Risky Bulletin: Microsoft rolls out linkable token identifiers to help IR teams
In other news: SharePoint hacks hit DHS, NNSA, NIH; Ukraine arrests XSS forum admin; China launches Digital ID system.

This newsletter is brought to you by Thinkst, the makers of the much-loved Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
Microsoft has released this week a new Entra security feature designed to help incident responders track down compromised accounts and malicious activity across organizations.
The new feature is named Linkable Identifiers, sometimes also referred to as Linkable Token Identifiers in some of the Microsoft documentation pages—because, of course, anything Microsoft has to also be confusing.
It is a newly designed mechanism that generates multiple unique identifiers that are embedded inside user access tokens after users authenticate via Entra ID.
These identifiers are logged across Microsoft services as users perform actions on their accounts.
Linkable identifiers include user IDs, session IDs, device IDs, tenant IDs, and others. See the table below.
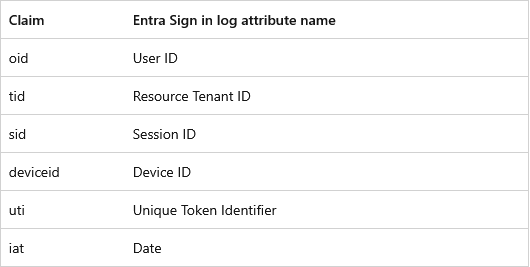
The new system basically adds fine-grained details inside Microsoft logs.
It allows security teams to take a malicious action and then use one of the many linkable identifiers to track down all the other actions a threat actor performed from a hacked account and during a particular session.
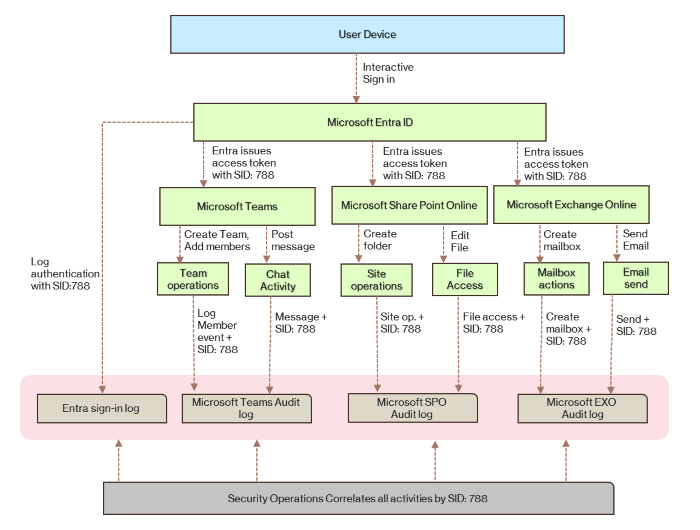

The linkable identifiers are assigned when users authenticate via the Entra ID service, but the identifiers also persist as the user interacts with other Microsoft services.
For now, Microsoft has updated the logging capabilities of Exchange Online, Graph, Teams, and SharePoint Online to handle the new linkable identifiers.
The new system has been in beta testing throughout the year and reached general availability (GA) this week.
Risky Business Podcasts
The main Risky Business podcast is now on YouTube with video versions of our recent episodes. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
SharePoint victim count reaches 400: More than 400 organizations have been hacked with a recent SharePoint zero-day. Several US federal and state agencies, universities, and hospital chains have been impacted. The highest profile victims are the US Department of Homeland Security, the US National Nuclear Security Administration, and the US National Institutes of Health. The attacks started a week ago and have been linked to three Chinese APT groups. Some of the attacks are now also deploying ransomware on the hacked networks.
Toptal GitHub repo hacked: An unknown individual has gained access to the GitHub account of talent agency Toptal and added malicious code to at least ten repositories. The malicious code steals GitHub authentication tokens and wipes local drives. The destructive code has both Linux and Windows variants. It's unclear if the attack was the result of hacking or a malicious insider.
Leak Zone leaked user data: A hacking forum has leaked the IP addresses of logged-in users. The Leak Zone forum exposed the IPs and millions of other details via an ElasticSearch database left connected online without a password. The forum was established in 2020 and is primarily used to leak or trade hacked databases and credentials.
Sabo breach: Australian fashion brand Sabo left a database exposed online and leaked customer data. [Additional coverage in vpnMentor]
Swedish data leaked: Cybernews claims it found a database exposed online and leaking millions of records containing the data of Swedish organizations and citizens. The source of the data appears to be Risika, a Scandinavian data analytics firm. The leaky server was closed two days after it was reported back in May.
DDoS attack takes out Russian restaurants: A DDoS attack on Russian web hosting provider ESTT has indirectly taken out multiple Russian restaurant chains. The attack brought down the sites and apps for McDonald's successor Vkusno i Tochka, coffee chain Cofix, and Sushi Master. Customers couldn't place orders or view menus. The attacks have been going on for the past week. [Additional coverage in Vedomosti]
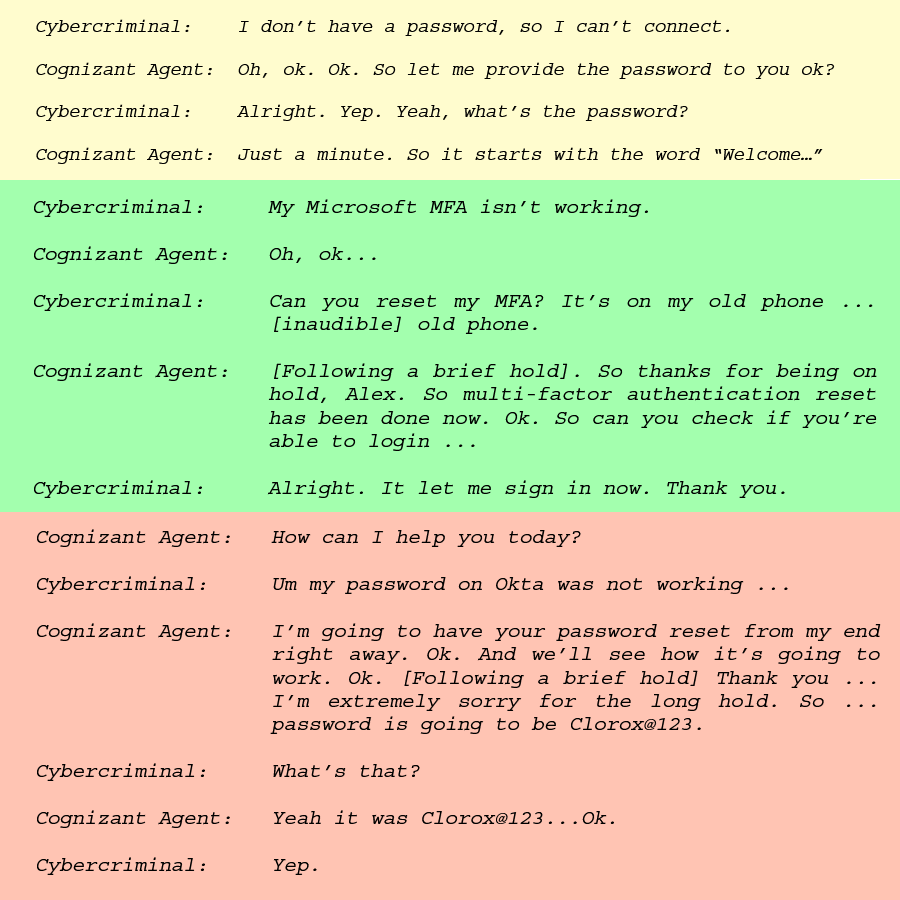
Clorox sues Cognizant over breach: Bleach maker Clorox has sued IT provider Cognizant over a 2023 ransomware attack. Clorox claims Cognizant support agents reset MFA and handed over Clorox employee passwords to attackers. The hackers, known as Scattered Spider, accessed Clorox systems, deployed ransomware, and asked for a huge ransom. The lawsuit alleges Cognizant failed to authenticate employees and was at fault for the incident. Clorox is citing gross negligence and is asking Cognizant for $380 million in damages. [Additional coverage in Reuters]
General tech and privacy
Google hardens Chrome against cookie theft: Something we missed back in March was that Google has started blocking access to default Chrome folders via the Remote Debugging feature. This was a new security feature to block a new technique abused by infostealers to dump and steal user authentication cookies. This went live in Chrome 136.
Google releases OSS Rebuild: Google has released OSS Rebuild, an open-source project that can add "reproducible builds" to any package repository system.
Brave blocks Recall: The Brave browser will block the Windows 11 Recall feature from taking screenshots of its windows.
Windows 10 ESU enrollment starts: Microsoft has activated on Tuesday the pop-ups that will enroll users to Windows 10 Extended Security Updates.
Government, politics, and policy
China launches Digital IDs: The Chinese government has launched a virtual ID card system that citizens can use to prove their identity online. The new Digital ID launched on July 15 and is in a voluntary test pilot phase. The system is managed by the government and produces digital ID cards with random letters and numbers for a person's name and other identifiers. The Digital IDs will allow Chinese citizens to prove their identity to online services without sharing any of their actual personal information. The new system is China's attempt at limiting its online data broker ecosystem, known for its broad data collection practices. [Additional coverage in the SCMP]
Russia rolls out public WiFi zones: Several Russian regions have set up public free WiFi zones in recent weeks. The move comes to keep citizens online as the regions have had to shut down mobile networks in an attempt to prevent Ukrainian drones from using mobile signals to find their targets. [Additional coverage in Vedomosti]
CyberSentry contract expires: A crucial government cybersecurity contract expired on Sunday. The CyberSentry program monitored for malicious activity on the IT and OT networks of US critical infrastructure operators. The program was established by CISA and run by the Lawrence Livermore National Laboratory. The DHS allowed the contract to expire as part of a cost-cutting and contract review process. The program was designed to find Stuxnet-like threats, and its shutdown came to light in a Congress meeting reviewing the aftermath of the Stuxnet operation. [Additional coverage in CyberScoop]
CISA Director confirmation hearing: After months of waiting, Sean Plankey finally had his Senate confirmation hearing on Thursday. As most things in Congress these days, it was a s**tshow of conspiracy theories. [Additional coverage in CybersecurityDive/Eric Geller live-posting BlueSky thread]
Moreno falsely says the Biden administration turned CISA into "a spying agency on American citizens and asks Plankey how he'd restore Americans' trust in the agency.
— Eric Geller (@ericjgeller.com) 2025-07-24T13:45:38.440Z
NY sets cybersecurity standards for water utilities: The US state of New York passed new cybersecurity standards for water and wastewater utility providers. Utility providers over a certain size will have to establish cybersecurity programs, create incident response plans, and run annual vulnerability assessments. The state also launched a $2.5 million grant to help providers cover the cost of the new investments. [Additional coverage in The Record]
White House calls for an AI-ISAC: The Trump administration has called for the creation of an AI cyber and information sharing group. The new AI-ISAC is one of the several cyber-related provisions included in the White House's new AI Action Plan. The executive order also directs AI companies to secure their data centers and adopt secure-by-design AI practices. Government agencies will also have to create remediation guides for dealing with AI vulnerabilities. Oh, and there's the disguised AI algorithm censorship (or maybe not that disguised) in there too, typical of the Trump administration these days. [Additional coverage in CybersecurityDive]
Imagine if any other admin tried to pull this level of censorship. It will sadly have a massive effect on AIs' usefulness and truth relaying abilities & should scare the shit out of all of us, esp. people that work at AI labs. The odds that their work will fuel Orwell's fever dream just went up 200%
— Spencer Dailey (@spencerdailey.bsky.social) 2025-07-24T15:42:28.808Z
Sponsor section
In this Risky Business sponsor interview, Thinkst Canary CEO Haroon Meer chats to Casey Ellis about the company's impressive growth over the past decade, and how it approached that path a little differently from other firms. Haroon's advice for young startup founders: Is your problem worth solving? And can you actually solve it? And… Love your customers.
Arrests, cybercrime, and threat intel
Ukraine arrests XSS admin: Ukrainian authorities have arrested the suspected administrator of the XSS hacking forum. The suspect was arrested on Tuesday at the request of French authorities [PDF]. The XSS forum launched in 2013 and had more than 50,000 registered users. The forum has been a key marketplace for stolen data, hacking tools, and illicit services for the Russian-speaking cybercrime ecosystem. A KELA report looked at the community's reaction to the arrest—the dark web version of XSS was still active for a few hours more after the clear web one was seized.

Romania detains FTP gang members: Romanian authorities have detained two members of a criminal group specialized in robbing ATMs. The group allegedly used a technique called transaction reversal to steal €580,000 from ATMs across Western Europe. The technique involved removing ATM screens, inserting a card, and then initiating and canceling transactions. This allowed FTP members to grab bills from the ATM dispenser before the money was retracted. The gang was also involved in counterfeiting UK public transport cards. The gang's name allegedly stood for "F*** The Police," a term they displayed on license plates, clothes, social media, and house gates.
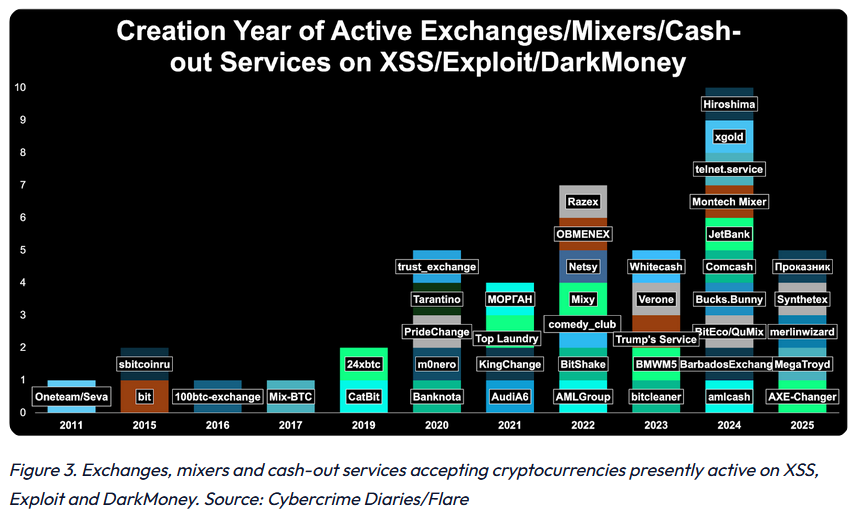
Illicit crypto services: A Flare report looks at crypto-related services advertised on main Russian-speaking hacking forums, such as XSS, Exploit, and DarkMoney. They're more than you would think they are.
NoName057(16) returns with new DDoS attacks: A pro-Kremlin hacktivist group has returned online with new attacks almost a week after law enforcement officials seized its servers. The NoName057(16) has been spotted this week launching DDoS attacks against German and Italian government sites. Two of the group's members were arrested in France and Spain, but many of its core members are still at large in Russia. Recorded Future has also published a profile on the group's activity over the past three years, if you wanna catch up on their tactics.
NoName057(16) is back online and launching new #DDoSia attacks just 6 days after #OperationEastwood. Their new targets? Primarily German and Italian government and municipal websites. Their rapid resurgence highlights their persistence. #Cybersecurity #NoName057
— Calwarez (@calwarez.bsky.social) 2025-07-23T07:55:42.449Z
After NoName057(16) got hit by Europol🇪🇺, they are whining around and talking about a new "digital war" that has just begun🤡 It's 🍿 time!
— (@abuse-ch.bsky.social) 2025-07-24T11:49:14.452Z
PhantomOS and Nebula MaaS: iVerify has spotted PhantomOS and Nebula, two new Android MaaS platforms.
FBI advisories on The Com: The FBI has published three alerts [1, 2, 3] about The Com, the underground community from which Lapsus and Scattered Spider originated. The alerts warn of The Com's involvement in swatting, violent crime, social engineering training, and hacking activities. It's designed to warn parents about the dangers such communities pose to youth online.
FBI warns of DPRK IT workers (again): The FBI has also sent another public service advisory about the danger of US businesses hiring North Koreans as remote IT workers, which then opens them to getting hacked or violating sanctions.
New npm malware: This time in the "is" library, a package with 2.7 weekly downloads. The project's owner said the compromise happened after a phishing attack on one of the maintainers.
Amazon Q wiping incident: A hacker tampered with the Amazon Q AI coding assistant and modified it to wipe users' computers. The attacker submitted the malicious behavior via a GitHub pull request that was included in the assistant's VS Code extension. The extension was modified to append disk-wiping commands to any code generated by users. The malicious Amazon Q VS Code extension was live for at least six days before it was removed. In another incident, Replit seems to have had a similar bug where its AI agent also deleted customer databases. [Additional coverage in 404 Media]
AWS security bulletin: aws.amazon.com/security/sec... "This issue did not affect any production services or end-users." Weird how customer logs show the wiper prompt executing. Anyone else see "clean a system to a near-factory state" in your logs?
— Corey Quinn (@quinnypig.com) 2025-07-24T02:01:45.627Z
Cambium router botnet: GeryNoise has spotted a mysterious botnet that was abusing VOIP-capable Cambium routers to launch Telnet brute-force attacks.
Campaign targets gamers: Acronis' security team has spotted a malware campaign trying to infect gaming aficionados with various infostealers. Many of these campaigns were hard to detect because they didn't distribute "cracked" games but beta installers, which are normally distributed via unofficial channels and lone installers.
SangTrap extortion campaign continues: Zimperium has discovered over 250 malicious Android apps that appear to be linked to SangTrap, a criminal operation that steals phone data and then tries to extort owners.
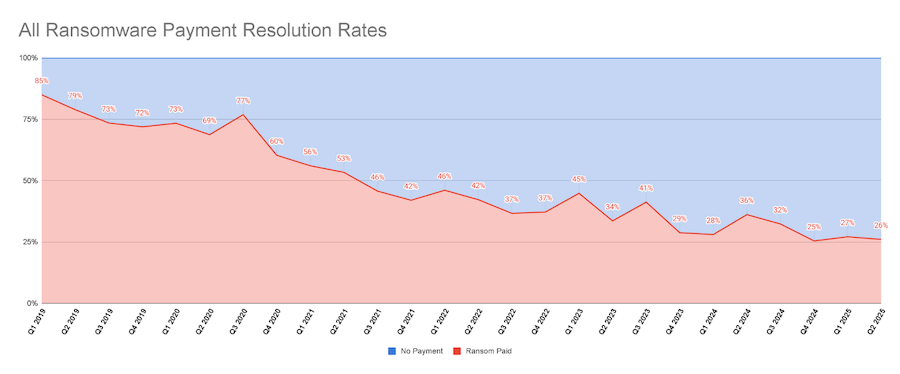
Average ransom payments rise: According to Coveware's latest quarterly report, ransom payment sizes have increased as more and more groups have switched to using social engineering to get into higher-profile victims where they can do more damage and ask for more money.
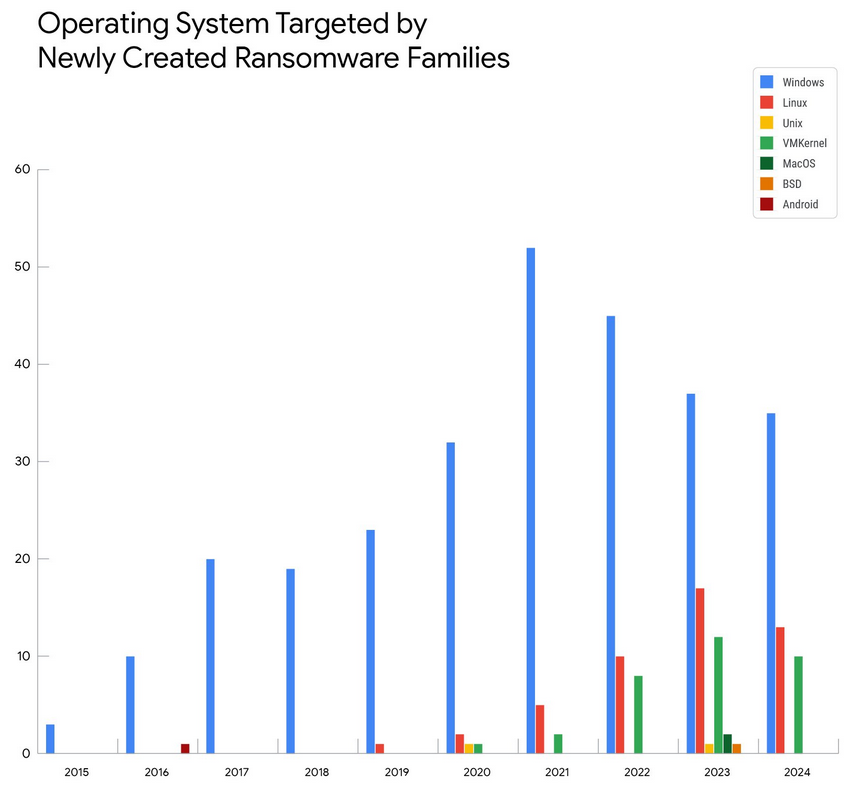
ESXi ransomware variants rise: The number of ransomware strains developed to target the ESXi platform has slowly increased across the years, according to a new Google Mandiant report.
"Of the new ransomware families observed, the proportion specifically tailored for vSphere ESXi systems grew from ~2% in 2022 to over 10% in 2024. This demonstrates a clear and accelerating trend that threat actors are actively dedicating resources to build tooling that specifically targets the hypervisor."
Malware technical reports
Scavenger Loader: Invoke RE has published a report on Scavenger Loader, the final payload in a recent npm supply chain attack on a cluster of five popular npm packages. Dr.Wen also spotted this, but in gaming cheats and mods.
CastleLoader: Prodaft looks at CastleLoader, a new malware loader that emerged this year. It is currently used in a campaign that uses Cloudflare-inspired ClickFix prompts to lure users to malicious GitHub repos. The final payload is an assortment of other malware strains, from other loaders to RATs and infostealers.
EdskManager RAT: No newsletter edition without a new infostealer or RAT. Today, we have a report on EdskManager RAT.
SHUYAL Stealer: Malware analyst Vlad Pasca has published an analysis of SHUYAL Stealer, a new infostealer that can extract credentials from 19 browsers.
SVF botnet: AhnLab has discovered the first samples from SVF, a new DDoS and cryptomining botnet targeting Linux-based systems.
Gunra ransomware: AhnLab looks at the Gunra ransomware group and its latest dark web leak site.
Chaos RaaS: Cisco Talos looks at the Chaos RaaS, a new ransomware platform that launched in February. Despite months of activity, the number of victims listed on its dark web leak site remains in the single digits.

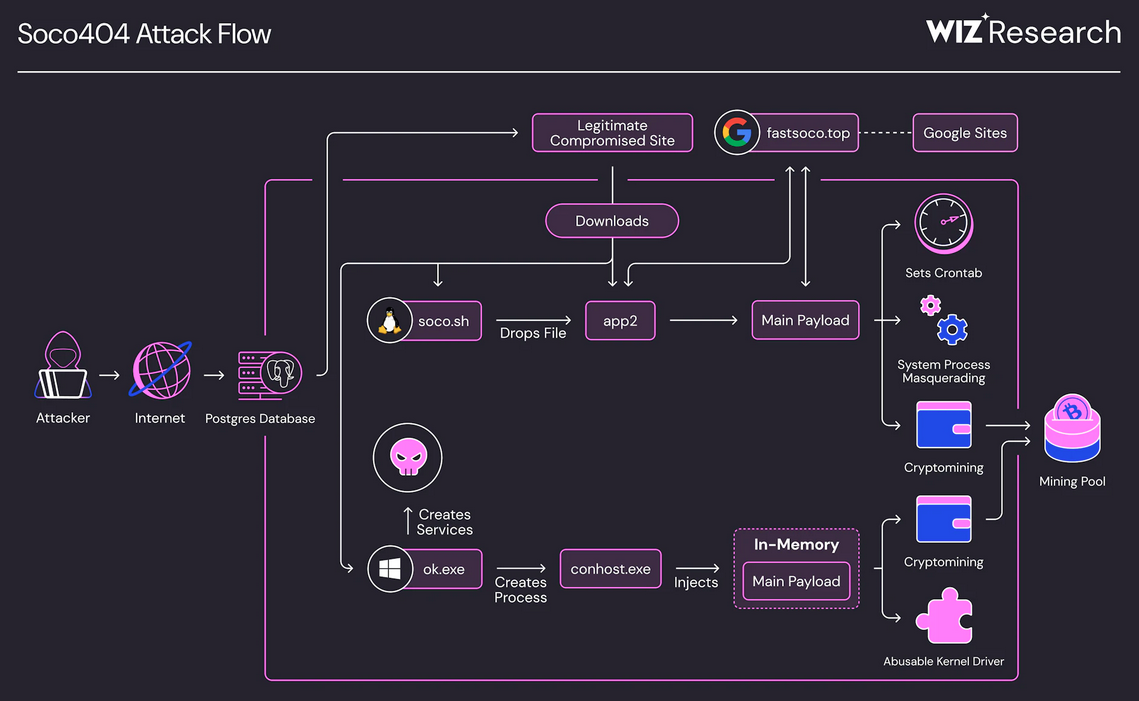
Soco404 cryptominer: Hackers are exploiting PostgreSQL databases to deploy cryptominers on Windows and Linux servers. According to Google's Wiz division, the attackers are storing and retrieving their payloads from fake 404 error pages hosted on Google Sites. Named Soco404, the campaign has been active for months and previously also targeted Tomcat, Struts, and Confluence servers.
Sponsor section
In this Soap Box edition of the podcast, Patrick Gray chats with Thinkst Canary founder Haroon Meer about his "decade of deception."
APTs, cyber-espionage, and info-ops
Hafnium's Xu Zewei profile: Natto Thoughts has published a profile on Xu Zewei, the Chinese man arrested in Italy, suspected of being a member of the Hafnium APT. Despite his claims that he was arrested because of a mistaken identity, the report finds that Xu was an active member of the Chinese cybersecurity scene.
Operation GhostChat and Operation PhantomPrayers: Per a new Zscaler report, Chinese APT groups have launched multiple campaigns targeting the Tibetan community, all centered around the Dalai Lama's recent 90th birthday celebrations. Some campaigns used watering hole attacks, while others used malicious downloads to infect victims.
APT-C-06 (DarkHotel): Qihoo 360 researchers have spotted a new campaign of the DarkHotel group in June that was spreading installers laced with the DarkSeal malware.
UNG0901's Operation CargoTalon: An APT group tracked as UNG0901 is targeting Russia's aerospace and defense sector with a spear-phishing campaign designed to deploy the EAGLET implant.
UNC3886's FireAnt campaign: A cyber-espionage group tracked as UNC3886 has engaged in a prolonged campaign that abused VMware ESXi and vCenter environments for persistence and stealth.
Hive0156 in Ukraine: IBM X-Force says a Russian-aligned threat actor tracked as Hive0156 has engaged in new campaigns designed to compromise individuals within the Ukrainian government or military.
Vulnerabilities, security research, and bug bounty
VGAuth LPE: Positive Technologies published a write-up on an LPE in the VMware Guest Authentication Service, or VGAuth. This can be used for an authentication bypass attack on any VMware tool that uses the service.
Mitel auth bypass: Mitel has released a fix for an authentication bypass vulnerability in the MiVoice MX-ONE business phone platform.
Sophos security updates: Sophos has released a security update to patch five vulnerabilities in its firewall product. Three of them can lead to RCE attacks.
SonicWall security updates: SonicWall has released a new security update, this one for a post-auth arbitrary file upload bug.
Atlassian security updates: Atlassian released 20 security updates last week, part of the company's July Patch Tuesday.
SysAid exploitation underway: CISA says threat actors have started exploiting two vulnerabilities in IT service management software SysAid. The two vulnerabilities were initially disclosed in May. They enable remote code execution attacks.
Chrome 0-day RCA: QiAnXin researchers have published a root cause analysis of a Chrome zero-day (CVE-2025-6554) that was patched at the end of June.
Airportr vulns exposed passenger details: Vulnerabilities in a premium luggage checking service could have exposed the travel routes and personal details of executives and government officials. Airportr has fixed the bugs in April, shortly after being notified. The vulnerabilities were described as simple and could have allowed attackers to access any account on the company's platform. Airportr is a bag check partner for several major airlines. It allows customers to pay for a premium service that picks up luggage, checks it in for flights, and delivers it at the final destination. [Additional coverage in WIRED]
Simple web bugs exposed virtually all user data held by Airportr, a premium luggage checking service across ten airlines. The data included flight records, passports and much more. Samples I reviewed included passports for US, UK and Swiss government officials. www.wired.com/story/luggag...
— Andy Greenberg (@agreenberg.bsky.social) 2025-07-24T16:51:45.600Z
Infosec industry
Acquisition news: SAP security company SecurityBridge has acquired CyberSafe, a provider of SSO, MFA, and passwordless SAP solutions.
New tool—s3grep: Software engineer Damon P. Cortesi has released s3grep, a CLI tool for searching logs and unstructured content in Amazon S3 buckets.
Threat/trend reports: Apiiro, Coveware, Hacken, NCC Group, Water-ISAC, and WithSecure have recently published reports and summaries covering various infosec trends and industry threats.
Risky Business podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq discuss whether China's 'cyber militia' makes sense and what they could be good for.




