Risky Bulletin: Microsoft joins industry crackdown on bulk email senders
In other news: US sanctions militia group leader for cyber scams; Nomad Bridge hacker arrested in Israel; NSA ordered to cut 8% of civilian staff.

This newsletter is brought to you by Stairwell. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
Microsoft has joined rivals in the consumer email inbox market, such as Apple, Google, and Yahoo, and implemented stronger anti-spam features for its Outlook.com email platform.
The new rules entered into effect on Monday, May 5, and apply only to bulk senders, which are domains that send more than 5,000 emails per day to Outlook users.
Bulk senders must now authenticate their domains using modern email security standards such as DKIM, DMARC, and SPF.
They must also provide an easy way for users to unsubscribe and remove invalid email addresses from their sender lists to prevent server bandwidth waste.
Microsoft says it will block any domain that breaks the rules, and "especially for critical breaches of authentication or hygiene."
Google and Yahoo implemented the same rules last year for bulk senders. Apple also started enforcing the same rules in March.
Microsoft has also implemented a special error message so bulk senders can determine why their emails have been sent to Junk folders.
"After careful consideration and to ensure the protection of users and remove any confusion on why a message was in the junk folder for both the recipient and sender, we have made a decision to reject messages that don't pass the required authentication requirements detailed above. The rejected messages will be designated as "550; 5.7.515 Access denied, sending domain [SendingDomain] does not meet the required authentication level." This change will state taking effect on May 5th as originally stated."
Microsoft to being enforcing SPF, DKIM & DMARC on Monday 5/5. We've been doing this for years and always struggled to get clients to understand why we've rejected their emails. This is great news for email security, but 5/5 will be an interesting day for companies that haven't been paying attention.
— Scott Vintinner (@flakshack.bsky.social) 2025-04-30T15:03:08.568Z
Risky Business Podcasts
Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
TeleMessage hacked again: A second hacker has now breached TeleMessage, an Israeli company that sells modified versions of secure messaging apps used by the US government. NBC News reported the second hack on Monday after 404 Media reported the first breach a day before. TeleMessage became famous at the end of last week after a photograph revealed that members of the Trump administration were using a TeleMessage-modified version of Signal to log past conversations. The hacker didn't provide White House chat logs to NBC but proved they had access by sharing a list of Coinbase employees using TeleMessage.
GlobalX hacked: Hackers have breached and stolen data from GlobalX, an airline used by the Trump administration for deportation flights. According to 404 Media, the stolen data includes flight records and passenger manifests of all flights. It covers all flights since Trump took office to May 1. They also defaced the airline's website.
M&S didn't have IR plan before cyberattack: An inside source told Sky News that British retailer Marks & Spencer didn't have an incident response plan before it was hit by a ransomware attack last month. The company has struggled to recover and has had to suspend online orders and send staff home in the incident's wake. It also lost £500 million in market value since the incident.
NSO ordered to pay WhatsApp hacks: A US judge has ordered Israeli spyware maker NSO Group to pay $167 million in damages to Meta for a 2019 hacking campaign. Over $444,000 are compensatory damages to WhatsApp for the time employees spent investigating the hacks while $167,256,000 are punitive damages against NSO. Barring an appeal, the verdict represents the end of a lawsuit that started five years ago in 2020. [Additional coverage in TechCrunch]
General tech and privacy
Belgian psychiatrists call for social media ban for kids: A coalition of psychiatrists and psychology experts from Belgium have written an open letter to the local government asking for a ban on social media for children under 16.
Twitter censorship: Pekka Kallioniemi takes a look at all the censorship, algorithm changes, and right-wing bias taking place on Twitter these days.
Government, politics, and policy
Azerbaijan blames APT29 for news org hack: Azerbaijan says Russian state-sponsored group APT29 hacked Global Media Group, one of the country's largest media corporations. The intrusions took place in February after Azerbaijan shut down a Russian cultural center on espionage charges. The attacks disrupted four news portals and the operation of the Baku TV channel. The APT29 group has been previously linked to Russia's SVR intelligence agency. [Additional coverage in APA.az/English coverage in Trend.az]
Moscow internet disruptions: Russian officials are restricting internet and mobile access between May 5 and May 9 for security reasons ahead of the country's yearly Victory Day parade. The disruptions are part of a recent Russian countermeasure to blind Ukrainian drone attacks that officials had tested in some border regions. [Additional coverage in The Moscow Times]
NSA staff cuts: The White House has ordered the US National Security Agency to cut 8% of its civilian workforce. According to The Record, the layoffs must happen before the end of the year and will impact between 1,500 and 2,000 employees. Last week, the Trump administration also ordered the CIA to cut around 1,200 of its staff.
NIST loses key cyber experts: Almost a dozen top cybersecurity experts from the US National Institutes of Standards and Technology (NIST) have taken the Trump administration's retirement offers and are leaving the agency. According to CybersecurityDive, the experts had worked in NIST's Computer Security Division (CSD). Their retirement will impact NIST's capacity to deliver standards for emerging technologies like quantum computing and artificial intelligence.
DOD to fast-track software security reviews: The Pentagon announced the Software Fast Track Initiative, a new software procurement process that expedites its cybersecurity reviews.
Europol sets up OTF GRIMM: Europol has set up a special task force that will focus on investigating Violence-as-a-Service providers. The task force is named GRIMM and will be led by Swedish authorities. Europe has been dealing with a wave of violent attacks that have been traced back to underground online communities that recruit and pay teens, locals, or immigrants for violent attacks and sabotage.
Locked Shields exercise: The annual NATO Locked Shields cyber defense exercise is taking place is taking place between May 5 and May 9 in Estonia. [Additional coverage in The Baltic Times]
Sponsor section
In this Risky Bulletin sponsor interview, Mike Wiaceck, CEO and founder of Stairwell, explains why he believes security is really a data storage and retrieval problem. He demonstrates how that pays off in the analysis of new malware.
Arrests, cybercrime, and threat intel
US sanctions militia leader for cyber scam compounds: The US Treasury has sanctioned the leader of a Myanmar militia group for their involvement in running cyber scam compounds. Officials sanctioned Saw Chit Thu and two of his sons, and designated the Karen National Army as a criminal organization. US officials claim Saw and his militia group are now central figures in Myanmar's scam economy.
Nomad Bridge hacker arrested in Israel: Israeli authorities have arrested a dual Russian-Israeli national for allegedly hacking cryptocurrency exchange Nomad Bridge. Alexander Gurevich was one of several individuals who found and exploited a vulnerability in the platform in August 2022. He allegedly stole $2.89 million worth of crypto assets and then demanded a $500,000 reward to return the funds and share details about the bug. The Nomad Bridge lost more than $190 million in the hacks. [Additional coverage in The Jerusalem Post]
Child sextortion is getting popular in Russia: Russia's Ministry of Internal Affairs warns of a rise in child sextortion cases.
Akira negotiations: Security researcher Chum1ng0 has published details from the negotiations of four companies with the Akira ransomware group.
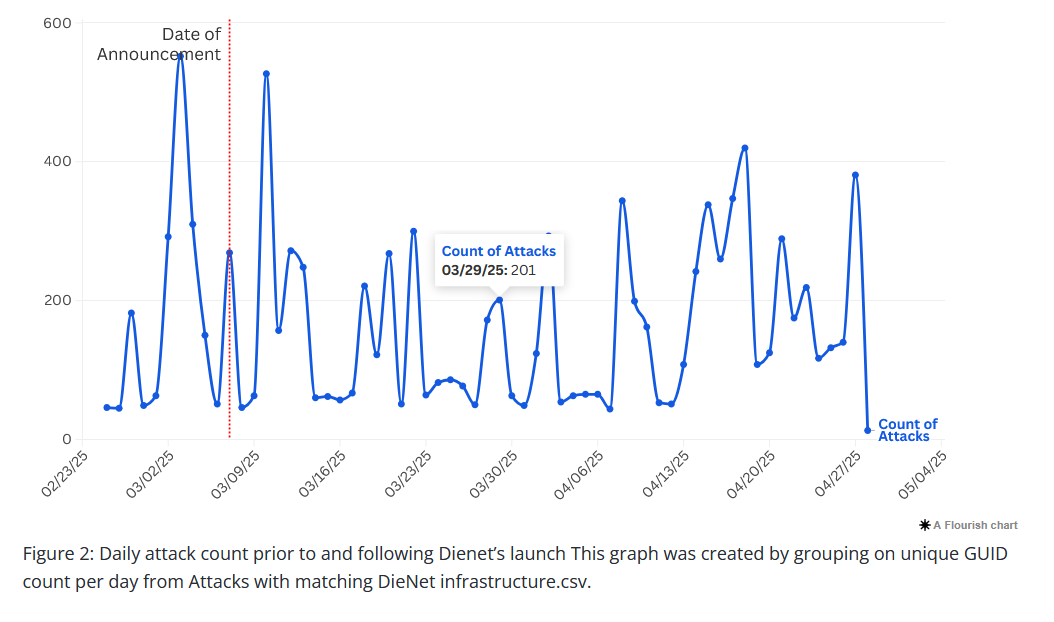
New DieNet group: Netscout has published a profile on DieNet, a new hacktivist group linked to over 60 DDoS attacks.
UNC3944: Google Cloud has published a profile on UNC3944, the remnants of the Scattered Spider group linked to the recent attacks on UK retailers.
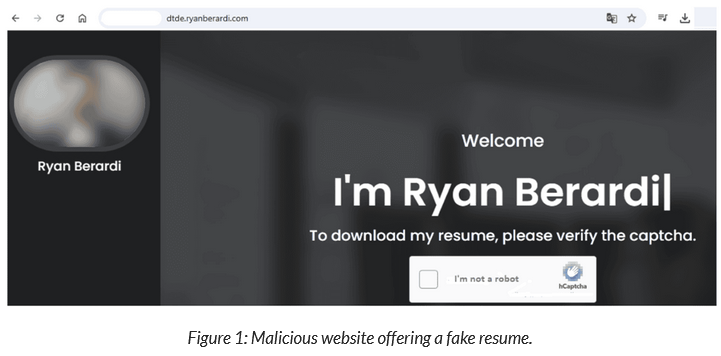
Venom Spider targets HR departments: A cybercrime group is applying to real jobs using malicious resumes that deploy malware. Security firm Arctic Wolf linked the attacks to a group known as Venom Spider, or TA4557. The group has used the same technique on and off to compromise major corporate targets since at least the end of 2023.
Malware technical reports
DragonForce ransomware: The Hybrid Analysis team looks at how the DragonForce ransomware takes inspiration and samples code from the leaked Conti and LockBit strains.
- DragonForce ransomware deploys payloads derived from leaked LockBit3.0 and Conti source code.
- DragonForce logs all its activity in an encrypted log file stored in the Public directory.
- The new ransomware employs the "stack strings" obfuscation technique to hide information.
- The encryption percentage of a file is determined by both file size and whether the extension is included in the ransomware's targeted list.
- DragonForce ransomware uses the ChaCha8 algorithm, with the encryption key and nonce protected by the public RSA key.
Mamona ransomware: Mauro Eldritch has published a technical analysis of the new Mamona ransomware strain.
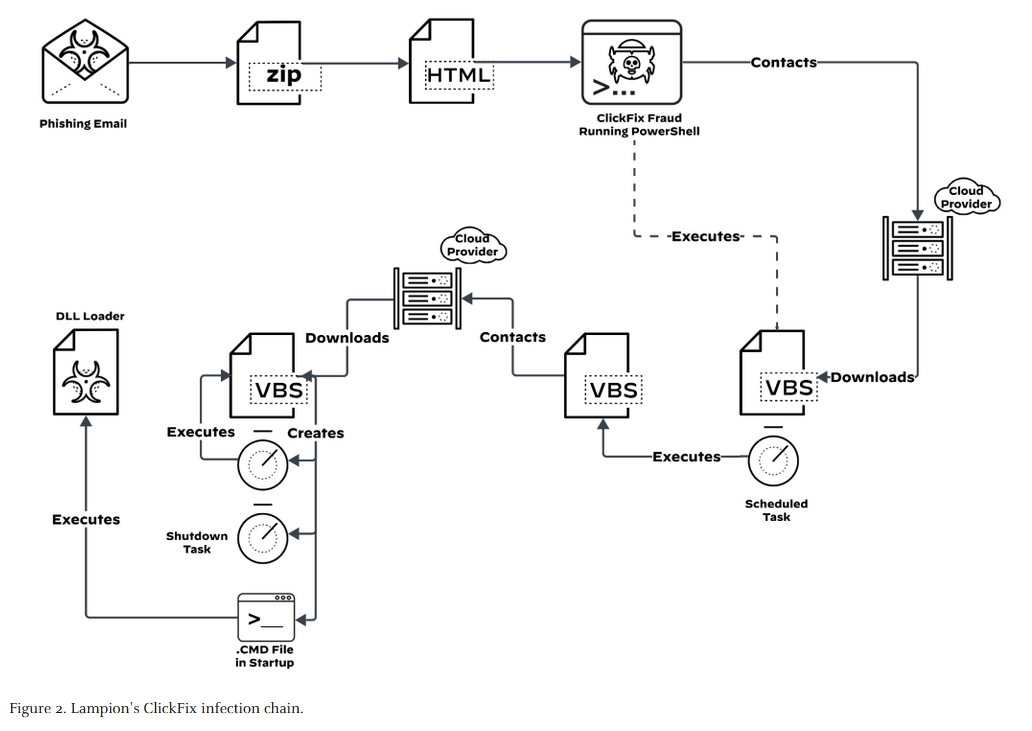
Lampion is back: The criminal group behind the old Lampion banking malware is back with new attacks and is now using ClickFix techniques. The current campaign targets Portuguese-speaking individuals and organizations.
Sponsor section
Learn why traditional security falls short and how Stairwell gives you the edge to outpace tomorrow's threats and uplevel your security team.
APTs, cyber-espionage, and info-ops
Core Werewolf: F6 has spotted new campaigns from the Core Werewolf APT targeting military organizations in Belarus and Russia.
Operation Overload: The Institute for Strategic Dialogue has published a report on Operation Overload, a disinformation campaign active in the first quarter of 2025 from the Storm-1679 (Matryoshka) group.
Gaelic disinformation: The Times reporters have spotted Russian disinformation being peddled in Gaelic to Scottish audiences.
Vulnerabilities, security research, and bug bounty
Android Security Bulletin: Google has released the Android security updates for May 2024. The company says that one bug was under active exploitation (CVE-2025-27363), which is the same zero-day reported by Facebook back in March in the FreeType font-rendering library.
Langflow exploitation: Threat actors are exploiting a vulnerability disclosed last month to take over AI apps and servers that use Langflow, a UI-based toolkit for building AI agents and workflows. Tracked as CVE-2025-3248, the vulnerability allows unauthenticated, remote attackers to run malicious code and fully compromise Langflow servers. Exploitation started taking place after proof-of-concept code was published online last month. The attacks are part of a recent trend where threat actors actively scout and go after insecure AI infrastructure.
MagicINFO exploitation: A Mirai botnet is exploiting a 2024 bug in MagicINFO, a Samsung digital signage system.
GeoVision exploitation: Another Mirai botnet is exploiting two 2024 bugs in GeoVision IP cameras.
Critical library linked to sanctioned entities: HuntedLabs says that a Go library named easyjson is fully owned and controlled by Russian tech giant VK, whose owners are subject to US sanctions. The library is widely used inside projects used by the US government.
Bring Your Own Installer technique: Threat actors are exploiting a new technique to stop and bypass EDR agents. Named Bring Your Own Installer, the technique exploits a gap in the EDR agent update process, where attackers kill the update process while the EDR agent is stopped to be updated, leaving systems without protection.
Kubernetes Helm Charts have weak defaults: The Kubernetes Helm Charts component uses insecure defaults that can leave servers exposed to attacks. According to research from Microsoft, Helm charts required no authentication and left ports and services open on the internet. Similar exposures were also noted with Apache Pinot.
Curl bans AI slop bug reports: The Curl project has reached a breaking point and has banned bug reports created using AI tools and which look like AI slop. The project says they have not "seen a single valid security report done with AI help."
"A threshold has been reached. We are effectively being DDoSed. If we could, we would charge them for this waste of our time."
Solana patches major bug: The Solana Foundation has patched a bug in its blockchain that could have allowed infinite token mints and token thefts.
AWS security update: AWS has released a fix for an input validation issue in an AWS Amplify Studio UI component.
Dell security updates: Dell has released three security updates this month.
Infosec industry
UNIDIR conference: The United Nations Institute for Disarmament Research is holding the Cyber Stability Conference next week. You can attend online.
New tool—MATRIX: Security firm Trustwave has released MATRIX, a security testing tool for Modbus TCP protocol implementations.
New tool—GPOHound: Security firm COGICEO has released GPOHound, a tool for dumping and analyzing Group Policy Objects (GPOs) extracted from the SYSVOL share.
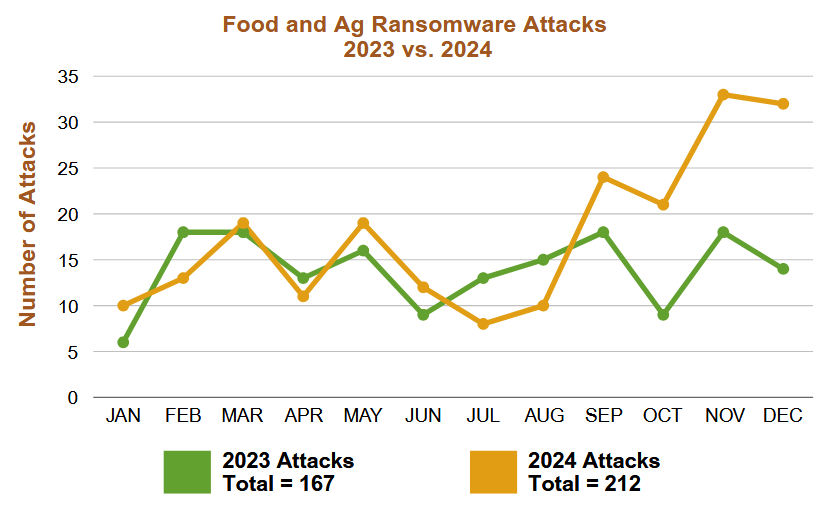
Threat/trend reports: The Food and Ag-ISAC [PDF], Privacy Journal, and SITA have recently published reports and summaries covering various infosec trends and industry threats.
Risky Business podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about an in-depth report on a Ukrainian hacking control panel. The panel shows how the Ukrainian group thinks about hacking operations, and the pair discuss why the report exists and what it achieves.
Tom Uren and Patrick Gray talk about a SentinelOne report about how it is constantly targeted by both cybercriminal and state-backed hackers. Security firms are high-value targets, so constant attacks on them are the new normal.




