Risky Bulletin: Major scam kingpin arrested in Cambodia, extradited to China
In other news: Spyware maker pleads guilty; Bitfinex hacker released from jail early; far-right dating site hacked and leaked.

Risky Business Podcasts
In this special documentary episode, Patrick Gray and Amberleigh Jack take a historical dive into hacking in the 1980s. Through the words of those that were there, they discuss life on the ARPANET, the 414s hacking group, the Morris Worm, the vibe inside the NSA and a parallel hunt for German hackers happening at a similar time to Cliff Stoll’s famous Cuckoo’s Egg story.
Breaches, hacks, and security incidents
China hacks US House committees: Chinese hacking group Salt Typhoon has hacked the email systems used by congressional staff on multiple committees in the US House of Representatives. [Financial Times]
"Chinese intelligence accessed email systems used by some staffers on the House China committee in addition to aides on the foreign affairs committee, intelligence committee and armed services committee, according to people familiar with the attack. The intrusions were detected in December."
Jaguar sales slump after cyberattack: Jaguar Land Rover says its sales fell by 43% in Q3 following a ransomware attack that stopped production at its factories last fall for almost a month.
Sedgwick ransomware incident: IT company Sedgwick has confirmed that a ransomware attack has impacted its government contracting subsidiary over the New Year's Eve. The incident was claimed by the TridentLocker ransomware gang. [The Record]
Palo Alto crosswalks hacked again: Nine months after the first incident, crosswalks across Palo Alto, California, were hacked again to play AI-manipulated messages from Elon Musk and Mark Zuckerberg.
Fake Resecurity hack: Cybersecurity firm Resecurity says that the ScatteredLapsusShinyHunters hacking group breached a honeypot of its network and not its real systems—after the group claimed the hack in a Telegram post last year. [DataBreaches.net]
Global-e breach: Crypto-wallet Ledger is notifying users of a breach that exposed the owner's personal data after hackers breached Global-e, a third-party company the wallet maker uses to process payments. [Cryptopolitan]
Prosura hack: Hackers have stolen the data of car insurance Prosura. The hack seems to have originated from the company's VroomVroomVroom portal, with the threat actor emailing some customers about the hack. The hacker claimed to have found and reported a vulnerability but was ignored and didn't receive a bug bounty. [ABC]
Manage My Health gets court injunction: New Zealand health provider Manage My Health has obtained a court injunction against hackers who are threatening to release its data. A hacker named Kazu claims to hold more than 430,000 data records. [NZ Herald]
Bot attack on Romania's tax payment site: A "bot attack" is suspected to have taken down Ghiseul[.]ro, Romania's government tax payment portal. The site went down on the first days of the year when the government was expected to reveal and update everyone's new property tax values. [Antena 3 CNN]
FF14 DDoS attacks: DDoS attack waves have taken down the servers of Final Fantasy 14 during the release of new content earlier this week. [Eurogamer] [h/t Danny Palmer]
Canary Mission leak: More than 100GB of data was leaked from Canary Mission, a pro-Israel doxxing group. The leak exposed unlisted web portals where the group's members celebrate their doxxings, firings, or deportations. [Drop Site News]
WhiteDate leak: The data on more than 8,000 users of far-right dating site WhiteDate was scraped and leaked online after its administrators didn't secure their WordPress site properly. A German security researcher going by the name of Martha Root took credit for the leak and presented their findings at this year's 39C3 conference. [Cybernews]
General tech and privacy
X goes child pr0n wild: Elon Musk and his idiot management at X have lost their mind and are allowing the company's Grok AI to generate nude images, even for young children. Despite public backlash, the platform has yet to crack down on the practice, with Musk promoting some of the photos.Several investigations are now live across EU countries, but only crickets from the US. [WIRED // The Record]
The same Republican state legislatures that passed age verification laws for porn are silent on Grok creating and publishing CSAM. It was never about the children.
— Jake Williams (@malwarejake.bsky.social) 2026-01-06T13:55:20.231Z
X basically industrialized the creation of fake porn of women who don't consent. Others did it first, but Grok made it normalized and centralized: publicly visible, instantly creatable by anyone, regardless of who's being targeted and dehumanized. Only question now is will X suffer any consequences
— Drew Harwell (@drewharwell.com) 2026-01-07T12:45:50.595Z
Videos people created with Grok are more extreme than images on X: - A review of around 800 Grok videos found around 10% appeared to involve sexual content and minors - Some videos involved violent sexual scenes - Celebrities and real people were put into explicit videos, including Princess Diana
— Matt Burgess (WIRED) (@mattburgess1.bsky.social) 2026-01-08T13:05:59.956Z
Microsoft disables phone activation: Microsoft has shut down a system that allowed Windows and Office users to activate their products via phone. [Tom's Hardware]
Discord ready for IPO: According to multiple reports, Discord is preparing for an IPO, which means a major enshittification and monetization will be on the way after that. [Games Industry]
Samsung to pack AI into every new TV: Samsung, the world's largest smart TV maker over the past two decades, said at the annual CES conference that it will add AI capabilities into every of its TV models going forward. [techXplore]
DROP goes live: California has launched DROP, the Delete Request and Opt-out Platform, an online portal where California residents can request that data brokers delete or not sell their data.
WhatsApp deploys device fingerprinting protections: Meta has allegedly silently deployed anti-device fingerprinting protections for its WhatsApp service.
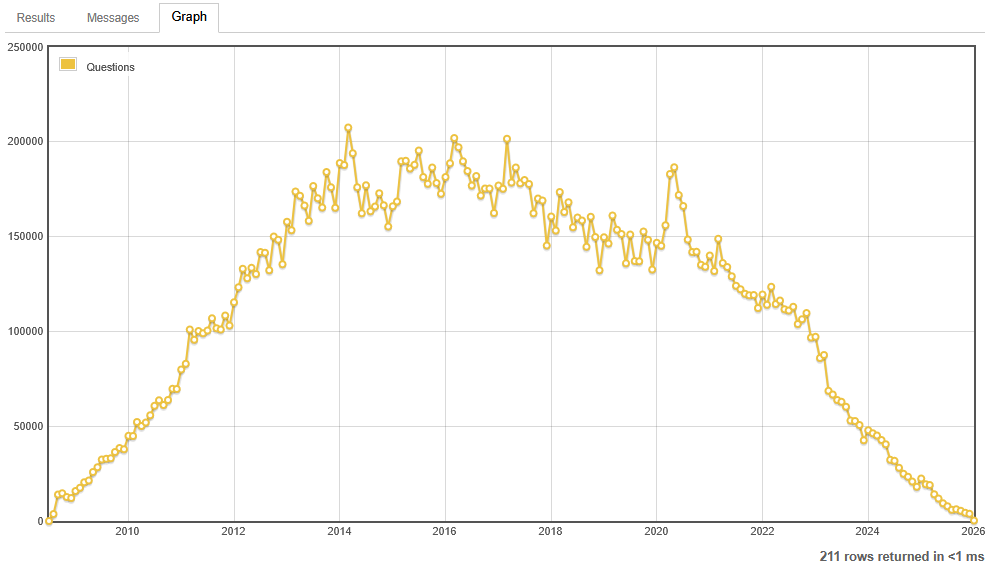
StackOverflow collapses: The number of monthly questions on Stack Overflow has collapsed from its peak of 207,000 in 2014 to just around 300 at the end of last year. The slow decline predates LLMs and chatbots, but appears to have been accelerated by them.
Government, politics, and policy
US Cyber Command active in Venezuela: Both the CIA and Cyber Command were active and contributed to the arrest of Venezuelan dictator Nicolas Maduro. What that was is unknown. Power outages in the capital Caracas on the night of the US attack were apparently caused by damage to two substations and not cyber. [DefenseOne]
Gen. Dan Caine, chairman of the Joint Chiefs, says Cyber Command provided support for the overnight operation to capture Maduro
— Sean Lyngaas (@snlyngaas.bsky.social) 2026-01-03T17:13:22.145Z
Venezuela confirms that the U.S. operation involved an attack on the National Electric System hitting 2 substations & causing power outages mppee.gob.ve?p=103279 But it wasn't 'cyber' A video posted by the Electric Energy Ministry shows physical damage t.me/minenergia_v...
— Oleg Shakirov (@shakirov2036.bsky.social) 2026-01-05T11:14:26.634Z
Cyber Trust Mark loses admin: UL Solutions, the company that was selected to run the Biden-era US Cyber Trust Mark program, has withdrawn from the contract after a Trump-era FCC launched an investigation into its alleged Chinese ties. The Cyber Trust Mark program is supposed to test smart devices and assign a cybersecurity compliance mark. [NextGov]
FCC pokes some holes: After the dummies at the FCC realized that a blanket ban on all foreign-made drone components was a bad idea, the agency has now added some vendors to an exemption list, allowing US companies to import some foreign-made drones and components. [Reuters]
US withdraws from cyber orgs: This week, the US has withdrawn from 66 international organizations, including several cybersecurity-related bodies such as the Global Forum on Cyber Expertise, the Online Freedom Coalition and the European Centre of Excellence for Countering Hybrid Threats. [Cyberscoop]
Germany spied on Obama: German intelligence service BND monitored Air Force One phone calls during the Obama years and did it without approval from then-chancellor Angela Merkel. [Die Zeit]
UK Government Cyber Action Plan: The UK government has allocated £210 million to a Cyber Action Plan, a project to strengthen the cybersecurity of UK government organizations and public services. The government will also set up a special "cyber unit" to help implement the plant.
Innos interview: In an interview, Col. René Innos of Estonia's Cyber Command, says Russia is an expert at "manipulating populations through social media and digital platforms." [InCyber News]
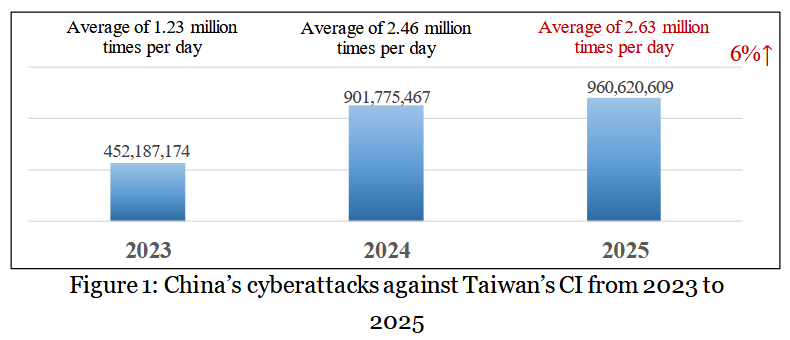
Cyberattacks against Taiwan intensify: Taiwan's National Security Bureau says Chinese cyberattacks against its critical infrastructure have gone up over the past year.
Arrests, cybercrime, and threat intel
pcTattletale founder pleads guilty: Bryan Fleming, the founder and admin of former spyware maker pcTattletale, has pleaded guilty to hacking and advertising surveillance software. [TechCrunch]
Scammer kingpin arrested: Cambodian authorities have arrested and deported to China Chen Zhi, the CEO of the Prince Group, a company tied to running a giant network of cyber scam compounds across South East Asia. He was also the subject of a US indictment. [The Standard]
Bitfinex hacker released early: Ilya Liechtenstein, the man who stole 120,000 Bitcoin from Bitfinex in 2016, was released early from prison. He only served 14 months of his five-year prison sentence.
Snapchat hacker charged: The US DOJ has indicted a former Northeastern University coach for hacking the Snapchat accounts of almost 570 women to steal and sell nude photos.
Desjardins hacking suspect arrested in Spain: Spanish authorities have arrested a man for allegedly hacking Canadian credit union Desjardins in 2019. Juan Pablo Serrano was arrested in November and is still in custody awaiting extradition. [CBC]
Russian basketball player freed in ransomware investigation: French authorities have released Daniil Kasatkin, a Russian basketball player who was sought by the US in connection to Conti ransomware attacks. He has already left for Moscow. [Reuters]
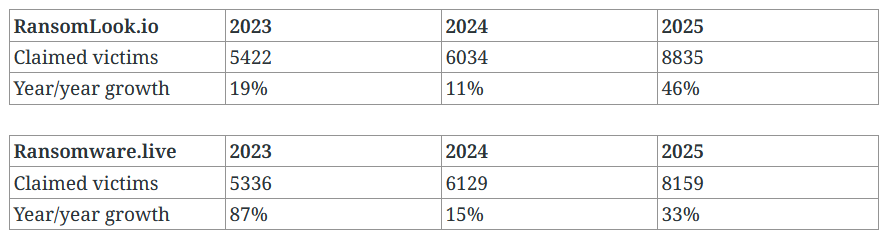
Ransomware had a massive year: According to Emsisoft, ransomware groups had a massive year claiming between 8,100 and 8,800 victims last year, between 33% and 46% growth from the previous year (depending on sources).
Zestix profile: Hudson Rock has published a profile of Zestix, a hacker advertising the data of dozens of companies on dark web forums.
Black Cat group: China's CERT team looks at Black Cat, a group engaged in SEO poisoning attacks mimicking popular apps.
Resecurity leaks IRDev email comms: Security firm Resecurity has released 105 pages containing the email subjects extracted from the one of the email inboxes of John Erin Binns, aka IRDev, one of the members of the Scattered LAPSUS$ Hunters hacking group. [h/t SwitHak]

Venezuela BPG anomalies: Cloudflare says that BGP routing anomalies right before the US intervention and arrest of Nicolas Maduro appear to have been just "an accident."
New spyware vendor: Intelligence Online has published a profile on 9th Vision, a South African company that has sold zero-click spyware to several governments, such as Indonesia, Pakistan, Myanmar, Venezuela, and Mexico.
"Among the government bodies listed on documents seen by Intelligence Online are 🇵🇰Pakistan and its defence ministry, 🇮🇩Indonesia's State Intelligence Agency, the 🇲🇲Myanmar Police Force, 🇲🇽Mexico's army and navy and 🇻🇪Venezuela's defence ministry." www.intelligenceonline.com/americas/202...
— Vas Panagiotopoulos (@vaspanagiotopoulos.com) 2026-01-06T20:20:29.989Z
Fake BSODs ClickFix: It was to be expected but ClickFix pages now mimic the Windows Blue Screen of Death screen. [Securonix]
Phishing ops abuse routing misconfigs: PhaaS platforms are abusing misconfigurations in complex routing scenarios and anti-spoofing protections to spoof domains for their operations, making their emails appear as have been sent internally, inside a targeted org, per a new Microsoft report.
Tap-to-pay malware trend: Group-IB looks at a trend rising in China where cybercrime groups are shifting to the use of malware that uses an NFC-based tap-to-pay scheme to steal user funds, using malicious apps to trick users into taping their card on their phones and approving malicious transactions. These schemes are also known as ghost tapping.
"From August 2024 through August 2025, multiple tap-to-pay applications were documented in the cybersecurity community, including NGate in August 2024, ZNFC in February 2025, SuperCard X in April 2025, and most recently, PhantomCard in August 2025."
ownCloud warns of credential thefts: ownCloud has urged customers to enable MFA for their accounts after reports of credential thefts.
Malicious Edge add-on: Microsoft has removed a malicious Edge add-on named MadaoL Newtab that exploited the Office Assistant software to deploy malware on user systems. The software is very popular in China.
Extensions continue to steal AI prompts: After an initial discovery last year that some Chrome extensions were stealing AI prompts, three new extensions (two+one) have been discovered since doing the same thing.
Malware technical reports
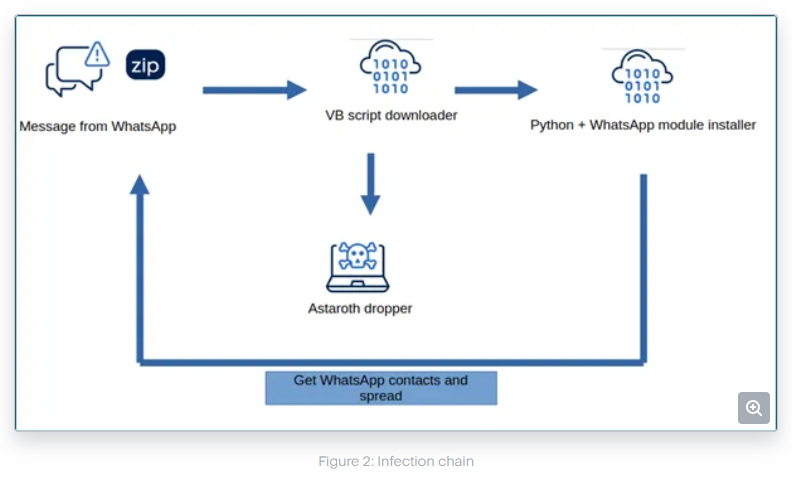
Astaroth activity: The Astaroth banking trojan is active again in Brazil, leveraging a WhatsApp self-spreading mechanism.
Predator spyware: ReverseSociety has published a technical analysis of the NSO Group's Predator iOS spyware implant.
NodeCordRAT: Zscaler looks at NodeCordRAT, a remote access trojan delivered via malicious npm packages last November.
VVS Stealer: Palo Alto Networks has published a technical analysis of VVS Stealer, a new infostealer that launched last April.
pkr_mtsi packer: ReversingLabs has a breakdown of pkr_mtsi, a malware packer used in the wild across several infostealer campaigns.
Lockbit 5.0: AhnLab has published a report looking at 5.0 version of the Lockbit ransomware.
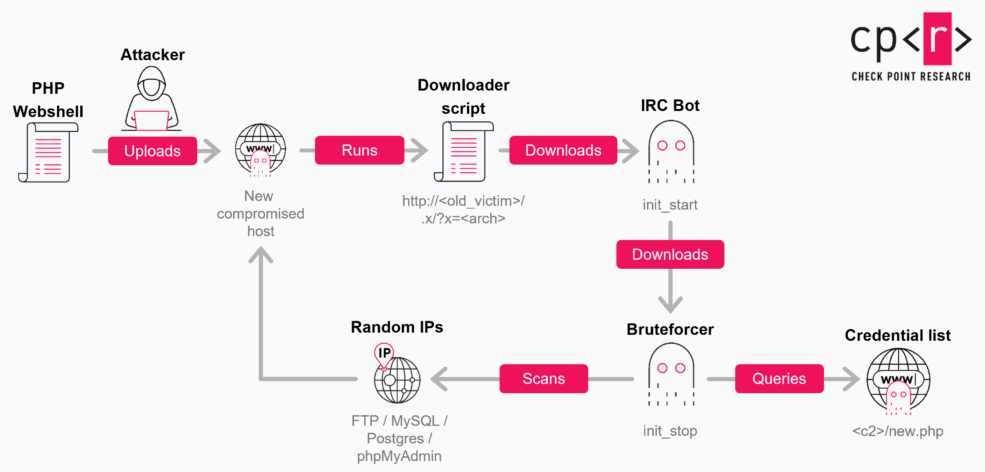
GoBruteforcer: Check Point looks at GoBruteforcer, a Go-based botnet used for brute-force attacks. The company estimates the botnet is running roughly on more than 50,000 systems.
APTs, cyber-espionage, and info-ops
Patchwork's StreamSpy: QiAnXin looks at StreamSpy, a backdoor used by Indian APT group Patchwork, aka Dropping Elephant and APT-Q-36.
UAT-729: Cisco has published a report on UAT-729, a suspected Chinese APT group spying on telcos and critical infrastructure across South Asia since 2022. Its arsenal includes implants such as RushDrop, DriveSwitch, and SilentRaid.
Lotus Panda's Sagerunex: Securite360 has published a report on Sagerunex, a malware implant used by the Lotus Panda APT, also known as Billbug, Lotus Blossom, and Red Salamander.
Knownsec leak analysis: Resecurity takes a look at the data leaked from Chinese security firm and government cyber contractor Knownsec.
"Overall, the collected material points to an organization operating far beyond the scope of a conventional cybersecurity vendor. Knownsec appears to combine commercial security products with large-scale data aggregation, offensive tooling, and close collaboration with government, public security, and military entities. The breadth of datasets, the nature of the capabilities shown, and the number of state-linked projects indicate a role that aligns with national-level intelligence collection, cyber-operations support, and network infrastructure mapping."
BlueDelta: Recorded Future looks at a credential-harvesting campaign from the GRU-affiliated BlueDelta APT that targeted the Turkish energy and nuclear research agency, staff affiliated with a European think tank, and organizations in North Macedonia and Uzbekistan.
Russian disinfo-ops: …never stop.
Kimsuky quishing operations: The FBI has sent out a flash alert warning that North Korean hacking group Kimsuky has adopted quishing, the use of malicious QR codes, for its phishing operations in the US. [Flash alert PDF]
Vulnerabilities, security research, and bug bounty
Important security updates: Cisco, Coolify, D-Link, Forcepoint, jsPDF, n8n, Open WebUI, QNAP, Roundcube, Veeam.
Hinge abuse: Security researcher Matt Wiese has published a write-up on how to use the Hinge dating app as a command and control infrastructure.
D-Link zero-day exploitation: VulnCheck has spotted exploitation of a new zero-day (CVE-2026-0625) in D-Link DSL routers and gateways. Affected devices were declared end-of-life/end-of-service in early 2020, so there are no patches.
HPE OneView exploitation: CISA says threat actors are exploiting an HPE OneView vulnerability that was patched in December. Attacks have also been spotted targeting a 2009 Office bug.
Unpatched Totolink bug: Totolink has declined to patch a vulnerability in its EoL EX200 firmware.
Ni8mare vulnerability: There's a 10/10 CVSS vulnerability in n8n, an automation platform for building AI agents. This is tracked as CVE-2026-21858 and by the name of Ni8mare.
ZombieAgent vulnerability: Radware researchers have discovered a zero-click vulnerability in OpenAI's ChatGPT that can expose a user's data. The vulnerability has been named ZombieAgent and has several variations.
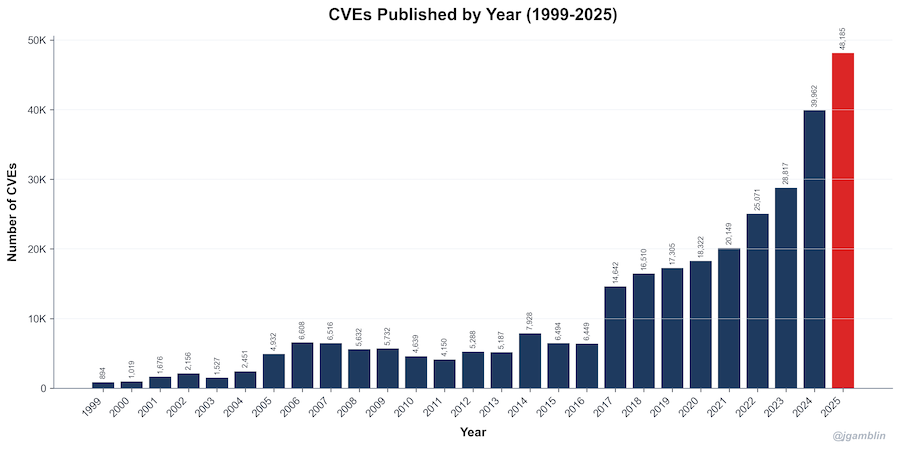
2025 vulnerabilities in review: More than 48,000 vulnerabilities were reported and received a CVE last year, up from the 39k reported in 2024. The Linux kernel saw the most vulnerabilities this year, followed by Windows 10 and Android. [Jerry Gamblin]
Infosec industry
Threat/trend reports: Barracuda, CyFirma, Emsisoft, Microsoft, Nametag [PDF], Netskope, Objective-See, Rapid7, Recorded Future, and Top10VPN have recently published reports and summaries covering various threats and infosec industry trends.

New tool—SILPH: Security researcher Haroun AL Mounayar has released SILPH, an open-source red team tool designed to dump LSA secrets, SAM hashes, and DCC2 credentials entirely in memory, without writing any files to disk.
New tool—Tailsnitch: Security firm Adversis has released Tailsnitch, a tool to audit Tailscale configurations.
New tool—WaSonar: Security researcher Adam Habchi has released WaSonar, a tool for discovering security flaws in WhatsApp. It includes real-time device tracking, silent RTT probing, and protocol stress testing.
New tool—Proxycontain: Diego Fernando Uribe has published Proxycontain, a Firefox add-on to support different proxying and HTTP header manipulation for Firefox containers.
Acquisition news: Security giant Cloudflare will acquire SGNL, a provider of AI-based identity solutions.
VULNCON videos: Talks from the VULNCON 2025 security conference, which took place in April, are available on YouTube.




