Risky Bulletin: nRootTag turns any Bluetooth device into an AirTag
In other news: VMware patches three ESXi zero-days; France debates encryption backdoors; a fifth of Bybit stolen funds are now untraceable.

This newsletter is brought to you by cloud security firm Prowler. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
A team of academics has found a way to remotely turn any Bluetooth-capable device into an AirTag tracker.
The technique is named nRootTag and abuses how Apple's FindMy network indexes AirTags and searches for tracked or lost devices.
In normal circumstances, when a user pairs an AirTag to their account, Apple takes the AirTag's Bluetooth signal and generates a cryptographic private-public key pair. When the user wants to find the AirTag's location, the FindMy network queries for the public key associated with that Bluetooth signal and then notifies the owner of its location.
The nRootTag technique works by using cloud computing power to infer what would be the private key of any public Bluetooth signal.
This allows attackers to take any device's Bluetooth signal, compute a possible private key, feed it to Apple's FindMy servers, and then get back that device's location.
"While Apple designs an AirTag to change its Bluetooth address based on a cryptographic key, an actor could not do this on other systems without administrator privileges. So instead of trying to modify the Bluetooth address, the researchers developed efficient key search techniques to find a key that is compatible with the Bluetooth address, making the key adapt to the address instead."
Computing the key takes a few minutes, but nRootTag can also be used almost instantly if attackers pre-compute private keys in rainbow hash tables.
The four-man research team from George Mason University says they've tested the technique and converted various devices into "fake AirTags" and tracked their location, such as Windows and Linux laptops, Android smartphones, IoT devices, and gaming consoles.
Apple released security patches in December for all its currently supported hardware devices. They will now ignore nRootTag-converted devices, but older Apple gear may still relay information to an attacker via the FindMy network.
The research team says nRootTag will slowly lose its accuracy as these older Apple devices are retired, but the attack remains possible for the time being.
Risky Business Podcasts
Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
POLSA cyberattack: Poland's space agency has been the victim of a cyberattack over the weekend. POLSA has disconnected its network from the internet while it investigates the incident. Authorities have not disclosed whether the attack was carried out by ransomware groups or an APT group. [Additional coverage in VOA]
Houston Symphony ransomware attack: The Houston Symphony has been hit by the Qilin ransomware, with the organization being listed on the gang's dark web leak site last week. [Additional coverage in Cybernews]
Hunters behind Tata: The Hunters International ransomware gang has taken credit for the attack at Indian mega corp Tata Technologies in January.
Toronto Zoo ransomware attack: The Toronto Zoo has published its final breach notification on a 2024 ransomware attack and the type of data compromised in the incident.
Beeline DDoS attack: Russian telecom company Beeline went down on Monday after a series of DDoS attacks. [Additional coverage in The Record]
A fifth of Bybit funds are now untraceable: Cryptocurrency exchange ByBit says that a fifth of the $1.5 billion stolen by North Korean hackers have been successfully laundered and are now untraceable. Two weeks after the hack, Bybit says it only managed to recover and freeze only 3% of the stolen funds. The rest of the funds have been laundered but are still traceable—for now. [Additional coverage in Crypto News]
General tech and privacy
UK to investigate TikTok: The UK's privacy watchdog is investigating Chinese social media company TikTok over how it collects children's data. The UK ICO will also analyze how TikTok recommends content to children's accounts. The agency has also announced similar investigations into Reddit and image-sharing site Imgur.
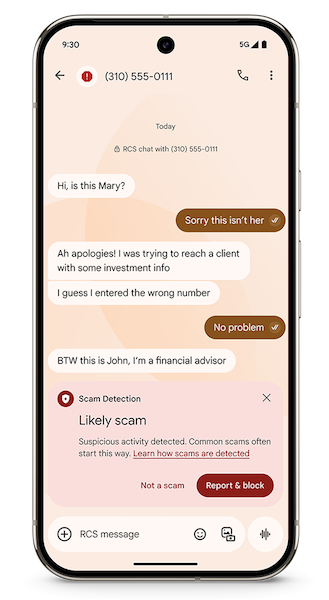
New Android AI scam detection: Google is rolling out two new AI-powered scam detection systems for Android devices. The two systems work by analyzing ongoing SMS and phone calls for signs that a benign call has turned into a financial scam. The system is meant to be used for scams where fraudsters approach victims using friendly conversations that turn malicious at a later date. Most scam detection systems usually scan the first few messages in a conversation.
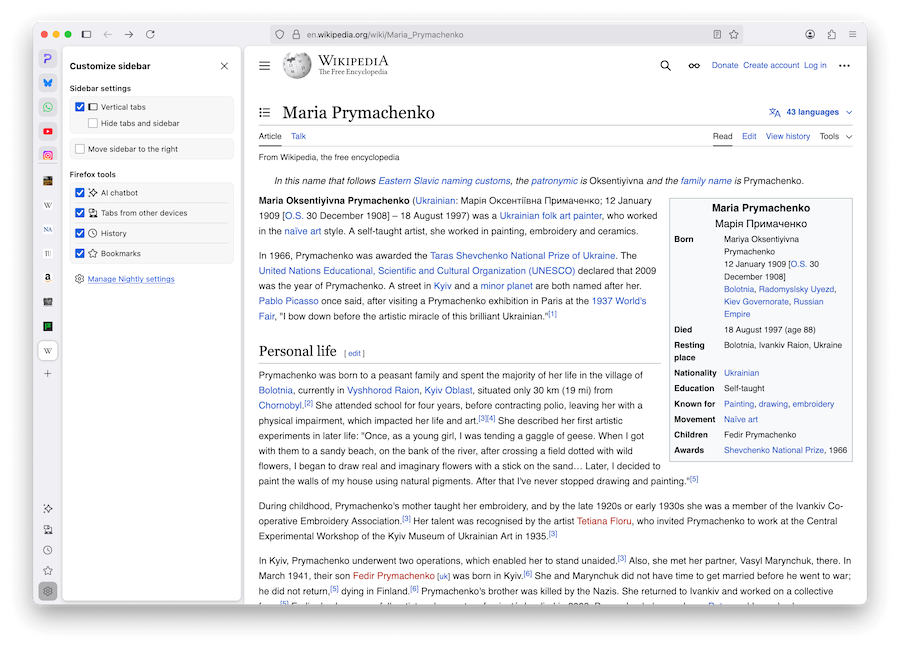
Firefox 136: Mozilla has released Firefox 136. New features and security fixes are included. The biggest feature in this release is the addition of an Opera-like sidebar and a new layout for vertical tabs.
Government, politics, and policy
France wants encryption backdoors: The French government has proposed an amendment to its narco-traffic law that would require encrypted communications providers to implement backdoors. The amendment advanced to the country's parliament in late January. The move is similar to another law proposed in Sweden but also applies to VPN service providers and not just instant messaging clients. Signal threatened to leave the Swedish market if the law passed and is likely to take a similar decision in France.
Trump administration re-enables money laundering: The US Treasury has suspended the Corporate Transparency Act, a law that required companies to reveal their real owners. The move came at the White House's request. According to financial experts, the suspension will bring back shell companies and "open the flood gates of dirty money" through the US, such as flows coming from drug gangs, human traffickers, fraud groups, and those juicy political bribes.
NIST layoffs: The US government has fired 73 NIST probationary employees as part of DOGE's "efficiency" rampage through government agencies. [Additional coverage in NextGov]
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Toni de la Fuente, founder and CEO of cloud security firm Prowler. Toni talks about his company's latest effort, the Open Cloud Security Movement, an initiative to get more cloud security vendors to open-source their core projects.
Arrests, cybercrime, and threat intel
UK sentences Bitcoin ATM operator: UK authorities have sentenced a man to four years in prison for operating a network of unlicensed Bitcoin ATMs. Olumide Osunkoya operated ATMs across 28 UK locations via a company called GidiPlus. The UK's financial watchdog says the network facilitated transactions of over £2.5 million through his ATMs. [Additional coverage in Reuters]
Catalan court gives green light to NSO indictment: A court in the Spanish region of Catalonia ordered this week that prosecutors indict three executives at Israeli spyware maker NSO Group. The court found that the three executives facilitated the unlawful surveillance of 63 Catalans following anti-government protests in the mid-2010s. The executives are NSO founders Shalev Hulio and Omri Lavie, and Yuval Somekh, a manager at NSO's parent company Q Cyber Technologies. The order also blamed Spain's Public Prosecutor's Office for trying to block the complaint and refusing to cooperate. Spanish authorities are believed to have used NSO's spyware against Catalan independence dissidents.
Black Basta admin arrested and released in Armenia: The suspected leader of the Black Basta ransomware group was arrested in Armenia in June of last year. Oleg Nefedov was released three days later after a judge failed to issue an order prolonging his arrest. Nefedov was identified as the leader of the Black Basta gang after internal chat logs leaked online last month. Armenian officials detained Nefedov based on an international arrest warrant issued by the US. [via Intel471]
US sanctions Nemesis market admin: The US Treasury has imposed sanctions on Iranian national Behrouz Parsarad. Pasarad was the administrator of a dark web marketplace named Nemesis. German authorities seized the market in March of last year. The market launched in 2021 and had more than 150,000 registered users and 1,100 seller accounts. It was primarily known for the sale of illegal drugs.
Larva-24005: AhnLab looks at a new threat actor tracked as Larva-24005 that is sending phishing emails to Japanese and South Korean organizations.
UK crypto fraud: Kent Police in the UK says nine victims lost £1 million worth of cryptocurrency after calls from fraudsters posing as police officers.
Fake ransoms delivered via snail mail: Scammers are sending ransom notes to US companies via snail mail pretending to be the BianLian ransomware group. The scammers claim to have breached and stolen the company's data and are requesting payment via Bitcoin to a wallet address included in the mailed letter. Security firm GuidePoint received reports of mailed letters throughout the month of March. Ransom demands ranged from $250,000 to $350,000.
Malware technical reports
Eleven11bot botnet: The Eleven11bot botnet appears to have grown from 30,000 to over 86,000 infected devices in the span of a few days, per the Shadowserver Foundation.
FunkSec ransomware: Security researcher Vlad Pasca has published a technical deep dive into the FunkSec ransomware.
Cactus ransomware: Trend Micro looks at how the Cactus and BlackBasta ransomware groups have adopted the BackConnect malware to maintain persistence on infected systems. The company believes former BlackBasta members are now using the Cactus RaaS after BlackBasta imploded.
Remcos RAT: SonicWall's security team looked at a malspam campaign spreading Remcos RAT to European organizations.
Ragnar Loader: Prodaft has published a technical analysis of Ragnar Loader, a malware loader developed by the old Ragnar Locker ransomware gang. The malware is also known as the Sardonic Loader.
Sponsor section
In this sponsored product demo, Prowler founder and CEO Toni de la Fuente walks Risky Business host Patrick Gray through the company's open-source cloud security platform. Toni demonstrates how Prowler can identify and remediate security issues across AWS, Azure, GCP, and Kubernetes. There's a pointy-clicky GUI interface and a CLI, and both come in handy in different ways. The Prowler platform is completely free and open source, but there is a hosted version you can pay for if you don't want to run it yourself.
APTs, cyber-espionage, and info-ops
AdNow linked to FSB and SVR: Snoop, a Romanian investigative journalism outlet, has linked an online advertising company named AdNow to intelligence officials from Russia's FSB and SVR services. Previous Snoop reporting has found that the ad network helped monetize fake news portals carrying Russian propaganda, right-wing extremist groups, and a slew of crypto investment fraud sites. The network was active in the Balkans, mainly in Romania and Bulgaria.
UNK_CraftyCamel: A new cyber-espionage group named UNK_CraftyCamel is targeting aviation and satellite companies in the UAE. Security firm Proofpoint has described the group as extremely cautious and dedicated to remaining stealthy. The group's operations involved small-scale spear-phishing attacks targeting a handful of selected targets. The final payload is a backdoor named Sosano that uses polyglot files to avoid detection.
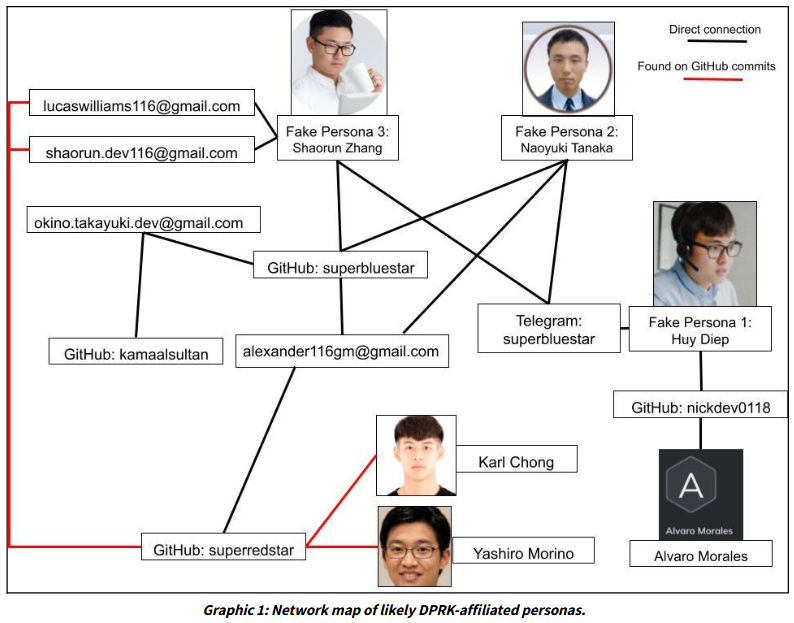
DPRK's GitHub worker network: Nisos researchers have published a report on a network of likely North Korean IT workers posing as various Asian nationals on GitHub, with the apparent goal of obtaining remote jobs in Japan and the US.
Vulnerabilities, security research, and bug bounty
Live API keys found in DeepSeek data: Security researchers have found almost 12,000 live API keys and passwords inside a massive open-source dataset used to train AI models. Named Common Crawl, the database has been used to train services like DeepSeek. Truffle Security says it detected 219 different types of secrets in Common Crawl, with AWS root keys being the most common.
Android Security Bulletin: Google has released the Android security updates for March 2025. This month, the company has patched two actively exploited zero-days (CVE-2024-43093 and CVE-2024-50302). One of the zero-days was part of Cellebrite phone-unlocking products. Amnesty International researchers found the zero-day while investigating cases of spyware secretly installed on the phones of anti-government dissidents.
VMware ESXi zero-days: Broadcom released security patches to patch three actively exploited zero-days in its VMware ESXi products. The zero-days are likely part of the same exploit chain. Broadcom credited Microsoft's MSTIC security team with spotting and reporting the attacks.
Xbox 360 Bad Update exploit: Video game hacker Ryan Miceli has released "a non-persistent software only hypervisor exploit for Xbox 360" that works on the latest Xbox firmware.
KEV update: CISA has updated its KEV database (twice) with nine vulnerabilities that are currently exploited in the wild. These include the VMware zero-days listed above, one of the Linux/Android kernel bugs exploited by Cellebrite products, Cisco, Windows, Hitachi, and Progress WhatsUp Gold bugs.
Infosec industry
Acquisition news: Apple-centric security firm Jamf has acquired IAM platform Identity Automation.
Threat/trend reports: Cado Security, DLBI, Fastly, iProov, Kaspersky, Keyfactor, Kroll, and OPSWAT have recently published reports and summaries covering various infosec trends and industry threats.
New tool—Penflow: Security researchers Riadh Bouchahoua and Ludovic Coulon have released Penflow, a platform for penetration testing workflow management and visualization.
New tool—Clio: Security researcher Sean Hopkins has released Clio, a collaborative logging system designed for red team operations and security assessments.
New tool—D3lta: France's disinformation investigations team, VIGINUM, has open-sourced D3lta, a library for detecting duplicate verbatim contents within a vast amount of documents.
Risky Business Podcasts
In this Risky Business Talks interview, we invited Will Thomas to talk about the recent leak of internal chats from the Black Basta ransomware group. Will is the co-founder of CTI community research project Curated Intelligence and author and instructor at the SANS Institute. Will walks us through the Black Basta leak and uses the group's attack on US healthcare provider Ascension to break down how the gang operated.
Tom Uren and Patrick Gray talk about the White House apparently considering kicking Canada out of the Five Eyes intelligence alliance to apply pressure on the country. It's a terrible idea, and even thinking about it undermines the strength of the alliance.
In this edition of Between Two Nerds, Tom Uren and The Grugq take a deep dive into incident response reports from Chinese cybersecurity firms that attribute the hack of one of the country's top seven defense universities to the US National Security Agency.




