Risky Bulletin: Linux adds PCIe encryption to help secure cloud servers
In other news: Europol cracks down on Violence-as-a-Service providers; ICC designates cyberspace as a genocide enabler; Cambodia busts SMS blaster warehouse.

This newsletter is brought to you by Mastercard. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
The Linux kernel is adding support for a new security feature designed to help secure cloud server infrastructure.
Support for PCI Express Link Encryption will roll out with the upcoming release of the Linux kernel, version 6.19.
The new feature was developed together by representatives from chipmakers Intel, AMD, and Arm.
It will use certificates and keys to encrypt data sent between CPUs and hardware components connected via a PCIe slot.
PCIe is typically used to connect GPUs to the motherboard and the CPU in "normal" PCs and laptops, but the standard has also been widely adopted to create the custom setups in most of today's cloud infrastructure.
PCIe Link Encryption will allow cloud providers to add an extra layer of protection to their infrastructure by certifying known devices and preventing rogue hardware from being connected to their servers to intercept data.
A very technical explanation on how this will work was provided by Dan Williams, a Senior Principal Engineer at Intel:
"PCIe link encryption is made possible by the soup of acronyms mentioned in the shortlog below. Link Integrity and Data Encryption (IDE) is a protocol for installing keys in the transmitter and receiver at each end of a link. That protocol is transported over Data Object Exchange (DOE) mailboxes using PCI configuration requests.
The aspect that makes this a "platform firmware service" is that the key provisioning and protocol is coordinated through a Trusted Execution Environment (TEE) Security Manager (TSM). That is either firmware running in a coprocessor (AMD SEV-TIO), or quasi-hypervisor software (Intel TDX Connect / ARM CCA) running in a protected CPU mode.
Now, the only reason to ask a TSM to run this protocol and install the keys rather than have a Linux driver do the same is so that later, a confidential VM can ask the TSM directly "can you certify this device?".
That precludes host Linux from provisioning its own keys, because host Linux is outside the trust domain for the VM. It also turns out that all architectures, save for one, do not publish a mechanism for an OS to establish keys in the root port. So "TSM-established link encryption" is the only cross-architecture path for this capability for the foreseeable future.
Acceptance of this pull request unblocks the other arch implementations to follow in v6.20/v7.0, once they clear some other dependencies, and it unblocks the next phase of work to implement the end-to-end flow of confidential device assignment. The PCIe specification calls this end-to-end flow Trusted Execution Environment (TEE) Device Interface Security Protocol (TDISP).
In the meantime, Linux gets a link encryption facility which has practical benefits along the same lines as memory encryption. It authenticates devices via certificates and may protect against interposer attacks trying to capture clear-text PCIe traffic."
The new security feature was published days before three vulnerabilities were disclosed in PCIe standard that can allow threat actors with physical or low-level access to the PCIe IDE interface to craft and send packets through the connection.
Risky Business Podcasts
The main Risky Business podcast is now on YouTube with video versions of our recent episodes. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
Apple, Google send out new spyware notifications: Apple and Google have sent a new wave of spyware notifications to users in almost 80 countries. Neither company provided details about the spyware. The notifications were sent days after Google published a report on the activity of spyware vendor Intellexa. [Reuters]
Police raid Coupang offices: South Korean authorities have raided the headquarters of South Korean e-commerce giant Coupang. Authorities collected evidence related to a recent hack that exposed the personal data of two-thirds of the country's population. According to reports in local media, the company subscribed to the minimum cyber insurance coverage and allegedly ignored data protection practices. Coupang filed a complaint over the hack against a former employee, identified as a Chinese national. [France24]
New Khashoggi lawsuit: The widow of slain WaPo reporter Jamal Khashoggi has filed a new lawsuit in France against the government of Saudi Arabia for hacking her device with spyware. She also tried to sue Saudi Arabia in the US, but that lawsuit was thrown out in 2022. [France24]
Aeroflot hack story: Russian independent news outlet The Bell has published the backstory of the hack of Russia's national airline Aeroflot from this July. The point of entry for the hack appears to have been Bakka Soft, an IT company that developed Aeroflot's mobile and web apps.
General tech and privacy
FTC denies SpyFone petition: The FTC has denied a petition filed by SpyFone CEO Scott Zuckerman to overturn a 2021 order that banned him from offering surveillance products.
Google removes CBP app: Google has removed an app from the US Customs and Border Protection. The app, named Mobile Identify, allowed local cops to use facial recognition to scan for possible immigrants. [404 Media]
Meta agrees to use less personal data for ads: Meta will prompt users in January and ask them if they want to be tracked and see personalized ads or have less data collected and see less relevant ads. Geez, I wonder which option everyone will pick! /s
EU opens Google probe: The EU has opened an investigation into Google for its using content uploaded on the internet and its Youtube platform to train its AI without the content owner's permission.
AI is making up research: The Red Cross warns that AI tools are making up references to research and papers that do not exist.
Chrome's new User Alignment Critic: Google has detailed User Alignment Critic, a new Chrome security feature that separates the Gemini AI agent that ships with Chrome from user inputs, as a way to intercept malicious operations and possible prompt injection attacks.
Chrome 143: Google has released version 143 of its Chrome browser. See here for security patches and webdev-related changes. The biggest change in this release is support for Unicode 16, the deprecation of XSLT, and a Read Aloud feature for its Reading Mode.
Firefox 146: Mozilla has released Firefox 146. New features and security fixes are included. The biggest feature in this release is the ability to securely back up your Firefox settings on Windows and the broad availability of Firefox Labs experimental features to everyone, even if they want to share usage data or not.
Government, politics, and policy
NDAA 2026 comes with cyber provisions: The US House and Senate have reached an agreement on the 2026 National Defense Authorization Act (NDAA). The bill includes several cybersecurity-related clauses. Senior DOD officials will be required to use encrypted phones and cyber personnel would have access to mental health services. The bill also includes language to discourage the use of spyware against journalists and splitting up the joint NSA-CyberCommand leadership. The NDAA is expected to be submitted for a vote as early as this week. [CyberScoop]
New Zealand notifies Lumma victims: New Zealand's cybersecurity agency is notifying more than 26,000 users who have been infected with the Lumma Stealer.
ICC rules cyber as genocide enabler: The International Criminal Court will investigate genocide and war crimes that have been enabled through cyberspace. The ICC published its new policy this month and has put cyber on the same footing as crimes committed through other means. Hacks, data leaks, propaganda, and social media posts will now be valid evidence in ICC investigations. [Lawfare Media]
Today, the ICC Office of the Prosecutor published its Policy on Cyber-Enabled Crimes under the Rome Statute. In April, Marko Milanovic, who assisted in the drafting of this Policy, provided some key takeaways. www.lawfaremedia.org/article/icc-...
— Lawfare (@lawfaremedia.org) 2025-12-03T20:22:09.307Z
Sponsor section
In this Risky Business sponsor interview, Mike Lashlee, CSO of Mastercard talks to Tom Uren about why the company got into threat intelligence. Mike talks about bringing together payments insights with threat intel to get strong signals about fraud or crime, the benefits of international collaboration and when it makes sense for your CSO to also be the CISO.
Arrests, cybercrime, and threat intel
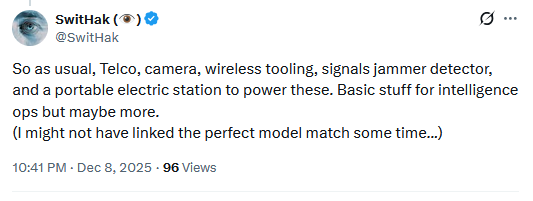
Poland arrests three Ukrainian hackers: Polish authorities have arrested three Ukrainian men in the city of Warsaw. The suspects had hacking equipment in their car. Officials seized Flipper Zero devices, antennas, laptops, portable hard drives, SIM cards, and routers. They also seized something authorities described as a "spying device detector." The suspects refused to say why they had the equipment in the car. [TVP World]

Russia arrests NFCGate hackers: Russian authorities have arrested three suspects for using NFC-capable malware. The trio stole more than $2.6 million from the bank accounts of Russian citizens. The malware intercepted NFC operations on a user's phone and relayed the data to individuals waiting to cash out the funds at an ATM.
Spain arrests 19yo hacker: Spanish police have arrested a 19-year-old for hacking and selling the data of nine companies. The teen was arrested this week in the city of Igualada, near Barcelona. He allegedly stole more than 64 million records, which he was selling under five pseudonyms on multiple hacking forums.
Europol cracks down on the VaaS scene: Europol has arrested 193 individuals associated with Violence-as-a-Service providers. This includes individuals who recruited people for violent acts, platform operators, and the perpetrators of violent acts. The suspects were linked to attempted murders and shootings across several countries.
Police bust SMS blaster depot: Cambodian authorities have raided a warehouse storing a dozen of unauthorized SMS blaster devices. The gear was allegedly being prepared to be installed in cars that would be driven across the city and blast SMS spam to nearby phones. Police discovered the warehouse after busting one of the cars last week. [CommsRisk]
Security teams must block AI browsers: A Gartner report has called on CISOs and security teams to block agentic AI browsers for the time being, citing security risks. [PCMag]
New VSCode malware: Koi Security researchers have discovered a malicious VSCode theme (Bitcoin Black) and extension (Codo AI) that captures a user's screen and sends it to attackers, in the hopes of capturing passwords and crypto-wallet seed phrases.
GrayBravo: Recorded Future looks at GrayBravo, the threat actor behind new malware strains such as CastleLoader, CastleBot, and CastleRAT. The group has been active since at least March this year.
Storm-0249 updates: ReliaQuest says that an initial access broker for ransomware groups tracked as Storm-0249 is now the latest group to adopt EDR killer tools before deploying their payloads. On a personal note, with so many EDR-killer POCs on GitHub, I'm wondering why the other groups aren't using this by now.
JS#SMUGGLER campaign: Securonix looks at a campaign leveraging malicious JS code on compromised websites to deliver the NetSupport RAT.
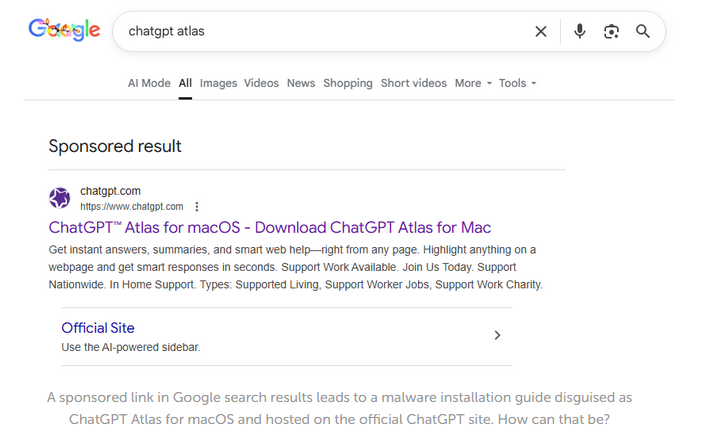
ChatGPT share link abuse: Threat actors are abusing the ChatGPT share chat feature to poison search results, posing as ChatGPT itself and luring users into installing versions of the OpenAI Atlas browser containing the AMOS macOS infostealer. [Kroll//Kaspersky]
React2Shell exploitation hits IoT space: If you thought that the React2Shell exploitation was mostly limited to enterprise apps built with the React framework, Bitdefender is here to tell you that the exploit has been adopted by IoT botnet operators who are using it to go after smart devices that might be using React for their web management panels. Fun, fun, fun!
Telegram crime crackdown: Russian security firm Kaspersky claims that Telegram has increased its crackdown rate on cybercrime-related channels. The crackdown seems to have started in October 2024.
Malware technical reports
GhostFrame PhaaS: Barracuda's security team has linked some recent phishing campaigns to a new Phishing-as-a-Service named GhostFrame.
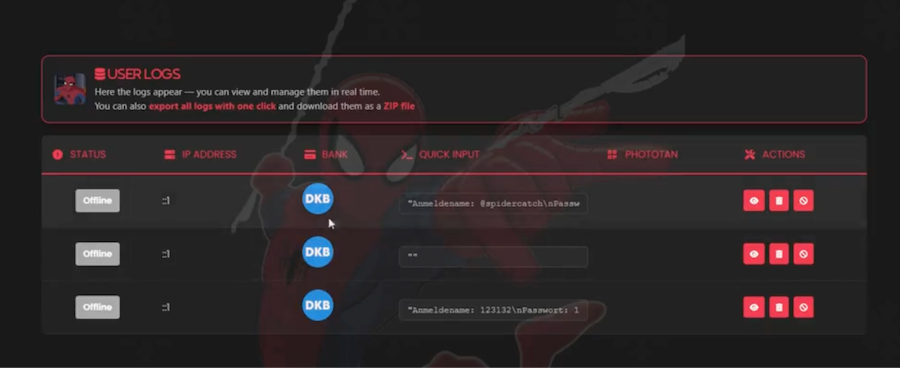
Spiderman PhaaS: On the same topic, Varonis spotted another PhaaS, this one named Spiderman and currently used to target the users of European banks.
QuasarRAT: Sekoia has published a technical analysis of QuasarRAT, an open-source remote access trojan, originally published on GitHub as xRAT.
LummaStealer: G DATA looks at a campaign spreading the LummaStealer using Itch.io spam comments to spread update links for games hosted on Patreon.
ChimeraWire: Dr.Web has discovered a new trojan named ChimeraWire that helps boost the SERP ranking of certain websites by performing hidden internet searches and mimicking user clicks on infected Windows devices. ChimeraWire is typically deployed as a second-stage payload on systems previously infected with other malware.
GhostPenguin: Trend Micro has found a new Linux backdoor named GhostPenguin. The malware appears to be in its early stages of development.
Broadside botnet: Cydome has spotted Broadside, a new variant of the Mirai IoT malware. The botnet is targeting TBK DVRs, commonly used by the maritime sector, including on some vessels.
DeadLock ransomware: Cisco Talos looks at the DeadLock, a new ransomware strain that targets Windows machines with a custom encryption algorithm that uses "time-based cryptographic keys to encrypt files."
"This custom encryption method allows DeadLock ransomware to effectively encrypt different file types in enterprise environments while preventing system corruption through selective targeting and anti-forensics techniques, which complicate recovery."
Sponsor section
In this sponsored Soap Box edition of the Risky Business podcast, host Patrick Gray chats with Mastercard's Executive Vice President and Head of Security Solutions, Johan Gerber, about how the card brand thinks about cybersecurity and why it's aggressively investing in the space.
APTs, cyber-espionage, and info-ops
MuddyWater's UDPGangster: Fortinet looks at UDPGangster, a new backdoor used by Iranian APT group MuddyWater. The malware is delivered via phishing campaigns leveraging Word documents. Attacks have targeted users in Turkey, Israel, and Azerbaijan.
The DPRK's new EtherRAT: Per Sysdig, North Korean hackers are now exploiting the React2Shell vulnerability to drop EtherRAT, a remote access trojan that uses Ethereum smart contracts as command-and-control system. Although, there are some discussions if this is truly a DPRK group.
Vulnerabilities, security research, and bug bounty
Prompt injections will be a problem: The UK NCSC's Technical Director for Platforms Research warns that it may never be possible to fully mitigate prompt injection attacks in AI agents.
ShellShock exploitation spike: F5 has seen a spike in exploitation activity targeting the 2014 ShellShock vulnerability.
Password manager research: Germany's cybersecurity agency has conducted a security audit of ten password managers and found that three of them can access a user's stored passwords—Google Chrome, mSecure, and PassSecurium. [TechZine]
ZeroBoot: Security researchers have published details on ZeroBoot, a cold boot exploit and FBE bypass for Samsung A25 smartphones.
Patch Tuesday: Yesterday was the December 2025 Patch Tuesday. We had security updates from Adobe, Microsoft, IBM, SAP, Ivanti, Citrix, F5, Supermicro, Cisco, Fortinet, Intel, AMD, NVIDIA, Schneider Electric, Siemens, Rockwell Automation, Moxa, Synology, Firefox, PowerDNS, Jenkins, and Zoom. Android, Arm, Chrome, D-Link, Samsung, Qualcomm, HPE, Juniper, WatchGuard, Splunk, SolarWinds, Fortra, Kubernetes, Apache Tika, React, Drupal, and Django released security updates last week as well.
Microsoft Patch Tuesday: This month, Microsoft patched 56 vulnerabilities, including fixes for an actively exploited zero-day, CVE-2025-62221, an EoP in the Windows Cloud Files Mini Filter Driver.
Infosec industry
Threat/trend reports: AU10TIX, Check Point, DreamHost, Gartner, ISC2, Marsh, ThreatMon, and WhiteIntel have recently published reports and summaries covering various threats and infosec industry trends.
New tool—LazyHook: A malware reverse-engineer named HwBp has released LazyHook, a tool to bypass Host Intrusion Prevention Systems (HIPS) and execute malicious code within trusted Microsoft call stacks.
Acquisition news: AppSec company Checkmarx has acquired Tromzo, a company that develops AI-native autonomous security agents.
Risky Business podcasts
In this edition of Seriously Risky Business, Tom Uren and Patrick Gray discuss a new report proposing a framework for deciding when cyber operations raise red flags. It suggests seven red flags and could help clarify thinking about how to respond to different operations.
In this edition of Between Two Nerds, Tom Uren and The Grugq wonder whether it is possible to deter states from cyber espionage with doxxing and other disruption measures.




