Risky Bulletin: Improperly patched bug exploited again in Fortinet firewalls
In other news: Hackers go after security testing environments; Jordan used Cellebrite against activists; new Cisco and SmarterMail zero-days.

This newsletter is brought to you by SpecterOps, the experts in Attack Path Management. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
Threat actors have mounted a new wave of attacks against Fortinet's FortiGate firewalls using a vulnerability that was improperly patched last month.
Security firm Arctic Wolf says hackers are bypassing Single Sign-On (SSO) authentication using generic usernames, creating their own admin account for future access, and stealing the device's current configuration file.
Since the attacks were first being reported online, Fortinet has confirmed in private emails to some customers that the attackers have found a new way to exploit CVE-2025-59718.
The company patched the bug in December but now says the vulnerability has persisted even in the newer firmware.
The original vulnerability resided in a feature that allowed admins to connect and authenticate on their FortiGate devices using a FortiCloud account, via SSO.
The bug allowed attackers to craft a custom SAML message that granted them admin access on the device without actually having to authenticate.
It now appears attackers have either found another way to craft that message or to bypass Fortinet's December patch to achieve the same result.
The same advice from last month also stands. Disabling the SSO login feature on the device is the easiest way to prevent exploitation. This feature is not enabled by default on Fortinet devices, so most of them are somewhat safe from attacks. I say somewhat because there's a trillion Fortinet bugs, so if this doesn't get you, something else will.
New wave of suspected 0day attacks hitting FortiGate firewalls via malicious SSO logins. Attackers exfil configs, create persistence accounts (secadmin, itadmin, backup…), grant VPN access – all in seconds.
— Costin Raiu (@craiu) January 22, 2026
Very similar to Dec 2025 campaign tied to FortiCloud SSO bypasses…
Risky Business Podcasts
The main Risky Business podcast is now on YouTube with video versions of our recent episodes. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
NZ to investigate Manage My Health app: New Zealand's privacy commissioner has launched an investigation into the Manage My Health app over a recent security breach. The app exposed the medical records of more than 120,000 people at the end of last year. Officials plan to investigate if the app had proper security measures in place.
SagaEVM crypto-heist: The SagaEVM platform has halted all transactions after a hacker stole $6.8 million worth of tokens. Despite lots of rumors online, the source of the hack has not been disclosed. [Cryptopolitan]
UStrive fixes data exposure: US online mentoring site UStrive has fixed a bug in its platform that exposed the personal data of its customers. [TechCrunch]
General tech and privacy
Mozilla has record financial year: Mozilla reported a massive $680 million in revenue for 2024, its best financial result so far. Most of the funds, around $498 million, came from search deals, and the most of it came from Google. The org's expenditures were $590 million. [Soren Hentzschel]
AI agents are incompatible with E2EE apps: Signal president Meredith Whittaker warned that AI agents embedded in secure messaging apps are a major weak point since they need access to extensive sensitive data and are easy to hijack via simple prompt injection attacks. [Bloomberg]
Grok's "impressive" stats: Twitter's Grok AI agent generated an estimated 3 million sexualized images including 23,000 of children. According to the Center for Countering Digital Hate, the image generation feature saw abuse after Elon Musk promoted its undressing capabilities. The social network is currently under investigation in several countries over the feature.
W Social rises as Twitter alternative: European tech leaders are investing in W Social, an European alternative to Twitter based out of Sweden. [Bilanz]
Ads are coming to Threads: Meta is bringing online ads to its Threads social media app after testing them with US and Japanese users last year.
Fine for mysterious company: France's privacy watchdog has fined an unnamed company €3.5 million for using tracking cookies without permission, allowing users to set weak passwords, using the weak SHA-256 hashing algorithm, and sharing customer data with social media companies for targeting purposes.
Government, politics, and policy
China accuses Taiwan of hacks: The Chinese government says it investigated more than 4,000 cyberattacks last year that originated from Taiwan. The attacks sought to steal classified information from Chinese companies across multiple sectors. Some of the operations were allegedly carried out by Taiwanese cyber troops.
Kazakhstan to tighten data breach laws: Kazakhstan will introduce criminal liability for individuals who leak large quantities of personal data. The new law also comes with increased fines for companies that fail to protect user data. The fines will triple from roughly $17,000 to around $42,500. [The Times of Central Asia]
Jordan used Cellebrite phone-hacking tools: The Jordanian government has used Cellebrite phone-hacking and forensics tools to extract data from the devices of Jordanian activists. Investigators from CitizenLab and the OCCRP have found dozens of victims dating back to 2020. The victims had devices hacked while they were arrested and interrogated by police. Some of the recent victims were activists who organized protests in support of Palestinians in Gaza.
Iran uses crypto to stabilize economy: Elliptic has spotted the Iranian central bank using cryptocurrency in an attempt to stabilize its rial fiat currency and the economy.
GDPR fines total: EU privacy watchdogs have issued fines worth more than €1.2 billion for GDPR infractions last year.
Spain dismisses NSO case: Spain has closed a probe into the use of the Pegasus spyware against government officials. The country's high court closed the probe after Israel refused to answer five cooperation requests. Spanish officials started the probe in 2022 after the spyware was used to hack Prime Minister Pedro Sánchez and Defence Minister Margarita Robles. [The Record]
Dutch want to avoid US clouds for govt data: The Parliament has urged the upcoming cabinet to block the Dutch DigiD service from storing data on US clouds. The DigiD service allows Dutch citizens to authenticate on official government sites for tax, educational, pension, and healthcare purposes. The Netherlands has been one of the first EU countries to push for its government data and systems to be moved away from US clouds. [NL Times]
Sponsor section
In this Risky Business sponsor interview, Tom Uren talks to Justin Kohler, Chief Product Officer at SpecterOps, about how attack paths exist in the seams between different identity or permissions management domains.
Arrests, cybercrime, and threat intel
LastPass warns of phishing campaign: Password manager LastPass has notified and warned users of an ongoing phishing campaign seeking to capture their master passwords.
ClickFix adopts LotL: New research from Expel looks at how threat actors using the ClickFix technique are adopting living-of-the-land techniques to hide the malicious code they trick users into executing.
Attackers compromise test environments: Hacking groups are compromising security testing applications to breach and move laterally inside corporate environments. According to Pentera Labs, several Fortune 500 companies and security vendors have been breached using this technique. Targeted apps included the likes of OWASP Juice Shop, DVWA, and Hackazon.
Malicious PyPI package deploys cryptominer: Socket Security has spotted a malicious PyPI package posing as SymPy to deploy crypto-miners on victim's systems.
r1z profile: KELA has published a profile of r1z, a Jordanian national who pleaded guilty in the US to working as an initial access broker for ransomware gangs.
LATAM fake loan scams: Group-IB looks at an online fraud operation that tricks victims into surrendering their personal data for fake loan offers. The campaign is primarily active in Peru, but also targets other LATAM countries.
INC happy ending: Security firm Cyber Centaurs has helped a dozen victims recover from ransomware attacks after infiltrating the backup server of the INC ransom group. The company mapped the backup infrastructure and retrieved the victims' original unencrypted data. The INC group started operations in 2023 and has listed more than 100 victims on its dark web leak site.
Massive Zendesk spam: A massive spam campaign is abusing Zendesk servers. The attacks exploit Zendesk servers that allow anyone to create support tickets without registration. So far, the messages have been generic and did not contain malware or malicious links. [BleepingComputer]
hey if you're seeing zendesk tickets made by my email no you're not! they dont seem to verify email addresses at all so it's just spam from Not Me glhf whoever has to figure that out and @zendesk fix ur shit
— Wham! ✨ (@wamwoowam.co.uk) 2026-01-19T23:46:33.986Z
it fucking rules that zendesk set up an open spam relay and just goes "yeah sorry, it's on our customers to turn that off and our software is just diarrhea dogshit that can be used to spam forever" email security@zendesk.com and yell at them about it support.zendesk.com/hc/en-us/art...
— X ΘΔ (@xkeeper.net) 2026-01-19T22:52:24.991Z
Malware technical reports
HEURRemoteAdmin.GoToResolve.gen: Point Wild looks at a PUA sample associated with the GoTo Resolve Unattended Access application, a legitimate remote administration tool.
Osiris ransomware: Symantec looks at Osiris, a new ransomware family that launched operations in November of last year. The ransomware has been dormant for a few weeks now, though.
Android malware uses ML to click on ads: An Android trojan uses machine learning to load ads inside a hidden browser window and click on the relevant advert element. The Android Phantom trojan has been found in at least six apps offered through the Xiaomi store. It has also been distributed through two third-party app stores and Discord and Telegram channels.
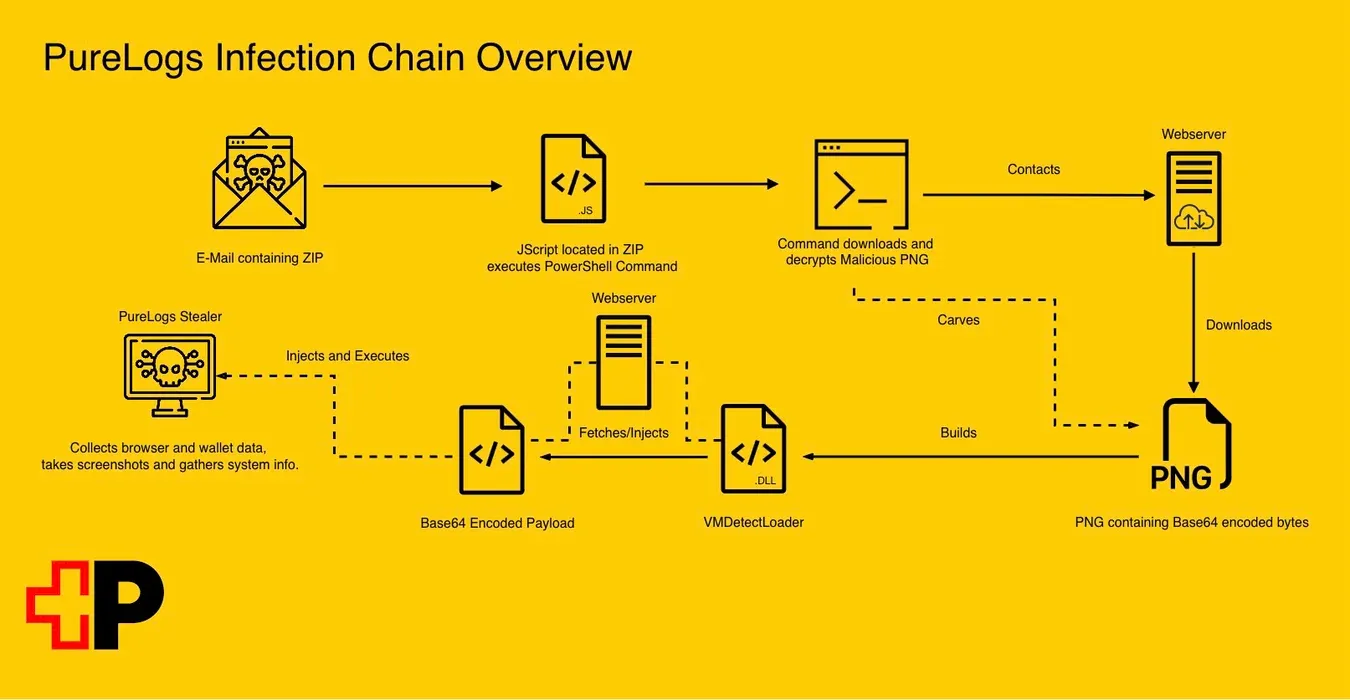
PureLogs: The cybersecurity team at the Swiss Post service has published an analysis of the PureLogs infostealer.
Sponsor section
Justin Kohler, VP of Product at SpecterOps, shows how BloodHound Enterprise can be used to find and fix Active Directory (mis)configurations that could let attackers easily own your entire enterprise.
APTs, cyber-espionage, and info-ops
Three APTs sitting in a tree: The Rostelecom security team has found at least three APT groups on the network of a Russian organization—Erudite Mogwai (Space Pirates), Obstinate Mogwai, and GOFFEE.
PhantomCore: F6 researchers have spotted a new phishing campaign from PhantomCore that is targeting Russian and Belarusian companies.
More Contagious Interview: Abstract Security looks at new Contagious Interview campaigns targeting job seekers with VSCode project files that deploy malware.
PurpleBravo (Contagious Interview): Recorded Future also looks at the same group and also notes some connections between this campaign and PurpleDelta, North Korea's remote IT workers scheme.
Konni adopts AI: North Korean cyber-espionage group Konni is using AI to generate PowerShell-based backdoors. According to Check Point, the malware was used in recent campaigns targeting the APAC region. The attacks targeted blockchain developers and sought to establish a foothold in their environments.
BlueNoroff: Picus Security looks at the basic methods used by BlueNoroff, a North Korea APT group focused mainly on financial crime.
New Matryoshka info-op: Without missing a beat, Russian disinfo outfit Matryoshka has jumped on the "US invading Greenland" topic. To be honest, Matryoshka may be outmatched here by official Russian media, which has been slobbering over this even more.
Kremlin-linked Matryoshka bot network launches campaign on Greenland dispute, claims Zelensky ready to send troops to fight against the U.S. theins.ru/en/news/288644
— Eliot Higgins (@eliothiggins.bsky.social) 2026-01-21T09:27:41.967Z
Vulnerabilities, security research, and bug bounty
Important security updates: Atlassian, Cisco, GitLab, Oracle, Zoom.
New Cisco zero-day: Cisco has patched an actively exploited zero-day in the Unified Communications Manager phone call and conferencing software. Tracked as CVE-2026-20045, the vulnerability allows remote unauthenticated attackers to run malicious code on the platform's web interface. The attacks leverage a sequence of maliciously crafted HTTP requests to gain root access on the device.
SmarterMail zero-day: A zero-day in the SmarterMail business email platform can allow attackers to reset the application's administrator password. A patch was released on January 15 but the bug had been exploited in the wild before them. watchTowr Labs spotted the bug in logs shared by some of the hacked customers.
GitLab patches 2FA bypass: The GitLab project has patched a vulnerability (CVE-2026-0723) that could have allowed attackers to bypass two-factor authentication. Threat actors knowing a victim's credentials could have submitted forged device responses to bypass 2FA. The bug is one of five security flaws patched this week.
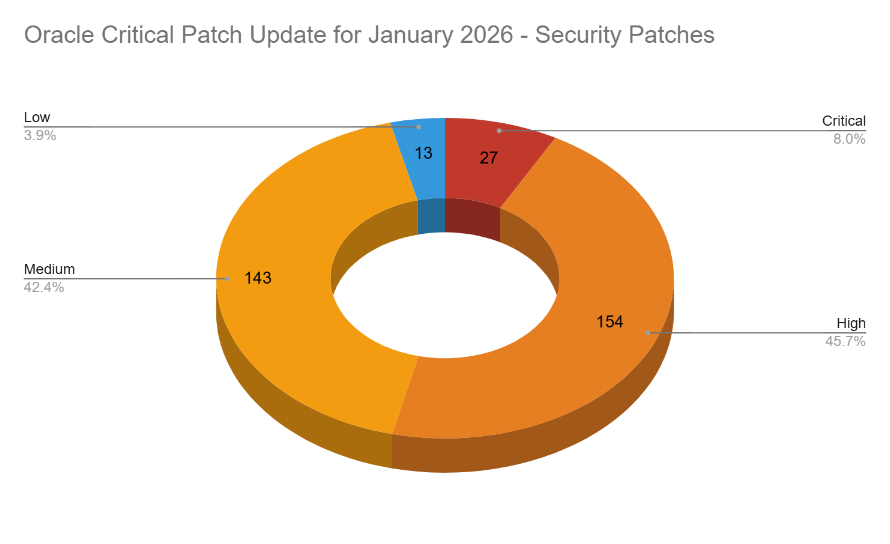
Oracle CPU: The quarterly Oracle security updates are out, with patches for 337 vulnerabilities. Tenable has a breakdown of the fixes.
Vivotek vulnerabilities: Old Vivotek security cameras can be hacked remotely. A newly discovered vulnerability (CVE-2026-22755) allows remote attackers to run remote code without authentication. According to Akamai, at least 37 Vivotek camera models are affected, all running the company's legacy framework.
ChainLeak vulnerabilities: Security firm Zafran has discovered two critical bugs in Chainlit, a framework for building AI applications.
"The flaws allow attackers to leak cloud environment API keys and steal sensitive files (CVE-2026-22218), as well as perform Server-Side Request Forgery (SSRF) against servers hosting AI applications (CVE-2026-22219). These vulnerabilities can be triggered with no user interaction."
Git MCP server vulnerability: Security firm Cyata has found three vulnerabilities in Anthropic's official Git MCP server.
"These flaws can be exploited through prompt injection, meaning an attacker who can influence what an AI assistant reads (a malicious README, a poisoned issue description, a compromised webpage) can weaponize these vulnerabilities without any direct access to the victim’s system."
Upcoming OpenSSL security fixes: The OpenSSL project will release security fixes on January 27, next week.
New Telnet auth bypass is a "nothingburger": GreyNoise and Censys have classified a recently disclosed auth bypass in Telnet as a "nothingburger."
Eviction Notice attack: Academics have discovered a new side-channel attack against a CPU's memory cache pages.
Unpatched OpenAI issue: According to PromptArmor, OpenAI has refused to patch a bug in its API log viewer that can allow threat actors to steal data from apps and agents built and using OpenAI APIs.
Packagist bugs: Security firm Sansec used the Claude coding agent to find 353 vulnerabilities across the top 5,000 PHP extensions on the Packagist repository. The bugs impact libraries with almost 6 million downloads. Almost three-quarters of the bugs are IDOR and authentication bypass issues.
curl to shut down bug bounty: The curl project will shut down its bug bounty by the end of the month. cURL author Daniel Stenberg blamed the influx of AI-generated bug reports received over the year. The reports have allegedly been time-consuming to triage and most are not even security flaws. [Elektroniktidningen]
as you may have noticed: my temper and wiggle room for stupidity in security reports have shrunk to a minimum
— daniel:// stenberg:// (@bagder.mastodon.social.ap.brid.gy) 2026-01-17T15:05:15.000Z
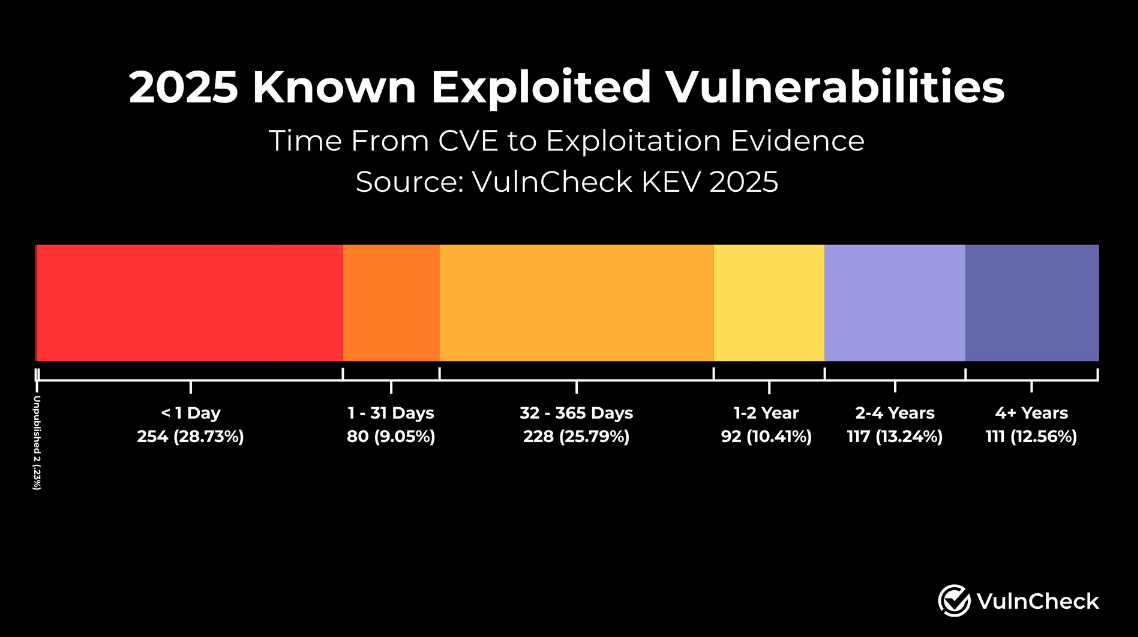
884 new bugs exploited last year: 884 vulnerabilities were exploited for the first time last year. According to vulnerability management company VulnCheck, almost a third were exploited before or shortly after the CVE was published. Network edge devices like firewalls, VPNs, and proxy gateways, were the most frequently targeted technologies.
Infosec industry
Threat/trend reports: Abnormal AI, Black Kite, CyberArk, DLA Piper, Expel, Harmonic Security, Permiso, RSAC, and VulnCheck have recently published reports and summaries covering various threats and infosec industry trends.
Risky Business podcasts
In this edition of Seriously Risky Business, Tom Uren and Amberleigh Jack talk about the rise of technologies that can undermine internet blackouts such as Starlink and its relatively new direct-to-cell service.
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about what information warfare even is, revisit a 30-year-old paper and examine why Western governments struggle with the concept.




