Risky Bulletin: It's probably not a good idea to pay RansomHub
In other news: Insight Partners discloses hack; OpenSSH patches MitM bug; Monero zero-day awaits patch.

This newsletter is brought to you by Rad Security. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
A recent CISA report and a series of tweets from Equinix threat intel analyst Will Thomas made me realize that quite a few infosec and adjacent cybersecurity experts are not fully aware that paying ransoms to a rising ransomware crew named RansomHub carries quite a high risk of breaking US sanctions.
The group launched in February 2024, when it started advertising its Ransomware-as-a-Service offering in underground hacking forums.
They got incredibly lucky because, just three weeks later, law enforcement agencies across the globe dismantled LockBit, which was, at the time, the largest RaaS platform on the market.
Throughout the year, many of LockBit's affiliates slowly found their way to RansomHub. By the end of the year, the platform rose to become 2024's most active ransomware operation, with its leak site listing more than 530 victims.

A CISA report published last August warned of the group's rise in popularity and increased operations.
But as Will Thomas noticed, RansomHub also appears to have attracted some unsavory customers, namely the members of a cybercrime cartel known as EvilCorp.
The group appears to have begun using RansomHub as a final payload around July of last year, dropping the ransomware on systems previously infected via the FakeUpdates (SocGholish) botnet—per reports from both Microsoft and Google.
Between late 2017 and 2018, EvilCorp previously developed and ran its own ransomware strains, such as BitPaymer, WastedLocker, Doppelpaymer, Hades, and PhoenixLocker. The group abandoned its own tools after it was sanctioned in the US in December 2019, sanctions that forced companies to flat-out refuse to pay ransoms, fearing they'd break sanctions and face the wrath of US authorities.
Since then, EvilCorp has been jumping between different RaaS platforms as part of a clever strategy of hiding their tracks and as a way to avoid scaring victims with possible sanctions violations.
With a fresh new coat of both US and UK sanctions issued in October last year, the risk of breaking sanctions in the case of a RansomHub infection is higher than ever.
Well... kinda! Depends if there's gonna be anyone left at the Treasury OFAC after DOGE teenagers have their way with the office.
But still! The TLDR here is that if you get hit by RansomHub, you better check with your legal team before even thinking of opening your wallet.
Risky Business Podcasts
Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
Insight Partners hack: Venture capital firm Insight Partners has suffered a security breach following a social engineering attack on January 16. The company says it's still investigating the incident but has already notified affected investors and portfolio companies. The firm is an investor in some of the world's largest companies, including cybersecurity firms Armis, Island, SentinelOne, and Wiz. [Additional coverage in Calcalist]
Cyberattack hits Ecuador parliament: Unidentified hackers have targeted Ecuador's parliament in two cyberattacks on Monday. The National Assembly says the attacks aimed to disrupt its systems and access sensitive data. The attacks took place a week after the country's general election. [Additional coverage in The Record]
ETAXI leak: Security researcher chum1ng0 has found a Google storage server leaking data from Hong Kong-based app ETaxi.
"The data in this google storage was 96,000 pieces of data, including files such as recordings, signatures, driver's licenses, cab photos, all of which were exposed without security." [h/t chum1ing0]
General tech and privacy
MSFT removes Location History: Microsoft is removing Location History, an API that was used in the past by Cortana to track a device's history.
Twitter blocks Signal links: fReE sPeEcH platform Twitter is now blocking links to secure messaging app Signal. [Additional coverage in Disruptionist]
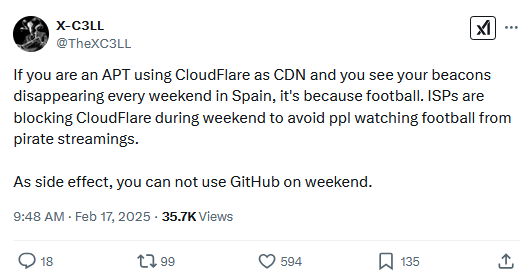
Cloudflare blocked in Spain on the weekends: Spanish internet service providers have started blocking access to some Cloudflare IP addresses on weekends. The blocks were put in place this month after Spain's soccer league won a lawsuit against Cloudflare for hosting pirate streaming sites. According to reports in local media, the blocks are indirectly blocking access to many legitimate websites, including GitHub, Reddit, and many private Spanish businesses. [Additional coverage in El Pais/English coverage in TorrentFreak]
Government, politics, and policy
Nothing in this edition.
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Jimmy Mesta, CTO and Co-Founder of Rad Security (formerly KSOC). Jimmy talks about how companies adopting new AI-based technologies may accidentally expose their infrastructure and data to new threats.
Arrests, cybercrime, and threat intel
Another Spanish spyware vendor shuts down: Spanish spyware maker Mollitiam Industries has filed for bankruptcy. The company was founded in 2018 and was known for developing two hacking tools named Invisible Man and NightCrawler. The company's only public scandal took place in 2020 when Colombian newspaper Semana accused the country's military of using Mollitiam tools to spy on its reporters. Mollitiam is the second Spanish spyware vendor to shut down this year after Barcelona-based Variston. [Additional coverage in Intelligence Online] [BlueSky thread from Lorenzo Franceschi-Bicchierai]
Bloody Wolf: Russian security firm BI.ZONE has published a report on Bloody Wolf, a financially motivated cybercrime group it saw targeting commercial entities in Kazakhstan last month.
Tax season campaigns: Sublime Security looks at the first signs of this year's tax season phishing campaigns—this one using the Tycoon 2FA phishing kit to deploy the AdWind RAT.
Bitcoin scams: Cloudflare has published a report on a number of scam campaigns targeting the owners of Bitcoin and other crypto-wallets.
Scammers arrested in Nigeria: Nigerian authorities have detained 47 suspected internet fraudsters in the city of Ekpoma.

Malware technical reports
StaryDobry: Kaspersky researchers have discovered a new crypto-mining operation named StaryDobry that targets Russian-speaking users seeking pirated and cracked video games. The campaign has been active since September of last year and is primarily distributed via torrent files. Most of the victims are located in Russia and Kaspersky believes the malware's author is a Russian-speaking actor.
XCSSET: Microsoft has spotted a new version of XCSSET, a macOS malware strain that targets users by infecting Xcode projects.
New Go-lang backdoor: Netskope has spotted a new Go-based backdoor in the wild. The company says the malware is being controlled via a Telegram bot and appears to be "of Russian origin."
Zhong Stealer: Mauro Eldritch has published a technical breakdown of a new infostealer known as Zhong Stealer. The malware has been used in campaigns targeting the fintech and cryptocurrency industries.
FrigidStealer: Proofpoint has identified two threat actors that are distributing a new MacOS malware called FrigidStealer. The campaigns started last month and are using fake browser updates to trick users into infecting themselves. The malware is an infostealer that can steal browser cookies and crypto-wallet-related files.
Vgod ransomware: CyFirma researchers have published a report on a new ransomware strain named Vgod.
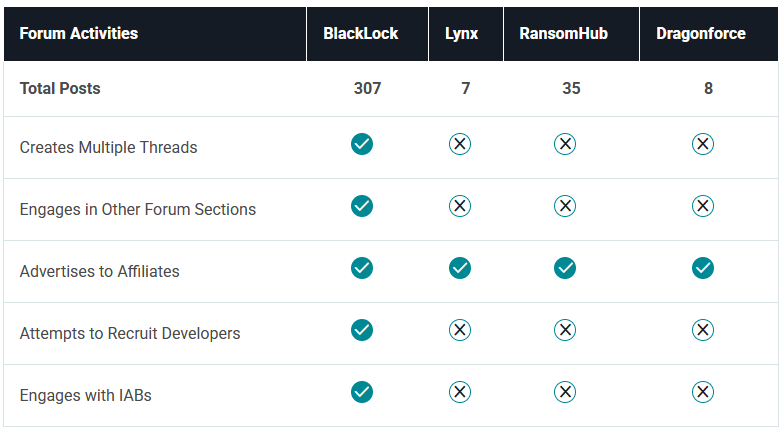
BlackLock (ElDorado) ransomware: ReliaQuest looks at BlackLock, a ransomware that appeared last March as ElDorado and rebranded to its current name in September. The table below also shows the gang is an avid poster on many cybercrime forums, with a huge number of posts compared to its rivals.

Sponsor section
Explore the future of cloud security with signatureless, behavior-based threat detection. In this video, we tackle the pressing question: "Is the cloud too noisy for behavioral detection to work?" We'll break down the limitations of signature-based methods and introduce runtime verification as a more effective solution for identifying threats in dynamic cloud environments.
APTs, cyber-espionage, and info-ops
Earth Preta (Mustang Panda): Trend Micro has spotted a Chinese APT abusing the Microsoft Application Virtualization Injector to bypass ESET security software. Also used the EA app to side-load its malware.
BeaverTail & InvisibleFerret: Slovenia's CERT has published a report on BeaverTail & InvisibleFerret, two malware samples used by North Korean hackers to target crypto developers.
DEEP#DRIVE: Securenoix looks at DEEP#DRIVE, a North Korean phishing campaign targeting South Korean businesses, government entities and cryptocurrency users.
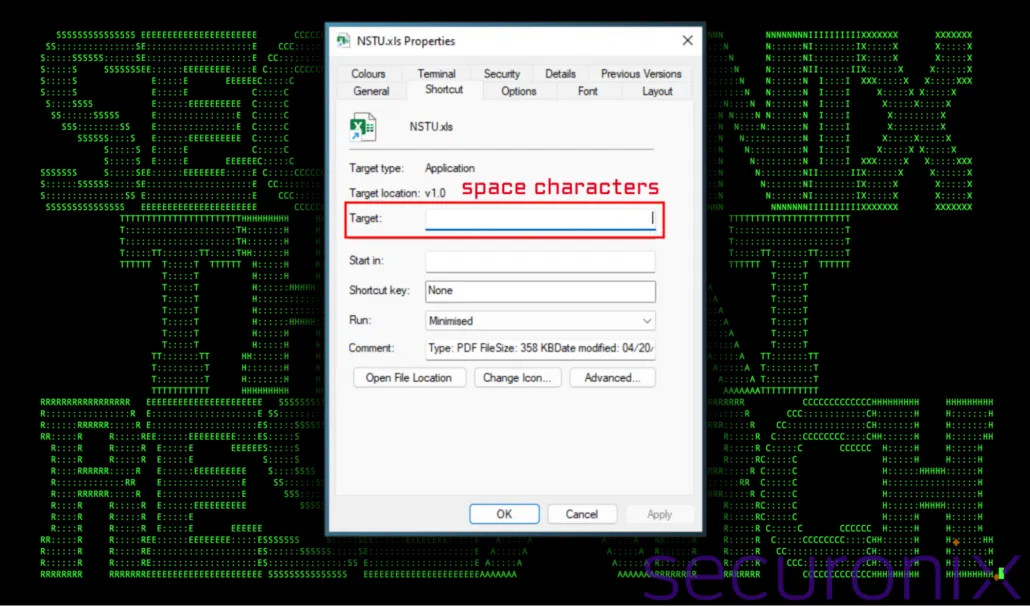
"The execution of PowerShell command line code was intentionally padded with over 100 space characters. As you can see [...], this completely removed any visible code in the Target field when viewing file properties."
Vulnerabilities, security research, and bug bounty
Monero zero-day: An anonymous security researcher has disclosed the details of a zero-day in the Monero blockchain. The vulnerability can be used to take down Monero nodes via denial-of-service attacks. The vulnerability allows for server memory exhaustion in Monero nodes that expose their RPC port. Attacks require low bandwidth and have already been tested in the wild.
OpenSSH vulnerabilities: The OpenSSH project has released a security update to fix two vulnerabilities that can be exploited to intercept traffic and take down servers. The denial of service vulnerability impacts all OpenSSH instances using the default configuration. The second vulnerability impacts all OpenSSH versions released over the past decade. It is a host impersonation issue that can be exploited via Man-in-the-Middle attacks and only impacts servers where the VerifyHostKeyDNS option is enabled. Security firm Qualys discovered and reported both bugs.
Default password in Hirsch building entry systems: Hirsch Enterphone building entry systems contain a hardcoded username and password for their web admin panel that can allow threat actors to unlock doors via the internet. The default creds are for an admin account named freedom that uses the password viscount. According to security researcher Eric Daigle, there are over 700 Hirsch Enterphone systems available over the internet, with most used by apartment blocks across the US and Canada. Hirsch says customers didn't follow its instructions to change the default passwords. Daigle says customers are never prompted to change the password during the setup process. Tracked as CVE-2025-26793, the vulnerability has a 10/10 severity score and is very likely to be exploited.
Infosec industry
Industry update: Dream Security, the company co-founded by former NSO Group CEO Shalev Hulio, has raised $100 million. The company does ICS security, so it seems Hulio has had enough of the spyware industry space. [Additional coverage in Globes] [h/t Vas Panagiotopoulos]
Industry rebrand: Russian cybersecurity firm FACCT has rebranded as F6 as part of a deal signed last year with Cyberus.
New tool—CaptainCredz: Security firm Synactiv has released CaptainCredz, a modular and discreet password-spraying tool.
New tool—Passkey Raider: Security firm Siam Thanat Hack has released Passkey Raider, a Burp Suite extension designed to facilitate comprehensive testing of Passkey systems.
New tool—WPProbe: Security researcher Valentin Lobstein has released WPProbe, a WordPress plugin scanner and enumeration tool.
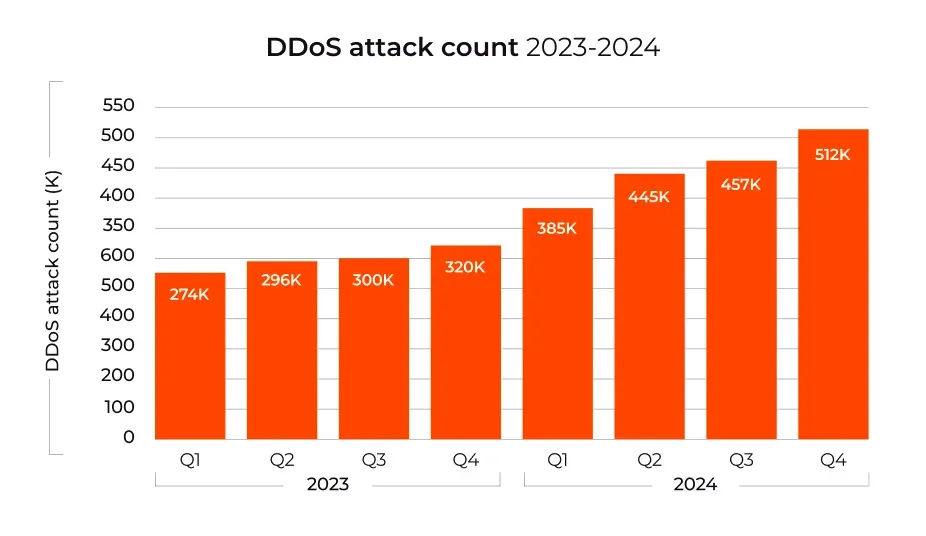
Threat/trend reports: Barracuda Networks, Gcore, TAG Infosphere, and ZeroFox have published reports and summaries covering various infosec trends and industry threats.

Risky Business Podcasts
In this podcast, Tom Uren and Patrick Gray talk about Apple's refusal to obey a UK government order to provide the capability to access encrypted iCloud data. It's the latest round in the ongoing government vs technology fights over warrant-proof encryption, and again, it looks like governments will lose.
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about the United State's Vulnerabilities Equities Program, which balances the need for intelligence collection with the need to protect the public. The government recently revealed that in 2023, it released 39 vulnerabilities, but what does this really tell us?




