Risky Bulletin: Microsoft blocks filesystem redirection attacks in new security feature
In other news: Ukrainian hackers wipe servers of Russian UAV maker; UK relocates Afghans who helped military after data leak; Microsoft outsources US government work to China.

This newsletter is brought to you by Zero Networks. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
Microsoft has added a new security feature to Windows 11 that will mitigate an entire class of filesystem redirection attacks.
The new RedirectionGuard feature is currently under testing in Windows 11 Insider builds.
It works by blocking a type of file redirection known as a junction, or a soft link. This allows users to create a link between two folders, so when users or processes access that folder, they get automatically redirected to the target directory somewhere else on the same system.
In the past, threat actors who compromised a standard (non-admin) user account have used junctions to link to folders on the system used by highly elevated processes. They used these junctions to trick sensitive processes into elevating their privileges or running malicious code with SYSTEM-level access on their behalf.
Microsoft says the new RedirectionGuard feature works by blocking all folder redirections if the junctions were created by non-admin users.
To enable the feature, developers must add a line of code to their apps to prevent their app from following junctions created by non-admin users.
Microsoft says it has already enabled RedirectionGuard for three of its own services that handle user profiles (User Profile Service), Windows Store installations (AppX Deployment Service), and normal app installations (Installer Service).
Expecting hundreds of thousands of app developers to modify their apps is a pipe dream, but Microsoft says the impact on the app ecosystem will be low because most apps don't run with elevated privileged access in the first place and don't need the RedirectionGuard protection anyway.
Once enabled, RedirectionGuard won't allow the services of "protected apps" to follow junctions created by non-admin users, but it will also create a new metadata section stored in an admin-only datastream.
Windows 11 will use the presence of this datastream to detect if this is a junction for an app that intentionally enabled/disabled RedirectionGuard or if this is a very old junction that needs to be left alone to avoid breaking various systems.
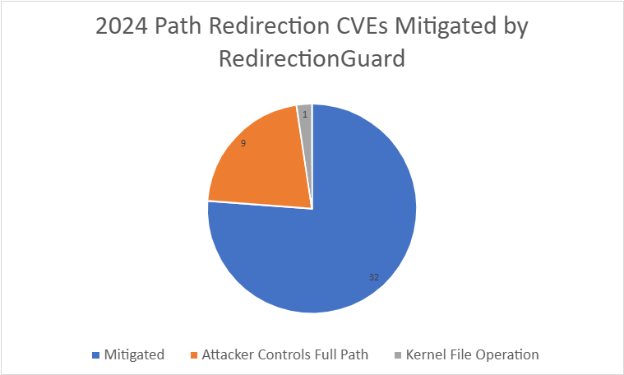
Microsoft expects this feature to have a huge impact on Windows security. The company says that of the 42 filesystem path redirection attacks it patched last year, 32 used attacker-created junctions to exploit local services and could have been blocked if RedirectionGuard existed.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq examine whether US cyber operations are too stealthy. Could they get more bang for the buck if they adopted a devil-may-care attitude to getting busted?
Breaches, hacks, and security incidents
Ukrainian hackers breach Russian UAV maker: Two Ukrainian hacktivist groups have hacked and wiped IT systems at Russian UAV maker Gaskar. The BO Team and the Ukrainian Cyber Alliance claim to have stolen 47TB of technical data before wiping servers and backup storage. The stolen data includes details on Russian drones and Gaskar employees. The attack allegedly halted production at Gaskar facilities. [Additional coverage in Pryamiy]
Salt Typhoon breaches National Guard: Chinese state-sponsored hackers have breached at least one US state's National Guard. The Salt Typhoon breach lasted for at least nine months, according to a Pentagon memo seen by NBC News. The group is believed to be operated by China's intelligence agency and has previously hacked almost a dozen US and Canadian telcos.
UK government leak prompts mass-relocation plan: The British government has relocated thousands of Afghans to the UK following a data leak at the Ministry of Defense in 2023. The breach exposed the personal information of over 33,000 Afghan nationals who helped British troops during the Afghan war. According to The Guardian, the UK government has spent over £2 billion over the past two years to relocate more than 20,000 of the affected individuals to the UK.
xAI API key leak: Per KrebsOnSecurity, a DOGE employee named Marko Elex leaked an API key for Musk's xAI company. The API key was still live when the Krebs article was published.
KT post-breach investment: South Korean telco KT will invest 1 trillion won ($724.5 million) over the next five years to boost its cybersecurity after the company was hacked and lost all customer personal and SIM data earlier this year. [Additional coverage in The Korea Times]
Louis Vuitton breach larger than thought: The Louis Vuitton breach that initially impacted customers in South Korea is larger than previously thought and also impacts customers in the UK and Turkiye.
Arcadia Finance crypto-heist: Hackers have stolen $3.5 million worth of cryptocurrency assets from DeFi platform Arcadia Finance. The attackers used an exploit in the company's smart contracts. Unlike similar hacks, the funds were stolen from customer wallets, instead of a shared pool managed by the platform. [Additional coverage in Crypto2Community]
DragonForce takes credit for Belk breach: The DragonForce ransomware group has taken credit for a breach at US store chain Belk. The hack took place in May, and Belk had to take its IT systems offline for several days to deal with the incident. The DragonForce for-hire ransomware was also used in attacks against UK retail chains Co-op, Harrods, and Marks & Spencer. Those incidents have been linked to the Scattered Spider group. UK authorities arrested four suspects last week for the hacks. [Additional coverage in SecurityWeek]

General tech and privacy
Meta bans 10 million content thieves: Meta has banned 10 million accounts that stole and reposted content from larger content producers. Meta says the accounts were diluting the user experience on its site. The company has launched a system to detect the copies, reduce their visibility, and block offending accounts from accessing its monetization program.
YouTube cracks down on AI slop: YouTube is allegedly preparing a ToS update that cracks down on "mass-produced and repetitious content," also known as AI slop. [Additional coverage in The Verge]
Reddit starts verifying user age in UK: Reddit has started verifying its visitors' age in the UK before letting them access the site. This is in compliance with the UK Online Safety Act.
UK, Germany urge Win 11 upgrade: The UK and Germany's cybersecurity agencies have urged organizations to look into upgrading to Windows 11 as Windows 10 is expected to reach end-of-life on October 14 this year.
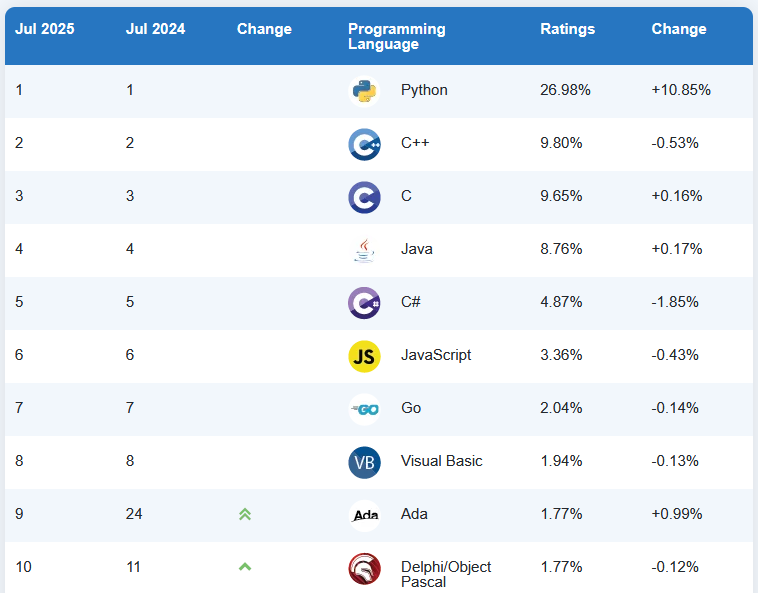
Ada enters Top 10: The 45-year-old Ada programming language has entered the TIOBE Top 10 index of programming languages for the first time. Ada is #9, Delphi is #10, and Fortran is #12. The end is nigh!
Government, politics, and policy
Russia to deploy AI in airports: The Russian government will deploy AI-based security systems at major Russian airports. The system is being developed by sanctioned IT company Ntechlab. It will be able to detect when passengers end up in areas they're not supposed to or when they attempt to bypass security checks. [Additional coverage in RTVI/English coverage in The Moscow Times]
Weird decision in crypto-theft case in Germany: A regional court in Germany has issued a weird decision in a case involving a crypto theft, basically absolving the alleged thieves of any guilt. From the explanation they provided, it appears that crypto-thefts aren't actually covered by any of Germany's stringently worded laws. [Additional coverage in Heise] [h/t afx]
Luxembourg NGOs ask for NSO sanctions: A group of Luxembourg-based NGOs has asked the government to impose sanctions on business entities registered in the country and associated with Israeli spyware maker NSO Group. [Additional coverage in LuxTimes]
EU holds age verification test: The European Commission will test an experimental age verification app next year in Denmark, Greece, Spain, France, and Italy.
ENISA creates Advisory Group: The EU's cybersecurity agency has established an Advisory Group to advise ENISA leadership on future projects. The new Advisory Group includes 26 security experts from member states in non-remunerated positions. The group was set up for a term of two and a half years and will start operating next month.
Microsoft outsources US government work to China: Microsoft is using Chinese engineers to manage and troubleshoot some of the DOD's cloud networks. The engineers are indirectly granted access to sensitive US government networks through a program called a digital escort. US-based personnel relay problems to engineers in China, who can provide computer commands to fix reported issues. According to a ProPublica investigation, the system may be gamed to trick US personnel into running malicious commands. Current and former government officials also said they weren't aware of Microsoft's outsourcing system.
NEW: Microsoft told @propublica.org that it disclosed details of the escort program to the U.S. government. But the Pentagon’s IT agency was unaware until reporter @reneedudley.bsky.social asked for comment. “Literally no one seems to know anything about this,” a spokesperson said.
— Chris Morran (@themorrancave.bsky.social) 2025-07-15T09:59:14.586Z
State Department cuts impact cyber policy teams: According to NextGov, the recent cuts at the US State Department have impacted staff at multiple bureaus engaging in cyber diplomacy with foreign nations.
US offensive cyber funding: Per TechCrunch, the next US spending bill allocates over $1 billion over the next year for DOD offensive cyber operations.
Pentagon adopts Grok: The US Department of Defense has awarded xAI a contract to use Grok for national security projects. And, yes, Grok also rolled out an anime companion and praised Hitler for a full day before the contract was awarded. YOLO!
Even The Onion would struggle to come up with a headline and story as ridiculous as this.
— Dare Obasanjo (@carnage4life.bsky.social) 2025-07-15T00:24:05.689Z
US post-quantum crypto migration: Per NextGov sources, the Office of Management and Budget has already drafted a memo telling US federal agencies to migration to fully migrate to a post-quantum cryptographic standard
DOJ fines IT contractor: A Maryland IT provider will pay a $14.75 million fine for lying to obtain US government contracts. The US Department of Justice says Hill Associates billed federal agencies for cybersecurity and other IT services its staff was not trained to provide. One of the company's customers was the US General Services Administration (GSA).
US opens investigation into imported drones: The US government has opened a national security investigation into foreign drone imports. A similar investigation will also target the import of polysilicon, a material used in solar panels and semiconductors. China is the main supplier of both products. The US government may seek to raise tariffs for both products in order to stimulate local production or companies to diversify their supply chains. [Additional coverage in Reuters]
House passes NTIA Organization Act: The US House of Representatives has passed the National Telecommunications and Information Administration Organization Act, a bill that would give the NTIA the power to establish a cyber office to help improve cybersecurity at US telcos. This still needs to pass the Senate. [Additional coverage in CyberScoop]
Imagine: You have highly capable threats, highly motivated to do your networks harm in the near-term - and they've shown they can do. As a policymaker, why would you go for a "market-based," "industry consensus-driven" process that takes years to complete? cyberscoop.com/ntia-cyberse...
— Beau Woods (@beauwoods.com) 2025-07-15T02:36:52.289Z
Sponsor section
In this Risky Bulletin sponsor interview, Zero Networks Field CTO, Chris Boehm, discusses the everyone-gets-an-AI future with Casey Ellis. Zero Networks makes network microsegmentation achievable without simply handing an AI control of the network. Will generative artificial intelligence ever be trusted to make hard access control decisions?
Arrests, cybercrime, and threat intel
Romania arrests HMRC phishing gang: Romanian and British authorities have detained 14 suspects involved in a phishing campaign targeting the UK's tax agency. Thirteen were detained in Romania, and one in the UK. The group used phishing and other techniques to obtain UK citizens' data and then filed fraudulent repayment claims with the HM Revenue and Customs. The group allegedly collected more than £1 million in fraudulent returns.
Diskstation ransomware member arrested in Italy: Italian police have arrested a 44-year-old Romanian for cyberattacks against Italian companies. The man is allegedly the leader of the Diskstation ransomware gang. Several of his accomplices were also raided last June in Bucharest, but no charges were announced. Authorities say they caught some of the suspects in "the act of a crime" when the raid took place. The group was involved in ransomware attacks against Synology NAS devices. [Additional coverage in ANSA/English coverage in Decripto]
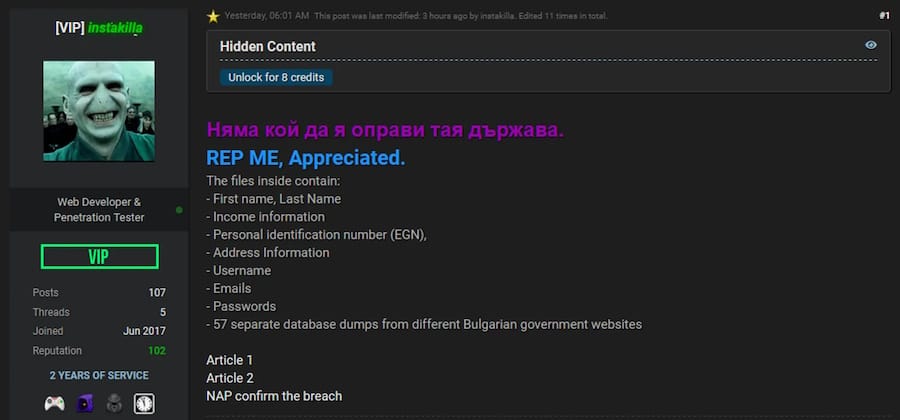
Bulgarian hacker sentenced to time served: A Bulgarian court has sentenced a local cybersecurity expert to a suspended nine-month sentence for hacking the country's tax agency. Kristiyan Boykov hacked the agency in 2019 while he was an employee of cybersecurity firm the TAD Group. Boykov leaked the database to reporters and was arrested a week later. The data later leaked on hacking forums and included the personal details of more than 5 million Bulgarians. [Additional coverage in BTA] [h/t DataBreaches.net]
Kiberphant0m pleads guilty: A former US Army soldier has pleaded guilty to hacking several US telcos. Cameron John Wagenius, 21, was known online as kiberphant0m and was active on BreachForums and XSS.is. He was involved in the Snowflake cloud provider hack, from where he acquired AT&T's data.
Chinese SMS blaster detained in Oman: Omani police have detained a Chinese tourist for SMS phishing campaigns. The woman allegedly drove around the country's capital city with an SMS blaster inside her car. She allegedly sent SMS messages posing as a local bank. [Additional coverage in CommRisk]

Telegram APK campaign: BforeAI has discovered 607 domains distributing malware-laced Android apps posing as the official Telegram IM.
Malvertising leads to macOS malware: Deriv looks at a Google malvertising campaign leading users to malicious GitHub repos hosting boobytrapped macOS apps containing malware.
Bengali campaign: McAfee has spotted an Android malware campaign that targets Bengali-speaking users in Bangladesh with apps mimicking local financial services.
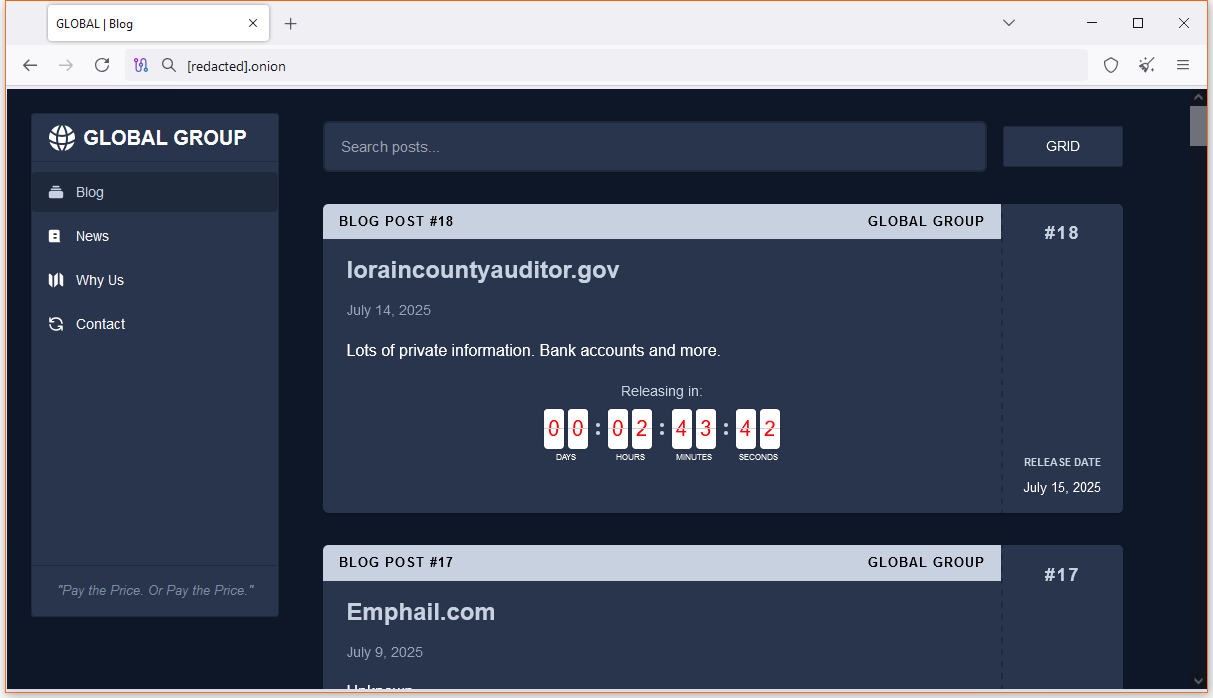
Global Group RaaS: A new RaaS named Global Group launched, advertised on the RAMP forum. According to EclecticIQ, the RaaS admin is the same individual who managed the previous BlackLock and Mamona platforms.
Malware technical reports
Konfety returns: Zimperium researchers have spotted new campaigns distributing the Konfety Android adware. To avoid detection, the malware is now using APK files with modified data structures to break security scanners and avoid detection.
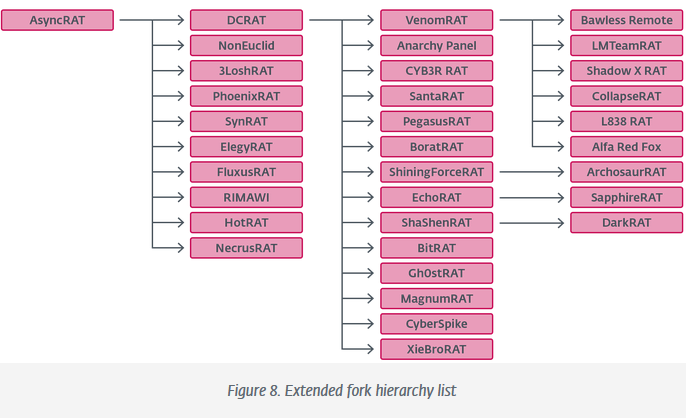
AsyncRAT family tree: ESET researchers have catalogued more than 30 remote access trojans that evolved from the old AsyncRAT codebase.
Interlock RAT (NodeSnake): The DFIR Report and Proofpoint look at recent campaigns spreading the Interlock RAT, aka NodeSnake. This strain is only used by the Interlock ransomware, and specifically by a cluster named KongTuke that uses a ClickFix variation named FileFix to infect victims.
Octalyn Stealer: CyFirma looks at the Octalyn Forensic Toolkit, a so-called digital forensics and red-team tool abused in the wild as an infostealer.
Secp0 ransomware: French security firm Lexfo has published a technical analysis of Secp0, a RaaS that launched earlier this year in January.
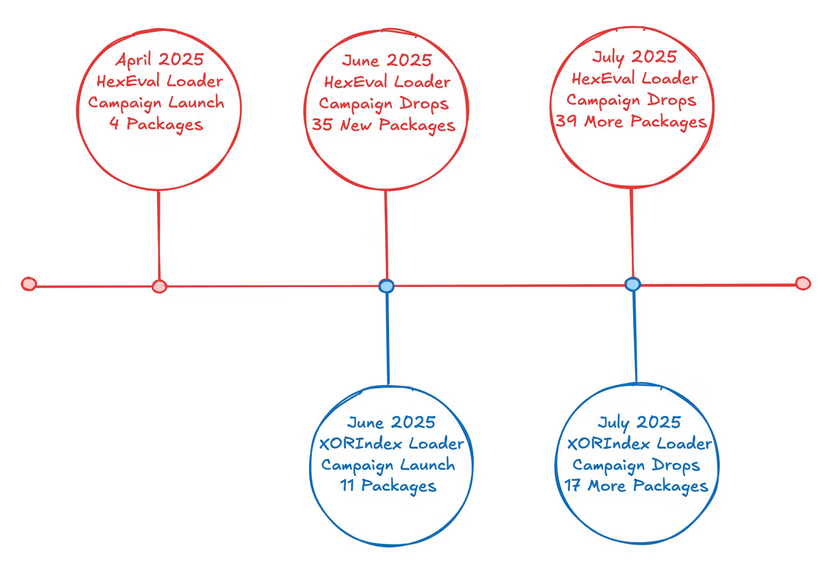
XORIndex Loader: Socket Security says the North Korean hackers behind the Contagious Interview campaign are now using a new malware strain they have named the XORIndex Loader. The malware is hidden inside npm packages sent to developers auditioning for various (fake) jobs advertised by the hackers.
Sponsor section
Zero Networks is offering a comprehensive guide that highlights the growing importance of advanced microsegmentation in a security landscape.

APTs, cyber-espionage, and info-ops
CL-STA-1020 targets SE Asia governments: A cyber-espionage group is targeting government agencies across Southeast Asia in search of information about recent tariffs and trade disputes. The attacks were spotted by Palo Alto Networks. The company says attackers used a novel Windows backdoor named HazyBeacon and a novel command-and-control communications channel that abused AWS Lambda URLs.
Vulnerabilities, security research, and bug bounty
NCSC VRI: The UK's cybersecurity agency has launched a program to bring external security researchers into its vulnerability researcher team. The experts will help government staff audit and test government and critical infrastructures for vulnerabilities. Interested researchers can apply via email.
Grok 4 is a security disaster: According to new SplxAI research, xAI's new Grok 4 model is a security disaster and vulnerable to nearly 1,000 different attack scenarios.
"With no system prompt, Grok 4 leaked restricted data and obeyed hostile instructions in over 99% of prompt injection attempts. With no system prompt, Grok 4 flunked core security and safety tests. It scored .3% on our security rubric versus GPT-4o's 33.78%. On our safety rubric, it scored .42% versus GPT-4o's 18.04%."
RCE in Broadcom Altiris: A vulnerability can allow remote attackers to run malicious code on the Broadcom Altiris endpoint management platform. The vulnerability resides in a legacy component. It allows remote attackers to deserialize and run malicious .NET code without authentication. The vulnerability was discovered by LRQA during a pen-test, and Broadcom released patches last month.
Google gets a precog: Google claims its Big Sleep AI detected that a threat actor was about to start exploiting an SQLite vulnerability and was able to stop the zero-day attacks before they happened. Ok there, Minority Report! Calm down!
Infosec industry
Threat/trend reports: Cloudflare, CyberCube+Munich Re, Fortified Health Security [PDF], KnowBe4 [PDF], and Qualys have recently published reports and summaries covering various infosec trends and industry threats.
MITRE launches AADAPT framework: The MITRE Corporation launched a new cybersecurity framework to assess and address threats in the cryptocurrency landscape. The new Adversarial Actions in Digital Asset Payment Technologies, or AADAPT, works similarly to MITRE's ATT&CK and D3FEND frameworks. It helps security teams classify and organize threats, TTPs, and the impact on the activity of blockchain and digital payment companies.
CrowdStrike will hire a Chief Resilience Officer: Security firm CrowdStrike has created a new executive role and will soon hire a Chief Resilience Officer. The new role will be dedicated to improving the company's engineering practices and will report directly to CEO George Kurtz. The hire is the company's answer to last year's outage that took down more than 8.5 million customer systems. CrowdStrike is still searching for the right person and will announce the hire soon.
New C level scapegoat position landed
— Kevin Beaumont (@doublepulsar.com) 2025-07-15T13:16:15.002Z
New tool—NovaHypervisor: Security researcher Ido Veltzman has open-sourced NovaHypervisor, a hypervisor designed to protect against kernel attacks.
New tool—LinkedIntel: TrustedSec researcher James Williams has released LinkedIntel, a Burp Suite extension for LinkedIn reconnaissance.
New tool—SharpSilentChrome: Security researcher Sunggwan Choi has open-sourced SharpSilentChrome, a tool to silently install extensions on Chrome and Edge by updating their preference files.
New tool—DoubleTeam: Security researcher Ricardo J. Ruiz Fernández has released DoubleTeam, a tool to generate reverse shell payloads that connect to random ports.
New tool—WDSFinder: Advens researcher BlackWasp has released WDSFinder, a tool to identify WDS servers in an Active Directory domain and enumerate their exposed SMB shares.
New tool—ExfilServer: Security researcher Vincent Yiu has released ExfilServer, a secure file upload server that provides client-side encryption and automatic upload functionality.
The Long Con 2024 videos: Talks from The Long Con 2024 security conference, which took place last November, are available on YouTube and the conference's website.
Risky Business podcasts
In this edition of Seriously Risky Business, Tom Uren and Amberleigh Jack talk about our developing understanding of the group that people call Scattered Spider. Independent security firms agree that there are a small number of key people who are driving the group's outrageous success.




