Risky Bulletin: Large-scale study aims to assess Rowhammer's real world impact
In other news: Trump nominates new CISA Director; DOGE fires CISA red teams; crucial Firefox root certificate expires this week.

This newsletter is brought to you by GreyNoise. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
A team of academics is conducting a large-scale public study to assess the real-world impact of the Rowhammer vulnerability.
First described in a 2014 research paper, Rowhammer is an attack that revolves around the concept of "hammering" a row of RAM memory cells with constant read or write operations. The constant process of turning memory cells on and off causes electrical interference on nearby memory cells, which academics say can be exploited to alter or leak memory data.
For the past decade, multiple teams of academics from all over the world have expanded the original attack to cover multiple technology platforms and optimize and speed up attacks, even showing theoretical web-based exploitation via JavaScript code and raw network packets. Researchers even bypassed some of the tech industry's Rowhammer protections.
In 2021, Google warned that Rowhammer attacks were getting more powerful as memory cards were getting smaller and memory raws were smaller and even more bunched together than before.
But despite all the academic work done on the topic, there have never been any reports of Rowhammer attacks in the wild. This has led some people to repeatedly question the attack's feasibility in real-world scenarios.
In a talk at the 38th Chaos Communication Congress in December, a team of three academics said that the actual impact of this attack is still unknown and purely theoretical.
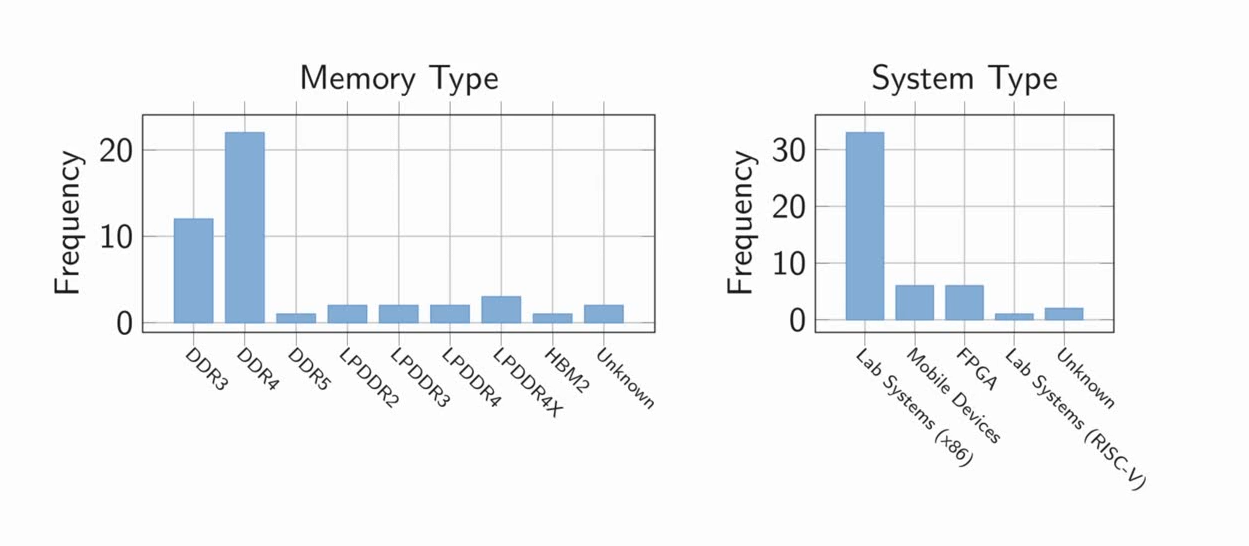
They cited past Rowhammer academic work and highlighted that most papers had almost microscopic sample sizes.
"Basically, the sample size of the different papers is very low. The sample size has a median of four. Most papers have a sample size of one."
Now, this very same team has launched a new project named FlippyRAM, which aims to test the Rowhammer attack against real devices in the real world and not just academic lab setups.
The researchers have released an ISO file that can be installed on a USB thumb drive. Once plugged into a system, the drive will conduct a Rowhammer attack against the system and generate a report that users can upload back on the FlippyRAM website.
The research team—made up of Daniel Gruss, Martin Heckel and Florian Adamsky—hopes that through their website, they will set the debate around what Rowhammer's real-world impact is and have a better grasp of what systems are most at risk.
The team's 38C3 talk is below.
Risky Business Podcasts
Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
NY AG sues Allstate over past breaches: The state of New York sued insurance provider Allstate for two breaches at its National General subsidiary. The breaches took place in 2020 and 2021 and exposed the personal information of almost 160,000 New York residents. National General allegedly failed to detect the hacks in time and failed to notify affected customers. The New York Attorney General says the company's woeful security posture continued after the Allstate acquisition.
Twitter DDoS attack: A pro-Palestinian hacktivist group named the Dark Storm Team has taken credit for a DDoS attack that took down social media network Twitter for hours on Monday. Twitter owner Musk confirmed the attack and claimed it originated from a cluster of Ukrainian IPs. Sources have told RiskyBusiness this is not true and that the attack was geographically distributed. [Additional coverage in Reuters]
Elon Musk’s claim the X DDoS is from “IP addresses originating in the Ukraine area” is missing a key fact - it was actually IPs from worldwide, not just Ukraine. It’s a Mirai variant botnet, made of compromised cameras. They specifically targeted a Twitter ASN which had origin servers not behind CF
— Kevin Beaumont (@doublepulsar.com) 2025-03-10T22:30:56.010Z
General tech and privacy
Location data industry investigation: California AG Rob Bonta has initiated a broad investigation into the location data industry for breaking the state's privacy law, the CCPA.
Google tells users not to factory-reset Chromecasts: Google has told customers not to factory-reset old and outdated Chromecast devices due to a bug that breaks device validation. [Additional coverage in Android Police]
Firefox root certificate expiration: Mozilla has asked users to update to Firefox 128 or above by Friday, March 14, before a crucial Firefox root certificate expires that day. Once the root certificate expires, the browser will stop receiving security updates, add-ons will be disabled, and some DRM-protected content won't play.
BlueSky expands video support: Social media app BlueSky now supports videos of up to three-minutes long. It now also separates DMs from unknown users in a separate inbox as a way to fight spam.
📢 App Version 1.99 is rolling out now (1/5) With every update, we’re aiming to make the Internet less toxic, more fun, and more in your control. • 3 minute videos! • A separate request inbox for DMs from unknown users • Mute accounts more quickly
— Bluesky (@bsky.app) 2025-03-10T18:28:34.826Z
Government, politics, and policy
DOGE fires CISA red teams: The US Department of Government Efficiency (DOGE) has fired two of CISA's red teams. Over 300 CISA employees were fired, including over 100 working on the agency's red teams. The firings are the third round of DOGE-ordered layoffs at the agency this year. [Additional coverage in TechCrunch]
New CISA director: The Trump administration nominated Sean Plankey for the role of director of the US Cybersecurity and Infrastructure Security Agency. Plankey server in different cybersecurity roles during the first Trump administration. He also served in US Cyber Command and was chief information officer for the US Navy. His approval is considered a formality. [Additional coverage in CyberScoop]
CISA cuts MS-ISAC funding: CISA has cut funding for the Multi-State Information Sharing & Analysis Center (MS-ISAC). The group was established in 2004 to allow federal, state, and local governments to easily share information about emerging cyber threats and vulnerabilities. CISA was funding the program with $10 million per year. MS-ISAC had over 17,000 members representing state, local, tribal, and territorial government organizations. [Additional coverage in StateScoop/Eric Geller's BlueSky thread]
CISA has terminated a $10m partnership w/ the Center for Internet Security to run the info sharing & analysis centers (ISACs) for state & local govts and elections. Spox says work "no longer effectuates [DHS] priorities" & cut will focus CISA on "mission critical areas" & "eliminate redundancies."
— Eric Geller (@ericjgeller.com) 2025-03-11T18:42:54.623Z
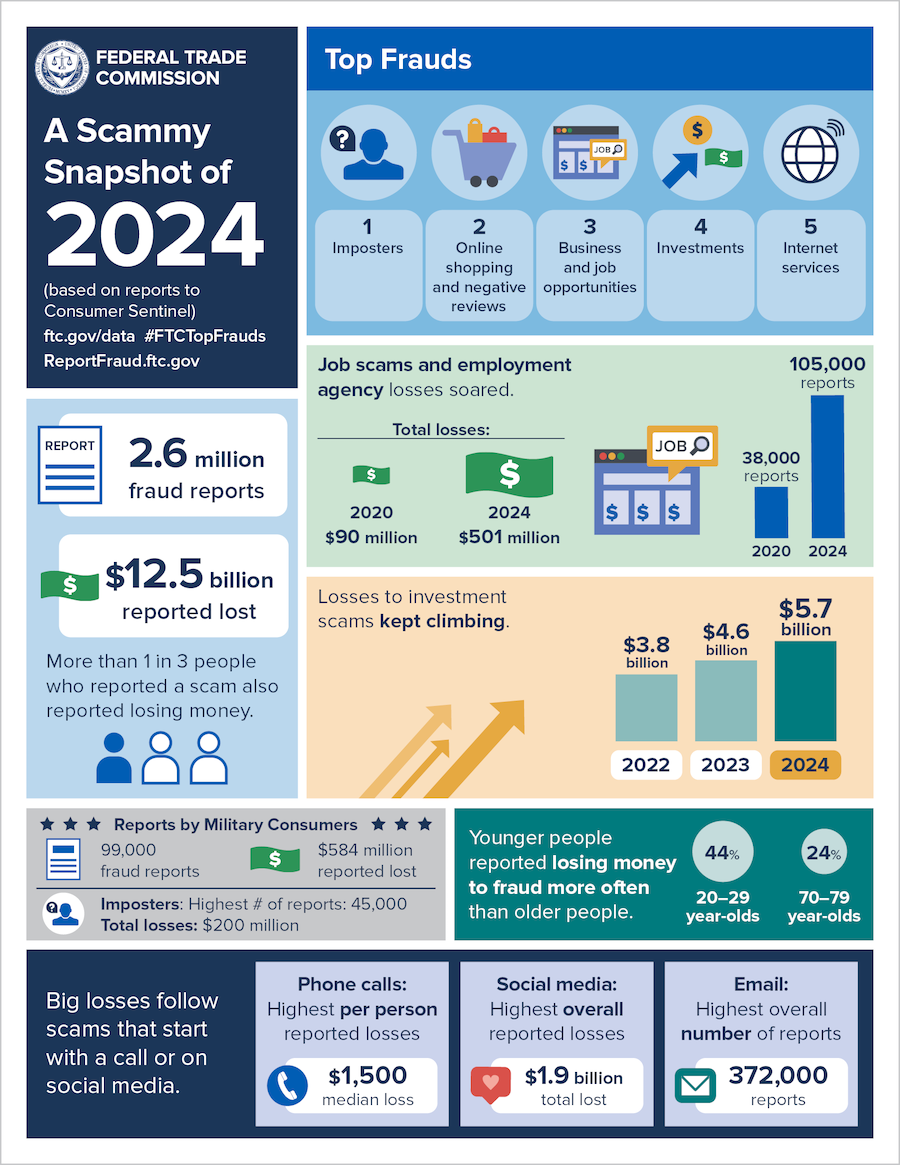
Record fraud losses: The FTC says Americans reported losses of over $12.5 billion to fraud in 2024. The number increased by 25% from the previous year despite the agency receiving about the same number of reports. Almost half of the losses were linked to investment scams.
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Andrew Morris, founder of security firm GreyNoise. Andrew talks about the major trends in mass internet scanning and exploitation, as per GreyNoise's yearly threat report.
Arrests, cybercrime, and threat intel
Garantex co-founder arrested in India: Indian authorities have arrested a Lithuanian national and the co-founder of the Moscow-based Garantex cryptocurrency exchange. Aleksej Besciokov was indicted in the US last week on money laundering charges for his role in running the platform. The FBI seized the platform last week for its role in laundering funds linked to dark web marketplaces and ransomware activity. Besciokov was detained while on vacation with his family on India's southern coast. [Additional coverage in KrebsOnSecurity]
FTC to reimburse some tech support scam victims: The US Federal Trade Commission is making more than $25.5 million available to consumers impacted by Restoro and Reimage tech support scams. Victims can file refund orders via the FTC website to receive their money back. The agency secured reimbursement funds after fining the two companies last year. Restoro and Reimage lured users to malicious websites that showed fake Microsoft pop-ups claiming computers were infected with malware. The companies then sold software to remove the alleged malware for fees ranging from $27 to $58.
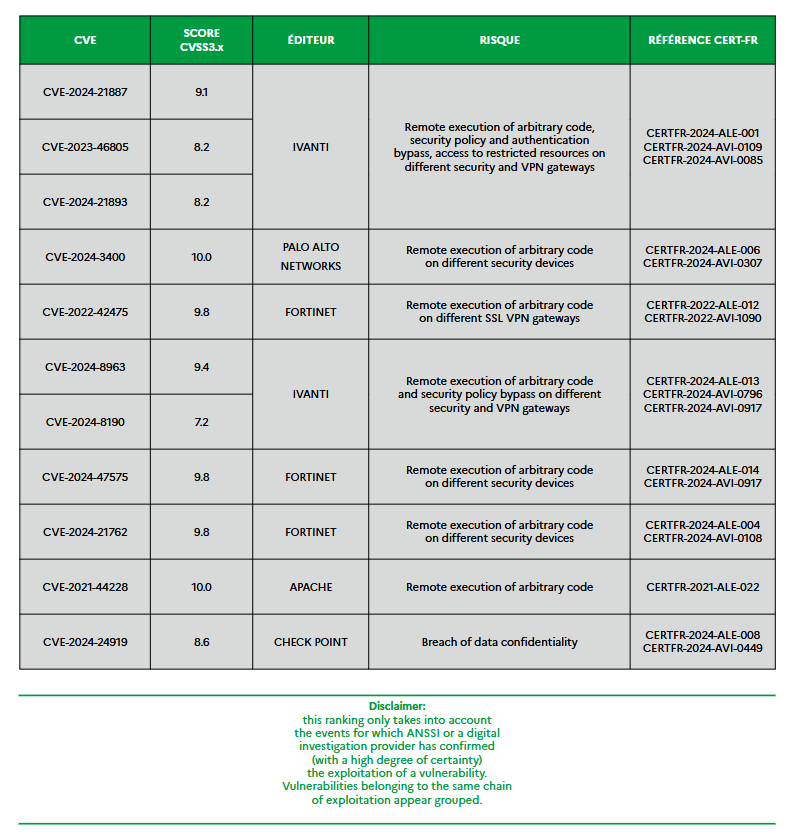
ANSSI yearly cyber threat report: ANSSI, France's cybersecurity agency, published its yearly cyber threat report for 2024. The primary trend observed last year was the rise in cyberattacks aimed at destabilizing services, particularly DDoS attacks conducted by hacktivist groups.
GitHub AI-generated repos spread malware: A threat actor has deployed a large number of malicious GitHub repositories for tools that infect users with malware. Security firm Trend Micro says descriptions for the repositories have been generated using AI tools. The malicious repositories infect users with the SmokeLoader, which then deploys the LummaStealer malware to exfil user credentials.
Belsen-ZeroSevenGroup connection: Threat intel firm KELA claims it found some connections between the Belsen and ZeroSevenGroup, two hacking groups claiming to be from Yemen.
Trump memecoin phishing: Cofense researchers spotted a malspam campaign using the Trump memecoin as a lure to infect themselves with the ConnectWise RAT.
Scammers target children while parents are sleeping: Russian security firm F6 (formerly FACCT) has spotted a social engineering campaign that targets children. The goal is to convince children to access a parent's bank account at night while they are sleeping and transfer funds to the attacker.
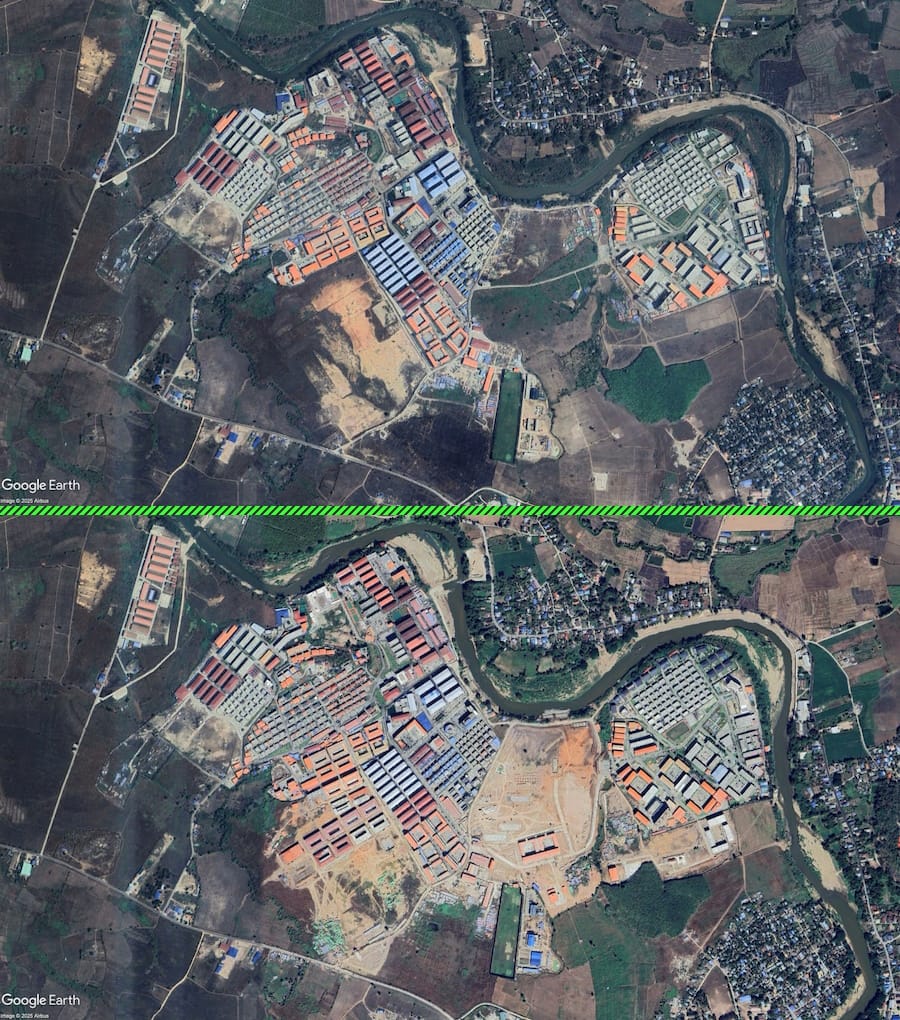
Myanmar scam compounds expanded last year: Companies linked to the Myanmar military and its militia forces have allegedly built two new cyber scam compounds in the country's Myawaddy region throughout 2024. According to a covert group of activists named Justice For Myanmar, six other compounds also received major expansions. The biggest beneficiary was the KK Park scam center, which built over 20 new structures between February and December last year. At least two scam compounds grew even after neighboring Thai authorities cut power to Myanmar border regions at the end of 2023.
Malware technical reports
Ballista botnet targets TP-Link routers: Cato Networks has discovered a new IoT botnet used for DDoS attacks. Named Ballista, the botnet is mostly comprised of TP-Link Archer routers. Ballista uses custom source code and doesn't appear to be based on Mirai and Mozi like most of today's IoT botnets. Ballista's author appears to be based in Italy.
Elysium ransomware: Netskope has published a technical report on Elysium, a new variant of the Ghost (Cring) ransomware.
DragonForce ransomware: Resecurity looks at DragonForce, a ransomware strain used against many attacks targeting Southeast Asian countries.
XCSSET: Microsoft has spotted a new version of XCSSET, a macOS malware strain that targets users by infecting Xcode projects.
DCRat: Kaspersky has spotted a new campaign spreading the old DCRat malware. This campaign uses YouTube videos advertising cheats and cracks to infect victims. The campaign targets Russian-speaking audiences.
MassJacker: A new malware operation has stolen over $300,000 worth of crypto assets from users using a novel clipboard hijacker. Named MassJacker, the malware secretly replaces cryptocurrency addresses in a user's operating system clipboard. Security firm CyberArk says it found over 778,000 wallets used by the malware, making it one of the biggest operations to date.
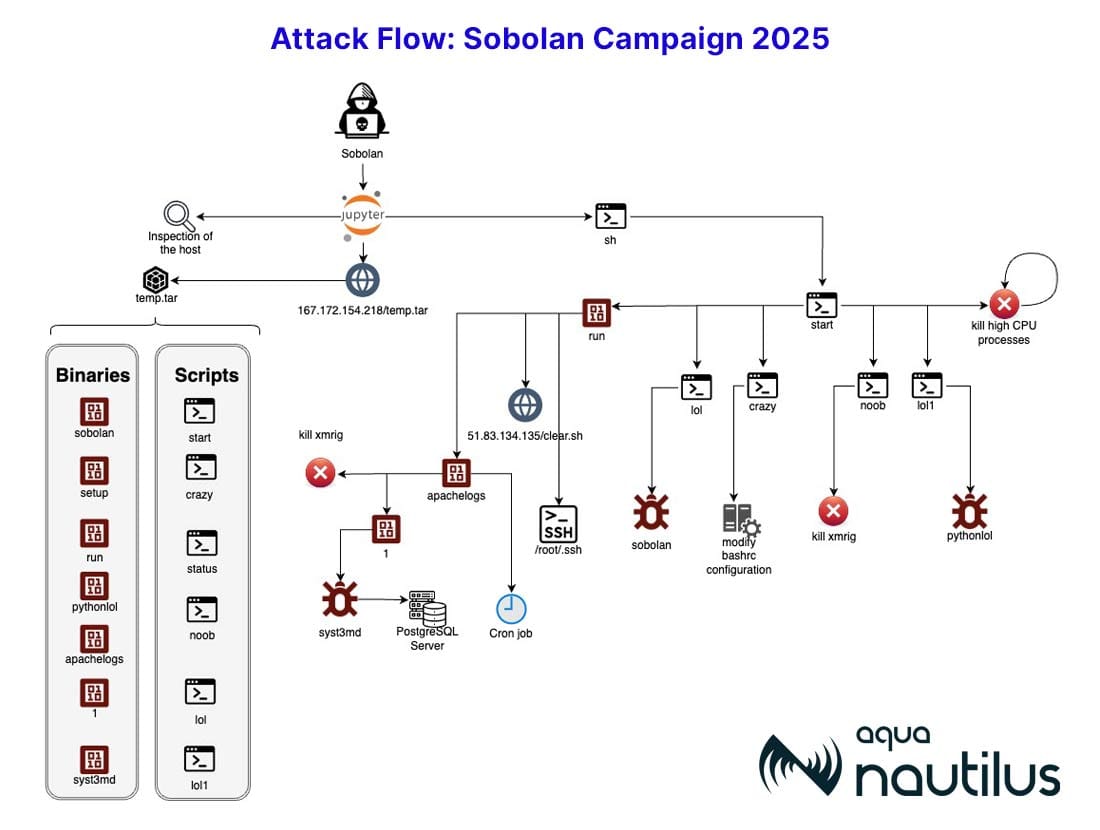
Sobolan: AquaSec has spotted a new crypto-mining botnet targeting Jupyter computing notebooks. The botnet is named Sobolan, the Romanian word for "rat."
Sponsor section
Attackers are automating exploitation at scale, targeting both new and old vulnerabilities — some before appearing in KEV. Our latest report breaks down which CVEs were exploited most in 2024, how ransomware groups are leveraging mass exploitation, and why real-time intelligence is critical.

APTs, cyber-espionage, and info-ops
Squid Werewolf: A North Korean APT group named Squid Werewolf is using the classic job interview and recruiting lures to phish employees at Russian organizations. The campaign marks the first time a North Korean APT has used this tactic outside of Western targets. The group is also known as APT37, Ricochet Chollima, ScarCruft, and Reaper.
APT37's RokRat: Security researcher Mohamed Ezat published a technical analysis of RokRat, a remote access trojan used by North Korean espionage group APT37.
SideWinder: Iranian APT group SideWinder is going after the maritime and nuclear sectors across multiple continents.
Blind Eagle: The Blind Eagle APT group has compromised over 1,600 victims inside Colombian institutions and government agencies. The campaign took place in November and December of last year and used an exploit similar to a zero-day (CVE-2024-43451) exploited by Russian hackers in Ukraine. Blind Eagle is a group with a history of exclusively targeting Latin American countries. Check Point described the group's large number of infections as surprising since the group usually carries out very targeted attacks.
Vulnerabilities, security research, and bug bounty
Voice cloning apps have no protections: Four of the six most popular voice cloning apps have no protections against abuse and allow threat actors to easily clone anyone's voice. A Consumer Reports study found that Speechify, Lovo, PlayHT, and Descript did not ensure that users had consent to reproduce another person's voice. Products like Descript and Resemble AI took some steps, but they could also be bypassed. The study's findings come as voice cloning scams are seeing a wider adoption across the fraud landscape.
KEV update: CISA has updated its KEV database with five vulnerabilities that are currently exploited in the wild. They include three Ivanti EPM vulnerabilities from 2024 and two VeraCode bugs.
Patch Tuesday: Yesterday was the March 2025 Patch Tuesday. We had security updates from Adobe, Apple, Microsoft, Chrome, SAP, Ivanti, Fortinet, Supermicro, NVIDIA, Zyxel, Schneider Electric, Siemens, and Zoom. The Android Project, AMD, Firefox, VMware, Cisco, Drupal, Moxa, DrayTek, Apache Camel, Jenkins, Elastic, D-Link, and QNAP released security updates last week as well.
Microsoft Patch Tuesday: This month, Microsoft patched 58 vulnerabilities, including six actively exploited zero-days.
- CVE-2025-24983 — Windows Win32 Kernel Subsystem Elevation of Privilege Vulnerability (via ESET)
- CVE-2025-24984 — Windows NTFS Information Disclosure Vulnerability
- CVE-2025-24985 — Windows Fast FAT File System Driver Remote Code Execution Vulnerability
- CVE-2025-24991 — Windows NTFS Information Disclosure Vulnerability
- CVE-2025-24993 — Windows NTFS Remote Code Execution Vulnerability
- CVE-2025-26633 — Microsoft Management Console Security Feature Bypass Vulnerability (via Trend Micro)
Apple zero-day: On top of that, Apple also patched a WebKit zero-day (CVE-2025-24201) in iOS and macOS. The company described the attacks as "extremely sophisticated."
Apache Camel write-up: Akamai has published a write-up and PoC for an Apache Camel filter bypass and injection vulnerability (CVE-2025-27636).
Infosec industry
Threat/trend reports: ANSSI, Check Point, Coalition, Fortinet, Kordia, Mimecast, and ScamWatch have recently published reports and summaries covering various infosec trends and industry threats.

Acquisition news: Forcepoint has acquired Getvisibility, a company specializing in AI-powered Data Security Posture Management (DSPM) and Data Detection and Response (DDR).
New tool—goLAPS: Orange's SensePost has released goLAPS, a tool to retrieve LAPS passwords from a domain.
New tool—Abuse.ch Hunting: The Abuse.ch malware repository launched a new feature, a new malware-hunting platform that aggregates data from seven platforms—URLhaus, MalwareBazaar, ThreatFox, YARAify, Sandnet, IPintel, and ProxyCheck.
New tool—RepoMan: Security researcher Andy Gill has open-sourced RepoMan, a tool to generate and populate GitHub repositories with random content and commit histories.
New tool—DS Viper: Security researcher Dhanush Arvind has released DS Viper, a tool to bypass Windows Defender's security mechanisms.
Disobey 2025 videos: Talks from the Disobey 2025 security conference, which took place in Helsinki in mid-February, are now available on YouTube.
Risky Business Podcasts
In this edition of Between Two, Nerds Tom Uren and The Grugq talk about what Europe should do given that US security guarantees are evaporating. Should Europe grow its cyber capabilities, what would it get out of it, and how should it go about doing it?
In this podcast, Tom Uren and Patrick Gray discuss how Starlink is providing an internet lifeline for scam compounds that have had their internet access cut by Thai authorities. Starlink has a very poor track record dealing with unauthorized use, but it is time for the company to develop the processes to keep on top of these problems.




