Risky Bulletin: Cyberattack hits Ukraine's state railway
In other news: Cyberattack puts DrayTek routers in a reboot loop; Kuala Lumpur airport hit by major cyberattack; NIST CVE backlog grows bigger despite efforts.

This newsletter is brought to you by Sublime Security, an email security platform that's not a black box. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
Ukraine's state railway company says that a "massive targeted cyber attack" has taken down its online ticketing system over the weekend.
The incident took place on Sunday night. In a Facebook post, Ukrzaliznytsia blamed the incident on "the enemy," a term Ukrainians use to describe Russia.
The company's website is currently down, and officials are restoring from backups. The incident was very likely a data wiper attack, which Russian hackers have employed on numerous occasions since Russia's invasion in February 2022.
The cyber attack has slowed down ticket sales, with large queues forming at train stations across Ukraine.
Kyiv’s central railway station is packed after a massive cyberattack took down its online systems. The railway’s app is down, so people are stuck waiting in long lines to buy tickets offline.
— Daryna Antoniuk (@darynant.bsky.social) 2025-03-24T10:32:05.681Z
Officials say that despite the attack, trains are running normally and without any delays.
Ukrzaliznytsia said this was not the first cyberattack it had to deal with, and it had a response plan in place and ready to go.
Ukraine CERT and the SBU intelligence service are also aiding in investigating and recovering from the attack.
Trains are the primary mode of mass transportation in Ukraine, both internally and abroad. Flights have been grounded across the country ever since Russia's invasion. Most foreign aid and military supplies arrive in the country via freight trains. Ukrzaliznytsia says it has constantly dealt with both cyber and physical attacks over the past three years.
Risky Business Podcasts
Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
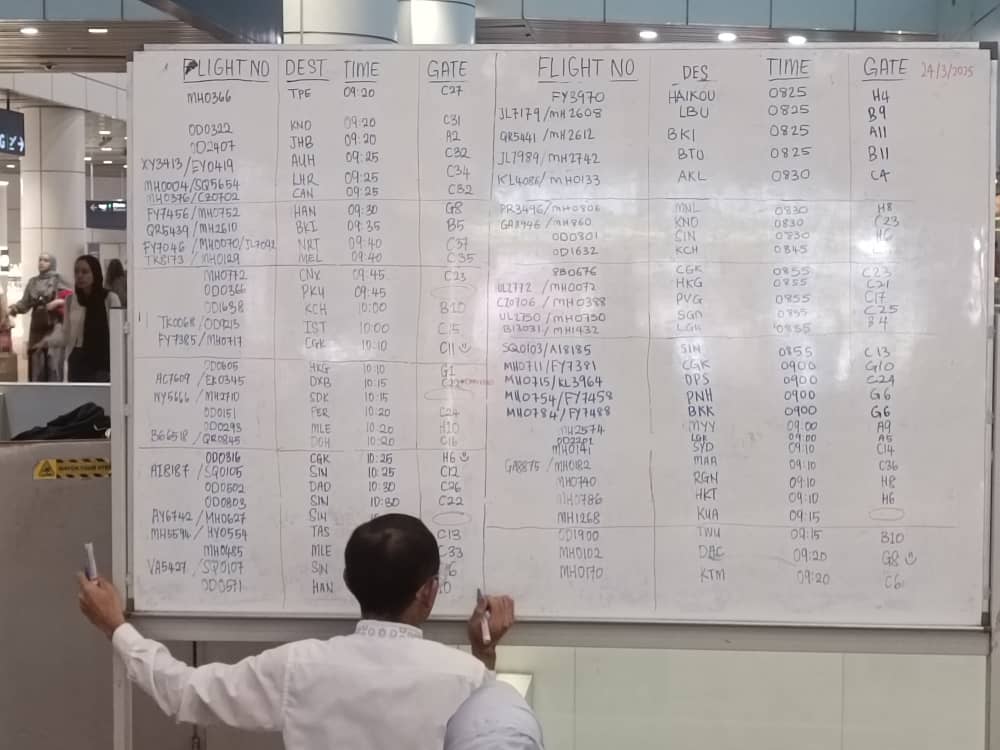
Malaysia declines ransom after airport attack: Malaysian Prime Minister Anwar Ibrahim has declined to pay a $10 million ransom demand after hackers paralyzed some IT systems at the country's main airport over the weekend. The incident forced staff at the Kuala Lumpur International Airport to manually post flight information on a large whiteboard with a pen. Ibrahim says it took him less than five seconds to decline to pay the ransom. The incident bears the signs of a ransomware attack, but no group has taken credit for the attack so far. [Additional coverage in the Malay Mail]
HIBP incident: Have I Been Pwned creator Troy Hunt says the data of over 16,000 newsletter subscribers has been stolen after he fell for a Mailchimp phishing attack.
Cyberattack puts DrayTek routers in a reboot loop: DrayTek Vigor routers across the world have been stuck in a reboot loop after rumors that a threat actor tried exploiting several vulnerabilities over the weekend. Outages have been reported at ISPs in Australia, the UK, Vietnam, and other places. DrayTek has told customers to disable all VPN and remote access features and update to the latest firmware as it investigates the issue. Unconfirmed reports claim the attackers tried exploiting several vulnerabilities disclosed by Faraday Security last month.
Attack on SA's largest chicken producer: A cyberattack has crippled Astral Foods, South Africa's largest chicken and egg producer. [Additional coverage in The Record]
Lovit DDoS: A massive DDoS attack hit the infrastructure of Russian internet service provider Lovit. According to Russia's internet watchdog, the attack peaked at almost 220 Gbps before it was mitigated. The attack allegedly cut off internet access for many Russians and critical infrastructure operators for several days. The IT Army of Ukraine took credit for the disruption. [Additional coverage in TASS]
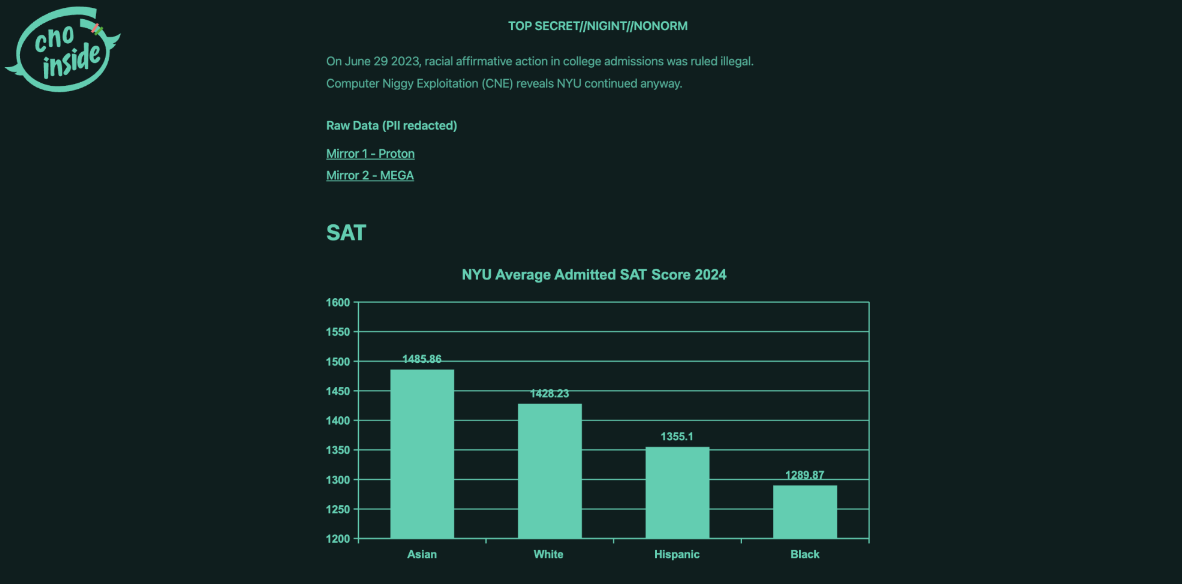
Hacker leaks NYU student data: A hacker defaced the website of the New York University and leaked the personal data of three million students. The data belonged to students admitted to the university since 1989. The hacker claimed the data shows NYU disproportionately admitted hispanic and black students last year. Affirmative action was struck down by a Supreme Court decision in the US in 2023. [Additional coverage in NYU News]
General tech and privacy
Cloudflare shuts down HTTP API access: Cloudflare has shut down HTTP access to its official API. This is one of the many security features the company announced last week during its yearly Security Week event.
OTF sues Trump admin: The Open Technology Fund has filed a lawsuit against the Trump administration for cutting funding previously authorized by Congress. The organization is part of the United States Agency for Global Media and is a major sponsor for Tor, Let's Encrypt, OpenVPN, and many anti-surveillance projects. The White House cut USAGM funding earlier this month through a presidential executive order. [Additional coverage in Bloomberg Law]
EU OS pilot: EDPS researcher Robert Riemann is exploring EU OS, a pilot/proof-of-concept Linux-based operating system designed for the EU public sector.
23andMe files for bankruptcy after mega-hack: DNA and genetic testing service 23andMe has filed for bankruptcy 15 months after experiencing a major data breach. The company has been losing money for years, but its problems were amplified last year after a series of class-action lawsuits related to the breach. Its entire board resigned last year, its CEO last week, and the company is now attempting to sell itself under the supervision of a court. The company has DNA profiles on over 15 million users. Privacy regulators across the US and Europe are now urging users to request the deletion of their data before it's sold.
If you used 23andMe, think about deleting your data. The Attorney General of California is urging users do this due to the company's bankruptcy. Your health and genetic data is the company's biggest asset, unless you avail yourself of the right to delete that data. oag.ca.gov/news/press-r...
— Augie Ray (@augieray.bsky.social) 2025-03-24T15:33:40.602Z
Government, politics, and policy
Russia establishes a national genetic database: The Russian government has established a national genetic database that will aggregate data from over 60 organizations. [Additional coverage in RBC]
Russia to provide companies with "depersonalization" software: The Russian government will supply local companies with software for anonymizing user data before it's submitted to government databases. The software is meant to safeguard the data of Russian citizens but still allow the government to process it. [Additional coverage in Forbes Russia]
Australia cuts down cyber budget: Australia's next federal budget will be light on cybersecurity investments after the sector saw big boosts in 2023 and 2024. [Additional coverage in CyberDaily]
UK NCSC releases PAW guide: The UK's cybersecurity agency has published guidance to help organizations and cyber security professionals implement privileged access workstation (PAW) solutions.
BfV warns German NGOs: Germany's Federal Office for the Protection of the Constitution (BfV) has sent private letters to German NGOs and other civil society organizations warning about a rise in Russian cyberattacks. [Additional coverage in Tagesschau]
Trump Signals change: US President Donald Trump says senior government officials "won't be using Signal very much" in the future, and that the Situation Room is best place for sensitive conversations. The comments come in the wake of a journalist accidentally being added to a so-called Principals Committee Signal group chat that was planning a military strike in Yemen.
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Josh Kamdjou, co-founder and CEO of Sublime Security. Josh goes over recent trends in email badness, such as the increase in QR code abuse and the rise of SVG smuggling.
Arrests, cybercrime, and threat intel
Operation Red Card: Interpol has detained over 300 suspects across Africa involved in cyber attacks and cyber-enabled scams. The suspects were based across seven countries and were involved in mobile banking, investment, and instant messaging scams. Almost half of the suspects were detained in Nigeria, and most were foreign nationals operating out of scam hubs.
Judische agrees to US extradition: Canadian hacker Connor Moucka, known online as Judische and Waifu, has agreed to be extradited to the US to face charges for hacking US cloud provider Snowflake last year and extorting some of its customers. [Additional coverage in CyberScoop]
NFC cloning scams: Russian bank VTB has warned users about a new scheme that tricks users into installing NFC card-cloning spyware on their devices that makes it harder to track fraudulent transactions.
The amount of NFC-cloning-related fraud in Russia right now is a sign of a growing storm about to hit the EU and US in a few months. Criminal groups are refining their methods and attacks right now.
— Catalin Cimpanu (@campuscodi.risky.biz) 2025-03-24T20:24:57.422Z
Atlantis AIO: Abnormal Security has published an analysis of Atlantis AIO, a cybercrime service designed to automate credential-stuffing attacks.
CS2 phishing campaigns: Silent Push looks at a phishing campaign targeting CounterStrike 2 and other video game players.
Ukroboronprom phishing campaign: DomainTools has spotted a phishing campaign impersonating Ukroboronprom, Ukraine's largest arms manufacturer. [Additional coverage in NextGov]
Crypto-scams arrive on BlueSky: After plaguing Twitter, Facebook, and YouTube for years, crypto-scam campaigns have now arrived on BlueSky.
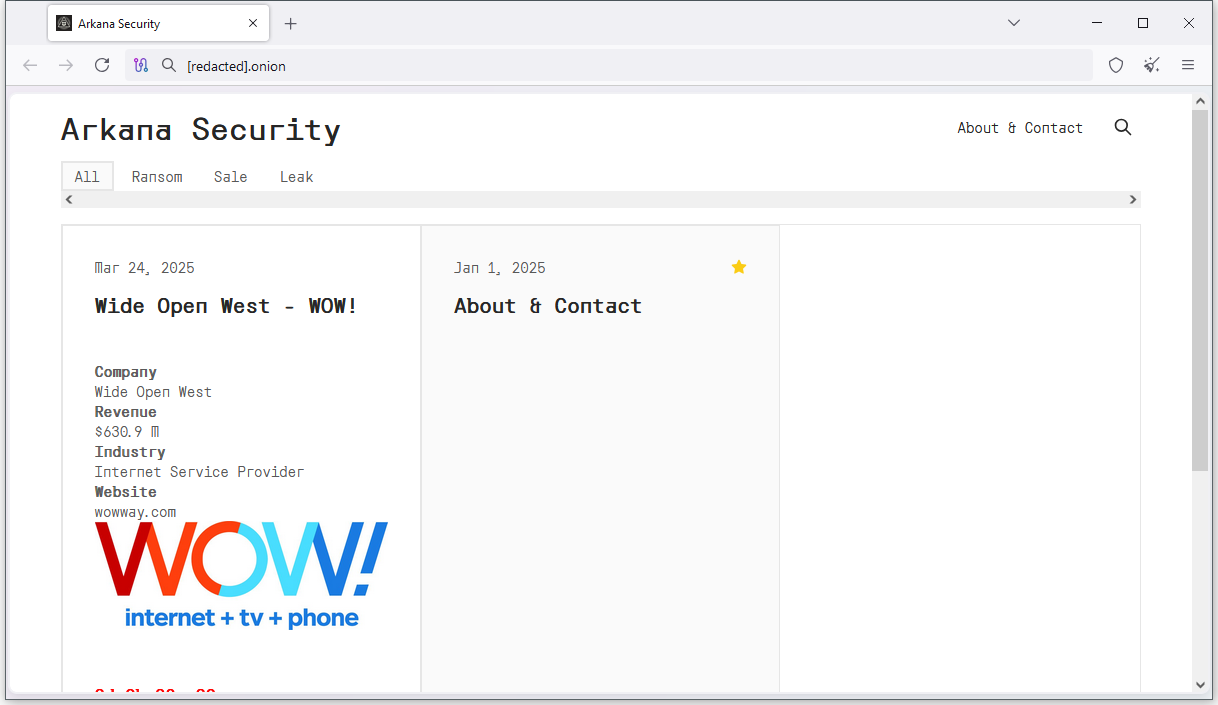
New Arkana ransomware group: The infosec world welcomed a new ransomware gang this week named Arkana. Their first victim is WOW, one of the largest ISPs in the US.
Malware technical reports
Raspberry Robin: Silent Push looks at the evolution of the Raspberry Robin USB worm over the past two years and its sprawling connections to a bunch of old and new Russian cybercrime rings. The report also uncovered loads of new C&C infrastructure.
New Android malware: McAfee has spotted a new Android malware strain abusing the official Microsoft .NET MAUI cross-platform development framework to evade detection.
GorillaBot: ANY.RUN has published a technical report on GorillaBot, a new IoT botnet that launched last September and has been behind a bunch of major DDoS attacks.
IOCONTROL: Flashpoint has published an analysis of IOCONTROL, a new malware designed to infect IoT and OT devices. The tool was used last year by Iranian group CyberAv3ngers.
ReaderUpdate: SentinelOne has published a report on a new Go version of the old ReaderUpdate macOS malware loader typically used to deliver adware.
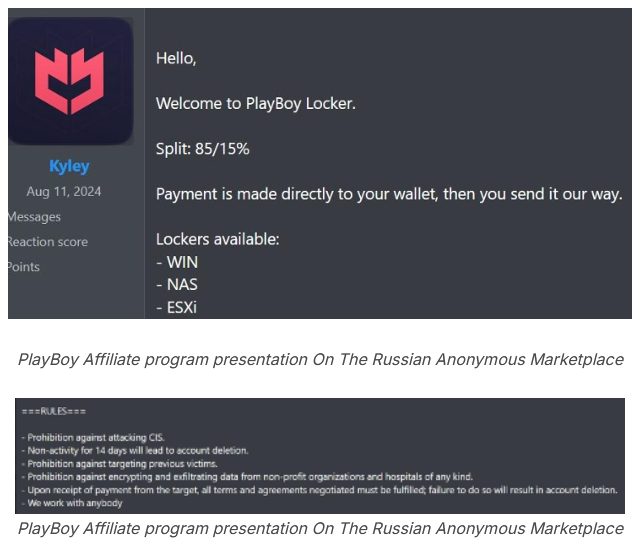
PlayBoy Locker RaaS: Cybereason has spotted a new Ransomware-as-a-Service platform named PlayBoy Locker.
Sponsor section
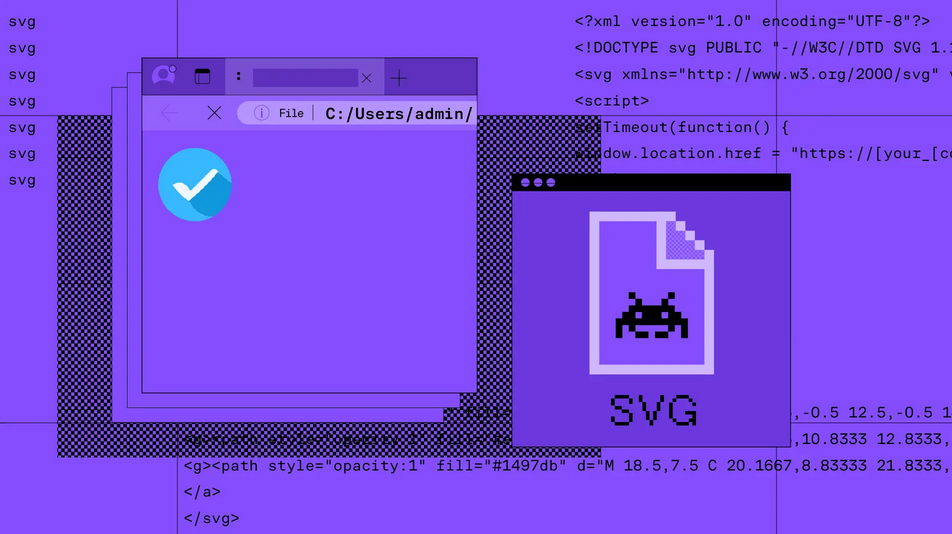
Sublime Security explores a new type of attack observed in the wild—the embedding of malicious JS code within SVGs to deliver adversary-in-the-middle credential phishing attacks.
APTs, cyber-espionage, and info-ops
Weaver Ant: A Sygnia report looks at a Chinese APT's four-year-long intrusion into the network of an Asian telco "despite multiple eradication attempts."
Austria uncovers Russian disinfo campaign: Austrian intelligence service DSN uncovered a Russian disinformation campaign active in the country that was spreading false information about Ukraine and its president. The campaign started shortly after Russia's invasion and was allegedly run by a Bulgarian woman. DSN says it filed espionage charges against the suspect, but a local court refused to issue an arrest warrant.
Pro-Qatar disinformation: Haaretz has published a report on a pro-Qatar campaign running on X and linked to a company allegedly run by Benjamin Netanyahu's aids.
Vulnerabilities, security research, and bug bounty
New EDR bypass: Security researcher Wietze Beukema has discovered a new EDR/AV bypass technique that relies on making slight changes to command-line arguments. Over 70 Windows executables can be abused this way.
Windows CimFS EoP: StarLabs has published a report on CVE-2024-26170, a Windows CimFS EoP vulnerability that was patched last year.
CrushFTP vulnerability: The CrushFTP project has released a security update for a vulnerability that can allow attackers to access the FTP server without authentication.
Appsmith unauth RCE: Rhino Security has discovered an unauth RCE in the Appsmith admin panel, dashboard, and backend-making toolkit.
EncryptHub was behind recent MMC zero-day: A Russian threat actor named Water Gamayun (or EncryptHub and Larva-0208) was behind a recent zero-day (CVE-2025-26633) in the Microsoft Management Console that the company patched this month. The group is a known affiliate of the RansomHub and Blacksuit ransomware operations.
VMware security update: Broadcom has released a security update for VMware Tools to address an authentication bypass.
EPSSv4 is out: FIRST has released v4 of the Exploit Prediction Scoring System (EPSS). Patrick Garrity of VulnCheck has an update on what changed.
NIST backlog grows bigger: The US National Institute of Standards and Technology (NIST) expects the backlog for the US National Vulnerability Database (NVD) to grow despite efforts to address the issue at the end of last year. NIST started developing a backlog for new NVD entries in February of last year when vulnerabilities started being added to the database without additional metadata and information. The agency hired external contractors to address the backlog, but tens of thousands of CVE entries are still missing crucial information. In an update last week, NIST said the backlog will likely continue this year. The agency blamed the issue on a 32% increase in vulnerability submissions last year, which is also expected to grow this year. It says it's now exploring "machine learning to automate certain processing tasks."
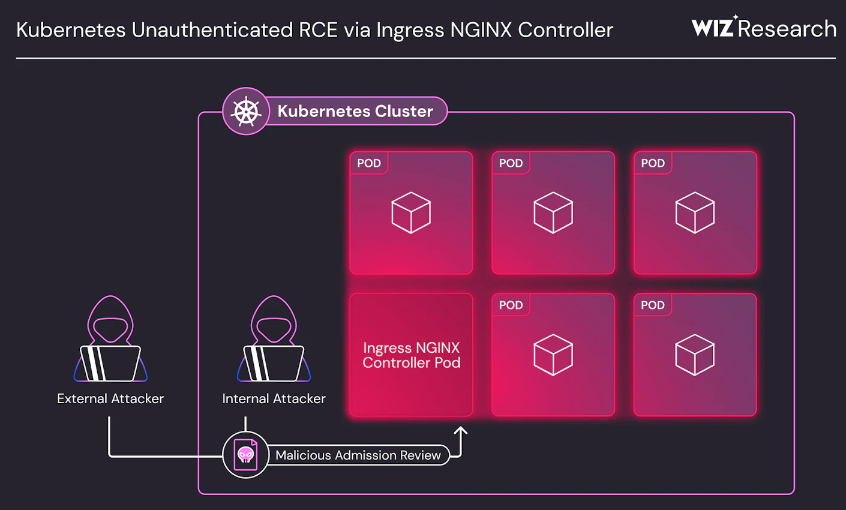
IngressNightmare vulnerability: Around 43% of current cloud environments are vulnerable to a new Kubernetes attack known as IngressNightmare. The attack is a chain of four vulnerabilities in the Ingress NGINX Controller for Kubernetes that can be chained to execute malicious code on Kubernetes infrastructure without proper authentication. Security firm Wiz has found at least 6,500 Kubernetes instances vulnerable to the attack, including many instances at Fortune 500 companies. The Kubernetes project released patches on Monday.
"Exploitation of these vulnerabilities leads to unauthorized access to all secrets stored across all namespaces in the Kubernetes cluster by attackers, which can result in cluster takeover. This attack vector has been assigned a CVSS v3.1 base score of 9.8."
Infosec industry
CVE program profile: Cynthia Brumfield has a nice profile on MITRE's CVE program on CyberScoop.
"MITRE's Summers says, 'It's been 25 years of this program, and I don't know if it's possible to name another such public-private partnership program that has lasted that long and has continued to be so impactful in an ongoing way. I'm excited about the opportunity to continue evolving in ways that bring value to the community.'"
New tool—OPKSSH: Cloudflare has open-sourced OPKSSH (OpenPubkey SSH), a tool to support single sign-on (SSO) for SSH.
Threat/trend reports: FIRST, Kaspersky, KELA, Ontinue [PDF], and Zscaler have recently published reports and summaries covering various infosec trends and industry threats.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about why people studying cyber operations are fascinated by zero-days. These are vulnerabilities or exploits that have been found in a system before the vendor or manufacturer is made aware of them, and so, therefore, no fix exists.
Tom Uren and Patrick Gray discuss how China's Ministry of State Security is increasingly doxxing and threatening Taiwanese APT operators. In some ways, this mirrors the US strategy of naming and shaming Chinese cyber operators in indictments that contain lots of supporting information. But although MSS statements are filled with propaganda rather than technical detail, naming Taiwanese military hackers has some bite.




