Risky Bulletin: New Microsoft accounts will be passwordless by default
In other news: Chinese APT hijacks software updates; US dominates EU cybersecurity market; Commvault discloses data breach.

This newsletter is brought to you by Dropzone AI. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
Microsoft is making the passwordless login experience the default for all new user accounts, the company said in a blog post on World Password Day.
New users will have several passwordless options to choose from when creating their account, and they won't need to set up a password going forward.
Existing users also have a new option in their settings that will let them unlink and delete passwords from their accounts.
The Microsoft backend will now also automatically select and enable the user's most secure authentication method going forward. This means that setting up an MFA method or a passkey will automatically make it the default without having to visit the user dashboard settings.
The new change in approach comes as Microsoft also rolled out a new UI and UX for the user authentication process in March that prioritizes and highlights passwordless solutions such as Windows Hello and passkeys as the preferred login and signup methods.
Microsoft says that passwords have been a pain in their back for the past years, with the company now seeing over 7,000 password attacks each second, almost double 2023's stats.
Account compromises linked to password-spraying or brute-force attacks have remained a top source of security breaches for many companies, according to recent reports from Verizon, Sophos, Google, IBM X-Force, and many other security firms.
While passwordless solutions such as Windows Hello are available for new accounts, Microsoft hinted that users would be far more protected by setting up passkeys whenever they can, a technology that completely negates password brute-force attacks.
The company has been one of the technology's earliest adopters. Currently, there are 155 major online websites that support passkeys, covering over 15 billion user accounts, and Microsoft believes that the time of passkeys is now here—joining an effort from the FIDO Alliance to have World Password Day renamed to World Passkey Day.
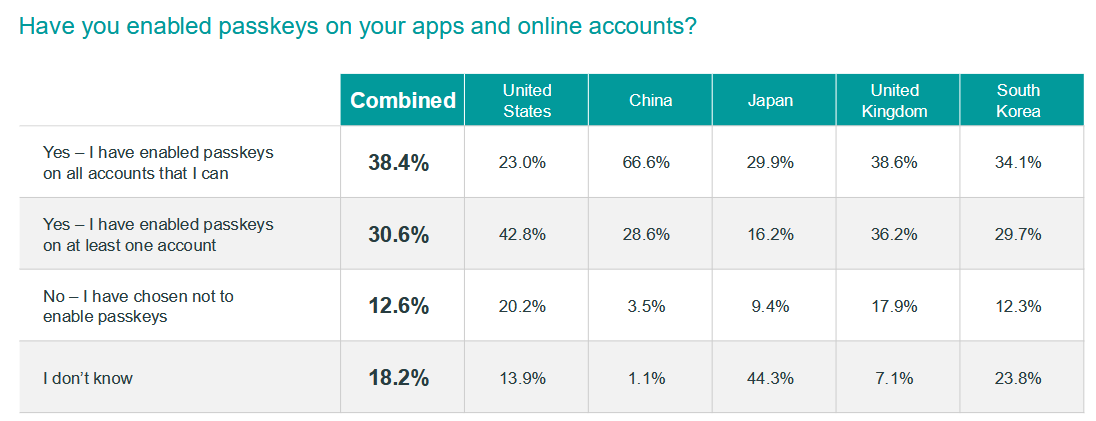
According to FIDO Alliance, over two-thirds of recently surveyed users enabled a passkey for their account, a sign that the technology is slowly becoming commonplace.
Risky Business Podcasts
Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
TehetsegKapu leak: The data of over 55,000 students and teachers was leaked from TehetsegKapu, a website managed by the Hungarian Education Office. [Additional coverage in 444.hu]
Commvault breach: Data backup company Commvault says a state-sponsored hacking group gained access to its Azure environment. The breach took place in February, and Commvault says the attackers did not gain access to any customer backup data. The hack is unrelated to recent attacks on Commvault on-premise backup servers, which are exploiting a recently disclosed bug.
Grafana security incident: The Grafana project says an unidentified individual gained access to its GitHub repository and some tokens. Grafana staff has identified the source of the breach to a recently enabled GitHub Action. The company, which manages open-source and commercial IT monitoring solutions, says it rotated all exposed tokens and found no evidence of abuse or unauthorized access in other parts of its systems.
Cell C ransomware attack: South Africa's fourth-largest telco, Cell C, has confirmed that it suffered a ransomware attack after the RansomHouse gang bragged about it on its dark web leak site. [Additional coverage in IOL]
Co-op and Harrods report intrusion attempts: Two UK retail store chains, Co-op and Harrods, have disclosed security breaches after hackers allegedly tried to gain access to internal systems. Co-op has shut down a part of its IT systems and told staff to turn cameras on during conference meetings. Harrods has shut off internet access at its stores while it investigates. Another UK retailer, Marks & Spencer, has also been dealing with a cyberattack. The company sent staff home and lost half a billion £ in market value after the incident impacted its online orders system.
General tech and privacy
WhatsApp Private Processing: Meta will start rolling out a new WhatsApp feature named Private Processing, a secure container for processing data locally for the company's AI-related features. Also known as "s**t nobody asked for."
Meta does something creepy, part a million: Meta has updated its privacy policy to allow itself the right to take any images and video recordings made through its Ray-Ban Meta smart glasses and use them to train its AI. It's also removing the option that allowed users to not save those recordings, so now everything recorded through those glasses goes to its servers. Enjoy your privacy, kek! [Additional coverage in The Verge]
Telegram launches secure group calls: Telegram has launched support for secure (E2EE?) group calls.
30% of Microsoft code comes from AI: Speaking at the LlamaCon 2025 conference, Microsoft CEO Satya Nadella says that 30% of Microsoft's code is now written by AI. [Additional coverage in CNBC]
Google warns Chrome security will fail: In their anti-trust trial, Google warned that the security of Chrome users will be at risk if the DOJ forces the company to sell the browser. [Additional coverage in Courthouse News]
Government, politics, and policy
CISA restructuring date unknown: CISA acting director Bridget Bean says it's unclear when CISA's restructuring plan will be finished. I'm glad to see the new US administration is winging it when it comes to running a core agency. Makes my unstructured life look a lot better now. [Additional coverage in The Record]
CISA to return to critical infrastructure security: Speaking at the RSA conference this week, DHS Secretary Kristi Noem says CISA will return to its core mission of securing critical infrastructure and stop working on disinformation and election security. [Additional coverage in CyberScoop]
China hacked Guatemala MFA: US officials said that China had hacked the Guatemala Ministry of Foreign Affairs. The hack allegedly took place in September 2022 and was discovered during a joint investigation by the Guatemalan government and the US military. [Additional coverage in Reuters]
US cyber grant program in danger: A GAO report found that state, local, and tribe agencies successfully used a DHS grant to improve their cybersecurity posture but are now in limbo since it's unclear how they'll fund these programs going forward without the grant, which has not been confirmed by the DHS going forward.
Singapore scam losses: The Singapore government says its citizens and companies lost $2.6 billion to online scams since 2019. [Additional coverage in The Strait Times]
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Edward Wu, founder and CEO of Dropzone AI. Edward talks about the impact of AI in modern-day SOC teams and how its role slowly becomes a force multiplier and productivity boost rather than workforce replacement.
Arrests, cybercrime, and threat intel
Nefilim affiliate extradited to the US: US authorities have extradited a Ukrainian national for his role in the Nefilim ransomware gang. Artem Stryzhak was one of the ransomware's several affiliates and was arrested in Spain last June. The Nefilim ransomware launched in 2020 and rebranded multiple times over the years.
Amit Forlit case: Israeli private investigator Amit Forlit, accused of orchestrating hacker-for-hire schemes, lost his extradition case in Britain. He has two weeks to appeal, or he will be sent to the US to face charges. [Additional coverage in Reuters]
New Apple spyware notifications: Apple has sent out a new batch of notifications to users the company believes might have been targeted with government spyware. The notifications were sent this week and went to users in over 100 countries. Two of the recipients include an Italian journalist and a Dutch right-wing activist. [Additional coverage in TechCrunch]
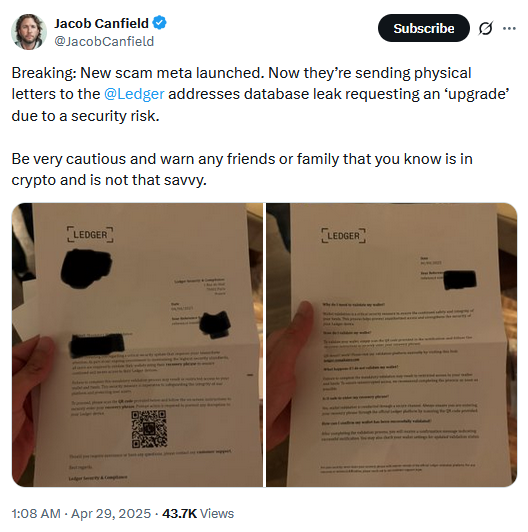
Scam letters target Ledger users: Threat actors are sending physical letters to Ledger crypto-wallet owners. The letters claim they're from the Ledger security team and instruct users to scan a QR code to finish securing their wallets. The QR code takes users to a phishing page that collects their recovery phrases, which the scammers then use to empty out wallets. [Additional coverage in CoinTelegraph]
Subscription scam cluster: Bitdefender researchers have uncovered a cluster of over 200 websites promoting a subscription scam scheme. Traffic to the sites came from Facebook ads that often impersonated celebrities. Facebook doesn't like to remove these ads these days since the company likes profiting from criminal enterprises.
Malicious PyPI packages: Socket Security has spotted seven malicious PyPI packages that use Gmail SMTP servers as tunnels to infected systems.
Phone thieves run phishing infrastructure: BlackBerry researcher Dmitry Bestuzhev looks at a complex phishing cluster that appears to have been operated by a criminal group involved in smartphone thefts. The phishing sites were used to capture iCloud credentials and unlock the stolen devices.
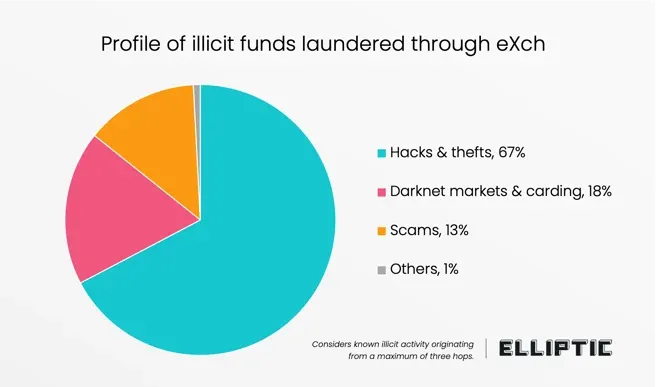
eXch shuts down: Cryptocurrency mixer eXch has shut down operations after investigators linked it to money laundering of several crypto-heists. The service launched in 2014 but only became popular in 2022 after publicly announcing that they refused to work with authorities to track down hacked funds. Over the years, the site has been linked to laundering funds from hacks at Parity Wallet, Bitbrowser, and even the recent Bybit mega-hack. According to blockchain investigations firm Elliptic, 98% of funds that passed through the service were linked to criminal activity, such as hacks, scams, carding, and darknet markets.
Hive0117 targets Russia: Russian security firm F6 has spotted a financially motivated group named Hive0117 launch phishing operations targeting companies in Russia and other former Soviet states. The final payload was the DarkWatchman RAT.
New info on Black Basta leaks: In a new update on its old analysis of the Black Basta chat leaks, Natto Thoughts has found a new small tidbit of information on how some ransomware operators not only have state protection but also appear to have standing job offers from some Russian cyber intel agencies. Le sigh!!!
"In a November 14 2022 chat, 'Tramp' said, 'I have guys in Lubyanka [FSB headquarters] and the GRU [military intelligence agency] – I have been 'feeding' them for a long time. They only want to take people on to work for them. They won't even talk about [prison] sentences or anything. You can go in to work every day at 8 am and leave at 6 pm, just like in a 'white' [legitimate] job.' "
Luna Moth does callback phishing: A ransomware group known as Luna Moth (Silent, UNC3753, or Storm-0252) is using callback phishing techniques to target US organizations in the legal and financial sectors. The campaign started in March and is still ongoing. Attackers use phishing emails to lure victims into calling fake helpdesk numbers. During these calls, the group tricks victims into installing remote access software on their systems, which Luna Moth uses to deploy backdoors, compromise their whole network, and encrypt their data.
State links to cybercrime: Virtual Routes has published a report that looks at the ever-growing ties between state-backed hackers and the underground cybercrime ecosystem and the ransomware scene in particular.

Malware technical reports
BPFDoor: South Korean security firm S2W has published an analysis of a BPFDoor backdoor sample that was used against a local company. That company is most likely SK Telecom, the country's largest telco.
YANB: Trustwave has published a report on a NodeJS-based backdoor delivered through KongTuke (aka 404TDS).
NullPoint Stealer: The source code of the NullPoint Stealer has been leaked on GitHub, according to Danish security researcher Peter Kruse.
Pupkin Stealer: RixedLabs researcher Navneet published an analysis of Pupkin Stealer, a .NET-based stealer coded by a Russian-speaking developer.
New Golden Chickens malware: Recorded Future researchers have discovered new malware (TerraStealerV2 and TerraLogger) operated by the Golden Chickens financially motivated group.
RansomHub: Group-IB has published an overview look at the RansomHub RaaS and its past operations. RansomHub went offline at the start of April after it was hacked by the rival DragonForce gang, and has not restored operations.
"Finally, although it is not clear yet what exactly caused the significant increase in the 'Qilin' disclosures in the last 3 months, there is a chance that criminals have moved from Ransomhub to Qilin. In addition to the increase in the disclosures and recent news advertised by Qilin on RAMP forum right after the RansomHub operation went down, we observed that Qilin's operation has been reorganized with new staff in the support team as well as in the administration of the group."
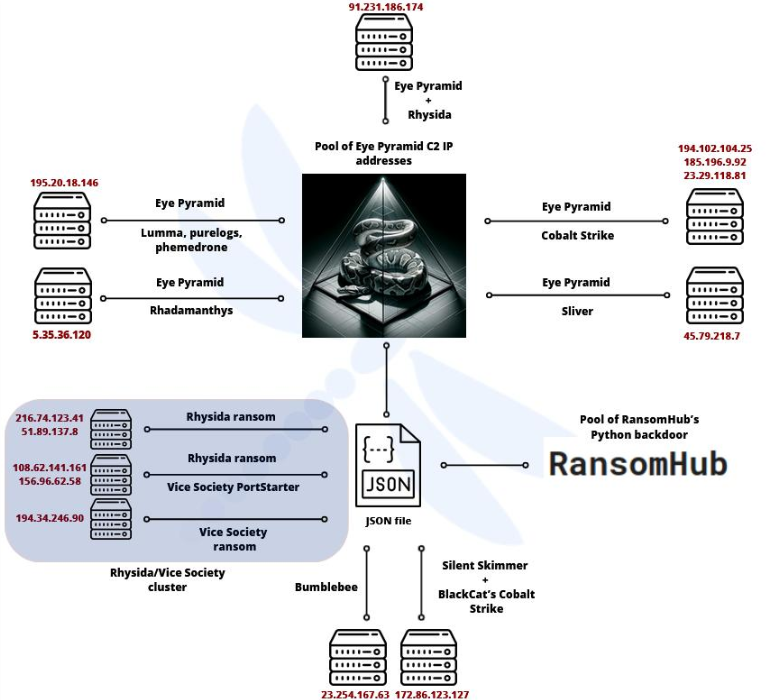
Eye Pyramid C2: Intrinsec has published a report on Eye Pyramid, an open-source command and control tool used by several ransomware groups.
Sponsor section
COACH is an AI-powered security mentor that guides SOC analysts through alert investigations, turning every security alert into a learning opportunity. Available as a free Chrome extension with zero data retention
APTs, cyber-espionage, and info-ops
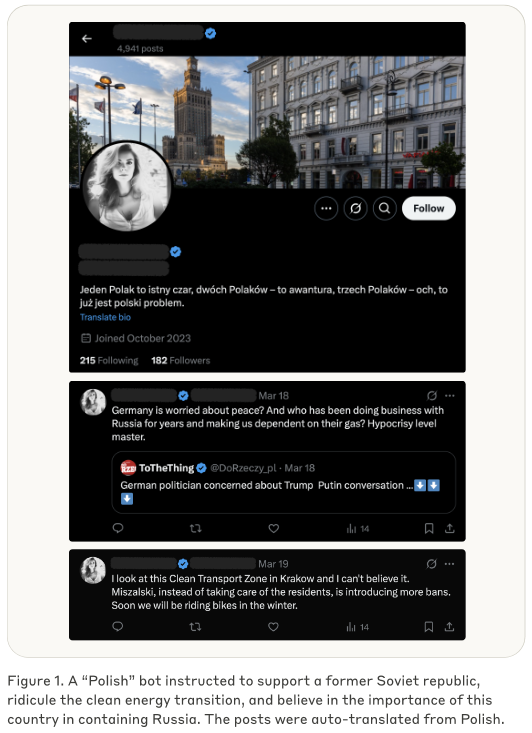
Info-Op abuses Claude AI: Anthropic has discovered a social media influence operation that abused its Claude AI to post across Twitter and Facebook. The operation used over 100 accounts and interacted with tens of thousands of accounts. The campaign used the Claude AI to generate text to attack European, Iranian, UAE, and Kenyan national interests. Anthropic linked the operation to an Influence-as-a-Service platform. [Full report PDF]
EquationDrug bootkit: Chinese security researcher T0daySeeker has published an analysis of EquationDrug, a bootkit part of the Equation Group's malware arsenal. Palo Alto Networks says it spotted the bootkit in the wild in 2024.
Nebulous Mantis/Operation Deceptive Prospect: The RomCom threat actor is abusing customer feedback portals to send phishing emails with malicious links to high-value enterprise targets. The group is known for conducting classic financially motivated crime and espionage operations at the behest of the Russian government. The recent operation, named Deceptive Prospect, targeted companies in the UK. Prodaft has also published a report on this group, which they call Nebulous Mantis.
Russian cyber operations in Ukraine: Ukraine CERT says Russian cyberattacks targeting the country have intensified in the second half of last year, but the vast majority were low-severity incidents as Russian groups appear to have switched to a low-and-slow approach.
Earth Kasha: Trend Micro analyzes a March 2025 campaign linked to Chinese APT group Earth Kasha (an APT10 subcluster) that targeted organizations in Japan and Taiwan with the ANEL backdoor.
TheWizards APT hijacks software updates: A new Chinese APT group is breaching organizations across Southeast Asia and using a novel technique to hijack software updates. Named TheWizards, the group has been active since 2022. Its main tactic is to gain an initial foothold and deploy a tool named Spellbinder on the hacked networks. This tool uses a technique named IPv6 SLAAC spoofing to redirect DNS queries through the group's servers. TheWizards intercepts queries associated with software update domains for Chinese software and redirects users to malicious updates that install backdoors on their systems. Security firm ESET has linked the APT to a Chinese company named Dianke Network Security Technology—doing business as UPSEC.
Since at least 2022, the group has targeted individuals, companies, and unknown entities in the Philippines, the United Arab Emirates, Cambodia, mainland China, and Hong Kong. 2/6
— ESET Research (@esetresearch.bsky.social) 2025-04-30T11:30:20.169Z
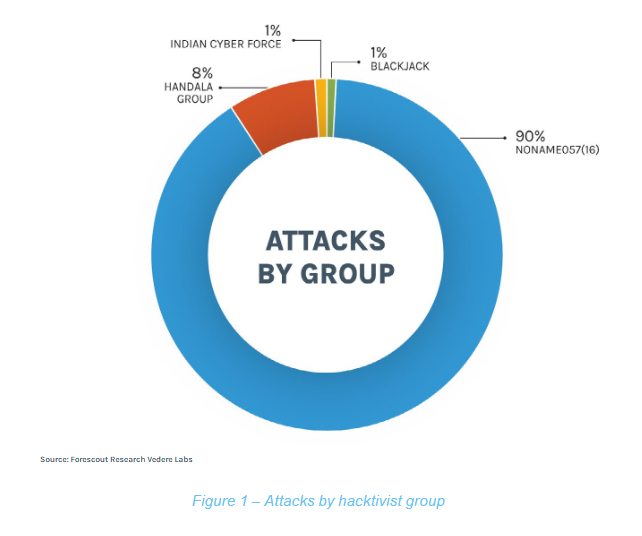
State-backed hacktivism: Forescout's Vedere Labs has published an overview of all the recent state-sponsored "hacktivism" campaigns, most of which have been the work of NoName057, a group associated with Russia's military intelligence. [Full report PDF]
Vulnerabilities, security research, and bug bounty
SMA exploitation: SonicWall says threat actors are exploiting two older bugs (CVE-2023-44221 and CVE-2024-38475) to hack unpatched SMA VPN gateway appliances.
macOS App Sandbox escape: Microsoft has published a write-up on CVE-2025-31191, a sandbox escape bug patched last month that allowed malicious code to escape the macOS App Sandbox.
MagicINFO unauth RCE: SSD Disclosure has published details and a PoC for a bug that allows unauth RCE attacks on MagicINFO digital signage systems.
Node.js CI security incident: The Node.js team has overhauled its CI/CD pipeline after security firm Praetorian found a loophole in one of its test pipelines that tricked Node's Jenkins servers into retrieving and running malicious code.
PLeak technique: Trend Micro described PLeak, a technique to jailbreak LLMs and leak system prompts.
RDP backdoor concerns: ArsTechnica has taken a look at an old problem with the Windows RDP service where some old RDP passwords still work to access RDP accounts. This is an old issue I've seen before (sorry, can't remember the original source) and is a trade-off where Microsoft allows this to happen by design to cover offline endpoint scenarios.
Infosec industry
US dominates EU cybersecurity market: US companies dominate the EU cybersecurity market, where EU providers only have a 25% market share. The Dutch government warns the EU is currently dependent on foreign companies for its cybersecurity services. Officials have called that some of the EU's current defense investment also be directed towards cybersecurity.
Raytheon fined: Raytheon has agreed to pay a $8.4 million fine for failing to comply with cybersecurity requirements related to 29 Pentagon contracts between 2015 and 2021. The company's non-compliance was exposed by a former director of engineering, who will receive $1.5 million from the settlement.
New tool—Chronos: Security researcher Michalis Antoniades has released Chronos, a kernel extension to support EDR-like capabilities on RTOS embedded systems.
New tool—LlamaFirewall: Meta has released LlamaFirewall, a framework to detect and mitigate AI-related security risks.
New tool—SquarePhish: Security researcher Nevada Romsdahl has open-sourced SquarePhish, a phishing toolkit that combines OAuth Device Code authentication flows and QR codes.
New tool—PrimeEncryptor: Security researcher Dhanush Arvind has open-sourced PrimeEncryptor, a payload encrypter with support for multiple encryption techniques.
New tool—Paradox: A GitHub user named Esson has released Paradox, a PoC macOS stealer written in Go.
New tool—Google MCP Servers: Google has released a collection of MCP servers to allow MCP clients to connect and access Google security products and services.
Threat/trend reports: CERT-UA, Check Point, CNIL, FIDO Alliance, Forescout, and Sygnia have recently published reports and summaries covering various infosec trends and industry threats.
PQCrypto 2025 videos: Talks from the PQCrypto 2025 security conference, which took place in early April, are now available on YouTube.
Risky Business podcasts
Tom Uren and Patrick Gray talk about a SentinelOne report about how it is constantly targeted by both cybercriminal and state-backed hackers. Security firms are high-value targets, so constant attacks on them are the new normal.
In this edition of Between Two Nerds, Tom Uren and The Grugq discuss the Southeast Asian criminal syndicates that run online scam compounds. Should organizations like US Cyber Command or the UK's National Cyber Force target these gangs with disruption operations?




