Risky Bulletin: Hacktivists claim cyber-sabotage of 116 Iranian ships
In other news: Iran calls out China for hacking; six new Paragon customers come to light; North Korea creates new cyber unit.

This newsletter is brought to you by /no-code automation platform Tines. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
An anti-regime hacktivist group has claimed credit over a cyberattack that crippled the on-ship communication systems of 116 Iranian ships.
The ships are operated by the National Iranian Tanker Company (50) and the Islamic Republic of Iran Shipping Company (66).
According to Nariman Gharib, a London-based Iranian cyber espionage investigator, the alleged affected vessels are these ones.
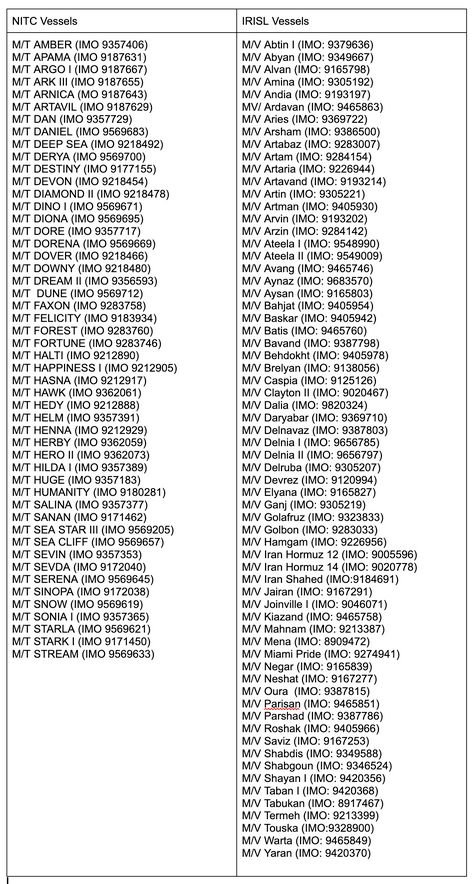
A group named LabDookhtegan took credit for the sabotage. The attack allegedly targeted the VSAT satellite communication systems of the two companies, where the group wiped data storage devices.
LabDookhtegan claimed the two companies had used their ships to resupply the Houthi rebel group in Yemen, which has been attacking ships passing through the Bab-el-Mandeb straight and disrupting global commerce for the past year.
The group also claimed it received help conducting the attack from government insiders.
For those familiar with the group's history, this is not that much of a stretch of one's imagination.
The LabDookhtegan appeared in 2019 and initially leaked hacking tools and malware used by an Iranian espionage group named APT34.
Through tens of subsequent leaks, the group leaked troves and troves of internal documents from Iranian government agencies. These leaks have helped out cybersecurity companies and foreign government agencies map out the Iranian government's structure and dox many of its cyber units and private cyber contractors.
This marks the first time when the group has claimed credit for a destructive attack, which is a big change from its regular "leak, leak, leak" modus operandi.
Risky Business Podcasts
Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
SpyX hack: A hacker has breached and leaked the data of almost two million users who signed up for spyware app SpyX and two of its clone services. The leaked data contained emails, IP addresses, country of origin, and even some information on surveilled targets. The hack took place in June of last year but only came to light this week after a researcher shared the data with the Have I Been Pwned service. According to TechCrunch, SpyX is the 25th mobile spyware app to get hacked since 2017.
Baidu denies breach: Chinese search giant Baidu denied suffering a security breach after the daughter of a top executive doxxed internet users following an online argument. Baidu Cloud Vice President Xie Guangjun apologized for the incident on Monday in a WeChat post. He said his teenage daughter obtained the personal data from foreign doxing databases. [Additional coverage in Reuters]
Crypto AI bot gets hacked: An attacker used malicious Twitter replies to hack an AI crypto chatbot and steal over $100,000 worth of Ether. [Additional coverage in Decrypt]
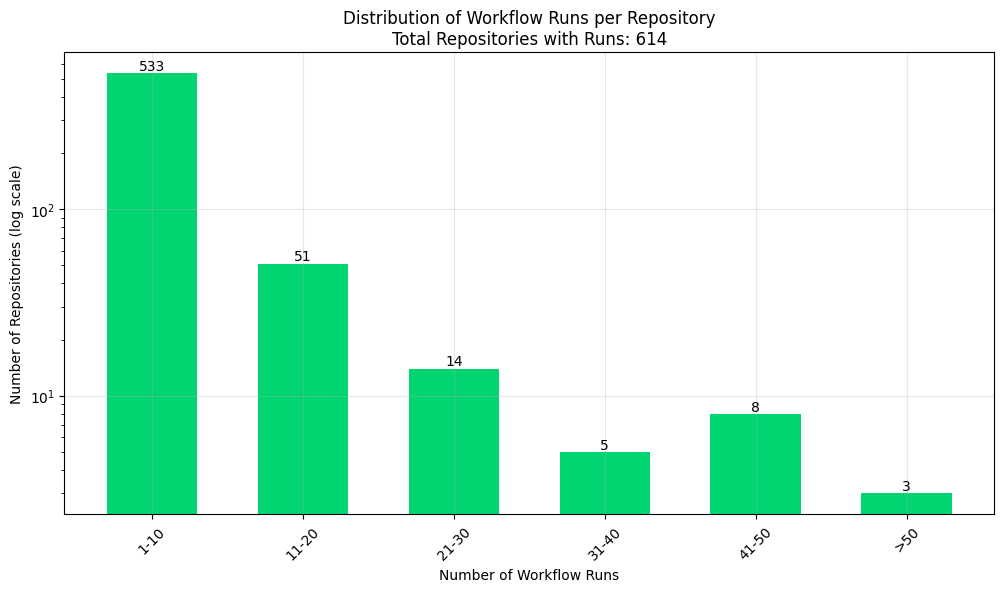
Changed-Files impact was very small: A supply chain attack on the Changed-Files GitHub action impacted just over 600 repositories and leaked secrets only from 218. The number is far below the initial estimate of 23,000. EndorLabs says that even if the action contained malicious code for 18 hours, only a small percentage of the action's users ran the file. The Changed-Files incident took place last Friday after an attacker added malicious code to the action that printed a project's credentials and secrets in build logs. According to Wiz, the action was allegedly compromised after a hack of another GitHub action (ReviewDog/Actions-Setup).
General tech and privacy
TikTok deal: Oracle has emerged as the main candidate to take over TikTok's US operations. [Additional coverage in Politico]
HP adds PQC to printers: HP has released its first printers with support for PQC protections.
Chrome rolls out new Rust-based font loader: Google has rolled out a new Rust-based font loader for Chrome to improve the browser's security. The new Skrifa engine replaced FreeType as the default font renderer in Chrome in February this year. It shipped on Android, Linux, and ChromeOS. On Windows and macOS, font rendering is handled by the OS, and Skrifa is used as a backup for unknown fonts. Skrifa is the latest Rust component to ship in Chrome after Google committed in 2023 to slowly transition from Chrome's C++ code to Rust.
EU warns Apple and Google: The European Commission has sent letters to both Apple and Google informing them they are not DMA compliant. Fines may soon follow since the two companies are now hiding behind an overly anti-EU Trump, and the EU seems to be looking for a fight.
Government, politics, and policy
US suspends disinformation work: The White House has suspended the work of several US intelligence agencies that were helping EU allies detect and prevent Russian cyber-espionage, disinformation, and sabotage attacks. The previous Biden administration set up the working groups last year. According to Reuters, the groups stopped working and scheduling meetings after Trump took office.
US agencies abuse E2EE apps: An AP investigation found that more and more US federal and local agencies are using E2EE-capable apps in an attempt to hide their communications and keep them off public records.
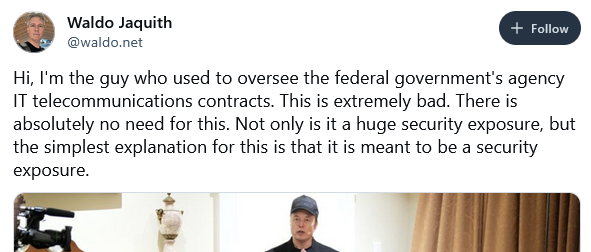
Starlink in the White House: There are more and more reports that connecting Starlink terminals to White House infrastructure is a major national security threat due to the platform's insecurity.
Hong Kong passes cybersecurity bill: The Hong Kong government has passed its first-ever cybersecurity bill. The new law introduces new cybersecurity requirements for critical sector operators, such as reporting incidents to the Security Bureau within 12 hours and filing yearly risk assessments. It also introduces fines of up to $640,000 for any security lapses or failure to maintain cybersecurity standards. [Additional coverage in the Hong Kong Free Press] [h/t DataBreaches.net]
UK sets PQC migration plan: The UK's cybersecurity agency has published a three-phase plan to help organizations migrate to using quantum-resistant encryption methods. Companies must identify cryptographic services using old encryption standards and migrate to a PQC alternative by 2035. High-priority and critical services must migrate by 2031.
New Dutch espionage law: The Dutch government passed a new law that criminalizes more forms of espionage, such as digital/cyber and diaspora espionage.
Dutch MPs approve a Dutch cloud: The Dutch Parliament passed several motions this week to create a Dutch-based cloud service, move government systems back into the country, and stop using "unsafe" US infrastructure.
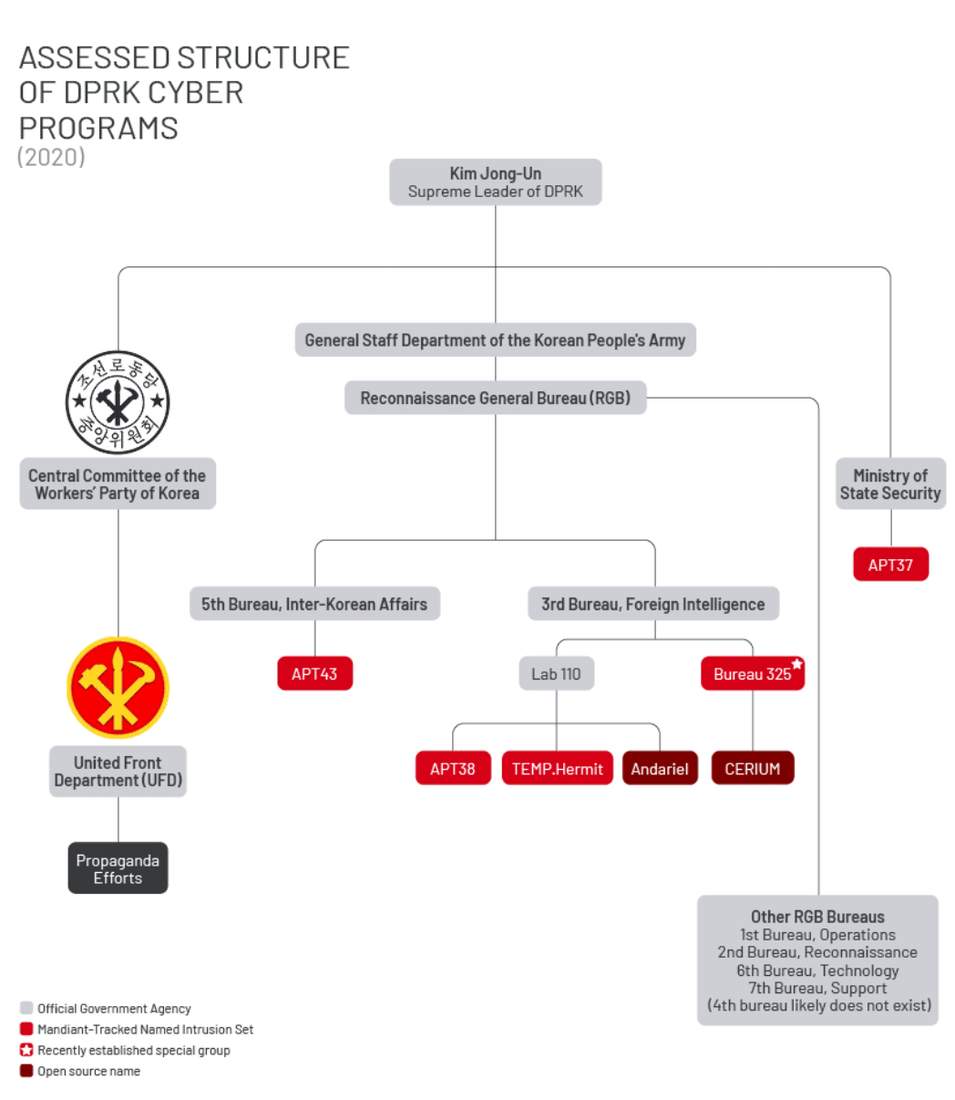
North Korea creates new cyber bureau: North Korea has established a new cyber unit inside its military intelligence agency for developing new offensive hacking technologies. The new Research Center 227 will operate under the Reconnaissance General Bureau, the agency that directs all of the country's foreign hacking operations. Most of the country's APT groups are operated by RGB Bureau 3, 5, 121, and 325. The center began operations at the start of the month and will allegedly be staffed with around 90 computer experts. [Additional coverage in the Daily NK]
Sponsor section
In this Risky Business News sponsor interview, Tom Uren talks to Matt Muller, field CISO of Tines. He explains how governments are using carrots and sticks to improve the security of enterprise software. Matt discusses CISA's "Secure by Design" pledge and the UK NCSC's effort to quantify "unforgivable bugs."
Arrests, cybercrime, and threat intel
CapitalOne hacker to be resentenced: A US appeals court has vacated a sentence handed out to Capital One hacker Paige Thompson. Appeal judges considered the original 2022 sentence of time served and a five-year probation period to be too lenient and an unreasonable departure from recommended sentencing guidelines. The case was sent back to a district court for resentencing. This is the second time in two months that an appeals court has ordered a hacker's case to be resentenced after the case of BreachForums admin Pompompurin. [Additional coverage in Reason]
More Paragon customers uncovered: CitizenLab researchers have identified at least six other governments who bought access to spyware from Israeli company Paragon Solutions. An analysis of Paragon server infrastructure has found ties to possible customers in Australia, Canada, Cyprus, Denmark, Israel, and Singapore. Paragon found itself at the center of a public scandal in late January when Meta notified around 90 users that they'd been targeted with Paragon's Graphite spyware. Many of the initial infections were Italian activists and journalists. Paragon has since dropped the Italian government as a customer, citing a breach of terms.
State protection for BlackBasta admin: A new analysis of the BlackBasta leaked internal chats suggests the group's administrator requested and received help from Russian authorities after he was arrested in Armenia last year. BlackBasta admin Oleg Nefedov bragged about contacting a high-level Russian official who then flew to Armenia to secure his release. Security firm Trellix says the BlackBasta admin described the procedure as a "green corridor" but did not name the official. Nefedov was arrested in Armenia based on a US arrest warrant in June last year and was mysteriously released after a judge did not extend his detain order in highly unusual circumstances.
Rise in ServiceNow attacks: Security firm GreyNoise has seen a notable rise of in-the-wild activity targeting ServiceNow servers. The attacks are exploiting three ServiceNow vulnerabilities patched last year. The exploitation wave surged over the past two days, and around 70% of sessions targeted servers in Israel.
Chrome extension market: Security firm SecureAnnex has published a deep dive into the underground market of Chrome extensions, where cybercrime groups buy good extensions and turn them into malware.
Desorden profile: Group-IB has published a profile of the Desorden (AltDos) hacker, which they helped arrest earlier this month.
Dragon RaaS: SentinelOne has published a profile of Dragon RaaS, a pro-Kremlin hacktivist group and ransomware operation that emerged last July as an offshoot of the Stormous group.
New Ox Thief ransomware: FalconFeeds has identified a new ransomware gang going by the name of Ox Thief.
🚨 OX THIEF Ransomware Alert 🚨 We have identified and begun monitoring a new ransomware group named "OX THIEF". They have listed Broker Educational Sales & Training as a victim on their dark web portal. Note : Broker Educational Sales & Training previously fell victim to MEDUSA Ransomware.
— FalconFeeds.io (@falconfeedsio.bsky.social) 2025-03-03T20:34:00.356Z
Babuk2 ransomware: A new threat actor is posing as the old Babuk ransomware gang and attempting to ransom and scam companies with old leaked data.
Malware technical reports
DollyWay botnet: GoDaddy's security team has discovered a botnet that has compromised over 20,000 WordPress sites. Named DollyWay, the botnet has been active since 2016 and uses the hacked websites to redirect users to online scams and fake browser update pages. The botnet's operators often apply security updates to compromised sites and remove any competing malware. GoDaddy says DollyWay is the larger parent cluster of previously reported groups such as Master134, Fake Browser Updates, and CountsTDS.
VanHelsing ransomware: CyFirma researchers have spotted a new ransomware strain named VanHelsing.
Anubis backdoor: G Data has published a technical analysis of Anubis, a new Python-based backdoor linked to FIN7 operations. Also, check out the Prodaft report.
Betruger backdoor: Symantec has published a report on Betruger, a new backdoor used by the RansomHub gang. The backdoor is pretty sophisticated and includes support for:
- Screenshotting
- Keylogging
- Uploading files to a command and control (C&C) server
- Network scanning
- Privilege escalation
- Credential dumping
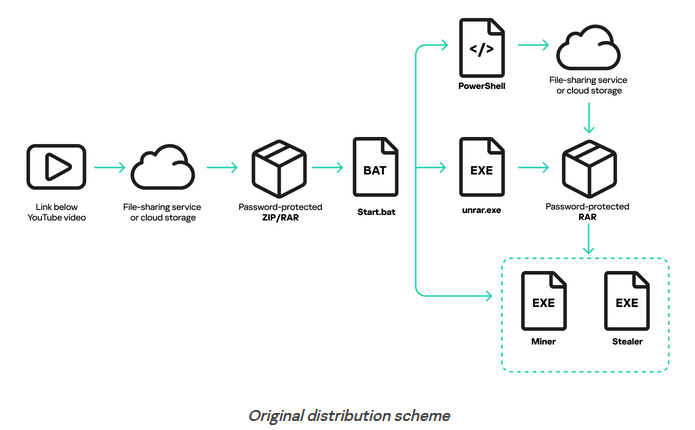
Arcane Stealer: Kaspersky researchers have published an analysis of Arcane Stealer, a new infostealer spread via YouTube videos promoting links to video game cracks and cheats.
Sponsor section
In this product demo, CEO Eoin Hinchy shows how Tines' Workbench can integrate an LLM into security workflows to gather, analyze, and act on data from both inside and outside your company. This demo includes grabbing IOCs from an external webpage, comparing them to your companies' own incidents, and taking actions like resetting passwords.
APTs, cyber-espionage, and info-ops
Iran stops APT15: Iran's cybersecurity agency AFTA said it detected and stopped an attack from Chinese cyber-espionage group APT15. The group allegedly gained access to critical infrastructure and government networks. This marks the first time the Iranian government has called out China for its espionage operations.
UAT-5918 targets Taiwan: A newly discovered cyber-espionage group (UAT-5918) is targeting Taiwan and aiming to establish long-term persistent access to local networks. Cisco Talos says the activity of this group overlaps with four different Chinese APTs—Volt Typhoon, Flax Typhoon, Earth Estries, and Dalbi.
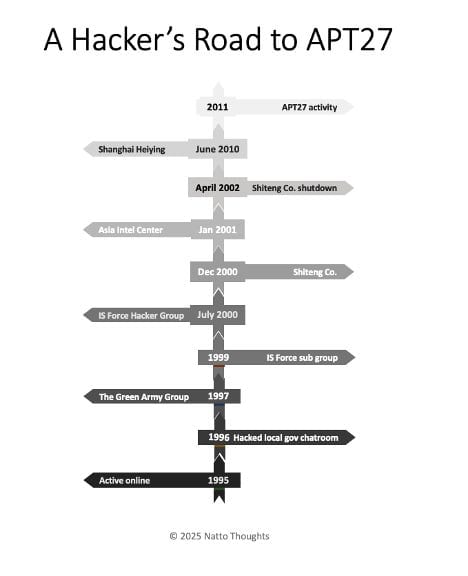
Zhou Shuai profile: Natto Thoughts has published a profile on Zhou Shuai, one of China's oldest hacktivists known as Coldface, now turned government hacker. The US indicted and sanctioned Zhou earlier this month for his and his company's ties to a cyber-espionage group known as APT27.
Vulnerabilities, security research, and bug bounty
NTLM hash leak bug: Security researcher 0x6rss has published details and a PoC for CVE-2025-24071, an NTLM hash leak vulnerability that Microsoft patched this month.
"Windows Explorer automatically initiates an SMB authentication request when a .library-ms file is extracted from a .rar archive, leading to NTLM hash disclosure. The user does not need to open or execute the file—simply extracting it is enough to trigger the leak."
Azure App Proxy leak: TrustedSec researchers have found a bug in the Azure App Proxy that may accidentally expose private networks to internet access.
Veeam RCE: Software company Veeam has fixed a remote code execution vulnerability in its widely-used Backup & Replication server. The vulnerability (CVE-2025-23120) has a severity score of 9.9/10 and can allow users from the same network (domain-authenticated) to run malicious code on the server. According to watchTowr Labs, the vulnerability exploited and bypassed the app's deserialization blacklist to run a deserialization attack.
Jenkins update: The Jenkins project has released a security update to fix three vulnerabilities in major plugins.
WP Ghost vulnerability: Patchstack researchers have found an LFI vulnerability in WP Ghost, a WordPress plugin installed on over 200,000 sites.
Apple Passwords app was vulnerable to phishing: Mysk researchers have found a phishing vector in Apple's Passwords app. The issue was patched, but Apple declined to pay for the bug report—which is becoming a regular occurrence at the company these days.
Infosec industry
Threat/trend reports: CyFirma, Europol, NCC Group, and Positive Technologies have recently published reports and summaries covering various infosec trends and industry threats.
New tool—WEBCAT: The SecureDrop project has open-sourced WEBCAT, a project to sign and verify websites before they load.
Risky Business Podcasts
Tom Uren and Patrick Gray discuss how China's Ministry of State Security is increasingly doxxing and threatening Taiwanese APT operators. In some ways, this mirrors the US strategy of naming and shaming Chinese cyber operators in indictments that contain lots of supporting information. But although MSS statements are filled with propaganda rather than technical detail, naming Taiwanese military hackers has some bite.
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about how offensive cyber operations could do so much more than just "deny, disrupt, degrade, and destroy." Grugq thinks this thinking is rooted in US military culture, and he wonders why cyber operations are always so mean.




