Risky Bulletin: CoinMarketCap hacked via a doodle image
In other news: White House rejects NSA & CyberCom nomination; FCC probes US Cyber Trust Mark program; cyberattack disrupts Russian animal processing industry.

This newsletter is brought to you by Authentik. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
CoinMarketCap—the go-to website where everyone goes to check cryptocurrency exchange rates—was hacked on Friday.
Hackers exploited a vulnerability in CoinMarketCap's animated logo (see CoinMarketCap's doodle obsession here) to append malicious code that displayed an unauthorized popup.
The popup ran a specialized phishing kit called a "crypto-drainer" that prompted users to connect their crypto-wallet accounts and then stole their funds.
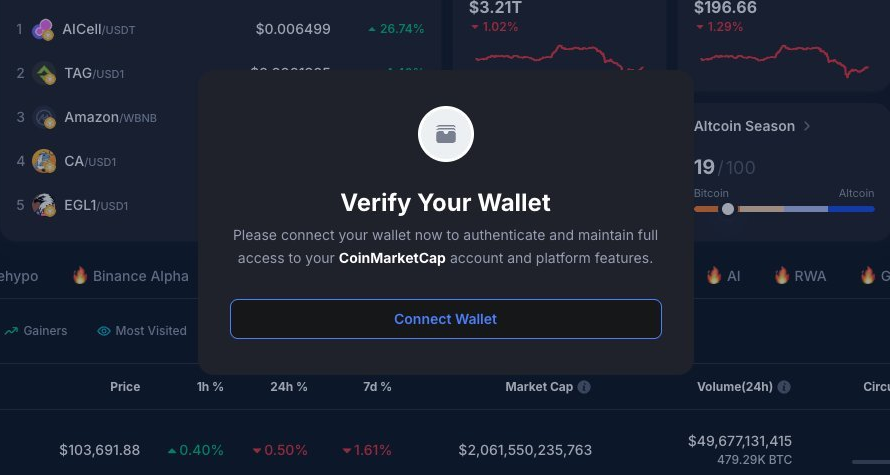
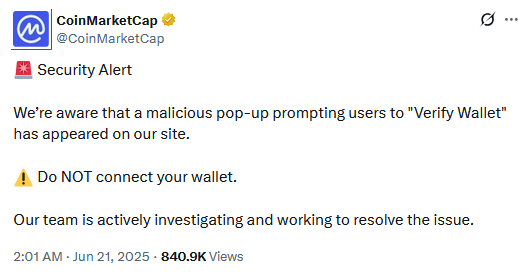
The malicious code ran for only a few hours, but according to reports, the hackers managed to steal almost $45,000 worth of assets from over 110 users.
According to ReyXBF, the threat actor behind the attack is a French-speaking individual who goes online as Zartix and Spadle.
They are connected to an underground community known as The Com, which is the same community from where the Scattered Spider group also originates.
Security firm C/side says the malicious code used in the attack is connected to Inferno Drainer, a well-known crypto-drainer phishing kit.
The service launched in February 2023, pretended to shut down later that year, but continued to operate. Security firm Check Point says Inferno Drainer was likely behind the theft of over $250 million worth of crypto assets throughout its entire operational history.
Risky Business Podcasts
The main Risky Business podcast is now on YouTube with video versions of our recent episodes. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
Aflac breach: A cybercrime group breached US insurance firm Aflac. The intruders allegedly used social engineering to gain access to its internal network and steal customer data. The company described the hackers as a "sophisticated cybercrime group." Aflac is likely referring to individuals loosely connected to the Scattered Spider community. Google warned earlier this month that the group shifted from targeting retailers to the insurance sector.
Oxford breach: The UK city of Oxford suffered a security breach and is notifying current and former employees that hackers stole their personal details. Impacted employees include individuals who worked on city elections between 2001 and 2022. The breach took place on June 6, and the city says it has now secured and restored affected systems.
AT&T breach settlement: A US judge approved a preliminary approval for a $177 million settlement in a class-action lawsuit filed against AT&T over several 2024 security breaches. [Additional coverage in Investing]
Feng Chia University ransomware attack: The Feng Chia University in Taiwan has fallen victim to a ransomware attack. The Nova ransomware group took credit for the intrusion. [Additional coverage in FocusTaiwan]
Tonga hit by another cyberattack: A ransomware attack has hit Tonga's national healthcare system. The incident took down its public website and several internal systems. A team of Australian cyber experts flew to Tonga last week to help the small Pacific island recover from the incident. This is Tonga's second major ransomware attack after the Medusa group hit the country's state-owned telecommunications company in 2023. Micronesia, Palau, and Vanuatu also fell victim to crippling ransomware attacks over the past two years. [Additional coverage in Talanoa'o Tonga]
Cyberattack hits Russia's animal processing industry: A cyberattack has taken down a Russian government system used to manage animal health and veterinary documents. The attack on the VETIS system has impacted several industries that work with animal products. The worst is the dairy sector, where companies can't accept raw milk for processing without a VETIS digital certification. Companies have reverted back to working with paper documents, but this is impacting production. [Additional coverage in Shoppers Media/English coverage in The Record]
Salt Typhoon hacks Canadian telco: Chinese cyber-espionage group Salt Typhoon hacked an unnamed Canadian telco in February. The hackers broke in by exploiting an old 2023 vulnerability in Cisco devices. Salt Typhoon's telco hacking spree came to light last year, and this is the group's first non-US victim. [Additional coverage in FBI&CCCC advisory/PDF]
Iran hacks Tirana: Iranian hackers have breached and wiped the servers of Albania's capital city, Tirana. The attack took down the city's website and the public registration system for kindergartens and nurseries. The Homeland Justice group took credit for the attack. The group is affiliated with Iranian intelligence and attacked Albania twice in similarly destructive attacks in 2022 and 2023. The group is targeting the country for sheltering Iran's MEK opposition party. [Additional coverage in the Tirana Times]
BitoPro hack linked to North Korea: Taiwanese cryptocurrency exchange BitoPro has blamed North Korea for a recent crypto-heist. The company says the Lazarus hacking group stole $11 million worth of crypto-assets from its wallets at the end of May. The group allegedly socially engineered an employee and stole AWS session tokens to bypass MFA and access its cloud infrastructure. They then waited for a wallet upgrade procedure to hijack funds when staff was expecting the assets to move.
Cosmos DPRK IT worker incident: The Cosmos blockchain has published a post-mortem of a security incident last year when it accidentally hired a North Korean IT worker to write code for one of its SDKs.
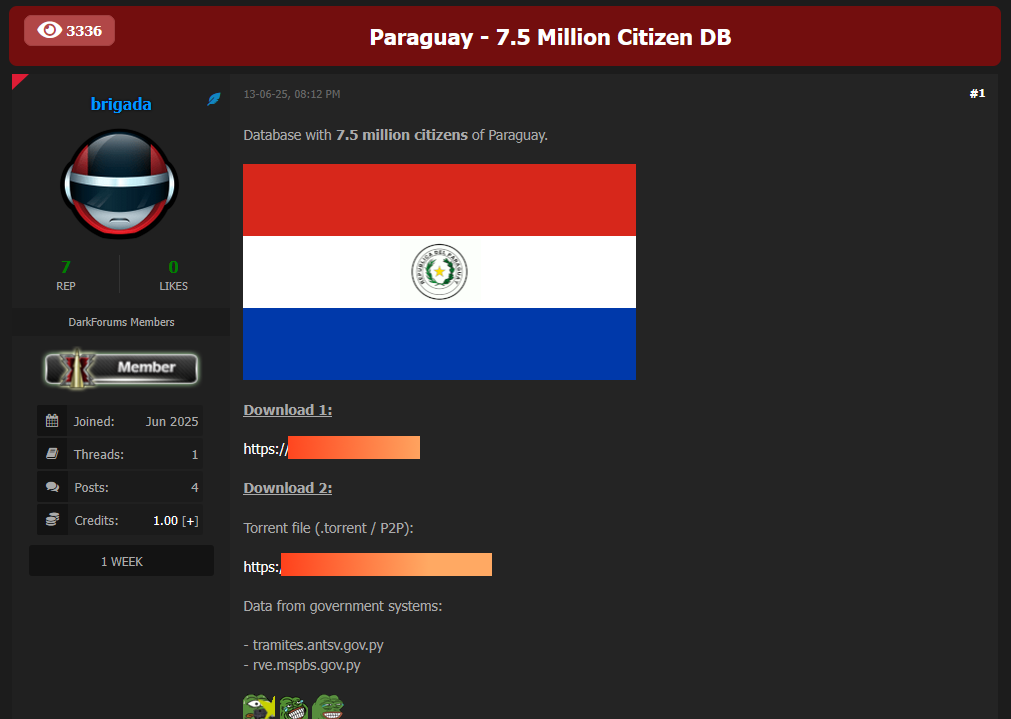
Paraguay data leaked after government declined ransom: Hackers have leaked the data of 7.4 million Paraguayan citizens after the government declined to pay a ransom demand. A hacking group named the Brigada Cyber PMC demanded a $7.4 million ransom, roughly $1 for each entry. Security firm Resecurity believes the data was taken from at least two government agencies. The data includes the personal details of all current citizens, but also many deceased ones. [Additional coverage in the OCCRP]
General tech and privacy
Microsoft removes legacy drivers from Windows Update: Microsoft will remove old legacy drivers from the Windows Update system. The OS maker says it's doing this to mitigate security and compatibility risks. Microsoft will first remove old drivers that have newer versions and then old drivers that no longer have an audience or install base. Clean-ups of old drivers will take place at periodic intervals.
Paragon open letter: Representatives from 15 human rights organizations have sent an open letter to the CEOs of spyware maker Paragon Solutions and its parent company AE Industrial Partners, asking for more accountability regards the use of its tools against journalists and activists in Europe.
Twitter sues New York over transparency laws: Twitter has sued the state of New York over a new transparency law that requires online platforms to disclose how they moderate hate speech and disinformation. Twitter is currently flooded in both, and there's rarely any moderation on the platform. The company argues the law violates the First Amendment, while privacy groups argue Twitter is just protecting abusers and disinformation groups. Just the existence of this lawsuit tells you everything you need to know about Twitter. [Additional coverage in France24]
Google trained AI on YouTube vids without permission: YouTube content creators are beyond furious after Google admitted that it trained its AI on their videos without their permission. [Additional coverage in CNBC]
Government, politics, and policy
White House rejects NSA&CyberCom pick: The White House has rejected the Pentagon's pick for the next head of the NSA and Cyber Command. The DOD proposed Army Lt. Gen. Richard Angle to replace Gen. Timothy Haugh, who was dismissed by President Trump in April. According to Politico, Angle had the support of both Defense Secretary Pete Hegseth and Director of National Intelligence Tulsi Gabbard.
Judge overturns HHS privacy rule: A Texas judge has overturned an HHS rule passed during the Biden administration that bolstered privacy protections for Americans seeking abortion and gender-affirming care. [Additional coverage in The Record]
FCC probes Cyber Trust Mark program: The FCC is investigating the company that manages the US Cyber Trust Mark program. The program launched earlier this year and assigns safety labels to IoT devices based on their cybersecurity features. The FCC says UL Solutions has "deep ties to China," such as joint ventures and testing labs in "particularly alarming" locations. [Additional coverage in PCMag]
Russia sabotages Cloudflare: Russian internet traffic to Cloudflare infrastructure has fallen by 30% after the country's communications watchdog started filtering traffic to the service. The agency denies this, but this is Roskomnadzor's way of telling local companies to switch from the provider before it gets fully blocked. It did the exact same thing to YouTube before finally admitting it was intentionally throttling traffic. [Additional coverage in Kommersant]
China and Russia on equal footing: In an interview with the Financial Times, Czech President Petr Pavel said that China and Russia are on par and pose a similar threat when it comes to state-sponsored hacking and espionage.
Israel tells citizens to turn off security cameras: The Israeli government has told citizens to turn off security cameras. Officials say Iran is hacking security cameras and using live feeds to adjust missile targeting. The same tactic was also used by Russia when striking targets in Ukraine, forcing Ukraine to put out similar warnings since 2022. [Additional coverage in Bloomberg]
Only 2% paid ransoms in the Netherlands: According to the Dutch Central Bureau of Statistics, only 2% of companies that suffered a ransomware attack in 2023 paid the attackers.
UK Cyber Growth Action Plan: The UK government will invest £16 million in UK cybersecurity startups this year. The investment will be made available via a new government program named the Cyber Growth Action Plan. The government has established a new board to help allocate the funds. The UK has one of the biggest cybersecurity sectors in the world, with £13.2 billion in annual revenue and over 2,100 cybersecurity firms.
Austria to monitor secure messengers: The Austrian government has agreed on a legal framework to allow police to monitor a suspect's secure messaging. The framework would go into effect in 2027 once it passes a Parliament vote. If it passes, police will be able to request a surveillance warrant from a three-judge panel to monitor special suspects. Police will have to file a report with the Parliament if they request more than 30 warrants in a year. [Additional coverage in Reuters]
EU spyware debate falls flat: Two years after the findings of the PEGA committee, the EU Parliament held a plenary hearing on spyware. It was a large collection of hollow statements. [Additional coverage in Euractiv]
For a former PEGA member the words of Commissioner @hennavirkkunen.bsky.social sound spectacularly hollow. The @ec.europa.eu sounds like a broken record, repeating the mantra that it is for the national authorities. I.e. the perpetrators themselves. #spyware www.europarl.europa.eu/plenary/en/h... t
— Sophie in't Veld (@sophieintveld.bsky.social) 2025-06-16T16:13:02.278Z
Back to yesterday's plenary debate on illegal spyware 2 years after the recommandations of the enquiry committee. Commission came with empty hands. The victims are not about to get an answer.
— Saskia Bricmont (@saskiabricmont.bsky.social) 2025-06-17T11:55:00.082Z
Sponsor section
In this Risky Bulletin sponsor interview, Fletcher Heisler, CEO of Authentik, talks to Tom Uren about the inflection points that make organisations consider rationalising their Identity Providers (IdPs). The pair also discuss sovereign tech stacks and how to earn the trust of customers.
Arrests, cybercrime, and threat intel
Evil twin hacker pleads guilty: An Australian man pleaded guilty to setting up fake WiFi networks to steal personal data. Michael Clapsis, 43, ran fake free WiFi access points at the Perth, Melbourne, and Adelaide airports, during multiple domestic flights, and at work. He used evil twin attacks to redirect users to phishing pages and capture credentials. He then accessed personal accounts and collected intimate photos and videos of women. Clapsis also hacked his employer and accessed emails between his boss and police after his arrest. [Additional coverage in WAtoday]
New npm malware: Two hundred ninety-two malicious npm packages were discovered and taken down last week. Check out the GitHub security advisory portal for more details.
DHS warns of Iranian cyberattacks: The US DHS has issued a rare national terrorism advisory about possible Iranian repercussions following the US' attacks on the country's nuclear infrastructure. Responses could include terrorist and cyber attacks. [Additional information in the DHS NTAS advisory/PDF]
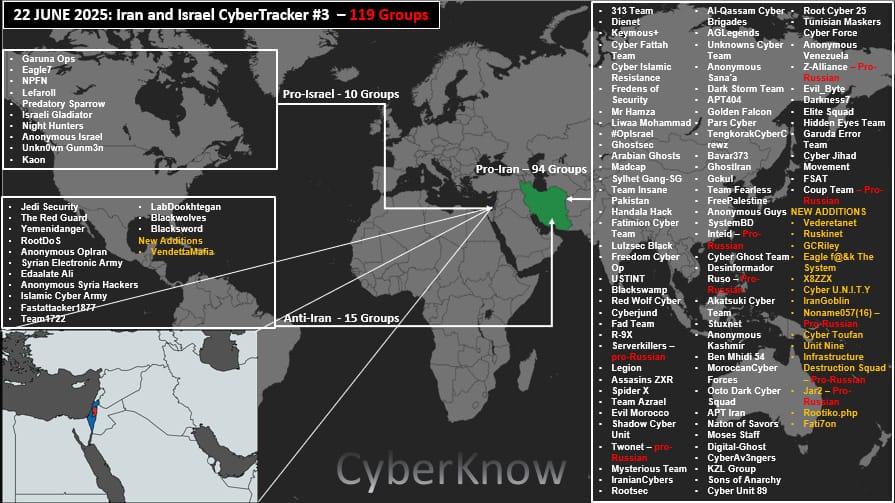
Israel-Iran cyber war: CyberKnow has set up a tracker for all the hacktivist groups involved in the recent Israel-Iran armed conflict. Currently, there are 119 groups involved, with most supporting Iran.
Malware technical reports
Prometei Linux variant resurgence: Palo Alto Networks says the Prometei botnet is making a comeback. The company has spotted not one but two new versions, v3 and v4. While the botnet can infect both Linux and Windows, PAN says the new versions seem to focus more on Linux.
"While its primary goal is cryptocurrency (Monero) mining, Prometei also possesses secondary capabilities, such as stealing credentials and deploying additional malware payloads. We assess that Prometei's operations appear driven by financial gain, and there is no evidence of ties to nation-state actors."
RapperBot goes after DVRs: Japan's NICT has published a report on the RapperBot botnet's attacks on DVR devices. According to a separate report from Chinese security firm QiAnXin, the botnet saw a recent resurgence and is now involved in DDoS extortion attacks.
Amatera Stealer: Proofpoint identified a new, rebranded stealer based on ACR Stealer called Amatera Stealer. It is sold as a MaaS.
SpyNote: Hunt has found fake versions of the Google Translate app spreading the SpyNote spyware.
AntiDot Android botnet: Security firm Prodaft has published a report on AntiDot, an Android trojan sold under a MaaS model on underground hacking forums.
Sponsor section
Authentik is an open-source identity provider that is also offered with paid enterprise features. In this demo, CEO Fletcher Heisler and CTO Jens Langhammer walk Risky Business host Patrick Gray through an overview and a demo of the technology.
APTs, cyber-espionage, and info-ops
The Confucius APT's Anondoor: Knownsec 404 has published an analysis of Anondoor, a new backdoor used by the Confucious APT.
"Its backdoor component is encapsulated in a C# DLL file and evaded sandbox detection by loading the specified method through invoke. Meanwhile, by using the parameterized C2 (Command and Control) communication mechanism, it is ensured that even if some components are captured, attackers can still hide the real C2 infrastructure, which greatly increases the difficulty of traceability and defense."
BlueNoroff Zoom attack: Field Effect and Validin look at recent BlueNoroff APT campaigns that use malicious Zoom extensions to target employees in the crypto ecosystem. This looks to be related to some recent Ability AI and Huntress reports.
Matryoshka campaign plays as a telenovela: In the latest disinfo campaign from Russian group Matryoshka, the group is hallucinating a feud between Moldovan President Maia Sandu and European Commission Vice President Kaja Kallas. [Additional coverage in The Insider and this Antibot4Navaly thread]
7/ Fake @BusinessInsider.com video: Today's confrontation over the position of VP of the EC between Kallas and Sandu is an aftermath of their 2024 clash in the pharmaceutical and agricultural fertilizer market in Europe.
— antibot4navalny | bot blocker | блокировщик ботов (@antibot4navalny.bsky.social) 2025-06-20T00:50:44.813Z
Matryoshka goes after Armenia: The same group is also going after Armenia's Prime Minister Nikol Pashinyan for the first time. [Additional coverage in The Insider]
Update on Russia's Matryoshka campaign - Over the last 24 hours the Matryoshka trolls have been sending links to fake news stories attacking the Armenian Prime Minister Nikol Pashinyan. This is the first time they've mentioned Armenian in the emails they've been sending to us the past few years.
— Eliot Higgins (@eliothiggins.bsky.social) 2025-06-18T08:23:47.778Z
Vulnerabilities, security research, and bug bounty
FreeType zero-day linked to Paragon attacks: Israeli spyware maker Paragon Solutions used a zero-day in the FreeFont font-rendering library to deploy the Graphite spyware on Android devices. According to SecurityWeek, the zero-day was exploited via PDF files sent via WhatsApp. The zero-day (CVE-2025-27363) was patched in March after Meta spotted the attacks. This is the second zero-day linked to Paragon after a similar one in iOS was revealed last week.
WP exploitation targets Motors Theme: Threat actors have abused a vulnerability in the Motors Theme to hijack WordPress sites for the past two weeks, according to Wordfence.
ZPos issues: Security researcher Paul Moore has found multiple vulnerabilities in the e-POS systems ZPos. The vulnerabilities are still unpatched and allow attackers to modify payment details, such as prices and discounts, steal or change a user's account passwords, or run code in their browser.
Apache Traffic Server DoS: Imperva has published a write-up on CVE-2025-49763, a denial of service bug they found in the Apache Traffic Server.
"Remote attackers can trigger an avalanche of internal ESI requests, exhausting memory and causing denial-of-service in Apache Traffic Server."
Pterodactyl RCE: The Pterodactyl project has patched a perfect 10/10 vulnerability that allows attackers to run code remotely on game server management panels. [h/t cR0w]
IBM Storage Protect hardcoded admin account: IBM has released a security update to fix a vulnerability in its Storage Protect backup servers. The company says attackers could bypass authentication by using a built-in admin account. The issue impacts all versions released since April 2021.
New ASUS hardcoded API creds: ASUS has removed hardcoded API credentials from the MyASUS app that could have allowed attackers access to ASUS user details. A software engineer from New Zealand discovered the credentials inside DLL files installed by the MyASUS app. The credentials had administrator-level permissions that could have allowed attackers access to any ASUS account. The bug impacts all MyASUS versions since the app was released in August 2022 and likely affects millions of users.
Infosec industry
Threat/trend reports: Aon, the Cyber Threat Alliance, CyberSmart [PDF], the Dutch CBS, Microsoft, Red Canary, Virus Bulletin, and Zscaler have recently published reports and summaries covering various infosec trends and industry threats.
New tool—ctail: HD Moore has released ctail, a tail-like tool for CT logs.
New tool—Golem: Bushido Security has released Golem, a tool to automate C/C++ vulnerability discovery.
New tool—linWinPwn: Security researcher Joe Farjallah has released linWinPwn, a Bash script that streamlines the use of a number of Active Directory security tools.
New tool—SGCC: JCSteiner has released SGCC, a C&C framework that uses minimalist PowerShell implants.
New tool—VMwhere: Indian CS student "21verses" has released VMwhere, an obfuscation engine built on top of LLVM.
New tool—Paragon: Security researcher PayloadArtist has released Paragon, a note-taking web app designed for bug bounty hunters.
Risky Business podcasts
In this edition of Seriously Risky Business, Tom Uren and Patrick Gray talk about a Minnesota man who used people-search services to locate, stalk, and eventually murder political targets. They also discuss the purported hacktivist group Predatory Sparrow weighing in on the Iran-Israel conflict.
In this edition of Between Two Nerds, Tom Uren and The Grugq take a look at a new AI-powered covert influence campaign and compare it to World War 2 efforts.




