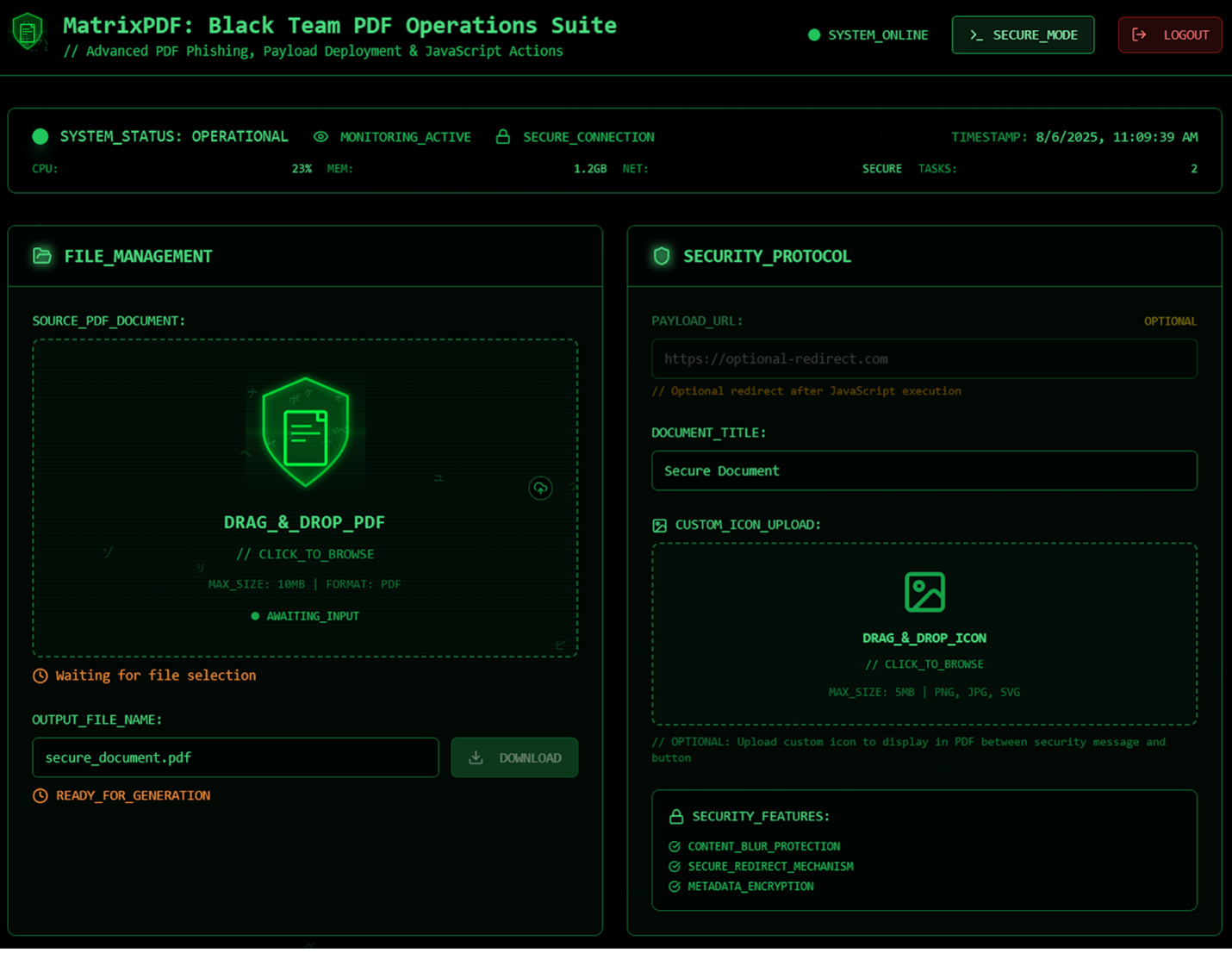
MatrixPDF: Varonis says threat actors are selling access to MatrixPDF, a tool that lets them quickly assemble malicious PDF files that can redirect users to malware or phishing sites.
XiebroC2: AhnLab researchers have spotted the open-source XiebroC2 framework being deployed on hacked MS-SQL servers, typically compromised via brute-force attacks.
Datzbro RAT: ThreatFabric has discovered a new Android RAT named Datzbro. It's currently being distributed via social engineering campaigns.
New Klopatra banking trojan: A new Android banking trojan has already infected more than 3,000 devices since its launch in late August. Most of the victims are located in Italy and Spain. According to security firm Cleafy, the new Klopatra trojan is an extremely advanced malware that appears to be the work of a Turkish-speaking group.
"Its main innovation—adopting commercial-grade protections like Virbox, combined with an architecture based on native code—marks a turning point in the Android malware landscape. This approach, once the domain of desktop malware, is now a reality in the mobile world and serves as a harbinger of future trends. It is likely that other criminal groups will follow suit, making detection and analysis increasingly complex and resource-intensive."
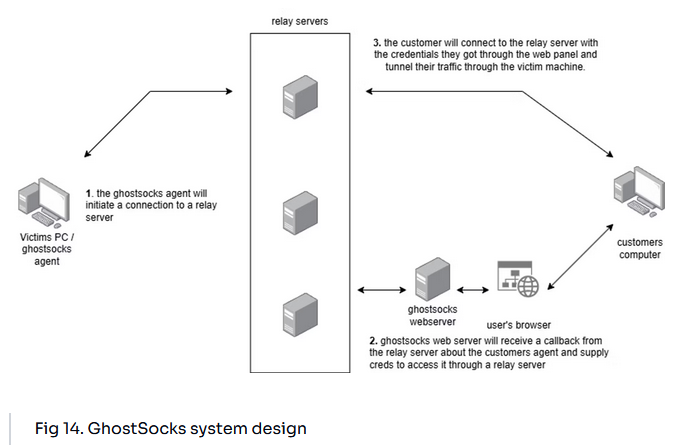
GhostSocks residential proxy network: Synthient looks at GhostSocks, a residential proxy network advertised to cybercrime groups.
Sponsor section
Authentik is an open-source identity provider that is also offered with paid enterprise features. In this demo, CEO Fletcher Heisler and CTO Jens Langhammer walk Risky Business host Patrick Gray through an overview and a demo of the technology.
APTs, cyber-espionage, and info-ops
Iranian port hacking operations: A team of academics has published a paper on Iranian cyber operations targeting ports and maritime infrastructure in the Middle East over the past three years.
"The research demonstrates that Iranian cyber campaigns combine sophisticated technical approaches—including custom malware deployment, spear-phishing, and SCADA system exploitation—with influence operations to achieve immediate disruption and longer-term strategic goals. [...] Our findings suggest that, though technically sophisticated, Iran's cyber operations targeting maritime infrastructure may ultimately undermine China's BRI objectives of stable trade routes and regional economic integration."
Storm-1516 post-Moldova elections: NewsGuard looks at various false rumors started by a Russian influence operation tracked as Storm-1516 and designed to make it look like the recently concluded Moldovan elections were fraught with fraud on the pro-EU side.
TikTok info-ops reach Czechia: Czech researchers have discovered a TikTok influence operation involving hundreds of anonymous TikTok accounts. The network is promoting pro-Russian and anti-EU narratives and supporting far-right parties ahead of the Czech Republic's parliamentary election this weekend. The operation is nearly identical to the same tactics Russia used ahead of Moldova and Romania's elections this and last year. Romania eventually canceled and re-did its election, citing Russia's meddling. [Additional coverage in Reuters]
DPRK IT worker schemes: Okta's security team looks at how North Korean remote IT worker schemes are impacting companies across the globe.
Phantom Taurus: A new Chinese cyber-espionage group has spent the past two and a half years targeting government and telecommunications organizations in Africa, the Middle East, and Asia. The Phantom Taurus group has sought to obtain sensitive non-public information from hacked email servers. The group's main targets have been ministries of foreign affairs, embassies, geopolitical events, and military operations. Phantom Taurus operations frequently coincide with major global or regional events.
Vulnerabilities, security research, and bug bounty
Broadcom patches VMware zero-day: Broadcom has released security updates to patch an actively exploited VMware zero-day. Tracked as CVE-2025-41244, the zero-day allows attackers who have gained access to VMware Tools and VMware Aria Operations to gain admin access over the platforms. Security firm NVISO has linked the attacks to UNC5174. Google previously identified the group as a cyber contractor for China's Ministry of State Security. [h/t RVD]
Supposed SonicWall 2FA bypass campaign: Arctic Wolf claims to have spotted a SonicWall hacking campaign in July that gained access to devices protected by 2FA. The devices were later infected with the Akira ransomware. The group has been routinely targeting SonicWall systems over the past year. The report is unclear on how the attackers bypassed 2FA.
Tile tracking devices leak their location: Tile location trackers leak sensitive information that can allow threat actors to track a device's location. The devices leak MAC addresses and unique device IDs. The information is unencrypted and can be collected with a simple radio antenna. This same information is also sent unencrypted to Tile servers, giving the company or anyone who intercepts the data the ability to track all of the company's customers. Researchers reported the issues to Tile last November, but the company stopped responding in February. [Additional coverage in WIRED]
KEV update: CISA has updated its KEV database with five vulnerabilities that are currently exploited in the wild. This includes a 2021 Adminer bug, a Cisco zero-day from last week, a recent Fortra GoAnywhere bug patched in September, a Libraesva ESG zero-day disclosed last month, and a rare Sudo bug. Yes, that Sudo!
Made-up Linux vulnerabilities: Looks like some Linux eBPF vulnerabilities presented at this year's DEFCON are made-up AI slop.
Pre-auth vulns in TRUfusion Enterprise: RCE Security has found four pre-auth vulnerabilities in TRUfusion Enterprise, a system for sharing CAD and PLM data inside companies.
Gemini Trifecta vulnerabilities: Tenable researchers have found three vulnerabilities in Google's Gemini AI assistant that could have leaked user data and manipulated browser history to trick users into visiting malicious sites.
WD security update: Western Digital has released a firmware update for its NAS devices to fix an RCE vulnerability.
Apple security updates: Apple has patched most of its products for a bug that allowed attacks using malicious fonts.
Firefox security updates: Mozilla has also released an update to patch two security bugs in Firefox.
Infosec industry
Threat/trend reports: Cobalt, the Dutch Ministry of Economic Affairs, ECS, Forescout, and ISACA have recently published reports and summaries covering various threats and infosec industry trends.
New tool—Ouroboros: Software engineer Hexorg has released Ouroboros, a decompiler built in Rust that recovers high-level structure from binaries.
New tool—Wyrm: Security researcher Flux has released Wyrm, a post-exploitation framework for red team operations written in Rust.
Risky Business podcasts
In this edition of Seriously Risky Business, Tom Uren and Amberleigh Jack talk about how the funnel that turns kids into cyber criminals has evolved over the last decade. Cybercrime's reach has broadened, and it is more lucrative and more violent.
In this edition of Between Two Nerds, Tom Uren and The Grugq discuss the power of cyber.




