Risky Bulletin: NIST releases face-morphing detection guideline
In other news: Oracle CSO departs after 37 years; Europol offers reward for Qilin admins; UK drops Apple backdoor request.

This newsletter is brought to you by Kroll. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
The US National Institute of Standards and Technology released guidance this week to help companies detect face morphing incidents.
The technique involves blending photos of two or more real people to generate a new face that can be used to bypass facial recognition scans.
The new photo can be used to trick face recognition systems into identifying the morphed, combined face as both original individuals at the same time.
This can be abused to allow rogue individuals to access online accounts or sensitive areas of a facility they do not have authorization to access.

The technique is a particular and pervasive threat to government and military facilities, banks, and cryptocurrency platforms.
These types of attacks were once considered the height of threat actor sophistication, but are now extremely likely due to readily available face morphing software online, such as mobile and desktop apps, and new AI-based tools.
NIST researcher Mei Ngan says that, along with the tools that power the attacks, face morphing detection software has also "improved dramatically in recent years."
Detection tools look for artifacts left in the morphed photo by the morphing software, such as inconsistent skin texture, skin color, and unnatural-looking areas around the iris, nostrils, lips, and eyebrows.
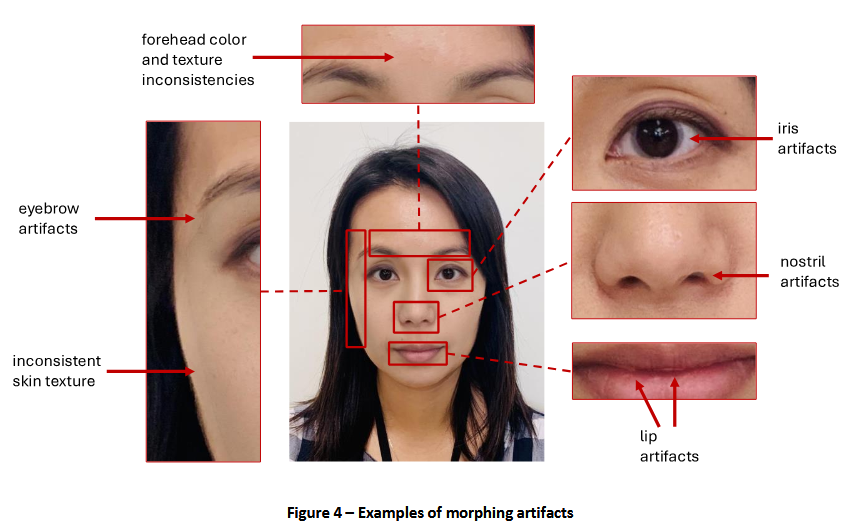
The new NIST guideline (NISTIR 8584/PDF) provides recommendations on what type of detection tools are ideal for specific cases. For example, organizations and systems that receive image submissions from users in real-time (e.g., passport authority, bank, etc.) need different tools and defenses compared to organizations that have to scan and compare a person's face to their document (e.g., border crossing, corporate access systems, etc.).
Defenses include a variety of techniques ranging from visual inspections to checking for EXIF data and requesting new "live" photos.
NIST says that while software tools are now available for detecting face morphing in near real-time, the best defense is to prevent morphs from getting into systems in the first place. As such, the main recommendation is to focus and deploy most of the detection capabilities in the document application and issuance process.
"For organizations that permit user-submitted photos as part of the application process, a practice that carries a higher risk of image manipulation, additional safeguards should be considered. These may include implementing trusted capture methods to prevent tampering, substitution, or morphing. When trusted capture is not feasible, entities should assess the risk level and consider proportionate countermeasures, such as deploying automated morph detection tools and training staff to recognize morphing threats. Staff should also be equipped to interpret detection results and take appropriate steps to verify the applicant's true identity."
Risky Business Podcasts
The main Risky Business podcast is now on YouTube with video versions of our recent episodes. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
Online casino group discloses breach: A major developer of online casino gaming platforms has disclosed a security breach. The Bragg Gaming Group says hackers breached its internal IT network in an incident discovered over the weekend. The company says the hack has not affected its main operations.
iiNet hack: Australian mobile operator TPG Telecom is investigating a hack of its iiNet subsidiary. Hackers allegedly breached an order management system that iiNet was using to process customer requests for new services. The incident took place on Saturday, August 16. [Additional coverage in iTnews]
Nuance settles MOVEit lawsuit: Microsoft's Nuance division has settled a lawsuit for $8.5 million related to the company's 2023 MOVEit-caused breach. [Additional coverage in the HIPAA Journal]
DDoS attacks target Australia: A pro-Kremlin and pro-Palestine hacktivist group named DieNet is launching DDoS attacks against Australian government sites to pressure officials into putting pressure on Israel and supporting Palestine. More on the group from Netscout and Orange [PDF]. [Additional coverage in CyberDaily]
DRPK hack sinks crypto startup: A UK cryptocurrency exchange was liquidated after losing almost $23 million in a hack last year. The company ceased operations shortly after the hack and was liquidated this year when customers sued to get their funds back. According to court documents, the hack was carried out by the Lazarus North Korean hacking group. [Additional coverage in The Digital Watch Observatory]
Inotiv discloses ransomware attack: A ransomware attack has disrupted the operations of US pharmaceutical research group Inotiv. The incident took place on August 8 and impacted internal data storage and some business applications. The company has confirmed that data was encrypted in the attack. The Qilin ransomware group took credit for the intrusion by listing the company on its leak site.

General tech and privacy
Win11 security update causes SSD failures: There are reports that a recent Windows 11 security update is causing some SSDs to crash and fail. The same updates are also causing Windows reset and recovery operations to fail.
Cloudflare Browser Developer Program: Cloudflare has launched a private program for browser makers to test new features before they go live and prevent breaking navigation to its sites.
Google settles YouTube privacy lawsuit: Google has agreed to pay $30 million to settle a class-action lawsuit that it violated children's privacy on YouTube by secretly collecting their data without parental consent. The company paid a $170 million fine in 2019 to the FTC and the state of New York for similar practices. [Additional coverage in Reuters]
PyPI blocks domain resurrection attacks: The Python Package Index (PyPI) has rolled out a new security feature that blocks domain resurrection attacks. These are instances where threat actors register expired domains that were once used to set up PyPI accounts. This allows attackers to take over Python libraries and ship malicious code inside official projects. PyPI says the feature rolled out in June, and it already unverified more than 1,800 accounts that used an expired email address domain.
Firefox 142: Mozilla has released Firefox 142. New features and security fixes are included. The biggest features in this release are the ability to preview links through a long-press, improvements to collapsed tab groups, and local AI capabilities for extension developers. Yeeeeyyy! I guess that's why my CPU was at 75% after the update!!!!
Git changes: SHA-256 will become the standard hashing function of the Git version control system in Git 3.0.
Government, politics, and policy
White House looking at AI to replace fired employees: The Trump administration is "100%" looking at using AI to replace the thousands of fired government workers, according to US government CIO Gregory Barbaccia. [Additional coverage in NextGov]
Australia fines Google over Search mobile deals: Australia has fined Google AUD$55 million (USD$35.8 million) for anti-competitive practices on the online search market. The Australian Competition and Consumer Commission says Google hurt competition by paying telcos to pre-install its search app. The telcos, Telstra and Optus, received revenue for ads displayed in the app.
UK backs down from Apple backdoor: The UK has abandoned a request that would have required Apple to create a backdoor to its encrypted cloud data. The UK dropped its request following pressure from the US government. UK officials made the request in January. [Additional coverage in Al Jazeera]
UK continues to get stupider: The UK's Children's Commissioner wants to introduce age verification checks for VPN apps—because the current age verification process didn't turn out to be a complete unwanted mess.
Sponsor section
In this Risky Business sponsor interview, Ed Currie from Kroll Cyber talks to Tom Uren about the recent hack of the Gravy Analytics geolocation data provider. He explains the hack and how geolocation data can be used by malicious actors.
Arrests, cybercrime, and threat intel
SMS blaster detained in Bangkok: Thai police have arrested two local men over the weekend for driving with an SMS blaster around Bangkok. The men said they were recruited by a Chinese gang to drive around and send SMS spam across the city. The suspects were initially paid $100/day to drive in their personal cars. They were later paid $40/day after the Chinese gang forced them to use rental cars and minimize exposure. [Additional coverage in the Thai Examiner]

Scammers arrested in Gambia: Gambian authorities have arrested 19 suspects involved in online scam activities. The suspects are Nigerian nationals aged 19 to 35. They were arrested in the city of Brusubi after locals reported suspicious activity. They claimed they were being trained to run online scams by two Chinese nationals. The two are still at large. [Additional coverage in Foroyaa]
Israeli cyber official arrested in Las Vegas: An Israeli cybersecurity official was arrested in Las Vegas over the week. Tom Artiom Alexandrovich was charged with luring and soliciting a minor for sex. He was one of eight suspects detained during a police undercover operation. Alexandrovich was released after paying a bond and is back in Israel. According to his LinkedIn page, Alexandrovich is the executive director of the Israel Cyber Directorate.
Website defacer sentenced: A UK judge sentenced a 26-year-old hacker to 20 months in prison. Al-Tahery Al-Mashriky hacked and defaced over 3,000 websites during a three-month period in 2022. He conducted the hacks while he was a member of two hacktivist groups known as the Spider Team and the Yemen Cyber Army.
Nebraska cryptominer sentenced: A Nebraska man was sentenced to one year in prison for defrauding cloud providers as part of a large-scale crypto-mining scheme. Charles O. Parks rented servers from two cloud providers through fake companies and never paid his bills. He used $3.5 million worth of computing resources to mine more than $1 million in crypto tokens. He then used the money to buy NFTs, luxury cars, jewelry, and expensive hotels and travel while posing as a crypto influencer and thought leader on social media.
Europol puts a bounty on Qilin: Europol is offering a $50,000 reward for information on two administrators of the Qilin ransomware group. The two individuals go by their hacker names of Haise and XOracle. They have been in charge of the Qilin ransomware since its launch in May 2022. The group is one of today's most active ransomware operations. According to Check Point, Qilin accounted for an eighth of all public ransomware attacks last month. [Additional coverage in The 420]
Child sextortion cases linked to scam compounds: Researchers have linked almost 500 child sextortion cases to scam compounds operating in Southeast Asia. Forensic data has linked the cases to 40 of the 44 previously known scam compounds operating in Cambodia, Myanmar, and Laos. IP address data may link up to 18,000 cases to the same cluster, according to human rights group the International Justice Mission. [Additional coverage in WIRED]
Scaly Wolf returns after two years: A financially motivated group named Scaly Wolf returned to hack a Russian engineering company two years after the initial intrusion.
New Salty 2FA PhaaS: The Storm-1575 group launched a new Phishing-as-a-Service platform named Salty 2FA. The group previously operated Rockstar 2FA and Dadsec.
DPRK IT worker leak: Threat intel analyst Rakesh Krishnan looks at a recent leak of almost 1,400 emails used by DPRK remote IT workers.
Scattered Spider profile: Flashpoint researchers have released TTPs typically associated with Scattered Spider attacks.
GenAI abuse: PAN's Unit42 looks at how genAI services are being abused for phishing operations.
Cisco Safe Links abuse: Phishers are (ab)using Cisco Safe Links to hide their malicious links and make URLs appear authentic. This works only in the initial phases before Cisco actually indexes the links and starts flagging them as malicious.
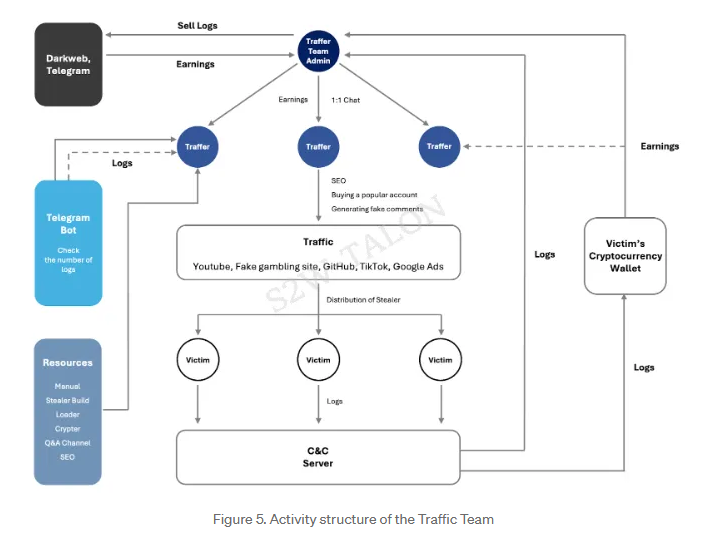
Traffer ecosystem: S2W has published a report on how the traffer ecosystem works with infostealer gangs to drive massive amounts of traffic to their malicious sites.
Malware technical reports
Lockbit's Linux ESXi variant: Security researcher Marion Marschalek has reverse-engineered Lockbit's Linux ESXi variant.
VELETRIX Loader: Malware researcher 0x0d4y has published a follow-up on his initial analysis of the VELETRIX Loader. They linked the attack to a China-nexus threat actor.
DripDropper: A threat actor is hacking Apache ActiveMQ servers to deploy a new Linux backdoor named DripDropper.
GodRAT: Kaspersky has published a report on GodRAT, a new RAT based on the open-sourced Gh0stRAT that's being deployed in attacks against financial institutions.
PipeMagic backdoor: According to BI.ZONE, Kaspersky, and Microsoft, the PipeMagic backdoor is still active in the wild, even if the RansomExx ransomware group (where it was first seen for the first time in 2022) is barely active anymore.
Noodlophile Stealer: Morphisec researchers say the Noodlophile Stealer is now being distributed via phishing emails posing as copyright strikes. This is an evolution from its initial campaigns that abused genAI apps.
Lazarus Stealer: CyFirma researchers have spotted a new Android infostealer going by the name of Lazarus Stealer. Some of its features suggest the malware can also work as a banking trojan, but advertising everything as a "stealer" seems to be the best "marketing strategy" on underground hacking forums these days.
Risky Business podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about whether the cyber industry and intelligence agencies focus too much on technical details and ignore the bigger picture.
APTs, cyber-espionage, and info-ops
Kimsuky's GitHub abuse: Trellix looks at 19 Kimsuky spear-phishing campaigns that targeted foreign embassies in Seoul and (ab)used GitHub to store payloads, such as the XenoRAT.
Vulnerabilities, security research, and bug bounty
Intel portal hack: Security researcher Eaton Zveare has discovered two ways to break into Intel backend systems and even more ways to dump and exfil the data of all Intel employees.
SHAR Attack: A vulnerability in the Dnsmasq software can allow threat actors to poison and manipulate DNS results.
Deanonymizing Google's Privacy Sandbox: Security researcher Eugene Lim has found a way to subvert the protections provided by the Google Chrome Privacy Sandbox APIs and deanonymize users visiting a site.
Unfixed Enterprise Linux 9 bug: A vulnerability in the systemd-coredump utility remains unfixed in Red Hat's Enterprise Linux 9. The bug can allow attackers to steal password hashes and cryptographic keys within seconds. The vulnerability was initially disclosed by Qualys back in May.
XBOW to stop HackerOne leaderboard hunt: AI pen-testing company XBOW will stop competing for the HackerOne leaderboard. The company became the first ever AI product to reach the number one spot on a bug bounty platform. XBOW says it will focus on working with private customers to test product security pre-launch.
Elastic rejects zero-day claim: Elastic has rejected a report from AshES Cybersecurity about a zero-day in its Elastic Defend EDR. The company says AshES researchers never submitted working proof-of-concept code, and was unable to reproduce the attack. Elastic called their behavior "contrary to the principles of coordinated disclosure."
Infosec industry
Threat/trend reports: FB-ISAO, Juniper Research, Malwarebytes, Unisys [PDF], and WanAware have recently published reports and summaries covering various infosec trends and industry threats.
Oracle CSO departs after 37 years: Oracle's chief security officer is leaving the company as part of a reorganization. Mary Ann Davidson has been one of the longest-serving CSOs in the industry. She joined Oracle in 1988 as a product manager, joined its security department in 1993, and became the company's CSO in 2001. According to Bloomberg, Oracle is cutting jobs to reduce costs while it invests in AI infrastructure.
New Phrack: The Phrack hacker e-zine issue 72 is now out. The e-magazine is now also 40 years old!
New tool—Glato: Security firm Praetorian has open-sourced Glato, or GiLab Attack Toolkit, an enumeration and attack tool to identify and exploit pipeline vulnerabilities in GitLab repositories.
New tool—AzureStrike: Pen-tester David Garcia has released AzureStrike, an application designed to simulate Azure Entra scenarios for Red Team simulations and adversarial training.
New tool—DllShimmer: Security researcher Print3M has released DllShimmer, a tool to backdoor any function in any DLL without disrupting normal process operation.
New tool—Auth0 Security Detection Catalog: Identity provider Okta has open-sourced a catalog of detection rules for monitoring Auth0 environments.
Risky Business podcasts
In this edition of Seriously Risky Business, Tom Uren and Amberleigh Jack talk about a recent hack of the US Courts' document management system.




