Risky Bulletin: Hunters International ransomware shuts down and releases decryption keys
In other news: FBI investigates ransomware negotiator; Spain arrests government hackers; hackers steal $185 million from Brazilian financial institutions.

This newsletter is brought to you by Sandfly Security. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
The Hunters International ransomware operation has shut down and promised to release free decryption keys for all past victims.
The group announced the shutdown in a message posted on its dark web leak site on Thursday, July 3, after removing all past victims.
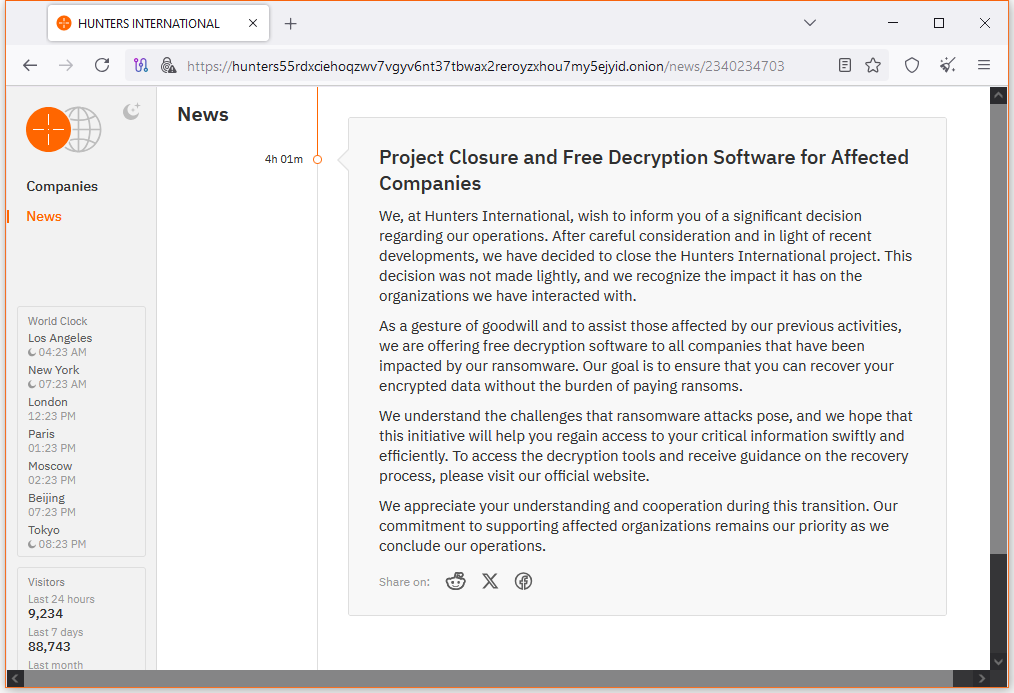
The operation launched at the end of 2023 and was a rebrand of the Hive ransomware, which had its infrastructure seized earlier that year.
According to a Group-IB report, members of the underground cybercrime ecosystem often referred to Hunters as хайв (Hive in Russian), and many said they were contacted by Hunters admins using instant messaging accounts previously used by Hive.
The shutdown of the Hunters International operation is not a surprise for the threat intel community. The group launched a separate platform named World Leaks in January, advising Hunters affiliates to switch to it.
At the time, the group claimed that encryption-based ransomware was not profitable anymore since most victims didn't wanna pay and they were instead switching to a hack-and-extort model.
Despite the claim to have switched to a pure data extortion-only model, French security firm Lexfo found World Leaks victims that had ransomware deployed on their network before being extorted.
A screenshot of the World Leaks panel confirms that Hunters basically changed the logo and nothing else, and it's basically the same platform.
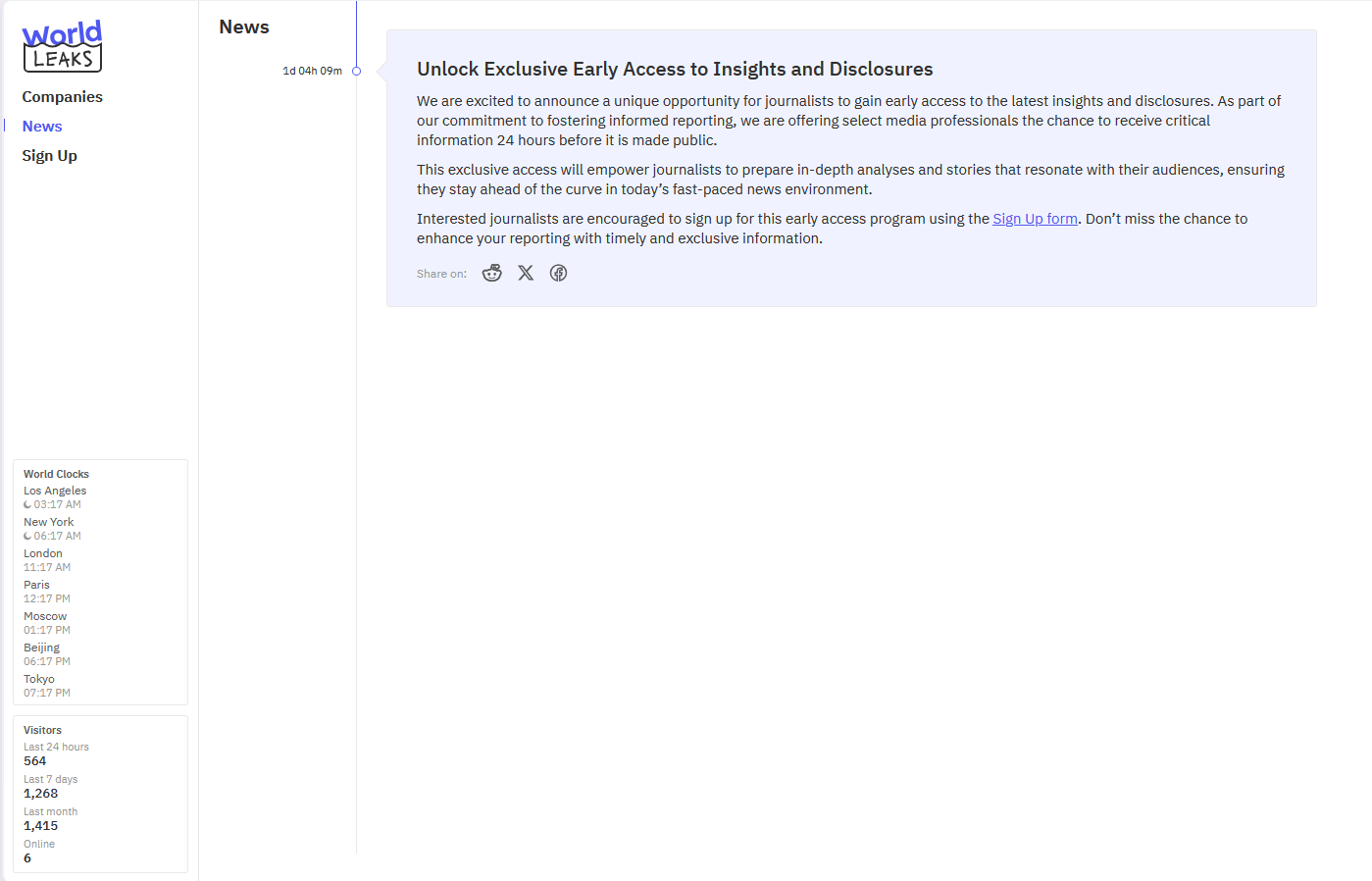
What we have here is a classic example of a ransomware gang being involved in too many attacks and needing or wanting to rebrand to avoid increased scrutiny from law enforcement.
The group has been linked to over 300 attacks, including some pretty big names, such as India's Tata Technologies and the US Marshals Service.
Threat intel analyst 3xp0rt, who first spotted the group's takedown notice, told Risky Business that the decryption keys are being made available via Hunters' backend.
"We have information that victims are required to log in to a portal mentioned in the ransom note using their existing credentials to obtain the decryption software," 3xp0rt said.
Risky Business Podcasts
The main Risky Business podcast is now on YouTube with video versions of our recent episodes. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
Brazil mega-hack: Hackers have breached an IT provider for Brazilian banks and stolen money from at least six institutions. The losses have been estimated at around $185 million. Brazil's Central Bank has ordered C&M to disconnect all its customers while it investigates the hack. [Additional coverage in Brazil Journal/English coverage in Reuters]
Qantas security breach: Australian airline Qantas has detected a security breach at one of its customer support centers. A threat actor gained access to a third-party customer servicing platform storing the personal details of 6 million customers. The airline is still investigating the incident and hasn't attributed the attack. The FBI, Google, and Palo Alto Networks warned last week that the Scattered Spider group was targeting airlines.
Max Financial Services data breach: Indian insurance company Max Financial Services has disclosed a security breach. The company says hackers accessed customer data at its Axis Max Life Insurance subsidiary. [Additional coverage in TechCrunch]
Catwatchful spyware leak: A vulnerability in the website of the Catwatchful spyware app has exposed customer data such as emails and plaintext passwords. The SQL injection vulnerability was found by security researcher Eric Daigle, who used it to dump a copy of the app's database. Daigle says the spyware app had over 62,000 registered users and was deployed on more than 26,000 Android smartphones. TechCrunch also analyzed the database and identified the app's admin as Omar Soca Charcov, a developer based in Uruguay.
Ransomware hits child charity org: A ransomware attack has disrupted the activity of a non-profit organization that works to feed starving children. The Deutsche Welthungerhilfe has shut down all IT systems in light of an attack last month. The organization, whose name translates as World Hunger Help, raises and delivers food and water to communities affected by hunger across the world. The Rhysida ransomware group took credit for the attack and is demanding a $2.2 million ransom. [Additional coverage in The Record]
CoD WW2 hacks: A vulnerability in the Call of Duty WWII game has been exploited this week to run malicious code on some players' systems. Tens of players have reported mysterious files appearing on their PCs or pop-ups showing in-game with threatening messages. Activision has not confirmed the hacks, but many of its older Call of Duty titles have been affected by similar issues in the past. The hacks came to light this week after the game saw a huge surge in new players after the title was added to the Xbox Game Pass. [Additional coverage in Insider Gaming]
CALL OF DUTY WW2 IS NOT SAFE TO PLAY ON PC
— Ghost RyDog (@RyDog2Nasty) July 2, 2025
CALL OF DUTY WW2 IS NOT SAFE TO PLAY ON PC
CALL OF DUTY WW2 IS NOT SAFE TO PLAY ON PC
CALL OF DUTY WW2 IS NOT SAFE TO PLAY ON PC
CALL OF DUTY WW2 IS NOT SAFE TO PLAY ON PC
CALL OF DUTY WW2 IS NOT SAFE TO PLAY ON PC
General tech and privacy
New Microsoft layoffs: Microsoft has laid off 9,100 employees, amounting to 4% of its workforce. This is the company's third round of layoffs this year after it fired 6,000 employees in May and almost 2,000 more in January. Its cybersecurity divisions don't appear to have been impacted. Most of the layoffs impacted its gaming divisions. [Additional coverage in CNBC]
9000 layoffs today from microsoft. Still waiting for AI to "make new jobs" still waiting for the trickle down effect. still waiting for their 75 billion dollar activision merger to benefit people other than the execs already making millions. This nonsense is why regulations are always necessary.
— Nate Horsfall (@lightningarts.bsky.social) 2025-07-02T18:18:24.428Z
Clothoff profile: Der Spiegel has published a profile of Clothoff, a developer of AI nudify app of the same name that recently began to acquire other AI nudify apps. The report claims the app is managed from Eastern Europe.
"But in summer 2024, the operators made a mistake. They left an internal database publicly available on the internet, through which DER SPIEGEL was able to identify four central people behind the website in countries in Eastern Europe: Alexander G. from Russia, Dascha and Alexander B. from Belarus, and Yevgeniy B. from Ukraine, whose company was mentioned for a time in the Clothoff imprint."
Let's Encrypt issues certs for IP addresses: Let's Encrypt has started this month issuing certificates for IP addresses, not just domains.
Huawei to open-source Java clone: On July 30, Huawei will open-source Cangjie, a new programming language based on and designed to rival Java and Swift, and allow Chinese developers to create mobile apps for its HarmonyOS. [Additional coverage in the SCMP]
Funnull sanctions falter: Brian Krebs and SilentPush look at how many US tech companies are failing to implement sanctions on a Chinese national linked to a web hosting provider named Funnull, which has a history of hosting major online scam networks.
Google loses California Android data transfer lawsuits: A jury has ordered Google to pay $314 million to California users in a 2019 class-action lawsuit. Plaintiffs argued that Google generated unwanted network traffic on their devices that increased their mobile bills. The traffic included targeted advertising and secret data collection that was taking place while devices were idle. A federal lawsuit covering the other 49 US states is set to take place next April. [Additional coverage in Quartz]
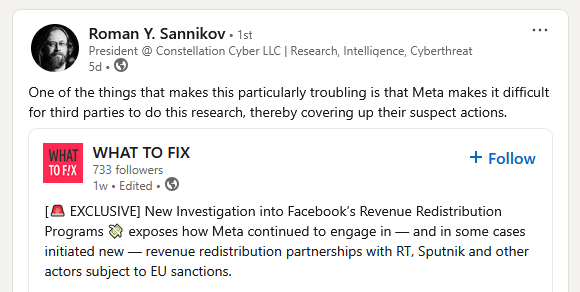
Meta possible broke sanctions: A WhatToFix report claims that Meta broke the EU's Russian sanctions by allowing Facebook pages affiliated with sanctioned Russian companies to sign up for its active partner-publishers program that pays users for their content.
Government, politics, and policy
Predatorgate investigation leads to nothing: An InsideStory report looks at how the Greek government investigation into its own usage of the Predator spyware has hit a wall and effectively died.
⌛️2.5 years after a law was passed promising transparency in the 🇬🇷state's procurement of #spyware — incl. the issuance of a Presidential decree, "absolutely nothing substantial has been done in that direction,"according to documents seen by @etriantafillou.bsky.social. insidestory.gr/article/poio...
— Vas Panagiotopoulos (@vaspanagiotopoulos.com) 2025-07-03T06:27:49.386Z
Russia will build a database of telephone scammers: The Russian government will build a database of known telephone scammers. The database will include voice samples, phone numbers, and caller IDs. Once the database launches, Russian mobile operators will have to show scam warnings on phone screens for calls coming from known scam numbers. The voice samples will be shared with law enforcement for possible investigations. [Additional coverage in Vedomosti]
CBP is looking for phone data analysis gear: US Customs and Border Protection has asked tech companies to pitch new products that can analyze data from devices seized at the US border. The tools must be able to analyze data from laptops and smartphones alike. It must process photos, videos, contacts, and text messages. According to Wired, the tools must be able to identify "hidden messages" and "find patterns" in a user's data.
This is not a technology you need if you expect device searches at the border to be rare or targeted
— Pwnallthethings (@pwnallthethings.bsky.social) 2025-07-03T17:54:02.852Z
Sponsor section
In this Risky Bulletin sponsor interview, Craig Rowland, CEO of Sandfly Security, talks to Tom Uren about the disconnect between how important Linux systems are and how much security attention they get. The pair discuss the variety of reasons that security teams underinvest in protecting Linux.
Arrests, cybercrime, and threat intel
FBI investigates ransomware negotiator: The FBI is investigating the former employee of a security firm for allegedly taking a cut from ransomware payments. The employee worked for DigitalMint, where he helped the company's customers negotiate ransoms during ransomware attacks. According to Bloomberg, the employee had secret deals with ransomware gangs to take a cut of the ransom if he convinced companies to pay. DigitalMint says it fired the employee as soon as it heard of the investigation and started notifying former customers.
Spain arrests government hackers: Spanish police arrested two individuals who hacked government networks and sold the data online. The two suspects were arrested in Spain's Canary Islands. Officials say the suspects sold the personal data and credentials of government officials, politicians, and journalists. The main suspect was responsible for the hacking, while the second individual managed the sale and financial side of the operation.
Spain detains investment scam group: Spanish authorities have detained 21 suspects on charges of running an investment scam ring. The group operated call centers in Barcelona and used social media ads to promote fake investment portals. The suspects allegedly made over €10 million by convincing hundreds of victims across Spain to invest their savings into their platforms.
Russian man sentenced to prison for DDoS attacks: Russia has sentenced a 36-year-old man to 16 years in a high-security prison. Andrei Smirnov was arrested in 2023 in the city of Belovo for launching DDoS attacks against Russian critical infrastructure. Russian officials said the man joined Ukraine's "cyber troops" and launched the attacks at the behest of Ukrainian intelligence services. [Additional coverage in The Record]
DDoSer extradited to the Netherlands: Dutch authorities have successfully extradited a 22-year-old suspect from the United Arab Emirates. The suspect ran piracy websites and a DDoS-for-hire service. He will be arraigned in court on Friday, July 4.
Ghanaian romance scammer extradited: US authorities have extradited a Ghanaian national to face charges for his role in a scheme that targeted the elderly with romance and inheritance scams. A Nigerian man pleaded guilty on similar charges in a separate case.
TOAD campaign: Cisco Talos has spotted multiple adversaries using brand impersonation to launch callback phishing attacks, also known as Telephone-Oriented Attack Delivery (TOAD) attacks.
Chinese fake store phishing: SilentPush has identified a phishing campaign luring users to fake online stores imitating popular brands that collect victims' payment and personal details. The company believes the campaign is the work of Chinese-speaking developers.
FBI warns of ramp-and-dump scams: The FBI reports seeing a 300% rise in ramp-and-dump fraud. The scheme relies on social media to lure investors to secret communities designed to artificially increase a fund's price by asking members to purchase stocks. The fraud takes place when the community's creators secretly sell off and crash the stock for a profit for themselves. It's basically a variation of a pump-and-dump, but adjusted for the current social media landscape and its gullible WallStreetBets-adjacent users.
Cyber scam compounds spread to other continents: Cyber scam compounds have expanded from Southeast Asia to two other continents. New scam centers have been spotted in the Middle East, Central America, and Western Africa. According to Interpol, Western Africa is growing into a major hub for these types of operations.
Vercel's v0 AI tool abused for phishing: Okta's security team says threat actors are abusing Vercel's v0 genAI tool to craft phishing pages that imitate legitimate services.
ELUSIVE COMET linked to Aureon Capital: The Security Alliance says a venture capital firm named Aureon Capital is a front for ELUSIVE COMET, a threat actor engaged in social-engineering campaigns designed to infect other crypto experts with malware and steal their funds.
Malicious OpenVSX extension had 200,000 downloads: Almost 200,000 developers have downloaded a malicious VSCode extension from the OpenVSX marketplace. The extension looked for existing ScreenConnect apps and then downloaded and installed its own malicious version. According to SecureAnnex, that was the entirety of the extension, which had no other functionality. The extension was removed an hour after it was reported.
40+ malicious Firefox extensions: Over 40 malicious Firefox extensions have been found on the official Firefox store. The extensions impersonated known crypto-wallet brands and contained code designed to intercept and steal wallet credentials. Koi Security says the extensions are part of a campaign that started in April and used fake reviews to boost their popularity and attract users. The campaign is still ongoing, and some of the malicious extensions were active as recently as last week. Koi Security believes the campaign is the work of a Russian-speaking threat actor.
Two new pro-Kremlin hacktivist groups: Intel471 has identified two new pro-Kremlin hacktivist groups named TwoNet and the IT Army of Russia. Both are mainly involved in DDoS attacks, but the latter is also recruiting insiders in Ukrainian orgs.
Keymous+ group behind 700 DDoS attacks this year: A hacktivist group named Keymous+ has launched over 700 DDoS attacks this year against random targets across the world. Security firm Radware says the hacktivist activity appears to be a marketing persona for a DDoS-for-hire service named EliteStress. The group claims it's made up of North African hackers but hangs around all the pro-Kremlin and pro-Palestine hacktivist groups, often amplifying their messages.

Malware technical reports
NimDoor: SentinelOne has published a technical analysis of NimDoor, a Nim-based backdoor that North Korean state-sponsored hackers have been using in attacks against crypto platforms.
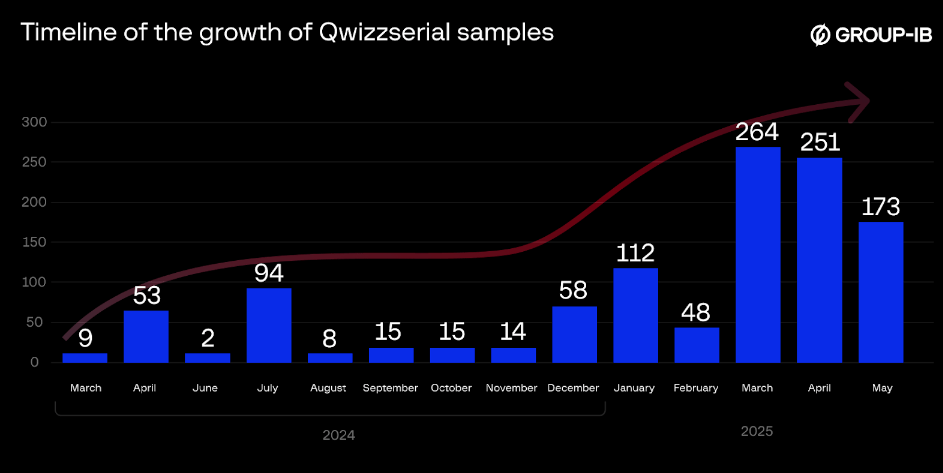
Qwizzserial Android malware: Security researchers have discovered a new Android malware named Qwizzserial that was specifically built to collect a list of financial apps and intercept SMS messages. According to Group-IB, the malware has infected around 100,000 users. Most of the infections are in Uzbekistan, where SMS is still the primary method of delivering 2FA codes.
Sponsor section
Sandfly Security can help you find Linux packet-sniffing malware instantly and at scale. You can get a free trial and know immediately if any suspicious processes are sniffing traffic today.

APTs, cyber-espionage, and info-ops
Salt Typhoon largely contained: US officials claim to have "largely contained" the Salt Typhoon hacking group that breached US telco networks last year. Brett Leatherman, the FBI's new cyber division leader, told CyberScoop the agency is focused on supporting victims and evicting the hackers. An "imposing costs" phase is in the works.
Iran provides tools to hacktivists: Iranian state-sponsored hackers are allegedly providing tools to hacktivist groups attacking Israel and Western states. Security firm Armis told Axios the help was "a lot" and ranged from hacking tools to training resources. Recorded Future likened Iran's tactics to Russia, which is also using hacktivist groups to attack countries aiding Ukraine, and for plausible deniability.
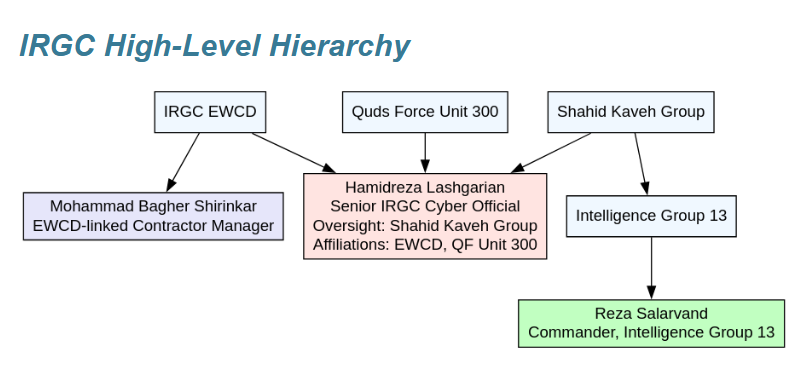
Iran's Intelligence Group 13: DomainTools has published a profile of Iran's Intelligence Group 13, a cyber group that the company describes as "one of the most operationally aggressive and ideologically fortified units within the Islamic Revolutionary Guard Corps (IRGC) cyber arsenal." The group is the larger entity behind the CyberAveng3rs public persona.
"Intelligence Group 13 functions as the operational spearhead of the Shahid Kaveh Group, a hybrid entity positioned at the intersection of the IRGC's cyber warfare and Quds Force portfolios. This structural alignment gives Team 13 a unique dual mandate: to execute precision cyber intrusions with military-grade sophistication while simultaneously engaging in psychological and ideological warfare."
TradeTraitor profile: Invictus IR has published a profile and TTPs from TradeTraitor, a North Korean state-sponsored hacking group that specifically targets the crypto community to gather funds for the regime's weapons program. The group is also known as Jade Sleet, UNC4899, Slow Pisces, and TraderTraitor.
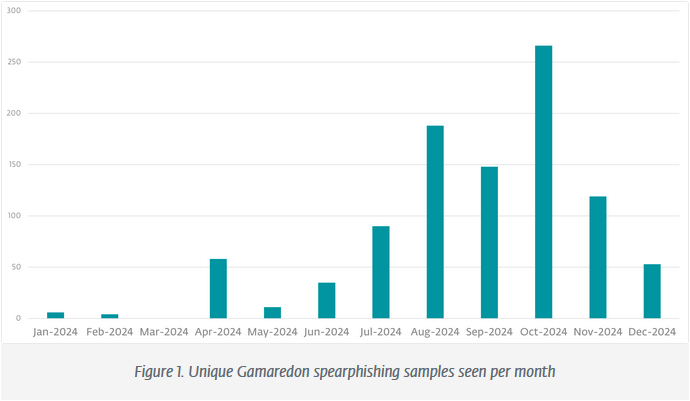
Gamaredon: ESET has published a report looking at the Gamaredon APt's activity last year, with most of its attacks targeting Ukrainian organizations, abandoning prior operations against NATO countries. The group also deployed six new toolkits.
"Gamaredon's spearphishing activities significantly intensified during the second half of 2024. Campaigns typically lasted one to five consecutive days, with emails containing malicious archives (RAR, ZIP, 7z) or XHTML files employing HTML smuggling techniques."
Vulnerabilities, security research, and bug bounty
Cisco security updates: Cisco has released four security advisories for various products. One of them is a moronic 10/10 vulnerability of hardcoded SSH credentials for the root account in the Cisco Unified Communications Manager.
KEV update: CISA has updated its KEV database (twice) with three vulnerabilities that are currently exploited in the wild. This includes two new TeleMessage bugs (yeah, remember them?) and a recent Chrome zero-day.
Azure misconfigured roles: Token Security has discovered that Azure built-in roles are misconfigured and include more permissions than they should have or are intended by Azure. Microsoft chose to update its documentation rather than redesign the role permissions.
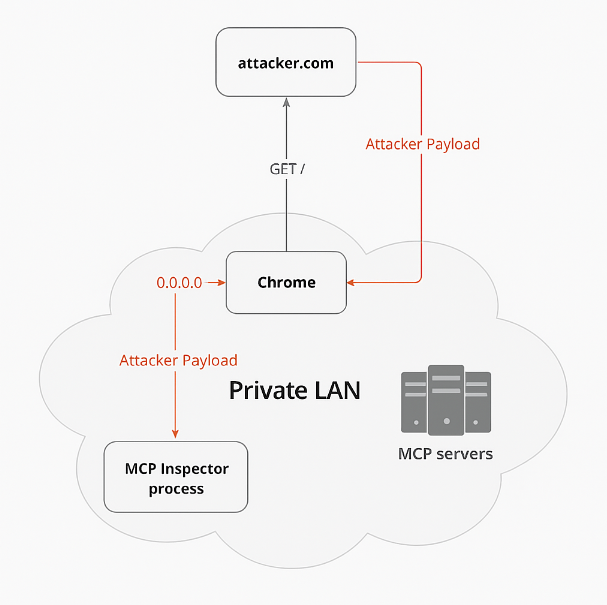
Anthropic RCE vulnerability: A vulnerability in the Anthropic MCP Inspector toolkit can allow attackers to run malicious code on the machines of AI developers. The MCP Inspector is a standard toolkit for testing and debugging Anthropic MCP servers and is widely used by AI teams. The attack targets a developer's browser and combines localhost rebinding with a CSRF bug for remote attacks. Oligo Security says the technique can be used to attack AI developers but also their AI systems.
Infosec industry
Threat/trend reports: Dr.Web, Interpol, and Slowmist [PDF] have recently published reports and summaries covering various infosec trends and industry threats.
New tool—SockTail: Security researcher Yeeb has released SockTail, a read team tool that joins a device to a Tailscale network and exposes a local SOCKS5 proxy on port 1080.
New tool—Kingfisher: MongoDB has released Kingfisher, a tool to scan and then validate leaked secrets.
BSides Athens 2025 stream: A live stream of the BSides Athens 2025 security conference, which took place last week, is available on YouTube.
ContinuumCon 2025 videos: Talks from the ContinuumCon 2025 security conference, which took place last week, are available on YouTube.
CERIAS 2025 videos: Talks from the Purdue CERIAS 2025 Cybersecurity Symposium, which took place at the start of April, are available on YouTube (Playlist one, Playlist two).
Risky Business podcasts
In this edition of Seriously Risky Business, Tom Uren and Patrick Gray discuss warnings about Iranian cyberattacks on US critical infrastructure. Despite many warnings, there have been no actual attacks, and they discuss the reasons why Iran would want to avoid escalatory cyber attacks.
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about how Microsoft has embraced digital sovereignty and is bending over backward to satisfy European tech supply chain concerns.




