Risky Bulletin: India orders IM apps to link user accounts to a SIM card
In other news: India mandates cyber app on all new smartphones; Coupang breach impacts two-thirds of all South Koreans; evil twin hacker sentenced to seven years in prison.

Risky Business Podcasts
The main Risky Business podcast is now on YouTube with video versions of our recent episodes. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
OpenAI security incident: OpenAI says some customer data was exposed during a breach at Mixpanel, a third-party analytics provider.
French Football Federation breach: The French Football Federation says hackers gained access to a software panel used by French football clubs to manage their licenses.
West London ransomware attack: A ransomware attack on a shared IT provider has brought down the networks of three city councils in West London—Royal Borough of Kensington and Chelsea, London Borough of Hammersmith and Fulham, and Westminster City Council. [MyLondon]
Brsk breach: British IPS Brsk says hackers have stolen the personal details of more than 230,000 customers. [ISP Review]
Coupang breach: Coupang, South Korea's largest retailer, has been hacked and the data of 33.7 million customers was stolen. The hackers allegedly emailed the company and threatened to disclose the breach publicly unless it improves its cybersecurity practices. There was no ransom demand. Weird, I know! [Reuters//The Korea Herald]
EU website hacked for SEO farming: A dev server for the European Commission's europa.eu domain was compromised and used for blackhat SEO-related redirects.
Yearn Finance crypto-heist: The Yearn Finance DeFi platform was hacked for $3 million worth of crypto assets. As usual, the funds were immediately laundered through Tornado Cash. [Tron Weekly]
Upbit crypto-heist: Hackers exploited a bug in the wallet system of South Korean cryptocurrency exchange Upbit to steal over $37 million worth of Solana tokens. [CoinDesk]
General tech and privacy
Entra blocks external script injection: Microsoft will block external script injection during the Entra ID authentication process. This will be enforced starting October 2026. This will most impact browser extensions that work to enhance or scan the Entra ID authentication procedures.
Airport operator fined €10mil: Spain's data protection agency has fined airport operator AENA €10 million over operating a biometric boarding system. [Biometric Update//AEPD decision PDF]
Vanity Fair fined over cookies: France's data protection agency has fined Vanity Fair €750,000 for placing cookies on user devices without permission.
GrapheneOS leaves France: GrapheneOS will migrate away from OVH cloud infrastructure due to a new French law that would mandate breaking its encryption.
Chrome DevTools MCP server: Something that I didn't notice in September was Google's release of an MCP server for the Chrome DevTools feature.
Government, politics, and policy
EU introduces weaker Chat Control: The EU has passed a version of its controversial Chat Control regulation that leaves CSAM message scanning as a "voluntary" measure for tech companies. The original text, much harsher, required mandatory scanning. [Euractiv]
EU in favor of a <16 social media ban: The European Parliament has called for the introduction of a social media ban for children under the age of 16. If passed, the new legislation would ban social media networks from accepting accounts for children absent a parent's explicit consent. [Euronews]
AI Fraud Deterrence Act: Two US lawmakers have pushed a bill, the AI Fraud Deterrence Act, to increase the maximum penalties for using AI to commit fraud.
Cyber Deterrence and Response Act: Congressman August Pfluger, R-Texas, introduced a bill this week named the Cyber Deterrence and Response Act that creates a unified federal process to identify, attribute, and sanction state-sponsored cyber actors. [NextGov]
India mandates cyber app: India has ordered smartphone makers to pre-install the government's Sanchar Saathi app on all smartphones sold in the country. The app is available for Android and iOS and allows users to report fraud and spam. [TechCrunch]
India orders SIM binding for IM apps: The Indian government has ordered all online messaging apps to implement SIM binding, a process that links all user accounts to a SIM card. [The Economic Times]
Russia formally restricts WhatsApp: While some restrictions on WhatsApp calls have been in effect since August, the country's communications watchdog has formally confirmed the blocks last week. Meanwhile, Russian lawmakers hinted that a full ban is coming soon.
China releases new (cyber) arms control paper: The Chinese government has published a new white paper on how the state will address arms control in the "new era." The document also covers cyberspace and cyberattacks, and is China's first document of its kind in the past two decades.
"China opposes attempts to "own the domain" from a position of strength and carry out large-scale, systemic and indiscriminate theft and cyberattacks around the globe. It condemns a certain country's wanton targeting of other nations' critical infrastructure in cyberattacks, which places global critical infrastructure at grave risk. It rejects the introduction of ideological confrontation and military alliance into cyberspace under the guise of "cybersecurity cooperation", including the deployment of cyber forces in the Asia-Pacific region, and the proliferation of cyber weapons and systems, which may increase risks of miscalculation and escalation."
China has released its new white paper on arms control today - the first comprehensive document on this topic in 20 years. Chinese: www.fmprc.gov.cn/web/wjdt_674... English: www.fmprc.gov.cn/mfa_eng/xw/w... Analysis forthcoming...
— Gesine Weber (@gesineweber.bsky.social) 2025-11-27T09:40:01.663Z
Risky Business podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq wonder whether it is possible to deter states from cyber espionage with doxxing and other disruption measures.
Arrests, cybercrime, and threat intel
Evil twin hacker sentenced to 7 years: An Australian man was sentenced to seven years in prison for setting up fake WiFi networks to steal personal data. Michael Clapsis, 43, from Perth, ran fake free WiFi access points at the Perth, Melbourne, and Adelaide airports, during multiple domestic flights, and at work. He used evil twin attacks to redirect users to phishing pages and capture credentials. He then accessed personal accounts and collected intimate photos and videos of women. Clapsis also hacked his employer and accessed emails between his boss and police after his arrest. [ABC]
CCTV hackers detained in South Korea: South Korean authorities have arrested four individuals who hacked more than 120,000 security cameras, downloaded footage, and sold the data on adult-sharing portals. [ChosunBiz]
Cryptomixer takedown: Europol has seized the domain of the Cryptomixer cryptocurrency mixing service. Yes! Original name, I know! Officials seized €25 million worth of assets and said the site allegedly helped criminal groups launder over €1.3 billion worth of assets.

Russian hacker arrested in Poland: Polish authorities have arrested a Russian national in Krakow who allegedly hacked Polish companies. [Reuters]
2025 losses to bank impersonation fraud: The FBI says Americans lost more than $262 million to threat actors impersonating banks and other financial institutions.
Scam compound raid: Cambodian officials have raided a cyber scam compound in the country's capital Phnom Penh and arrested 28 suspects. Of the 28 individuals detained, 27 are Vietnamese nationals and one is Cambodian.
Scam compounds move: Cyber scam compounds in Cambodia are migrating from the country's western border with Thailand to the east, to locations near the Vietnamese border. [Cyber Scam Monitor]
Bloody Wolf profile: Group-IB has published a profile on Bloody Wolf, an e-crime group targeting countries in Central Asia with commodity RATs.
DeerStealer interview: Threat intelligence analyst g0njxa has published an interview with the developer of the XFILES (DeerStealer) infostealer.
Most teen hackers stop in their 20s: According to a study from the Dutch government, most teen hackers abandon their cybercrime careers and choices by their twenties.
Rey profile: KrebsOnSecurity has published a profile on Rey, a Jordanian teen and the admin of the Scattered Lapsus$ Hunters group. Rey is allegedly named Saif Al-Din Khader, 16, from Amman, Jordan.
SLH goes after Zendesk instances: On the same note, ReliaQuest says that the same Scattered Lapsus$ Hunters group is now going after Zendesk servers in an effort to pilfer corporate data they can use for ransom operations.
ShadyPanda spreads malicious Chrome extensions: Koi Security has published a profile of ShadyPanda, a threat actor that has been spreading malware-laced Chrome extensions on the official Web Store for the past seven years. Some of the extensions also targeted Edge users.
Hackers go after emergency systems: The FCC says hackers hijacked Barix studio-transmitter link (STL) equipment to broadcast obscene materials and fake alerts via state emergency systems.
Malware is SmartTube app: A threat actor has breached and pushed a malicious update to SmartTube, an app typically used on Android-based smart TVs.
RomCom hops on SocGolish: Arctic Wolf has spotted the RomCom malware operation using SocGolish to deploy its payloads. These attacks targeted American companies supporting Ukraine's war efforts.
AIRedScam campaign: UV Cyber looks at a campaign using boobytrapped AI tools shared on GitHub to deliver SmartLoader and other infostealers.
Campaigns targeting Russia's aerospace industry: Intrinsec looks at a campaign targeting Russia's aerospace sector. While no formal attribution has been made, the security firm thinks the attacks might be Ukrainian hacktivist groups.
Salty2FA activity collapses: ANY.RUN says activity from the Salty2FA phishing service collapsed in October and payloads now seem to overlap with the IOCs of another service named Tycoon2FA.
No Sha1-Hulud on PyPI: The Python Software Foundation says there was no trace of the Sha1-Hulud worm on the PyPI repository but warned that the worm had likely stolen PyPI account credentials from the infected systems of npm developers, credentials that are likely to be used at a later stage.
New form of crypto fraud: Individuals who placed bets on the evolution of the Russian-Ukrainian war on the Polymarket crypto gambling site are circulating maps of fake Russian advances in the hopes of cashing in. [404 Media]
"We lied about the Ukraine war, not to make one side look stronger but to steal fake money from an even-more-immoral-than-usual betting shop" was not on my bingo card.
— Caspia Marina 🏳️⚧️ (@caspiamarina.bsky.social) 2025-12-02T02:52:03.186Z
Malware technical reports
GlassWorm returns: SecureAnnex says the GlassWorm self-replicating worm that targets VSCode extensions has had a resurgence, similar to the resurgence of the Sha1-Hulud npm worm last week.
CastleLoader & CastleRAT: DarkTrace researchers look at CastleLoader & CastleRAT, two new MaaS offerings that launched in March this year and have already been used in the wild in campaigns that leveraged GitHub repos to host boobytrapped software.
ShadowV2 DDoS botnet: Fortinet has spotted a new DDoS-for-hire botnet named ShadowV2. The botnet runs on top of a Go-based RAT and a Python-based spreader and primarily targets cloud-based systems for infection. Fortinet says the botnet ran test attacks during a recent AWS outage. DarkTrace has also published a report on the same botnet in September.
Qilin's MSP hack in South Korea: A Qilin RaaS affiliate has hacked a South Korean MSP and used the access for attacks against the country's financial companies.
Xillen Stealer: DarkTrace has published a report on two recent versions of the Xillen Stealer. The infostealer has an AI feature to detect high-value accounts on an infected system, such as cryptocurrency wallets, enterprise accounts, and banking info. It also claims to use a novel module to evade AI-based or behavior-based detection systems, such as EDRs and sandboxes.
Arkanix Stealer: G Data looks at Arkanix Stealer, a new infostealer advertised on Discord.
SetcodeRat: QiAnXin has discovered SetcodeRat, a new Telegram-based remote access trojan used in attacks against Chinese users.
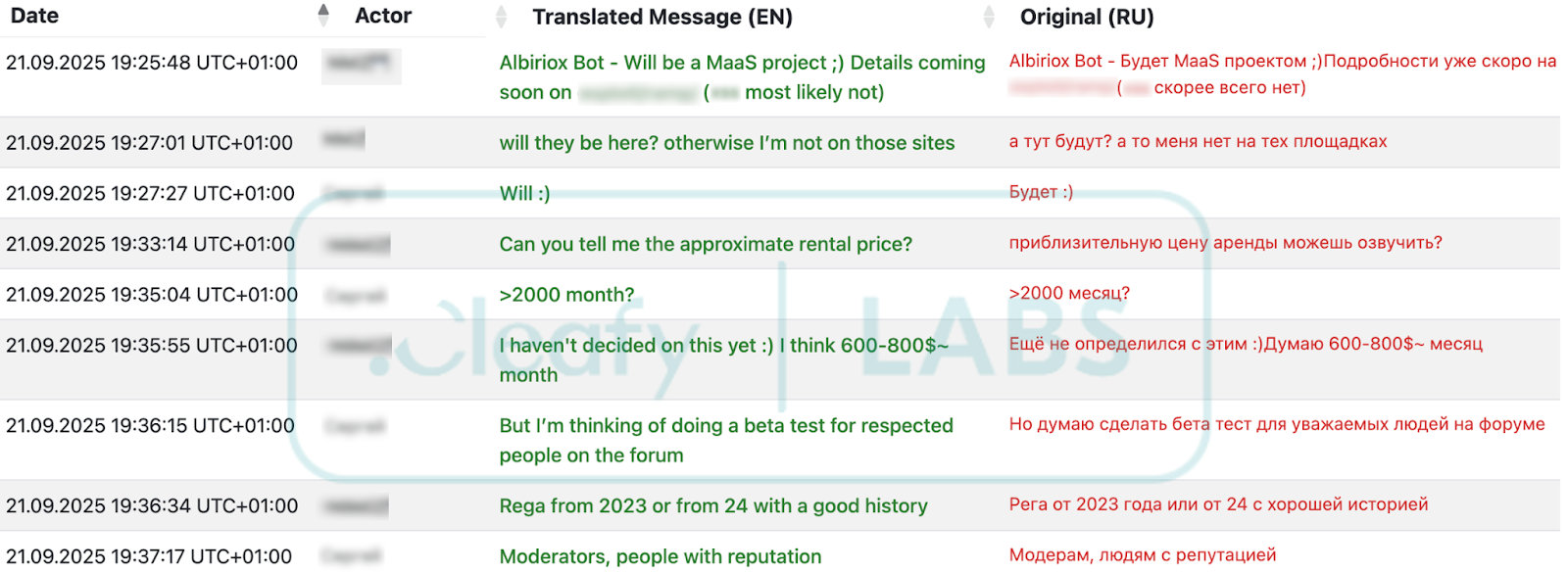
Albiriox RAT: Cleafy has uncovered a new Android RAT named Albiriox and offered for sale through a MaaS model.
Risky Business podcasts
In this edition of Seriously Risky Business, Tom Uren and Amberleigh Jack talk about Anthropic’s discovery of an “AI-orchestrated” cyber espionage campaign.
APTs, cyber-espionage, and info-ops
APT36: Indian security firm CyFirma looks at Python-based ELF payloads used by Pakistani APT Transparent Tribe (APT36) in attacks against the Linux environments of the Indian government.
"The analysis reveals a coordinated cyber-espionage campaign attributed to APT36, utilizing weaponized .desktop files to target BOSS Linux environments within Indian government entities. These files are engineered to appear as legitimate documents while covertly communicating with malicious infrastructure."
Tomiris: The Tomiris APT group has now adopted the Havoc and AdaptixC2 red team frameworks for its operations.
Primitive Bear: Synaptic Systems has published a report on Primitive Bear's abuse of a WinRAR vulnerability (CVE-2025-6218) for its operations.
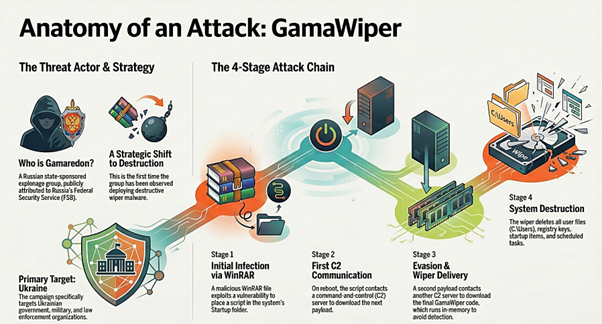
New Russian wiper hits Ukraine: ClearSky has spotted the Gamaredon APT deploying the GamaWiper in data-wiping attacks at Ukrainian organizations. The attacks leveraged a WinRAR vulnerability tracked as CVE-2025-80880.
Water Gamayun: The Water Gamayun APT has exploited the MSC EvilTwin (CVE-2025-26633) vulnerability in attacks this year. The group is a suspected Russian APT.
CopyCop expands AI disinfo globally: Russian disinformation group CopyCop is using AI tools to expand its fake news and disinformation empire to a global reach, after having spent the last two years targeting European countries ahead of their elections. Its new AI-driven news factory now includes more than 300 new domains.
Anti-Georgian disinformation: DFRLab has spotted multiple English, French, and Polish websites linked to sanctioned Russian propaganda networks spreading disinformation about Georgia's pro-Western demonstrations. Many of the news articles are linked to organizations run by Russian intelligence services. This revelation comes during reports that pro-Kremlin authorities used WWI toxins on protesters.
MuddyWater: Iranian cyber-espionage group MuddyWater has been seen targeting organizations in Israel and Egypt. The novelty here is their new MuddyViper backdoor and their adoption of CNG, the next-generation Windows cryptographic API.
DredSoftLabs linked to WageMole APT: Threat researcher Mees van Wickeren looks at DredSoftLabs, a front company for WageMole, a North Korean state-sponsored operation designed to plant remote IT workers at Western companies.
KimJongRAT returns: EST Security has spotted a new version of the old KimJongRAT.
Contagious Interview npm attacks: Socket Security looks at a North Korean group's use of malicious npm libraries to deliver the OtterCookie infostealer.
"Since we last reported on this campaign, it has added at least 197 more malicious npm packages and over 31,000 additional downloads, with state-sponsored threat actors targeting blockchain and Web3 developers through fake job interviews and 'test assignments'."
Contagious Interview VSCode attacks: The same operation also used malware that leveraged the VSCode Tasks feature to maintain persistence on infected hosts. [OpenSourceMalware]
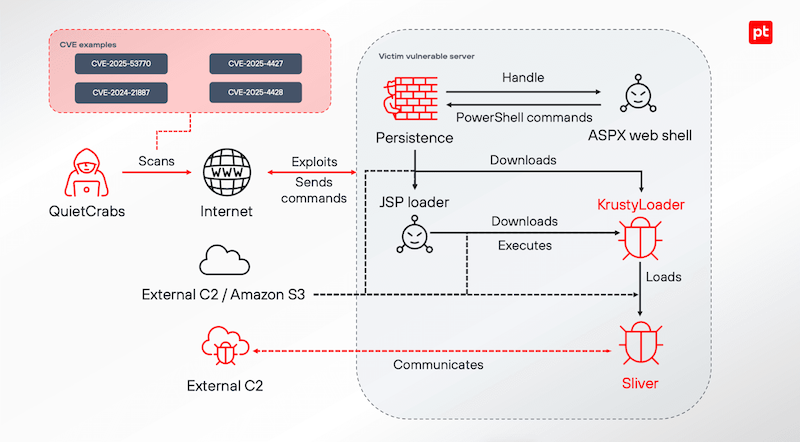
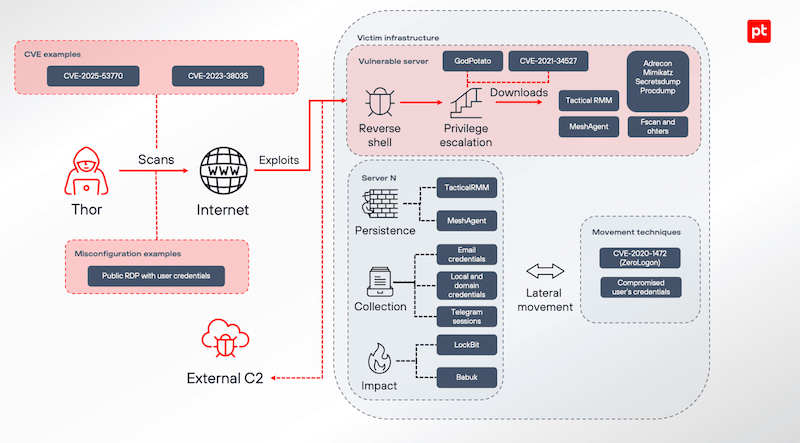
QuietCrabs and Thor: Positive Technologies has published a report on QuietCrabs, a suspected Chinese APT also tracked as UTA0178 and UNC5221. The group is known for targeting edge networking gear and deploying the KrustyLoader backdoor. The report also reveals the first details about Thor, a second threat actor they found while investigating QuietCrabs. This second group appears to be somewhat involved in ransomware attacks.
Vulnerabilities, security research, and bug bounty
OpenPLC exploitation: CISA says threat actors are exploiting a 2021 XSS vulnerability in the OpenPLC ScadaBR HMI visual editor.
GitLab servers leak secrets, just like GitHub: Truffle Security scanned 5.6 million public GitLab repositories and found more than 17,000 valid secrets and tokens.
Tyler juror website vulnerabilities: Tyler Technologies has fixed a vulnerability in websites used to manage juror information for individuals selected for jury duty in various US states. [TechCrunch]
MSFT Teams security bypass: According to new Ontinue research, Microsoft Teams enterprise users lose all their employer's Defender for Office365 protections (Safe Links, ZAP, malware scanning) when they accept invites to external attacker-controlled tenants. The attack is possible because all Teams users can receive invites from any user, by default, unless an organization specifically takes steps to block external invites.
HashJack attack: Cato Networks has discovered HashJack, an indirect prompt injection technique that conceals malicious instructions after the # in legitimate URLs. This attack works when AI agents have to parse links inside documents or emails.
ARX anonymization flaws: Academics from George Mason University have found a vulnerability in ARX, a data anonymization tool used to mask patient data for HIPAA compliance. The vulnerability can be used to leak some personal details from ARX-anonymized data.
Important security updates: Android (includes two zero-days), Kubernetes, Splunk, Synology.
Infosec industry
Threat/trend reports: CERT-FR, the Dutch government, Kaspersky, Intel471, and Semperis have recently published reports and summaries covering various threats and infosec industry trends.
New tool—Cyber Action Toolkit: The UK's cybersecurity agency has released Cyber Action Toolkit, an easy to follow guide to help SMBs protect their IT resources.
New tool—Fairy-Law: Orange's security team has released Fairy-Law, a tool to compromise or disable EDR security solutions.
GreHack 2025 streams: Live streams from the GreHack 2025 security conference, which took place over the weekend, are available on YouTube.
CornCon videos: Talks from the CornCon 2025 security conference, which took place in October, are available on YouTube.
KubeCon videos: Talks from the KubeCon 2025 conference, which took place last month, are available on YouTube.




