Risky Bulletin: Dutch intelligence agencies discover a new Russian APT
In other news: MATLAB maker hit by ransomware; Nigeria arrests 20 for hacking student exam results; Iranian pleads guilty for Robbinhood ransomware attacks.

This newsletter is brought to you by Sublime Security, an email security platform that's not a black box. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
Dutch intelligence agencies have uncovered a new Russian cyber-espionage group while investigating a security breach of its police force last September.
The new group is tracked as Laundry Bear by Dutch intelligence services AIVD and MIVD and Void Blizzard by Microsoft, which aided in the Dutch investigation.
Among the panoply of Russian APTs, the group appears to be a new cluster that was formed and started operations in mid-2024.
Its attacks are primarily focused on supporting Russia's war effort in Ukraine, and known targets are the who's who of military and diplomatic targets.
This includes the likes of defense and foreign affairs ministries in NATO member states, their ambassadors, branches of the armed forces, defense contractors, and any high-tech business involved in military production that's somehow linked to supporting Ukraine's defense effort.
Laundry Bear's tactics are unidimensional. They buy login credentials from infostealer shops, breach individual accounts at their desired targets, use open-source tools to expand access, and then scrape and steal files and email inboxes.
TTP-wise, it would be hard to distinguish Laundry Bear from any other initial access broker or ransomware group.
Microsoft says that starting April this year, the group is now also dabbling in spear-phishing attacks, which they primarily use to collect credentials from specific individuals.
The AIVD and MIVD say that while many of the Laundry Bear tactics overlap with what APT28 has been doing lately, the two are "distinct threat actors."
Dutch officials believe the group's tactics will grow in complexity as it learns and operates.
MIVD, Vice Admiral Peter Reesink: "We have seen that this hacker group successfully gains access to sensitive information from a large number of (government) organizations and companies worldwide. They have a specific interest in European Union and NATO countries. Laundry Bear is looking for information about the purchase and production of military equipment by Western governments and Western supplies of weapons to Ukraine."
AIVD Director-General Erik Akerboom: "We consciously choose to expose their working methods. We do this by making a technical advice about the method of Laundry Bear public. In this way, not only governments, but also manufacturers, suppliers and other targets can arm themselves against this form of espionage. This reduces the success rate of Laundry Bear and allows digital networks to be better protected. This increases our national resilience."
Risky Business Podcasts
The main Risky Business podcast is now on YouTube with video versions of our recent episodes. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
CSDN hack linked to UTG-Q-015: Chinese security firm QiAnXin says the hack of China's largest IT portal was part of an apparent "outsourcing war." The CSDN was hacked and hosted a watering hole attack in December of last year. The site was one of several IT portals hacked by a group the company calls UTG-Q-015. QiAnXin believes the group is made up of Chinese nationals living and working across Southeast Asia, trying to steal code from other developers.
Tiffany hacked: A hacker has stolen customer data from Tiffany's network in South Korea. The company notified users this week that data such as names, emails, phone numbers, and home addresses were stolen in a breach last month. Tiffany is the second company part of French fashion conglomerate LVMH that disclosed a security breach. Christian Dior's South Korean and Chinese networks were hacked as well. [Additional coverage in Chosun] [h/t DataBreaches.net]
South Korea probes other telcos for breaches: The South Korean government is investigating two other mobile carriers to uncover possible breaches. The investigation has targeted KT Corp or LG Uplus, but no traces of a breach have been found. Hackers breached South Korea's largest telco, SK Telecom, and stole the personal and SIM card data of over 26 million customers. [Additional coverage in The Korea Herald]
Adidas breach: Sportswear apparel maker Adidas says a threat actor accessed some customer data via the network of a third-party customer service provider.
MathWorks (MATLAB) ransomware attack: A ransomware attack has brought down MathWorks, the company behind the MATLAB software. Internal systems and customer online apps have been down for over a week since the attack on May 18. No ransomware gang has yet taken credit for the attack.
Woof....MATLAB has had a major outage for a week now ... and today, they've confirmed it was a ransomware attack. status.mathworks.com
— Ben Schwartz (@lthummus.com) 2025-05-26T00:43:28.706Z
General tech and privacy
Quantum computing attack prediction: Google estimates that a quantum computer with 1 million noisy qubits could break 2048-bit RSA encryption after a week of computations. This is around 20 times fewer noisy qubits than previously estimated.
Some excellent work by @craiggidney.bsky.social that reduces the number of qubits (in a quantum computer) required to break RSA by 20-fold. If you don’t have a migration plan to safe algorithms, now is the time to start one!
— Heather Adkins (@argv.bsky.social) 2025-05-23T16:22:59.950Z
App Store fraud: Apple stopped more than $2 billion in fraudulent App Store transactions last year and blocked more than 146,000 developer accounts over fraud concerns. Fraudulent transactions originated from 1.6 million accounts and used over 4.7 million stolen credit cards. The company says it has now blocked over $9 billion in fraudulent transactions over the past five years.
Chrome 137: Google has released version 137 of its Chrome browser. See here for security patches and webdev-related changes. The biggest change in this release is Gemini, Google's AI assistant, which is now integrated into Chrome on macOS and Windows. Chrome now also uses a local LLM to detect tech support scams and also supports the DTLS 1.3 protocol.
Firefox 139: Mozilla has released Firefox 139. New features and security fixes are included. The biggest feature in this release is support for themes on the new tab page and experimental support for link previews.
Twitter Community Notes champion: A blockchain security firm named Web3 Antivirus is the top contributor to Twitter's Community Notes. The company has used an automated process to create community notes on Twitter posts advertising crypto scams. It has contributed over 52,000 community notes, more than the next nine contributors combined. [Additional coverage in Indicator]
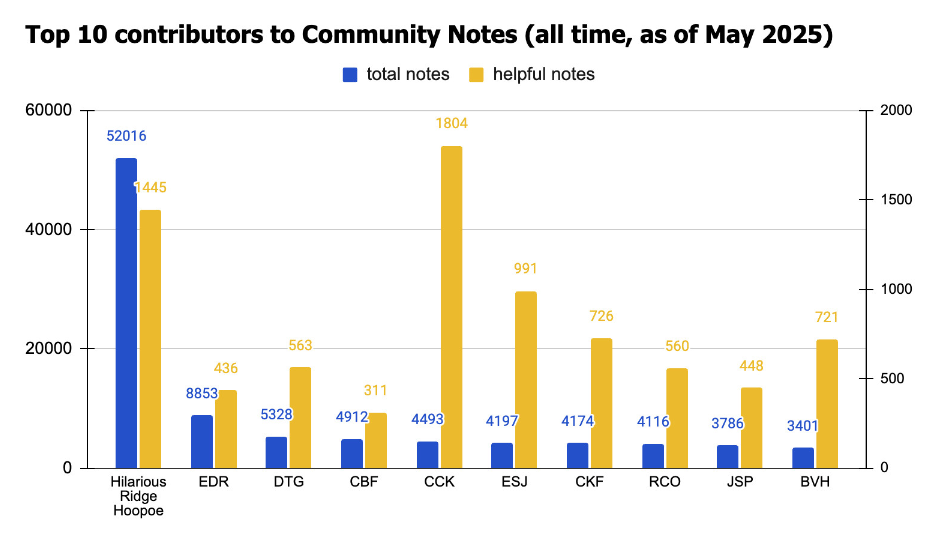
When I started researching this story, I thought it was going to be about a grifting private actor abusing Community Notes. Instead, the grifter appears to be X, benefiting from the free labor of a specialized contributor. indicator.media/p/the-top-co...
— Alexios Mantzarlis (@mantzarlis.com) 2025-05-26T13:10:59.874Z
Government, politics, and policy
New pay structure for Australia's cyber warfare workforce: The Australian Defense Force has adopted a new pay structure in an effort to build and retain a modern cyber warfare workforce. The new pay structure will be available to both specialists and officers alike. Australia is following a global trend, with several countries recently establishing cyber command-like structures or expanding existing cyber units.
Switzerland joins CFR: Switzerland has joined the EU's Cyber Ranges Federation (CRF), a network designed to carry out joint exercises, training, and research on cyber defense across Europe. [Additional coverage in The Defense Post]
EU data retention plan gets a downvote: The public comments on an EU proposed rule to impose a uniform bloc-wide data retention plan are mainly negative feedback.
EU Paragon meetings: Some EU MEPs will travel to Rome for meetings on Italy's use of the Paragon spyware to spy on journalists and human rights defenders.
China accuses Taiwan of another hack: China accused Taiwan of hacking an unnamed technology company in the city of Guangzhou. China's security service says the hackers have also targeted organizations in ten other provinces. They described the attackers as unsophisticated and claimed they were supported by Taiwan's pro-independence party. Taiwan officials denied the accusations and said Beijing was spreading false information about alleged cyber breaches to shift focus from its own hacks. [Additional coverage in Reuters and Xinhua News/Original MSS statement]
Indonesia blocks the Internet Archive: For reasons unknown, Indonesia blocked the Internet Archive on Monday, May 26.
‼️ Today, on 26th May 2025, #Indonesia started blocking access to the Internet Archive. OONI measurements show a block page returned. OONI data: explorer.ooni.org/chart/mat?te... #ooni #censorship #opendata
— OONI (@ooni.org) 2025-05-27T00:03:08.342Z
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Bobby Filar, Head of Machine Learning at Sublime Security. Bobby takes us through the rising problem of spam bombing, or email bombing, a technique threat actors are increasingly using for initial access into corporate environments.
Arrests, cybercrime, and threat intel
Robbinhood ransomware member pleads guilty: An Iranian national has pleaded guilty to hacking US companies and deploying the Robbinhood ransomware. Sina Gholinejad, 37, faces up to 30 years in prison on hacking and money laundering-related charges. The Robbinhood group is primarily known for its attack and extortion of the city of Baltimore, Maryland. According to court documents, the group also ransomed three other smaller US cities.

Estonia searches for Moroccan hacker: Estonian authorities have issued an arrest warrant for a Moroccan citizen for allegedly hacking a major pharmacy chain in February of last year. The suspect has been identified as 25-year-old Adrar Khalid. He allegedly hacked the Apotheka pharmacy chain using an admin account and downloaded customer loyalty card data. [Additional coverage in ERR]
Nigeria arrests 20 for hacking student exam results: Nigerian authorities have arrested 20 suspects on charges of hacking the country's national exam board to alter results. The suspects are believed to be part of a larger hacker-for-hire syndicate that offered to modify exam scores for prices between $400 and $1,200. The hackers are also suspected of stealing the personal data of almost 380,000 students.
DragonForce hacks an MSP: Sophos says DragonForce has used a chain of SimpleHelp vulnerabilities to gain access to the remote access system of an MSP.
Dark Partners malware campaign: Threat intelligence analyst g0njxa has published an analysis of Dark Patterns, a malware operation using websites impersonating famous AI, VPN services, and software brands that infect users with the Payday Loader and then an infostealer.
Mimo threat actor: Sekoia has identified Mimo, a threat actor that exploits a recently patched Craft CMS zero-day to deploy its own loader, cryptominers, and residential proxyware on hacked websites. Its operators appear to be based in the Middle East.
Malicious PyPI packages: Kaspersky researcher Leonid Bezvershenko has spotted three PyPI packages dropping clippers.
Malware technical reports
AsyncRAT: G DATA researcher Banu Ramakrishnan has published an analysis of AsyncRAT's new Rust-based version.
VenomRAT: DomainTools looks at a malware campaign spreading the VenomRAT for data theft and remote access.
StarFire ransomware: There's a new ransomware strain going around named StarFire.
SafePay ransomware: DCSO has published an analysis of SafePay, a ransomware gang that appeared last October.
Sponsor section
Gain essential visibility into evolving email threats, targeted industry attacks, and sophisticated evasion techniques observed across Q1 2025. Get the "Sublime Email Threat Research Report: Emerging trends & key insights" report here.
APTs, cyber-espionage, and info-ops
Earth Lamia: Trend Micro has published a report on Earth Lamia, a new APT that targets unpatched web apps to gain access to major organizations for data exfil. The group has been active since 2023, and it uses custom-developed tools such as PULSEPACK and BypassBoss.
Vulnerabilities, security research, and bug bounty
RCE in weather devices: ONEKEY researchers have discovered and helped patch an RCE attack vector (CVE-2025-4008) in MeteoBridge, small devices that connect weather equipment to the internet.
GitHub MCP vulnerability: A vulnerability in the official GitHub MCP server can allow attackers to hijack GitHub AI agents and leak data or run malicious code inside private repositories. Attackers only need to open a malicious issue on the targeted repositories to exploit the vulnerability. MCP servers are a new kind of software component that allows AI tools to integrate with software apps, and in this case, with GitHub repositories.
Standoff Bug Bounty payouts: Positive Technologies says that the Standoff Bug Bounty program has paid over $3 million to over 25,000 researchers ever since it launched in May 2022.
Infosec industry
InCyber postpones US conference: The InCyber Forum has postponed its US security conference, citing changes in US geopolitical policies. Several other US security conferences have either canceled or postponed events after low ticket sales. International travelers have avoided traveling to the US after border agencies have detained individuals with valid entry visas. [Additional coverage in the San Antonio Report]
Acquisition news: Israeli security firm Check Point will acquire Veriti, a pioneer of the Preemptive Exposure Management (PEM) market.
SIEM and SOAR guidance: CISA and the ASD have released joint guidance on how to configure secure SIEM and SOAR platforms.
New tool—OnionC2: Security researcher Zarkones has released OnionC2, a command and control tool with communications over Tor.
New tool—Okta Security Detection Catalog: Okta has shared an open GitHub catalog containing a collection of pre-built queries, contributed by Okta personnel and the wider security community, to help customers detect threat actors in their Okta environments.
Threat/trend reports: DB-Engines, F6, the US DIA [PDF], and Wipro have recently published reports and summaries covering various infosec trends and industry threats.
Risky Business podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about cyber's 'hard problems' and why they are intractable.
In this edition of Seriously Risky Business, Tom Uren and Patrick Gray talk about how Telegram took down the two largest ever criminal marketplaces recently. The pair discuss why Telegram is now cooperating with authorities after historically being reluctant and whether this assistance will continue.




