Risky Bulletin: iOS 26 change deletes clues of old spyware infections
In other news: Starlink disables 2.5k scam compound terminals; Caribbean hospital still down 5 months after ransomware attack; Poland charges officials in Pegasus scandal.

This newsletter is brought to you by Dropzone. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
Apple's latest mobile operating system update, iOS 26, has made a change to a crucial log file that stores evidence of past spyware infections.
According to iPhone forensics and investigations firm iVerify, Apple is now rewriting the shutdown.log file after every device reboot, instead of appending new data at the end.
This is removing older log entries that contain indicators of compromise with spyware families such as NSO's Pegasus and Intellexa's Predator.
This is also problematic on devices infected with recent versions of the spyware, which wipes the shutdown.log file on its own.
"This meant that even a seemingly clean shutdown.log that began with evidence of a Pegasus sample was, in itself, an indicator of compromise," says Matthias Frielingsdorf, VP of Research at iVerify.
Now, with iOS 26 doing the wiping, it will be hard to find evidence of super-old Pegasus/Predator infections, and a clean shutdown.log file will be indistinguishable from normal iOS behavior.
"This automatic overwriting, while potentially intended for system hygiene or performance, effectively sanitizes the very forensic artifact that has been instrumental in identifying these sophisticated threats. It could hardly come at a worse time - spyware attacks have been a constant in the news and recent headlines show that high-power executives and celebrities, not just civil society, are being targeted."
For now, it is unclear if this was intended or just an unintended bug in the iOS 26 code. Regardless, the bug is actively wiping traces of past spyware attacks, as users upgrade to the new OS versions.
iVerify is asking users to delay updating to iOS 26 until this is clarified, or make forensic images of their devices before they do.
Risky Business Podcasts
The main Risky Business podcast is now on YouTube with video versions of our recent episodes. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
Hospital down for five months after ransomware attack: A hospital in the US Virgin Islands has been offline for nearly five months due to a ransomware attack. The Juan F. Luis Hospital has been slowly rebuilding its computer systems since April this year. Around 85% of staff can now access the hospital's EHR system again. CEO Darlene A. Baptiste estimated the hospital has been losing up to $800,000 a week in revenue due to the IT outage. [Additional coverage in The Virgin Islands Consortium]
Jewett-Cameron Trading ransomware: A ransomware group has stolen images of meetings and computer screens from outdoor product vendor Jewett-Cameron Trading. The attacker deployed file encryptors, taking down some of the network and blocking access to some business applications. In SEC filings, the company expects the incident to have a material impact next year. [Additional coverage in The Record]
Jaguar breach financial loss: The ransomware attack on Jaguar Land Rover is expected to become the UK's costliest cyberattack. The financial impact is expected to reach £1.9 billion. More than 5,000 UK organisations were affected by the attack, most of which were Jaguar parts suppliers.
Origin Energy breach: An employee of Origin Energy allegedly attempted to email himself the personal data of more than 700 employees. The company is a major electricity, gas, and internet provider in Australia. [Additional coverage in the Information Age] [h/t XOXO]
LG Uplus breach: South Korean mobile operator LG Uplus is investigating a possible security breach. The telco's hack was first disclosed in the Phrack hacker e-zine in August. The company was allegedly tipped off by the country's intelligence agency shortly after. The hackers allegedly stole data from almost 9,000 servers. The company initially said it found no evidence of a breach. It reopened the investigation this week after the South Korean government also confirmed a breach disclosed in the same Phrack article. [Additional coverage in the Korea Herald]
OYO breach: The OYO Hotels & Casino in Las Vegas was hacked in January this year. Just over 4,700 individuals had their data stolen.
Another injunction to stop ransomware leaks: An Indian court has granted an injunction to Generali Central Life Insurance to prevent individuals from using data that is likely to be leaked by the Medusa ransomware group. [Additional coverage in Medianama] [h/t DataBreaches.net]
Aeroflot hack aftermath: According to Russian flight industry insiders, the Aeroflot hack is having a predictable impact on the company's operations, with employees and pilots often cutting corners on safety protocols. Take this with a grain of salt, though. There's an informational war around anything Russia and Ukraine these days.
LA Metro signage defacements: Hackers have hijacked signage boards for LA Metro to show a fake suicide bomb warning. The message replaced bus wait times at multiple bus stops. The incident took place on Tuesday and was traced back to a third-party content management system called Papercast. Turkish hackers took credit for the incident. [Additional coverage in KTLA]
General tech and privacy
TikTok weakens user privacy: TikTok has updated its policies and added language to allow sharing user data with "regulatory authorities." The update expands the company's policy of only sharing user data with law enforcement agencies. TikTok has also removed the promise to notify users when their data has been requested by a government. According to Forbes, the new updates would make it easier for ICE to request user data without a court order, using a process called administrative subpoenas.
Meta Ray-Ban recording LED can be disabled: Hardware hackers have found a way to disable the recording LED on Meta's Ray-Ban smart glasses. At least one hardware shop is selling the service for $60. The procedure includes the super complex procedure of opening the glass case and disconnecting the LED. Glass owners can then record without alerting their targets. [Additional coverage in 404 Media]
Windows disables File Explorer previews for security: Microsoft has disabled File Explorer previews for files downloaded from the internet. The change was made for security reasons during this month's Patch Tuesday updates. Microsoft says the change will block a new attack that can steal NTLM password hashes via the File Explorer previews.
Atlas "logged out" mode: OpenAI CISO Dane Stuckey says the company's new ChatGPT Atlas web browser has a "logged out" mode to prevent prompt injection attacks from accessing sensitive data.
Apple removes Tea apps: Apple has removed the Tea and TeaOnHer apps from its App Store for privacy and moderation violations. The apps allowed women and men to report abusive dates, but were often used to slander, attack, and dox individuals. Both apps suffered data breaches this year. [Additional coverage in 404 Media]
Reddit sues four companies: Reddit has filed lawsuits against four companies that scraped its content from search results. The lawsuits targeted Perplexity, SerApi, Oxylabs, and AWMProxy. Reddit claims some of the scraped data was used to train Perplexity's AI products. Reddit was one of the first tech platforms to offer its user content to AI companies under a financial model. [Additional coverage in Reuters]
US state attorneys ramp up privacy enforcement: An EPIC report has found that US state and tribal AGs have brought and settled more than 1,200 privacy-related cases in the US between 2020 and 2024.
Another DBSC trial: Google will test its new Device Bound Session Credentials (DBSC) security feature in a second Chrome trial from October 2025 to February 2026.
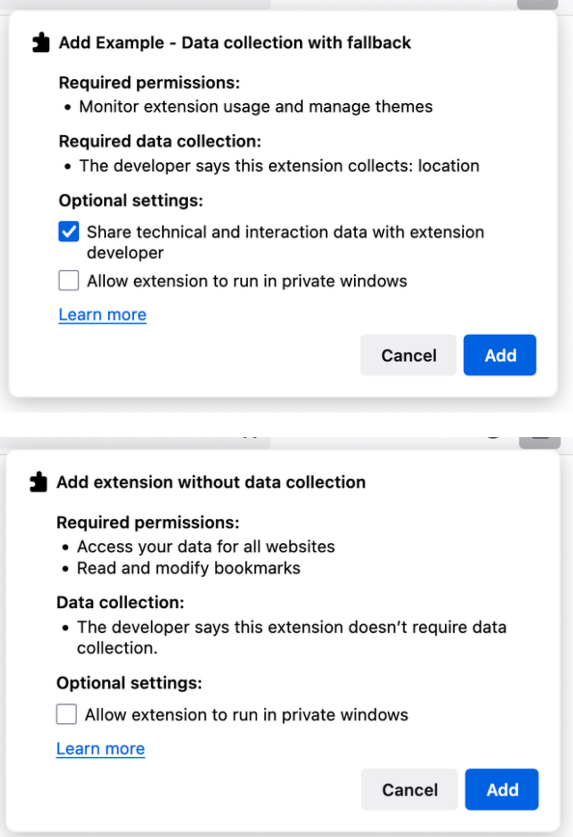
New Firefox data consent feature: Starting November 3, Mozilla will require all Firefox extensions to specifically declare in the manifest.json file if they collect and transmit personal data. This data will soon be integrated in Firefox permission prompts.
Government, politics, and policy
Russia clenches its fist around cybercrime: A Recorded Future report concludes that the Russian government's relation with its cybercrime ecosystem has "evolved from passive tolerance to active management."
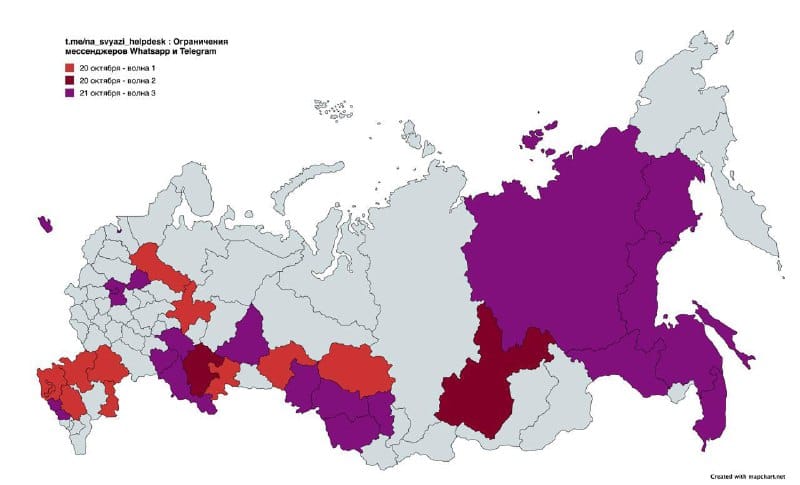
Russia restricts WhatsApp and Telegram again: The Russian government is blocking access to the WhatsApp and Telegram instant messaging services. Outages of IM services have been reported in 34 regions covering 40% of Russia's territory. The Russian government had already been restricting access to WhatsApp and Telegram voice and video calls since August. Officials said they're restricting access to the two services due to their use in extortions and the recruitment of saboteurs. [Additional coverage in The Moscow Times]
UN cybercrime treaty to be signed this weekend: A controversial UN cybercrime enforcement treaty that has been criticized for opening the door for authoritarian and human rights abuses is set to be signed this weekend in Hanoi, Vietnam.
EU rolls out digital driver licenses: The European Union will support digital driver's licenses for bloc members. The new digital license can be stored on a phone and may replace physical documents. It is set to roll out by 2030. The EU has also lowered age requirements for some licenses, such as those for driving buses and trucks.
South Korea to inspect 1,600 IT systems: The South Korean government will conduct cybersecurity audits of more than 1,600 IT networks. The audits will target government networks, as well as critical infrastructure operators. The measure comes in the aftermath of a major breach of government systems and the country's two largest telecom operators. [Additional coverage in Yonhap News]
Poland charges officials in spyware scandal: Polish authorities have charged two former government officials in the country's spyware scandal investigation. Authorities charged Michał Woś, a former deputy Justice minister, with abuse of power for purchasing the Pegasus spyware using funds meant to help the victims of crime. They also charged Daniel Karpeta, the country's former deputy anti-corruption chief, with sharing materials from the illegal Pegasus surveillance. A third official couldn't be charged because he's now a judge on the country's constitutional court. The Polish government under the previous leadership used Pegasus to spy on political opponents. [Additional coverage in Notes from Poland on the Woś charges, and the Karpeta charges]
Canada fined Cryptomus: Canada's financial regulator has fined the Cryptomus cryptocurrency exchange CAD$177 million for failing to follow anti-money laundering regulations. The company failed to submit suspicious transaction reports related to criminal activity. A KrebsOnSecurity report from December of last year found that Cryptomus was acting as a payments intermediary for Russian crypto platforms and cybercrime services. [Additional coverage in KrebsOnSecurity]
CISA shutters SED: CISA has shut down a division that worked to collaborate with the private sector and local governments to secure critical infrastructure. All 95 employees of the Stakeholder Engagement Division were laid off earlier this month at the start of the US government shutdown. The layoffs will go into effect at the start of December. The firings contradict statements from DHS Secretary Kristi Noem, who told Congress the agency will move away from election security to securing critical infrastructure. [Additional coverage in CybersecurityDive]
US loses cybersecurity protections: The US government is losing cybersecurity protections for the first time in its history. The CSC 2.0 project says almost a quarter of recommendations made by the Cyberspace Solarium Commission have lost their "fully implemented" status this year. CSC 2.0 members blame the regression on the loss of manpower at CISA and the rest of the US government.
Sponsor section
In this Risky Business sponsor interview, Tom Uren talks to Edward Wu, CEO and founder of Dropzone AI, about a study that measured how AI practically helps SOC analysts triage real-world problems. Analysts were faster, more accurate, and got less tired with AI assistance. Edward thinks the technology won't replace human analysts, but will speed their skill development.
Arrests, cybercrime, and threat intel
Trenchant exec charged: The US government has charged a former L3Harris executive with allegedly stealing and selling trade secrets to Russia. The suspect was identified as Peter Williams, a former general manager at Trenchant, an L3Harris division that develops hacking and surveillance tools. The DOJ says Williams received $1.3 million for selling seven trade secrets to a buyer in Russia. News of the arrest comes after a former Trenchant employee came forward this week, claiming he was unfairly fired following a leak of Trenchant hacking tools. [Additional coverage in TechCrunch]
Trump pardons Binance CEO: US President Donald Trump has pardoned Binance CEO Changpeng Zhao. Zhao pleaded guilty last year to money laundering after his company failed to crack down on the flow of hacked funds through its accounts. The pardon comes after Binance invested in the Trump family's World Liberty startup and USD1 cryptocurrency. [Additional coverage in the WSJ]
Devman RaaS: Analyst1 has published a profile on the Devman Ransomware-as-a-Service platform that launched in July, along with its modus operandi that includes rules like not targeting CIS countries and... Serbia, where the RaaS has many affiliates, apparently. Good to know, I guess!
Jingle Thief hacks gift card orgs: A hacking group is targeting and compromising organizations that issue gift cards. The group uses phishing and smishing to hack employees, gain access to work systems, and issue unauthorized gift cards that can be sold on gray markets. According to Palo Alto Networks, the group operates out of Morocco.
Belarus missing model linked to scam operations: A Belarusian model is believed to have been kidnapped, taken to a scam compound, and later killed. 26-year-old Vera Kravtsova has allegedly disappeared on October 4 after she traveled to Thailand for a modelling contract. Reports in Russian media claim the model was abducted to Myanmar, where she was forced to run scams on rich people. Thai tourism authorities denied the reports after Russian news outlets started circulating a document according to which she died of a heart attack and was cremated in Myanmar. [Additional coverage in The Independent]
Smishing Triad activity explosion: Palo Alto Networks has linked a recent explosion of toll and package delivery scams to a Chinese cybercrime group known as the Smishing Triad.
Starlink disables 2,500 scam compound terminals: SpaceX has suspended more than 2,500 Starlink terminals in the vicinity of known scam compounds in Myanmar. The terminals were shut down a day after a major Myanmar military raid on known compounds, where they also seized Starlink gear. The company's equipment has become ubiquitous at scam compounds after local authorities cut internet fiber to their locations. The US Congress Joint Economic Committee launched an investigation last month into Starlink's failure to disable terminals installed at scam compounds.
Flocks of Starlink satellite dishes soon began to cover many scam center roofs after Thailand cut its internet and power connections. Nearly 80 Starlink dishes are visible on one roof alone in AFP photographs of one of the biggest compounds, KK Park.
— E. Rosalie (@erosalie.infoepi.com) 2025-10-18T03:26:05.278Z
LuBian funds have moved: More than $1.8 billion in funds linked to the LuBian hack have been moved this week. The funds represent a small portion of the $14.5 billion stolen from the Chinese cryptomining pool in December 2020. Some of those funds have also been linked to the operators of Cambodian scam compounds. [Additional coverage in The Block]
Universe Browser installs apps behind your back: The Universe Browser has been caught installing hidden apps behind its users' backs. Security firm InfoBlox was unable to confirm any malicious activity from the apps, but is warning the public anyway. The browser has often been offered for download from the websites of online casinos. Its "features" include disabling access to right-click menus, settings, developer tools, and even some security features.
The hyperscale DDoS attack problem: Nokia's network security division, Deepfield, has published a blog about the rise in hyperscale DDoS attacks that have gotten so big they affect infrastructure past their intended target.
NuGet malware: Socket Security has spotted a malicious package on the NuGet package repo for .NET libraries. The package is designed to steal crypto wallet keys.
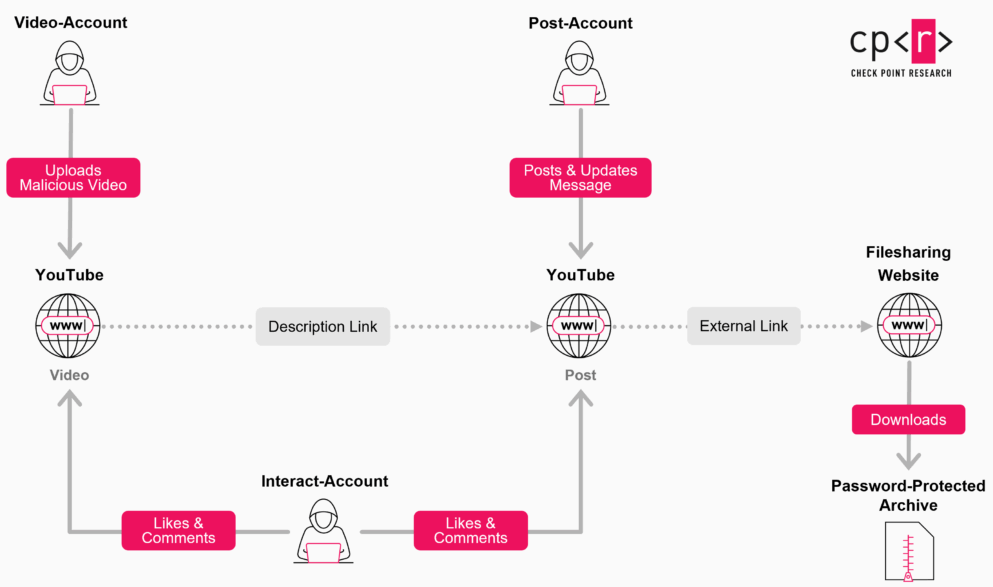
YouTube Ghost Network: A malicious network of YouTube accounts is publishing and promoting videos that lead to malware downloads. The network has been active since 2021 and has published more than 3,000 malicious videos. It leverages hacked accounts and usually replaces their content with malicious videos. Videos are usually centered around gaming cheats and software cracks and aim to infect users with infostealers. Check Point says the network tripled its output this year.
RedTiger abuse: Netskope researchers spotted cybercrime crews abusing the RedTiger Python-based red-team tool for malicious purposes.
Perplexity campaigns: BforeAI has found 13 malicious domains spreading malware-laced versions of Perplexity's Comet AI-based browser.
Malicious "job" domains: The DNSFilter security team has spotted more than 8,700 malicious domains containing the word "job," as well as another 1,100+ domains with the word "careers."
LockBit returns: Check Point says it's seeing new attacks with version 5.0 of the LockBit ransomware. Work on this version has been underway for quite some time.
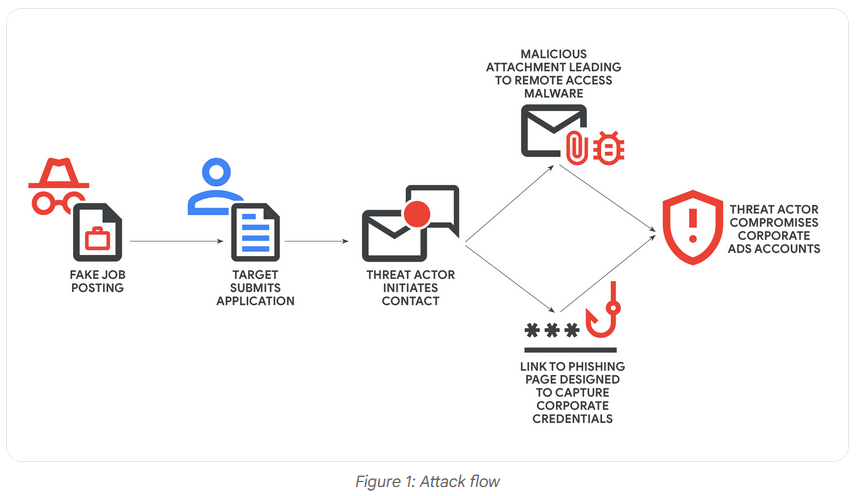
UNC6229 profile: Google's Mandiant team has published a profile on UNC6229, a Vietnamese threat actor using fake job lures to lead victims to malware.
"GTIG assesses with high confidence that this activity is conducted by a cluster of financially motivated individuals located in Vietnam. The shared TTPs and infrastructure across multiple incidents suggest a collaborative environment where actors likely exchange tools and successful techniques on private forums."
Malware technical reports
TOLLBOOTH: Elastic's security team has published a report on TOLLBOOTH, a malicious IIS module planted on hacked servers, designed to act as a backdoor and help attackers use the servers for SEO poisoning/cloaking attacks. On the same day, but separately, Harfang Labs published a report on HijackServer, which is the company's name for the same malware.
Qilin runs Linux variant on Windows: Trend Micro has spotted the Agenda (Qilin) ransomware group deploying a Linux variant of their ransomware on Windows systems... and managing to execute it successfully, bypass EDRs, and encrypt the network. Uhm... I'm confused!
Valley RAT: Cyderes has spotted a fake Chrome installer distributing the Valley RAT. The campaign specifically targeted users in China, which is weird since Chrome is not the main browser there.
Remcos RAT: CyberProof researchers have spotted new phishing and social engineering campaigns spreading the antique Remcos RAT. Yes, that garbage is still alive.
New Python-based RAT: Netskope has discovered a new Python-based RAT spreading in the Minecraft communities.
Baohuo: Dr.Web has discovered modified versions of the Telegram app that contained a malware strain named Baohuo. The malware collects the user's private data, from credentials to chat history. Baoguo also hides connections by hackers to the user's account in the app's sessions section.
Sponsor section
In this sponsored product demo, Dropzone founder and CEO Edward Wu walks Risky Business podcast host Patrick Gray through the company's AI SOC analyst.
APTs, cyber-espionage, and info-ops
China's Zingdoor: Symantec researchers have published a report on Zingdoor, a new backdoor deployed via Toolshell exploitation by a Chinese espionage group. Victims include telecoms in the Middle East and government agencies in Africa and South America.
Premier Pass-as-a-Service: Trend Micro says two Chinese APTs, Earth Estries and Earth Naga, appear to be collaborating for initial access and subsequent operations.
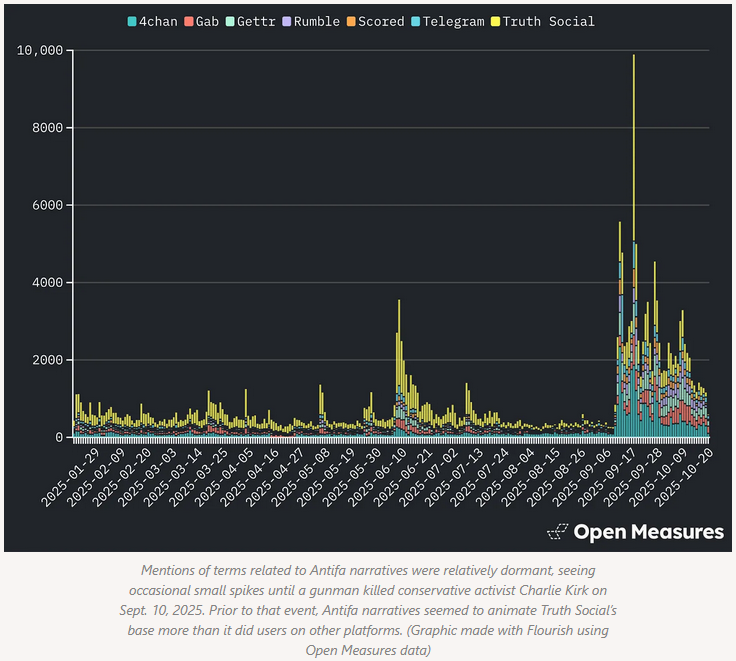
Antifa info-ops: OpenMeasures looks at info-ops campaigns that resurrected the topic of Antifa shortly after Charlie Kirk's assassination. Info-ops focusing on Antifa had been dormant since the last time Trump was in office.
Operation DreamJob goes after drones: North Korean state-sponsored hackers are going after the European drone and UAV industry. Employees at several companies have received fake job offers leading to malware-laced files. ESET has linked the activity to a cluster known as Operation DreamJob. Attacks against drone and UAV companies align with recent changes in North Korea's military program.
Targets are attracted to a lucrative job offer and lured to execute trojanized PDF readers or VNC tools. This social engineering technique seems to have been working well for several years, suggesting many employees still have insufficient awareness of this tactic. 2/9
— ESET Research (@esetresearch.bsky.social) 2025-10-23T04:10:11.403Z
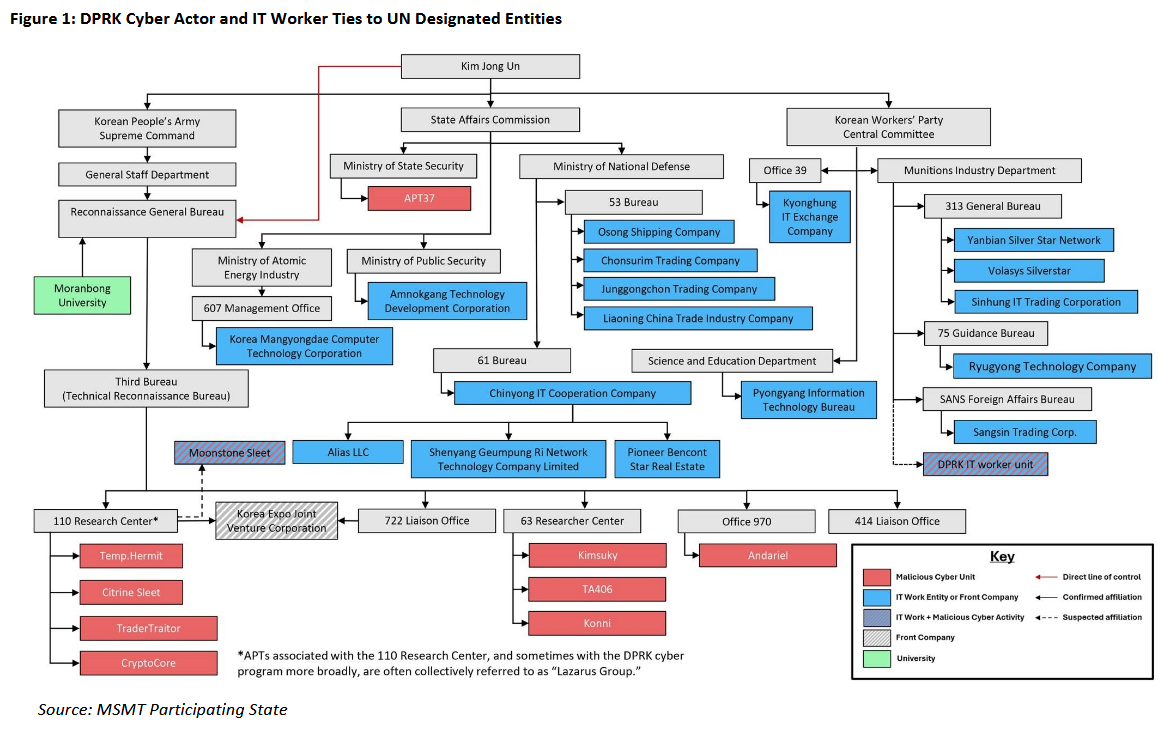
DPRK hacking report: The Multilateral Sanctions Monitoring Team (MSMT), an informal group of 11 countries set up to monitor North Korea's sanctions compliance, has published a 138-page report on the regime's efforts to evade sanctions. The report covers its crypto platform hacks, remote IT working schemes, and money laundering operations.
Cavalry Werewolf: Picus Security has published a report on the suspected Kazakh APT Cavalry Werewolf (YoroTrooper, SturgeonPhisher, Silent Lynx, Comrade Saiga, Tomiris, and ShadowSilk) and its campaigns targeting Russia's government and critical infrastructure. Also check out this BI.ZONE report on the same campaign.
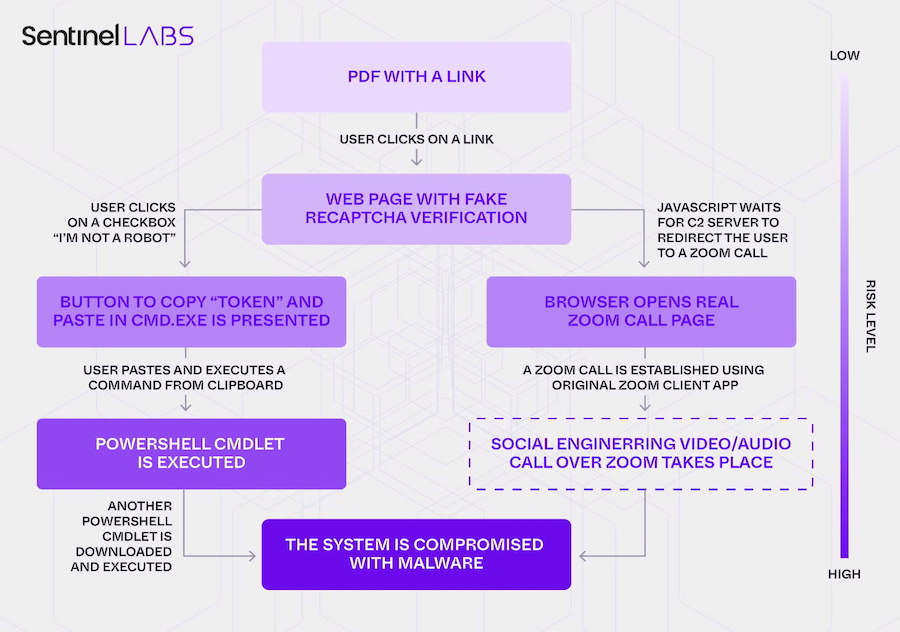
PhantomCaptcha targets Ukraine: A suspected Russian cyber-espionage operation is targeting the Ukrainian government and international NGOs involved in war relief efforts. The campaign uses fake CAPTCHAs (ClickFix) to deploy the WebSocket RAT. The campaign was set up over six months, but was only active for a day. SentinelOne says the campaign overlaps with known ColdRiver APT infrastructure.
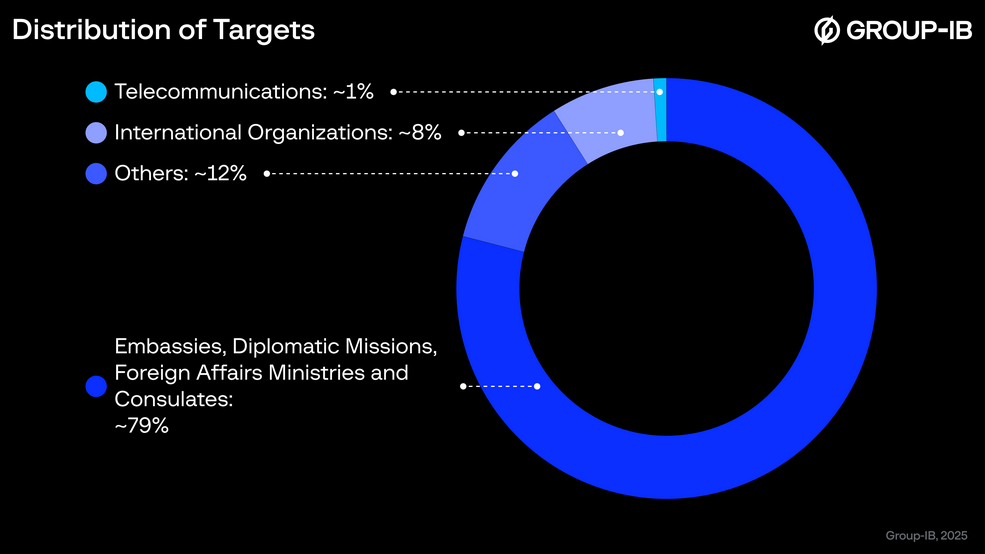
MuddyWater's Phoenix backdoor: A new Iranian cyber-espionage operation has targeted more than 100 government entities across the MENA region. Group-IB has linked the attacks to an Iranian APT named MuddyWater. The attacks deployed a new backdoor named Phoenix, as well as infostealers and legitimate remote monitoring and management tools.
Vulnerabilities, security research, and bug bounty
Oracle CPU: The quarterly Oracle security updates are out, with patches for 374 vulnerabilities. Qualys and Tenable have breakdowns of the fixes.
TP-Link security updates: TP-Link has patched two+two security flaws in its Omada gateway that allowed remote unauthenticated command injection. The last two were found by Forescout.
GitLab security updates: GitLab has released security updates to patch seven vulnerabilities in its main product.
BIND security updates: ISC has published three security updates for the BIND DNS resolver. [Additional coverage in ArsTechnica]
SessionReaper enters exploitation: Hackers are now exploiting a Magento bug known as SessionReaper (CVE-2025-54236). The bug was patched in September and allows remote attackers to take over online stores. Sansec says only 38% of Magento stores have patched, a number barely larger than when the patch came out.
Lanscope zero-day: Threat actors are exploiting a zero-day vulnerability in the on-premises servers of the Motex Lanscope Endpoint Manager. A patch was released earlier this week, on Monday, after the vendor received reports of attacks. Tracked as CVE-2025-61932, the vulnerability lets attackers take over the Lanscope client installed on customer systems using malicious crafted packets. CISA has also added the vulnerability to its KEV database.
More AI browser prompt injection bugs: The Brave browser security team has found new prompt injection attacks in Comet and Fellou, two AI-powered browsers.
Opera Neon prompt injection: On that note, Opera has also patched a prompt injection of its own in its new Neon AI-based browser.
AI sidebar spoofing: SquareX warns that threat actors can spoof sidebars for AI assistants inside browser interfaces to steal data or trick users into downloading and running malware. Affected browsers where SquareX successfully tested the attack include Perplexity's Comet and OpenAI's Atlas.
Shadow Escape attack: Operant researchers have published details on Shadow Escape, a zero-click attack on MCP servers.
Smithery path traversal bug: A misconfiguration in an AI hosting platform could have exposed credentials for more than 3,000 MCP servers. GitGuardian researchers have found a path traversal vulnerability that let them get admin credentials for the Smithery platform. The credentials could have later been used to retrieve all customer information. The issue was traced back to a misconfiguration in a Docker build image.
94 vulns in VS Code clones: Cursor and Windsurf, two IDEs cloned from Microsoft's VS Code editor, have failed to integrate patches for 94 Chromium-related bugs, per Ox Security.
Cloudflare CIRCL vulnerability: Botanica Software has found a vulnerability (CVE-2025-8556) in Cloudflare's CIRCL encryption library, specifically in the implementation of the FourQ elliptic curve.
"We reported the issues through Cloudflare's HackerOne bug bounty plan in March 2025, and subsequently contacted Cloudflare directly, after having received a lukewarm and laconic response from the HackerOne triage team. Once the team at Cloudflare stepped in the issues were appropriately acknowledged and fixed."
Netty vulnerability: Depthfirst researchers published a write-up on a vulnerability in Netty's SMTP codec tracked as CVE-2025-59419.
NTLM EoP: CrowdStrike has published a technical dive into CVE-2025-54918, a vulnerability patched in September that can allow attackers to elevate NTLM hash privileges in AD environments.
Azure Fabric abuse: NCC researchers have published research on how attackers could backdoor or steal data from Azure Fabric instances.
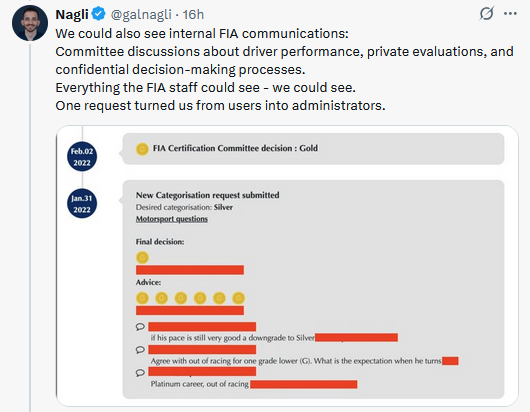
FIA portal exposes F1 driver data: The personal details of all F1 and other drivers could have been stolen via an FIA web portal. The site allowed any user to assign themselves an admin role. The portal stored information on drivers applying for F1 license categorization and internal FIA correspondence. The motorsport body fixed the vulnerability within a week.
Infosec industry
Threat/trend reports: Ernst&Young, ExtraHop, Gen Digital, MacStadium, Nokia, Red Canary, Trellix, and Trustwave have recently published reports and summaries covering various threats and infosec industry trends.
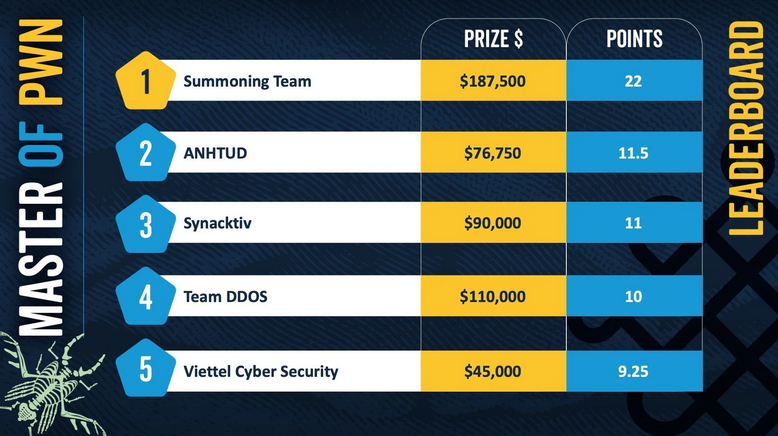
Pwn2Own Ireland results: The Summoning Team has won this year's edition of the Pwn2Own Ireland hacking contest. The results from days one, two, and three are linked. This year, researchers won $1,024,750 for 73 unique bugs.
AI for defense opinion: Google's John Hultquist has published an opinion piece on the need to adopt more AI for cyber defense, which is a pretty common take I've heard all year, too, since that's where AI shines the best in cybersecurity right now.
New tool—Wonka: Telefonica security engineer David Manuel Herrera Rodríguez has open-sourced Wonka, a Windows tool that extracts Kerberos tickets from the Local Security Authority (LSA) cache.
Ekoparty 2024 streams: Live streams from the Ekoparty 2025 security conference are available on YouTube. All the talks are in Spanish.
DevSecCon 2025 videos: Talks from Snyk's DevSecCon 2025 security conference, which took place this week, are available on YouTube.
Risky Business podcasts
In this edition of Seriously Risky Business, Tom Uren and Amberleigh Jack talk about how America can better use its private sector to scale up offensive cyber activities, including espionage and disruption operations. Involving it to tackle ransomware and cryptocurrency scammers makes a lot of sense.
In this edition of Between Two Nerds, Tom Uren and The Grugq talk to Joe Devanny, senior lecturer from King's College London, all about India's missing cyber power. It has the ingredients to become a cyber superpower, but so far, it hasn't shown the motivation.




