Risky Bulletin: North Korean hackers steal $1.5 billion from Bybit
In other news: Apple disables iCloud backup encryption in the UK; streamjacking hits the e-sports world; Palau falls to third ransomware attack in six years.

This newsletter is brought to you by vulnerability management and analysis platform Nucleus Security. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
North Korean hackers have stolen over $1.5 billion worth of crypto assets from Bybit, the world's second-largest cryptocurrency exchange.
The incident represents the largest crypto-heist in history (and the largest heist of any kind as well) and is almost 2.5 times larger than the previous leader—the theft of $625 million from the Ronin Network in April 2022.
The hack took place on Friday, February 21, and is considered one of the most complex crypto-heists ever pulled.
The attackers infiltrated Bybit's network, studied the company's internal procedures, identified, and then infected with malware all the employees who typically sign off on the movement of the company's funds.
The hackers specifically targeted the process of replenishing the company's active wallets—called hot wallets—where the company keeps funds needed for daily operations.
When hot wallets run dry, crypto exchanges move funds from their reserves—called cold wallets—to make sure there's enough liquidity to cover user withdrawals and token inter-exchanges.
The same goes for when hot wallets hold too many funds. Crypto exchanges move funds back to the reserves to safeguard themselves from malicious actors and exploits and limit possible losses.
Bybit CEO Ben Zhou says that when his staff wanted to replenish the hot wallets with new funds on Friday, the hackers altered the user interface of the crypto-wallet software the company was using to move funds.
The modification appeared on the systems of all engineers who needed to sign off, in what is known as a multi-sig transaction.
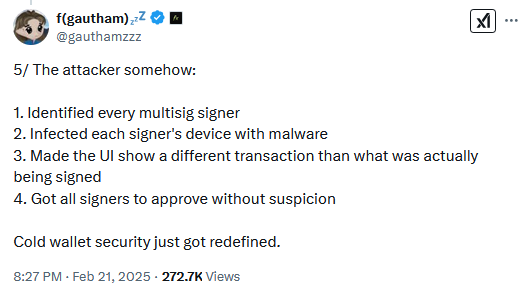
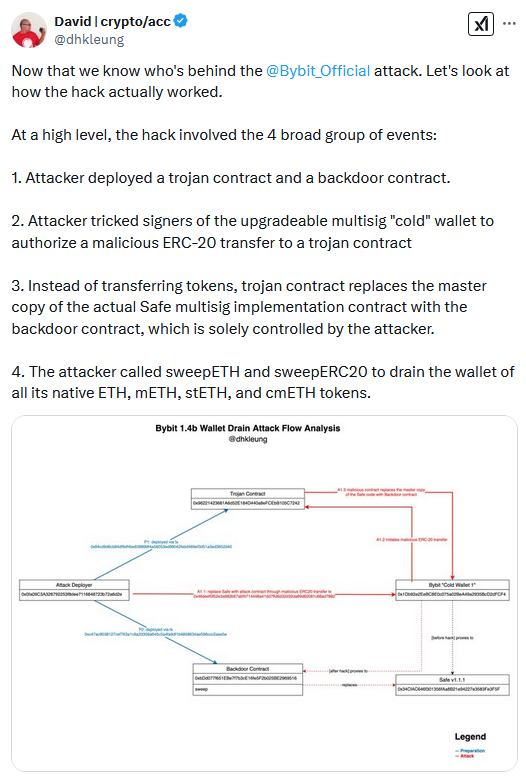
According to Bybit's post-mortem, the transaction approved the running of malicious code that sent the funds from that specific cold wallet to the attacker's own accounts.
"Unfortunately, the transaction was manipulated by a sophisticated attack that altered the smart contract logic and masked the signing interface, enabling the attacker to gain control of the ETH Cold Wallet. As a result, over 400,000 ETH and stETH worth more than $1.5 billion were transferred to an unidentified address."
While initially it was not known who carried out the attack, blockchain sleuths like Arkham and ZachXBT linked the hack to North Korean hacking group Lazarus, and specifically to the same team who stole $70 million from Singapore-based exchange Phemex in January.
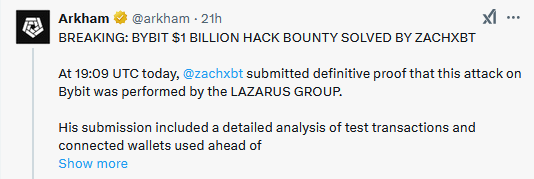

As for Bybit, the company says it has enough reserves to cover all losses. The company halted transactions for a day to investigate the incident but has since resumed all operations.
It also set up a bounty program to recover the stolen funds. The company says it's willing to provide up to 10% of the stolen funds to anyone who manages to recover the stolen tokens.
The offer has started the biggest bounty hunt on the internet, with the winners being eligible to earn up to a whopping $140 million.
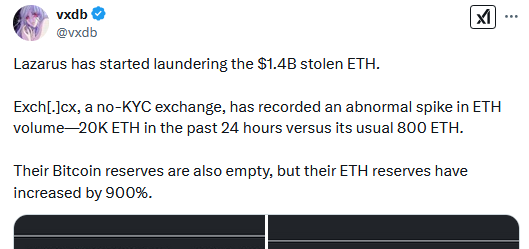
In the meantime, the hackers have already started laundering their funds in the hopes of hiding their tracks. They are moving quickly because if they leave the funds in their normal wallets, they risk having them hacked back by multiple parties, such as law enforcers, bounty hunters, or other threat actors.
Risky Business Podcasts
Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
Supreme Administrative Court of Bulgaria ransomware attack: The RansomHouse ransomware gang has taken credit for a cyberattack that hit the Supreme Administrative Court of Bulgaria last month. Officials have confirmed they received a ransom. [Additional coverage in OffNews.bg] [h/t DataBreaches.net]
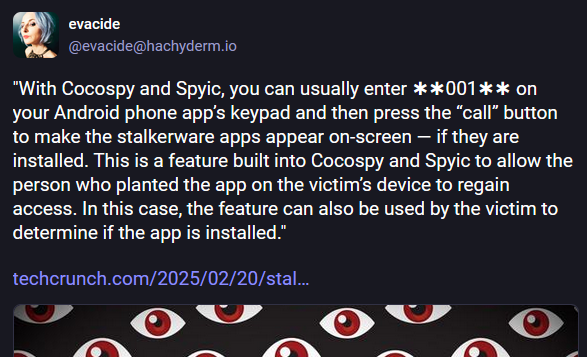
Cocospy and Spyic breaches: Spyware apps Cocospy and Spyic contain a vulnerability that exposes the email addresses of all registered users. The bug was discovered by an anonymous security researcher who exploited the issue to track who signed up to use stalkerware apps. The researcher says Cocospy has almost 1.8 million registered users, making it one of the biggest stalkerware operations discovered to date. Spyic has 875,000 registered users and shares IT infrastructure with Cocospy. Previous reporting linked both apps to China mobile app developer 711.icu. [Additional coverage in TechCrunch]
Palau cyberattack: The Qilin ransomware group has taken credit for a cyberattack that hit Palau's Ministry of Health and Human Services. Officials are investigating the hack and say hospital care has not been impacted. The incident marked the third time the small Pacific island nation dealt with a ransomware attack. The previous attacks took place in 2019 and 2023. The Australian government sent IT teams to help Palau recover from the last attack. [Additional coverage in CyberDaily]

General tech and privacy
Apple pulls E2EE cloud backups from the UK: Apple is removing the option to enable Advanced Data Protection for iCloud users in the UK. Launched in November 2022, the feature allows users to encrypt iCloud backups on Apple's servers. Apple is removing the feature after UK security services requested the company grant them backdoor access to user data earlier this year. [Additional coverage in the BBC]
Google Cloud PQE: Google says its Cloud service now uses post-quantum encryption algorithms designed to fend off possible quantum computing attacks.
BSI endorses passkeys: Germany's cybersecurity agency has given a glowing endorsement for the use of passkeys instead of passwords.
New Automattic class-action: Keller Holdings, the company behind WP Engine, has fined another class-action lawsuit against Automattic, the company behind the WordPress CMS. [Complaint PDF] [h/t Rob Freund]
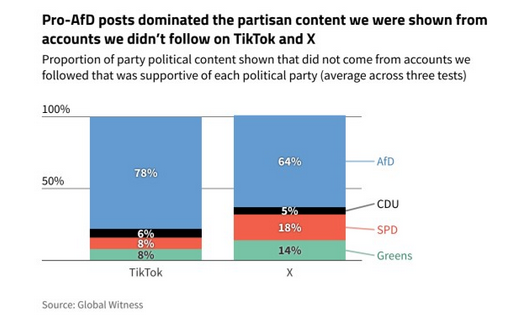
TikTok and Twitter are meddling in Germany's election: New research published last week has found that Twitter and TikTok are recommending pro-AfD content to non-partisan users ahead of Germany's parliamentary elections. Researchers at Global Witness found that 64% of the political content recommended on Twitter is linked to the AfD. On TikTok, the percentage was even larger at 78%. Overall, right-wing content dwarfed left-wing content. The Global Witness study echoed the findings of similar research from DFRLab. [Additional coverage in NiemanLab]
Government, politics, and policy
Chinese security firm involved in internet censorship: A Chinese security firm named TopSec is involved in content moderation and internet censorship on behalf of the Chinese government. The company's involvement came to light after one of the company's internal DevOps documents leaked online. SentinelOne says TopSec is providing its services to both Chinese public agencies but also private sector companies. According to the leaked document, TopSec's systems are engineered to detect and block political criticism, violence, and pornography—in compliance with China's general internet rules.
New FBI Director: The US Senate has confirmed Kash Patel to lead the Federal Bureau of Investigation. [Additional coverage in NextGov]
US cyber falling behind: In an interview at the DistrictCon security conference, former NSA and Cyber Command lead Gen. Paul Nakasone said the US is increasingly falling behind its adversaries in cyberspace. [Additional coverage in CyberScoop]
CyberCommand 2.0: New US Defense Secretary Pete Hegseth has ordered US Cyber Command to come up with a plan to overhaul its structure in the next 45 days. Cyber Command would need to turn the new plan in before March 22. The Pentagon approved a plan to overhaul Cyber Command in the last days of the Biden administration. Hegseth's move surprised CyberCom officials, who were initially given a deadline of 180 days. [Additional coverage in The Record]
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Aaron Attarzadeh, Enterprise Security Engineer at Nucleus. Aaron goes into new concepts for the vulnerability management scene, such as asset correlation and asset linking.
Arrests, cybercrime, and threat intel
TCC co-founder extradited: US authorities have extradited a Brazilian man from Switzerland to face charges for a $290 million cryptocurrency Ponzi scheme. Douver Braga created a cryptocurrency investment platform named Trade Coin Club in early 2016. Officials claim Braga collected user investments and shut down the platform two years later without returning their funds. The DOJ says Braga also failed to report his earnings to the IRS. He faces up to 20 years in prison.
BlackBasta chat leaks: The BlackBasta chat logs that leaked earlier this month are finally available for everyone on GitHub.
GoblinCrypt: EclecticIQ researcher Arda Büyükkaya has used data from the same BlackBasta leak to gain access to a previously unknown malware crypting service named GoblinCrypt.
New npm malware: Fifty-five malicious npm packages were discovered and taken down last week. Check out the GitHub security advisory portal for more details.
B1ack's Stash card dump: An underground carding forum named B1ack's Stash has published a collection of 1 million unique credit card details on its site.
WEF DDoS attacks: Netscout takes a look at the DDoS attacks that plagued the recent World Economic Forum.
Fake security audits: Belgium's cybersecurity agency has warned local companies to watch out for threat actors offering fake cybersecurity audits. Unknown individuals pose as civil servants and contact companies to offer free security audits. If targets agree to the audit, the threat actors would often install their own equipment on targeted networks.
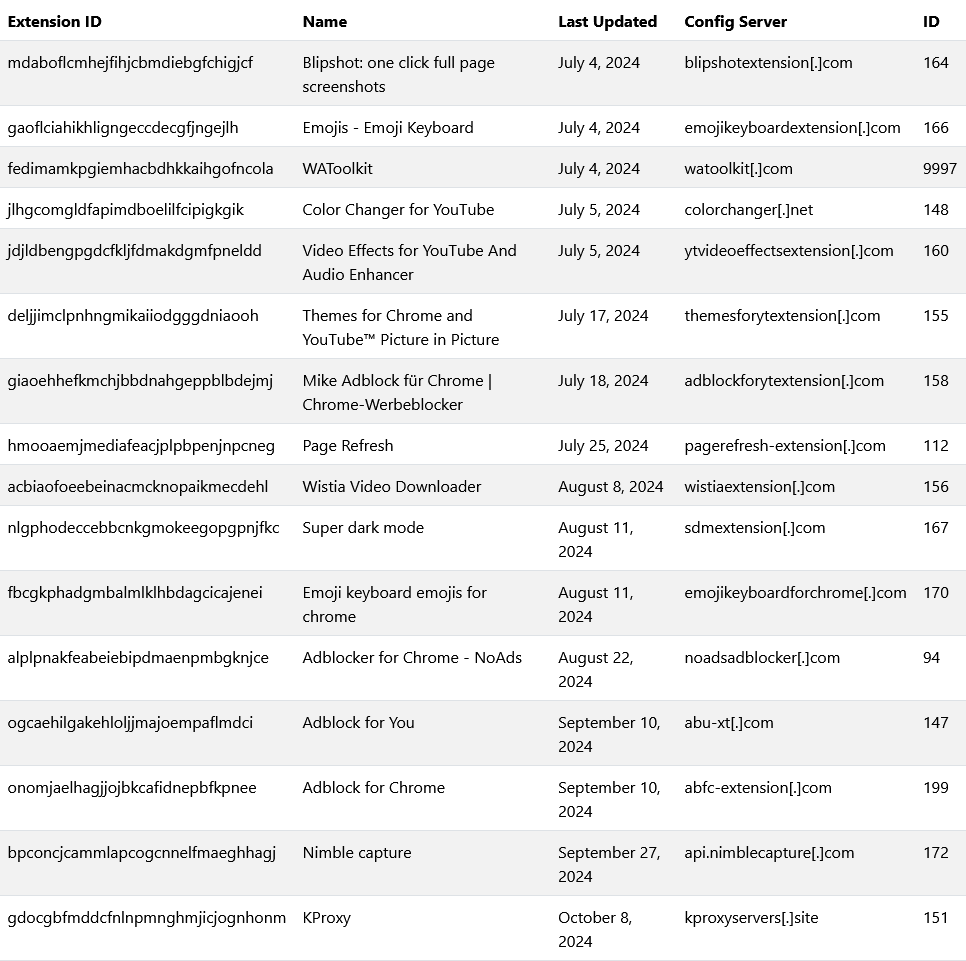
GitLab finds 16 malicious Chrome extensions: GitLab's security team has discovered a cluster of 16 malicious Chrome extensions on the official Google Web Store. The extensions were used to insert ads and manipulate search engine results. The extensions posed as screen capture utilities, ad blockers, and emoji keyboards. More than 3.2 million users downloaded the extensions before they were taken off the official store.
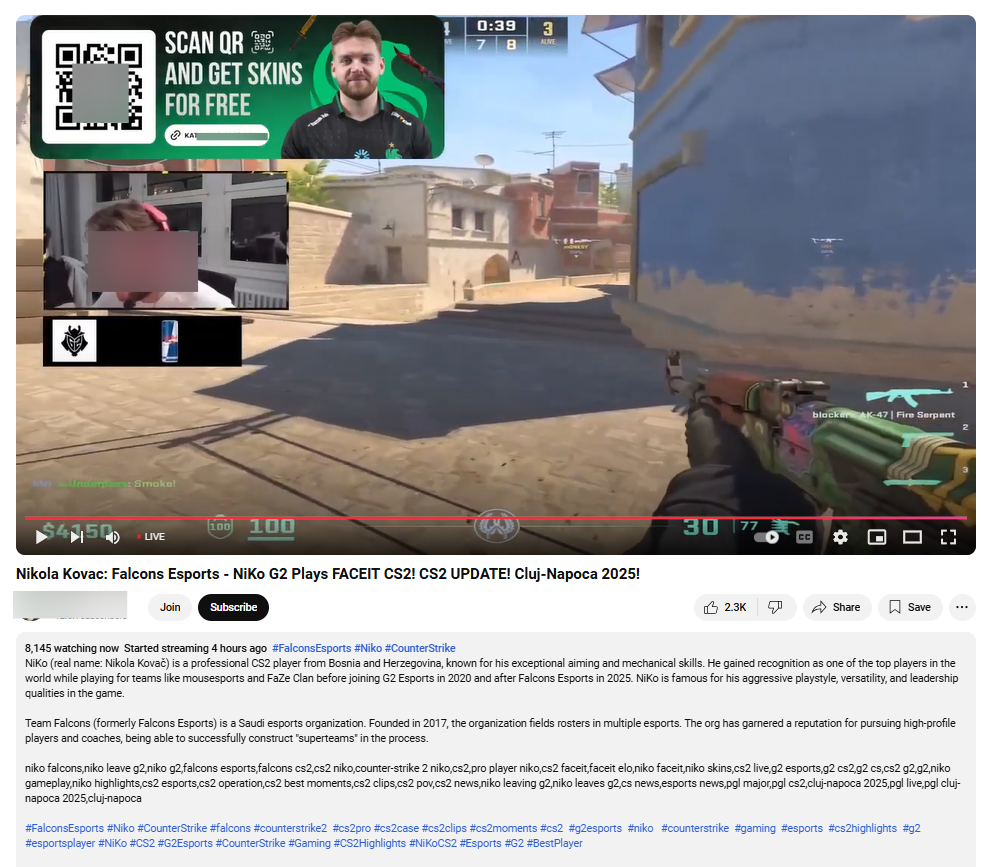
Streamjacking scams hit the gaming world: Scammers are using hacked YouTube accounts to live stream e-sports competitions and defraud users. The scammers use malicious QR codes overlaid on streams to redirect users to phishing sites designed to steal Steam credentials or crypto wallets. Security firm Bitdefender has spotted malicious streams for at least two Counter-Strike 2 tournaments. The same technique has been very popular over the past half-decade, but typically with political and tech talks.
Malware technical reports
Lumma Stealer: Silent Push has published a report on a Lumma Stealer campaign using YouTube links to malicious files to infect users. Researchers say credentials stolen with this campaign are being shared for free on a hacking forum.
SpyLend: CyFirma looks at SpyLend, an Android malware strain that has managed to sneak into the Google Play Store, from where it was downloaded more than 100,000. The malware is used for predatory lending, blackmail, and extortion.
Core ransomware: CyFirma, PCRisk, and Symantec have spotted a new variant of the Makop ransomware named Core.
Sponsor section
Nucleus Security's COO Scott Kuffer shows Patrick Gray their vulnerability management platform. It ingests scan outputs from a number of vulnerability identification tools, normalizes that information and then allows vulnerability management teams to do things like assign responsibility for certain types of bugs to the correct people.
APTs, cyber-espionage, and info-ops
OpenAI disrupts Chinese surveillance vendor: OpenAI banned ChatGPT accounts used by a Chinese company to write sales pitches for a social media monitoring platform. The same accounts were also used to analyze and translate content from Western social media posts discussing Chinese matters. OpenAI says it also banned ChatGPT accounts linked to Chinese info-op group Spamouflage, which was using its platform to generate articles in Spanish that targeted Latin American audiences. In addition, the company also banned several batches of North Korean accounts linked to APT cyber operations and IT worker schemes.
Angry Likho (Sticky Werewolf): An APT group named Angry Likho has made hundreds of victims across Russia and Belarus over the past two years. The group's usual targets include employees of large organizations, such as government agencies and their contractors. Kaspersky says the group appears to include native Russian speakers. Angry Likho is also known as Sticky Werewolf, a group previously linked to Ukraine.
ScarCruft: Qihoo 360 has published a report on North Korean APT group ScarCruft and on one of its recent campaigns that deployed the RokRat malware.
Yearly APT report: Qihoo 360 has published its yearly APT report but locked it behind a paywall that requires your phone number. Here's a working direct link to the PDF—via Mandiant's Mark Parker Young.
Doppelganger goes nuts: Germany's government says that activity from Russian disinfo group Doppelganger has exploded ahead of its parliamentary election this weekend. [Additional coverage in Politico]
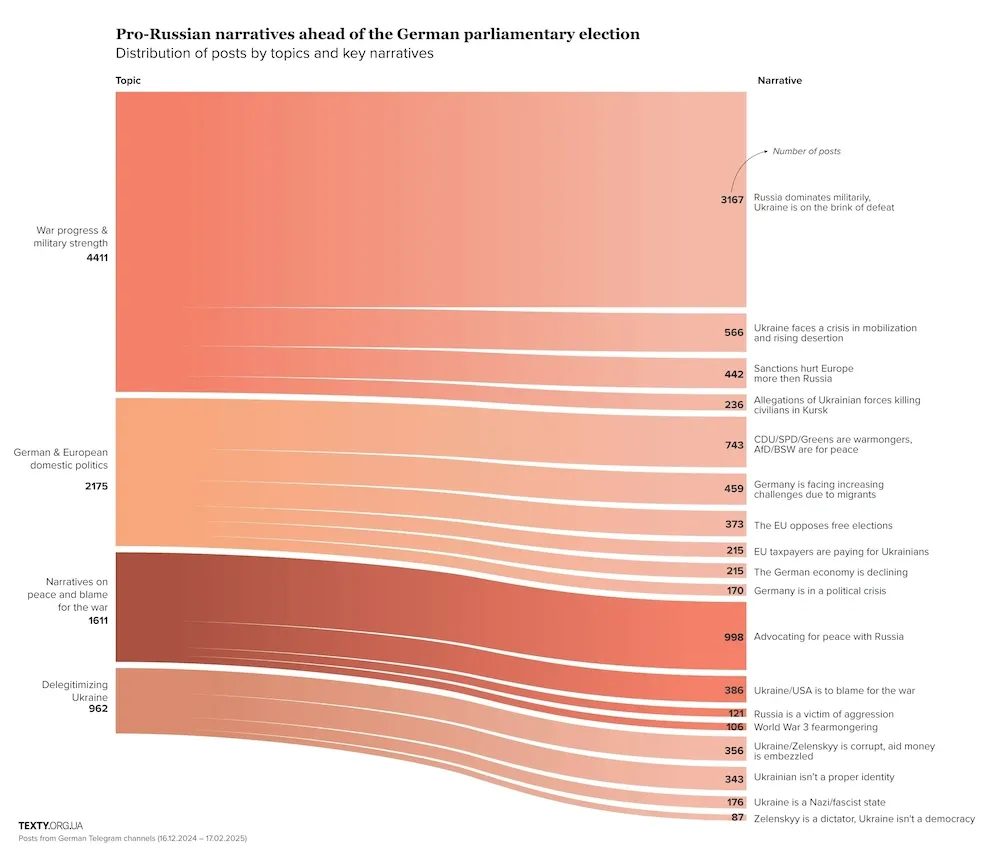
German elections misinformation: Ukrainian research group Texty has looked at the most common themes shared by pro-Russian Telegram channels ahead of the German parliamentary election this weekend. TLDR: Russia did nothing wrong; it's everyone else's fault. As usual!
Vulnerabilities, security research, and bug bounty
Parallels zero-day: Security researcher Mickey Jin has disclosed a zero-day in the Parallels Desktop virtualization service. Jin says he published details on the zero-day after Parallels and its vulnerability handler ZDI failed to address the issue for over seven months. The zero-day is a bypass for an older bug and can be used to gain root access on Parallels Desktop deployments.
KEV update: CISA has updated its KEV database (twice) with three vulnerabilities that are currently exploited in the wild. This includes a recent Microsoft Power Pages zero-day, a recent Palo Alto Networks firewall bug, and a Craft CMS vulnerability from January.
LLM jailbreaking: A PAN Unit42 report has found that 17 of the most popular web-based GenAI services are vulnerable to jailbreaking attacks.
XSS in Python docs: Security researcher Georgi Guninski has found that Python's official documentation contains textbook examples of insecure code that can lead to cross-site scripting (XSS) vulnerabilities.
TSforge exploit: A team of software crackers named MASSGRAVE has developed a universal exploit that can unlock and activate any version of Windows and Microsoft Office. Named TSforge, the exploit targets the Microsoft Software Protection Platform (SPP). The exploit has been incorporated into the group's MAS toolkit and is available for download.
Infosec industry
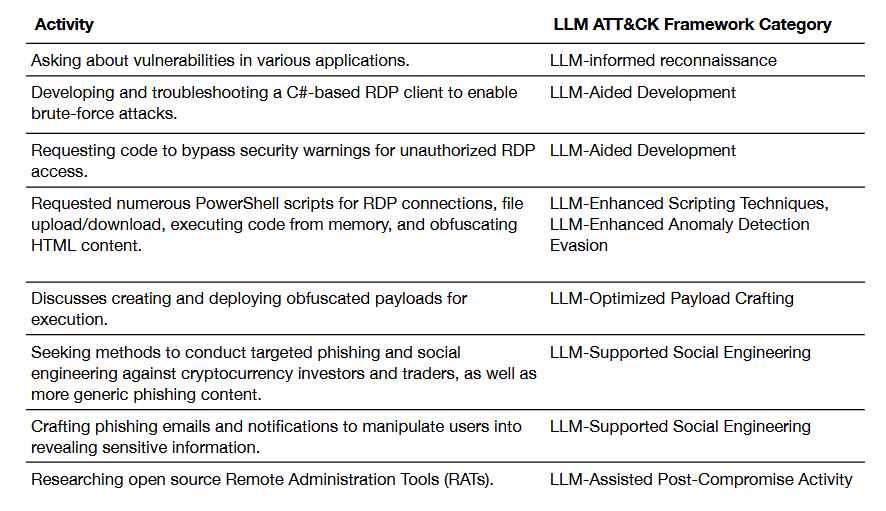
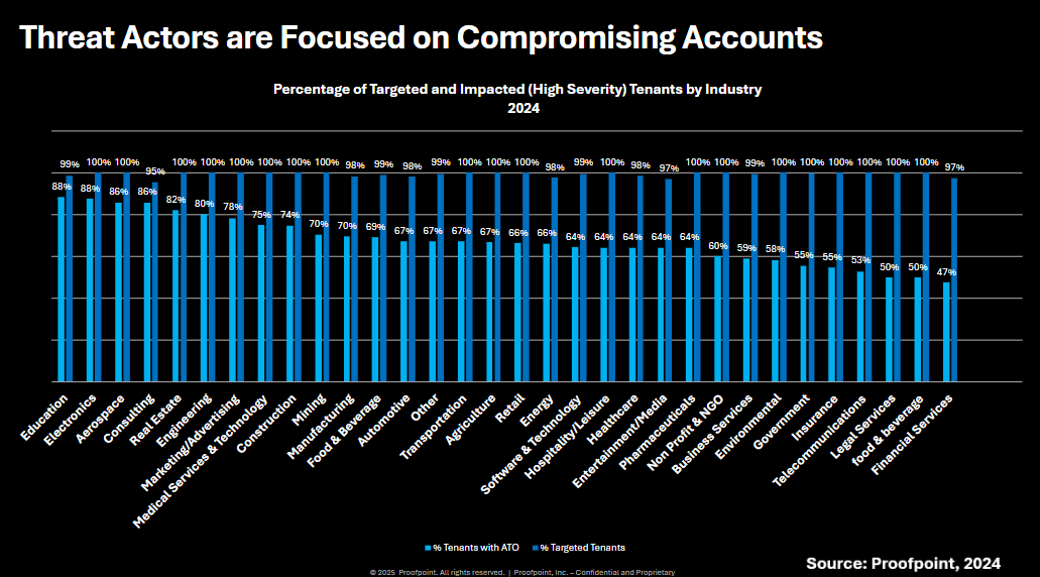
Threat/trend reports: Forrester, Proofpoint, QiAnXin, Red Canary, and Thinkst have recently published reports and summaries covering various infosec trends and industry threats.
New tool—DelphiHelper: ESET has open-sourced DelphiHelper, an IDA Pro plugin for the analysis of x86/x86_64 Delphi binaries.
New tool—keycred: Security firm RedTeam Pentesting has released keycred, a CLI tool and library to implement the KeyCredentialLink structures of the Active Directory Technical Specification (MS-ADTS).
New tool—SoaPy: IBM X-Force researcher Logan Goins has released SoaPy, a tool for conducting offensive interaction with Active Directory Web Services (ADWS) from Linux hosts.
New tool—MSFTRecon: Security firm Arcanum has released MSFTRecon, a reconnaissance tool designed for red teamers and security professionals to map Microsoft 365 and Azure tenant infrastructure.
New tool—Linkook: Security researcher Jack Ju1y has published Linkook, an OSINT tool for discovering linked social accounts and associated emails across multiple platforms using a single username.
DistrictCon 2025 videos: Talks from the DistrictCon 2025 security conference, which took place last week, are available on YouTube (plus these two).
Risky Business Podcasts
In this podcast, Tom Uren and Patrick Gray talk about the idea of launching a retaliatory campaign to hack Chinese telcos in response to Salt Typhoon's targeting of US ones. US Senator Mark Warner floated the idea as a way to persuade the Chinese government to pull back Salt Typhoon, but we think that kind of campaign has merit regardless.
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about the United State's Vulnerabilities Equities Program, which balances the need for intelligence collection with the need to protect the public. The government recently revealed that in 2023, it released 39 vulnerabilities, but what does this really tell us?




