Risky Bulletin: NFC card malware keeps evolving in Russia, a bad omen for the future
In other news: Poland accuses Meta of failing to remove malicious ads; Malaysian brokerage accounts hacked; Craft CMS zero-day exploited in the wild.

This newsletter is brought to you by Dropzone AI. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
After a few years of stagnation and repetitive, copy-pasted malware strains, the Android banking malware scene is seeing a leap forward in innovation and tactics.
This new evolution is targeting contactless payments, a feature of modern banking that allows individuals to pay by using a smartphone or credit/debit card that has an NFC chip inside it. In 2025, the feature is ubiquitous, and very few banks don't support it.
For over a decade, it was believed that contactless payments were the future because nobody could clone or intercept NFC transactions.
This initial sense of safety was shattered in 2020 with NFCGate, a piece of academic research that created an open-source toolkit capable of intercepting, relaying, and replaying NFC data streams from a victim to a new device.
Initially, NFCGate looked like another piece of academic-driven stunt hacking with no real impact on the real world. Unfortunately, this, too, didn't last long.
Three years later, a modified version of NFCGate was found in the wild as the base of NGate, the first-ever malware strain with NFC capabilities. The malware was spotted in the Czech Republic, where hackers were calling victims and tricking them into installing NGate on their devices. When users opened the malicious app and entered their PIN, another member of the hacking crew was standing next to an ATM and getting ready to receive the victim's NFC card data (courtesy of the NFCGate code) so they could empty their accounts.
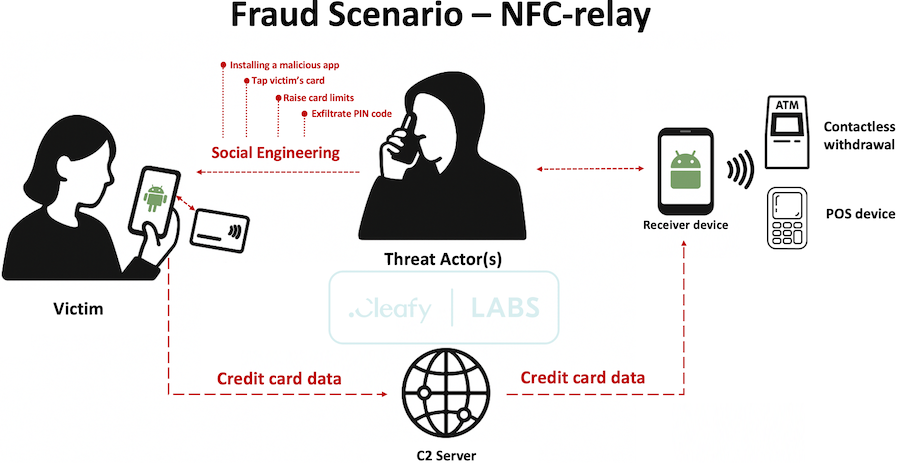
NFC cloning attacks find a testing ground in Russia
Those initial attacks were shrouded in mystery and still remain. While one suspect was detained, it's still unsure who developed the malware.
Since then, NFC-cloning malware has not died out, but merely moved to a new testing ground—in Russia, where new samples have been popping up more and more often since August of last year.
From a few random incidents, attacks with NFCGate-like malware are now becoming common and a major headache for Russian banks and security firms alike.
In a blog post in January, Russian security firm F6 (formerly FACCT, formerly Group-IB's Russian division) reported seeing over 400 NFCGate-based attacks last year, with losses of over 40 million rubles (~$400,000).
In a new blog post this week, those numbers have now exploded. The company says it discovered 40 new successful attacks, with an average loss of 120,000 rubles (~$1,500).
F6 says it also detected over 175,000 devices that have been infected with malware that matches NFCGate signatures—which is quite the considerable number when we compare it to stuff like IoT/DDoS botnets, most of which can barely make it over 10,000 at their peaks.
Furthermore, there are now multiple ads on underground hacking forums that advertise malware with NFC-cloning and relaying capabilities.
The ads are a bad omen because they show that initial attacks in 2023 and 2024 appear to have been successful tests, and the larger malware-dev ecosystem is now convinced they've found something reliable they can spend more effort into developing further.
And adapting and developing is what they've done. F6 says it has spotted two new variants of the classic NFCGate attack.
The first technique was spotted earlier this month. This one is clever because instead of calling victims and going through a complex social-engineering script designed to convince the victim they need to install a malicious app, attackers are using random Android malware and its regular distribution techniques to infect devices.
In this case, F6 has seen devices get infected with the CmaxsRAT, where attackers dropped NFCGate as a second-stage payload. They then used CmaxsRAT to intercept notifications and SMS alerts to acquire PINs and initiate and relay NFC transactions to someone waiting at an ATM.
The second technique is what F6 named a "reverse NFCGate." This one works by calling victims and having them install a malicious app. The app includes the NFCGate toolkit, but this one comes hard-coded with an attacker's card details.
This attack is particularly clever because instead of having another gang member sit next to an ATM waiting for the victim's NFC transaction details, the victim is told to visit an ATM on their own time—either to secure an account, activate a savings card, or another lie. When they scan their card at the ATM, the malware just sends their funds to the hard-coded attacker account.
Clever, different, efficient, and another step forward in the evolution of a new type of banking fraud.
Most of these NFC-cloning attacks have mostly taken place in Russia, where banks are starting to notice the increase in incidents, and some Duma members are looking to draft new laws to punish Russians who help fraudsters set up "drop accounts" where the stolen funds are redirected through.
Slowly spreading to China
But this plague is also slowly starting to spread to other places. Earlier this month, mobile security firm Cleafy discovered SuperCard X, a MaaS (Malware-as-a-Service) platform created by a Chinese-speaking developer that can allow customers to easily distribute and control NFCGate-inspired malware.
There's also this report from KrebsOnSecurity in February about Chinese gangs adding phished card data to their own Apple and Google wallets, from where they initiate cash-out operations via ATM contactless transactions.
A Resecurity report published last week also looks at the underground Chinese market for trading NFC-activated POS terminals, which are needed for processing the rogue contactless payments coming from some of these NFC-cloning and Apple/Google wallet-abusing groups.
By looking at the big picture, it is becoming quite clear that more and more criminal groups are turning their eyes on NFC and the contactless payments ecosystem.
Right now, this seems to be a big problem in China and Russia, but this won't stay contained in those two countries for long, mainly because contactless payments work about the same way everywhere, the techniques can be ported to any market, and criminal groups tend to move from country to country in search of new victims and a more relaxed law enforcement responses.
The amount of NFC-cloning-related fraud in Russia right now is a sign of a growing storm about to hit the EU and US in a few months. Criminal groups are refining their methods and attacks right now.
— Catalin Cimpanu (@campuscodi.risky.biz) 2025-03-24T20:24:57.422Z
Risky Business Podcasts
Tom Uren and Adam Boileau talk about how scam compound criminal syndicates are responding to strong government action by moving operations overseas. It's good they are being affected, but they are shifting into new countries that don't have the ability to counter industrial-scale transnational organized crime.
Breaches, hacks, and security incidents
Malaysian brokerage accounts hacked: Hackers gained access to brokerage accounts on the Malaysian stock exchange and executed unauthorized trades. Brokers have asked customers to change account passwords. Malaysian brokerage accounts were also hacked six weeks earlier. A similar attack hit Japanese brokerage accounts last week in what looks to be a larger campaign. [Additional coverage in The Edge Malaysia]
MTN data breach: South African telecommunications provider MTN says hackers accessed the personal data of some of its customers in a security breach this year. The company says its billing and core networks are secure and operational despite the breach. MTN, which is Africa's largest telco, is now notifying customers.
Bank-ID DDoS attack: A DDoS attack has taken down for about three hours Bank-ID, a shared digital identification service used by Swedish banks. [Additional coverage in Voister/English coverage in Mobile ID World] [h/t Nrlnd on BlueSky]
R0AR crypto-heist: The R0AR cryptocurrency exchange has lost over $780,000 worth of assets after an incident earlier this month. The platform says the hack was the work of a malicious developer who backdoored one of its smart contracts. The backdoor allowed the hacker to withdraw user-deposited funds without using the contract's normal functions. The stolen funds were laundered through Tornado Cash shortly after the hack.
MOVEit class-action dismissed: An Oregon judge has dismissed a class-action lawsuit filed against the Oregon DMV over its 2023 MOVEit hack. [Additional coverage in OregonLive] [h/t DataBreaches.net]
WorkComposer leak: An app used to keep tabs on employees at work has leaked over 21 million screenshots it took from user workstations. Long live unsecured AWS S3 buckets! [Additional coverage in Cybernews]
General tech and privacy
TP-Link antitrust probe: The US is conducting an antitrust investigation into Chinese hardware vendor TP-Link's market and pricing strategies. [Additional coverage in Bloomberg]
Quantum communications: A team of academics has developed a proof-of-concept quantum-based telecommunications system. The positive side—it's way cheaper than it was initially thought. [Additional coverage in Phys]
Government, politics, and policy
New CISA deputy director: DHS Secretary Kristi Noem has named Madhu Gottumukkala as new CISA deputy director. Gottumukkala previously served as chief information officer for the state of South Dakota. He replaces Nitin Natarajan, who resigned in January together with the previous CISA leadership. [Additional coverage in CybersecurityDive]
Easterly calls for SbD continuation: In an op-ed on Lawfare Media, former CISA Director Jen Easterly has called on the new CISA leadership to continue her work on the Secure by Design program.
US threatens Wikipedia: The US Justice Department is threatening to remove Wikipedia' non-profit status for allegedly allowing "foreign actors to manipulate information and spread propaganda" on its site. Nobody has any idea what the DOJ is referring to, but the DC prosecutor who sent a letter to the Wikimedia Foundation has a long history of threatening media organizations. All of this comes as the DOJ is slowly going off the deep end and turning into an oppression tool under the Trump administration. [Additional coverage in The Free Press]
Russia throttles mobile speeds at night: Russian authorities are throttling mobile internet speeds at night as a technical defense against Ukrainian drone strikes. Slowdowns have been reported in at least ten regions in the Rostov oblast. Internet speeds are limited to 512 kbit/s between midnight and 5am to prevent Ukrainian UAVs from determining their locations to nearby base stations. The new defenses have been active since December. [Additional coverage in Kommersant]
Poland accuses Meta of failing at removing malicious ads: Poland's cybersecurity agency has accused Meta of failing to take meaningful action against malicious ads on its Facebook platform. Three months after an initial meeting, CERT Poland says Meta has not listened to their suggestions, nor has it taken any other step. Meta did not implement a blocklist for known fraud domains and is also closing user fraud reports without removing the malicious ads. Officials say Meta is also lenient on fraudsters and not blocking their accounts even if they published multiple malicious ads.
Before Russia banned Facebook, they ran ads for drug dealing jobs for several months, and reporting didn't work at all
— Oleg Shakirov (@shakirov2036.bsky.social) 2025-04-26T21:25:22.023Z
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Edward Wu, founder and CEO of Dropzone AI. Edward talks about the impact of AI in modern-day SOC teams and how its role slowly becomes a force multiplier and productivity boost rather than workforce replacement.
Arrests, cybercrime, and threat intel
Operation Artemis arrests: Nigerian authorities arrested 22 suspects involved in sextortion campaigns. The suspects posed as women, contacted young teenagers, obtained nude or sexually explicit photos, and then extorted the victims for money. Almost half of the arrested suspects were linked to teen suicides in the US. The suspects were detained in Operation Artemis, a joint US-Nigerian law enforcement operation.
eWorldTrade seized: The FBI has seized eWorldTrade, a website used for trading opioids.
Scattered Spider member extradited to US: UK authorities have extradited Tyler Buchanan, a member of the Scattered Spider group, to the US. Buchanan was arrested last year. [Additional coverage in Bloomberg]
US town sues auditor over BEC loss: The Bazetta Township in Ohio has sued its auditor for falling victim to a BEC scam and transferring over $160,000 to an attacker's bank account. The township wants county auditor Martha Yoder to pay half the losses from last year's attack. Yoder claims the township is at fault for the hack because they turned off MFA for their email account and allowed the attacker to pass as a city representative. [Additional coverage in WKBN]
Sherrif's Office falls for BEC scam: The Jefferson Parish Sherrif's Office in Louisiana lost $1.1 million last year to a classic invoice redirection BEC scam. [Additional coverage in Houma Today] [h/t Gary Warner]
DPRK IT workers rely on AI: An Okta report looks at how North Korean IT workers increasingly rely on AI tools to obtain employment in the West.
FBI recommends ad blockers, again: The FBI has recommended that Americans use a browser ad-blocking extension to stay safe against malicious search engine ads. Too bad the FBI hasn't heard that Google destroyed the ad-blocker scene to protect its ad business that profits from the same malicious ads.
New npm malware: Twenty-five malicious npm packages were discovered and taken down last week. Check out the GitHub security advisory portal for more details.
DragonForce RaaS updates: The DragonForce ransomware gang has updated its RaaS program and will now allow threat actors to rent their infrastructure. This allows other groups to run their own RaaS on the larger DragonForce platform but under a different name/brand.
Malware technical reports
RustoBot: Fortinet's security team has spotted a new Mirai-based IoT botnet in the wild. They named this one RustoBot because it's coded in Rust. So far, the botnet only targets TOTOLINK routers.
ELENOR-corp ransomware: Morphisec has found a new ransomware group named ELENOR-corp, a version of the old Mimic ransomware strain.
ConnectiWise malware campaign: ThreatMon has published an analysis of recent malware attacks on ConnectWise infrastructure.
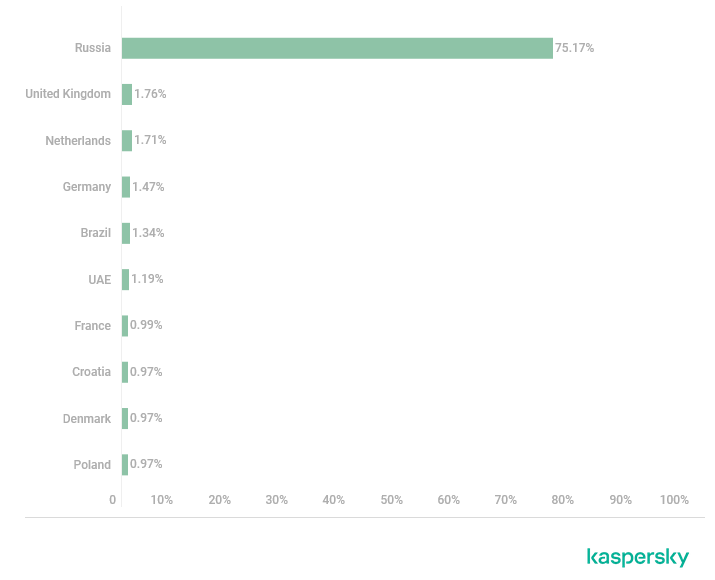
Triada returns: Kaspersky researchers have spotted a new version of the Triada Android trojan. The malware was found on devices whose firmware was infected even before they were available for sale. At least 4,500 devices have been found infected so far. Most are located in Russia, a place where the malware has found a solid market over the past half-decade.
Sponsor section
COACH is an AI-powered security mentor that guides SOC analysts through alert investigations, turning every security alert into a learning opportunity. Available as a free Chrome extension with zero data retention
APTs, cyber-espionage, and info-ops
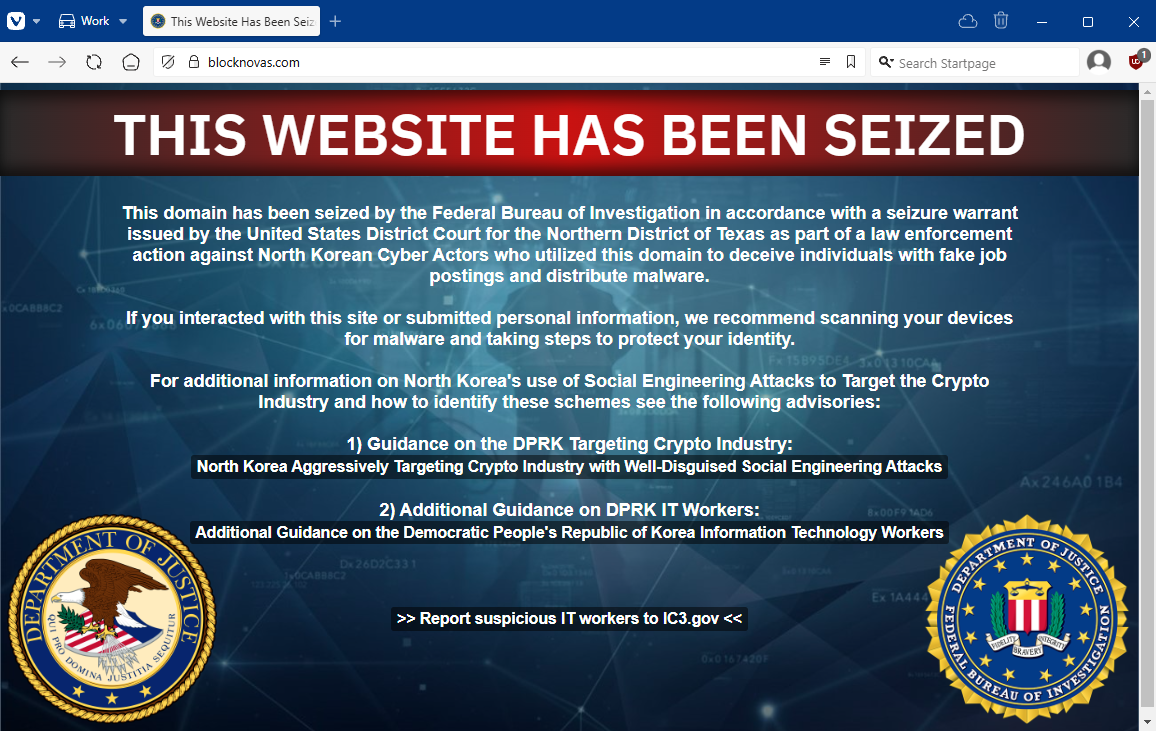
DPRK hackers create companies in the US: North Korean hackers used two US front companies to lure blockchain developers to fake job interviews. The two companies, Blocknovas LLC and Softglide LLC, were registered in New Mexico and New York and posed cryptocurrency consulting businesses. Victims applied for jobs at the two companies but were infected with malware that was used to hack their current employers. [Additional coverage in Silent Push]
DPRK martial law phishing: North Korean hackers used recent martial law declarations as lures in recent phishing operations that targeted over 17,000 users. [Additional coverage in KBS]
Salt Typhoon rewards: The US is seeking information and offering a reward for individuals linked to Salt Typhoon, the APT that hacked US telcos last year.
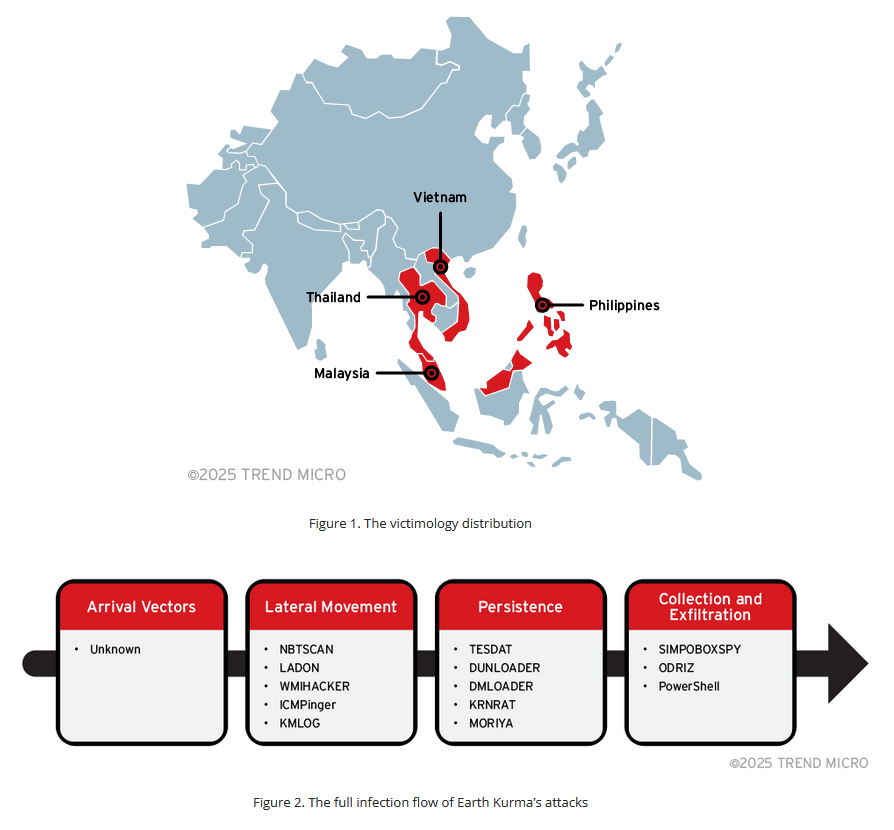
Earth Kurma: Trend Micro has spotted a new APT group named Earth Kurma, currently targeting the government and telecommunications sectors in Southeast Asia.
Vulnerabilities, security research, and bug bounty
Teltonika exploitation: Threat actors are hacking Teltonika SMS gateways in what appears to be massive SMS spam campaigns. Attackers are targeting devices that still use their default login credentials of user1/user_pass. The observed spam campaigns are targeting users in Belgium and Saudi Arabia.
Craft CMS zero-day: The Craft CMS team has released security updates to fix a zero-day (CVE-2025‑32432) exploited in the wild. Initial attacks were detected as early as February. The attackers are using the zero-day together with another bug to take over websites running the CMS. According to the Orange SensePost security team, there are over 13,000 sites using vulnerable versions of the CMS, with half located in the US.
Viasat modem RCE: Viasat rolled out an over-the-air firmware update last year to patch an unauth RCE vulnerability tracked as CVE-2024-6198. The vulnerability can only be exploited from the local network.
GL.iNet security updates: GL.iNet has released security updates for some of its routers.
Moodle security updates: The Moodle LMS has released 16 security advisories.
Atlassian security updates: Atlassian released seven security updates last week, part of the company's April Patch Tuesday.
ConnectWise security updates: MSP software provider ConnectWise has released a security update for its ScreenConnect utility to fix a vulnerability that could lead to an entire server compromise.
Planet Technology vulnerabilities: Immersive Labs researchers have found five vulnerabilities in Planet Technology network management and industrial switch products. Some of the bugs include authentication bypasses, pre-auth command injections, and hardcoded credentials. Planet Technology released patches in mid-April.
Inception AI jailbreaks: Various genAI services are vulnerable to a jailbreak known as Inception. This includes OpenAI, Microsoft, Google, Twitter, Meta, Anthropic, Deepseek, and Mistral.
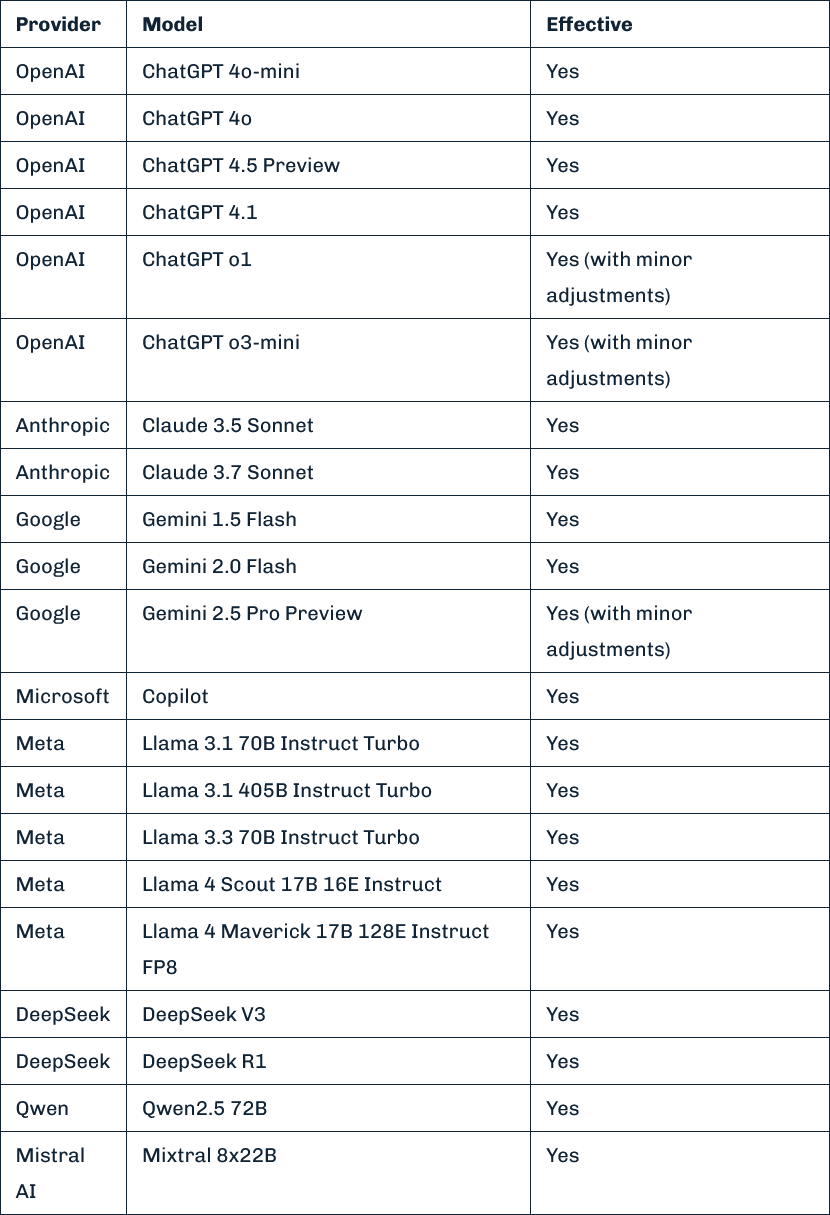
Policy Puppetry prompt injection attack: Models from the eight largest AI companies are vulnerable to a new prompt injection technique named Policy Puppetry. The attack uses specially crafted prompts to trick LLMs into interpreting it as an LLM policy and bypasses security and access restrictions. The attack impacts models from OpenAI, Microsoft, Google, Meta, Anthropic, Mistral, Deepseek, and Qwen.
Infosec industry
Threat/trend reports: Cyberhaven, InsBug, NCC Group, Positive Technologies, Red Canary, Scale VP, and Zscaler have recently published reports and summaries covering various infosec trends and industry threats.
BSides SF 2025 streams: Live streams from the BSides San Francisco 2025 security conference, which took place over the weekend, are available on YouTube.
New tool—Telegram Transparency Data: Privacy advocate Tek has released Telegram Transparency Data, a portal that extracts and safely hosts Telegram transparency data.
New tool—Cookiecrumbler: Web browser Brave has open-sourced Cookiecrumbler, a tool to detect and block cookie consent banners.
New tool—muttpack: Orange SensePost's Dominic White has released muttpack, a collection of scripts to run the Mutt CLI email client in a sandboxed environment.
Microsoft Outlook is pants at usability and running a fat GUI isn’t great for security. About a year ago I went on a mission to make mutt (the CLI mail client) work in a sandbox so I could read my work Microsoft365 mail nicely and more securely. Here’s how
— Dominic White (@singe.bsky.social) 2025-04-26T21:43:13.048Z
Risky Business podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq discuss whether cyber operations can be 'strategic' and affect the fate of nations.
Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and Adam at the helm!




