Risky Bulletin: Microsoft tells users to uninstall games affected by major Unity bug
In other news: Discord discloses data breach; Gmail rolls out E2EE; Apple and Google block ICE tracking app.

This newsletter is brought to you by Corelight. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
Microsoft and the Steam gaming platform have reacted over the weekend to a new security flaw discovered in Unity, one of today's most widely used game engines.
The vulnerability was discovered by RyotaK, a researcher for GMA Flatt Security, who has quite a few of these high-impact bugs to his name.
The bug is tracked as CVE-2025-59489, and it allows malicious apps on the same device to add command-line arguments to Unity-based games that load malicious code together with a game.
RyotaK says his research studied the vulnerability on Android, but that the bug can also impact games on other platforms as well. In some very narrow scenarios, the bug can also be exploited via browsers or remote scenarios, for even more wide-reaching impact.
The vulnerability was discovered and reported in June, and Unity released a patch last week.
It impacts all games that were compiled via the Unity Editor app version 2017.1 or later. That means all Unity games released for the past eight years are impacted.
Game developers will have to recompile their games in an updated Game Editor version and then ship the updated game to their users to prevent exploitation.
The bug is relatively easy to exploit and extremely dangerous due to Unity's popularity among developers and the large number of games in the wild. It is a huge attack surface, one that has scared both Microsoft and Steam alike, two of today's largest game platform operators.
While Microsoft said that Xbox games are not impacted, Windows games are ripe for exploitation. The company has urged users to uninstall Unity games until they receive security patches that directly address CVE-2025-59489.
Valve has also taken precautions, and its Steam platform now blocks all Unity-based games if they are launched with one of four command-line parameters shared by Unity and used to exploit the bug.
Over the weekend, some game developers rolled out patches, but more are likely to come this week, as they see the Steam platform's security alert.
The bug is extremely likely to see active exploitation, since it allows low-privileged attackers a way to run malicious code on a system, and you're bound to find a Unity game or app somewhere inside a network.
The Unity Security bug (affecting all Unity games) has been patched in Pinnacle Point and uploaded to Steam. CVE-2025-59489 related. #gamedev #screenshotsaturday #indiegamedev #horrorgames
— Robin | Pinnacle Point, Solo GameDev (@ready2rungames.bsky.social) 2025-10-04T08:44:09.251Z
We're pleased to announce that all of our downloadable game builds have been patched to fix the CVE-2025-59489 vulnerability of the Unity Editor, on Steam and Itch, for our two games:
— ShidyGames 🕹️ (@shidygames) October 4, 2025
➡️ Escape Space
➡️ Robot Arena Survivors
Thank you for your trust, and have fun!
I have personally patched all of my Unity games affected by CVE-2025-59489 on Steam. Please let me know if you run into any issues.
— Toikka (@TomiToikka) October 3, 2025
Risky Business Podcasts
The main Risky Business podcast is now on YouTube with video versions of our recent episodes. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
Discord breach: Hackers have stolen sensitive user data from messaging platform Discord. The breach took place at a third-party company that handles Discord's customer support. The stolen data includes names, emails, payment details, and customer support tickets. Some government ID scans collected for age verification were also stolen.
Renault UK hack: Renault's UK branch has been hit by hackers. The company says that customer data was stolen from one of its third-party data processing partners. The French carmaker didn't say how many users were affected. Stolen data included customer names, addresses, dates of birth, phone numbers, and vehicle details. [Additional coverage in the BBC]
US Air Force breach: The US Air Force is notifying individuals affected by a recent security breach. The Air Force allegedly shut down all its SharePoint and Teams servers to investigate the intrusion. Some personal data is believed to have been exposed or stolen. [Additional coverage in CyberDaily]
Rostec leak: A pro-Ukrainian hacking group has dumped a collection of files stolen from Russian state defense corporation Rostec. The documents allegedly show Rostec's efforts to evade Western sanctions. It's unclear when the files were stolen. [Additional coverage in The Insider]
Flagstar settlement in Accelion breach: Flagstar Bank will pay $31.5 million to settle a lawsuit related to a 2021 security breach, when hackers stole the personal information of 2.2 million customers from its Accellion file-transfer appliance. [Additional coverage in Bloomberg Law]
ParkMobile settlement: ParkMobile users received a $1 credit as part of a settlement in a class-action lawsuit filed against the company over its 2021 security breach. [Additional coverage in The Drive]
Partiful GPS leak: Social event planning app Partiful forgot to strip GPS location data from user-uploaded photos. [Additional coverage in TechCrunch]
US Courts post hack: The Administrative Office of the US Courts is ignoring a congressional request to review its cybersecurity practices after a security breach earlier this year. Instead, the Office has made it more difficult to get access to recently unsealed documents. According to CourtWatchNews, PACER users are now required to file requests directly with the courts that unsealed the documents, which greatly slows the process of gaining access to the files.
Oracle extortion campaign: Oracle has linked a recent extortion campaign against Oracle customers to a vulnerability in the Oracle E-Business Suite platform. Oracle CSO Rob Duhart says the vulnerability was patched in July. The campaign got underway last week and has been linked to the Clop ransomware and data extortion group. [Update: We removed the CVE from this item. It was not the CVE for the old July E-Business Suite vulnerability, but the CVE of a new zero-day. The Clop gang used both old bugs and a new zero-day. More updates will be provided in our next edition, on October 8.]
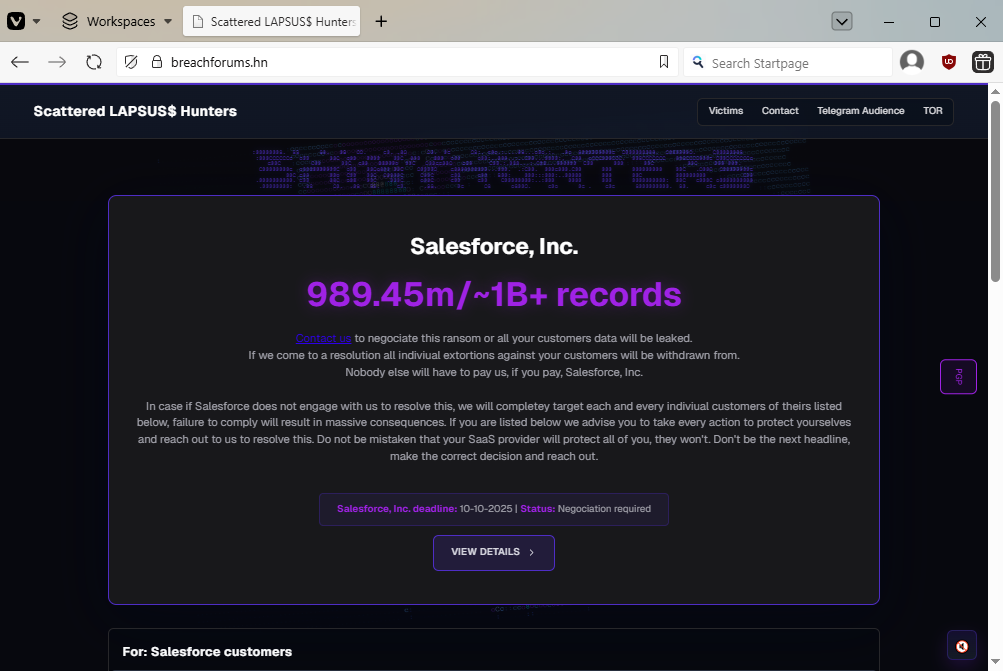
Salesforce denies new hack: Salesforce has denied getting hacked again after hackers launched an extortion portal on Friday. The company said the data came from the same breach from earlier this year. The hack took place after a group named Scattered LAPSUS$ Hunters socially-engineered Salesforce customer support, gained access to customer accounts, and then stole their data. The hackers are now threatening to release all the data unless Salesforce pays up.
General tech and privacy
LLMs in press releases: An academic study found that LLMs were used to write almost a quarter of all corporate press releases.
Very nice article co-authored by one of my former students, Mihai Codreanu, discovering how much of many documents eg press releases, job postings, have been written using LLMs (10-20% depending on type of document but it might have stabilised in late 2024) www.cell.com/patterns/ful...
— Diane Coyle (@dianecoyle1859.bsky.social) 2025-10-03T07:51:38.807Z
LinkedIn sues ProAPIs: LinkedIn has filed a lawsuit against a company and its CEO for using millions of fake accounts to scrape its website. LinkedIn claims that ProAPIs conducted an "industrial scale" scraping operation and charged $15,000 to access the data. Scraped data included user profile data, posts, reactions, and comments. LinkedIn won a lawsuit against another company that scraped its website in July. [Additional coverage in PCMag]
California sues El Cajon over privacy violations: The California Attorney General has sued the city of El Cajon for breaking the state's privacy laws. The city allegedly allowed law enforcement outside of the state to search California's license plate reader database. According to State Attorney General Rob Bonta, El Cajon officers run searches against the database on behalf of requests received from other states. [Additional coverage in The Record]
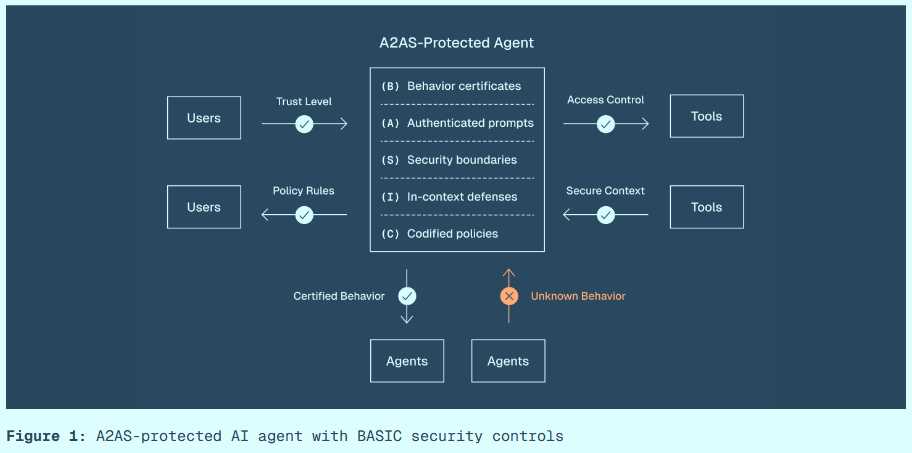
New A2AS standard: Ten tech companies have published a security framework designed to protect AI agents and protocols. The new Agent-to-Agent Security framework, or A2AS, provides recommendations for securing communications between AI agents and their prompts. Contributors include the likes of AWS, Google, Meta, Bytedance, and Cisco.
Signal adds SPQR support: Signal has added a new defense against post-quantum encryption attacks in the form of the Sparse Post Quantum Ratchet (SPQR).
Apple, Google block ICE tracking app: Apple and Google have blocked downloads of an app that allowed Americans to track the whereabouts of ICE agents. Apple took down the ICEBlock app after pressure from the US Justice Department, while Google took it down preemptively. US Attorney General Pam Bondi claimed the app put ICE agents at risk. [Additional coverage in the AP]
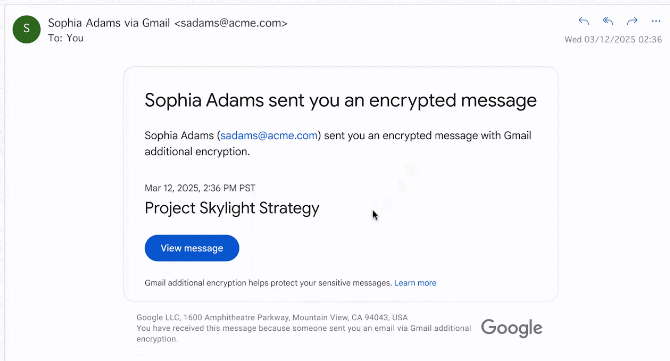
Gmail E2EE rollout: Google has rolled out support for sending end-to-end encrypted emails to Gmail enterprise customers. The feature will work even if recipients are not using a Gmail account. Recipients will receive a notification, and they'll be able to read the encrypted message via a guest Gmail account. The feature went live last Thursday.
Government, politics, and policy
Pentagon patches NCG2 platform: The US Army has patched multiple vulnerabilities discovered in its new battlefield communication platform. The Next Generation Command and Control platform, or NCG2, was developed by Anduril and Palantir and connects data from soldiers, sensors, and vehicles in real-time. An internal Army memo says that the platform was vulnerable to insider threats, external attacks, and data leaks. The Army says the issues have now been patched since being reported. Work on the new platform began this July and has cost the Pentagon $100 million. [Additional coverage in Breaking Defense]
Who, WHO could have foreseen that the techbros cosplaying as defense experts would create a disastrously insecure product?
— Taggart (@taggart-tech.com) 2025-10-03T12:57:56.000Z
Sponsor section
In this Risky Business sponsor interview, Catalin Cimpanu talks with Ashish Malpani, Head of Product Marketing at Corelight. The discussion looks at how NDRs might evolve, such as expanding to protect inter-cloud networks and complementing EDRs.
Arrests, cybercrime, and threat intel
Operation Contender 3.0: 260 suspects were detained across 14 African countries in a recent Interpol operation. The suspects ran social media campaigns to defraud users. They allegedly stole more than $2.8 million from at least 1,400 victims.
Scammers detained in Cambodia: Cambodian authorities arrested 24 foreigners following raids on local cyber scam centers. [Additional coverage in the Khmer Times]
Protests at KaiBo scam compound: A religious insult sparked a violent riot at a cyber scam compound in the city of Sihanoukville, Cambodia. Bangladeshi and Pakistani workers destroyed the office building and rioted in the streets at the infamous KaiBo scam compound on Saturday. The riot stopped after officials deployed military police forces. Several individuals were arrested. [Additional coverage in CamboJA News]
CAMBODIA: Videos posted on Telegram claim to show protest by Indian workers at Kaibo scam compound, Sihanoukville. Military police reportedly dispatched.
— Cyber Scam Monitor (@cyberscammonitor.bsky.social) 2025-10-04T15:50:05.759Z
Reports from Sihanoukville last night describe chaos in the city’s Chinatown area.
— Jacob in Cambodia 🇺🇸 🇰🇭 (@jacobincambodia) October 5, 2025
Thousands of Indian and Indonesian workers reportedly clashed with security and damaged property after a dispute with their Chinese employer over unpaid wages.
Police and military police… pic.twitter.com/4VOz6u35Qu
Australia fines man for AI deepfake pr0n: An Australian man was fined $343,500 for posting deepfake pornographic images of prominent Australian women online. Anthony Rotondo has been linked to at least 12 incidents from November 2022 to October 2023. Rotondo received the largest fine of its kind for generating and publishing nonconsensual adult content using AI. [Additional coverage in the Information Age]
The Four Great Families: Security researcher Gary Warner looks at what he calls "the Four Great Families" that ran most of the scam compound operations in Myanmar's Kokang region. China sentenced members from each family last week, with some receiving death sentences, but it's unclear what sentence each family received. Per Warner, the Four Great Families include the Bai, Wei, Liu, and Ming crime cartels.
New npm malware: Fifty-nine malicious npm packages were discovered and taken down last week. Check out the GitHub security advisory portal for more details.
18+ e-crime cluster: The DomainTools security team has spotted a cluster of malicious domains peddling 18+ social media content and Windows apps laced with malware.
DPRK money laundering: Chainalysis looks at how North Korea is laundering the salaries of its remote IT workforce via the blockchain.
Cisco brute-forcing campaign: A large-scale brute-force attack is targeting Cisco devices. The attack primarily went after Cisco ASA firewalls and Cisco AnyConnect VPN gateways. This is the second such wave that was recorded over the past months. The first wave preceded the disclosure of a Cisco ASA zero-day.
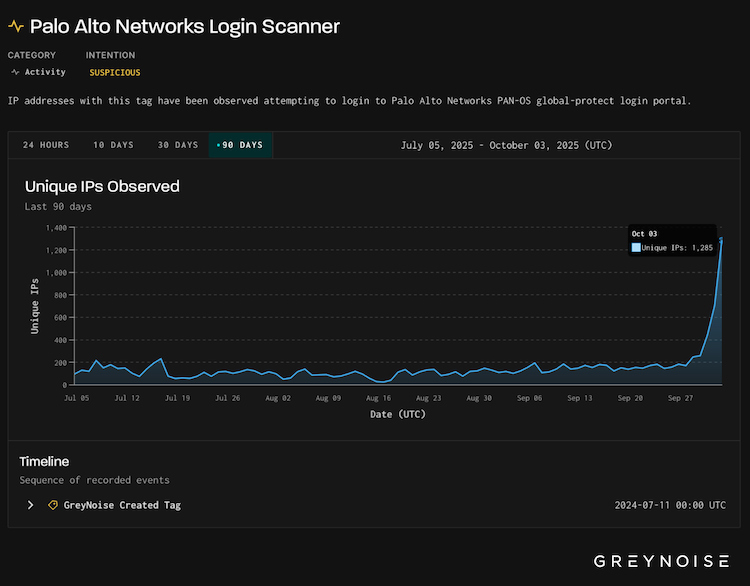
PAN scanning surges: At the same time, GreyNoise has also spotted a 500% surge in scans for Palo Alto Networks login panels. These types of surges typically predate active exploitation campaigns.
Malware technical reports
SORVEPOTEL worm: A self-propagating WhatsApp worm is spreading across Brazil, designed to infect Windows systems. The SORVEPOTEL worm uses WhatsApp private messages to spread and urges users to download and run its files on a Windows desktop. The malware installs an infostealer that steals credentials for financial institutions and crypto exchanges in the Brazilian market.
New WARMCOOKIE activity: Elastic's security team looks at new versions of WARMCOOKIE, a Windows backdoor they first spotted last June that is now heavily intertwined with the underground MaaS ecosystem.
XWorm RAT: Trellix looks at version 6 of the XWorm, a RAT that was supposedly abandoned by its developer back in 2024. Suprise! It's still alive, being revived a year later.
TamperedChef: WithSecure has published a report on TamperedChef, an infostealer that has been very active over the past month.
Sponsor section
James Pope, Corelight's Director of Technical Marketing Engineering, demonstrates the company's Open NDR Platform and how it combines network detections with a whole host of other data sources.
APTs, cyber-espionage, and info-ops
SideWinder's Operation SouthNet: Suspected Indian APT group SideWinder has recently launched a cyber-espionage campaign targeting the government and military entities in Pakistan and Sri Lanka with port and maritime lures. The campaign, called Operation SouthNet, also targeted Nepal, Bangladesh, and Myanmar, but to a lesser degree.
CN APT targets Serbia: StrikeReady looks at a Chinese APT's spear-phishing campaign against a Serbian government aviation department.
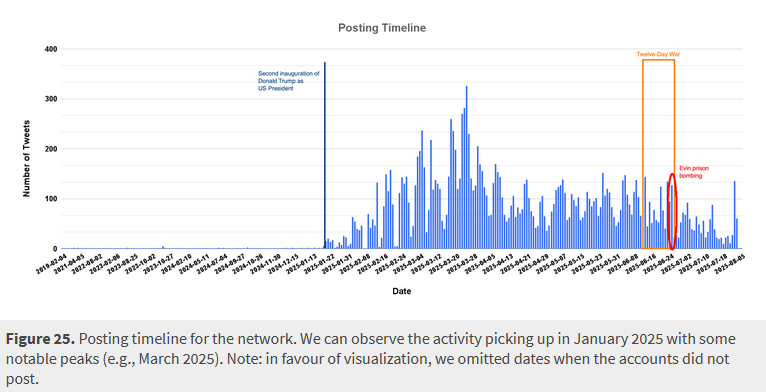
PRISONBREAK influence op: A network of at least 50 Twitter accounts engaged in an influence operation designed to incite a revolt against the Iranian regime. The accounts were created in 2023 but were activated this year, during an Israeli military offensive against the country. CitizenLab believes an Israeli intelligence agency or one of its contractors is behind the operation.
Vulnerabilities, security research, and bug bounty
ZeroDay Cloud hacking contest: AWS, Azure, and GCP are holding a joint cloud-hacking contest under the name of ZeroDay Cloud. The contest will be managed by Google’s Wiz division and will take place at Black Hat Europe this December. The prize pool is $4.5 million, and researchers can earn up to $300,000 for certain vulnerabilities.
New Zimbra zero-day discovered: A Zimbra vulnerability (CVE-2025-27915) patched in January was actually a zero-day that was exploited in cyber-espionage operations. The zero-day used malicious iCalendar files delivered to Zimbra email inboxes to run malicious code on Zimbra servers. According to security firm StrikeReady, the zero-day was used to target Brazil's military.
YoLink Smart Hub vulnerabilities: Bishop Fox researchers have found vulnerabilities that could have allowed attackers to take over YoLink Smart Hub, a platform that allows users to remotely manage all their YoLink IoT smart devices.
Dell UnityVSA pre-auth vuln: WatchTowr researchers have found a pre-auth command injection (CVE-2025-36604) in Dell's UnityVSA virtual storage appliance. It was one of 14 command injections patched in a firmware update that patched 116 bugs. Yes, it really looks like someone coded that firmware with their feet.
Tesla vulnerability: NCC researchers have found a vulnerability that can allow attackers to bypass authentication on the ADB connection to Tesla car telematics units. This can be used to connect unauthorized gear to Tesla cars. Tesla patched the bug in April.
Notepad++ vulnerability drama: Trustwave looks at the recent drama over a recent DLL hijacking vulnerability in the Notepad++ editor.
"Meanwhile, on Notepad++'s community board, some developers and programmers also shared the sentiment that CVE-2025-56383 is not a real vulnerability. In fact, the development team is not planning on addressing the issue at all. Don Ho (donho), echoed Gavrilov's thoughts, stating that by default, Notepad++ and its plugins are installed in Program Files. To compromise the app, threat actors must have elevated privileges, which could also mean that they could just replace any application or executable binary on the system."
NiceHashMiner hijack: There's a bug in the NiceHash Miner that can let you hijack the update system of crypto mining servers with zero admin interaction. [h/t Cr0w]
AWS X-Ray: Security researcher Dhiraj Mishra has documented a technique that uses Amazon's distributed application tracing service AWS X-Ray as a command and control server.
Splunk security updates: Cisco has patched seven security flaws in its Splunk SIEM product.
QNAP security updates: QNAP has released security updates over the weekend to address issues in several products.
CometJacking attack: A malicious crafted URL can hijack Perplexity's Comet AI browser and steal user data. The link includes a hidden AI prompt that bypasses the Comet browser's security. Extremely sensitive Comet data can be exposed, extracted, and exfiltrated, according to security firm LayerX.
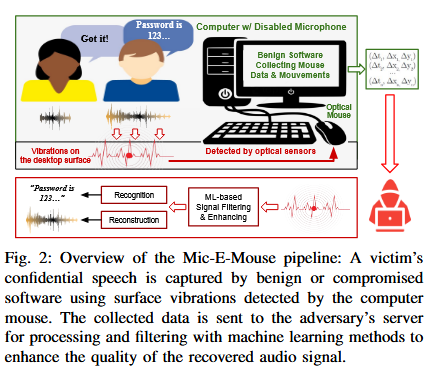
Mic-E-Mouse attack: Academics have developed a new technique that turns an optical mouse into a microphone to secretly record and exfiltrate data from air-gapped networks. The new Mic-E-Mouse technique takes advantage of the extremely powerful optical sensors that are now common in gaming mice. The optical sensors detect tiny vibrations caused by nearby sound and record the pattern in mouse movements. This data can be collected and then exfiltrated to recover conversations with the help of sound-processing LLMs.
Infosec industry
Threat/trend reports: ControlUp, the Cyber Civil Defense Initiative [PDF], Dr.Web, and Tribal-ISAC [PDF] have recently published reports and summaries covering various threats and infosec industry trends.
New tool—P0LR Espresso: Security firm Permiso has released P0LR Espresso, a tool for normalizing cloud logs between different platforms.
New tool—EnumEDRs: Security researcher Jony Schats has released EnumEDRs, a tool to enumerate active EDRs on a system.
Tool update—gULP: Security firm Mentat has released the first stable version of its gULP IR logs processor.
Risky Business podcasts
In this edition of Seriously Risky Business, Tom Uren and Amberleigh Jack talk about different ways foreign intelligence services are finding to recruit local proxies. These methods could be too risky for Western intelligence agencies, but for some states' services, they just make sense.
In this edition of Between Two Nerds, Tom Uren and The Grugq discuss the power of cyber.




