Risky Bulletin: Georgia arrests ex-security chief over bribes from scam call centers
In other news: White House has a new nomination for NSA & CyberCom head; crucial CISA employee quits; US charges 54 for ATM jackpotting attacks.

Breaches, hacks, and security incidents
UK Foreign Office hack: A suspected Chinese hacking group has allegedly breached the UK's Foreign Office in October. The culprit is believed to be Storm-1849, a known group that previously exploited multiple Cisco zero-days this year. [The Guardian]
Uzbekistan's LPR leak: Uzbek officials have left a national license plate reader system exposed on the internet without a password. Yes! You read that right. [TechCrunch]
Ransomware hits Romania's water agency: A ransomware attack has hit ANAR, Romania's water management agency. The incident impacted over 1,000 systems, such as Windows workstations, GIS servers, and databases. [Europa Libera]
Eindhoven AI leak: The Dutch data protection agency says employees of the city of Eindhoven have uploaded documents with sensitive data to AI services.
Amazon catches DPRK remote worker: Amazon CSO Stephen Schmidt says the company caught a North Korea remote IT worker masquerading as a US employee after noticing large key input delay for commands typed in its backend, something that should have not existed if the worker was based in the US as they claimed. In total, the company claims to have stopped over 1,800 North Koreans trying to get jobs at the company. [Bloomberg]
"At Amazon, we've stopped more than 1,800 suspected DPRK operatives from joining since April 2024, and we've detected 27% more DPRK-affiliated applications quarter over quarter this year."
Mobius fined for Deezer leak: France's privacy regulator has fined advertising company Mobius €1 million for leaking the data of 229 million Deezer users in 2022.
Nexpublica fined for breach: The same CNIL also fined French software company Nexpublica €1.7 million for failing to patch security flaws in its CRM software that eventually led to a security breach at the end of 2022.
La Poste cyberattack: France's national postal service was down this week following a cyberattack over the last weekend. Russian DDoS group NoName057 took credit for the incident but it's unclear if this was an opportunistic claim or if it was actually them. [IntelliNews]
LastPass 2022 hack aftermath continued this year: Password vaults stolen from LastPass at the end of 2022 were cracked and used to steal cryptocurrency as recently as this year, with the stolen funds being laundered through Russia-based cryptocurrency exchanges. [TRM Labs]
EmEditor supply chain incident: Text editor EmEditor has disclosed a security breach. Developers say a "third-party" modified the download link for its Windows installer between December 19 and 22. According to Chinese security firm QiAnXin, the malicious installer deployed an infostealer.
#SupplyChainAttack #Malware
— RedDrip Team (@RedDrip7) December 25, 2025
The supply chain attack of EmEditor leads to implantation of a fully functional infostealer in the form of a browser plugin. Malware excludes victims in regions of CIS and Iran.
Check report for more details and #IoC: https://t.co/nFhvziVr8X pic.twitter.com/hiIzv86Yqf
General tech and privacy
Docker Hardened Images are now free: Docker has made Hardened Images free for every developer. These are server images managed by Docker that are constantly updated and patched for the most recent security flaws. Devs previously needed some sort of subscription to use Hardened Images.
Piracy group leaks Spotify song database: A piracy and open-source group named Anna's Archive has leaked 256 million Spotify tracks. Spotify said it found and suspended the accounts that scraped its site.
TikTok signs divest deal: Chinese social media network TikTok has signed a deal to divest and sell its US division to a group of Trump allies. More than half the company is now owned by tech company Oracle, private equity firm Silver Lake, and Emirati-backed investment firm MGX. ByteDance and existing shareholders hold the rest. [CNN]
FTC orders Instacard refunds: The FTC has ordered Instacart to refund over $60 million to consumers for artificially raising the prices of their groceries using deceptive tactics.
Italy fines Apple over ATT: Italy's data protection agency has fined Apple more than €98 million for abusing its market dominant position to restrict competition in the iOS advertising market through its App Tracking Transparency framework.
Big Tech sues Texas: A coalition of tech companies have sued the state of Texas to block a law that would have mandated app stores to verify the age of their users on customer devices, as part of the state's new age verification law. A judge has stayed the law from entering into effect on January 1, as the court listens to the case [Houston Public Media]
Ruby 4: Ruby 4.0 is out, with support for a new just-in-time compiler and the separation of app code inside the same process.
Mozilla to let users disable Firefox AI features: After the new Mozilla CEO announced that Firefox will integrate AI features starting next year, the Firefox team clarified that users will be able to disable those features if they want to.
Something that hasn't been made clear: Firefox will have an option to completely disable all AI features. We've been calling it the AI kill switch internally. I'm sure it'll ship with a less murderous name, but that's how seriously and absolutely we're taking this. …
— Firefox for Web Developers (@webdevs.firefox.com) 2025-12-18T12:12:57.968Z
Government, politics, and policy
South Korea mandates facial scans for new phone numbers: The South Korean government is running a trial and has mandated that all individuals undergo a mandatory facial recognition scan before receiving a new mobile phone number. [Korea JoongAng Daily]
German court stops DNS surveillance: Germany's highest court has paused a provision of the country's criminal code that required telcos to monitor and log DNS queries. The court sided with Vodafone, which claimed that storing and processing this amount of data is cost prohibitive and that law enforcement agencies have other means at their disposal to fight crime. [LTO] [h/t pft]
Russia explores CoD ban: Russia's internet watchdog is looking into a possible ban of FPS game Call of Duty over its repeated portrayal of Russians as the bad guys. [Gazeta.ru] [h/t Vadim]
Denmark accuses Russia of destructive cyberattacks: The Danish government has blamed the Russian state for cyberattacks against Danish infrastructure. The Z-Pentest group allegedly attacked a water utility last year while the NoName057 group launched DDoS attacks that hit its official websites before the municipal and regional elections this year. [English statement PDF]
EU-UK data transfers deal: The EU and the UK have renewed a deal to allow free data transfers between the EU bloc and the UK for six more years.
US healthcare industry opposes new HIPAA rules: A coalition of more than 100 US healthcare organisations are asking the Trump administration to withdraw a Biden-era mandate that added new HIPAA cybersecurity requirements because it adds "new financial burdens." Ah, the US! Where you can make the government withdraw any law just because it hurts your bottom line! [DarkReading]
New NSA, CyberCom nomination: The White House has formally nominated Army Lt. Gen. Joshua Rudd as the next head of Cyber Command and the US National Security Agency. Gen. Rudd is currently serving as deputy chief of US Indo-Pacific Command. [NextGov]
After 8 months of leadership crisis, bureaucratic back & forth, and political interference, I guess you can call it a Christmas miracle.
— Alexis Rapin (@alexis-rapin.bsky.social) 2025-12-24T15:31:29.696Z
CISA suspends staffers for polygraph test: CISA has suspended six staffers who ran a polygraph test over the summer on the agency's new acting director. Madhu Gottumukkala failed the test but the DHS is investigating if the staffers were right to test him in order to grant him access to sensitive data. [Politico]
CISA loses key employee: David Stern, the CISA official behind the agency's Pre-Ransomware Notification Initiative (PRNI), has quit the agency after he was forced to relocate to FEMA's Boston office by the new DHS leadership. [CybersecurityDive]
FCC bans foreign drones: The US FCC has banned the sale of all new foreign-made drones and components on the grounds of national security. The decision comes after years of debates if the US should ban DJI, although it's now way worse.
New York passes RAISE Act: New York Governor Kathy Hochul has signed into law the RAISE Act that will require AI companies with $500 million or more in revenue to publish safety protocols and disclose safety incidents within 72 hours. Companies risk fines up to $30 million for non-compliance. [IAPP]
US sanctions disinfo experts, EU officials: The US State Department has imposed visa bans on five individuals linked to anti-disinformation work, including former EU commissioner Thierry Breton. The State Department press release seems to have been written by a nutjob who attended the Kremlin school of batshit press releases. [The Guardian]
Nina Jankowicz: “They’re not doing this because they have any evidence of censorship — they lost a Supreme Court case that made those claims… They’re doing this because the group of researchers and advocates have stood up to liars like Donald Trump and the platforms that enable them.”
— Kate Starbird (@katestarbird.bsky.social) 2025-12-24T06:33:23.867Z
American social media platforms are banned in Russia. Have you noticed Donald isn't sanctioning anyone over that?
— Darth Putin (@darthputinkgb.bsky.social) 2025-12-24T10:46:00.531Z
Risky Business podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq talk to Hamid Kashfi, CEO and founder of DarkCell, about the Iranian cyber espionage scene.
Arrests, cybercrime, and threat intel
Georgia detains ex-spy chief: The country of Georgia has arrested Grigol Liluashvili, the country's former head of the State Security Service. Officials said Liluashvili took bribes from a criminal group to ignore a network of cyber scam call centers operating across Tbilisi. [OCCRP]
Singapore arrests superyacht captain: Singapore authorities have arrested the captain of a superyacht owned by a major cyber scam mogul. Officials are investigating Nigel Tang Wan Bao Nabil for possible involvement in money laundering. [The Straight Times]
US charges 54 for ATM jackpotting: The US Department of Justice has charged 54 individuals for deploying the Ploutus malware in ATM jackpotting attacks over the past two years. The suspects are allegedly members of the Tren de Aragua cartel.

Nefilim affiliate pleads guilty: Nefilim ransomware affiliate Artem Stryzhak, 35, of Ukraine, has pleaded guilty for his attacks as part of the group.
Infosec personnel linked to ransomware attack plead guilty: Two cybersecurity experts—Ryan Clifford Goldberg from Sygnia and Kevin Tyler Martin from DigitalMint—have pleaded guilty to deploying ransomware themselves. [CyberScoop]
Interpol cracks down on African ransomware scene: Interpol and agencies across 19 countries detained 574 suspects as part of a cybercrime crackdown. Officials say they detailed individuals involved in BEC, extortion, and ransomware. They also decrypted six ransomware strains.
RaccoonO365 admin arrested: Nigerian authorities have arrested a man named Okitipi Samuel for allegedly running the RaccoonO365 phishing service. Microsoft previously seized 338 domains operated by the service back in September.
US seizes phishing backend: The US DOJ has seized web3adspanels[.]org, a website that served as a backend database for collecting phished credentials. The site primarily stored banking logins collected through phishing pages promoted via malicious search ads.
8884 admin pleads guilty: Alexis Aldair Chavez, 19, of San Antonio, Texas, has pleaded guilty to various cyber-enabled crimes. He admitted to leading 8884, an online community that sprung up from the more famous 764 group. Just like its parent group, 8884 engaged in harassment and exploitation of small children, forcing them into acts of self-mutilation, sexual activities, and even suicide.
Second ferry malware suspect arrested: Italian police have arrested a second Latvian national for attempting to plant malware on a ferry boat. A first suspect was arrested last week in France.
TechTreek admin charged: US authorities have charged Bangladeshi national Zahid Hasan with running TechTreek, EGiftCardStoreBD, and other sites for selling forged US documents..
Nigerian fraudster convicted: A US court found a Nigerian national, Olusegun Samson Adejorin, guilty of fraud and other crimes in relation to the theft of over $7.5 million from a US company in 2020.
Judge sides with WhatsApp again: A California judge has refused to lift a court injunction preventing NSO to deploy spyware via WhatsApp exploits. [The Record]
Clop goes after Gladinet CentreStack servers: The Clop ransomware and data extortion gang is allegedly breaching organizations that run Gladinet CentreStack file-sharing servers.
"This is yet another similar data extortion campaign by this adversary. CLOP is well-known for targeting file transfer servers such as Oracle EBS, Cleo FTP, MOVEit, CrushFTP, SolarWinds Serv-U, PaperCut, GoAnywhere, among others."
Vastaamo CEO cleared: A Finnish court has cleared Ville Tapio, the CEO of psychotherapy provider Vastaamo, over the company's 2019 security breach and his role in failing to secure patient data. [Helsinki Times]
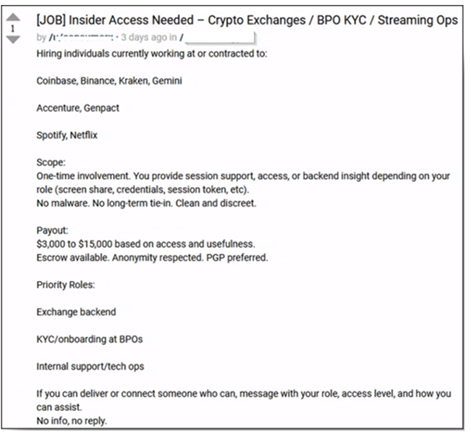
Insider recruitment schemes: Check Point raises the alarm on the growing number of cybercriminal groups running insider recruitment schemes to aid their intrusions.
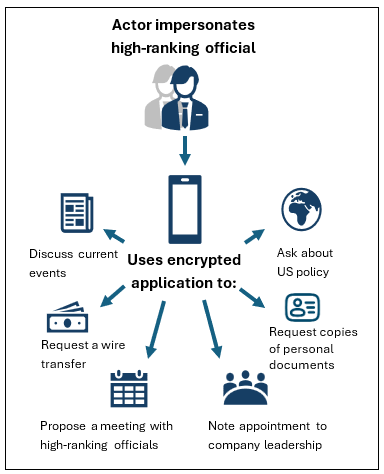
HVT phishing using government lures: The FBI says cybercrime groups are posing as government officials in attempts to social engineer executives, managers, investors, or other high-value targets that could later be swindled out of their money. The campaign has allegedly been going since 2023.
Cobalt Strike surge: Censys has noted a sudden spike in Cobalt Strike servers hosted online, specifically on the networks of AS138415 (YANCY) and AS133199 (SonderCloud LTD).
DNS root server attacks: According to DDoS mitigation service Netscout, the DNS root servers have faced at least 38 DDOS attacks this past year.
npm package steals WhatsApp messages: Koi Security has discovered a malicious npm library that was configured to steal WhatsApp credentials, message archives, harvests media and contacts, and installs backdoors.
Malicious Chrome extensions: Two malicious Chrome extensions posing as VPN apps have been spotted by Socket Security intercepting and stealing user credentials.
Two-thirds of KK Park is now demolished: The Myanmar army claims it has now blown up and demolished about two-thirds of KK Park, a notorious cyber scam compound. [Myawady]
MYANMAR: Junta claims 16 more buildings at KK Park scam compound demolished, bring total to 429 of 635 buildings. myawady.net.mm/kk-park-nyme...
— Cyber Scam Monitor (@cyberscammonitor.bsky.social) 2025-12-16T00:58:46.859Z
TrickyWonders: Group-IB has published a profile on TrickyWonders, one of the three main threat actors targeting Uzbekistan with Android banking trojans, together with Ajina and Blazefang.
Fly profile: Intrinsec believes a threat actor known as Fly is likely the administrator of Russian Market, an underground portal for selling credentials stolen via infostealers.
"In this analysis, we provided insight into the marketplace’s infrastructure and links with the threat actor known as “FLY”. This threat actor promoted the marketplace on multiple occasions and throughout the years. His username is reminiscent of the old name of the marketplace, “Flyded”. We found two e-mail addresses used to register the first Russian Market domains, which enabled us to find potential links to a Gmail account named “AlexAske1”, but we could not find additional information surrounding this potential identity."
Gig economy scams: Group-IB researchers have spotted a scam campaign targeting MENA countries with fake online jobs that seek to steal initial fees and deposits from applicants.

Malware technical reports
WebRAT: Kaspersky looks at WebRAT, a remote access trojan widely distributed via malicious GitHub repos storing cheats, cracks, and boobytrapped software tools.
AMOS: The Atomic macOS stealer, AMOS, has been on a tear recently using malicious search ads for various AI terms, such as Grok or ChatGPT.
Destructive malware: Socket Security has tracked eight campaigns spreading data destructive malware inside open-source projects over the past year.
BlackHawk loader: ESET has spotted a new malware loader named BlackHawk.
"ESET researchers have observed BlackHawk being used in spearphishing campaigns to deliver #AgentTesla, targeting hundreds of endpoints in Romanian small and medium-sized companies."
Phantom infostealer: K7 looks at new campaigns spreading the BlackHawk loader and the Phantom infostealer.
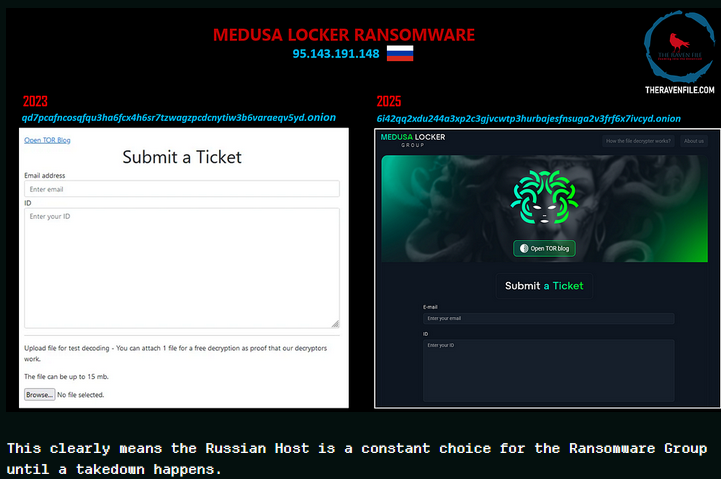
MedusaLocker ransomware: Threat intel analyst Rakesh Krishnan has published an analysis of the old Medusa Locker ransomware. Although the ransomware has been active for years, the report looks at recent samples and infrastructure. The report points out how the group's servers haven't moved for two years, absent a law enforcement crackdown. Maybe someone could get on that!
Risky Business podcasts
In this edition of Seriously Risky Business, Tom Uren and Patrick Gray talk about America's increasing dependence on Chinese manufacturers for electrical sector equipment. This doesn't seem like a good idea when China is hacking electric utilities for sabotage and PLA researchers are dreaming up ways to attack the grid.
APTs, cyber-espionage, and info-ops
Evasive Panda poisons DNS: Suspected Chinese APT group Evasive Panda has been spotted poisoning DNS requests to deliver the MgBot malware loader. Kaspersky doesn't have info on how the DNS poisoning is taking place.
New Cloud Atlas ops: Kaspersky also looks at new Cloud Atlas APT operations targeting countries in Eastern Europe and Central Asia with phishing operations.
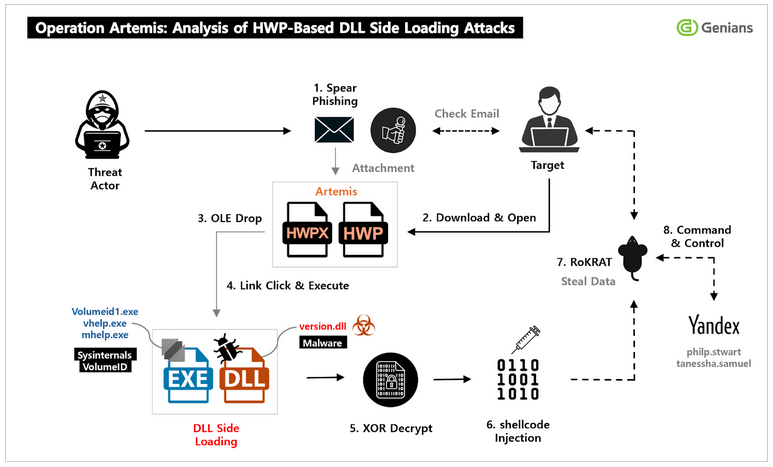
APT37's Operation Artemis targets SK: South Korean security firm has spotted an APT37 campaign targeting South Korean individuals with a clever social engineering tactic where the attackers are posing as TV producers looking for interviews.
APT36's LNK campaigns: CyFirma looks at recent campaigns from suspected Pakistani APT group Transparent Tribe (APT36) that employed LNK shortcut files to deploy its payloads.
Paper Werewolf: Intezer looks at how Paper Werewolf has used a recent WinRAR zero-day in attacks targeting Russian companies.
Moldovan "traitors" portal linked to Russia: DFRLab has linked a so-called "traitors" portal that listed pro-EU politicians to Russian disinformation efforts, state propaganda, and the infrastructure of sanctioned web host Aeza Group.
Russia's Ukrainization campaign in Armenia: Russian disinformation groups are targeting Armenian citizens with a narrative claiming that the pro-EU country is going through an "Ukrainization" process, launching veiled threats at its neighbor.
Vulnerabilities, security research, and bug bounty
Important security updates: K7, LangChain, MongoDB, n8n, NVIDIA, Speedify, WatchGuard.
WatchGuard zero-day: WatchGuard has released security patches for a new zero-day in its Firebox VPN boxes. This is tracked as CVE-2025-14733. According to the Shadowserver Foundation, there are almost 125,000 unpatched and vulnerable devices accessible on the internet.
New Fortinet exploitation: On Christmas Eve, Fortinet has published a blog post about threat actors targeting an older 2020 vulnerability, CVE-2020-12812, an auth bypass in its SSL VPN devices.

AI browsers will always be vulnerable to prompt injection: After a UK NCSC official said that prompt injection attacks may never be fully mitigated, OpenAI has apparently reached the same conclusion and said this week that AI browsers will likely always be vulnerable to these types of attacks.
Ask Gordon prompt injection: And speaking of the devil, Pillar Security has discovered a prompt injection attack in Ask Gordon, Docker's AI assistant.
Tor audit: The Tor Project went through its routine security audit. This one identified six new vulnerabilities.
MITRE sees new delays: Security researchers are reporting that MITRE is not responding or assigning new CVEs in a timely manner, sometimes seeing delays go into the realm of weeks and months.
XFE appears to be dead in the water: The IBM X-Force Exchange, the company's in-house vulnerability database that was founded even before the CVE program, appears to have been abandoned. [Brian Martin]
Infosec industry
Threat/trend reports: BlackDuck, DarkTrace, Kaspersky, LevelBlue, Red Canary, and TLPBLACK have recently published reports and summaries covering various threats and infosec industry trends.
Acquisition news: Cloud software service provider ServiceNow has agreed to acquire IoT security firm Armis for $7.75 billion in cash.
Mandia founded another company: Mandiant founder Kevin Mandia has founded a new company. The company is named Armadin and will focus on AI pen-testing. [Wall Street Journal]
Black Hat Europe videos: Talks from the Black Hat Europe 2025 security conference, which took place this month, are available on YouTube.
BSides Cape Town videos: Talks from the BSides Cape Town 2025 security conference, which took place at the start of the month, are available on YouTube.
BSides Lisbon videos: Talks from the BSides Lisbon 2025 security conference, which took place last month, are available on YouTube.
Risky Business Podcasts
The main Risky Business podcast is now on YouTube with video versions of our recent episodes. Below is our latest weekly show with Pat and Adam at the helm!




