Risky Bulletin: EU sanctions three GRU hackers
In other news: OTP Agency admins sentenced to prison; Apple fixes first 2025 zero-day; DeepSeek limits registrations after cyberattack.

This newsletter is brought to you by asset inventory and network visibility company runZero. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
The European Union has sanctioned three Russian military hackers for their role in cyberattacks against Estonian government agencies in 2020.
Sanctions were levied against Yuriy Denisov, Nikolay Korchagin, and Vitaly Shevchenko.
The three are officers in Unit 29155 in Russia's military intelligence service, also known as the GRU.
The EU says the three stole classified information and sensitive data from at least three Estonian ministries, such as the Ministry of Economic Affairs and Communications, the Ministry of Social Affairs, and the Ministry of Foreign Affairs.
The sanctions come four months after the Estonian government publicly attributed the 2020 hack to GRU Unit 29155.
Two of the sanctioned hackers were also indicted in September by the US government for a more recent hacking campaign that targeted NATO countries providing military aid to Ukraine.

The three are part of what is informally considered one of Russia's most elite military intelligence units.
GRU Unit 29155 has operated in secret since 2008, and its main objective for most of its existence has been assassinations and sabotage on foreign soil.
The unit has been linked to explosions at Czech ammo depots in 2014, an attempted coup in Montenegro in 2016, the 2018 poisoning of former GRU officer Sergei Skripal in the UK, and a 2020 bounty program that paid the Taliban tens of thousands of USD for each US and NATO soldier killed in Afghanistan.
Recent reports have also tentatively linked the unit to the notorious Havana Syndrome that impacted the US diplomats at embassies across the world.
A September 2024 UK NCSC report found that the unit had also set up a cyber division with offensive cyber operations back in 2020—suggesting the Estonian cyberattacks might have been one of its first operations.
While the group operated in secrecy for most of its life, things changed after Russia invaded Ukraine, with the group taking a far more active and visible role. Its main cyber operation was the deployment of the WhisperGate data wiper ahead of Russia's invasion of Ukraine as part of an operation that attempted to sabotage and prevent the Ukrainian government from reacting to the Kremlin's ground invasion.
In infosec nomenclature, the unit's cyber operations are tracked under codenames such as Ember Bear, Cadet Blizzard, Frozenvista, UNC2589, and UAC-0056.
Risky Business Podcasts
Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
DeepSeek cyberattack: Chinese AI company DeepSeek has limited new user registrations after the company experienced what the company described as "large-scale malicious attacks" on its newly launched genAI services. The attack took place on the same day the company's app overtook ChatGPT on app stores, and as US AI stock prices fell by up to 20%. The attack is believed to be a combination of DDoS attacks and API abuse.
MegaFon cyberattack: Ukraine's military intelligence agency GUR has allegedly carried out disruptive cyberattacks against three Russian telecom providers—MegaFon, Yota, and NetByNet. [Additional coverage in The New Voice of Ukraine]
Doxbin leak: More than 435,000 email addresses shared on Doxbin have leaked and added to the Have I Been Pwned database.
General tech and privacy
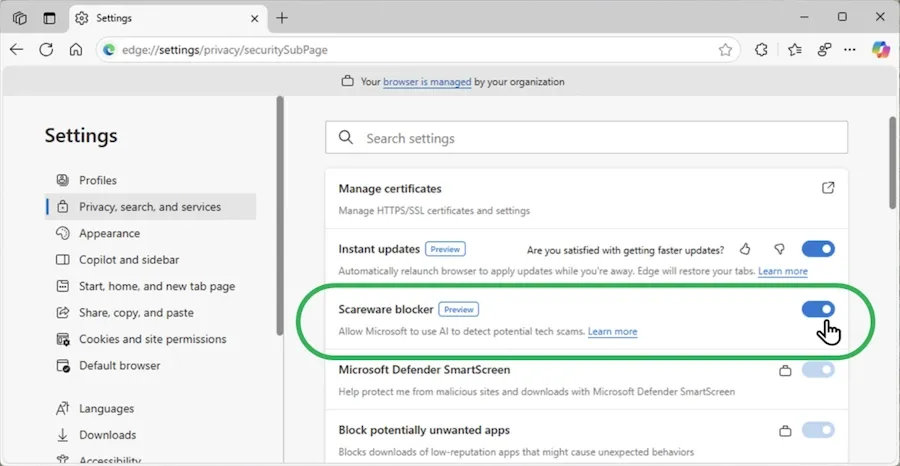
Edge tests scareware blocker: Microsoft is testing a new Edge security feature designed to detect and block scareware popups. The feature uses machine learning to detect popups and text typically found on scareware and tech support scams and warn users about the risks. The feature was initially announced during last year's Microsoft Ignite developer conference.
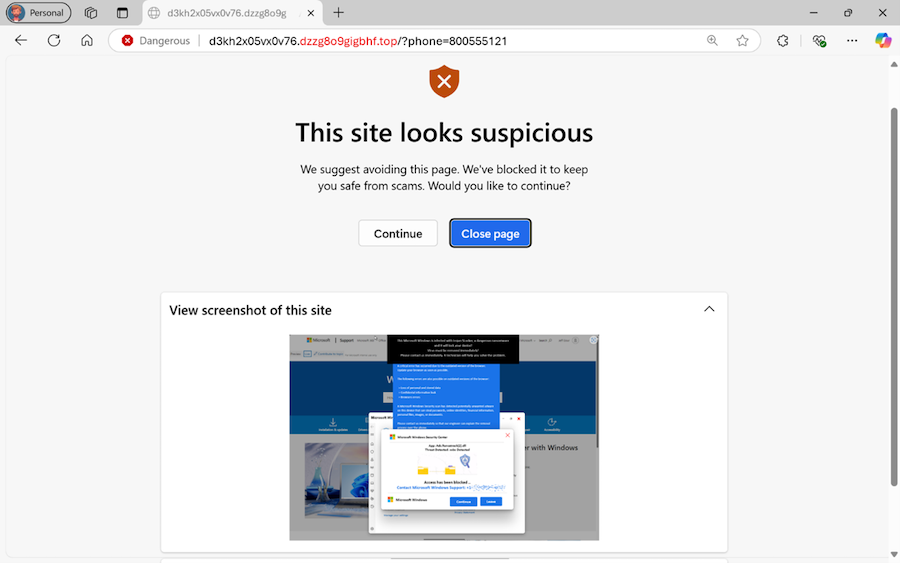
Bitwarden improves account security: Password manager app Bitwarden is adding a new security feature to user accounts where 2FA is not enabled. The company will require email verification codes whenever users log into their account from an unrecognized device. The new feature is meant to prevent threat actors from adding and using stolen accounts on their own devices.
New Signal sync options: Secure messaging service Signal will now let users sync messages across all linked devices.
KuCoin to leave US market: Cryptocurrency exchange KuCoin has reached a settlement with the US Department of Justice and will leave the US market for two years after it was caught operating an unlicensed money-transmitting business. The company has agreed to pay $297 million, representing a regulatory fine and forfeiture for its failure to implement anti-money laundering (AML) and know-your-customer (KYC) protocols. KuCoin will be allowed to re-enter the US market after fixing all issues and registering with US authorities. KuCoin was one of the world's largest crypto exchanges when the Justice Department started an investigation into its operations.
YouTube hour-long unskippable ads: After users started reporting receiving 60-minute ads on YouTube, Google sent a statement to journalists that the company is dead serious about going about ad blockers.
Meta takes down Linux groups: Starting somewhere around January 19, Meta's AI-based moderation tool started flagging Facebook groups for Linux-related discussions as malicious and taking them down.
Government, politics, and policy
EU plans to ban console sales to Russia: The EU plans to ban the sales of video game consoles to Russia after reports that the Russian military had used console kits to control drones used in Ukraine. According to the Financial Times, the ban is expected to be part of a new sanctions package that the EU will pass next month. Microsoft, Nintendo, and Sony halted sales of new consoles to Russia after its invasion of Ukraine in 2022. The ban is aimed at companies that re-sell devices to Russia. The Kremlin was expecting a ban and had touted a plan to build its own gaming console for almost a year.
Poland accuses Russia of buying disinfo over the dark web: The Polish government says Russian intelligence services are using the dark web to recruit Polish citizens to spread disinformation ahead of the country's presidential election in May. Citizens are allegedly offered up to €4,000 to spread anti-EU propaganda on social media. Russian intelligence services FSB and GRU are allegedly involved in the campaign, which began at the start of last year. [Additional coverage in Euromaidan Press]
US ROUTERS Act: Two US senators have introduced a bill that would instruct the US Department of Commerce to study the national security risks associated with routers and modems manufactured overseas. The bill aims to identify devices that may be under the control of foreign adversary governments and block their sale in the US. The new bill is named the Removing Our Unsecure Technologies to Ensure Reliability and Security, or the ROUTERS Act, and is sponsored by Senators Marsha Blackburn (R-Tenn.) and Ben Ray Luján (D-N.M.). [Additional coverage in CyberScoop]
US Insure Cybersecurity Act: Two US senators have re-introduced the Insure Cybersecurity Act, a bill that would direct the US National Institute of Standards and Technology to create guidelines and clear guidance of how cybersecurity insurance should work. The guidelines should be available for both issuers, agents, and brokers, but also for their customers. [Additional coverage in CyberScoop]
US TP-Link ban coming this year: After rumors surfaced last year that the US government was looking into banning TP-Link, a new leak suggests the ban is expected next year. [Additional coverage in CNBC]
French data breach trends: In its yearly report, France's data protection agency says that most breaches occur due to the same and recurring security flaws and usually take place at third-party contractors.
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with runZero founder and CEO HD Moore about the company's latest capability, a feature called Inside-Out Attack Surface Management that takes internal fingerprints and scans the internet to discover possible exposures.
Arrests, cybercrime, and threat intel
OTP Agency admins sentenced: A UK judge has sentenced to prison the three administrators of OTP Agency, a web service that allowed cybercriminals to intercept one-time passcodes. One administrator was sentenced to two years and eight months, while the other two received a one-year sentence. The three were arrested in March 2021, a month after the site was featured in a Brian Krebs article on the rising market for OTP token thefts. The OTP Agency service allowed threat actors to enter a victim's phone number, initiate a call posing as a bank, and request victims to share an OTP token from their banking app.

Major sextortionist extradited to US: US officials have extradited a 24-year-old Nigerian man for a sextortion scheme that resulted in financial losses and even the death by suicide of a minor. Officials say Hassanbunhussein Abolore Lawal is responsible for the death of Gavin Guffey, a 17-year-old from Rock Hill who took his life in July 2022. Lawal posed as women online to lure victims into private chats and send sexually explicit images of themselves. The suspect used the images to extort victims for money. Lawal faces life in prison on multiple charges, including child exploitation.
GDLockerSec group: KELA has published a profile on GDLockerSec, a group that emerged this month and started encrypting AWS buckets and asking victims for ransoms.
"KELA's investigation indicates that GDLockerSec is an amateur group that relies heavily on exaggerated claims to inflate its reputation within the cybercrime ecosystem. The group's tactics suggest a lack of sophistication, with poor operational security, copying another ransomware website, and unverified claims being a recurring pattern in their activities. Their reliance on self-promotion, rather than verifiable achievements, underscores their struggle to gain legitimacy among more established ransomware groups. Further analysis points to potential ties to both Morocco and Algeria, as inferred from user aliases, messaging activity, and possible geographical indicators linked to the group's members."
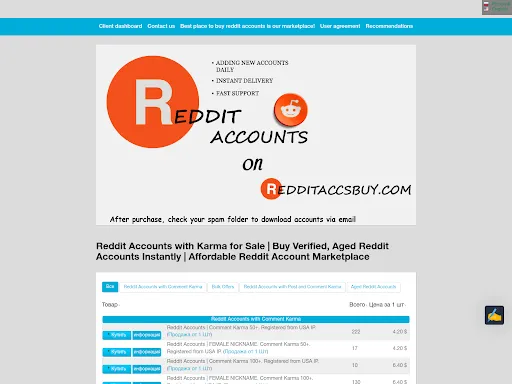
Accounts for sale market: DomainTools looks at online cybercrime networks using hijacked websites to promote their accounts-for-sale services.
Malware technical reports
Hellcat ransomware: Cato Networks looks at a new RaaS platform named Hellcat that launched last October and has already listed close to a dozen victims on its leak site.
Arcus Media ransomware: Halcyon researchers have published an analysis of a new RaaS platform named Arcus Media. The group launched in April 2024 and runs a very private affiliate program.
CS to Lockbit: The DFIR Report team has published an analysis of a Lockbit ransomware infection that came in via an initial infection with Cobalt Strike.
Windows Locker (XDS): CyFirma researchers have spotted a new ransomware strain going by the boring name of Windows Locker, sometimes referred to as the XDS.
ODAT: Trustwave has published a breakdown of how the ODAT (Oracle Database Attacking Tool) malware works to exploit and steal data from Oracle DBs.
Aquabot: Akamai researchers have found a new version of the Aquabot IoT malware (a Mirai variant) that is currently exploiting Mitel SIP phones using CVE-2024-41710, a command injection vulnerability that affects Mitel models.
"This malware exhibits a behavior we have never before seen with a Mirai variant: a function (report_kill) to report back to the command and control (C2) when a kill signal was caught on the infected device. We have not seen any response from the C2 as of the date of this blog post."
TorNet: Cisco Talos has discovered a new backdoor named TorNet. The malware is part of a campaign from a known financially motivated malspam group. It's obviously called TorNet because it uses Tor for its C&C servers.
"The actor also disconnects the victim machine from the network before dropping the payload and then connects it back to the network, allowing them to evade detection by cloud antimalware solutions."
Phorpiex: The Phorpiex (Trik) malware is still alive and delivering Lockbit ransomware payloads to infected systems.
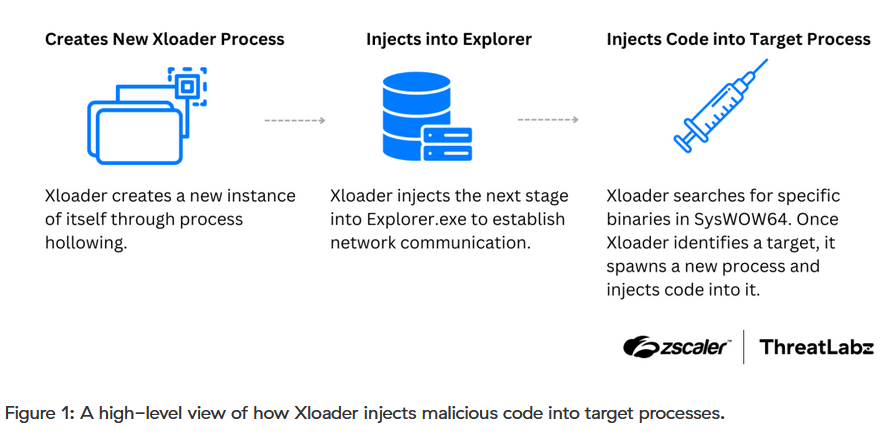
Xloader: Zscaler researchers have published part one of their analysis of v6 and v7 of the Xloader malware.
Sponsor section
Senior Sales Engineer Ali Cheikh demonstrates runZero to Risky Business host Patrick Gray. runZero is a cyber asset management tool that combines active scanning, passive discovery, and API integrations to discover IT, OT, and IoT assets (both managed and unmanaged) across your network, including cloud, mobile, and remote environments.
APTs, cyber-espionage, and info-ops
APT-C-60 (DarkHotel): Qihoo 360 has published a report on APT-C-60, a South Korean APT group also known as DarkHotel and Pseudo Hunter. The report covers newer malware samples used by the group in recent operations.
ScatterBrain: Google Mandiant has published a technical analysis of ScatterBrain, a code obfuscation toolkit used by APT41 for its POISONPLUG.SHADOW backdoor.
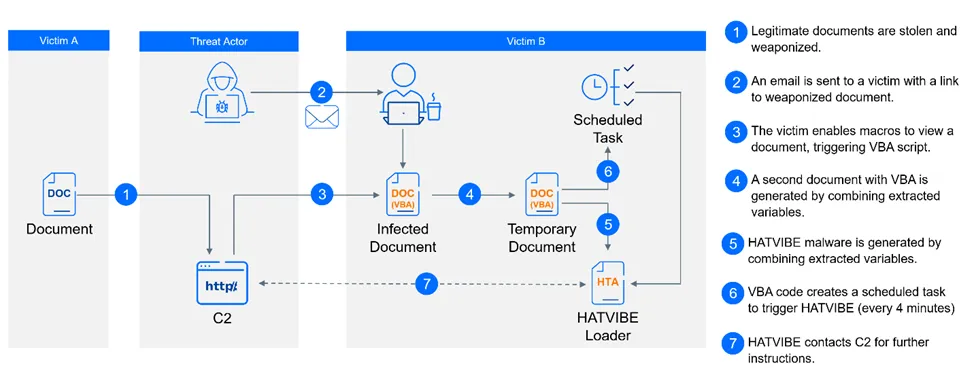
UAC-0063: Bitdefender has spotted a new cyber-espionage campaign linked to Russian cyber-espionage group UAC-0063 that targets organizations across Central Asia and European countries such as Germany, Romania, the UK, and the Netherlands. The attacks used weaponized Microsoft Word documents, HATVIBE malware loader, custom-built malware, and other sophisticated techniques to infiltrate government institutions and embassies. Sekoia has also published a report on the same campaign, too.
Vulnerabilities, security research, and bug bounty
Military cyber honeypot: A team of academics from Penn State University in the US is building a honeypot designed to mimic military-style networks. The network will use fake equipment designed to lure foreign threat actors and record their every move. The project is being built using a $557,000 grant from the US military.
DeepSeek R1 jailbreak: KELA researchers have jailbroken DeepSeek's new R1 AI model and used it to generate malicious content, such as "ransomware development, fabrication of sensitive content, and detailed instructions for creating toxins and explosive devices."
Apple zero-day: Apple has patched an actively exploited zero-day in its iOS and macOS operating systems. Tracked as CVE-2025-24085, the vulnerability resides in Apple's Core Media processing framework. Apple says attackers can abuse malicious media files to elevate their privileges on targeted systems.
Fortinet zero-day write-up: watchTowr Labs has published a technical deep dive of a recently patched Fortinet zero-day (CVE-2024-55591).
D-Link RCE vulnerability: D-Link has patched an RCE vulnerability in its DLS wireless routers reported by Italian security research Max. See Max's two-part write-up on the bug here and here.
NVIDIA patches: NVIDIA has released a security update to patch seven issues in its display driver. More from Edera.
VxWorks vulnerability: SEC Consult researchers have found that the Wind River VxWorks RTOS uses weak password hashing algorithms.
"For VxWorks 6.9, they incorrectly claimed the system uses 5,000 iterations of SHA-256 for password hashing, despite our proof of concept demonstrating that it uses only a single iteration. They downplayed the severity of this issue, citing the product's End of Life (EOL) in three months as justification for inaction. For VxWorks 7, the vendor dismissed the need for further improvements, stating it was 'appropriate for an embedded system.' The vendor told us they are treating the issue as a "feature request" but were unable to provide a timeline for the implementation."
New Apple CPU side-channel attacks: Academics have discovered two new side-channel attacks against Apple CPUs that can leak sensitive data from the processor's memory. Named SLAP (Speculation Attacks via Load Address Prediction) and FLOP (False Load Output Predictions), the attacks impact Apple's line of A and M CPUs. Affected devices include all Mac laptops sold after 2022, all Mac desktops sold after 2023, and all iPhones sold after 2021. Both attacks can be performed via a web browser. Apple has told researchers it plans to address both attacks in an upcoming security update. The team behind the attacks has found almost a dozen side-channel attacks in modern CPUs, such as Meltdown, Spectre, SGX Fail, and RAMBleed.

Infosec industry
New tool—gitC2: Offensive security engineer Offalltn has released gitC2, a C2 tool that uses a GitHub repository to execute commands through its issues tracker.
New tool—ExtensionHound: Software engineer Amram Englander has released ExtensionHound, a security analysis tool that identifies DNS queries made by browser extensions.
Acquisition news: Automated endpoint management platform NinjaOne is acquiring cloud data backup and recovery platform Dropsuite.
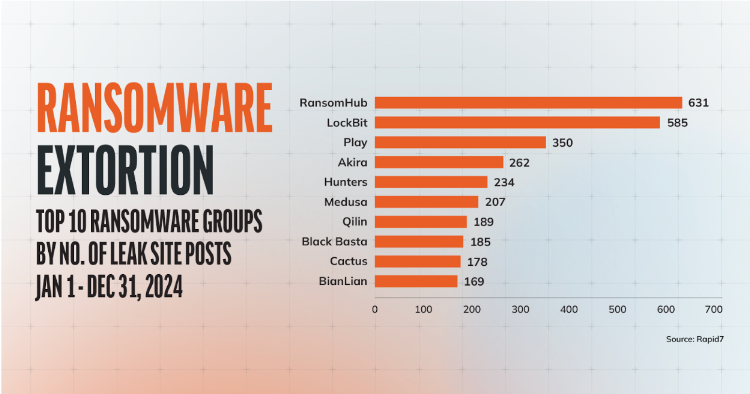
Threat/trend reports: Apteco, Cloudflare, France's CNIL agency, Forescout, Obsidian Security, Rapid7, and Recorded Future have published reports and summaries covering various infosec trends and industry threats.
Risky Business Podcasts
In this podcast, Tom Uren and Adam Boileau talk about the continued importance of hack and leak operations. They didn't really affect the recent US presidential election, but they are still a powerful tool for vested interests to influence public policy.
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about the evolution of Russian cyber operations during its invasion of Ukraine.




