Risky Bulletin: Hackers abuse secret WordPress feature you'll probably want to disable
In other news: EU to invest in AI&cybersecurity; backdoor found in robot dog; macOS to support TCC events.

This newsletter is brought to you by Kroll. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
Hackers are abusing a little-known WordPress feature named Must Use Plugins to install and hide malware from site administrators.
Also known as mu-plugins, the Must Use Plugins feature was added to the WordPress CMS in 2022.
Plugins placed in a special folder named /mu-plugins are automatically installed and enabled on a website without users needing to manually approve them.
These plugins don't show up in the normal Plugins section of the WordPress backend to prevent users from accidentally disabling or uninstalling them.
The feature was specifically designed for web hosting providers and theme developers to ship and hide plugins needed for hosted sites and themes to work—and hence why they're named "must use" plugins.
According to GoDaddy's Sucuri security team, threat actors began abusing Must Use Plugins since at least February this year. That abuse has now gotten worse.
Hackers are breaking into WordPress sites and dropping malware in the mu-plugins folder, knowing it will get automatically executed and won't show up in site backends.
Further, as an added benefit, because it's a relatively unknown feature, many WordPress security tools don't even scan the folder for possible threats.
Sucuri has seen attackers use the mu-plugins folder to deploy backdoors and web shells, host SEO spam on the hacked sites, and hijack and redirect traffic to malicious sites.
The wide spectrum of abuse suggests the abuse of this feature is gaining traction among underground groups.
"The fact that we've seen so many infections inside mu-plugins suggests that attackers are actively targeting this directory as a persistent foothold," says Sucuri security analyst Puja Srivastava.
Site owners are advised to keep a watch on the content of that folder, and if they are not using Must Use Plugins, just delete and make sure it stays deleted altogether.
Risky Business Podcasts
Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
Oracle Health data breach: Hackers have breached Oracle Health and have stolen medical data from the company's servers. According to Bloomberg sources, the hack took place at the end of January, and the hackers are extorting US medical providers with the stolen data. This is the second suspected breach at Oracle after a different hacking group claimed to have hacked the company's Cloud service earlier this month. Oracle has not reported any of the breaches to the SEC.
Cyber incident at Dutch Public Prosecutor's Service: The Dutch Public Prosecution Service has disconnected its IT system from the internet after a cybersecurity incident on Friday. The agency convened its crisis management team to address the incident. Officials described the incident as a large-scale failure of its infrastructure that was preventing staff from communicating with the police and the judiciary. [Additional coverage in NRC]
T-Mobile breach settlements to go out next month: T-Mobile will start paying users affected by the company's 2021 data breach. The telco is set to distribute $350 million as part of a class action settlement. Over 76 million customers are eligible for payments. Payments will range between $25 and $25,000 for users who can prove they suffered out-of-pocket losses. [Additional coverage in The Hill]
Hyperliquid crypto-heist: A threat actor manipulated the price of a memecoin named JellyJelly and stole almost $13 million worth of assets from liquidity pool Hyperliquid. [Additional coverage in The Block]
General tech and privacy
Quantum computer RNG: A team of researchers from banking giant JP Morgan claim to have generated truly random numbers using a quantum computer.
Chrome root program changes: Google has revamped some of the rules for its Chrome root store program, asking certificate authorities to invest more in modern infrastructure and automation.
macOS to support TCC events: Apple is adding a new logging feature to macOS that will help security products to detect and stop malware in a new way. The feature will be added to the Transparency Consent and Control framework, which prompts users for consent whenever an app needs to access their files, passwords, or other data. The new TCC event logging feature will allow security products to trace back malware infections to their source and even add new real-time detection capabilities for suspicious data access. [Additional coverage in Objective-See]
Windows 11 forces MSFT accounts: Microsoft has removed the ability to install Windows 11 with a local account. Going forward, users won't be able to install Windows 11 without internet connectivity and a valid Microsoft account. Microsoft has been trying to force Windows 11 users to install the OS with a Microsoft account for years, but this marks the first time when the company has made it a public policy in one of its blogs.
Government, politics, and policy
EU to invest in AI, cybersecurity: The European Union will invest €1.3 billion into strategic technologies such as AI, cloud, and cybersecurity. The funds will be made available through the Digital Europe Program over the next three years. Earlier this month, a coalition of European businesses urged EU lawmakers to invest in local alternatives to US tech services.
Italy admits to using spyware against NGOs: The Italian government has admitted to using spyware against the founders of an NGO that helps refugees crossing the Mediterranean. High-ranking intelligence officials told a parliamentary oversight committee they approved the surveillance on the grounds of national security. The hacks came to light earlier this year after Meta notified some of the activists. Italian officials initially denied the hacks. [Additional coverage in Euractiv]
Italy gets a new spyware provider: In the aftermath of the scandal (see above entry), Israeli spyware company Paragon cut off Italy's access to its Graphite spyware, citing a breach of contract. In the meantime, the Italian government has contracted a local Italian company Negg to provide it with new surveillance capabilities. Negg operates a one-click spyware platform known as VBiss. According to Google, the company's product was detected in the past in operations in Italy, Malaysia, and Kazakhstan. [Additional coverage in Intelligence Online]
Small 🇮🇹Italian cyber intelligence firm Negg recently won a contract to provide its services to the office of PM Giorgia Meloni "after #Paragon was exposed," according to Intelligence Online sources. "The firm is developing a 1-click spyware called VBiss." www.intelligenceonline.com/surveillance...
— Vas Panagiotopoulos (@vaspanagiotopoulos.com) 2025-03-21T07:03:34.529Z
Indonesia warns workers of countries with a scam risk: The Indonesian government has reminded workers they should not take jobs in Cambodia, Thailand, and Myanmar due to the high risk of getting kidnapped and forced to work in cyber scam centers. Indonesian officials say they have no bilateral working agreements with any of those countries and they will have an "illegal" status once they travel there, and hence no protections. [Additional coverage in Antara News]
Senator pushes crackdown on ad fraud: A US senator has asked the FTC and the US General Attorney's Office to crack down on digital ad fraud.
Trump union EO to impact CISA: US President Trump issued an executive order last week ordering 18 federal agencies to end collective bargaining agreements with federal unions. The White House claims the work of federal unions damages and hinders national security, intelligence, and counterintelligence work. The order applies to the DOD, DHS, CISA, and many federal agencies involved in cybersecurity. The DOJ and DOD have already filed lawsuits against the largest federal union on Friday, seeking to end its CBA. Union representatives called the executive order unlawful and an attack on the civil service.
This seems to be the actual executive order text decertifying many federal unions as "national security" related, notably excluding CBP's two unions. www.whitehouse.gov/presidential...
— CBPWatch (@cbpwatch.bsky.social) 2025-03-28T16:20:26.371Z
Sponsor section
In this Risky Bulletin sponsor interview Ed Currie from Kroll Cyber talks to Tom Uren about the recent hack of the Gravy Analytics geolocation data provider. He explains the hack and how geolocation data can be used by malicious actors.
Arrests, cybercrime, and threat intel
Texas GOP hacker arrested: The US Justice Department has indicted a Canadian man for hacking the Texas Republican Party. Aubrey Cottle allegedly hacked the party's web server in 2021, defaced their website, and stole files containing the personal information of party members. The suspect was identified after he took credit for the hack on social media. Cottle was arrested in Canada last week, and police found the stolen data on his devices.
New Pegasus spyware victims: The Balkan Investigative Reporting Network (BIRN) says that two of its Serbian journalists were targeted with the Pegasus spyware last month.
#Serbia: RSF firmly condemns the attempt to install Pegasus — a spyware only sold to governments — on the phones of 2 journalists for the investigative outlet BIRN. We ask the 🇷🇸authorities to explain this grave attempt on press freedom & hold the perpetrators responsible.
— RSF (@rsf.org) 2025-03-28T08:26:27.509Z
Rumor of raid on SiegedSec leader: Former members of SiegedSec, the now-disbanded hacker group that leaked details on Project 2025, claim the group's leader was raided by authorities. [Additional coverage in The Daily Dot]
Troy Hunt phish: Security firm Validin looks at a recent phish of HIBP owner Troy Hunt and the connections with the Scattered Spider (Oktapuss) group.
New npm malware: Two hundred twenty-two malicious npm packages were discovered and taken down last week. Check out the GitHub security advisory portal for more details.
Water Gamayun arsenal: Trend Micro has published a profile on Water Gamayun, a fin-crime group also known as EncryptHub and Larva-0208. The group recently used a Windows zero-day tracked as CVE-2025-26633.
EncryptHub interview: Threat intelligence analyst g0njxa has published an interview with the developer of the EncryptHub (Fickle Stealer) infostealer.
ClickFix overview: Logpoint has published an overview of the ClickFix tactic. See similar reports on this from Sekoia.

Malware technical reports
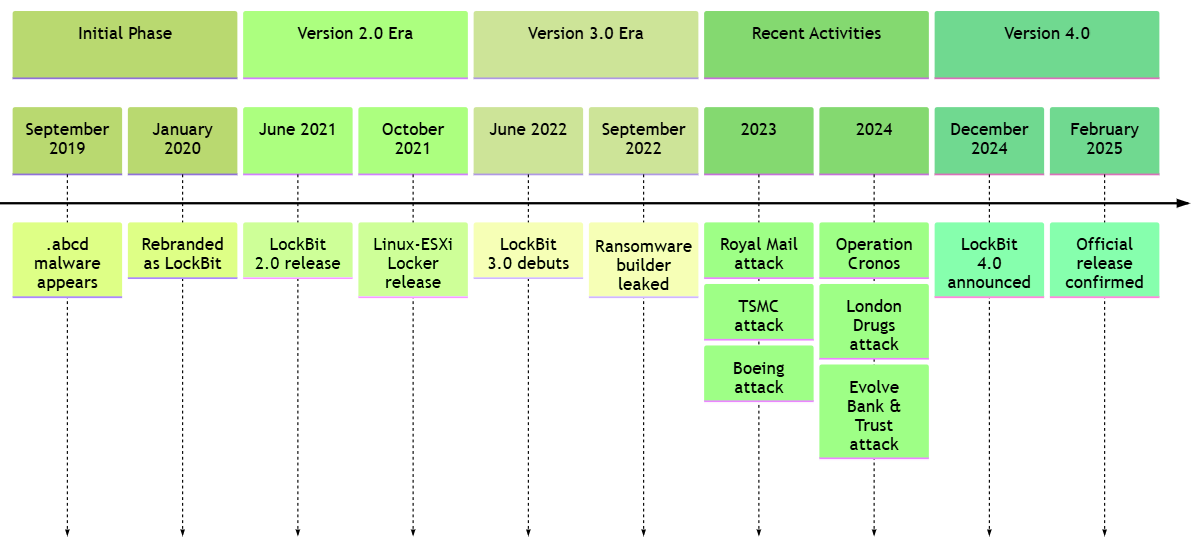
LockBit 4 RaaS: DeepInstinct researchers have published an analysis of the v4 version of the LockBit RaaS, announced at the end of last year.
Grandoreiro returns: The Grandoreiro malware operation is back up and running after some of its members were detained last year. Forcepoint has detected new large-scale phishing operations spreading the banking trojan to users in Europe and Latin America. Five Grandoreiro members were arrested in January last year in Brazil.
Crocodilus: Mobile security firm ThreatFabric has discovered a brand new and highly sophisticated Android banking trojan being distributed in the wild. Named Crocodilus, the malware can be used for overlay phishing attacks, keylogging, and for remote access and remote control operations. The new trojan was used in attacks targeting banks in Spain and Turkey and popular cryptocurrency services.
Evilginx: Sophos has published an analysis of Evilginx, a red-team tool used for phishing simulations that has become very popular with threat actors thanks to its support for interception MFA.
RESURGE web shell: CISA has published a technical report on RESURGE, a web shell installed on Ivanti Connect Secure devices via CVE-2025-0282.
SHELBY backdoor: Elastic's security team has published a report on SHELBY, a backdoor operated by the REF8685 threat actor that abuses GitHub for C&C.
Discord RAT: CyFirma looks at a recent RAT that uses Discord as a C&C mechanism. There are so many of these things that the company didn't even bother to name it.
Raton (SillyRAT): ThreatMon has published a technical report on a new remote access trojan named Raton, also known as SillyRAT, and available under a MaaS license.
Odyssey new version: Malwarebytes macOS security researcher Marcelo Rivero has spotted a new version of the Odyssey macOS infostealer.
CoffeeLoader: Zscaler has spotted a new malware loader named CoffeeLoader, which has been used in the wild since September of last year. The malware was used together and appears to bear similarities with SmokeLoader. One of the malware's unique features is its use of the GPU to run its code in an attempt to evade some security systems.
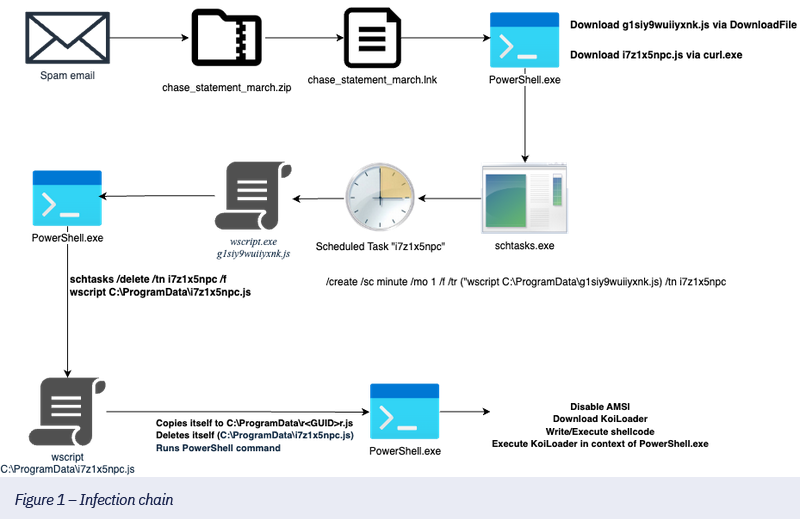
KoiLoader: eSentire has spotted a new version of KoiLoader.
Sponsor section
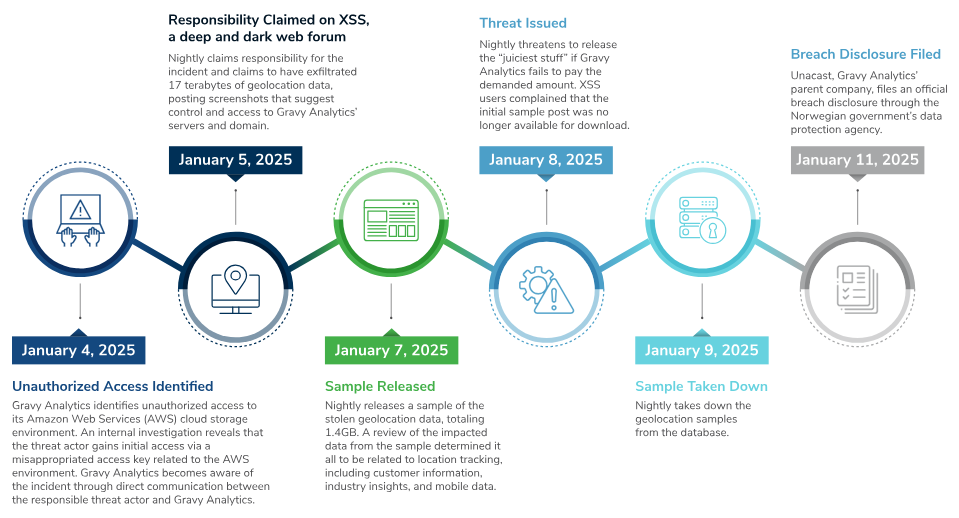
The Kroll team takes a look at the cyber risks emerging from leaks at data analytics and aggregators, using the recent leak of geolocation data from Gravy Analytics as a case study.
APTs, cyber-espionage, and info-ops
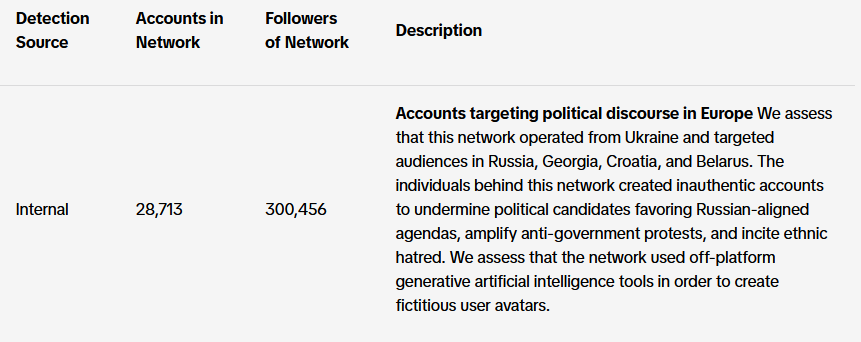
TikTok info-ops summary: TikTok has published its monthly report on covert influence operations the company has spotted on its platform in February this year. The company took down almost 30,000 accounts involved in info-ops targeting audiences in Europe and Latin America. Most of the accounts were part of a botnet operated out of Ukraine that attacked pro-Russian political figures across several countries and encouraged anti-government protests.
Gamaredon's LNK campaign: A new Cisco Talos report looks at a Gamaredon campaign targeting users in Ukraine with malicious LNK files.
"The PowerShell downloader contacts geo-fenced servers located in Russia and Germany to download the second stage Zip file containing the Remcos backdoor."
Head Mare's PhantomPyramid: A cyber-espionage group named Head Mare has targeted Russian engineering companies with a new Python-based backdoor named PhantomPyramid.
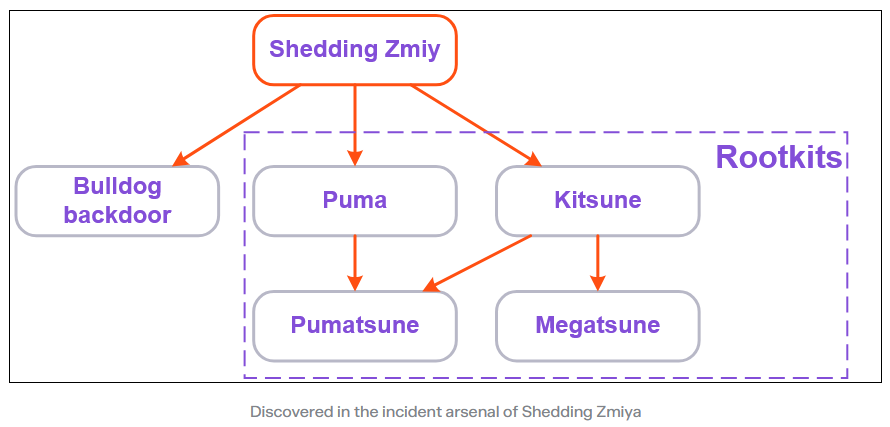
Shedding Zmiy: Rostelecom's security team has discovered new malware operated by Shedding Zmiy, a pro-Ukrainian espionage group made up of former members of the Cobalt cybercrime group. The new malware includes four new Linux rootkits (Puma, Pumatsune, Kitsune, and Megatsune) and the Bulldog backdoor. The rootkits are what Elastic also detected as PumaKit back in December.
Kimsuky's PowerShell and VBScript payloads: K7 researchers have published a report looking at recent PowerShell and VBScript payloads used by DPRK APT group Kimsuky in a recent campaign.
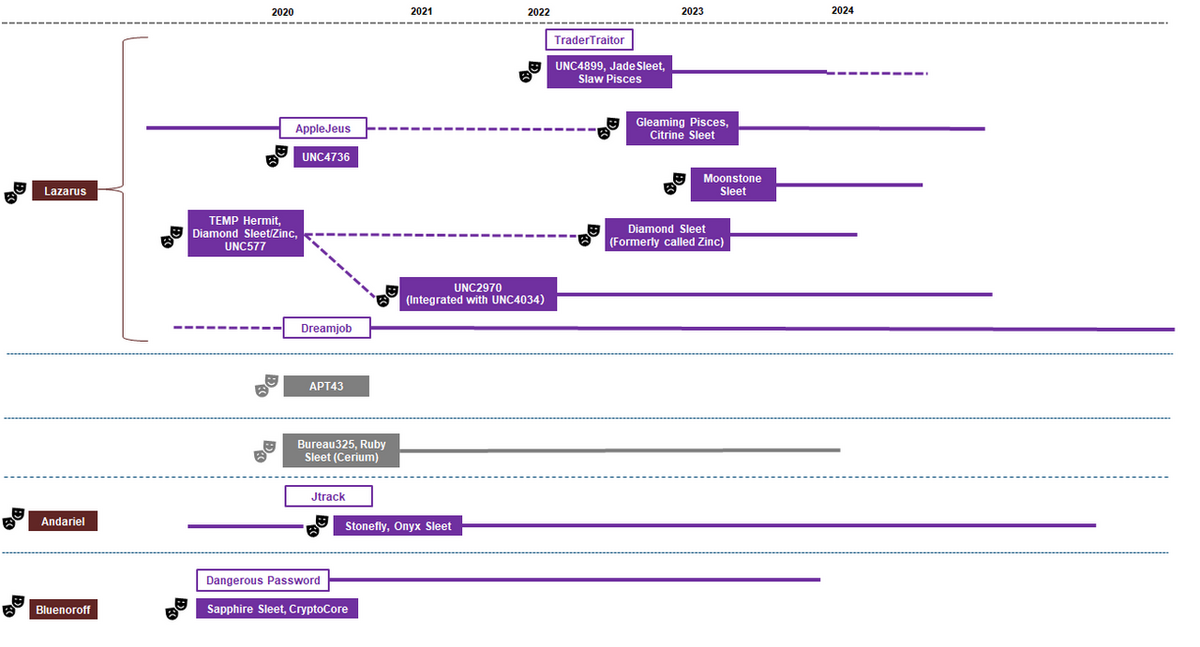
Lazarus classification: Japan CERT researchers look at the multitude of North Korean APT groups and the problem of classifying most of their activity as Lazarus.
Vulnerabilities, security research, and bug bounty
GitLab security updates: GitLab has released security updates to patch seven vulnerabilities in its main product. The one that stands out is a bug that allows users to keep their admin role even after it was revoked.
Apache Kylin security update: The Apache project has released security updates for the Kylin OLAP engine to fix an RCE attack (CVE-2025-30067).
Synology security update: NAS maker Synology has released a security update to fix an unauth attack in its NAS mail server.
WatchGuard VPN security update: WatchGuard has patched an EoP in their Windows VPN client.
Dirty COW evolution: DEVCORE security researcher "Pumpkin" has published an analysis on the evolution of exploits for the Dirty COW Linux vulnerability.
Ubuntu username bypass: Ubuntu has patched three vulnerabilities that can allow attackers with local access to create new user namespaces with full admin privileges. The bug was discovered by Qualys.
Backdoor in robot dog: Security researchers have found a backdoor in Go1, a bionic robot dog from Chinese robotics company Unitree. The undocumented backdoor resided in CloudSail, a remote access system included with the robot's firmware. An attacker with a specific CloudSail API key and the pi/123 username and password combo could access any Go1 robot. Attackers could move the devices or even access their built-in cameras. Unitree has revoked the API key but researchers urge robot owners to uninstall the CloudSail service to be completely safe. [Additional coverage in AHA and Cybernews]

Infosec industry
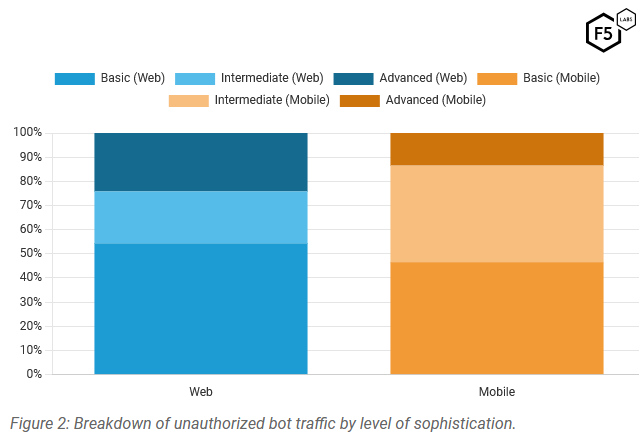
Threat/trend reports: Dr.Web, EAST (PDF), F5, and Rostelecom have recently published reports and summaries covering various infosec trends and industry threats.
New tool—Trigon: iOS security researcher Alfie CG has released Trigon, an iOS kernel exploit based on a 2023 vulnerability tracked as CVE-2023-32434.
New tool—Varalyze: Cybersecurity researcher Brayden has open-sourced Varalyze, a platform that unifies the APIs of multiple infosec tools in one backend. This includes VirusTotal, URLScan, AbuseIPDB, and more.
New tool—rkchk: Security firm Thalium has open-sourced rkchk, a Linux kernel module for detecting Linux rootkits.
0xCON 2024 videos: Talks from the 0xCON 2024 security conference, which took place last November, are available on YouTube.
Risky Business Podcasts
Tom Uren and Patrick Gray discuss how the Signalgate messages betray an alarming lack of security nous at the highest levels of the US natsec leadership. It's head-scratchingly bad.
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about why people studying cyber operations are fascinated by zero-days. These are vulnerabilities or exploits that have been found in a system before the vendor or manufacturer is made aware of them, and so, therefore, no fix exists.




