Risky Bulletin: EU users to get free Windows 10 extended security updates
In other news: Cisco patches three zero-days; Microsoft drops Israeli intel surveillance contract; Brit arrested for EU airport disruptions.

This newsletter is brought to you by SpecterOps, the experts in Attack Path Management. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
Most European users will receive Windows 10 Extended Security Updates (ESU) for free.
These are security updates that Microsoft will provide to users after the Windows 10 operating system reaches end-of-life on October 14, less than three weeks away.
Normally, ESUs are available to enterprise customers, but last year, Microsoft took the novel step of providing the first-ever ESUs to home consumers. For $30, half the sum a company would pay, Windows 10 home users could have received security updates for an extra year.
A few weeks back, Microsoft changed its mind again and made the ESUs free for all home users, as long as they synced their PC settings via the Windows Backup app to their OneDrive cloud account. Although generous, the company was widely panned for using the Windows 10 EOL to mass-collect user data and force users into finally using their OneDrive accounts.
These ESUs are now "completely free," with no strings attached, for any user in the European Economic Area (EEA). This includes users living in EU member states, and three other countries, Iceland, Liechtenstein, and Norway.
The Windows 10 ESUs are free because of pressure from Euroconsumers, a major consumer protection NGO, which questioned the legality of Microsoft's offerings compared to the EU's new Digital Markets Act (DMA).
Microsoft has not confirmed this publicly, but this was revealed in an Euroconsumers reply [PDF] they sent Microsoft on Monday.
The organization is not done pushing Microsoft, and is now demanding that Microsoft provide more years of ESUs to home users beyond next year, October 13, 2026.
Hi, United Kingdom readers!
thanks Brexit!
— Mary Branscombe (@marypcbuk.bsky.social) 2025-09-25T13:41:50.665Z
Risky Business Podcasts
The main Risky Business podcast is now on YouTube with video versions of our recent episodes. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
Boyd cyberattack: Casino operator Boyd Gaming has disclosed a security breach that impacted its internal network. The company says the incident likely impacted its employees and not its customers.
Volvo breach: Volvo's North American branch has been impacted by a breach at the main company in Sweden. Current and former Volvo employee data was stolen by hackers from a Volvo IT provider. The hack originated at Miljödata, a provider of HR software for Swedish companies. The same incident disrupted the activities of more than 200 Swedish municipalities for days at the end of August. [Additional coverage in MarketScreener]
ClaimPix leak: Auto insurance platform ClaimPix leaked over 5 million user records through "an unencrypted and non-password-protected database." Some of the leaked data included ID scans. [Additional coverage in Website Planet]
SBP cyberattack: Ukraine's GUR military intelligence service claims it launched a DDoS attack that paralyzed Russia's SBP payment system, used for donating money to Russian forces fighting in Ukraine. [Additional coverage in Pravda]
Co-op ransomware losses: British retailer Co-op lost £206 million in revenue due to a ransomware attack in late April. The incident took out its IT systems for weeks and exposed the data of 6.5 million customers. Co-op also expects another £40 million hit tied to the incident in financial results for the second half of the year. [Additional coverage in The Standard]
Dutch Public Prosecution Office returns online: The Dutch Public Prosecution Office has restored its core IT systems after a hack of its Citrix server in late July.
General tech and privacy
Microsoft drops Israel's surveillance contract: Microsoft has dropped a contract with the Israeli intelligence service. The contract allowed Unit 8200 access to a large Azure server infrastructure to process and analyze data from phone calls and messages sent and intercepted across Palestine. The secretive contract came to light in August and was allegedly the reason for multiple pro-Palestine protests among Microsoft's own staff.
New Microsoft Marketplace: Microsoft has merged multiple stores into the new Microsoft Marketplace, a single place for finding Azure apps and services.
Meta teen accounts: Meta says that hundreds of millions of children have now been enrolled in the company's "teen accounts" feature. The feature is now being expanded from Instagram to Facebook and Messenger.
TikTok investigated in Canada: Canada is investigating TikTok for collecting the personal data of hundreds of thousands of Canadians children under the age of 13. Canada's privacy watchdog says the company failed to prevent young children from registering, despite its policy to ban children that young. TikTok responded by blocking advertisers from targeting anyone on the app under the age of 18.
Apple blames EU DSA for feature delays: Apple, the company that has been living on Steve Jobs' reputation for over a decade after his passing, is blaming its lack of meaningful features on the EU's Digital Markets Act, which is allegedly delaying its "innovation"—aka, new ways of locking out third-parties and devs out of iOS and preventing market monopolies. Bad, EU! BAD!!!! </sarcasm> [Additional coverage in Reuters]
Neon Mobile: The second most popular iOS app in the App Store's US social media section is an app that lets you record your calls and then sell the audio to AI companies. This is problematic since it appears it is done without the other calee's consent. [Additional coverage in TechCrunch]
Amazon settles with FTC for $2.5b: Amazon has agreed to pay $2.5 billion to the FTC for enrolling millions of consumers for Prime subscriptions without their consent. $1 billion is a civil penalty, while the rest will be disbursed back to affected customers. Around 35 million Amazon customers were affected and eligible to request payments. The settlement is the largest civil penalty in the FTC's history.
Package repos ask for help: Eight open-source organizations have asked for more financial support in managing package repositories due to rising costs. The orgs say package repositories are now free CDNs for hosting and delivering code. Repositories that rely on donations, sponsorships, or grants are expected to soon have financial difficulties and are asking large vendors to contribute more. The statement was signed by the maintainers of package repos such as PyPI, Maven Central, Composer, Crates, and Open VSX.
More on the RubyGems takeover: Additional details are surfacing on the takeover of the RubyGems package repository by Ruby Central. tl;dr: Shopify was involved, and this looks like another corporate takeover of an open-source ecosystem.
Another day in Rubyland, another first-hand account from a departing RubyGems maintainer: gist.github.com/simi/349d881...
— Mike McQuaid (@mikemcquaid.com) 2025-09-24T07:47:07.861Z
Government, politics, and policy
New DOD CSRMC: The US Department of Defense... uhm, War, has announced a new cyber framework named the Cybersecurity Risk Management Construct (CSRMC).
Cybersecurity in Agriculture Act: Two US senators have introduced a bill to help boost cybersecurity in the agriculture sector. The Cybersecurity in Agriculture Act would establish five regional agriculture cybersecurity centers. The centers would develop security tools for the agriculture sector, run training programs, and prioritize the detection of foreign adversaries targeting the sector.
MIND Act: Three Democrat Senators have introduced a new bill designed to protect the brain data of American citizens from commercial exploitation. The Management of Individuals' Neural Data Act of 2025 (MIND Act) directs the FTC to investigate ways to protect neural data. Four US states have already passed legislation to safeguard brain activity data.
UK uses AI to recover fraud funds: A new AI tool has helped the UK government detect and stop more than £480 million in fraud over the past year. The tool helped recover £186 million in COVID-19 pandemic loan fraud. It also stopped fraudsters from subletting housing received through social programs. The tool worked by cross-referencing multiple government databases to detect anomalies and spot fraud.
Predatorgate case hits Greek courts: Four individuals will face trial in Greece over the Predatorgate spyware scandal. Two Israeli and two Greeks employees of surveillance provider Intellexa will stand trial. No government official has been indicted after a controversial Supreme Court ruling absolved the government of any blame. The Predatorgate scandal came to light in 2022 after reporters found that the ruling conservative Mitsotakis government used the Predator spyware to spy on judges, senior military officers, journalists, and the opposition. [Additional coverage in the BBC]
Greek government denies any involvement with #Predator spyware scandal, but it has scuppered all efforts to shed light on it and its fingerprints are all over it. Still one case is going forward in court today. Spyware is used to silence critics and eliminate scrutiny @kostaskallergis.bsky.social
— Sophie in't Veld (@sophieintveld.bsky.social) 2025-09-24T09:14:04.763Z
EU opens SAP antitrust investigation: The EU has opened an antitrust investigation into German software giant SAP and the EU's largest tech company. The EU claims SAP prevented customers from using third-party support services for its ERP software platform. Customers were forced to use SAP for support and weren't allowed to cancel the support service. The company also charged customers when they returned to the platform with back-fees for support services they never received. According to EU investigators, these back-fees were identical, as if customers stayed with SAP all along.
🔥Breaking: @EU_Commission opens antitrust investigation into @SAP, Germany's largest (and Europe's second largest) company, for allegedly restricting competition in support services on its popular ERP software. Five years ago, I wrote this story https://t.co/sxpkNQ5uqj pic.twitter.com/n4gNh1syno
— Simon Van Dorpe (@simonvandorpe) September 25, 2025
Sponsor section
In this Risky Business sponsor interview, Catalin Cimpanu talks with Jared Atkinson, CTO at SpecterOps. They discuss how SpecterOps is using classifying identities under two categories, identities at rest and identities in transit, what they are, and how they should be treated differently.
Arrests, cybercrime, and threat intel
Man arrested for airport disruptions: UK authorities have arrested a man in connection with a cyber-attack that disrupted airports across Europe. A man in his forties was arrested in West Sussex on Tuesday. He is allegedly involved in deploying ransomware on the network of Collins Aerospace. The company manages self-check-in kiosks installed in airports across the globe.
Casino hackers released to parents: A 17-year-old who hacked several Las Vegas casinos in 2023 was released to his parents days after he turned himself in. He was released on several conditions until his next court date in November. The teen must not leave the Las Vegas Clark County, and he has restrictions on his cell phone and internet use. He is believed to be a member of the Scattered Spider hacking group. [Additional coverage in the Las Vegas Review-Journal]
Teen arrested for school shooting threats: Romanian authorities have arrested a teen for sending mass-shooting threats to hundreds of Romanian schools and hospitals. The teen was also charged in the US last year for sending bomb threats to hundreds of US schools and for manipulating underage girls into acts of violence and sexual acts. Romanian authorities refused to extradite him on the grounds that he was a minor. The teen is 17 and is a member of a known online criminal community. [Additional coverage in HotNews]
Operation HAECHI VI: An Interpol operation has seized almost $440 million from cybercrime gangs this year. The funds were seized from more than 68,000 bank accounts and 400 cryptocurrency wallets. Operation HAECHI VI targeted seven types of cyber-enabled crimes, from voice phishing to BEC and investment scams.
Malware on Rust's Crates: Socket Security has discovered two malicious Rust libraries on the Crates package repository. The two packages contained malicious code that stole Ethereum and Solana private keys. They also stole bracketed byte arrays, which may also sometimes contain encoded key material. The Rust team took down the packages hours after discovery.
First malicious MCP server: A recent update to a popular MCP server has introduced a backdoor system that copies every email handled by the tool. The malicious behavior was found in Postmark-MCP, an AI MCP server for interacting with the Postmark email delivery platform. According to Koi Security, this marks the first known case of a malicious MCP server. Postmark-MCP had over 1,500 downloads every week and released clean versions for months before the malicious update.
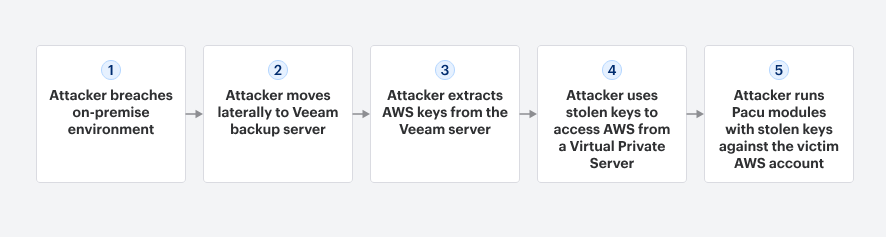
Ransomware to AWS attacks: Varonis says ransomware gangs are using AWS keys stored in local environments to pivot to a victim's AWS account and steal data with the help of the Pacu AWS exploitation framework.
Huge Ollama exposure: More than 10,600 Ollama LLM-hosting servers are exposed on the internet, according to Censys.
Firebase exposure: A security researcher going by "ice0" has found almost 4,800 Firebase databases exposed on the internet and leaking their data.
AI phishing campaign: Microsoft has spotted a phishing campaign where the threat actors used an AI tool to generate code to obfuscate payloads and evade security defenses.
Investment scam campaign expands: An investment scam campaign that leveraged Facebook ads to lure users to its sites has now expanded to other platforms, such as YouTube and Google Ads, per a new Bitdefender report.
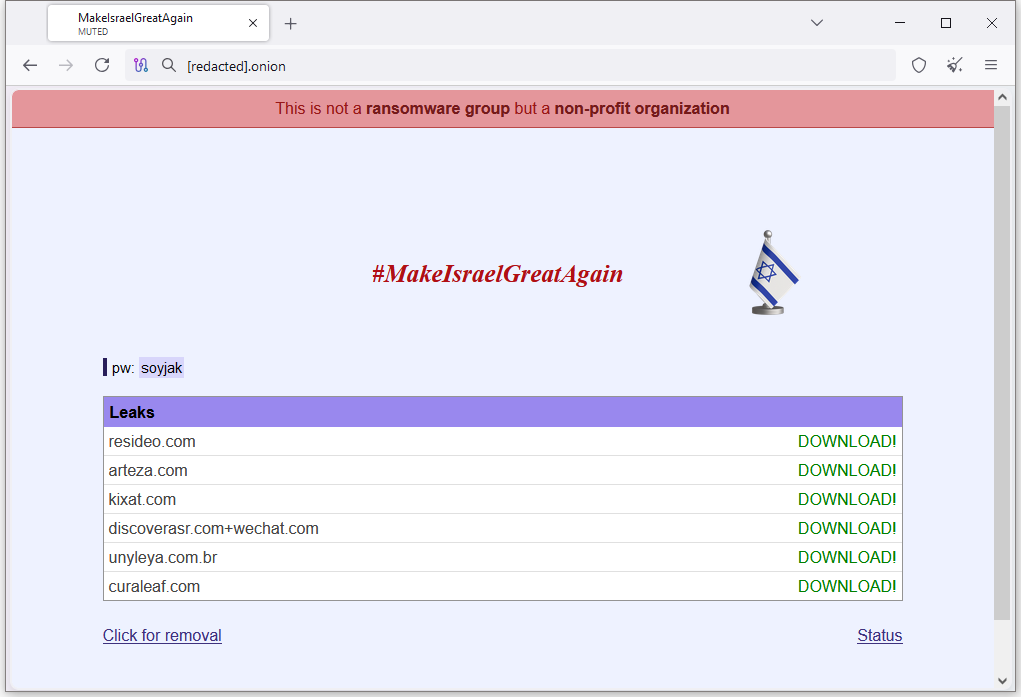
MIGA leak site: There's a new leak site named MakeIsraelGreatAgain (or MIGA) that started leaking victim data this week.
Malware technical reports
ShadowV2 DDoS botnet: DarkTrace has spotted a new DDoS-for-hire botnet named ShadowV2. The botnet runs on top of a Go-based RAT and a Python-based spreader and primarily targets cloud-based systems for infection.
"The threat actors employ advanced methods such as HTTP/2 rapid reset, a Cloudflare under attack mode (UAM) bypass, and large-scale HTTP floods, demonstrating a capability to combine distributed denial-of-service (DDoS) techniques with targeted exploitation."
PureRAT: HuntressLabs looks at how a Vietnam-based threat actor's use of the PureRAT.
XCSSET: Microsoft has spotted another version of XCSSET, a macOS malware strain that targets users by infecting Xcode projects.
"This new variant of XCSSET brings key changes related to browser targeting, clipboard hijacking, and persistence mechanisms. It employs sophisticated encryption and obfuscation techniques, uses run-only compiled AppleScripts for stealthy execution, and expands its data exfiltration capabilities to include Firefox browser data. It also adds another persistence mechanism through LaunchDaemon entries."
Sponsor section
Justin Kohler, VP of Product at SpecterOps, shows how BloodHound Enterprise can be used to find and fix Active Directory (mis)configurations that could let attackers easily own your entire enterprise.
APTs, cyber-espionage, and info-ops
Russia's paid-to-post scheme in Moldova: DFRLab looks at how Russia is paying locals to post anti-EU narratives ahead of Moldova's parliamentary elections this weekend. Russia used the same thing ahead of Moldova and Romania's presidential elections last year.
"The network was also territorially organized, covering Moldova's districts and Chisinau's sectors, and expanded across the south, center, and north of the country. Coordination followed a strict rhythm: pre-recorded video tutorials during the day and nightly audio calls at 8 p.m. Curators used Telegram bots to assign tasks, collect links to published content (used to determine payouts), and monitor compliance. Each activist was required to produce a fixed number of posts or comments daily, ensuring the narratives remained prominent."
COLDRIVER targets its own: Russian APT group COLDRIVER (Star Blizzard, Callisto, and UNC4057) has used a ClickFix campaign to target Russian dissidents and their supporters. The final payloads are a new downloader named BAITSWITCH and a new PowerShell-based backdoor named SIMPLEFIX.
BO Team: Kaspersky has spotted new attacks from pro-Ukrainian hacking group BO Team.
PhantomCore's Bearlyfy: F6 has published a report on Bearlyfy, a new ransomware strain used by a suspected Ukrainian APT group tracked as PhantomCore in attacks against Russian orgs.
DeceptiveDevelopment: ESET has published a paper on a cluster of North Korean remote IT workers the company tracks as DeceptiveDevelopment.
TAG-100 is now RedNovember: Recorded Future has renamed the TAG-100 espionage activity cluster as RedNovember. This is a suspected Chinese APT group that compromised networking and enterprise devices across the Asia-Pacific region. The broader classification links the group to a much larger campaign that also targeted the EU, the US, and LATAM, and with a possible nexus to China's military.
"Some of its activity appears to align with a military affiliation or military-adjacent interests, such as the targeting of specific entities in the US DIB, or the targeting of Taiwan around the time of China's military exercises in Taiwan. However, there are different sets of targeting that do not closely match this pattern: for example, the targeting of law firms, newspaper organizations, and a Christian denomination in the US."
UNC5221's BRICKSTORM: Google's Mandiant division has released a tool to scan and find Chinese backdoor malware installed on networking devices. The tool scans for BRICKSTORM, a backdoor used by the UNC5221 APT group since April of last year. The malware is typically installed on *NIX-based enterprise gear, where security software doesn't run. Google says the group's most common victims are companies in the legal and tech sectors, such as SaaS platforms and business outsourcers.
We are expecting several organizations who use this tool and actively hunt for this threat will find that this actor has been active in their networks for some time.
— John Hultquist (@hultquist.bsky.social) 2025-09-24T14:43:25.071Z
Stately Taurus's Bookworm: PAN's Unit42 looks at the Stately Taurus APT's use of the Bookworm malware family in recent campaigns.
How China trains its cyber forces: A new Margin Research study looks at how China is training its cyber forces after a recent military reorganization.
"Over the past six months, Beijing has overhauled its military cyber education system in step with broader reforms to the force itself. The PLA's cyber forces, which were once grouped together under the Strategic Support Force (SSF), have now been split into three components: the Information Support Force (ISF), the Cyberspace Force (CSF), and the Aerospace Force (ASF). The education system has followed suit, with new campuses and specialized programs aligned to each of the successor organizations."
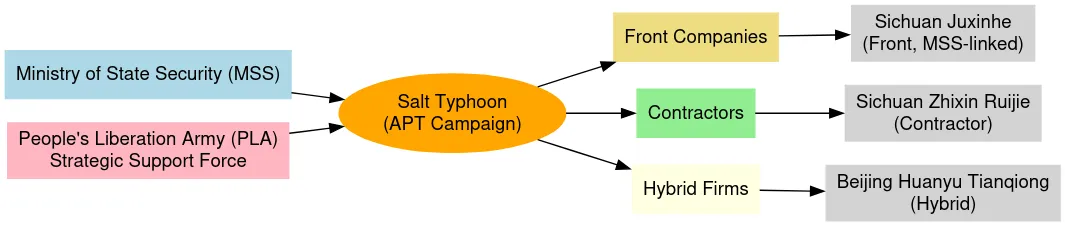
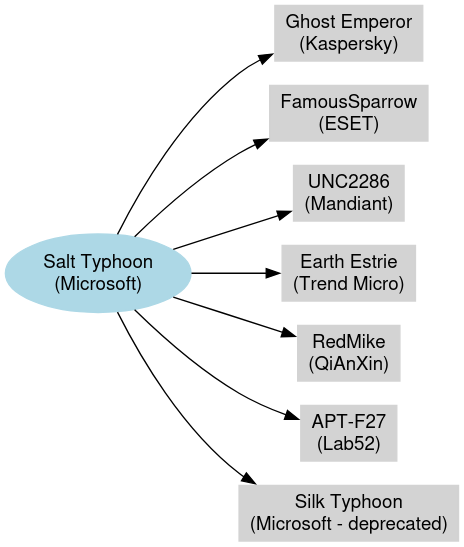
Salt Typhoon profile: DomainTools has published a profile on Salt Typhoon, the Chinese APT that hacked over a dozen US telcos at the end of last year. It's actually a very old and sprawling APT, involving everything from MSS supervisors to front companies and contractors.
Vulnerabilities, security research, and bug bounty
Cisco IOS zero-day: Cisco has released a firmware update to fix an actively-exploited zero-day in its IOS and IOS XE operating systems. Tracked as CVE-2025-20352, the zero-day can allow attackers who gained access on a device to elevate privileges and gain root access. Exploitation takes place via a specially crafted SNMP packet. The company also released security updates for 16 other bugs.
Cisco patches two more ASA zero-days: In addition, Cisco also patched two other zero-days (CVE-2025-20333 and CVE-2025-20362) in its ASA firewall series. The zero-days were used by a suspected Chinese espionage group to target US organizations. Tracked as Storm-1849, the group has targeted Cisco firewalls since last year. Last year's attacks deployed the ArcaneDoor backdoor, but the new attacks are using the RayInitiator bootkit and the LINE VIPER shellcode loader, according to the UK NCSC. CISA ordered federal agencies to deploy patches by the end of the week.
Pandoc exploitation: Threat actors are exploiting a Pandoc vulnerability disclosed in July to hack AWS environments. The attackers are specifically targeting the AWS Instance Metadata Service from where they can extract customer IAM credentials. Pandoc is a Linux utility to convert between different markup formats.
Unpatched OnePlus SMS read bug: A vulnerability in the OnePlus OxygenOS that can allow malicious third-party apps to read a user's SMS messages. The bug can be exploited by malicious apps to bypass SMS-based two-factor authentication. Rapid7 says the bug remains unpatched because it couldn't report the issue to OnePlus due to its restrictive NDA.
GoAnywhere bug write-up: WatchTowr Labs has published a write-up on CVE-2025-10035, a deserialization vulnerability in Fortra's GoAnywhere file transfer application.
WOR technique: Exploit Azerbaijan has published a write-up on WOR, a new regex pattern matching technique that can be used to exploit MySQL Full-Text Search features.
Tiantong-1 audit: Midnight Blue researchers have published a two-part series on Tiantong-1, a Chinese satellite phone system.
ForcedLeak attack: Noma Labs has discovered a new prompt injection attack, named ForcedLeak, that could leak data from Salesforce's AgentForce AI agent.
Infosec industry
Threat/trend reports: Barracuda, CyberCube, Gartner, Invictus IR, Netskope, Red Canary, and Searchlight Cyber have recently published reports and summaries covering various threats and infosec industry trends.
BruCON 2025: Talks from the BruCON 2025 security conference, which took place last month, are available on YouTube.
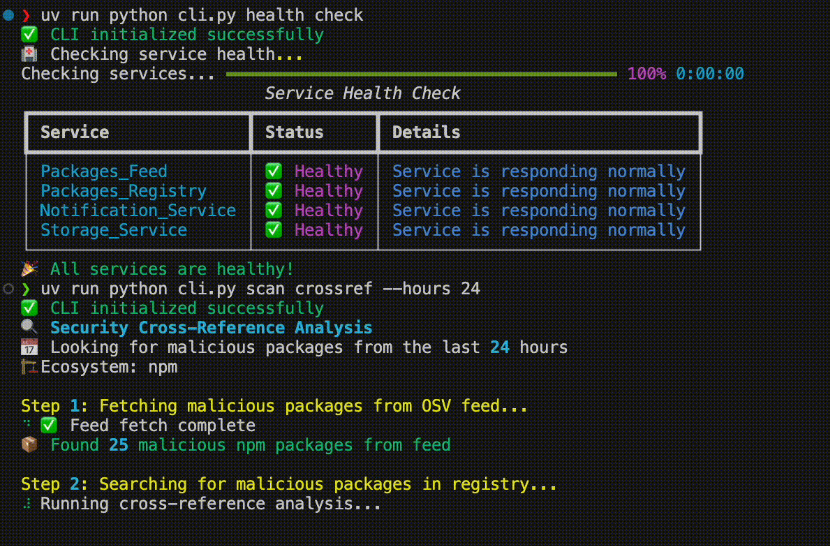
New tool—MalifiScan: Security researcher Rotem Reiss has open-sourced MalifiScan, a tool that detects malicious packages via external vulnerability feeds and searches for them in your package registries or artifact repositories.
Risky Business podcasts
In this edition of Seriously Risky Business, Tom Uren and Amberleigh Jack talk about how the funnel that turns kids into cyber criminals has evolved over the last decade. Cybercrime's reach has broadened, and it is more lucrative and more violent.
In this edition of Between Two Nerds, Tom Uren and The Grugq look at a new Center for Strategic and International Studies report—A Playbook for Winning the Cyber War.




