Risky Bulletin: FBI warns of online file converters that distribute malware
In other news: China backdoors Juniper routers; ransomware wave hits Taiwan; North Korean spyware slips onto the Play Store.

This newsletter is brought to you by GreyNoise. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
The FBI says that cybercriminals are using free file format and document conversion tools to scrape personal data and deploy malware, and even ransomware.
The warning applies to online websites that convert files between different formats, but also apps that users download on their devices.
Reports of malware being added to a converted file have been around for over a decade, although no major security breach has ever been linked to a file converter.
Such incidents are usually taking place at a smaller, more personal pace. Like for example, someone getting infected with a screen-locker while traveling! (Hi there, wifey!)
While screen-lockers are a threat of the past, these days, the chances are that victims will either get ransomware or an infostealer that steals all the passwords stored on their PC.
The FBI's Denver Field Office is asking victims to report such incidents, most likely in an attempt to get a larger view of the threat and start hunting some of the actors behind it.
"If you or someone you know has been affected by this scheme, we encourage you to make a report and take actions to protect your assets. Every day, we are working to hold these scammers accountable and provide victims with the resources they need," said FBI Denver Special Agent in Charge Mark Michalek.
Risky Business Podcasts
Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
Bybit hack analysis: Security firms NCC Group and Validin published their own investigations of the Bybit $1.5 billion crypto-heist.
ESHYFT leak: ESHYFT, a job portal that allows hospitals to hire nurses paid on daily contracts, has leaked the personal data of its users via a database that was left without a password.
DieNet DDoS attacks: A hacktivist group known as DieNet has conducted DDoS attacks on two Trump businesses—his winery and golf courses—as the US President was threatening the EU with tariffs on wines. [Additional coverage in CyberDaily]
TFE Hotels cyberattack: A cyberattack has disrupted services at the TFE hotel chain for over a week. The chain says its backend and booking systems are currently offline as they work to resolve the issue. TFE is also re-routing phone lines to a central call center while its staff manually assists incoming guests. The incident has the typical fallout of a ransomware attack but no major group has yet taken credit for the attack.
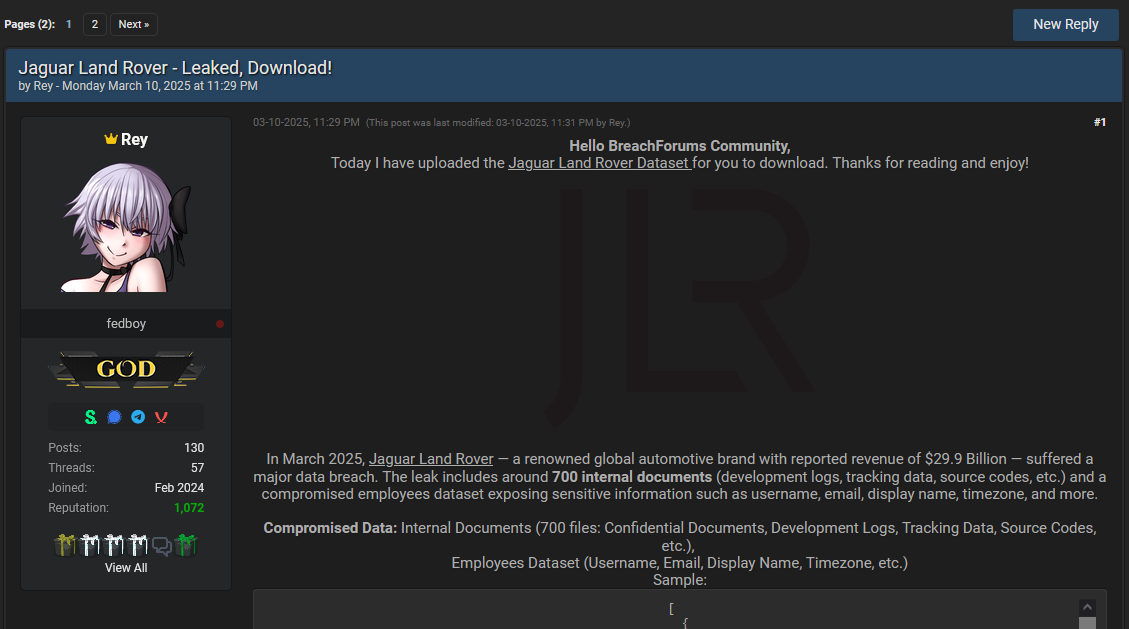
Jaguar Land Rover hack: A hacker named Rey has leaked hundreds of internal documents from the Jaguar Land Rover automotive group. The files were allegedly stolen during a breach this month. Rey is the same hacker who previously leaked data from Orange's Romanian branch, the Zurich Insurance Group, and Russian social media network VK.
General tech and privacy
NIST selects HQC: US NIST has selected HQC as the backup algorithm for post-quantum encryption operations. The agency selected last year ML-KEM to be the primary algorithm for securing data against post-quantum computing attacks. NIST says HQC is a backup standard and should be used only if a weakness were to be discovered in ML-KEM.
RIP Carl Lundstrom: One of the Pirate Bay founders, Carl Lundstrom, has passed following a plane crash. [Additional coverage in Euronews]
Meta's South Korean fine stays: South Korea's top court has rejected Meta's attempt to have a $4.6 million fine reversed. The country's privacy watchdog fined Meta in 2020 for sharing the data of 3.3 million South Koreans with third parties without authorization. This was Meta's last course of appeal. [Additional coverage in the Korea Herald]
Google-Meta spat: Google is apparently extremely mad that Meta sponsored a Utah age-verification bill that would offload the task of checking a suspected child account to play stores rather than the apps. Google may not have allies here since Apple is already doing this on its own accord.
UK sets eyes on mobile browsers: A report from the UK's markets authority found that Apple and Google are abusing their position in the mobile browser market.
ICANN to retire SU domains: ICANN will retire the .SU top-level domain in 2030. The domain was previously assigned to the now-defunct Soviet Union and is currently managed by Russian authorities. The SU country code was removed from the ISO standard in 1992 but ICANN has never acted on the removal until 2022. Another domain that could also be on the chopping block is .IO, the domain for the soon-to-be-non-existent British Indian Ocean Territories. [Additional coverage in DomainNameWire]
Government, politics, and policy
Spain to fine companies for unlabelled AI content: The Spanish government passed a bill this week to impose massive fines on companies that use unlabelled AI-generated content. Failure to comply with the law could lead to fines of up to €35 million or up to 7% of their global annual turnover. The law is meant to curb the spread of deepfakes and nonconsensual adult content. Spain is the first country in the EU bloc to incorporate provisions from the EU AI Act into its national legislation. [Additional coverage in Yahoo News]
Kazakhstan introduces children SIM cards: The Kazakhstan government has introduced SIM cards specifically designed for the use of children. All parents will be required to buy and deploy the new SIM cards to their children's devices. The cards come with built-in filters to restrict access to dangerous websites and social media. The cards also report a child's location to parents through a special app. [Additional coverage in Zakon]
Signal stops working with Ukrainian government: Secure messaging app Signal has stopped responding to requests from the Ukrainian government related to Russia's abuse of the messenger to target its soldiers and officials. Something here tells me that Ukraine might have tried to get Signal to take down some Russian accounts, something that Signal doesn't do. [Additional coverage in The Record]
DHS shuts down AI and cyber boards: The US Department of Homeland Security has shut down eight advisory boards, including two dedicated to AI and cybersecurity. The boards provided niche expertise to DHS officials on their respective topics. The DHS cited a Trump executive order signed after he took office that mandated agencies to cut costs. [Additional coverage in Bloomberg]
FCC launches national security council: The FCC has established a national security council to counter foreign adversaries targeting US telecoms. [Additional coverage in CybersecurityDive]
Senators call for US cyber offensive against China: A group of Republican senators has asked President Donald Trump to increase US offensive cyber operations against China. The attacks are to be a response to recent Chinese intrusions into US telcos, critical infrastructure operators, and the US Treasury. The Senators say the US needs to reestablish deterrence against China.
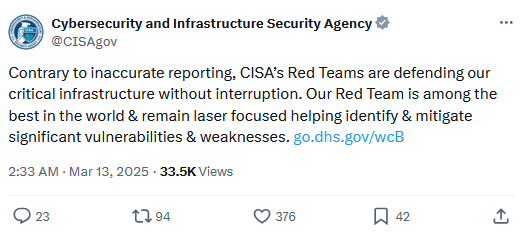
CISA denies, denies, denies: In typical Kremlin fashion, CISA has denied firing its red teams even after reports from former CISA red teamers.
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Andrew Morris, founder of security firm GreyNoise. Andrew talks about the major trends in mass internet scanning and exploitation, as per GreyNoise's yearly threat report.
Arrests, cybercrime, and threat intel
Zservers profile: Intel471 has published a profile on the Zservers bulletproof hosting provider that got smacked and seized by law enforcement last month.
"The personas triplex560 and ZserverS have not been active on cybercrime forums since the sanctions were announced. However, other threat actors responded to the sanctions. On the Exploit forum, one predicted Zservers would rebrand itself as a new player in the hosting market."
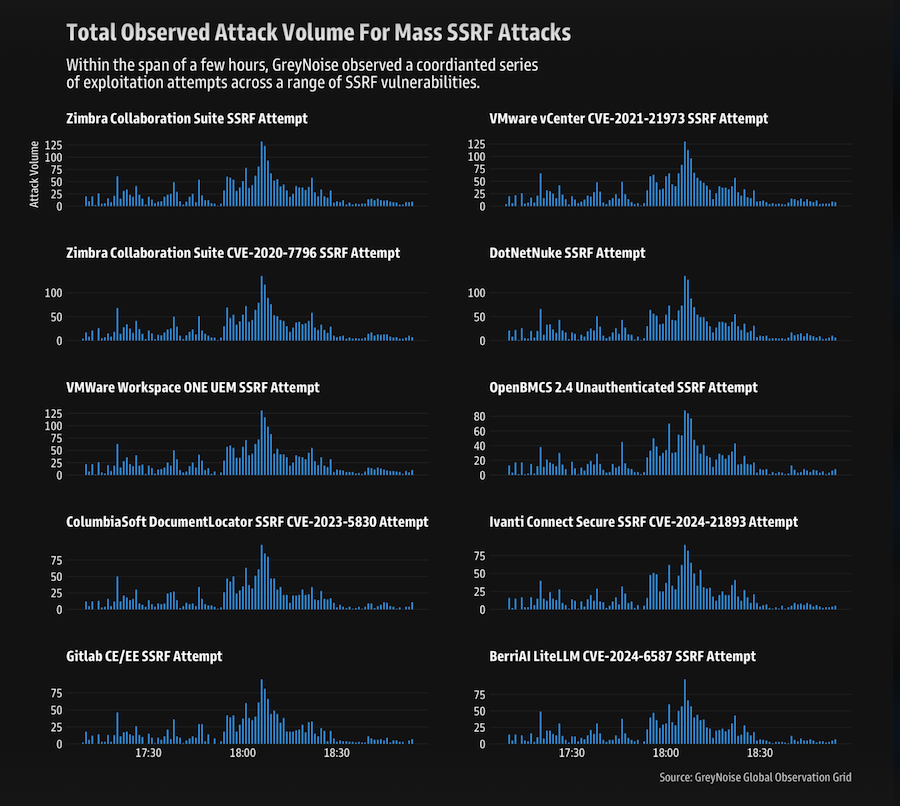
SSRF exploitation wave: Security firm GreyNoise has detected a coordinated campaign exploiting SSRF vulnerabilities across several software products. The spike began on March 9 and originated from a group of 400 IP addresses. Attacks targeted SSRF bugs in GitLab, VMware, Ivanti, Zimbra, and many other software. GreyNoise says the "pattern suggests structured exploitation, automation, or pre-compromise intelligence gathering."
GE MUSE attacks: Forescout says two botnets are targeting GE Healthcare MUSE Cardiology Information Systems (CIS). The catch—they're deploying ELF binaries on Windows, so there's no infection on the Windows-based system where MUSE runs.
Ruthless Mantis: Security firm Prodaft published a pretty hefty report on Ruthless Mantis, a well-known ransomware affiliate group specializing in double-extortion attacks. The group has worked with Ragnar Locker, INC Ransom, Qilin, Lynx, and many others.
Head Mare and Twelve: To pro-Ukrainian hacking groups have allegedly joined forces for attacks on Russian companies, according to Kaspersky.
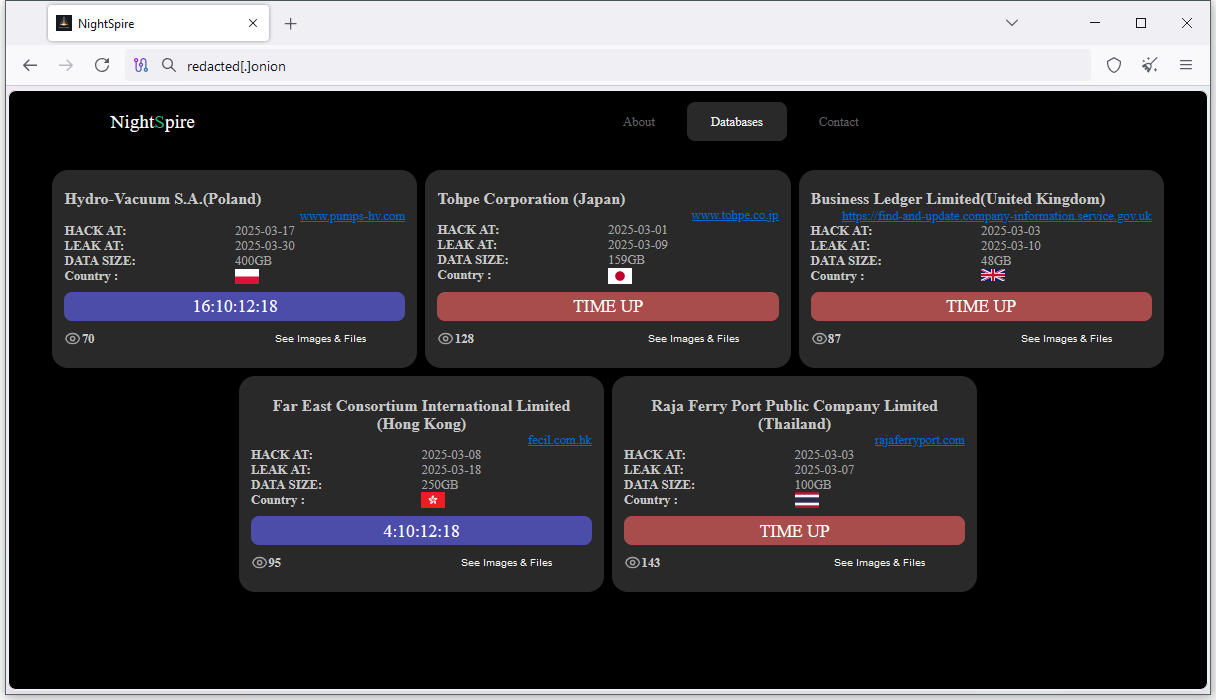
New NightSpire ransomware: A new ransomware group named NightSpire launched operations this week. The group has already listed 12 victims on its leak site. Most of the victims are from Europe and East Asia.
Fake Reddit campaign: Moonlock researchers have spotted a campaign using fake Reddit and WeTransfer pages to spread the LummaStealer and AMOS infostealers.
Investment scam campaign: Palo Alto Networks looks at a crypto-investment scam that targets users in East African and Asian countries that appears to originate from Singapore.
Booking.com campaign: Microsoft takes a look at a malware delivery campaign that uses Booking.com-looking websites and ClickFix to trick victims in the hospitality sector into infecting themselves with malware.
CSS abuse: Cisco Talos looks at how threat actors are abusing CSS code to hide "dangerous" parts of an email and avoid detection and how they're adding tracking code to see how users interact with the content. I know! The technique is old, but the blog post goes over recent variations.
LinkedIn recruiting scheme hack IR: Software developer Ron Jansen published a blog post about how he was hacked via one of those LinkedIn recruiting schemes.
"The tasks given were so trivial that even asking why these tasks would matter would be more work than actually just doing them. So, I implemented a few tiny changes, shared them, and was done within about 5-10 minutes. I remember when running npm install && npm run start having a very brief thought about whether this would be a stupid thing to do - as I'd heard about supply chain attacks before."
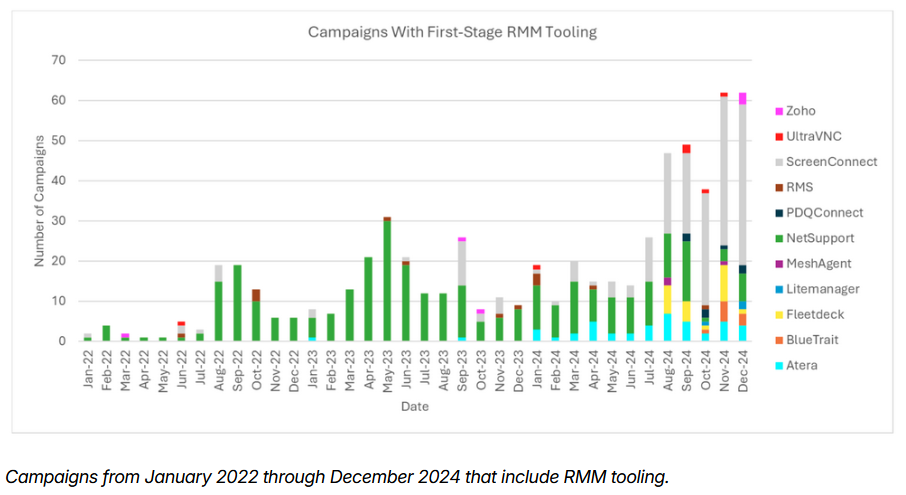
Rise in RMM as a first-stage payload: Proofpoint is seeing an increase in the use of remote monitoring and management (RMM) tools as an initial payload in email-delivered campaigns. The increase comes with a decrease in the use of malware loaders and botnets that were previously popular with attackers. The most common RMM tools seen in attacks include ScreenConnect, NetSupport, and Atera.
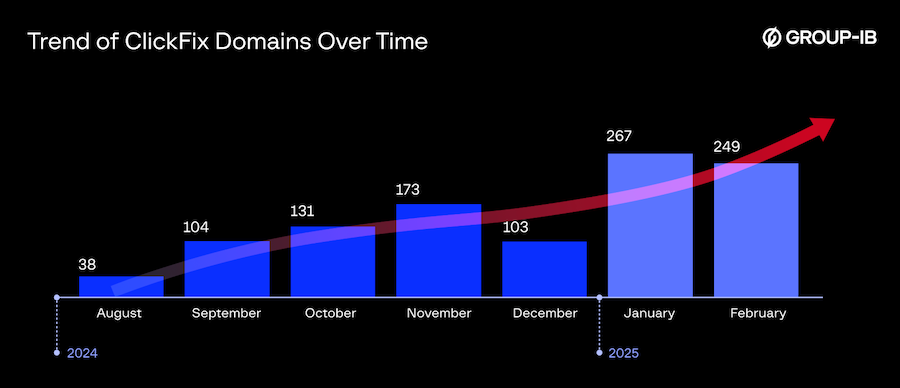
ClickFix technique gains adoption: Group-IB researchers have seen an increase in domains hosting ClickFix social-engineering pages over the past few months.
Malware technical reports
DocSwap: S2W has published a technical report on DocSwap, a new Android malware strain used to target the cryptocurrency space. The company has linked the malware to a possible DPRK group it tracks as puNK-004.
Medusa ransomware: In a recent security advisory, CISA and the FBI say the Medusa ransomware operation has made over 300 victims in critical sectors since its launch in June 2021.
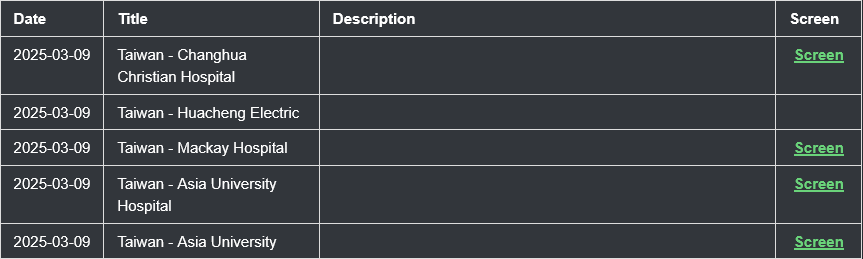
CrazyHunter ransomware goes after Taiwan: A new ransomware operation named CrazyHunter is targeting organizations in Taiwan's critical sectors. The group has ransomed three hospitals, a university, and a power grid operator since the start of the month. The Taiwanese Health Ministry says it already restored core functions at the targeted hospitals.
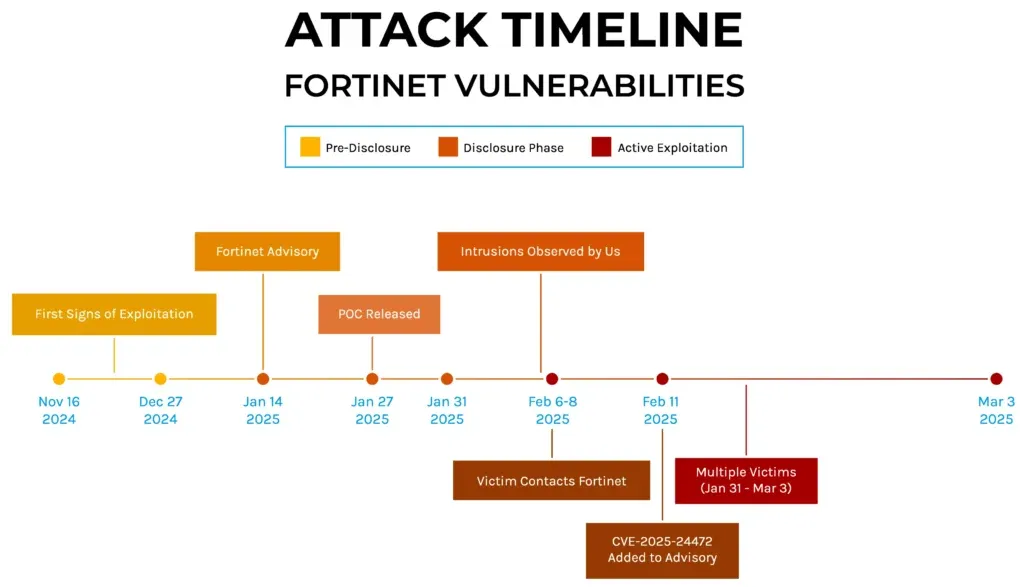
SuperBlack ransomware goes after Fortinet devices: A new ransomware gang named SuperBlack is exploiting two recently patched Fortinet vulnerabilities to gain access to corporate environments. The first attacks took place in late January after proof-of-concept was released for one of the bugs. Security firm Forescout has linked the ransomware to a former LockBit affiliate known as Mora_001.
Sponsor section
Attackers are automating exploitation at scale, targeting both new and old vulnerabilities — some before appearing in KEV. Our latest report breaks down which CVEs were exploited most in 2024, how ransomware groups are leveraging mass exploitation, and why real-time intelligence is critical.

APTs, cyber-espionage, and info-ops
Lazarus spotted on npm again: Socket Security has spotted new malicious npm packages on the npm index linked to North Korean hacking group Lazarus. The company says the packages are part of the group's Contagious Interview campaign, where Lazarus hackers approach developers with job interviews and ask them to debug or work with the malicious packages. The packages are still available both on npm and on GitHub. They contain code designed to steal credentials and deploy a backdoor on the infected host.
APT37 on the Play Store: North Korean hacking group ScarCruft has managed to sneak spyware on the official Google Play Store. The spyware was hidden in an app for file management designed for English and Korean-speaking users. Named KoSpy, the spyware could collect messages and call logs, device locations, keystrokes, record audio, and take silent photos using the device's camera. Security firm Lookout found KoSpy samples going as far as 2022.
Konni: South Korean security firm ENKI looks at a Konni malspam campaign delivering the AsyncRAT via Dropbox and Google Drive.
UNC3886 targets Juniper routers: A Chinese cyber-espionage group has exploited a zero-day (CVE-2025-21590) to deploy backdoors on Juniper MX routers. The attackers used legitimate credentials to access the device and then used the zero-day to bypass security protections and install the backdoor. Google's Mandiant division linked the attacks to a group it tracks as UNC3886. The group has been active since 2021 and previously also exploited zero-days in Fortinet and VMware ESXi systems. Its attacks mainly focus on defense, technology, and telecommunication organizations located in the US and Asia. Juniper released security updates for the affected products, even if they were End-of-Life since 2022. The Juniper team also released a 35-page technical document on the attacks.
Volt Typhoon: Chinese espionage group Volt Typhoon spent almost a year inside the network of a major Massachusetts water and electricity provider without being detected. Security firm Dragos detected the Chinese APT after spotting suspicious traffic going to Chinese IP addresses. The utility provider rebuilt its entire IT network to get rid of Volt Typhoon and its backdoors.
Vulnerabilities, security research, and bug bounty
Windows zero-day abused since 2023: A zero-day patched this week by Microsoft has been secretly exploited in the wild since March 2023. Attackers deployed the zero-day (CVE-2025-24983) on systems already infected with the PipeMagic backdoor. The zero-day was used to obtain admin access and take full control of the system. ESET says the zero-day only worked on systems before Windows 10, such as Windows 8 and Windows Server 2012.
FreeType zero-day: Threat actors have exploited a zero-day (CVE-2025-27363) in the FreeType font-rendering library. The attacks were detected by the Facebook security team. The zero-day resides in how the FreeType library parses font sub-glyph structures from TrueType GX and variable font files.
GLPI RCE: Lexfo researchers have found a pre-authentication SQL injection vulnerability in the GPLI open-source IT management solution. The vulnerability can be used for RCE attacks.
Apache Tomcat write-up: A security researcher known as Buherator has published a write-up and PoC for an Apache Tomcat remote code execution vulnerability (CVE-2025-24813) patched this week.
Auracast hijack: ERNW has published a write-up on a Samsung phone bug that can be used to hijack the Auracast Bluetooth audio casting feature.
PAN security updates: A day late after everyone else, Palo Alto Networks released its own batch of Patch Tuesday security updates.
Cisco security updates: Cisco also did one of these one-day later Patch Tuesdays. They fix ten bugs.
GitLab security updates: And so has GitLab. The company has patched eight issues.
Infosec industry
Threat/trend reports: Bitdefender, CIS, CyberArk, Kaspersky, NZ NCSC, PT Security, and ReversingLabs have recently published reports and summaries covering various infosec trends and industry threats.
New tool—Capchan: Orange's SensePost has released Capchan, a tool to solve image CAPTCHAs using image classification.
New tool—FBI Watchdog: DarkWebInformer open-sourced FBI Watchdog, a tool that monitors domain DNS changes in real-time, specifically detecting law enforcement seizures.
Risky Business Podcasts
Tom Uren and Patrick Gray discuss how X is actively engaging in political interference outside the US. The risks mirror those of TikTok. American legislators moved against TikTok because it could potentially be a powerful tool for the Chinese government to interfere with American political discourse. X is a realized threat, not a potential one, so we expect that foreign governments will start to consider a ban.
In this edition of Between Two, Nerds Tom Uren and The Grugq talk about what Europe should do given that US security guarantees are evaporating. Should Europe grow its cyber capabilities, what would it get out of it, and how should it go about doing it?




