Risky Bulletin: F5 says an APT stole source code, vulnerability reports
In other news: EU MEP files criminal complaint against Hungary PM over hacking; bulletproof hoster shuts down due to political reasons; PowerSchool hacker sentenced to four years.

This newsletter is brought to you by Nebulock. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
F5 (formerly F5 Networks), one of the largest US tech companies and a member of the S&P 500, has disclosed a security breach this week, in an incident that is in contention for the year's biggest hack award.
Details about the breach have been in flux since it was disclosed, so we put together a list with all we know happened so far.
- The company disclosed the breach via an SEC filing on Wednesday, October 15.
- The hack was detected in August, but disclosure was delayed at the request of the US DOJ, on the grounds of national security concerns.
- The company blamed the hack on "a highly sophisticated nation-state threat actor."
- A Bloomberg report cited sources blaming the intrusion on Chinese hackers.
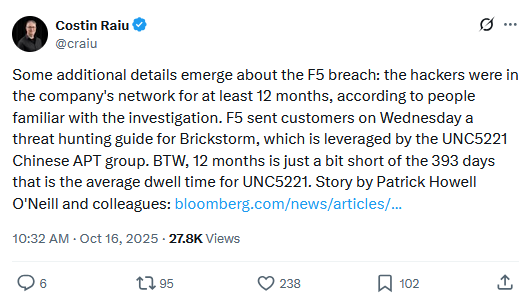
- The same Bloomberg article says F5 sent customers a guide on how to find and remove the Brickstorm malware.
- Google Mandiant published a report on this malware in September and linked it to UNC5221, a sub-group of Silk Typhoon APT, an infamous Chinese state-sponsored hacking operation.
- F5 says the hackers gained access and maintained "long-term, persistent access to certain F5 systems."
- Those systems included F5's engineering knowledge management platform and the development environment for F5's main product—the BIG-IP load balancer.
- F5 says the hackers stole the source code of BIG-IP products and reports on privately reported vulnerabilities.
- A day after disclosing the hack, F5 released patches for a bunch of vulnerabilities believed to have been stolen by the attackers.
- For the moment, F5 said it had no evidence of attacks exploiting the stolen vulnerabilities.
- F5 also rotated credentials across all its systems. This also covered rotating signing keys and certificates used by its software. This was done to prevent the hackers from compiling their own "backdoored" BIG-IP firmware and deploying it to BIG-IP devices across the world.
- Since BIG-IP appliances are literally everywhere, CISA also issued an emergency directive and ordered all federal agencies to patch F5 devices by October 22.
- CISA also acted weird on a call for no reason, because people in the US have clearly lost their minds these days.
- The UK cybersecurity agency also issued its own warning, urging local companies and government agencies to patch.
- GreyNoise noted a spike in scans for BIG-IP devices shortly after the hack was disclosed.
- The alleged hackers behind the breach have a history of targeting networking devices, so the BIG-IP source code and vulnerability reports are likely to be put to good use.
- That Google Mandiant report on UNC5221 mentioned that the group had been on a hacking spree this year, with other hacks targeting companies in the legal and tech sectors, such as SaaS platforms and business outsourcers.
- The group was in F5's network for almost a year, which means they're pretty good at avoiding detection, and companies should read that Mandiant report as soon as they can and start scanning their networks too. If they're lucky, they can be the next F5 and get some MASSIVE press coverage!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
Risky Business Podcasts
The main Risky Business podcast is now on YouTube with video versions of our recent episodes. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
Capita fined for ransomware attack: The UK's privacy watchdog has fined outsourcing company Capita £14 million ($18.7 million). The company was found at fault for a 2023 ransomware attack that exposed the personal details of 6.6 million customers. The UK ICO initially planned to fine the company £45 million ($60 million) before Capita accepted liability.
MuniOS ransomware attack: A ransomware attack has disrupted MuniOS for several days. The platform allows US local and state governments to share bond offering documents to obtain financing for their projects. According to Bloomberg, the site has been down for several days and has already disrupted some financing campaigns.
Prosper breach: Hackers stole the personal details of 17.6 million users from loan company Prosper in a breach last month.
Mango breach: Spanish clothing giant Mango has had user data stolen from a third-party marketing provider. The stolen data included names, emails, country, ZIP codes, and telephone numbers. [Additional coverage in Revista Capital]
LocalMind breach: Austrian AI startup LocalMind has been offline for 11 days following a security breach. Hackers gained access to a LocalMind beta instance, pivoted to the main servers, and then emailed all customers and partners. The attackers also accessed some customer environments. LocalMind responded by taking down its cloud infrastructure and rebuilding all its network from scratch.
Hyperliquid user has a bad day: Hackers have stolen $21 million worth of assets from a user of the Hyperliquid exchange. The incident was traced back to a private key leak. [Additional coverage in CoinTelegraph] [h/t Celecao44]
NY car insurance hacks: The state of New York has secured $14.2 million in settlements from eight car insurance companies for security breaches that exposed the data of more than 825,000 New Yorkers. All the companies used an insurance price quote tool that pre-filled forms with customer data that hackers later stole. Some of the stolen data was later used to file for COVID-19 unemployment claims.
HPN breach settlement: Plaintiffs have walked away with $50 million from a class-action lawsuit filed against the Heritage Provider Network over a 2023 breach that exposed the details of 3.4 million patients. [Additional coverage in DataBreaches.net]
Four airports were hack: Hackers have defaced screens and taken over PA systems at four airports across North America on Tuesday. The attackers broadcast messages praising Hamas and attacking US President Donald Trump and Israeli Prime Minister Benjamin Netanyahu. Incidents were reported at Harrisburg International Airport in Pennsylvania and three airports in Canada (Ontario, Kelowna, Victoria). [Additional coverage in CNN]
🍉 Kelowna and Victoria airports hacked Tuesday night with pro-Hamas and anti-Trump messages broadcast over PA systems and displayed on screens. #FreePalestine
— Bruce Dean (@brucedean1957.bsky.social) 2025-10-16T12:18:24.047Z
General tech and privacy
Tor to remove Firefox AI features: The Tor Project will remove all of the AI features that Mozilla has been recently adding to Firefox as a safety precaution for Tor Browser users.
Zorin OS 18: Linux distro Zorin OS released v18 on October 14, the day that Microsoft retired Windows 10. The distro is widely known as the most Windows-friendly Linux distro and is for those making their first migration to Linux.
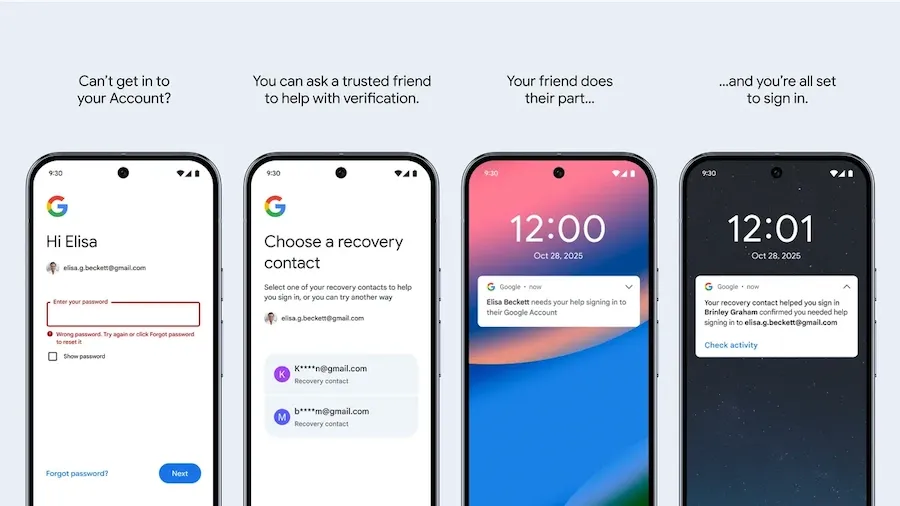
Google adds "Recovery Contacts" feature: Google has released a new feature named Recovery Contacts that will allow users to recover their accounts using the help of a friend or family member. The feature is intended for situations when users lose their phone or passkey device. When this happens, Google will send a code to a friend or family member that can then be relayed back to the account owner and recover their account.
Government, politics, and policy
Senator calls out Cisco: Louisiana Senator Bill Cassidy has sent a letter [PDF] to Cisco CEO Chuck Robbins and requested more information about two zero-days (CVE-2025-30333 and CVE-2025-20362) exploited in the company's products by suspected Chinese state-sponsored hackers. [Additional coverage in The Record]
The FBI's secret Group 78 task force: Two reports in Le Monde and Zeit described Group 78, a secretive FBI task force that was set up to dissuade the Russian government from protecting its cybercriminals. The group's operations and tactics appear to have annoyed European law enforcement so much that some think that Group 78 might be behind the recent Black Basta leak, although there's no actual evidence for this. [Also see Martin Untersinger's BlueSky thread]
Very interesting story by @zeit.de & @lemonde.fr, on how the European and the US law enforcement agencies recently clashed due to the FBI´s secret unit´s dubious guerilla tactics used to hunt down the infamous Russian cyber gang Black Basta www.zeit.de/digital/2025...
— Norman (@noaasm.bsky.social) 2025-10-16T07:01:41.543Z
China hacked UK's classified system... maybe: The UK government has refuted a media report that Chinese hackers breached its classified information system. The Times newspaper claims that Chinese hackers breached UK classified networks and maintained access for over a decade. The hackers allegedly accessed data classified as "official-sensitive" and "secret." This included diplomatic cables, government policy documents, and private communications. Former NCSC CEO Ciaran Martin described the report as "categorically untrue."
EU MEP files criminal complaint over hacking: A Member of the European Parliament has filed a criminal complaint against Hungary's Prime Minister Viktor Orban over an attempted hack. German Green MEP Daniel Freund claims the Hungarian Secret Service tried to deploy spyware on his device in May of last year. The incident was detected by the EU's cybersecurity team and linked to spyware developed by Israeli surveillance vendor Candiru. Freund has been one of Orban's biggest critics in the EU. [Additional coverage in Politico Europe]
Sponsor section
In this Risky Business sponsor interview, Tom Uren talks to Damien Lewke, CEO and founder of Nebulock, about countering adversary use of AI… with AI. They talk about how threat actors are rapidly adopting AI and what defenders should be doing in response.
Arrests, cybercrime, and threat intel
PowerSchool hacker sentenced: A 20-year-old from Massachusetts was sentenced to four years in prison and three years of supervised release for hacking the PowerSchool education cloud platform. Matthew D. Lane stole the personal details of 70 million students and teachers from PowerSchool's servers last year. Lane received a $2.85 million ransom from PowerSchool and later also tried to extort individual school districts. He was caught earlier this year and pleaded guilty. The judge also ordered him to pay $14 million in restitution to PowerSchool for the damages he caused. [Additional coverage in CyberScoop]
SMS blaster trial starts in Paris: Six suspects accused of sending SMS scams using an SMS blaster device are set to go on trial next month in Paris. They were arrested in December 2022 and are expected to reach plea deals to reduce their possible sentences. The group was run by a Chinese man and also included the owners of a local SMS marketing firm. [Additional coverage in CommsRisk]
Microsoft disrupts Vanilla Tempest operations: Microsoft has revoked 200 certificates used by the Vanilla Tempest group to sign malware in ransomware attacks. The certificates were being used to sign apps that posed as legitimate software distributed via poisoned search results. The Vanilla Tempest group is more widely known as Vice Society and has been active for several years. It has been a customer of multiple ransomware-as-a-service platforms, and the recent attacks were deploying the Rhysida ransomware strain.
In early October 2025, Microsoft disrupted a Vanilla Tempest campaign by revoking over 200 certificates that the threat actor had fraudulently signed and used in fake Teams setup files to deliver the Oyster backdoor and ultimately deploy Rhysida ransomware.
— Microsoft Threat Intelligence (@threatintel.microsoft.com) 2025-10-15T22:46:41.468Z
Chinese gangs behind toll scams: Organized cybercrime crews operating out of China are behind a wave of toll and other types of text scams that have stolen $1 billion from Americans over the past three years. [Additional coverage in the WSJ]
1K Koreans working in scam compounds: The South Korean government estimates that roughly 1,000 of its citizens are either working on their own volition or are trapped in slavery in cyber scam compounds in Cambodia. [Additional coverage in The Korea Times]
TigerJack's malicious extensions: A threat actor tracked as TigerJack has spent the past months constantly uploading malicious VS Code extensions on the official VS Code marketplace and the OpenVSX portal, even re-uploading extensions when they're taken down. The extensions are focused on cryptocurrency theft.
Major VS Code extension leakage: More than 500 VS Code extensions have leaked access tokens and credentials. In more than 130 cases, the tokens would have allowed threat actors to publish malicious updates via official marketplaces such as the official VS Code registry or Open VSX. Most of the leaks were found in JSON configuration files that ship with the extensions. According to Wiz, the impacted extensions had a cumulative install base of 150,000.
BearHost exit-scams, cites political reasons: A major Russian bulletproof web hosting provider has shut down, citing "political reasons." BearHost exit-scammed, leaving customers without refunds or access to their servers. The service had been operating since 2016 and also went by Voodoo Servers. According to Resecurity, one of its most well-known customers was the Qilin ransomware group.
LastPass phishing campaign: LastPass's security team warned users about a massive phishing campaign leveraging the company's brand and attempting to collect their master passwords.
Colombian phishing: Seqrite researchers look at a phishing campaign targeting Colombian users with judicial notifications that deploy the AsyncRAT with the help of malicious SVG files.
MENA hacktivism: A recent Kaspersky report takes a look at the hacktivist landscape in the MENA region and the new groups that have appeared over the past year.
Malware technical reports
Maverick trojan: Over the past two weeks, security researchers have spotted SORVEPOTEL, a WhatsApp worm spreading across Brazil. Kaspersky says the worm is currently being used to deploy a new banking trojan named Maverick.
PhantomVAI Loader: PAN's Unit42 looks at phishing campaigns distributing the PhantomVAI Loader, which is then used to deploy an assortment of RATs and infostealers. The malware is also known as the Katz Stealer Loader, as it started out as a simple loader to initially deploy the Katz Stealer.
Whisper 2FA: Barracuda's security team looks at Whisper 2FA, a new phishing kit that has been on the market since July this year.
HyperRat: iVerify researchers have discovered a new MaaS platform renting access to HyperRat, a new remote access trojan for Android devices. The project is only available to Russian-speaking buyers (for now).
Sponsor section
Agentic AI platform Nebulock pitches its product in one of our recent Snakeoilers episodes.
APTs, cyber-espionage, and info-ops
Mysterious Elephant APT evolves: Kaspersky says the tactics of an APT group known as Mysterious Elephant (APT-K-47, Bitter) have significantly evolved and gotten more sophisticated over the past two years.
"The group's latest campaign, which began in early 2025, reveals a significant shift in their TTPs, with an increased emphasis on using new custom-made tools as well as customized open-source tools, such as BabShell and MemLoader modules, to achieve their objectives. In this report, we will delve into the history of Mysterious Elephant's attacks, their latest tactics and techniques, and provide a comprehensive understanding of this threat."
Operation Silk Lure: Seqrite has found an advanced spear-phishing operation targeting Chinese individuals seeking employment in the fintech and crypto space.
APT36's StealthServer: QiAnXin has published a technical deep-dive of StealthServer, a new backdoor used by APT36, the suspected Pakistani espionage group also known as Transparent Tribe.
Jewelbug targets Russia: A suspected Chinese APT group hacked a Russian IT service provider. The attackers maintained access for at least five months this year and sought access to the company's source code repositories. Broadcom's security team believes the group was trying to launch a supply chain attack. The group also hacked a LATAM government, a Taiwanese company, and another South Asian IT provider. Broadcom tracks the attackers as Jewelbug (aka REF7707, CL-STA-0049, Earth Alux).
Famous Chollima's new malware: Cisco Talos has discovered new versions of BeaverTail and OtterCookie, malware used by North Korean APT group Famous Chollima. The malware was deployed in campaigns targeting job seekers in the cryptocurrency space.
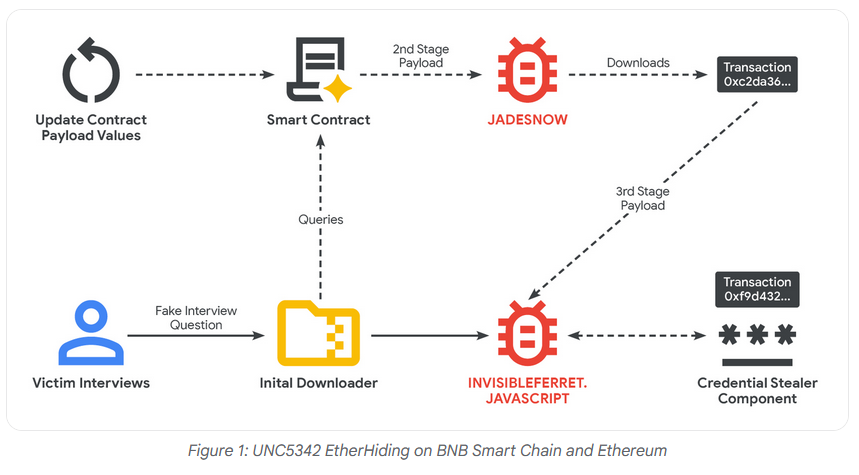
DPRK hackers adopt EtherHiding: North Korean state-sponsored hackers are using smart contracts to store portions of malicious code on the Binance public blockchain. The technique is called EtherHiding and has been previously used by multiple cybercrime and botnet operations since 2023. Google tracks the North Korean group as UNC5342, but it is more widely known as Contagious Interview. The group is widely known for its massive cryptocurrency heists. The original group that developed and deployed EtherHiding in the wild is known as ClearFake, and Google also published a report on this group, which it tracks as UNC5142.
Vulnerabilities, security research, and bug bounty
Sixnet RCE: Red Lion has released a security update to patch two vulnerabilities that can be used to take over Sixnet industrial controllers. The vulnerabilities allow attackers to bypass authentication and run code on the devices with root privileges. Vulnerable models include Red Lion SixTRAK and VersaTRAK remote terminal units. Both vulnerabilities have a CVSS severity score of 10/10.
AEM vulnerability exploited in the wild: Threat actors are exploiting a recently patched vulnerability in the Adobe Experience Manager form-building extensions. Attackers are bypassing authentication and running malicious code via a component that was left enabled in dev-mode. Exploitation was expected because security researchers published a detailed write-up and proof-of-concept code in July. Adobe eventually patched the bug a week later in August. The vulnerability has a maximum severity of 10/10.
Cisco ZeroDisco exploitation: Hackers are exploiting a recent Cisco zero-day to deploy rootkits on Cisco switches. Cisco patched the vulnerability (CVE-2025-20352) at the end of September while it was under attack, but did not provide other details. Trend Micro says the hacking campaign targeted Cisco 9400 and 9300 series switches. Some attacks also targeted legacy 3750G series devices. On the hacked devices, the attackers set up a universal password that contains the word "disco" in it, to allow for future access.
WatchGuard RCE write-up: WatchTowr Labs has published a deep dive into a recent remote code execution vulnerability that was patched in WatchGuard Firebox firewalls last month (CVE-2025-9242).
Cisco security updates: Cisco has released three security advisories for various products.
Gladinet patches zero-day: Software maker Gladinet has released a security update for a zero-day that was actively exploited in the wild this month. Tracked as CVE-2025-11371, the zero-day targeted CentreStack and Triofox file-sharing servers.
Training Solo attack: VUSec researchers have developed Training Solo, a new version of the Spectre v2 attacks that can break CPU domain isolation mechanisms such as IBPB, eIBRS, and BHI_NO.
Infosec industry
Threat/trend reports: Arctic Wolf, Backblaze, Datadog, F6, Hiilco Global, Kaspersky, Microsoft, Positive Technologies, and Wordfence have recently published reports and summaries covering various threats and infosec industry trends.
REcon 2025 videos: Talks from the REcon 2025 security conference, which took place in June, are available on YouTube.
New tool—nightMARE: Elastic's security team has released nightMARE, a Python library for malware analysis and reverse engineering.
"We primarily use it to create our configuration extractors for different widespread malware families, but nightMARE is a library that can be applied to multiple use cases."
New tool—Singularity: MatheuZSec, a red teamer for Kyntra, has released Singularity, a modern Linux kernel rootkit, compatible with modern 6.x Linux kernel releases.
New tool—MCP-Snitch: Security firm Adversis has open-sourced MCP-Snitch, a macOS application that intercepts and monitors MCP server communication.
Risky Business podcasts
In this edition of Seriously Risky Business, Tom Uren and Amberleigh Jack talk about First Wap, a Jakarta-based company that is selling surveillance-as-a-service. The good news is that it appears that government and media attention have had an impact on high-profile spyware vendors like NSO Group. The bad news is that these smaller players are flying under the radar and aren't afraid of selling to sketchy customers.
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about how different cybercriminal groups are looking for insiders to provide network access.




