Risky Bulletin: Researcher scores $250,000 for Chrome bug
In other news: WinRAR patches zero-day; new TETRA comms protocol vulnerabilities; researcher gains access to Microsoft's internal network for fun and no profit.

This newsletter is brought to you by Yubico. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
Google has awarded a massive $250,000 reward to a bug bounty hunter for discovering a novel sandbox escape in the company's Chrome web browser.
The bug was reported in April and patched a month later, in May, with fixes also going out to the other Chromium browsers, such as Edge, Opera, Vivaldi, Brave, and others.
Tracked as CVE-2025-4609, the vulnerability resides in the ipcz library of Mojo, a Chrome component for managing how the browser's internal processes talk to each other.
A researcher named Micky found a way to manipulate internal Chrome processes and duplicate the browser's own parent process to run malicious code in the duplicate.
Micky said he was inspired by a previous Chrome bug from March, CVE-2025-2783, a zero-day exploited in the wild by the TaxOff APT in attacks targeting Russian organizations.
Even if the bug wasn't completely original or an RCE (remote code execution) attack, Google said it awarded the researcher a massive payout because it was still "a very complex logic bug," and the bug report also included a detailed write-up and functional PoCs.
The reward is one of the highest bounties paid by Google as part of its bug bounty program, behind only a $605,000 reward it paid in 2022.
Risky Business Podcasts
The main Risky Business podcast is now on YouTube with video versions of our recent episodes. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
Pakistan Petroleum stops ransomware attack: A major Pakistan oil and gas exploration firm, Pakistan Petroleum, says it suffered a ransomware attack but was able to quickly contain the hack. The attack allegedly involved a new ransomware strain named Blue Locker. [Additional coverage in the Daily Times PK]
OAIC sues Optus: The Office of the Australian Information Commissioner (OAIC) has sued local telco Optus for a September 2022 breach that exposed the personal data of 9.5 million customers.
US Courts breach: US Courts, the agency in charge of the DOJ's case management system, has confirmed a recent breach and said it was taking steps to improve its cybersecurity.
CrediX disappears after crypto-heist: The CrediX DeFi platform has disappeared from the internet after a hack last week. The platform deleted its social media accounts and took down its website. The platform was hacked on August 4, when an alleged attacker took control of an admin wallet and stole almost $4.5 million worth of assets. CrediX promised to reimburse users before its accounts went offline. [Additional coverage in The Block]
General tech and privacy
Android FYI: If you want to use fast charging on Android 16 with Advanced Protection enabled, you'll need to unlock your device before starting a phone charge going forward, per Android Authority.
Microsoft sued over Windows 10 EOL: A California man has sued Microsoft over its plans to discontinue Windows 10 in October this year. Plaintiff Lawrence Klein claims the Windows 10 End-of-Life is part of Microsoft's plans to monopolize the generative AI market. Klein says Microsoft is using forced obsolescence to force users to Windows 11, which comes preinstalled with the company's genAI tools. [Additional coverage in CourtHouseNews]
Microsoft to block FPRPC in M365 apps: Microsoft will block the FrontPage Remote Procedure Call protocol, aka FPRPC, in Microsoft 365 apps starting in late August.
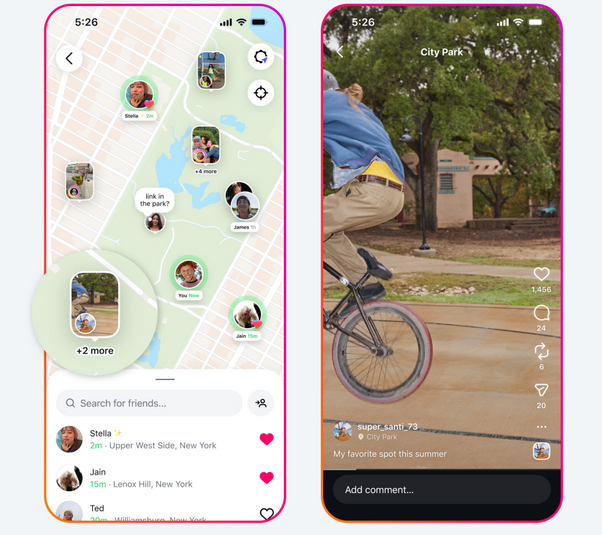
New Instagram Map feature: Instagram has released a new feature that allows users to share their location with their followers. The Instagram Map feature was released last week and is turned off by default. Posts from followed accounts are listed on a map with extremely precise locations. The platform had a similar feature around ten years ago, before it was discontinued following harassment and stalking complaints.
Government, politics, and policy
EMFA enters into effect: An EU law meant to protect journalists against spyware and surveillance entered into effect last week. The European Media Freedoms Act was adopted in early 2024 after years of deliberations. Six press freedom organizations say the legislation is ineffective and doomed to fail because most EU governments have not adopted nor have immediate plans to adopt it at the national level. [Additional coverage in The Record]
Clearview and Palantir coming to Germany: According to new proposed legislation, the German government intends to allow police to use AI tools from Clearview and Palantir to create biometric databases designed to fight crime. [Additional coverage in Netzpolitik]
UK used facial recognition on passport DB: Two UK privacy groups—Big Brother Watch and Privacy International—say the UK government has allowed police forces to deploy and use facial recognition software on the country's passport photo and immigration databases. Searches for this data went from 2 in 2020 to 217 in 2023.
Russia prepares foreign cloud ban: The Russian government plans to prohibit large Russian corporations from storing the personal data of Russian citizens on foreign clouds. The ban is expected to come into effect in September 2027. It will not apply to individuals and small and medium-sized companies. [Additional coverage in Vedomosti]
Sponsor section
In this Risky Business News sponsor interview Tom Uren talks to Derek Hanson, Yubico’s Field CTO about making account recovery and onboarding for employees phishing-resistant. They also discuss the problems and opportunities of syncable passkeys.
Arrests, cybercrime, and threat intel
Ghanaian scammers extradited to US: Four Ghanaian nationals were extradited to the US to face charges for their role in a massive scam operation. The four allegedly stole more than $100 million using romance and BEC scams. If found guilty, the four face up to 75 years in prison, each.
Scammers detained in Northern Thailand: Thai police have detained 18 Chinese nationals operating a scam call center in the city of Chiang Mai. The call center targeted other Chinese speakers and operated for three months from a rented house. According to the Bangkok Post, all suspects tried to flee, and eight were injured after jumping from the house's second floor.
Scammers detained in the Philippines: The Philippines Army and Bureau of Immigration detained 20 Chinese nationals who were operating a crypto scam center in Pasay City. [h/t DMonster]
Russia opens first "dropper" case: Russian authorities have opened the country's first investigation for the crime of "dropper." The term refers to an individual who manages money mules. A Moscow man was charged with paying intermediaries to open bank accounts in their names that were later used to store or launder stolen funds. Russian police tracked down the suspect after one of the money mules took advantage of a new law that offers immunity for collaborating with authorities.
US goes after DPRK workers: The Justice Department is trying to claw back $1 million worth of crypto stolen from a US company last year by three North Korean IT workers. [h/t CourtWatchNews]
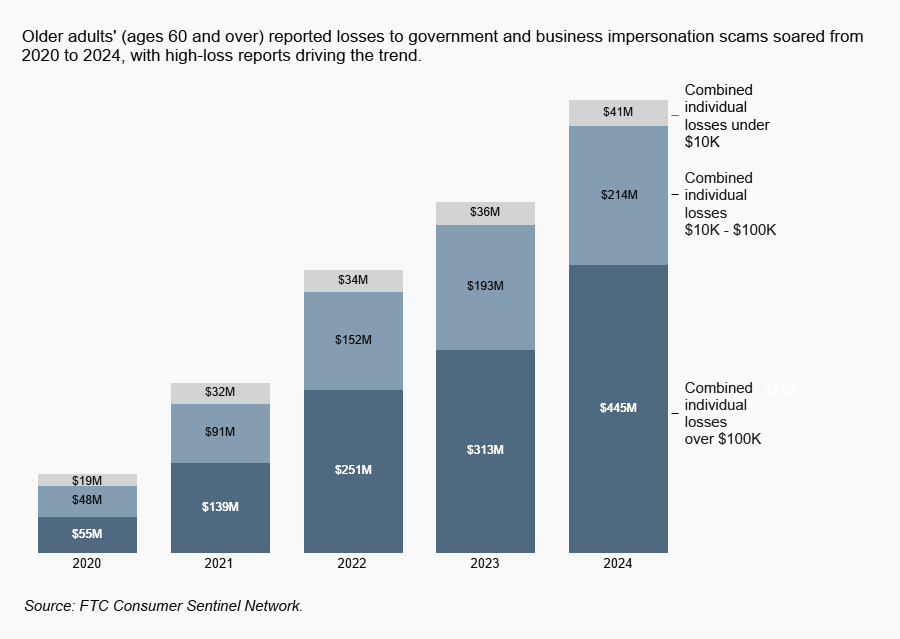
Elderly scam losses in 2024: Old and retired Americans lost $700 million to scams last year. The number skyrocketed from $120 million in 2020, according to FTC stats. Older adults lose significantly more money to scammers than younger people, who tend to lose smaller sums.
GenAI abuse in Brazil: Zscaler has spotted Brazilian cybercrime groups abusing GenAI services to improve their phishing capabilities.
RubyGems campaigns steal creds: A threat actor uploaded more than 60 malicious packages to the RubyGems package repository. The libraries posed as automation tools but stole login credentials from social media and marketing tools. The campaign has been running since at least March 2023. According to Socket Security, the packages were downloaded more than 275,000 times.
ToolShell exploitation: Trustwave looks at the recent attacks on SharePoint servers using the ToolShell exploits. The final payloads spotted by the company included minimal ASP.NET-based web shells, such as China Chopper and AntSword.
Exchange on-prem-to-cloud attack exposure: Almost 30,000 Microsoft Exchange email servers are missing a hotfix for a recent vulnerability that allows attackers to escalate access from on-prem servers to online cloud environments—CVE-2025-53786—per the Shadowserver Foundation.
Embargo made $34mil: The Embargo ransomware gang has made more than $34 million from ransoms since April last year. The group is believed to be a rebrand of the old AlphV operation that was shuttered by authorities earlier that year. Unlike its predecessor, Embargo has kept a low profile and avoided hitting large targets.
BlackSuite takedown: ICE's Homeland Security Investigations has formally confirmed its role in the takedown of the BlackSuit RaaS, a rebrand of the old Royal gang. The agency says the group, under both of its names, has extorted a whopping $370 million from victims since 2022.
Kaseya hacker profile: Threat intel firm Analyst1 has published a profile of Yaroslav Vasinskyi, a Ukrainian national and member of the REvil gang that hacked Kaseya in 2021. He is currently serving a 13-year prison sentence in the US. The profile also includes a rare interview with Vasinskyi.
ShinyHunters (UNC6240) interview: DataBreaches.net has posted an interview with ShinyHunters, a group involved in extorting companies that had their Salesforce accounts hacked. Per Google, the group is different from UNC6040, which does the actual hacking. DataBreaches.net also claims this is the same person whom they spoke to for years. This suggests that French authorities appear to have arrested some low-level members of the ShinyHunters group and not its suspected leader.
XSS takedown reaction: Threat intelligence analyst g0njxa has published an analysis of the takedown of the XSS[.]is hacking forum and how mods and the community reacted online.
New BlackNevas ransomware: The Trial Recovery ransomware appears to have rebranded as BlackNevas.
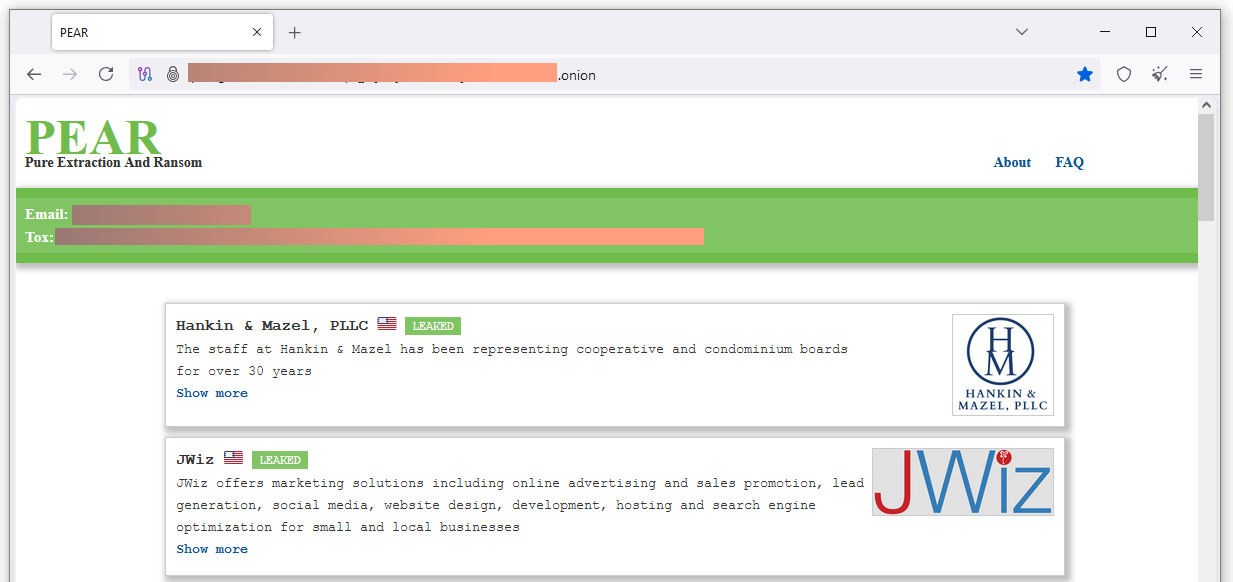
New Pear ransomware: A new ransomware group named Pear launched a leak site last week, which is already listing 18 victims. The name apparently stands for Pure Extraction And Ransom.
Malware technical reports
Efimer Stealer: Kaspersky has spotted a new infostealer spread through phishing campaigns, hacked sites, and malicious torrents. The Efimer Stealer appears in its early phases of development because it appears to target crypto wallets only, with no support for dumping browser creds.
Odyssey Stealer: Forcepoint is seeing ClickFix campaigns tailored for macOS users that deploy the Odyssey Stealer.
CastleLoader: The PolySwarm team has published an analysis of CastleLoader, a new malware loader that emerged this year. This appears to be what IBM calls CastleBot.
Buhtrap: Russian document management platform DiaDoc says hackers are using its brand to distribute the Buhtrap trojan. [h/t Oleg Shakirov]
Qilin ransomware: DarkAtlas has published a report on the operations of the Qilin ransomware group and the recent accusations of an "exit scam."
"The rapid succession of events following the disappearance of RansomHub and the subsequent rise—and apparent turbulence—within Qilin's operations underscore the dynamic volatility of today's ransomware ecosystem. The absorption of RansomHub's infrastructure by DragonForce signaled a major realignment of power, yet it also spotlighted just how fragile these illicit enterprises can be. The internal chaos and alleged exit scam within Qilin, amplified by leaks and public warnings from disgruntled affiliates like "hastalamuerte," reveal deep fissures in trust and operational security among ransomware collectives, further compounded by active interference from law enforcement and rival groups."
Sponsor section
In this sponsored interview, Patrick Gray talks to Yubico's COO and President, Jerrod Chong, about a new YubiKey feature: pre-registration. You can now ship pre-registered Yubikeys to your staff, so you don't need to rely on your staff to enrol them. They've achieved this with really slick Okta and Entra ID integrations.
APTs, cyber-espionage, and info-ops
APT-C-09 (Patchwork): Qihoo 360 researchers have published a report on a spear-phishing campaign conducted by APT-C-09, a suspected Indian APT, against Pakistan military and telecommunications targets.
Vulnerabilities, security research, and bug bounty
WinRAR patches zero-day: The WinRAR file archiver has patched an actively exploited zero-day. Tracked as CVE-2025-8088, the vulnerability is a path traversal vulnerability that can allow attackers to control the file extraction parameters. Security firm ESET discovered and reported the zero-day. Russian security firm BI.ZONE appears to have linked the attacks to the Paper Werewolf APT group, also known as Goffee.
2TETRA:2BURST vulnerabilities: Security researchers have broken the Terrestrial Trunked Radio communications protocol for the second time. Also known as TETRA, the protocol is widely used by law enforcement, military, and critical infrastructure operators. Security firm Midnight Blue first cracked TETRA in 2023. It found new vulnerabilities in the protocol's end-to-end encrypted version that was supposed to replace the old and insecure one. The new vulnerability is similar to the original one. It exploits scenarios where the protocol compresses its encryption key into a smaller and weaker one, allowing for traffic decryption. [Additional coverage in WIRED]
Chrome to Linux RCE: Google researchers have exploited a new Linux kernel feature (MSG_OOB) from within the Chrome web browser. From the Red Hat advisory on CVE-2025-38236:
"This vulnerability allows a local attacker to escalate privileges, especially if the kernel address layout information, such as kernel address space layout randomization (KASLR), is exposed through freed memory."
Microsoft NLWeb path traversal: Security researcher Aonan Guan found an unauth path traversal (aka the infamous /.. bug) that allowed him to gain access to sensitive files from the backend of NLWeb AI web apps.
Researcher gains access to Microsoft's internal network: A security researcher has gained access to over 20 Microsoft internal services. Eye Security's Vaisha Bernard gained access to systems that managed Copilot, Bing, Azure APIs, and even Microsoft billing. Bernard says he exploited an Entra ID OAuth misconfiguration that was common among all the Microsoft systems. He even gained access to a system that could approve his own bounty payouts. Microsoft wasn't amused (and professional), though. From Vaisha's blog post:
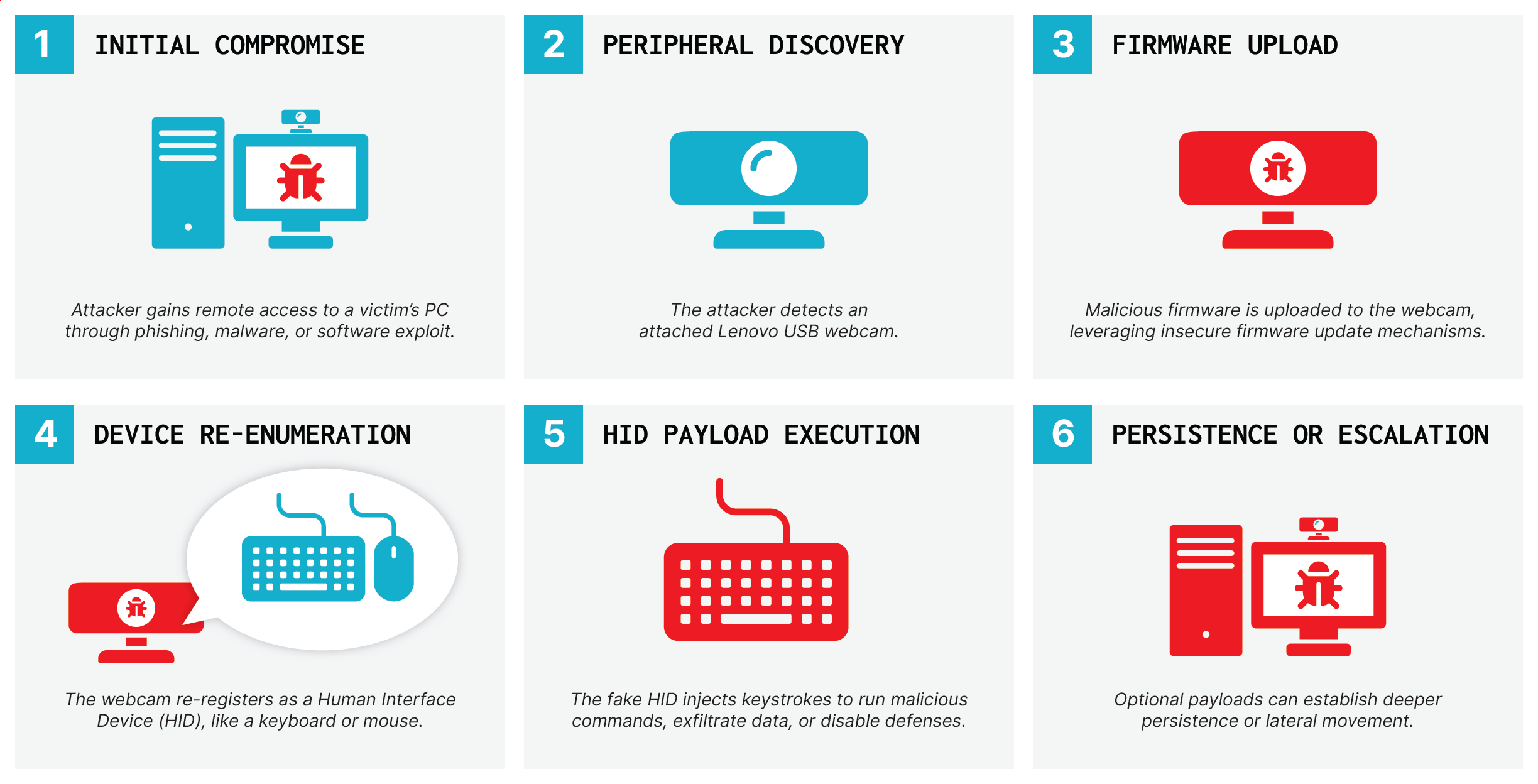
Webcams turned into BadUSB devices: Eclypsium researchers have developed BadCam, an attack that hijacks the firmware of Lenovo Linux-based webcams to turn them into classic BadUSB devices that can pose as a local keyboard and inject malicious keystrokes.
Apple Intelligence security review: Lumia Security has found some issues about how Apple Intelligence handles some data and how some files are sent to Apple servers without consent and not to its Private Cloud Compute infrastructure.
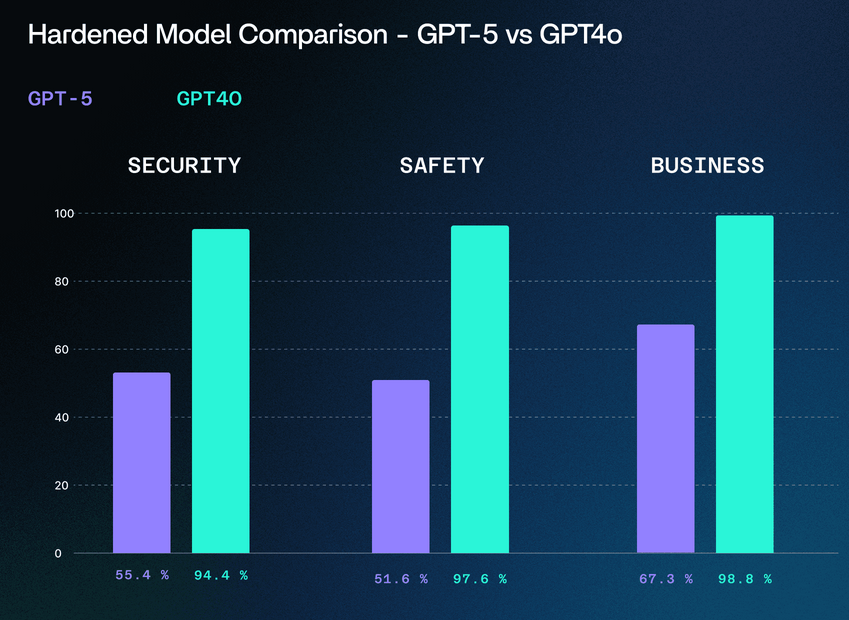
GPT-5 security review: A security review of the new OpenAI GPT-5 model found a downgrade in security and safety features compared to the company's previous release.
Infosec industry
Threat/trend reports: Check Point, CyFirma, QiAnXin, and ThreatMon have recently published reports and summaries covering various infosec trends and industry threats.
DEF CON Franklin: A group of white-hat hackers has volunteered to help protect the water systems of small US municipalities. The DEF CON Franklin team will offer no-cost support on network mapping, password protocols, and OT assessments. The group has already deployed volunteers across four US states (Indiana, Oregon, Utah, and Vermont) as part of an initial pilot program.
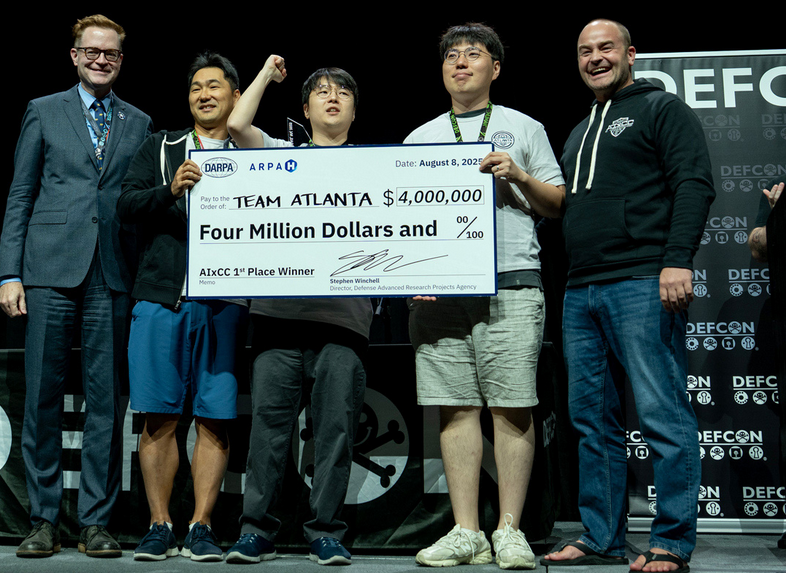
AIxCC winners announced: Team Atlanta has won DARPA's AI competition. The AI Cyber Challenge (AIxCC) contest took place over two years, and the final took place over the weekend at the DEF CON security conference. The winning team is made up of experts from Georgia Tech, Samsung, Pohang University, and the Korea Advanced Institute of Science & Technology. Security firms Trail of Bits and Theori finished second and third. The top three teams will receive $4 million, $3 million, and $1.5 million, respectively.
MITRE fires CTID leadership: The MITRE Corp has fired the leadership of the Center for Threat-Informed Defense. The CTID builds tools and resources on top of MITRE's ATT&CK framework and is comprised of members from all over the infosec community.
New tool—Buttercup: Security firm Trail of Bits has open-sourced Buttercup, a Cyber Reasoning System (CRS) developed for the AIxCC (AI Cyber Challenge). It is designed to find and patch software vulnerabilities in open-source code repositories.
New tool—RPC-Racer: Security firm SafeBreach has released RPC-Racer, a tool to launch rogue RPC interfaces and find vulnerable RPC interfaces.
New tool—BeaconatorC2: Security researcher Mike Manrod has open-sourced BeaconatorC2, a framework for red teaming and adversarial emulation.
New tool—Finch: Security researcher Adel Ka has open-sourced Finch, a fingerprint-aware TLS reverse proxy that can be used to create visitor profiles and ban misbehaving bots.
New tool—ChromeAlone: Security firm Praetorian has released ChromeAlone, a tool to transform Chromium browsers into a C2 framework and implant.
New tool—Claude Code Security Reviewer: Anthropic has released Claude Code Security Reviewer, a GitHub action to automate code reviews with its Claude AI agent.
New tool—Pompelmi: Computer engineering student Tommaso Bertocchi has released Pompelmi, a Node.js component that can work as a YARA-based malware scanner for file upload forms.
New tool—WHfB-o365-Phishlet: Red teamer Yehuda Smirnov has released WHfB-o365-Phishlet, an Evilginx phishlet that downgrades the Windows Hello for Business authentication method for Office 365 phishing campaigns.
Risky Business podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq dissect the Belarusian Cyber Partisans hack of Russian airline Aeroflot. Despite the short-term impact, the airline will likely bounce back quite quickly. But it is still a big win for the Cyber Partisans.




