Risky Bulletin: Microsoft will integrate Sysmon into Windows
In other news: Another sneaky Chat Control push; Russian surveillance vendor gets hacked; CISA to hire new staff in 2026.

Risky Business Podcasts
The main Risky Business podcast is now on YouTube with video versions of our recent episodes. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
Russian surveillance vendor got hacked: An unidentified threat actor has hacked and leaked sensitive data from Protei, a Russian company that makes telecom-grade surveillance gear, including equipment for Russia's SORM system. [TechCrunch]
Cyberattack disrupts Russian port operator: A cyberattack has crippled the operations of Port Alliance, a Russian company that manages cargo terminals at six Russian ports. The incident lasted days and disrupted Russian coal and fertilizer shipments. [The Record]
NHS impacted by Oracle zero-days: The UK National Health Service (NHS) has joined a long list of companies that were hacked using an Oracle EBS zero-day this summer. [SecurityWeek]
Logitech discloses breach: Logitech has confirmed a security breach to the US SEC after the company's name was listed on the Clop ransomware group's dark web leak site last month. This is the group behind the Oracle EBS zero-day attacks.
LG ransomware attack: LG's battery subsidiary has fallen victim to a ransomware attack. The Akira group took credit for the attack in a post on its dark web leak site. [The Record]
DoorDash breach: Food delivery service DoorDash is notifying users of a security breach that took place last month.
Princeton hacked: A hacker has stolen the data of the University of Princeton alumni, donors, faculty, students, and parents. [Princeton]
Somalia e-visa system hack: Hackers breached and stole data from Somalia's e-visa system, a portal where foreigners apply for entry visa in the country. The data of more than 35,000 applicants was stolen in the incident. [The Somalia Guardian]
Kenyan govt sites defacements: Hackers have defaced multiple Kenyan government websites with nazi and white supremacy messages. [The Record]
Under Armour ransomware attack: The Everest ransomware group has claimed an attack on sportswear brand Under Armour. [Cybernews]
Eurofiber hack: Internet infrastructure company Eurofiber has confirmed a security breach at its French division. The breach impacted the company's ATE customer portal and ticket management platform.
Pajemploi breach: French social security agency Pajemploi has disclosed a security breach that impacted the personal information of more than 1.2 million individuals.
Victoria schools hack: Parents at Catholic schools across the Australian state of Victoria have been locked out of school accounts after a security breach. [The Courier] [h/t Scrantic]
General tech and privacy
Sysmon to be added in Windows 11: Microsoft will add Sysmon, a third-party app from the Sysinternals package, into future versions of Windows 11 to help with security log analysis.
Windows point-in-time restore: Microsoft Intune will get a new feature that can restore Windows 11 systems to a particular point in time. The same service is also getting a feature to send installation media to a Windows 11 system and force it to rebuild itself.
Apple to require apps to disclose AI data sharing: Apple has updated its developer guidelines and will now require every app to disclose if it collects and shares user data with AI companies. They must also ask users for permissions. [Cult of Mac]
Cloudflare outage: Cloudflare has experienced another internet-shattering outage on Tuesday, November 18.
Thunderbird now supports Exchange accounts: Thunderbird 145, released this week, now natively supports Microsoft Exchange-based email accounts.
New PyPI security feature: The PyPI portal will now require email-based verification for all Time-based One-Time Password (TOTP) logins coming from new developer devices.
"Users who have enabled WebAuthn (security keys) or passkeys for 2FA will not see any changes, as these methods are inherently phishing-resistant."
npm shortens auth tokens: The npm portal has revamped its user access tokens. New tokens will have a default life of seven days (instead of 30), which can be updated to a maximum lifespan of 90 days (previously unlimited). The changes are going live this month.
Outdated device leads to death: Australian telco TPG Telecom says a customer died after their Samsung phone was running out-of-date software and couldn't connect to the Triple Zero emergency service. [ABC]
I find this outrageous Triple zero emergency calls must operate on any device that's what the system is for Weasel words ducking responsibility 'TPG Telecom says a Sydney customer died after outdated software blocked a Samsung phone from making Triple Zero (000) calls' www.abc.net.au/news/2025-11...
— Ross (@flicksfan.bsky.social) 2025-11-18T08:13:53.109Z
Government, politics, and policy
New Chat Control push: Danish officials have found a new way to push for the Chat Control encryption-breaking legislation without the proposed law going through a public debate. [Patrick Breyer]
CatalanGate spyware scandal: The European Court of Human Rights has dismissed a case brought by Catalan opposition figures over the CatalanGate 2022 spyware scandal due to a lack of evidence. [Politico]
Germany prepares more Chinese equipment bans: The German Parliament has given the country's Interior Ministry the legal power to ban Chinese equipment over cybersecurity and national security risks.
Taiwan warns of China's genAI: The Taiwanese government has warned citizens against using Chinese-made generative AI models because they may contain pro-CCP propaganda in their output.
UK's ransom ban gets pushback: The private and public sectors are opposing the UK government's plan to ban ransomware payments. [The Financial Times]
CISA to hire new staff: After firing roughly a third of its staff, CISA has promised to hire new personnel next year. [CybersecurityDive]
Scoop: CISA plans to embark on a hiring spree and change some workforce policies in an effort to rebuild its depleted ranks ahead of a possible conflict with China, according to a memo from its acting director that I obtained. www.cybersecuritydive.com/news/cisa-hi...
— Eric Geller (@ericjgeller.com) 2025-11-17T21:30:28.758Z
IRS accessed data without warrant: The US Internal Revenue Service accessed and searched a data broker's database of flight and travel records without a legal process, such as a warrant. [404 Media]
Incoming US VPN bans: At least two US states are considering banning VPN products in order to prevent residents from avoiding internet age verification checks. [EFF]
US invests in AI cyberwarfare: The US government has quietly invested in AI agents that could be used for cyberwarfare. [Forbes]
CISA 2015 to get another 10: US lawmakers want to extend the CISA 2015 cyber data-sharing law by another 10 years. [NextGov]
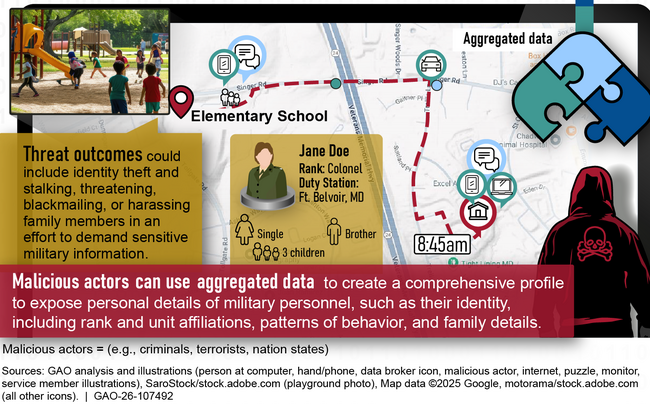
A ton of exposed DOD gear/data: GAO says the US Department of Defense is at heightened risk because huge quantities of sensitive data on personnel and their devices are easily accessible online through data brokers or leaked data sets.
Risky Business podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about the strategic "logic" of Russian wiper attacks on the Ukrainian grain sector.
Arrests, cybercrime, and threat intel
South Korean sentenced for contacting North Korean hacker: South Korea has sentenced a man to one year in prison for buying hacking tools from a North Korean hacker via the QQ messenger. [The Chosun Daily]
Wind farm admin sentenced: A Dutch man has been sentenced to 120 hours of community service for deploying cryptominer equipment on the wind farm's network.
Dutch police arrest credit card fraudsters: Dutch authorities have arrested two men from Amsterdam for using phishing emails impersonating the International Card Service (ICS) to steal funds from victims' bank accounts.
Bulletproof server seizure: Dutch police have seized 250 servers linked to an unnamed bulletproof hosting provider. According to Spamhaus, the takedown also took down the CrazyRDP marketplace for hacked servers.
Twitter hack seizure: The UK has seized £4 million from Twitter hacker Joseph James O'Connor.
DOJ issues warrants for Starlink gear: US investigators have started to issue seizure warrants for Starlink devices and accounts tied to scam compounds in Southeast Asia. This comes after the company failed to move its buttocks and do something/anything about the abuse. [WIRED]
DPRK helpers plead guilty: Four Americans pleaded guilty to helping North Korean IT workers find remote jobs in the US by selling their own identities and even hosting laptops at their homes. A fifth, a Ukrainian man, pleaded guilty to stealing the identities of US citizens and selling the data to DPRK workers.
ValleyRAT campaign in Vietnam: Vietnam's cyber police warn of a ValleyRAT distribution campaign that uses draft documents of the Community Party's upcoming 14th National Congress as a lure. The malware has been historically linked to SilverFox, a Chinese-speaking cybercrime group. [Bao Van Hoa]
EVALUSION campaign: eSentire has spotted EVALUSION, a new ClickFix campaign delivering the Amatera Stealer and NetSupport RAT.
WEBJACK campaign: WithSecure looks at a malware campaign that compromises Microsoft IIS servers to deploy malicious IIS modules belonging to the BadIIS malware family. The hacked IIS servers are used for SEO poisoning and to redirect users to gambling and casino sites.
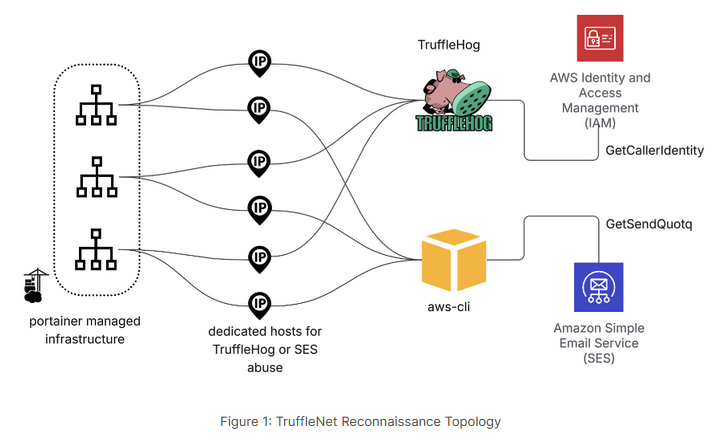
TruffleNet campaign: Fortinet has spotted a campaign targeting cloud environments. The campaign, named TruffleNet, is built around the TruffleHog open-source toolkit.
Finger abuse: A threat actor is using the Finger protocol as part of a malware campaign, to retrieve and run malicious commands on infected hosts. [BleepingComputer]
Online investment scam increase: In its semi-annual threat report, Switzerland's cybersecurity agency says there's a five-fold increase in online investment scam ads.
npm token farming: AWS has spotted a campaign that flooded the npm portal with more than 150,000 packages as part of a scheme to generate Tea cryptocurrency tokens. These tokens provide rewards to developers based on the popularity of their projects. The campaign started in April 2024, and some of the packages are still live.
New DPRK remote IT worker insights: The Chollima Group has published new insights into North Korean remote IT worker schemes and personnel.
Proxy.vn proxy network: Qurium has linked recent DDoS attacks against investigative news outlet iStories to Proxy.vn, a Vietnam-based proxy-for-hire network.
"Qurium has attributed the attacks to Proxy.vn, a proxy service operated by Hoàng Văn Chung and Hà Minh Trọng. Proxy.vn runs a vast IP-rotation system that enables anonymous high-volume traffic, DDoS activity, and coordinated manipulation of online social media platforms. Qurium has located the previously undisclosed tin-roof warehouse datacenter in Tuyên Quang Province. This facility aggregates hundreds of residential and mobile internet connections from large Vietnamese ISPs, enabling activities that appear to originate from real user networks."
Major Aisuru DDoS attack: Microsoft says it mitigated a massive 15.72 Tbps and nearly 3.64 bpps DDoS attack targeting one of its Azure customers. The company linked the attack to Aisuru, a botnet of more than 500,000 infected home routers and security cameras.
Remcos C2 survey: Censys says it is tracking 150+ command and control servers for the Remcos RAT.
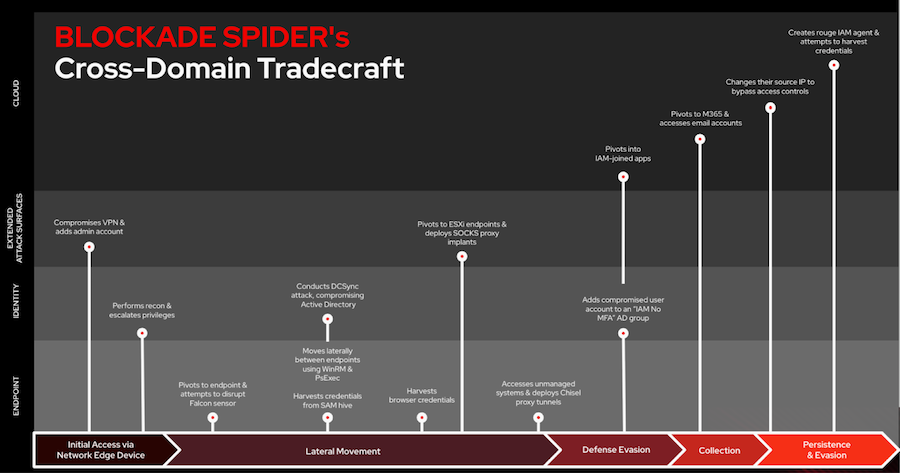
BLOCKADE SPIDER profile: CrowdStrike has published a profile on BLOCKADE SPIDER, an e-crime group engaging in attacks with the Embargo ransomware.
Malware technical reports
Sneaky2FA adopts BitB: The Sneaky2FA phishing kit has added support for Browser-in-the-Browser (BITB) functionality, a technique that shows a fake browser address bar inside the browser window to trick users into thinking they're on a legitimate website. [Push Security]
Tuoni: Morphisec has spotted threat actors abusing the Tuoni post-exploitation C2 framework in the wild.
Gh0st RAT: PAN's Unit42 looks at the rising number of large-scale campaigns targeting Chinese-speaking users with the Gh0st RAT.
RONINGLOADER: Elastic has discovered RONINGLOADER, a new multi-stage loader used by the Dragon Breath (APT-Q-27, Golden Eye Dog), a financially motivated group targeting the gambling sector with SERP poisoning, social engineering, and DDoS attacks.
BTMob on the Play Store: D3Lab has spotted the BTMob spyware hidden inside GPT Trade, an app available through the official Android Play Store.
Lynx Ransomware: The DFIR Report team looks at an intrusion with the Lynx ransomware.
The Gentlemen ransomware: Cybereason has published a technical report on The Gentlemen, a new ransomware group that popped up online in August.
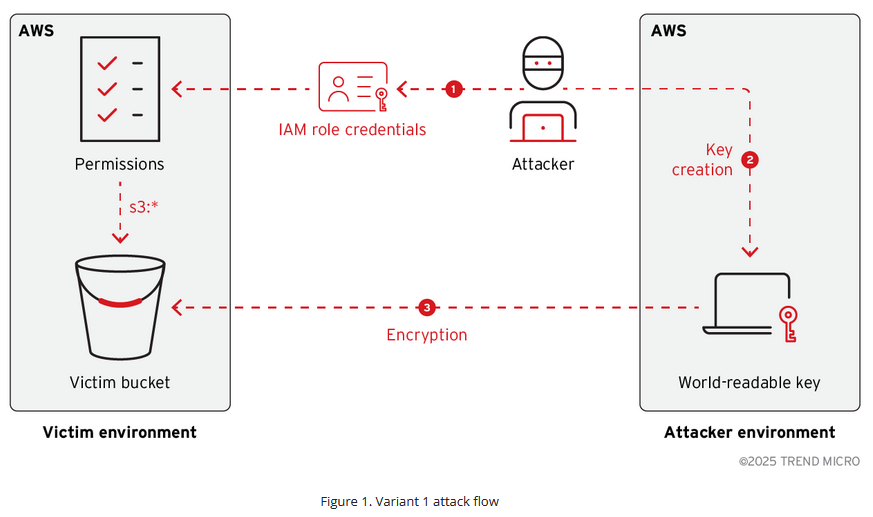
S3 ransomware variants: Trend Micro looks at all the ransomware versions spotted in the wild that attacked Amazon S3 buckets.
Risky Business podcasts
In this edition of Seriously Risky Business, Tom Uren and Amberleigh Jack talk about a new Reuters report that reveals how Meta is knowingly raking in cash from scam advertisements. It's around $16 billion worth, and in documents, Meta calculates that it outweighs the costs of possible regulatory action.
APTs, cyber-espionage, and info-ops
Void Blizzard arrest: Thai authorities have arrested Russian national Denis Obrezko at the request of the US. He is allegedly a member of the Void Blizzard (Laundry Bear) APT. [CNN]
SpearSpecter: The Israel National Digital Agency has published a report with the most common TTPs of Iranian APT group SpearSpecter (APT42).
UNC1549: Google has published a report on UNC1549, an Iranian cyber-espionage group targeting the aerospace, aviation, and defense industries. This appears to be what others call Nimbus Manticore.
MuddyWater: Qihoo 360 has published a report on a MuddyWater campaign delivering the UDPGangster backdoor.
APT37's RokRAT Loader: CTI researcher YUCA has published an analysis of RokRAT Loader, a malware strain used by DPRK APT group APT37 (Reaper).
Lazarus' ScoringMathTea: Malware researcher 0x0d4y analyzes looks at ScoringMathTea, a new RAT linked to the Lazarus Group.
UNC5174's SNOWLIGHT: IIJ-SECT has published a report on the Windows version of SNOWLIGHT, a malware downloader used by UNC5184. The group is a suspected MSS cyber contractor.
New disinfo tactic: A Russian disinfo network is using Mastodon instances and bridge accounts to push propaganda on BlueSky.
There's a Russian disinformation network operating from Mastodon to push content into BlueSky, it's a few hundred active accounts (they also exist directly on BlueSky natively too). It probably costs more to run than the value it provides to whoever runs it, tbh. cyberplace.social/@GossiTheDog...
— Kevin Beaumont (@doublepulsar.com) 2025-11-15T11:46:08.857Z
Vulnerabilities, security research, and bug bounty
Important security updates: ASUS, Atlassian, Netgear, SolarWinds, Synology, Zyxel.
Chrome zero-day: Google has released a Chrome security update to patch an actively exploited zero-day (CVE-2025-13223).
Fortinet zero-day #1: A threat actor is exploiting a zero-day (CVE-2025-64446) in the web GUI of Fortinet firewalls. Attacks were first spotted by Defused. Some write-ups on the bug are available via Rapid7, PwnDefend, and watchTowr Labs. The zero-day allows attackers to create admin accounts on internet-exposed devices using a malcrafted HTTPS request.
Fortinet zero-day #2: A few days later, a second Fortinet zero-day was also spotted being exploited in the wild, this one tracked as CVE-2025-58034. It's unclear if it's connected to the first.
New ShadowRay exploitation: Oligo Security has spotted a threat actor named IronErn440 exploiting a 2023 vulnerability in the Anyscale Ray AI framework, aka ShadowRay, in new attacks.
GoSign Desktop RCE: Security researchers have found vulnerabilities that can lead to RCE attacks against the Tinexta GoSign Desktop electronic signature solution.
Shelly smart relay power outages: Nozomi researchers have found a vulnerability in the Shelly Pro 4PM smart relay and power metering product that could cut power to smart homes.
Elliptic vulnerabilities: Trail of Bits has found two vulnerabilities in Elliptic, a widely used JavaScript library for elliptic curve cryptography with more than 10 million downloads/week.
EchoGram attack: HiddenLayer researchers uncovered a new technique named EchoGram that can reliably flip the decisions of the guardrails of all major LLMs, including the new GPT-5.1 (and all underlying models), Claude, and Gemini.
WhatsApp enumeration bug: A team of academics has found an enumeration bug in WhatsApp that allowed them to extract the phone numbers of all of the app's users. [WIRED]
Meta bug bounty: Meta says it awarded more than $4 million in bug bounties this year and $25 million since its launch 15 years ago. This year, it received 13,000 bug reports and awarded bounties for 800.
Infosec industry
Threat/trend reports: The Center for Strategic Research [PDF], DCSO, IANS, NCC Group, Positive Technologies, Rubrik, Swiss NCSC, Thinkst, ThreatMon, Trellix [PDF], the US DOJ, Veracode [PDF], and WanAware have recently published reports and summaries covering various threats and infosec industry trends.
Acquisition news: Security firm Huntress has acquired Inside Agent, a London-based company specializing in Microsoft 365 security.
New tool—YAMAGoya: Japan's CERT has open-sourced YAMAGoya, a C# application that leverages Event Tracing for Windows (ETW) to capture real-time system events.
New tool—SAMDump: Security researcher Ricardo Ruiz has released SAMDump, a tool designed to extract SAM and SYSTEM file data using the Volume Shadow Copy (VSS) API.
Fluxcon 2025 videos: Talks from the Fluxcon 2025 security conference, which took place at the start of the month, are available on YouTube.
Nullcon Berlin 2025 videos: Talks from the Nullcon Goa 2025 security conference, which took place at the start of September, are available on YouTube.




