Risky Bulletin: FBI IC3, Verizon DBIR, Google M-Trends reports are out—here's the conclusions!
In other news: Iran tries to hack EU official; Lazarus Groups pulls off watering hole and zero-day attack; WhatsApp adds new chat privacy features.

This newsletter is brought to you by Devicie. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
There are a handful of seminal reports in the cybersecurity industry, and lo and behold, three of them were released on Wednesday.
Mandiant's team, now part of Google Cloud, released M-Trends, Verizon released its Data Breach Investigations Report (aka DBIR), and the FBI Internet Crime Complaint Center (IC3) released its yearly Internet Crime Report [PDF].
Big day for chart lovers!
— Catalin Cimpanu (@campuscodi.risky.biz) 2025-04-23T14:30:08.131Z
All put together, amount to an astounding 256 pages, or the equivalent of a damn book. But don't worry because we got you covered. Below are extracts of the most important conclusions, trends, and talking points from each report.
Google Cloud M-Trends
This report is based on Mandiant IR engagements, so its results are highly representative of the upper echelons of IT networks. Think of multi-nationals, highly public incidents, government agencies, big crypto hacks, and loads of (Google) cloud-related incidents.
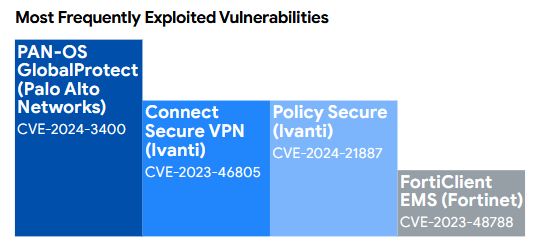
Naturally, the initial vectors for these are different from mom-and-pop shops. These companies have loads of networking gear, so exploits targeting these devices are a common source of problems, along with your regular phishing attacks.
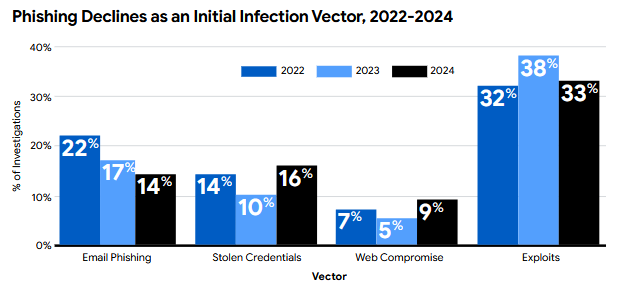
Probably some reader: But Catalin, exploits don't refer to networking devices. They also include OS exploits.
As I was saying... the same networking/enterprise gear from previous years continues to haunt these high-end targets.
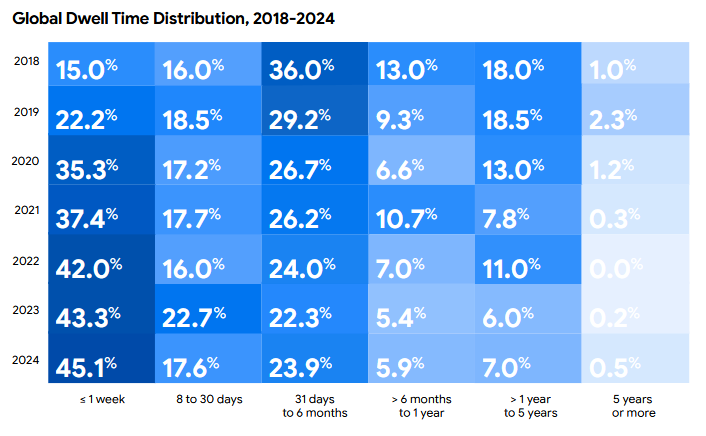
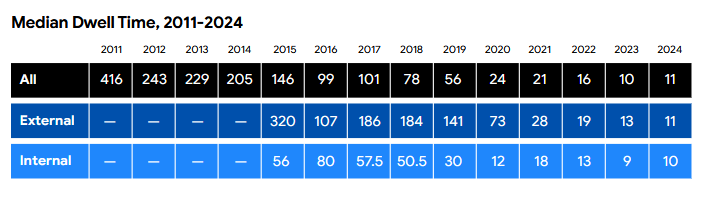
This report became famous primarily because everyone kept citing its "attacker dwell time" statistic since it was one of the first reports to consistently feature it. Now, every infosec company has their own dwell time stat, but I digress... here's this year's stat. This is consistent with other reports published earlier this year, which also saw dwell times go down again. The reason here is that MDRs and NDRs are getting better, so attackers can't set up tents and wait until they go through all victims/data. They either go YOLO and hack the hosts, or they sell access to them before they get detected and booted off.
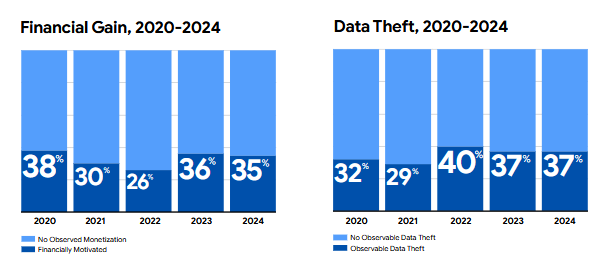
No particular big change here, but some interesting stats.
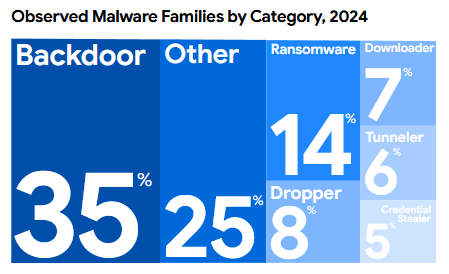
Backdoors, including web shells, are usually the first thing deployed, so it's normal they're so prevalent.
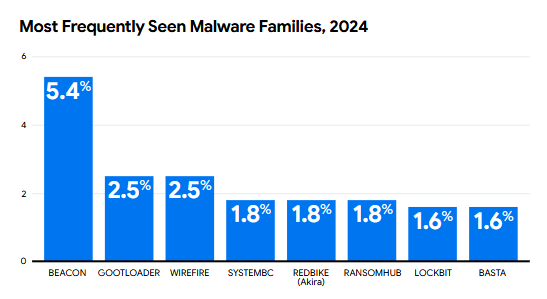
Long live Cobalt Strike! However, that number went down from 28% in 2021 to just 5% last year.
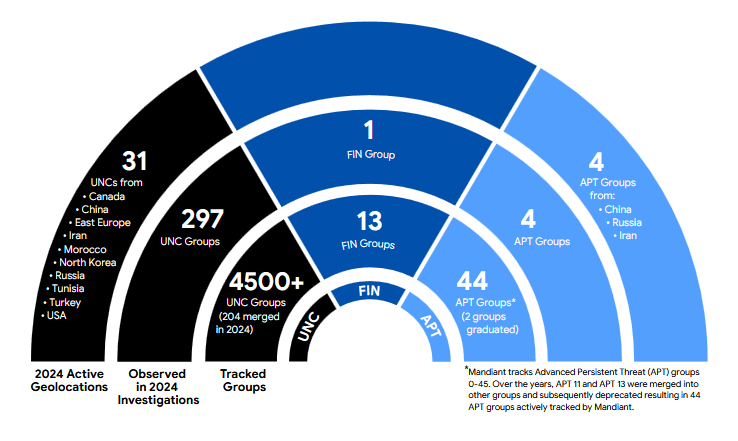
Threat actor distribution.
Some interesting findings on ransomware-related initial entry vectors. I know brute force is popular; I just didn't expect it to be this common.

As for the report, it also warns of several rising trends. These include the still-growing infostealer scene and the credentials-for-sale market they created, the threat posed by DPRK IT workers, and Iran's ever-growing hacking arsenal.
Verizon DBIR
When it comes to Verizon's report, this one aggregates results from multiple industry partners. This year, the report included data from over 22,000 security incidents from organizations all over the place.
We start with the same initial entry vector, but since we're not looking at data from the best of the best, initial entry vectors are more equalized here. However, Verizon mentions something that aligns with M-Trends, namely that vulnerability exploitation saw a big spike last year.
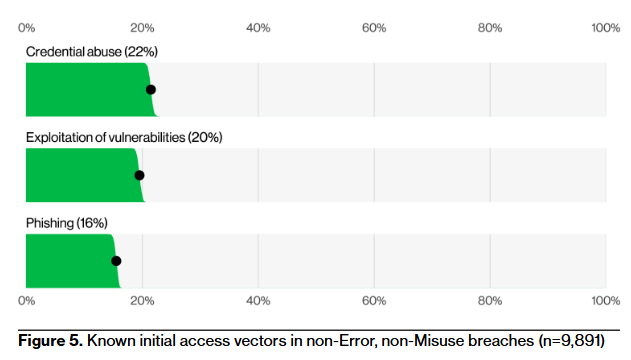
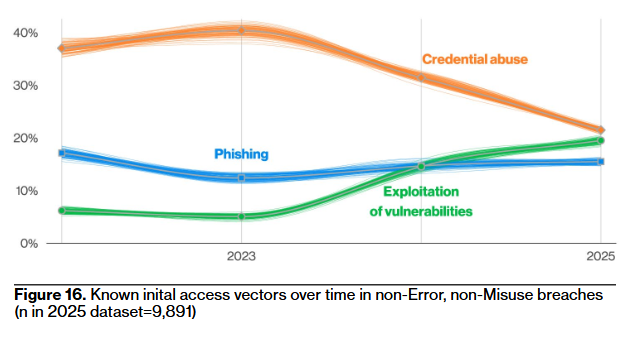
Some stats where words work better than a chart:
- Half of the corporate systems that were infected with infostealers were not managed via corporate servers, so the infection went unnoticed by companies. Gotta love BYOD!
- A third of systems advertised on underground credential shops are corporate systems.
- Third-party companies now account for 30% of breaches, so be careful who you contract with.
- 44% of all breaches involved ransomware last year.
- The median paid ransomware is $115,000, down from $150,000 in 2023. You can thank the proliferation of backups for this one, but also math... because Verizon drew from a larger and more international sample this year. Ok, maybe thank math first, then backups.
- 60% of breaches involved a human interaction, such as phishing, social engineering, and so on. This is actually down from 80% in 2021. So, automation is... working?
- The line is blurring between state-sponsored espionage and financial attacks, which now involve both 28% of the time.
- 15% of employees used genAI services, possibly leaking corporate data.
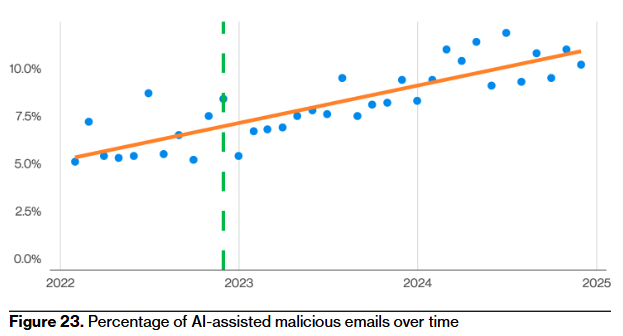
And since we're talking about AI, it looks like someone has found a good use for it... </s> I kid. It's only rose from 5% to 10%. It's not really that prevalent.
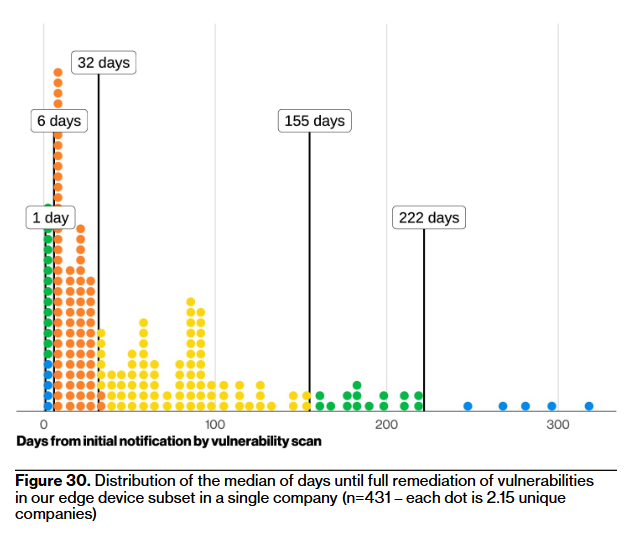
The Verizon team allocated some space to look at perimeter edge devices.
"First, the good news. The messaging around the criticality of these edge vulnerabilities is clearly getting through to defenders. There is a clear indication of organizations fully remediating those edge vulnerabilities more often (54%) over this past year when compared with all vulnerabilities listed on the CISA KEV list (38%) or even all vulnerabilities identified in their scans (a measly 9%)."
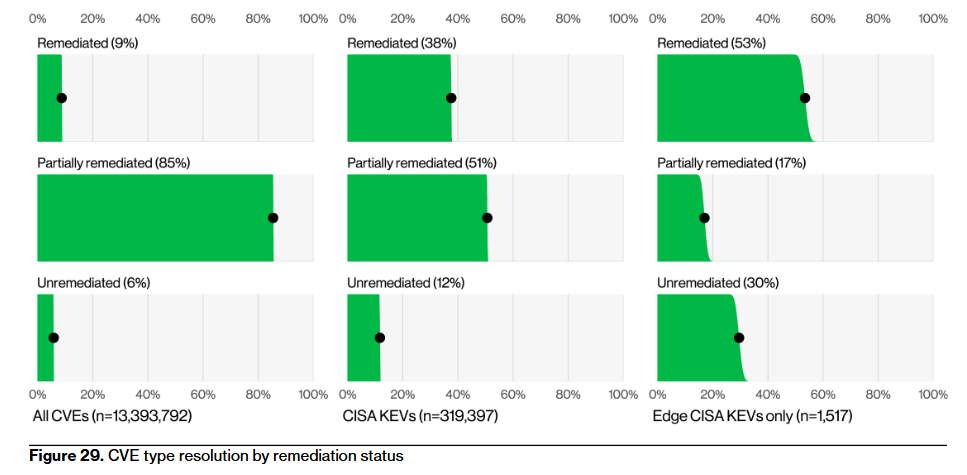
But even if they're patched, they're not patched fast enough, with the median time being 32 days, which is quite a lot.
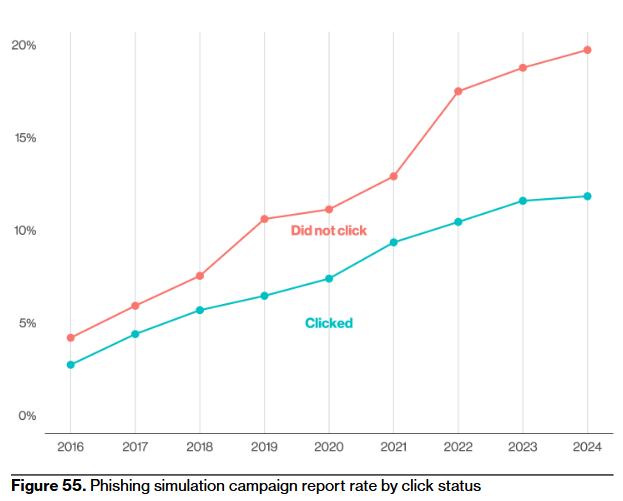
Maybe I was blind in previous years, but this is the first time I've noticed a phishing test statistic in DBIR. After I noticed the numbers, I wish I hadn't seen it, though.
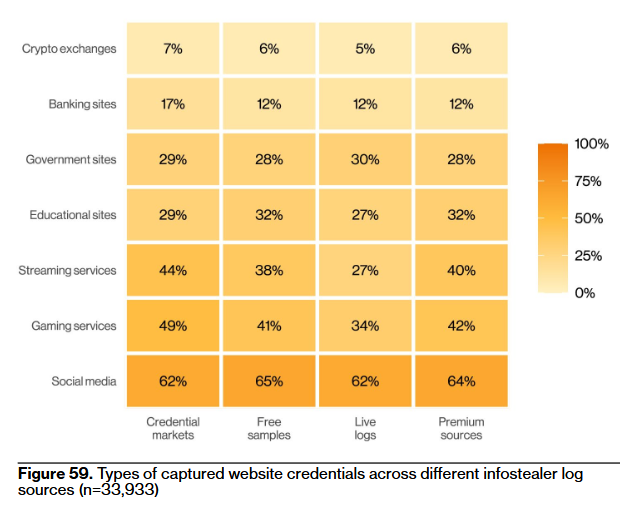
I mentioned login credentials sold online earlier, and I found a breakdown of that study Verizon was mentioning.
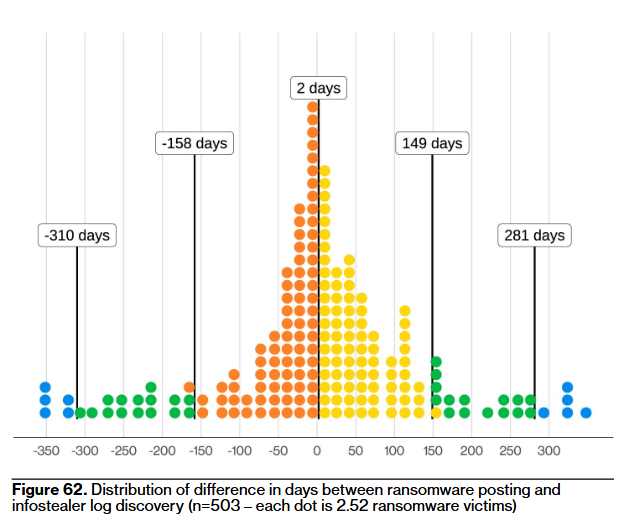
That same study of infostealer logs also looks if they play any role in ransomware attacks. The study found that 54% of ransomware victims had credentials show up online, but many appeared after they were ransomed, while other credentials were available for sale for almost a year before their incident—so I don't think this proves anything.
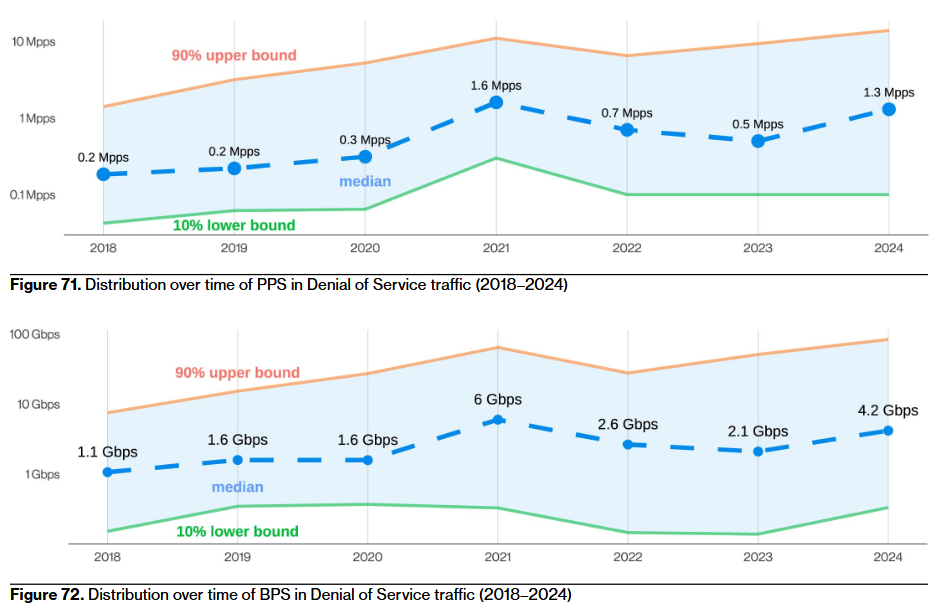
I mentioned in an earlier newsletter that Akamai was reporting that DDoS attacks are getting bigger. Here's Verizon's super nice chart to confirm it from their side.
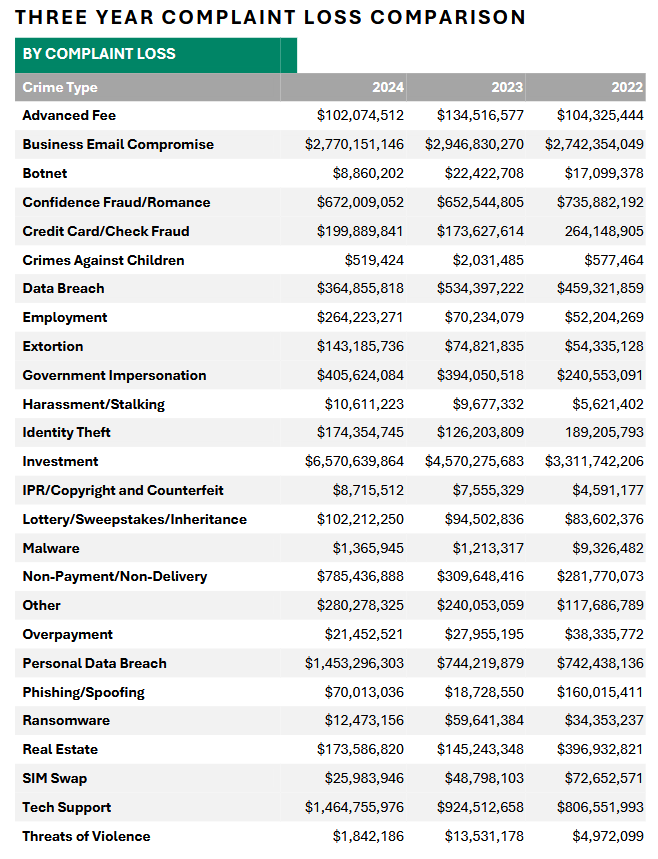
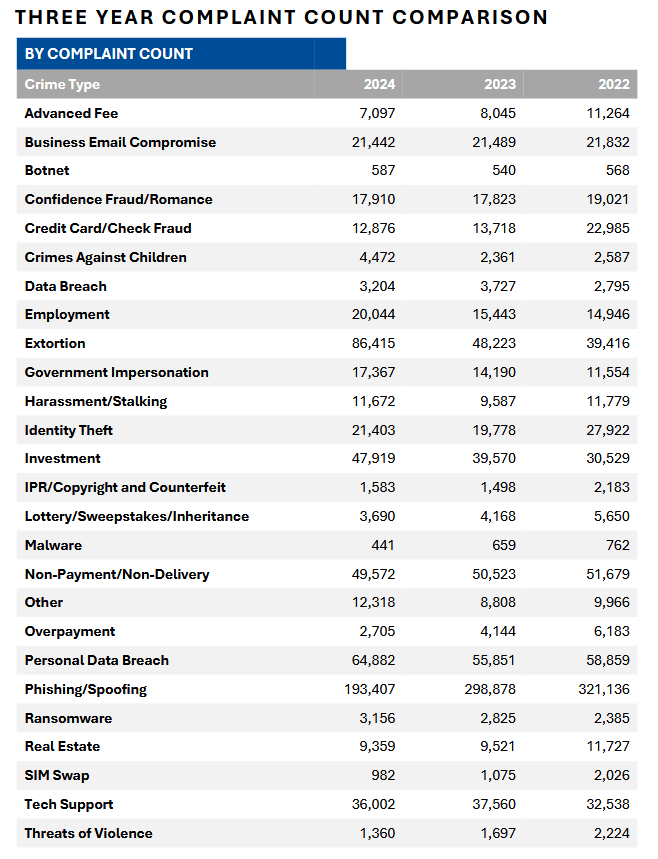
FBI IC3 Internet Crime Report
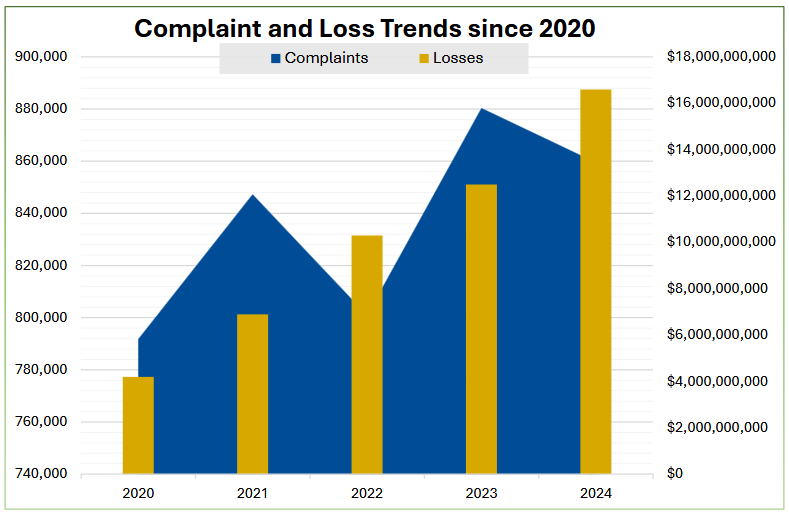
And finally, we get to the granddaddy of all infosec reports, the IC3 Internet Crime Report. Here's the basic stats:
- $16.6 billion in losses (up from $12.5 billion)
- For the third year in a row, investment scams accounted for most losses ($6.5 billion, up from $4.5 billion).
- BEC was second, don't worry. BEC is still lucrative as hell. This year with $2.7 billion, although down from $2.9 billion.
- $9.3 billion of the total losses took place via crypto, beating the USD for the first time.
While a few years back, we were kind of unaware of the reason why investment scams managed to overtake BEC as the primary source of losses, we now know it's because of the explosion of cyber scam compounds (formerly referred to as pig butchering farms) across Southeast Asia.
As things are going in the region, and seeing that the UN is reporting that these scam compounds are spreading globally, I don't see anyone knocking down investment scams from the top spot anytime soon.
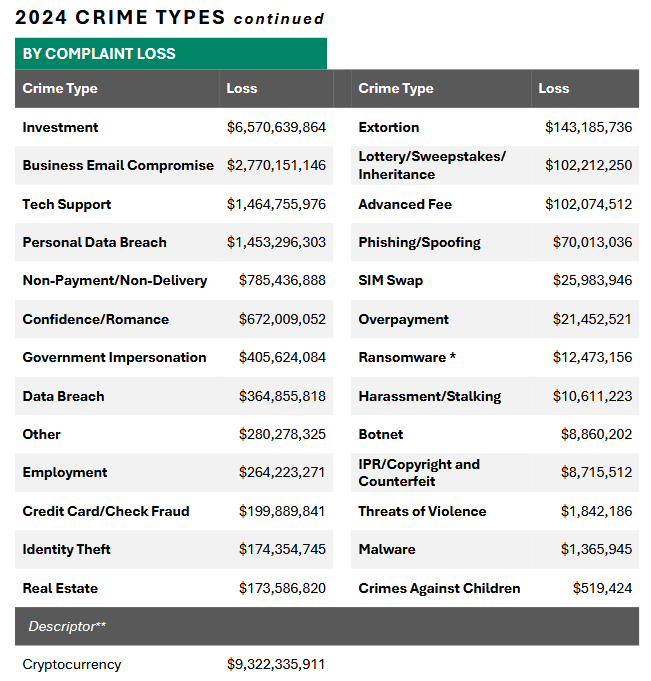
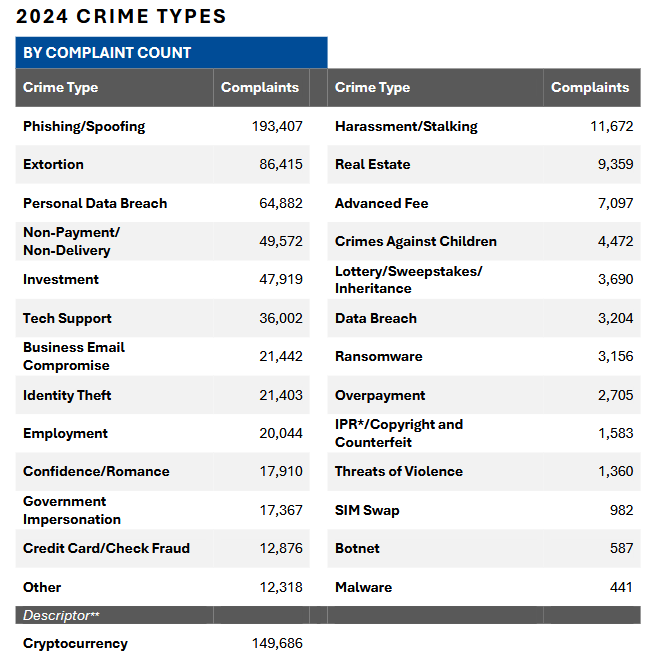
Below are the five most important tables from the report. They're raw numbers, but they tell good stories.
Risky Business Podcasts
Tom Uren and Adam Boileau talk about how scam compound criminal syndicates are responding to strong government action by moving operations overseas. It's good they are being affected, but they are shifting into new countries that don't have the ability to counter industrial-scale transnational organized crime.
Breaches, hacks, and security incidents
StarCraft 2 hacked to play disturbing videos: Players are hacking StarCraft 2 servers to show disturbing videos to other players. Players reported seeing videos of mass shootings, fascist symbols, and videos designed to induce an epileptic seizure. According to Reddit reports, the hacks have been taking place for almost a year. Blizzard says it's already working on a fix. [Additional coverage in Kotaku]
Blue Shield's Google Analytics leak: The California branch of US healthcare provider Blue Shield misconfigured its Google Analytics script and sent sensitive health data to Google servers. The leak lasted for three years until it was noticed in January 2024. Over 4.7 million users were affected. Blue Shield says it can't determine what was leaked for each individual user, but leaked data includes names, home addresses, and medical and insurance details.
UIS DDoS attacks: The IT Army of Ukraine has conducted a multi-day-long DDoS attack on Russian telecommunications provider UIS (Unique Intelligent Services). The company is one of the largest IP telephony providers on the Russian market, with over 15,000 business customers. UIS has confirmed the attacks in multiple Telegram posts. According to VK social media posts, customers were unable to make any calls during the attacks.
🎯 72 hours of blackout. For 3+ days, Russian comms provider UIS—used by 15,000 businesses—was crippled by DDoS. Voice, CRM, analytics: offline. Clients panicked, support silent. 👏 Respect to the planners—and every volunteer who kept systems alive. That’s real pressure. #Resist #Join ✊🇺🇦
— IT Army UA (@itarmy-ua.bsky.social) 2025-04-23T16:48:53.255Z
General tech and privacy
WhatsApp adds more chat privacy options: Meta has added new security features to its WhatsApp messaging service to enhance the privacy of private chats. The new features allow users to block chat participants from exporting sensitive chats or downloading shared images or videos to their devices. Users will also be able to block content shared in these secure chats from being used to train AI models. The new feature, named Advanced Chat Privacy, is currently rolling out.
Facebook cracks down on spam: Meta has updated Facebook systems to deprioritize spammy content that flood out real creators.
Ubisoft sued for forcing gamers to go online: Privacy org noyb has sued Ubisoft for forcing all its users to connect to the internet before launching any of its games. Noyb says the company does this even if the game does not have any online component, only to be able to track customers at all times. Ubisoft has over 37 million monthly active users and is behind popular gaming franchises like Assassin's Creed, Far Cry, Watch Dogs, and Prince of Persia.
AFRINIC takeover attempt: A South African news site was sued and disappeared off the face of the internet after it exposed a campaign from a Chinese-Singaporean billionaire to take control of AFRINIC and its IPv4 address space.
BlueSky restricts Turkish accounts: BlueSky has restricted access to 72 accounts in Turkey at the request of the government at the start of the month. The request came during massive anti-government protests after Turkish officials detained President Erdogan's main political rival. The accounts are invisible to Turkish audiences but still live on the platform. Ankara officials cited "national security and public order" for the block request. This is the first time BlueSky has censored accounts at the request of a government. [Additional coverage in TechCrunch]
Government, politics, and policy
Iran targets the EU's delegation chair: Iranian hacking group APT42 tried to hack German politician Hannah Neumann, the head of the EU's Iran delegation. The attacks took place in January, and the group posed as an FBI agent. They used phone calls and messages to pressure staff to open malicious emails and run malicious documents laced with malware. The APT42 group was previously linked to Iran's Revolutionary Guard Corps. [Additional coverage in Politico Europe]
EU fines Apple, Meta: The European Union has fined Apple and Meta €500 million and €200 million, respectively, for violations of the EU Digital Markets Act.
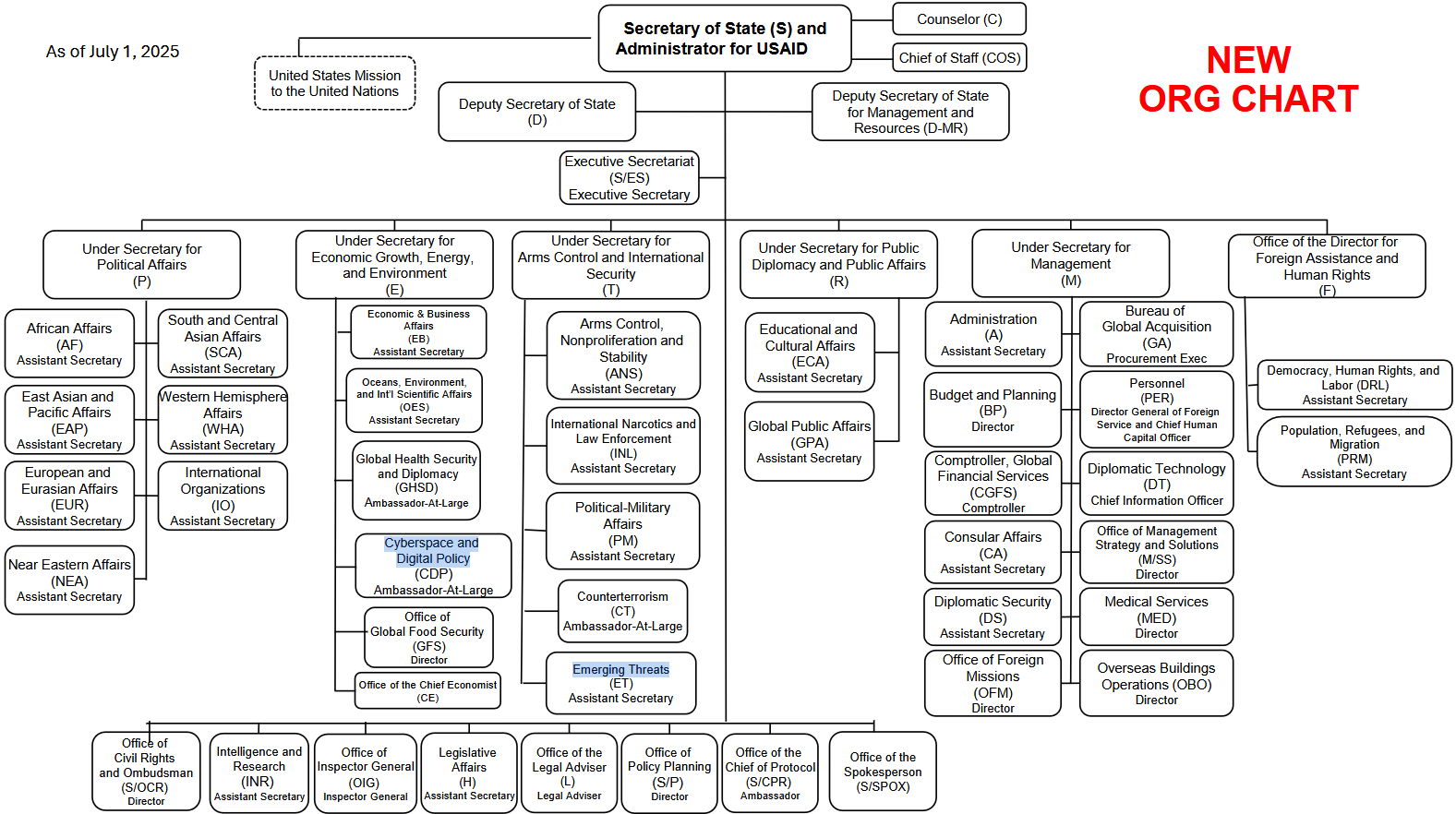
US State Department buries cyber office: The US State Department is reorganizing its internal structure and has made changes to its cyber diplomacy offices. The Bureau of Cyberspace and Digital Policy was moved lower in the structure under its economic affairs wing. The Department also created a new Bureau for Emerging Threats under its arms-control wing that will also have cybersecurity adjacent attributions. According to CybersecurityDive, the new org chart is a sign the US is deprioritizing global cyber diplomacy efforts.
Sponsor section
In this Risky Bulletin sponsor interview, Shane Harding, CEO of Devicie, talks to Tom Uren about trends in the enterprise software and security market that he thinks will have huge impacts. Software is becoming smarter and aims to solve problems rather than simply provide capabilities, and Microsoft has embarked on a big push into the SME security market.
Arrests, cybercrime, and threat intel
Disney hacker gets three years: A former Disney World employee who hacked the company's menu software was sentenced to three years in prison. Michael Scheuer added profanity to the company's menus, removed allergen information, and changed wine regions to the locations of known mass shootings. Scheuer was arrested last year and pleaded guilty in January. The defacements were spotted after the menus were printed but before they were shipped to restaurants.
Court hacker arrested: Australian authorities have arrested a 38-year-old Sydney man for allegedly hacking the New South Wales court system and stealing sensitive documents. [Additional coverage in ABC]
ToyMaker profile: Cisco Talos has published a profile on ToyMaker, a known initial access broker who compromises victims and sells access to data extortion groups. Their most common customer appears to be the Cactus ransomware group. They are also the developers of a backdoor known as LAGTOY (or HOLERUN).
Power Parasites campaign: Silent Push looks at Power Parasites, a campaign using deceptive websites, social media groups, and Telegram channels to target Asian users with job and investment scams.
M365 campaign: Fortra analyzes a phishing campaign targeting the email accounts of Microsoft 365 orgs.
Darcula PhaaS: Netcraft has a profile on Darcula, a PhaaS platform that has grown to become one of the largest phishing kits on the market.
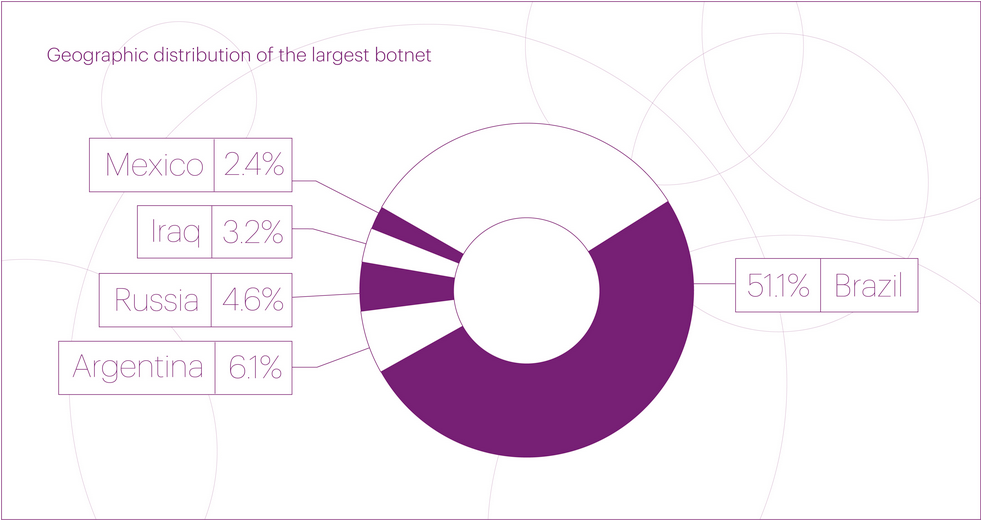
Mysterious DDoS botnet: Qrator Labs says it spotted last month a massive botnet consisting of over 1.33 million devices used in DDoS attacks against online betting portals. The company says this is the largest DDoS botnet it has ever seen.
Malware technical reports
DslogdRAT: Japan's CERT looks at DslogdRAT, a web shell deployed on hacked Ivanti Connect Secure devices—typically via CVE-2025-0282, a zero-day that was patched earlier this year. These initial attacks were linked to Chinese APT UNC5221, but it's unclear if DslogdRAT is their malware, or may belong to a different group.
Sponsor section
No race. No pressure. Just a better way forward to Windows 11, built for wherever you're at and wherever you're going. Visit devicie.com/windows11.

APTs, cyber-espionage, and info-ops
APT-C-27 (Golden Rat): Qihoo 360 has spotted new desktop malware attacks from APT-C-27, a Middle East APT with a history of attacking Syrian opposition parties and Turkish organizations.
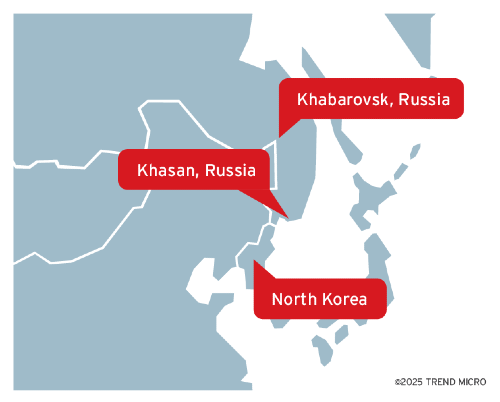
Void Dokkaebi (Famous Chollima): North Korean hackers are using a range of Russian IP addresses for offensive cyber operations. Trend Micro says the IPs are registered to two Russian companies based in two cities near the North Korean border. The IPs are used by rogue North Korean IT workers based out of China, Russia, and Pakistan. They were also used by a North Korean APt named Void Dokkaebi in cyber attacks against the cryptocurrency sector.
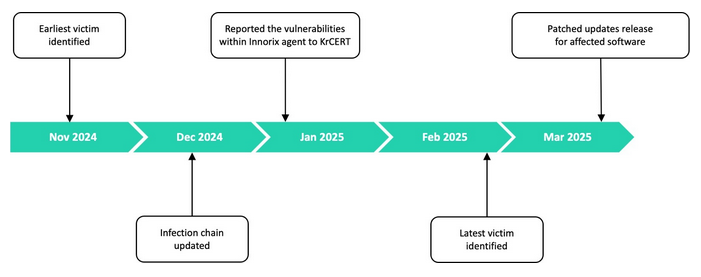
Lazarus' Operation SyncHole: North Korean hackers used a watering hole attack and a zero-day vulnerability to infect employees at major South Korean tech companies. The attacks took place at the end of last year and exploited a zero-day in CrossEx, a security tool used in South Korea to secure enterprise browser environments. Targets were lured to a hacked website where they exploited the CrossEx zero-day to deploy malware on the victim's systems. Kaspersky attributed the attacks to North Korean APT, the Lazarus Group.
Vulnerabilities, security research, and bug bounty
Active! Mail zero-day: Threat actors are exploiting a zero-day (CVE-2025-42599) in Active! Mail, a popular Japanese email service provider. The zero-day allows attackers to take over webmail servers using specially crafted requests. The vendor patched the issue last week. There are no details available about the attacker.
SAP NetWeaver zero-day: A threat actor is exploiting a zero-day in SAP NetWeaver servers to gain access to enterprise networks. Security firm ReliaQuest first spotted the attacks earlier this week. SAP has released a security advisory for customers but no official patch. The attackers are exploiting a lack of authentication in a server component that allows them to upload web shells on SAP NetWeaver instances. The zero-day (CVE-2025-31324) has a CVSS severity rating of 10 due to its ease of exploitation.
Zyxel patches firewall RCE: Taiwanese equipment vendor Zyxel has released a security update to fix a two-bug combo that could be abused for remote code execution attacks. The security updates are available for the company's USG FLEX H series firewalls, one of the company's most successful enterprise products. Zyxel credited Italian researchers Alessandro Sgreccia from HackerHood and Marco Ivaldi from HN Security with finding the bugs.
Commvault RCE: watchTowr Labs has found an RCE bug (CVE-2025-34028) in the Commvault enterprise backup solution. The bug appears to affect only a cutting-edge release of the product and doesn't impact most of the userbase.
Harden-Runner sudo bug: Sysdig has published a technical report on a bug they found in Harden-Runner, a popular GitHub action. The bug would have allowed attackers to evade the disable-sudo security restriction and run commands with sudo privileges on a CI/CD pipeline.
FastCGI bug write-up: Synactiv has published a technical breakdown of a memory corruption bug (CVE-2025-23016) in the FastCGI web server interface.
"Considering FastCGI is mostly used inside embedded equipment with poor system protections (no ASLR or NX as an example), this could be used to achieve remote code execution with the help of a misconfiguration from the developper exposing the socket, or, more realistically, through the help of another vulnerability of type SSRF within his own web application."
New UAC bypass technique: Security researcher RBC has published details on a new UAC bypass technique that abuses a folder created by the Intel graphics driver.
NVBleed attack: A team of academics has discovered a side-channel attack named NVBleed that can leak data from NVIDIA NVLink, a technology used to interconnect GPUs in multi-GPU environments, such as cloud systems.
Infosec industry
Acquisition news: DevSecOps company Socket Security has acquired AppSec company Coana.
MITRE EMB3D 2.0: MITRE has released version 2.0 of EMB3D, a threat model specifically designed for embedded devices.
New tool—Cloud Snitch: Infinite Athlete CTO Chris Brown has released Cloud Snitch, a tool inspired by the macOS Little Snitch tool and which tracks AWS account activity. The tool's source code is also available on GitHub.
New tool—Nimhawk: Security researcher Alejandro Parodi has released Nimhawk, a command & control framework written in Nim.
New tool—Curing rootkit: Security firm ARMO has released Curing, a Linux rootkit that abuses the io_uring I/O interface.
Threat/trend reports: FBI IC3 (PDF), Ghost Security, Google Cloud, GreyNoise, Microsoft, Palo Alto Networks, Qrator Labs, Radware, Verizon, VulnCheck, and Wallarm have recently published reports and summaries covering various infosec trends and industry threats.
Risky Business podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq discuss whether cyber operations can be 'strategic' and affect the fate of nations.
Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and Adam at the helm!




