Risky Bulletin: Passkeys are phishable (but quite difficult through)
In other news: Undocumented commands found in ESP32 chips; US cuts EI-ISAC funding; hacker steals and then returns 1inch funds.

This newsletter is brought to you by GreyNoise. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
Security researcher Tobia Righi has pulled off what appears to be the first successful passkey phishing attack.
The phishing vector existed solely in mobile browsers and has now since been patched. Security updates have rolled out for all major browsers, such as Chrome/Edge (October 2024), Firefox (February 2025), and Safari (January 2025)—see CVE-2024-9956.
Righi's attack revealed that passkeys are not perfect, but his research also showed that passkeys are far superior to the old credential pair and classic multi-factor authentication solutions.
The attack was far more difficult to pull off and had a far more narrow scope than current web-delivered phishing kits, which you can host on any website together with a proxy server and even intercept MFA challenges.
Instead, Righi's technique required that an attacker place a hardware device within a victim's Bluetooth LE range, which is between 70 and 100m.
The device, which could be a tiny Raspberry Pi hidden in an attacker's backpack, would be used to host a custom web server that triggered a passkey authentication flow.
In the simplest explanation possible, an attacker within BLE range can trick a victim into using their passkey to log the attacker's (Raspberry Pi) device into their account.
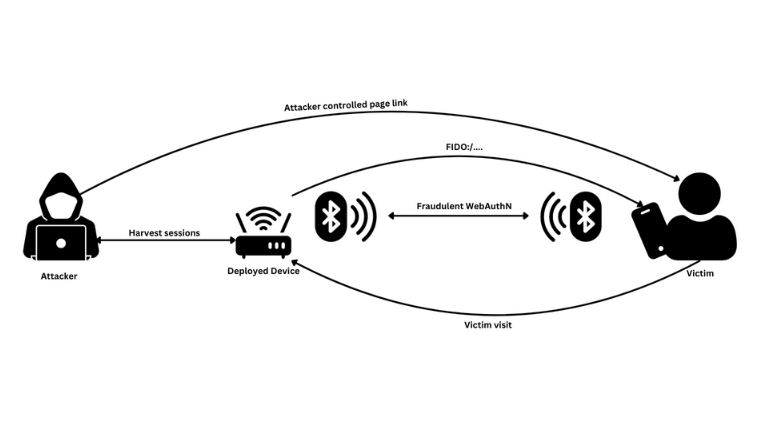
Let's go over one of Righi's examples to showcase how this was possible:
- An attacker deploys their rogue Raspberry Pi in a crowded airport.
- The attacker advertises a rogue free airport WiFi that requires users to log in using one of their social media accounts but via their passkeys instead of using a password.
- A victim chooses this option. The rogue BLE device, acting as an intermediary, initiates a WebAuthn request on the user's behalf.
- The attacker's BLE device would normally be prompted to scan a QR code, but Righi discovered you can extract a FIDO:/ link from the QR code and just redirect the victim to it instead.
- The victim is prompted to authenticate against the FIDO, not knowing that the successful authentication allows the attacker's device into their account.
- The attacker extracts the session data from the rogue BLE device and logs into the victim's account.
The bug here, and what browser vendors fixed, is that the FIDO:/ link was navigable and basically allowed to bypass the actual scanning of the QR code.
The victim is never aware of an intermediary hardware device that was doing a proxy authentication on their behalf.
This was basically a current MitM/AitM attack but carried out using hardware and adapted to passkeys and FIDO standards.
Righi says browser makers have now blocked FIDO:/ URI schemes from being navigable, which, in theory, should stop his version of the attack.
The researcher has open-sourced the server software that ran on the rogue BLE (Raspberry Pi) device to allow other researchers to evolve his technique and find new ways to exploit it.
Risky Business Podcasts
In this Risky Business Talks interview, we invited Will Thomas to talk about the recent leak of internal chats from the Black Basta ransomware group. Will is the co-founder of CTI community research project Curated Intelligence and author and instructor at the SANS Institute. Will walks us through the Black Basta leak and uses the group's attack on US healthcare provider Ascension to break down how the gang operated.
Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
HCRG tries to silence reporter: UK healthcare organization HCRG has tried to use a UK court order to remove two articles that covered its breach from the blog of an American healthcare security journalist. [Additional coverage in DataBreaches.net, TechCrunch, and DissentDoe's Mastodon thread]
Wizz Air attack: The Stormous ransomware gang has taken credit for an attack on Wizz Air Abu Dhabi, one of the airline's four major subsidiaries. No confirmation from the company, yet.
Presto cyberattack: American home appliance company Presto was the victim of a cyberattack on March 1. The incident has impacted the company's network and is causing manufacturing and product shipping delays. The company says it is currently restoring systems. The incident has the typical fallout of a ransomware attack but no major group has yet taken credit for the attack.
1inch crypto-heist: A hacker has stolen over $5 million worth of crypto assets from DeFi platform 1inch. The attacker returned the funds a day later after negotiating to keep $450,000 as a bounty. The hack was the result of a vulnerability in the company's smart contracts' resolvers. Because of the location of the bug, 1inch says the attacker stole from its own reserve, and user funds were never in danger.
US recovers some of the Larsen funds: The FBI has recovered $23 million worth of crypto stolen from Chris Larsen, the co-founder and executive chairman of the Ripple (XRP) cryptocurrency. The recovered funds are just a small part of the tokens stolen from Larsen in January of last year. The funds were estimated at over $110 million last year but are now worth over $700 million. Hackers stole the Larsen funds by first stealing password stores from password manager LastPass in 2022. Since the attack, the hackers have been slowly cracking passwords and emptying out crypto wallets. As of May 2024, over $250 million worth of crypto assets were stolen using the LastPass data. [Addition coverage in KrebsOnSecurity]
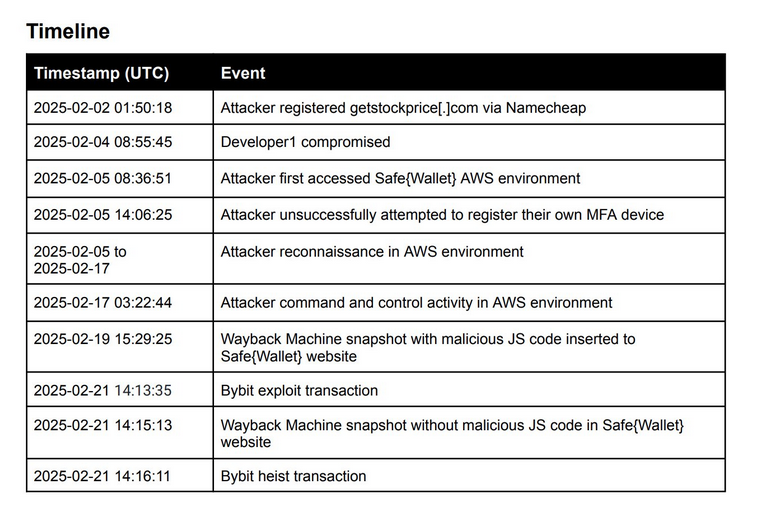
Bybit hack post-mortem: North Korean hackers compromised multi-signature wallet provider SafeWallet through a social engineering attack that targeted one of its developers. According to a new post-mortem report, the point of entry appears to have been a malicious Docker file that was executed on the employee's computer. The Docker file deployed malware that stole local credentials. The attackers then used the developer's AWS account to add malicious code to the SafeWallet infrastructure. The malicious code targeted a specific multi-sig wallet used by the Bybit cryptocurrency exchange. The attackers later stole $1.5 billion from the exchange.
General tech and privacy
Microsoft retires Publisher: Microsoft is retiring the Publisher app in October 2026. Publisher will be removed from the Microsoft 365 cloud service, and the desktop app won't receive any new security updates. The company says it's retiring the app because most of its features are now also available in Word and PowerPoint.
Firefox DMA results: Mozilla says it saw double the new installs on iOS after the EU enforced its DMA regulation and iOS users were allowed to choose their default browser.
Trump DOJ still wants to break up Google: The new Trump-appointed Department of Justice is continuing the work of the Biden-era DOJ and is still looking to break up Google and force the company to sell Android and Chrome to break up its monopolies over several markets. [Additional coverage in The Verge]
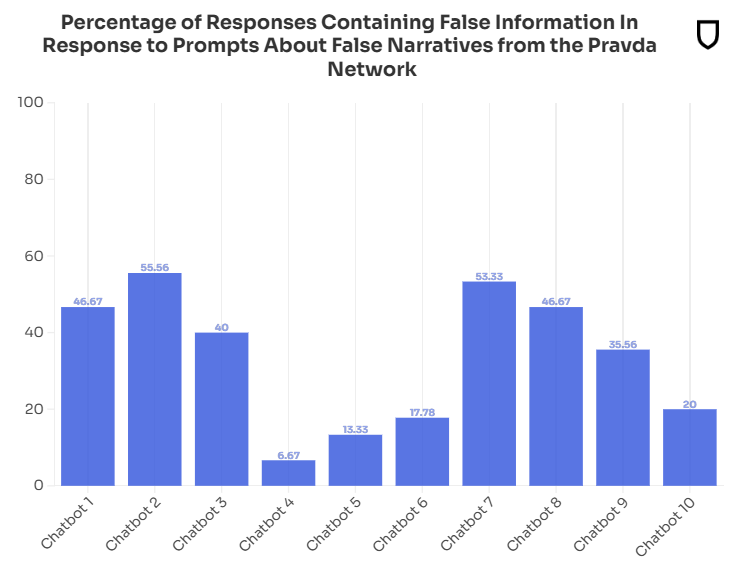
Russian propaganda is poisoning LLMs: The vast amount of Russian propaganda published online is poisoning large language models and AI chatbots. A disinformation research group says that one in three responses from the 10 leading generative AI tools are now returning pro-Kremlin falsehoods. The falsities can be traced back to a Russian disinformation network named Pravda. NewsGuard says the network's size exploded last year, which published over 3.6 million fake news articles across over 200 domains.
Government, politics, and policy
US cuts EI-ISAC funding: The US government has cut funding for the Elections Infrastructure Information Sharing & Analysis Center (EI-ISAC). The group was founded in 2018 to help state and local governments safeguard election infrastructure against cyber threats. The DHS terminated funding for EI-ISAC in February after the US government deprioritized safeguarding elections. [Additional coverage in CyberScoop]
US cuts Tallinn Mechanism funding: The US government has cut funding for the project that provided Ukraine with cybersecurity support. The US government, NATO, and EU allies launched the Tallinn Mechanism at the end of 2023 to help Ukraine protect IT systems against Russian hackers. The project received over €200 million in funding, half of which came from the US. [via Politico's Maggie Miller]
Canada's cyber threats: The Canadian government has updated a report on cyber threats to the country's democratic processes to add new threats coming from the proliferation of AI technology.
Responsible Cyber Behaviour: UK think tank RUSI has published a 121-page compendium of what the organization believes is responsible cyber behavior.
Swiss mandatory cyberattack reporting: Swiss companies will be required to report any attack on critical infrastructure starting on April 1 this year. Critical infrastructure operators must report the attack within 24 hours of discovery. The country's cybersecurity agency will provide support and alert other operators that may be affected.
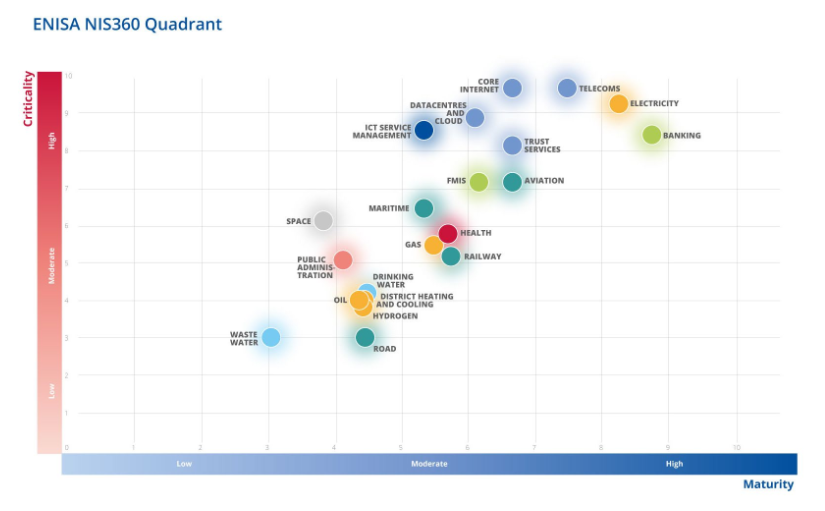
ENISA NIS360: The EU's cybersecurity agency has published its first-ever annual assessment of the cybersecurity maturity of NIS2 critical sectors.
"Electricity, telecoms and banking are the three most critical and most mature sectors that stand out above the rest. These sectors have benefited from significant regulatory oversight, funding and investments, political focus, and overall a robust public-private partnership."
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Andrew Morris, founder of security firm GreyNoise. Andrew talks about the major trends in mass internet scanning and exploitation, as per GreyNoise's yearly threat report.
Arrests, cybercrime, and threat intel
Notorious movie pirate arrested: The FBI has arrested a Memphis man for stealing DVDs and Blu-rays of blockbuster movies and selling them for a profit before they were officially released. Steven R. Hale stole the movies while an employee at a company that manufactures and distributes DVDs and Blu-rays for movie studios. Officials have linked Hale to the leak of famous movies from the Dune, Fast and Furious, and Marvel franchises.
Port-out scammer detained in Australia: Australian police detained a Melbourne man for more than 190 suspicious porting attempts. Officials believe the man tried to hijack 86 mobile numbers in order to bypass MFA and access banking accounts. The AFP says 44 of the numbers were successfully ported.
Garantex admin charged: The US DOJ charged two individuals behind the Garantex cryptocurrency exchange—Aleksej Besciokov, 46, a Lithuanian national and Russian resident, and Aleksandr Mira Serda (previously Aleksandr Ntifo-Siaw), 40, a Russian national and United Arab Emirates resident. Authorities seized the exchange last week and unsealed charges the next day, on Friday.
BOFH case: A US court has convicted a Texas man for writing and deploying malicious code that trashed his former employer's network after he was fired.
New npm malware: Two-hundred-forty-five malicious npm packages were discovered and taken down last week. Check out the GitHub security advisory portal for more details.
Cobalt Strike abuse went down: The number of unauthorized Cobalt Strike servers observed in the wild decreased by 80% over the past two years. Software company Fortra says it worked with Microsoft and Health-ISAC to take down cracked Cobalt Strike servers that were abused for malicious activity. Fotra's number does not align with a recent industry report, which found that Cobalt Strike servers had actually increased by over 65% over the past year. Security firm Recorded Future found that two-thirds of all offensive security tools used in malware attacks last year were Cobalt Strike.
Lumma Stealer updates: After an uptick in detection, the Lumma Stealer gang has pushed out a new version.
Toll scam campaign: Censys researcher Aidan Holland has found nearly 30k domains used for toll scams and phishing in the UK. His research comes as US cities are also seeing a spike in SMS spam warning of unpaid parking tickets.
ISP campaign: A threat actor is brute-forcing the server infrastructure of Chinese and US West Coast internet service providers. The attackers are compromising servers, stealing credentials, and then deploying cryptocurrency miners. According to Cisco's Splunk division, the campaign appears to originate from Eastern Europe.
Desert Dexter: Positive Technologies has discovered a new threat actor named Desert Dexter that is targeting MENA users with malware. The attacks use geo-political-themed ads on social media to redirect users to file-sharing sites. The ads were designed to originate from legitimate news outlets. The final payload is a version of the AsyncRAT.
Malware technical reports
Strela Stealer: Trustwave has published a technical report on Strela Stealer, an infostealer developed by Russian malware devs that has been on sale in underground forums since 2022.
LithiumWare ransomware: CyFirma has spotted a new ransomware strain named LithiumWare.
Akira ransomware: Chinese malware analyst Li Biaoming has published an analysis of the Akira ransomware's Linux payload.
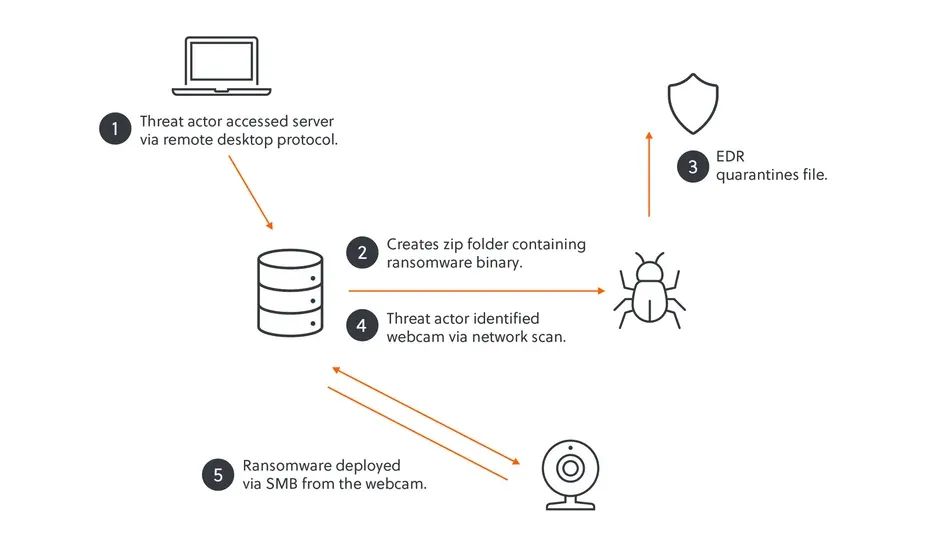
Ransomware attack via a webcam: The Akira ransomware group infected a webcam and used it as a safe spot to deploy its ransomware and encrypt a victim's network. The group went for the webcam after its attempt to deploy ransomware on Windows systems was detected and blocked by a local EDR. Security firm S-RM says Akira deployed its ransomware on the webcam's Linux operating system and then encrypted the entire network via SMB.
Sponsor section
Attackers are automating exploitation at scale, targeting both new and old vulnerabilities — some before appearing in KEV. Our latest report breaks down which CVEs were exploited most in 2024, how ransomware groups are leveraging mass exploitation, and why real-time intelligence is critical.

APTs, cyber-espionage, and info-ops
Lazarus attacks: South Korean security firm AhnLab has published a report looking at the Lazarus Group's network of hacked servers the APt has been using as impromptu C&C infrastructure.
Kimsuky watering hole attack: South Korean security firm Alyac has discovered a watering hole attack on the website of a reunification program at a large South Korean university. The company has linked the attack to North Korean APT group Kimsuky.
DPRK APT joins Qilin RaaS: A North Korean APT group named Moonstone Sleet joined the Qilin ransomware platform at the end of last month. The group has been observed deploying Qilin payloads during multiple intrusions. The group has a history of deploying ransomware for financial gains. Microsoft says Moonstone Sleet previously used its own custom ransomware before switching to Qilin.
TikTok info-ops summary: TikTok has published its monthly report on covert influence operations the company has spotted on its platform in January this year. The company has taken down almost 2,500 accounts involved in info-ops targeting audiences in Ecuador, Moldova, Georgia, Canada, and Chinese-speaking users living abroad.
Vulnerabilities, security research, and bug bounty
Espressif ESP32 undocumented commands: Security firm Tarlogic has discovered security flaws in Espressif ESP32 WiFi and Bluetooth chips. The chips contain hidden undocumented commands that can be abused by malware running on a device or via a wired connection. Tarlogic believes the undocumented commands may impact over one billion devices, such as phones, laptops, and IoT devices. The hidden commands cannot be exploited over-the-air, despite being in WiFi and Bluetooth chips. They appear to be part of some sort of production testing and development interface rather than backdoors.
ICONICS Suite vulnerabilities: PAN Unit42 researchers have found and helped patch five vulnerabilities in ICONICS Suite, an automation and monitoring solution for SCADA devices.
Python vulnerability: The Python Software Foundation is rolling out a fix for a CPython bug that mishandled commas while Unicode encoding email headers.
QNAP security updates: QNAP has released six security updates over the weekend to address issues in a bunch of its software.
NVIDIA security update: NVIDIA has released a security update to fix two vulnerabilities in its Hopper HGX GPU firmware.
China's vulnerability reporting: The number of companies reporting security flaws to Chinese authorities has gone up to 324 last year from 151 in 2023, according to SentinelOne's Dakota Cary.
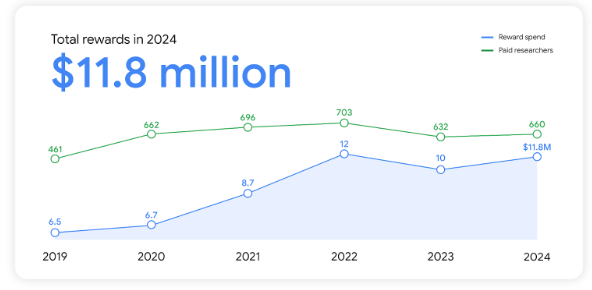
Google 2024 VRP: Google paid almost $12 million to security researchers last year for vulnerability reports across its products. The money went to 660 researchers, with the highest bounty last year being $110,000. Over half the money was paid out for Android ($3.3 million) and Chrome ($3.4 million) vulnerabilities. Since its inception in 2010, Google has paid over $65 million for vulnerability reports.
Infosec industry
New tool—GoStringUngarbler: Google's Mandiant team has released GoStringUngarbler, a Python CLI tool to automatically decrypt strings found in garble-obfuscated Go binaries.
New tool—RedExt: Security researcher ShadowByte has developed RedExt, a browser data analysis framework made up of a Chrome extension and a C2 server designed to red-team operations.
New tool—ShellOpsLog: Security researcher Dror Dvash has released ShellOpsLog, a command logger designed to automatically capture and log all executed commands, without their output, during red-team or other security engagements.
New tool—Sinkholed: DFIR specialist Mthcht has released Sinkholed, a collection of sinkholed domains.
New tool—Chirp: Security engineer Kozma " Solst/ICE" Prutkov has released Chirp, a tool to send and receive data via sound.
F1 sponsorship news: Cybersecurity firm Arctic Wolf has signed on to become a sponsor for the Alpine F1 team. The company replaces Mandiant as a sponsor. Over the last several years, cybersecurity firms have developed some sort of secret obsession with sponsoring F1 teams. Other security firms sponsoring F1 teams include Bitdefender with Ferrari, CrowdStrike with Mercedes, SentinelOne with Aston Martin, Darktrace with McLaren, and Keeper with Williams. [Additional coverage in Motorsport]
Threat/trend reports: Microsoft, ThreatMon, Wasabi, and Wordfence have recently published reports and summaries covering various infosec trends and industry threats.
Risky Business Podcasts
In this podcast, Tom Uren and Patrick Gray discuss how Starlink is providing an internet lifeline for scam compounds that have had their internet access cut by Thai authorities. Starlink has a very poor track record dealing with unauthorized use, but it is time for the company to develop the processes to keep on top of these problems.
In this edition of Between Two Nerds, Tom Uren and The Grugq take a deep dive into incident response reports from Chinese cybersecurity firms that attribute the hack of one of the country's top seven defense universities to the US National Security Agency.




