Risky Bulletin: Cock[.]li gets hacked
In other news: WaPo email accounts hacked; hackers disrupt and steal data from Sorbonne University; EU invests €145.5 million in hospital security.
![Risky Bulletin: Cock[.]li gets hacked](/content/images/size/w1200/2025/06/000-RBN-logo-6.png)
This newsletter is brought to you by enterprise browser maker Island. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
A threat actor named Satoshi has allegedly hacked controversial email provider Cock[.]li and is now selling its data on an underground hacking forum.
They are selling this data on a Russian language underground hacking forum named XSS for 1 Bitcoin, or approximately $105,000.
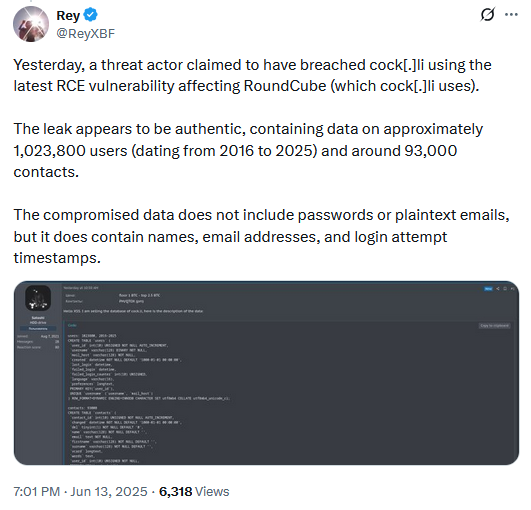
The hacker allegedly used a recently disclosed zero-day in the Roundcube webmail software (CVE-2025-49113) to dump Cock[.]li's database and steal the details of over one million registered users.
The email service denied getting breached in a post-mortem published on its webmail page, claiming that the vulnerability exploited in the attack does not affect its version of Roundcube—even if public reporting says it does.
Even if it found "no signs of intrusion or successful exploitation," Cock[.]li said it plans to stop using Roundcube regardless. It has told users to use a desktop email client to connect to their email accounts until it chooses another webmail software solution.
Although Cock[.]li denied getting hacked, Risky Business spoke to several threat intel researchers who confirmed the authenticity of leaked samples and believe the breach is real.
The data is a threat intelligence gold mine and will most likely end up high on the must-buy list of many cybersecurity firms and law enforcement agencies.
Cock[.]li launched in 2013 as a free email service and was quickly adopted by the internet's worst figures. Its email addresses have often been used for sending death and bomb threats and for ransomware and data extortion campaigns.
Its early adoption by the internet's scumbags got the service into legal problems early on, and German authorities seized server hard drives back in 2015 in an investigation connected to a major bomb hoax across the US.
The zero-day allegedly used in the attacks has its own history and is the very definition of what security researchers call a "patch gap," a technique where someone goes through security updates of open-source projects or smaller libraries before they make it to larger projects or commercial products.
In the case of Roundcube, the project's developers deployed a security fix to the GitHub codebase but then took days to deliver a new project version, leaving information about the security flaw in the public domain and Roundcube webmail servers exposed to attacks.
According to security firm FearsOff, threat actors noticed the modified code and sold exploits for the bug on hacking forums before Roundcube shipped the fix and before users could deploy it.
The Shadowserver Foundation estimated that over 85,000 Roundcube webmail servers were exposed to attacks, and many still are even today. It's very likely that a huge swath of these got hacked and their data is now traded or sold on underground forums, just like Cock[.]li.
Risky Business Podcasts
The main Risky Business podcast is now on YouTube with video versions of our recent episodes. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
WaPo email accounts hacked: The Washington Post has notified staff that hackers gained access to some of its reporters' email accounts. The hack primarily targeted reporters covering national security and economic policy. According to the Wall Street Journal, the hack appears to be the work of a foreign government. The breach was discovered on Thursday, and staff were notified on Sunday.
WestJet breach: Canadian airline WestJet is investigating a security breach that disrupted some of its internal systems. The incident affected the company's website and mobile app for several hours on Friday. The company says there were no disruptions to scheduled flights.
Zoomcar breach: Indian car-sharing platform Zoomcar says hackers breached its network and stole the data of 8.4 million users. The intruders stole customer names, phone numbers, car registration numbers, home and email addresses. The hackers are now extorting the company, threatening to release the data if a ransom wasn't paid. The company suffered a similar breach in 2018 when hackers stole the data of 3.5 million users.
Sorbonne security breach: Sorbonne University, France's most prestigious university, has fallen victim to a cyberattack. The intrusion took place earlier this month and damaged several of the university's IT systems. Officials say the hackers also stole sensitive data from the hacked systems, including banking details and social security numbers for some of its staff. The university also experienced a security breach in October last year when hackers stole the personal information of over 73,000 staff and students. [h/t Valéry Rieß-Marchive]
Orion Telecom hack: Ukraine's military intelligence agency GUR has allegedly hacked Russian internet service provider Orion Telecom. GUR hackers allegedly disabled 370 servers and 500 network switches and wiped backup servers. The hack caused widespread internet and TV outages across four major Russian cities. The intrusion took place on June 12, Russia's national day. Hacktivist group BO Team was also involved in the breach. [Additional coverage in Kyiv Post]
US helps Vietnam with sensitive ransomware attack: A US law enforcement agency provided a decrypter to help a major Vietnamese state company recover from a ransomware attack. The attackers demanded a $2.5 million ransom after encrypting more than 1,000 of the company's servers. Vietnamese officials worked with the US because there's no legal framework to allow state companies to pay ransoms. The victim was identified only as an energy company with billions of dollars in annual revenue. [Additional coverage in VietnamNet Global]
General tech and privacy
Ireland fines itself: Ireland's data protection agency has fined its social protection agency €550,000 for unlawfully collecting biometric data from users who set up a Public Services Card. [Additional coverage in RTE]
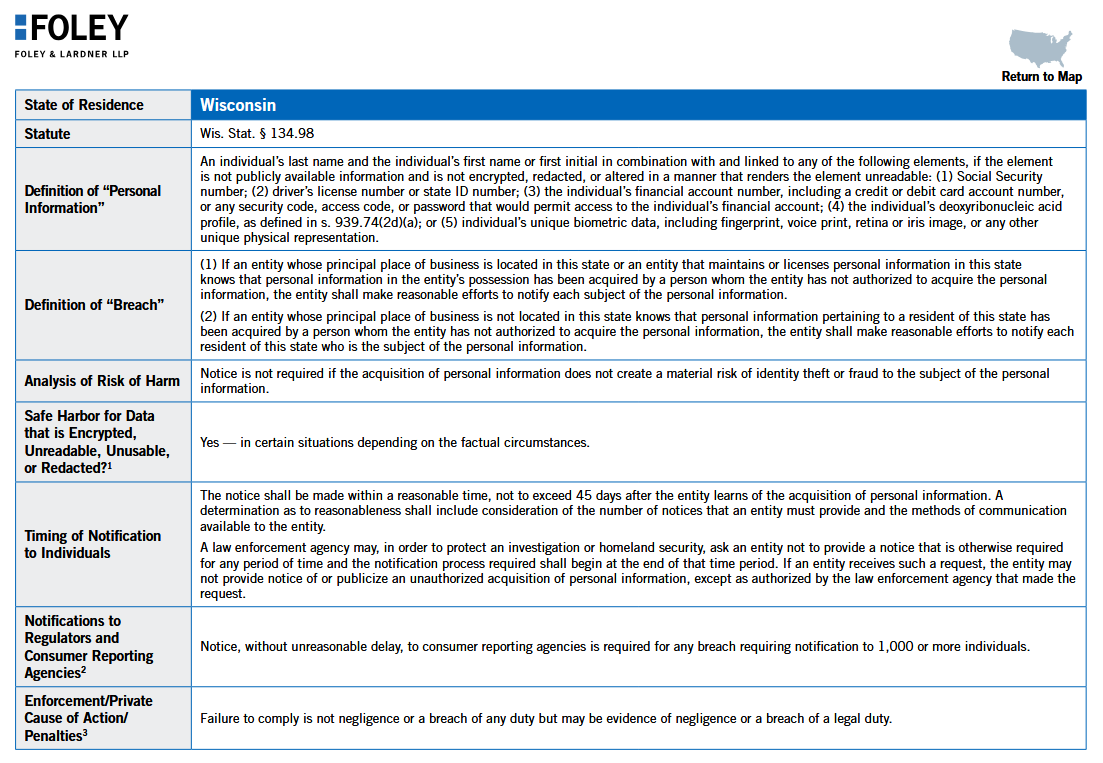
US data breach notification laws: US law firm Foley & Lardner has published an overview of all the data breach notification laws active at the level of each US state. [h/t DataBreaches.net]
Google outage: Google says an issue in its API management platform was to blame for last week's outage that impacted its own services and even many other third-party websites such as Cloudflare, Spotify, Discord, and others.
"From our initial analysis, the issue occurred due to an invalid automated quota update to our API management system which was distributed globally, causing external API requests to be rejected. To recover we bypassed the offending quota check, which allowed recovery in most regions within 2 hours. However, the quota policy database in us-central1 became overloaded, resulting in much longer recovery in that region. Several products had moderate residual impact (e.g. backlogs) for up to an hour after the primary issue was mitigated and a small number recovering after that."
Strong echoes of CrowdStrike in the cause of a major multinational outage being neglect, including for _testing_ and _staggering_ updates, by the vendor. status.cloud.google.com/incidents/ow...
— Ravi Nayyar (@ravirockks.bsky.social) 2025-06-14T04:35:16.624Z
PCIe 7.0 specification: PCI-SIG has released the PCI Express (PCIe) 7.0 specification to its members. PCIe is a high-speed standard used to connect hardware components inside computers. Version 7.0's main features are faster SSD data transfer speeds and various changes to support the growing AI market.
macOS Tahoe ASIF: Apple's next macOS release will come with support for a new disk image format named ASIF (Apple Sparse Image Format).
iOS Call Screening: Apple is adding a new feature in iOS named Call Screening. The feature automatically answers calls from unknown numbers and asks callers for a name and reason for calling. Users will then be prompted if they want to take the call. Apple estimates the new feature will help block up to one billion scam calls per year. Call Screening will ship with iOS 26 later this year. [Additional coverage in TechRadar]
Government, politics, and policy
Russian police seek access to bank accounts: Russian police officials are lobbying the Duma for access to everyone's bank accounts, despite bank secrecy protections and the right to freeze accounts even without making arrests. They say it's to combat fraud. [Additional coverage in TASS]
IRS needs better oversight of ID.me service: A US GAO report found that the IRS was not properly assessing and monitoring ID.me, the third-party-developed user authentication system the agency uses to allow US citizens access to the IRS portal. [Additional coverage in NextGov]
'[The IRS had] not shown documented procedures to routinely evaluate credential service providers' performance. '... identity-proofing process involves [AI] ... IRS has not documented these uses in its AI inventory or taken steps to comply with its own AI oversight policies'.
— Ravi Nayyar (@ravirockks.bsky.social) 2025-06-14T04:21:52.249Z
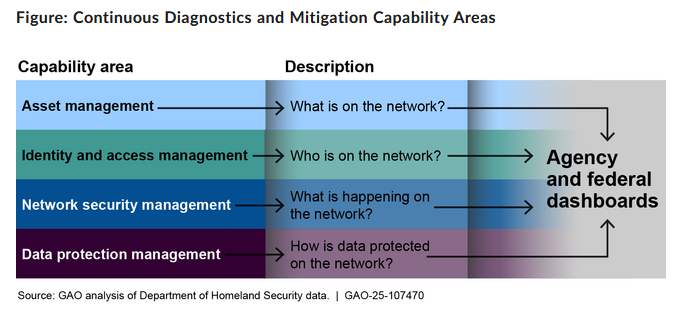
GAO finds gaps in DHS CDM: CISA's Continuous Diagnostics and Mitigation (CDM) program has only met two of its four key goals, a GAO report has found. The program provides federal agencies with a dashboard for tracking cybersecurity-related tasks. GAO says the program helped agencies reduce exposure to insecure configurations and vulnerabilities and also provided useful incident response capabilities. The program was not as successful with its two other goals of helping agencies implement network security and data management capabilities. [Additional coverage in MeriTalk]
UK Spending Review 2025: UK intelligence agencies and the NHS are the main beneficiaries of cybersecurity-related spending boosts this year, according to the UK government's Spending Review 2025. [Additional coverage in Bobsguide]
EU invests €145.5mil in hospital security: The European Union is investing €145.5 million to boost the cybersecurity posture of EU hospitals and healthcare providers. The money will go to two programs—Horizon Europe Programme (€90.5mil) and Digital Europe Programme (€50mil). The first will support the use of generative AI for cybersecurity applications, while the second aims to boost ransomware defenses.
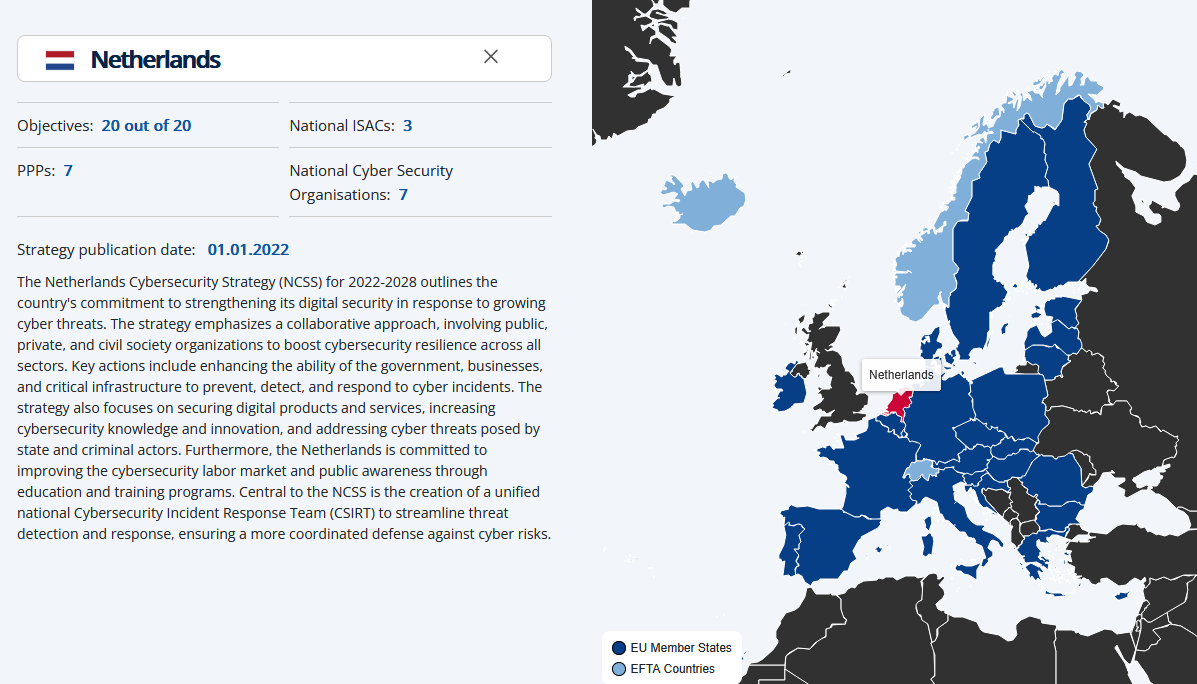
ENISA NCSS Interactive Map: The EU's cybersecurity agency ENISA has published an interactive map showing each member's implementations of national cybersecurity strategies and their status.
Sponsor section
In this Risky Bulletin sponsor interview Michael Leland, Field CTO of Island, talks about how Island manages risks from extensions, phishing and infostealers. Even when credentials are stolen, it is still not game over and there are still ways to prevent data loss and breaches.
Arrests, cybercrime, and threat intel
Scam compound dismantled in Bali: Indonesian police have arrested 38 suspects for running a cyber scam compound on the island of Bali. The group operated from five locations across Denpasar and allegedly received orders from a handler in Cambodia. The suspects targeted foreigners and sought to collect their personal data for future investment scams. Suspects were allegedly paid $1 for each user data point. [Additional coverage in the Jakarta Globe]
Ohio man sentenced for BEC scams: A US judge has sentenced an Ohio man to 57 months in prison for laundering money linked to business email compromise scams. Gabriel Waters, 54, registered US bank accounts where scammers sent stolen funds. He was also ordered to pay $547,000 in restitution to victims.
Ransomware gangs target SimpleHelp: CISA has urged US companies to patch their SimpleHelp servers. The agency says ransomware groups are targeting unpatched servers to breach corporate networks. The attacks are exploiting an unauthenticated path traversal vulnerability (CVE-2024-57727) that was disclosed and patched in January.
Iranian hacktivist activity: Iranian hacktivist activity is underway after Israel's attack on Iran on Friday. Known pro-Palestine and pro-Iranian groups have started leaking data from Israeli companies and taking down websites and other resources using DDoS attacks.
New npm malware: One hundred seventy-three malicious npm packages were discovered and taken down last week. Check out the GitHub security advisory portal for more details.
Malicious Firefox add-ons: Socket Security has found malicious Firefox add-ons on the browser's official store. One of the add-ons used Apple-style popups to redirect users to tech support scam pages. Several others manipulated user engagement metrics on platforms like Facebook by artificially inflating likes and views.
GrayAlpha (FIN7): Recorded Future has found new infrastructure linked to GrayAlpha (FIN7) operations, some used as recently as April.
Lockbit panel hack: Trellix looks at a recent dump of hacked data from the LockBit RaaS backend, specifically looking at affiliate activity.
Malware technical reports
Anubis adds wipe mode: The Anubis ransomware operation has added a "wipe mode" that permanently deletes all of the victim's files. It's unclear why they did this since the purpose of a ransomware attack is to extract a ransom. Deleting files will 100% dissuade victims from paying.
DeerStealer: eSentire has published a technical analysis of the DeerStealer infostealer, also known as the XFiles Spyware.
DarkHack ransomware: There's a new ransomware strain named DarkHack going around in the wild, targeting regular end users.
Sponsor section
APTs, cyber-espionage, and info-ops
APT naming scheme pushback: Former CISA Director Jen Easterly and former GCHQ NCSC CEO Ciaran Martin are calling out the cybersecurity industry for their silly APT names and their inability to arrive at a common naming scheme.
"The oft-repeated claim that a single universal naming system is 'not practical' or 'not possible' simply isn’t credible. The international community has standardized complex naming systems in every domain from biology to medicine to defense"
— Kim Zetter (@kimzetter.bsky.social) 2025-06-13T12:13:08.079Z
Kimsuky: South Korean security firm AhnLab has spotted a new Kimsuky spear-phishing campaign targeting the country's educational sector with malicious Word documents.
APT41: Resecurity looks at APT41's recent abuse of Google Calendar as a C2 mechanism, abuse first spotted by Google's Mandiant at the end of May.
Matryoshka BlueSky labeler: Anti-disinfo researcher Antibot4Navalny has released a BlueSky labeler for posts from accounts linked to Russian disinfo group Matryoshka.
Russian state disinfo bots are active on BlueSky for over 2 weeks now. They are posting fake videos using AI-generated voice to promote talking points of Russian state. Please help us to reduce its visibility: follow this labeler, choose Warn or Hide; spread the word: @ab4n-labeler.bsky.social
— antibot4navalny | bot blocker | блокировщик ботов (@antibot4navalny.bsky.social) 2025-01-03T12:31:15.372Z
Vulnerabilities, security research, and bug bounty
OneLogin vulnerabilities: SpecterOps has found leaked AWS credentials for IAM provider OneLogin that allowed the company access to the OneLogin API and customer logs.
"These logs leaked the customer API key that can be used to obtain the signing key and generate valid JWT tokens, enabling arbitrary user impersonation."
Pan-tilt-zoom camera updates: CISA has asked organizations to install firmware updates or restrict access to pan-tilt-zoom security cameras from four vendors. The devices are affected by similar vulnerabilities. They can let attackers access the cameras' admin panels using hard-coded credentials, execute malicious code, or leak user credentials and configuration files. Firmware updates are only available for PTZOptics camera models. ValueHD, multiCAM, and SMTAV have failed to reply to security researchers. CISA has asked companies to restrict access to these cameras to prevent future breaches.
Numa hotel chain IDOR: Germany's CCC has found an IDOR vulnerability in the online booking system used by the no-reception hotel chain Numa.
GIMP code exec: Security researcher Craig Young has found a vulnerability in the GIMP open-source photo editor that can lead to denial-of-service or code execution attacks.
Credentialless iframe abused for XSS: Security researcher Vsevolod Kokorin has abused a new browser technology named credentialless iframes for a new way to execute XSS attacks.
KSA financial software security review: A team of academics and security researchers from Theori have published details on vulnerabilities [PDF] they found in the KSA financial software—which is mandatory to use across South Korea's financial sector.
"While KSA 2.0, a suite of software mandated for online banking and public services in South Korea, aimed to bolster security, its flawed design and implementation highlight the risks of over-reliance on security solutions without rigorous testing. Motivated by real-world hacking incidents exploiting KSA 2.0 from North Korea in 2023, we investigated its major vulnerabilities. Our analysis uncovered four critical design issues: inconsistencies in threat models between KSA and web browsers, improper use of TLS, violation of browser sandboxing, and enabling user tracking."
Mitel security updates: Mitel has released a security update for its MiCollab VoIP telephony platform to fix an unauth path traversal.
IBM security update: IBM has released a security update for its Security Directory Container for a bug that can allow normal users to run commands as root.
Infosec industry
New tool—Objective-C helper: Security firm Synacktiv has released Objective-C helper, an IDA plugin for reverse-engineering Objective-C code.
New tool—COMmander: IBM X-Force researcher Jonathan Beierle has released COMmander, a tool to enrich defensive telemetry around RPC and COM.
New tool—GoClipC2: Security researcher Andy Gill has released GoClipC2, a PoC command and control framework that uses the Windows clipboard mechanism for communication in environments where traditional network-based C2 channels may be restricted or monitored.
Threat/trend reports: CyFirma, Foley & Lardner, HP Wolf Security, NZ NCSC, Pindrop, and Socket Security have recently published reports and summaries covering various infosec trends and industry threats.
Risky Business podcasts
In this edition of Seriously Risky Business, Tom Uren and Patrick Gray talk about how a Trump executive order has scaled back the government's cyber security ambitions. They also discuss North Korea's use of AI in its IT worker scam and the emergence of espionage-as-a-service... perhaps.
In this edition of Between Two Nerds, Tom Uren and The Grugq take a deep dive into the hackers of Unit 29155, Russian military intelligence's sabotage and assassination group.




